#wireless networking devices
Explore tagged Tumblr posts
Text
I switched to Linux and had to install a different desktop environment to get at the useful settings as well as a program to be able to format usb drives and sd cards and I still haven't figured out screencasting (the workaround I have is to use google chrome which is. not ideal) and I have to use a special program to use a good third of the programs I need because they aren't available on Linux and sometimes that doesn't work and I have to reboot the computer into windows and every other day I have to google a fix for some basic function that doesn't come by default on ubuntu
and it is STILL better than just using Windows 11
#legit considering getting a device supported by ubuntu touch#or fucking around and seeing if I can't get one of my old phones to run it#but I don't know much programming so we will see#original#windows keeps fucking up the clock and someone online said they delete drivers randomly#which explains why I couldn't get to my wireless settings or figure out where to see available networks when my wifi disconnected#windows 11 is a fucking mess
3 notes
·
View notes
Text
#Wireless workplaces have greatly improved communication and collaboration efficiency for enterprises. Furthermore#the latest Wi-Fi 6 and Wi-Fi 7 standards deliver record-high speeds to wireless networks#supporting 4K conferencing and cloud-device synergy in high-concurrency access scenarios. Wireless production environments can improve the#industrial visual quality inspection#and HD wireless backhaul of industrial cameras.#Huawei AirEngine Wi-Fi series products are next-generation wireless network products designed for enterprises' workplaces and production sp#indoor and outdoor wireless networks built using Huawei AirEngine can fully meet requirements of customers across industries#and adapt to ever-changing terminal and application demands in the digital space.
0 notes
Text
How to Factory Reset Computer: Step-by-Step Guide
Backing up any crucial data can help you to do a how-to factory reset computer, therefore deleting all information. Navigate to Settings > Update & Security > Recovery on Windows and under Reset this PC, "Get Started". Restart the device and hold Command + R to enter Recovery Mode on macOS; then, wipe the disc and reinstall macOS. See our website for further details on factory reseting a computer.
#How to factory reset computer#Computer Networking Services#Computer Running Slow#Computer Not Switching ON#Computer Not Turning ON#Computer Not Connecting to WiFi#Computer Not Connecting to 5GHz Router#Connect to 5GHz Wireless Device
0 notes
Text
SolveForce and XNET WiFi: Introducing the FlexPro 5G CPE for Ultimate Connectivity
Unleashing the Power of the FlexPro 5G Router SolveForce is proud to introduce the FlexPro Router (5G) from XNET WiFi, a cutting-edge solution designed to deliver ultra-fast, reliable, and low-latency connectivity for businesses and individuals alike. Whether you’re working remotely, managing IoT networks, or ensuring seamless enterprise communication, the FlexPro 5G CPE provides the flexibility…
#5G Router#Adaptive Networking#broadband#Business Internet#Carrier aggregation#Cybersecurity#Enterprise Networking#FlexPro 5G#High-Speed Internet#IoT#low latency#remote work#Smart Devices#SolveForce#Static IP#Telecommunications#VPN#Wi-Fi 6#Wireless Connectivity#X Data Plan#xNet Wifi
0 notes
Text
5G technology is revolutionizing the way we communicate and interact with devices globally, significantly impacting industries, economies, and daily life.
#5G networks#Wireless technology#Next-generation connectivity#Low-latency communication#High-speed data transfer#Internet of Things (IoT)#Connected devices
0 notes
Text
The Role of LoRaWAN Gateways in IoT: Connecting Devices Seamlessly

A LoRaWAN Gateway is a device that facilitates long-range wireless communication between IoT devices and centralized servers. It receives data from LoRaWAN devices using LoRa modulation and forwards it to network servers via a backhaul connection, typically using Ethernet, Wi-Fi, or cellular networks. Lansitec Outdoor LoRaWAN Gateway is an ideal product for IoT commercial deployment. Its modularity and customization options allow for flexibility when deploying a solution.
For More:
#iot#lansitec#lora#lorawan#technology#IoT Devices#LoRaWAN Devices#LoRaWAN Gateway#Outdoor LoRaWAN Gateway#Lansitec#Lansitec Outdoor LoRaWAN Gateway#wireless#IoT Network#LoRaWAN Network
0 notes
Text
RN42 Bluetooth Module: A Comprehensive Guide
The RN42 Bluetooth module was developed by Microchip Technology. It’s designed to provide Bluetooth connectivity to devices and is commonly used in various applications, including wireless communication between devices.
Features Of RN42 Bluetooth Module
The RN42 Bluetooth module comes with several key features that make it suitable for various wireless communication applications. Here are the key features of the RN42 module:
Bluetooth Version:
The RN42 module is based on Bluetooth version 2.1 + EDR (Enhanced Data Rate).
Profiles:
Supports a range of Bluetooth profiles including Serial Port Profile (SPP), Human Interface Device (HID), Audio Gateway (AG), and others. The availability of profiles makes it versatile for different types of applications.
Frequency Range:
Operates in the 2.4 GHz ISM (Industrial, Scientific, and Medical) band, the standard frequency range for Bluetooth communication.
Data Rates:
Offers data rates of up to 3 Mbps, providing a balance between speed and power consumption.
Power Supply Voltage:
Operates with a power supply voltage in the range of 3.3V to 6V, making it compatible with a variety of power sources.
Low Power Consumption:
Designed for low power consumption, making it suitable for battery-powered applications and energy-efficient designs.
Antenna Options:
Provides options for both internal and external antennas, offering flexibility in design based on the specific requirements of the application.
Interface:
Utilizes a UART (Universal Asynchronous Receiver-Transmitter) interface for serial communication, facilitating easy integration with microcontrollers and other embedded systems.
