Don't wanna be here? Send us removal request.
Text
Week 8 | Tutorial
This week we firstly went through everybody’s something awesome, this is was pretty cool, seeing what everyone got up to over the past term.
The case study is worth mentioning though, because it was so weird. We were given a conundrum involving communication channels. So we have a General, a cadet and an alien. The general can give messages to the cadet but cannot receive anything from the alien. The alien can both talk to and hear the cadet as well as talk to and hear the general. And finally the cadet can hear the cadet and see and hear the alien.
So the problem was, how do we guarantee authentication if the only way we can get a message from cadet to general is through the alien.
My group came up with the idea that we should get the general to talk to the cadet and give him a protocol out of ear shot of the alien. The cadet passes the message to the general and if the protocol is passed then we should be able to guarantee that our message is correct.
However it was also brought up that there a whole lot of issues with authentication. What if the cadet is compromised? How do we know he is on our side. What if the alien managed to guess the protocol? I guess the issue is that really, it’s impossible for us to know if it’s 100% correct. The best way is to get information for ourselves and not through a third party. We can only trust ourselves in the end.
0 notes
Text
Week 6 | Lecture
I missed this lecture as I was down with the flu. So I had to read my friend’s notes as well as the lecture notes.
AES - Uses a substitution permutation network. This is a series of linked operations used in block ciphers and is where substitution boxes transform one change in the input into changing half of the entire block.
ECB (Electronic Code Book) - So for this one, each separate block is encrypted and decrypted separately.
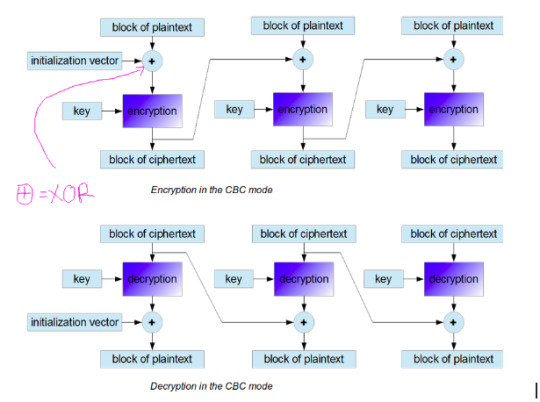
CBC (Cipher Block Chaining) - Each plaintext block is XORed with the plaintext block before. Therefore it is chained.
DIsk Encryption - Disk Encryption is a technology which generates a random key to encrypt data and stores it in a place that’s not in the disk. Thus it creates unreadable code and is why it is so special.
Feistel Ciphers work by splitting the data block into two and applies encryption over multiple rounds to encrypt it.
It was kinda hard to know what Richard was saying since I wasn’t there. Its worth it to go the lectures because the extra research is a lot of work and Richard is interesting at least.
0 notes
Text
Week 3 | Lecture
Risk - Risk is invisible. There is no way to know you took a risk until it goes wrong. Unless it is super obvious. Risk is always bad. Richard gave us the example of a laptop repair store. There is always a chance they would destroy your laptop but you wouldn’t know unless you went there time after time. Allocate resources appropriately across risks.
Low Probability / High Impact - an example is asteroids crashing into Earth. The chance is terribly low but could happen
Risk Matrix - Helpful to figure out where our risks are. 2D graph of likelihood vs impact.
Bits of Security - A good way to measure the security of a system in place. Measured in bytes and is an average of the brute force method to crack a password.
Centralisation - places with single point of failures often have a really high level security at that point. However if it falls then it’s a huge impact.
RSA Keys - have made a huge impact on worldwide security. Uses public and private key encryption/decryption and is extremely secure.
Message M has numerical equivalent ‘m’
Choose p,q to be different primes
Calculate n = pq
Calculate 𝛷(n) = (p-1)(q-1)
Choose an integer ‘e‘ such that 0<<e<<p,q and gcd(e, 𝛷(n)) = 1 (relatively prime)
Choose an integer ‘d such that ed≡1 mod 𝛷(n)
Encoding m: m → m^e mod (n)
Decoding c: c → c^d mod (n)
Receiver makes n and e public (and keeps p, q, d private)
Edit: Most of this is in my Something Awesome
Richard has been a really entertaining lecturer, but I’m not sure a lot of the time as to which bit is just Richard’s ramblings or which is assessable. Honestly I think that I should just record key words he mentions and go home and learn about it myself.
0 notes
Text
Week 2 | Lecture
Defence in depth - solution towards security designed around single points of failure. Is a good solution for such single points of failures. It allows for when one security aspect is breached, it is then able to recover from that by having additional security aspects implemented.