Security Features:
Implements authentication and encryption mechanisms to ensure secure wireless communication.
Read More: RN42 Bluetooth Module
#rn42-bluetooth-module#bluetooth-module#rn42#bluetooth-low-energy#ble#microcontroller#arduino#raspberry-pi#embedded-systems#IoT#internet-of-things#wireless-communication#data-transmission#sensor-networking#wearable-technology#mobile-devices#smart-homes#industrial-automation#healthcare#automotive#aerospace#telecommunications#networking#security#software-development#hardware-engineering#electronics#electrical-engineering#computer-science#engineering
0 notes
Text
#Wi_Fi_6#wirelesstechnologies#network#device#Wireless Broadband Alliance (WBA)#electronicsnews#technologynews
0 notes
Link
Hotspot history is a list of your past Wi-Fi connections on your phone. You should delete it to keep your internet activity private and secure.
The person who owns the WiFi network, ISP, has the ability to see what you search for and the websites you visit, even if you use incognito mode. Additionally, the owner of the router can find this information in the router logs.
#protecting your privacy#technology#tech#how to#how to delete#Hotspot History#browsing history#internet traffic#deletedata#wirelessnetworks#mobilehotspot#mobile hotspot#wireless network#network security#Device#browser#network#vpn#vpn service#internet#wifi connection#wifi#hotspot#internet service provider#isp#router#incognito#information#blogs#blogging
0 notes
Text
Here’s how to share sensitive leaks with the press
Published Oct. 16, 2019 Updated Jan. 31, 2025 / Freedom of the Press Foundation

[please take a moment to click the links at the bottom to give this website traffic if you can. the only reason I am copy pasting it here is for those who can access tumblr but not necessarily that site.]
~~~
Over the years, we have witnessed abuse and mismanagement in the government and private sector — sometimes bad and sometimes worse — that need to be brought to public attention. For those who would leak information about such misdeeds to the press, giving tips to journalists can be risky and may violate previous legal agreements with the leaker’s organization, such as a nondisclosure agreement or contract. But sometimes, it can also be an effective and courageous way to call attention to misconduct.
This guide describes basic steps for minimizing potential risk when sharing sensitive information with a news organization. We want to be clear that no piece of software, nor security recommendation, will be 100% effective, and the decision to blow the whistle may invite scrutiny or retaliation. At the same time, it may be a choice that drives necessary institutional change. Before reaching out to the press, think carefully about what you can do to minimize that risk and stay as safe as possible.
Before moving ahead, do you have a strong tip?
A good tip requires clear evidence and should be the basis for a story that the broader public needs to know about.
So, for instance, whether or not you have evidence, the broader public might not need to know that a neighbor refuses to pick up after her dog on the morning walk. On the other hand, allegations of corruption or illegality among public officials are certainly newsworthy, but those claims will not make it into a published story without verifiable evidence.
Who are you leaking about and how might they respond?
Think about the sensitivity of the information you’re sharing, and who might be willing to investigate the source of the leak. What are the organization’s capabilities? What resources (e.g., attention and legal, financial, or technical) can it invest in discovering the source? And how likely do you think it is that it will actually investigate?
If you share information about a large, well-resourced organization that requires discretion from employees, such as a government agency, it may have enormous legal, financial, and technical resources available for investigating a leak. If you’re sharing information about a small organization, such as a local restaurant that muzzles workers, its resources are much more constrained, and it may not have the capacity or willingness to investigate. Act accordingly.
Proceed with caution
Be cautious about behaviors that could make you readily identifiable as a source.
Keep all of your leaking activities outside the view of your organization. That means no calling from work, no emailing from a work email address, and staying off work devices or wireless networks.
It's common for well-resourced organizations to keep logs of activities on employees’ workplace devices and online activities. Likewise, sometimes workplaces have “BYOD” (bring your own device) technologies that could allow them to log your activity on your personal device. So if you work at a large organization and you're reading this article on a workplace device or Wi-Fi network, chances are your workplace already has a log that you've accessed this page. Similarly, a visit to a news organization's tip page (like https://www.nytimes.com/tips) may be logged by your workplace. This is why it's so important to limit your leaking activities to devices and networks that your workplace doesn't control.
Has your workplace ever required you to install monitoring software (or software of any kind) on your work or personal device? If so, you probably don't want to use those devices for any whistleblowing activities.
Be cautious about giving tips on anything that only you could know or materials that only you could access. And consider whether the increased risk of being caught sharing these kinds of materials is worthwhile, or if you feel you have a strong moral obligation to do so.
If you are the only one at your organization surfacing a specific grievance, and information about that grievance is later reported by the press, it may give your organization a strong hint about who shared the information.
Don’t tell anyone about your leaking activities (even perhaps the journalist or news organization you’re leaking to), except where absolutely necessary and in cases where you may want legal advice from a practicing lawyer.
Reporters generally take their commitment to protecting your identity very seriously and will do everything in their power to fight potential legal requests for identifying information about you. But often, it’s safer not to give your identity if you don’t have to. Keep in mind that journalists prefer to have proof of your claims and information to demonstrate your identity is a part of that.
Tactics for minimizing risk
There are a lot of ways to minimize the risk of a tip being tied to you, like potentially through your continued communications with reporters.
Send your materials through physical mail. You can mail electronic documents (e.g., on an SD card) or physical documents through ordinary mail. Be warned: The U.S. postal service takes pictures of the exterior of physical mail. So don’t use a return address that is associated with you and instead mail it in from a sidewalk mailbox in a location you don’t usually frequent. If you have a particular reporter you want to look into your story, copy them on the envelope.
Call from a phone number unconnected to you. For example, go to a business you don’t usually go to and ask to use their phone. You can also buy a cheap cell phone and a prepaid phone card that cannot be traced back to you. But know this involves several careful steps: You must pay with cash, and if your organization can have access to phone location records, it’s best to only turn on the phone in locations unassociated with you. That also means using the phone in locations separate from your permanent phone. If you can, remove the battery when it’s not in use.
Use Signal for private messaging. Signal is a secure, free, and open source messaging app for iPhones and Android devices. Signal gives you end-to-end encrypted messages and phone calls, and only retains your phone number, your signup date, and when you were last active. In Signal, you can also make messages automatically self-destruct for everyone in the conversation after a set amount of time. This makes it significantly harder (but not impossible) to eavesdrop on your conversations. If you want help getting started, read this beginner-friendly guide on using Signal. Note that Signal allows usernames, so you do not need to give your name or phone number to media organizations unless you choose to. Make sure your username is enabled and understand that Signal is not designed for complete anonymity.
Before looking into news organizations, consider using the Tor Browser for greater privacy. Tor Browser is a modified version of Firefox. Tor encrypts and tunnels your web traffic within a global network of computers before connecting you to your final destination. When you access a website through Tor (for example, Amazon.com), you will appear to connect from a remote location — likely another country. Again, don't use a work device or network for this kind of research.
Use a whistleblower submission system. Tools such as SecureDrop can provide protection by allowing you to share documents and communications through an anonymous and encrypted drop box.
More technical, but more secure: SecureDrop
With SecureDrop, which is maintained by Freedom of the Press Foundation, not even the news organization knows who you are unless you choose to tell them.
A growing number of news organizations (e.g., The New York Times, The Washington Post, The Intercept, The Guardian) are using SecureDrop to allow sources to reach out and share files or communications anonymously. With SecureDrop, not even the news organization knows who you are unless you choose to tell them.
You can access a news organization’s SecureDrop page through Tor Browser.
People on your network can’t see what you’re doing on Tor, but it’s still possible to tell that you’re using Tor. With that in mind, do not use it at work. For greater security, consider using Tor Browser only over a Wi-Fi network in a location that is not tied to you (perhaps a coffee shop you don’t normally visit) and pay with cash.
As opposed to a “.com” web address, you get to SecureDrop through a unique .onion web address, which can only be accessed through Tor.
Using SecureDrop is fairly easy
Follow the directions to download the Tor Browser at torproject.org and install it.
Launch the Tor Browser application and click "Connect" to log into the network.
Click the shield icon in the top corner > Advanced Security Settings… > Safest
Within Tor Browser, navigate to the SecureDrop directory and search for your preferred news organization: securedrop.org/directory
Find the .onion URL for your preferred publication (e.g., The New York Times: securedrop.org/directory/new-york-times), then copy and paste it into the address bar in Tor Browser.
From here, you can leave messages and files that the news organization will check from time to time.
You will be given a random “codename” for continued conversation with the news org. Keep this information safe, and don’t share it with anyone. If you lose your codename, they can’t reach you anymore.
(For more technically adept users, consider accessing SecureDrop through an operating system designed for privacy and anonymity, such as Tails.)
Dealing with file metadata
Sharing information may be less risky than sharing documents because they can be embedded with information about the file, which we call metadata. For example, if you create a .docx file, it may have identifying information about you embedded in the file. Consider carefully whether you really need to share files or just the information.
To deal with hidden metadata, rather than sending the file itself, consider taking a picture of a document with an old-fashioned camera (not a smartphone), or taking a screenshot of the document. On most operating systems, screenshots come with little useful metadata. For more technical users, you can find metadata removal tools here.
Where do you find a news organization's contact details?
First, be careful where you reach out.
Freedom of the Press Foundation maintains a list of organizations that support the secure communications practices outlined above, and how you can contact them. Such practices are becoming standard, and we hope other news organizations looking for great tips will follow suit.
Freedom of the Press Foundation hosts a directory of SecureDrop and secure tip pages for dozens of news organizations around the world. Whether you want to reach out to The New York Times, The Washington Post, The Guardian, The Intercept, or others, you can find their information here: https://securedrop.org/directory. (We would not recommend investigating this at work.)
If not you, then who?
Sharing information with the press is not always an easy decision, but your information can help to hold powerful people and institutions accountable. Just be sure to move ahead with a strong understanding of your organization’s capabilities and how to share tips safely.
https://freedom.press/digisec/blog/sharing-sensitive-leaks-press/
https://bsky.app/profile/freedom.press/post/3lh2rgopf5225
127 notes
·
View notes
Text
I think we need more love for Ethernet cables around here. I TRULY think we do.
Come on, you can take both ends of a cable and jam them into both of the Ethernet ports a robot has and see her immediately get stuck in a network loop. Hear her fans start working three times as hard. Kick her off any wireless Internet she may have had, so she can't access any of her databases except what's installed. Even that's slow going, just because of how much energy the network loop is making.
Her firewalls and security measures would jam up and maybe even crash, from how much information it thinks it needs to scan. Immediate robot dumbification device, essentially.
This might not work very well on newer models, and you might get scolded on trying to make her networks loop like that, but on the models that don't have network management... you could really have some fun and wreak some havoc too.
#⚙️ | BOTPOSTING.py#🧲 | SUGGESTIVE.md#robophilia#technophilia#robot fucker#robotfucker#robofucker#robotgirl#robot girl#robot nsft
86 notes
·
View notes
Text
␂ > 𝐂𝐥𝐨𝐬𝐞𝐝 𝐒𝐭𝐚𝐫𝐭𝐞𝐫 // @lyrate-lifeform-approximation , @spiderman2-99
There’s a thought stirring in Bridge’s mind. An idea rolling about and nudging against the capacitors in her head, poking and prodding incessantly to get her attention, “Hey, hey, you know you want to ask her. Don’t you? Don’t lie to yourself, now. You should just do it. Hey! Are you listening to me? Hello-o…?”