An interesting example Richard used to demonstrate was a castle, where in addition to a moat, a castle would additionally have archers as well as soldiers to defend its walls. Here, additional defences unrelated to each other are examples of defence in depth.
Side Channels are methods of breaching security systems that does not actually not based on weaknesses in the algorithm itself, but rather information able to be gained from the system.
Bell Lapadua is the machine model that enforces access control by the US government and the US military.
Type 1 and Type 2 errors in technical terms are false positives and false negatives respectively. It’s about the decision between which you’d consider worse. For example, would you rather be falsely diagnosed with cancer or would you rather be falsely diagnosed to be cancer free? I think I’d rather be falsely diagnosed with cancer, which means that false negatives seem like a better option to me.
0 notes
Text
Week 8 | Spot the Fake
Something I noticed while travelling in Japan was the complete lack of regulation involving underage people buying alcohol and cigarettes. I realised that most convenience stores in Japan sold alcohol and cigarettes. The legal age however, in Japan is 20 years old.
But the only authentication you need to purchase these items is an item that comes up when you purchase at the counter that asks you whether you are indeed 20 years old or not. And if you tap no then you’re allowed to purchase whatever you want no questions are asked.
So obviously this is more of a trust system than a system really implemented to prevent minors from purchasing prohibited goods. It’s really easy to fake age in Japan because there are not many authentication methods in place. Perhaps it’s just a culture thing where it’s not really important to prevent underage drinking and smoking?
0 notes
Text
Week 7 | Trump Phishing
Dear Mr Trump,
Your subscription to Haircuts for an Orange has expired. To continue your subscription, please click on the following link. Urgent Action is required!
Regards, Playboy Magazine
0 notes
Text
Week 7 | Block Modes
So I basically figured out a few rules.
ECB: Find out how many bytes in the block. And once we find that repeat that byte size phrase twice. Once we do that we can see if it repeats or not and if there are any repeats then we know that it is ECB
CBC: We basically change one character, and if the rest change with it then it is CBC
CTR: The encrypted text will enlarge with the plaintext
0 notes
Text
Week 6 | One Time Pads
One Time Pads are supposed to be unsolvable. It uses a key of randomly generated numbers and the key is exactly the same length as the message. We’ll be using the blog post: https://travisdazell.blogspot.com/2012/11/many-time-pad-attack-crib-drag.html to try and figure it out.

We’ll be using the below instructions for the following encrypted messages.
LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl
WdafvnbcDymxeeulWOtpoofnilwngLhblUfecvqAxs
UijMltDjeumxUnbiKstvdrVhcoDasUlrvDypegublg
LpaAlrhGmjikgjdmLlcsnnYmIsoPcglaGtKeQcemiu
LpaDohqcOzVbglebjPdTnoTzbyRbuwGftflTliPiqp
I figured that the XOR process wasn’t necessary, because I can see that Lpa is repeated several times so if I guess that its The, then it seems pretty likely. So subbing in The for Lpa we can see that the key is 18, 2, 22 for the first 3 letters. and so:
Message 1: The
Message 2: Eve
Message 3: Can
Message 4: The
Message 5: The
After a while of guessing, I eventually figured that Eve can only have so many, and most likely continue with an R. Also I figured that the capitalisation was the start of a new word. So I guessed Every for message 2, applying the key to the rest gave me:
Message 1: These
Message 2: Every
Message 3: Canyo
Message 4: Themo
Message 5: Thepr
Then I could guess message 3 to be can you, so:
Message 1: Thesec
Message 2: Everyo
Message 3: Canyou
Message 4: Themos
Message 5: Thepri
At this point I got pretty tired of it so I just looked for the answers in comment sections. Here is the finished messages:
Message 1: The Secret To Winning Eurovision Is Excellent Hair
Message 2: Everyone Deserves A Hippopotamus When They’re Sad
Message 3: Can You Please Help Oliver Find The Flux Capacitor
Message 4: The Most Important Person In The World Is Me Myself
Message 5: The Price Of Bitcoin Is Too Damn High Given The Data
Hooray for one time pads!
0 notes
Text
Week 5 | Vulnerabilities
Martha’s Recipes:
Vanilla Cake First off, quantity of ingredients is not specified, and the baking temperature is way too low to be legit.
Caramel Slice There seems to be no actual measurement, just numbers. We could assume the measuring unit but we could also misinterpret it.
Cheese Souffle The very first step mentions a prepared soufflé so honestly, I can’t trust it.
Code 1 The vulnerability is in the length variable. Doesn’t consider negative numbers and so can be exposed through an overflow.
Code 2 The buffer is not dereferenced and would hence find the pointer size
Code 3 We’re comparing two different sizes of ints which can cause errors.