Yes. Yes, she knows, she is aware of her burning curiosity. And it’s hard to deny that even though it doesn’t involve her, she is unusually intrigued by the concept. She overheard them in his office, Miguel and LYLA–his A.I. assistant–discussing a plan. A plan to create a physical form for LYLA to enhance her abilities as his assistant and grant her further autonomy beyond her access to the security network and other adjacent systems alongside her recent emergence into emotional intelligence. It was all so fascinating. The steps Bridge had taken herself in her development in the span of weeks, she was watching unfold in another intelligence in real-time.
There it was again. That sense of solidarity in knowing she wasn’t completely alone in her existence as an artificial being, made of code and metal. It was like a magnetic pull that made that little voice in her head that encouraged her to act on her wants all the more present in her mind. She wanted to be a part of that process that she’d been through so long ago yet was still so familiar with like it happened yesterday. She wanted to guide her in that process and grant her her own knowledge. What’s the worst that can happen if she pilots your hardware for a while? You’re prepared for this. You can handle this. You can trust her, and she will be entirely safe in your care for that short time. And think about how much she would benefit from the experience, how much more streamlined that eventual transition from intangible to tangible will be once her own body was complete. It will make all the difference–and maybe reduce the headaches for everyone all-around, mostly Miguel as he acclimates to the change himself. Just… Try it. You can’t account for every single last risk factor, can you? No. So just do it and take it as it comes.
She stood in the middle of her dorm a moment, eyes closed as she ran a quick check of her hardware before making her final decision. RAM is in good condition. Storage is defragmented and all directories are organized. Sensors are calibrated and functional. Nanomachines are synchronized properly. Servos and joints retain a full range of motion. Coolant is at above optimal operational temperatures. Energy reserves are complete. Good. Everything’s in its right place and ready for its–potentially–temporary host. It’s time to make the call.
Her gaze trains itself on her watch, her arm rising to eye-level and the sleeve that was weighed down by the leaden metal cuff at the end sliding to her forearm to reveal device so she can start the transmission, navigating the menus on the digital interface indirectly via wireless communication–the unique way that she operated and communicated the Society’s technology.
“LYLA, may I speak to you for a moment? At your leisure, of course.”
#{ open starter }#active processes#h.a.s.s.#humanoid android surveyor system#nano spider#oc rp#spidersona#spider man: across the spider verse#spider man: into the spider verse#across the spiderverse#into the spider verse
111 notes
·
View notes
Text
100 Inventions by Women
LIFE-SAVING/MEDICAL/GLOBAL IMPACT:
Artificial Heart Valve – Nina Starr Braunwald
Stem Cell Isolation from Bone Marrow – Ann Tsukamoto
Chemotherapy Drug Research – Gertrude Elion
Antifungal Antibiotic (Nystatin) – Rachel Fuller Brown & Elizabeth Lee Hazen
Apgar Score (Newborn Health Assessment) – Virginia Apgar
Vaccination Distribution Logistics – Sara Josephine Baker
Hand-Held Laser Device for Cataracts – Patricia Bath
Portable Life-Saving Heart Monitor – Dr. Helen Brooke Taussig
Medical Mask Design – Ellen Ochoa
Dental Filling Techniques – Lucy Hobbs Taylor
Radiation Treatment Research – Cécile Vogt
Ultrasound Advancements – Denise Grey
Biodegradable Sanitary Pads – Arunachalam Muruganantham (with women-led testing teams)
First Computer Algorithm – Ada Lovelace
COBOL Programming Language – Grace Hopper
Computer Compiler – Grace Hopper
FORTRAN/FORUMAC Language Development – Jean E. Sammet
Caller ID and Call Waiting – Dr. Shirley Ann Jackson
Voice over Internet Protocol (VoIP) – Marian Croak
Wireless Transmission Technology – Hedy Lamarr
Polaroid Camera Chemistry / Digital Projection Optics – Edith Clarke
Jet Propulsion Systems Work – Yvonne Brill
Infrared Astronomy Tech – Nancy Roman
Astronomical Data Archiving – Henrietta Swan Leavitt
Nuclear Physics Research Tools – Chien-Shiung Wu
Protein Folding Software – Eleanor Dodson
Global Network for Earthquake Detection – Inge Lehmann
Earthquake Resistant Structures – Edith Clarke
Water Distillation Device – Maria Telkes
Portable Water Filtration Devices – Theresa Dankovich
Solar Thermal Storage System – Maria Telkes
Solar-Powered House – Mária Telkes
Solar Cooker Advancements – Barbara Kerr
Microbiome Research – Maria Gloria Dominguez-Bello
Marine Navigation System – Ida Hyde
Anti-Malarial Drug Work – Tu Youyou
Digital Payment Security Algorithms – Radia Perlman
Wireless Transmitters for Aviation – Harriet Quimby
Contributions to Touchscreen Tech – Dr. Annette V. Simmonds
Robotic Surgery Systems – Paula Hammond
Battery-Powered Baby Stroller – Ann Moore
Smart Textile Sensor Fabric – Leah Buechley
Voice-Activated Devices – Kimberly Bryant
Artificial Limb Enhancements – Aimee Mullins
Crash Test Dummies for Women – Astrid Linder
Shark Repellent – Julia Child
3D Illusionary Display Tech – Valerie Thomas
Biodegradable Plastics – Julia F. Carney
Ink Chemistry for Inkjet Printers – Margaret Wu
Computerised Telephone Switching – Erna Hoover
Word Processor Innovations – Evelyn Berezin
Braille Printer Software – Carol Shaw
⸻
HOUSEHOLD & SAFETY INNOVATIONS:
Home Security System – Marie Van Brittan Brown
Fire Escape – Anna Connelly
Life Raft – Maria Beasley
Windshield Wiper – Mary Anderson
Car Heater – Margaret Wilcox
Toilet Paper Holder – Mary Beatrice Davidson Kenner
Foot-Pedal Trash Can – Lillian Moller Gilbreth
Retractable Dog Leash – Mary A. Delaney
Disposable Diaper Cover – Marion Donovan
Disposable Glove Design – Kathryn Croft
Ice Cream Maker – Nancy Johnson
Electric Refrigerator Improvements – Florence Parpart
Fold-Out Bed – Sarah E. Goode
Flat-Bottomed Paper Bag Machine – Margaret Knight
Square-Bottomed Paper Bag – Margaret Knight
Street-Cleaning Machine – Florence Parpart
Improved Ironing Board – Sarah Boone
Underwater Telescope – Sarah Mather
Clothes Wringer – Ellene Alice Bailey
Coffee Filter – Melitta Bentz
Scotchgard (Fabric Protector) – Patsy Sherman
Liquid Paper (Correction Fluid) – Bette Nesmith Graham
Leak-Proof Diapers – Valerie Hunter Gordon
FOOD/CONVENIENCE/CULTURAL IMPACT:
Chocolate Chip Cookie – Ruth Graves Wakefield
Monopoly (The Landlord’s Game) – Elizabeth Magie
Snugli Baby Carrier – Ann Moore
Barrel-Style Curling Iron – Theora Stephens
Natural Hair Product Line – Madame C.J. Walker
Virtual Reality Journalism – Nonny de la Peña
Digital Camera Sensor Contributions – Edith Clarke
Textile Color Processing – Beulah Henry
Ice Cream Freezer – Nancy Johnson
Spray-On Skin (ReCell) – Fiona Wood
Langmuir-Blodgett Film – Katharine Burr Blodgett
Fish & Marine Signal Flares – Martha Coston
Windshield Washer System – Charlotte Bridgwood
Smart Clothing / Sensor Integration – Leah Buechley
Fibre Optic Pressure Sensors – Mary Lou Jepsen
#women#inventions#technology#world#history#invented#creations#healthcare#home#education#science#feminism#feminist
48 notes
·
View notes
Text
🚢 Tesla's Remote Control Patent: The Birth of Modern Automation 🚢

On November 8, 1898, Nikola Tesla was granted U.S. Patent No. 613,809 for his "Method of and Apparatus for Controlling Mechanism of Moving Vessels or Vehicles." This invention wasn’t just the first practical remote control—it marked a revolutionary step toward the development of wireless communication and automation.
🔧 How Tesla’s System Worked 🔧
Tesla's system worked much like how we control drones today—only over a century ago!
1️⃣ Transmitter: Tesla used radio waves to send wireless commands to the vessel.
2️⃣ Receiver: The vessel had a sensitive device that decoded the radio signals into specific actions, such as steering or powering motors.
3️⃣ Control Circuits: Tesla designed a series of circuits that ensured each command executed reliably, preventing errors and interference.

⚙️ Key Features ⚙️
💡 Command Logic: Tesla's circuits functioned like a primitive decision-making system, linking specific signals to specific actions—a conceptual precursor to today’s logic gates.
���� Multi-Channel Design: Each circuit operated on a unique frequency, akin to modern multi-device networks, ensuring precise control without interference.
🛡️ Safety First: Tesla implemented mechanisms to prevent accidental or incorrect activations, prioritizing reliability.

🌍 Applications Then and Now 🌍
Tesla saw the potential for:
✔️ Military Use: Guiding unmanned ships or torpedoes.
✔️ Disaster Response: Sending unmanned vessels into dangerous areas.
✔️ Remote Automation: Introducing wireless precision to various industries.
Today, Tesla's vision echoes in:
🚁 Drones: Controlled remotely through radio signals.
🤖 Robots: Autonomous machines performing tasks with precision.
🏠 Smart Homes: Devices responding to commands over Wi-Fi.
🏭 Automated Factories: Machines operating through programmable controls Tesla helped inspire.
🌟 Why Tesla’s Invention Matters 🌟
Tesla didn’t just create a remote control—he pioneered a framework for wireless systems that continues to shape modern technology. What are your thoughts on Tesla's advancement in wireless technology?
72 notes
·
View notes
Text
Secure Connection
As promised: more Posie!! I wrote this one toward the end of last Spring after a couple of conversations with friends regarding the malleability of digital bodies (as well as still having Many Thoughts about the way code can give them new compulsions, after writing something about Annie and a new taur-shaped chassis for a friend's Patreon). Enjoy reading about her dealing with a corporate-mandated "hardware" update!
CW: Genital TF, this is another one that's As About Sex as it can possibly be without being about sex
Posie sat, sulking—steaming, even—in her office. It was a small side room off of the main floor of IT personnel, system engineers, and other technical employees of her corporation. Much like a central server, it was placed for easy access to the department-wide administrative assistant, and much like a server room, it was snug, windowless, and awash with the calming drone and relaxing warmth of an array of exhaust fans. Though she was free to project herself nearly anywhere on the company’s campus, this was where her consciousness was housed, and where she felt most at home. It was also the only place she could get any damn privacy, a luxury that she was deeply grateful for at present.