0 notes
Text
Week 5 | Dropping the Bomb
Context:
In 1980, in rural Arkansas, during the height of the Cold War, two technicians were performing routine checkups on a nuclear war missile in a US military silo. However, due to a variety of reasons, they brought the wrong tools and ended up losing a tool, piercing the fuel tank and alarming everyone in the vicinity. Eventually, the US Government sent in a repair team, but the missile exploded. Luckily the nuclear warhead did not go off, but the repair team was killed.
Assets:
In the podcast on The Damascus Titan II explosion in 1980, it seems evident that the US Government had one important thing to protect. Namely, their reputation. The air force knew well ahead that items could easily be accidentally dropped in the silo, but to save face, decided to blame it on human error. Furthermore, the military stated that there was no chance that the nuclear warhead could go off due to safety precautions, something that completely went against everything scientists and specialists said.
However once situations became dire, the second thing, human life became the most important to protect. A small team was sent into defuse the situation, meaning that the government valued saving the warhead and protecting the population around the site rather than the immediate repair team.
Recommendations:
My first recommendation would be to make sure that nothing of that sort could happen. As the podcast mentions, tools can be dropped all the time. In all honesty, there should’ve been some form of safety preventions.
Also, I believe that placing the control centre next to the silo is not a good idea. To have the control team have to operate a missile while being in the strike range is not good for calm and rational decisions.

0 notes
Text
Week 4 | Human Morals
Sydney’s lock out laws were implemented after an incident in 2013 involving a drunken fight and ultimately a death as a result. Thomas Kelley was killed by Kieran Loveridge after he hit Thomas in the back of his head, from a drunken night out. From this, the NSW government decided to implement a lock out law preventing alcohol being sold at establishments after a certain time
Main Factors:
Pressure from a certain area of the public after the incident called for deep legislation changes to Sydney’s night life laws. In an attempt to make Sydney safer, the NSW government at that time decided to implement the lock out laws. Some called against it, saying that banning alcohol from establishments after a certain time period did not deal with the ultimate issue of cheap alcohol and a toxic drinking culture.
I believe that instead of hurting the economy, small business owners and Sydney’s nightlife reputation, there were much better solutions to deal with something like this. Such as programs for alcoholism or a shift in the drinking culture in Australia. Either way, there are better solutions.

0 notes
Text
Week 3 | ATM Attack and Defence
Attackers
The most obvious ATM attack is the card skimmer where an attacker can manually install on any ATM, and any unwary suspects.
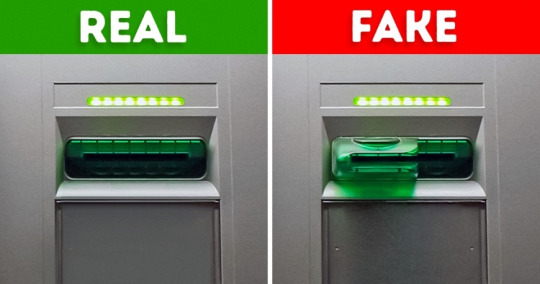
They would pretty much the information on the card by stealing information from the magnetic stripe on the card.
Another few ways I can think of is to install a camera around an ATM machine so that whenever a customer inserts a pin number, it’d be pretty easy to track the pin number. And maybe steal the card later or something.
Alternatively you could always just hammer at an ATM machine until it breaks or like drive a car into it. It after all is still just a plastic case full of money.
Defense
Some good defence strategies would firstly be to educate people about ATM card skimmers because they’re pretty obvious if you know about it. Otherwise, you could always just keep monitoring the ATM to make sure it isn’t compromised. Otherwise just keep guards around it, or make ATMs be able to withhold a lot of force.
0 notes
Text
Week 5 | OWASP Vulnerabilities
Injection Flaws
Injection Flaws are similarish to format strings. The whole basis of injection flaws are that programs that take user input into their database to do anything to it, can equally and maliciously attacked if not dealt with properly.
Just like with format strings, usually as users, when told to input, for example our names into a website, the website treats it as a string and searches for matches. However, what if the user had malicious intent, and instead of just inputting a plain string into the input, it was instead shell commands? What if instead of just searching for a string, it actually ran system calls to the program. Unfortunately, there are many ways to assume control via this method and was thus a big issue.
Essentially attackers can inject malicious software into a user input and cause all sorts of havoc. SQL injections could alter database values, it could install malware run scripts and completely destroy the security of a program.
The simplest way to avoid this vulnerability is to avoid accessing external inputs. Also a good way is to have checks in place to make sure that the data is not malicious.
0 notes
Text
Something Awesome | Reflection
youtube
Sooo, I’ve completed the tasks that I set out to do and in the process, learnt a lot about different ciphers and encryption methods. From Caesar Ciphers to RSA Keys, the process of coding them up in Python really forced me to have an in-depth and solid understanding of all these concepts.