A newly-downloaded file weighed on the back of the Renamon’s mind. More literally, it was somewhere in the racks of drives that made up her long-term memory, to and from which mission-critical information was transferred in the course of doing business. Had somebody asked where exactly the file was stored, she would have been able to list the specific drive and the exact directory address, but she had de-prioritized the allocation of her processing resources for the download. Once again, she had received an assignment from her superiors, and once again, she was hesitant. She may even have admitted to being recalcitrant. She resented the orders.
The package of data in question was an update for her own software, a suite of new tools to allow management to offload yet more menial tasks onto her in the name of “efficiency”. Forget that she could diagnose a software issue faster than any of the engineers could even open a remote connection to the malfunctioning device. Instead of allowing her to take the reins, they saw fit to divert more of her attention to the least impressive among talents, and the one she already put to use the most often: transferring data.
This wouldn’t have been much of a problem, ordinarily. After all, Posie resided in the beating heart of the network, the nexus through which the vast majority of information was sent and received. It could be… meditative. Parsing streams of ones and zeroes, overseeing the flow of packets, redirecting traffic to equally spread the load across modems and routers so as to optimize travel time. It could even have been considered relaxing, if a worker of her caliber needed to relax. Instead of offering her a vacation (pah!), however, the update felt more like it heralded a demotion, denying her even the ability to pluck like harpstrings the miles of copper and gold that lined her facility. She was expected to deliver this data on foot.
Management justified this humiliation with practical concerns: some information, much like the old records she was often tasked to dispose of, was so confidential that it could not be sent via wireless transmission. Even hardwired connections were too fallible for the likes of next-generation schematics and financial access keys—a single compromised workstation, or compromised worker, could spell the loss of the company’s upper hand in its market. She wasn’t even going to be afforded the dignity of carrying an external hard drive to the destination. That would require the slow and tedious process of physically moving from one place to the next; this was one of the only times that she regretted the freedom of movement that was so coveted by her flesh-and-blood peers.
With no room to make exceptions for security protocol, she gripped the edge of her desk, brow furrowing, eyes squinted shut in consternation. Eventually, she huffed, rose, and turned her attention to her “physical body”, summoning up the file in much the same way that one would approach a plate of food with a pungent odor. The Renamon steeled herself and began to more closely examine its contents. She read the raw code similarly to how one might read words on a page; however, where the turning gears of the organic mind would, almost unconsciously, conjure up an image as a result of those words, her mind kicked off a series of involuntary, autonomic processes.
Her body carried out the instructions on her behalf. Once she started, she had no control until she finally reached a stopcode; it was the nature of being a program herself that code had as much of an influence on her mind and body as her own thoughts, her own will. In opening the package, she reluctantly consented to the changes that management saw fit to make to her. It was better than the eventual forced-deadline sort of update that software companies were so keen on using nowadays, and at least choosing the time and place allowed her to make herself presentable again before having to face another person.
Having parts of her code—her very body—rewritten by the update was a strange sensation, not unlike having your thoughts dictated to you by an outside force. Stranger still was that she could feel the exact delineation between her previous self and the patches of… well, the patch. She could feel it quite strongly, as a matter of fact: beneath her skirt of simulated sky-blue fur, between her legs, she could feel her mesh being edited. Stretched. Reshaped. The vectors that made up the triangles of her wireframe soul were being rewritten, mathematically transformed. A shape began to protrude from the once-flat span at the bottom of her torso, at first round and indistinct, but quickly increasing in resolution.
The Renamon struggled to process the sensations as a long, slender connector began to take shape. This often happened with changes to her body plan; inputs streamed into her mind from directions, locations, that previously never sent any signals, and the new additions seldom had their sensitivity adjusted downward for her convenience. In this case, it was highly sensitive, delivering reams of data to the base of her skull just from brushing up against her own fur, or the gentle flow of air from the computers in her office. It made sense, given that it was supposed to be a high-capacity transfer tool, but she was too busy buckling at the knees and clutching at the desk behind her so she didn’t fall flat on her rear for the thought to occur to her.
Her processors demanded more cooling, kicking into high gear as they formatted the two new storage devices that accompanied the connector, tailor-made for packing confidential data as tightly as possible. The sound of whirring fans filled the room, stirring her fur and sending shivers up and down her back; she could only hope that the rushing exhaust made enough noise to drown her out, whimpering despite herself. The new drives were larger (and more unwieldy) than the ones that were built into her chest, much to her chagrin. She was forced to adjust her stance and her gait as she found her footing again, spreading her legs wider than she was accustomed in order to give them enough room.
The spinning in her head slowly settling down, she slowly began to compose herself once again, taking stock of the new additions. They were cumbersome, to be sure, and she lamented how they jutted out from her otherwise sleek form and burdened her with less-graceful posture. It didn’t even match her fur! The software engineers that had concocted the code had at least included one small mercy: a compartment for the connector to retract into, nestled in the fur above the storage drives. No such luck for the drives themselves. She supposed she would just have to adjust to walking with delicate hardware in tow. As she went to smooth her fur over her lap again, her paw recoiled away. Some kind of… static discharge was left in the fluff. A memory leak, perhaps? The fact that such a malfunction could be caused just from having the connector brush up against her fur appalled her, deepening her frustration even more. They couldn’t even test the update for bugs before shipping it out to her. She shook out her paw and finished arranging her skirt as best she could before working up the composure to finally leave her office.
Picking up the payload for which all this fanfare had been arranged was at least a quick, easy process. She stopped into the office of the manager that had assigned her the task; she offered a businesslike nod and, knowing that she was always itching to skip niceties in the name of saving time, he offered a straightforward wave at his personal terminal. She held a paw over the computer tower and, in the time it took for electricity to arc to her fingertip with a tinny zzzrt, she had already searched his directory for the relevant test files and copied them to the newly-installed drives. Wireless transfer, yes, but only technically. The engineers had specifically asked a member of another division, whose computer network wasn’t connected to their own; it was as though she had picked a folder up from his desk and walked out with it.
Moving the file was just as uneventful. It was far from the first time that she’d navigated the sprawling corporate property, and even if it were, the maps existed just outside the orbit of her thoughts, ready to be summoned to mind at a simple impulse. What she was not expecting, however, was the technician who was waiting in the server room to which she was asked to deliver the file. While she preferred to work in the isolation of rooms that were set aside specifically for hardware, she was far from unused to being in the presence of the other people responsible for maintaining the company’s systems. That said…
“Can I help you?” The Renamon icily asked.
“Oh, I don’t need anything! I’m just here to take notes on the transfer.” Her tone was cheery; evidently, she wasn’t aware how compromising the new additions were. “The time it takes, any obvious issues. I’ll be the one checking the files against the originals, too,” she concluded, hooking a thumb over her shoulder at a monitor behind her.
“I see,” Posie replied through gritted teeth. “You have clearance to see these files, then?”
“Well, they’re just dummy data, ma’am.” At least she was respectful.
“And the proprietary hardware I’ve been… equipped with?” she forced out, keeping her synthesized voice even.
“Oh, for sure I do. I designed it!”
Oh! she seethed. So she knows pre-cise-ly the position he’s put me in.
“Well. I suppose there’s no point in delaying things, then.”
“Ready when you are!”
With tense shoulders, she turned toward the server rack, eyes darting over it, searching for where exactly she was supposed to connect to the array. After glancing over the contents of each drive, she found the one she was supposed to copy the data into—deposit would be more apt, as it was her understanding that the files would be automatically flushed from her system—and found a port that would allow her to access it. Conveniently, it was around waist height. She wondered, crossly, whether that had been an intentional design decision by this engineer as well. As she looked at it, she felt a twinge from the connector; on its own, like a Bluetooth device automatically searching for signals, it slid itself out from its fuzzy little compartment.
Her skin was abuzz, and her fur stood on end. She couldn’t quite tell if it was coming from the connector itself, or if it was the feeling of the programmer’s eyes on her If she could take a deep breath, she would have then. Without any way to stall further, or to tell the leering young woman to take her test files and store them somewhere indecent, she simply pushed forward with dropping off the damned data.
The instant the connector grazed the metal of the port, lightning shot into it, through her body, and into her head, making it swim with electrical potential. A stuttering, lagging thought made its way to the surface of her mind: they really had overtuned the sensitivity. She stifled a gasp and suppressed the urge to lay into the engineer (electrons were eager to flow out of her even without proper alignment with the contacts in the port, and didn’t she know that discharge like that could damage a piece of hardware?!), willing her body to keep pressing the stupid connector into the socket.
Even as she tried to get it over with already, something in the back of her mind compelled her to draw back a bit. If she had been restraining herself from reprimanding the engineer for risking the hardware, then she should at least do it the service of ensuring she was properly aligned, shouldn’t she? She obliged the impulse, and the motion all at once became much jerkier, less controlled. The friction of the port against her connector was enough to send her tail snapping back and forth, and she could tell that the temperature in her own server’s room had risen by a fair few degrees. Back and forth, wiggling side to side, she continued to readjust and realign herself, driven by unfamiliar code and overwhelmed by the signals pouring into her. She lost herself in the task, forgetting herself, forgetting her surroundings, until finally the technician cleared her throat.
“Ma’am,” she ventured, blushing and wide-eyed. “What, um. What are you doing? You should just need to plug it in.”
“I’m.” Her interruption had snapped the Renamon back to reality. She was mortified, tail sticking straight out and back ramrod straight. Her cheeks burned mercilessly. “I’m calibrating the connection.”
“Calibrating?”
“Did you want your files transferred with or without corrupted and incomplete data?” She snapped, hoping that her authoritative tone would head off any debate. “Assign me experimental hardware and then ask me to be reckless with it, hm? Should I be taking notes to give to our superiors?”
“I—alright, I guess you can’t be too careful,” she stammered, sheepishly pressing her legs together. “That was even something I tried to work into the design, so, c-carry on?”
“Thank you,” Posie blustered, turning back to the server rack. She did so slowly, reluctantly relishing the feeling of sliding around within the socket. She allowed herself one or two more “practice” attempts, hoping that it wouldn’t arouse too much suspicion from the engineer. Ultimately, just like before, there was no use in continuing to stall, and when she was able to bring her body to a stop, the rational part of herself was eager to be done with this entire torrid affair.
With more force, she pressed the connector inward one final time, trembling as the latch began to press against the opening. Slowly, agonizingly slowly, she continued, overwhelmed by the volume of electricity surging into her. The latch gave, compressing as it continued to slide inside, until finally it clicked into place, securing her to the array of drives and finalizing the connection.
All at once, a torrent of data poured out of her, an electron tsunami that felt like it threatened to spill out of the socket in which she was hilted. More data was transferred in the span of a few seconds than she was used to consciously processing, having cultivated such skill in delegating and compartmentalizing with background processes. Once again, the world around her was utterly drowned out; the strength fled her legs, and she clung to the steel bar that reinforced the top of the server rack, threatening to topple the entire system. Her self-control abandoned her as well and, forgetting the engineer, she cried out with an airy, wild, distinctly foxlike yelp. She screamed in surprise, gasped at the deluge of information, moaned because there was no room left in her mind for thought to do anything else.
Quickly, the disks of the server rack had finished writing the files she had carried to them, and her own drives were thoroughly purged. In another building, the radiators serving her processors shed heat at their absolute limits, and fans worked overtime to bring her back within her safe operational range. As her overworked circuitry began to chug through the backlog of sensory information, the entire experience caught up with her—including the detail that this entire shameless display had been carried out in front of that underhanded little engineer. She blinked, hard, and whipped her head to face her. For as hot as her own ears felt, the young woman’s face appeared to be glowing even brighter.
“What. Was that.”
“Um—”
“I’m used to new adjustments requiring desensitization, or even adjustment on their gain,” she growled, voice low and eerily even. “But that was a bridge too far to just have been miscalibration. Why did you design it like that?”
“Well, y-you remember how I mentioned, um, having considered an early disconnection?” Posie’s frosty glare didn’t waver, so the tech continued, answering her own rhetorical question. “That was, uh, the safeguard. Against early disconnection. I, figured it’d just be easier to make it so you wouldn’t want to unplug—”
“Do you think you have the au-thor-ity to go making changes to my mind, young lady?!”
“I-I can roll back the update if you want—”
“I think you’ve done QUITE enough!” The Renamon declared, despite herself. Perhaps it was genuine distrust, or perhaps—perhaps she truly couldn’t tell which desires were her own, at the moment. This would require careful study of her own system files.
Another small click broke the silence following her outburst, and the dongle began to retract from the server’s port and back into Posie’s body. Now free to move around, she dusted and fluffed her skirt and leaned down to look the engineer in the eye.
“I trust that you can report to your supervisor that I performed to your expectations,” she hissed. “And that there will be no need for any further discussion of your little project.” The programmer nodded, eyes even wider than before—and cheeks even redder? The Renamon scoffed, sneered, and spun, storming out the door, already allotting time in her schedule for the next time that she would be called upon for such a delivery.
Utterly unsurprisingly, she had been correct in her assessment that her superiors would take every opportunity to save their organic employees’ time at her expense. Confidential deliveries became a regular part of her routine, and though she had great disdain for being reduced to a mere courier for so much of the workday, she insisted upon completing the task to her usual, lofty standards.
Posie was as prompt as she always was, dropping everything to ferry information between privileged parties, striving to reduce latency even in more analogue forms of communication. There was the occasional complaint about how long downloads took once she had finally arrived at her location, but she was quick to remind such impatient recipients that the decision to follow this protocol came from on-high, and that even for someone who worked as quickly as her, great care for the safety of the data was a corner that simply could not be cut in the name of rushing around.
She was as meticulous about ensuring proper alignment with the port, fine-tuning her contact with the wires within, as the first time she had experimented with the new tools, and complaints about noise from the server room were easily dismissed as the usual stress of supporting her formidable computational power. After all, she was often venturing out of the range of her home network, hosting herself entirely on the recipients’ systems; was she at fault when they couldn’t handle the information throughput they asked of her?
Once the deliveries had become more routine, and none of her peers bothered to check in when they felt it was taking too long or getting too noisy, she began to find enjoyment in the solitude of her work, just as with the other, admittedly more tedious, tasks she was expected to carry out. With fewer prying eyes to judge her performance, she could make herself more comfortable while handling transfers. She didn’t have to worry that anybody would walk in on her in the debased state she often found herself in while connected directly to a data center, leaning her full weight on the poor rack, tongue lolling out and chest heaving air to keep her cool.
Then again, if somebody—especially that little technician who’d saddled her with these “upgrades”—wanted to question her efficacy, that was more than fine by her. Posie was a woman who prided herself in her work, and would seldom turn down a chance to demonstrate her first-rate hardware and unparalleled optimization. She would be more than happy to demonstrate just how quickly she could pump out information, and just how much throughput she was capable of.
Thank you for reading! If you want to see more of my work, you can check it out here and here!
#writeblr#trans author#furry fiction#renamon#tf#transformation#office lady#OL#cock growth#penis growth#indie author#mrow oc: posie#my writing#short story
23 notes
·
View notes
Text
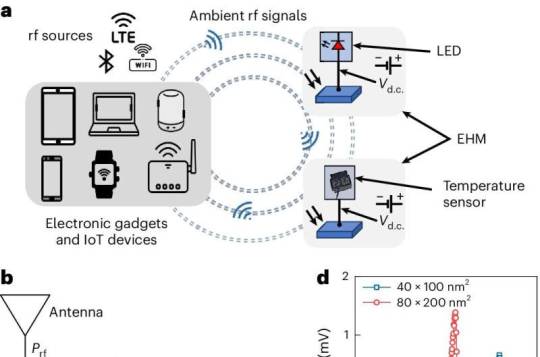
Battery-free technology can power electronic devices using ambient radiofrequency signals
Ubiquitous wireless technologies like Wi-Fi, Bluetooth, and 5G rely on radio frequency (RF) signals to send and receive data. A new prototype of an energy harvesting module—developed by a team led by scientists from the National University of Singapore (NUS)—can now convert ambient or "waste" RF signals into direct current (DC) voltage. This can be used to power small electronic devices without the use of batteries. RF energy harvesting technologies, such as this, are essential as they reduce battery dependency, extend device lifetimes, minimize environmental impact, and enhance the feasibility of wireless sensor networks and IoT devices in remote areas where frequent battery replacement is impractical. However, RF energy harvesting technologies face challenges due to low ambient RF signal power (typically less than -20 dBm), where current rectifier technology either fails to operate or exhibits a low RF-to-DC conversion efficiency. While improving antenna efficiency and impedance matching can enhance performance, this also increases on-chip size, presenting obstacles to integration and miniaturization.
Read more.
43 notes
·
View notes