Caesar Ciphers were a good introduction into the whole cipher world, because it’s a perfect beginner cipher. Incredibly easy to understand while still maintaining a little difficulty in the whole coding process. The special thing about coding a Caesar Cipher was understanding how computers interpret characters. Because the easiest way to do this was to convert characters to their ASCII values and perform the shift.
Transposition Ciphers were a lot harder than Caesar was. The concept was easy enough to understand but thinking about within the framework of coding logic was challenging to get my head around. However because of the fact I had to get used to the whole logic of coding something like this, and using columns to create the message, it helped me understood the process of creating a transposition cipher.
Vignere Ciphers, once the understanding is reached and how it really is just a lot of different Caesar Ciphers mapped to a key word, it became pretty much the same process as a Caesar Cipher. Except this time around, since the key was not in the form of a number, a discovered a quick hack to this way finding the index of that letter in the alphabet to shift. I now have a much better understanding of Vignere Ciphers and its operation.
For RSA Keys, I believe it was a good thing to finish on. The whole process and rules for RSA are so complex and intricate that it really proves to be a much more challenging and interesting project to work on. Because I had to implement this in code, I really had to study up on a lot of the mathematical properties in RSA. Modulus being a big part, and factorising another. I found it very interesting to note, as this one was different to the other ones being that, this is still used in modern day encryption methods. So to know how it maintains that was very interesting.
Overall, I completed all 4 ciphers I was planning to code, each with decoding tools. Other than that, for each cipher I created a substantial report detailing the history and uses and implementation of each one with a compiled blog report of the entire coding process.
0 notes
Text
Week 8 Lecture
The China Syndrome! Gotta watch for finals! Is this HSC english.
Human Weaknesses
Honesty - commander in chief Human’s lie and do not tell the truth. We talking about Trump, who maybe doesn’t even know himself that he’s lying.
Misdirection and intended focus / Chekhov 1 Humans tend to focus on a few things based on preconceived heuristics. We don’t have time to think about every single thing and are therefore subject to misdirection.
People are bad at picking the right thing to focus on
Logically Important vs psychologically salient What seems logical may not be our first course of action as humans tend to stray towards more flashy things or something more exciting.
Similarity matching With similarity matching, humans don’t have to think very much
Frequency Gambling Availability Heuristic
Confirmation bias, cognitive strain, group think syndrome, developmental phase (goad and breaked 2)
Systems
Cassandra and Apollo and hindsight and Chekhov and simplification, belief event has only one significant cause. Plan for fewer contingencies that occur. Ability to control outcomes, the illusion of control.
Hindsight bias - knowledge of outcome of previous event invreases. Perceived likelihood of that outcome, complexity coherence coupling usability 5. Defense in depth. Operator deskilling due to automatic safety devices. Common mode failures.
Latent vs active failures.
0 notes
Text
Week 7 Activity | Letter
Dear Mr Trump,
I regret to inform you of our decision to not go ahead with your request to deny Huawei access to Australian Telecommunications. I see Huawei’s 5G implementation a vital next step in the history of human kind and if it were any other country besides China, there would be absolutely no questions as to whether this was a good or bad thing.
i view it like this, China, in all its glory would have absolutely no problem if it wanted to spy on Australia right now anyway. I mean yes, giving it access to our telecommunications would allow easier access, but if China wanted something from us, it’d have it anyway. Their resources outweigh us by a whole lot.
And with that, I see the benefits from this to be overwhelming. It allows Australia to skip past its terrible internet situation and go straight to a wireless 5G system. Australians would all forget about the failures of NBN! And that to me is a win. Also the economic savings and production would be insane. I see no reason to not go ahead with this.
Regards,
Kevin07
0 notes
Text
Week 7 Tutorial
Week 7, as Hayden did tell us was in fact pretty interesting. Although I must say, I could’ve gone without the debate due to crippling social anxiety. Anyway, this week we had to go through a big big question about our political viewpoints and expectation of government. Mostly in the form of government data collection. Is more better? Is right now too much? Should we have less?
For me, I’m indifferent as to whether the government has data on me or not, as long as its a government I support and a system that I endorse. But that therein lies all the problems with this issue. World governments are not stable. If history has taught us anything is that nothing is stable. You could go from having a free market capitalist democracy in one decade, to an authoritarian totalitarian genocidal regime in the next. (that’s right, I’m looking at you Weimar Germany).
So what my point was, is that. Sure, right now big data could help us, by capturing criminals, lowering crime rates and maybe being able to better run a society due to having more information. But the problem is that, once information is taken and stored, it’s there forever. From one government to the next, its amazingly hard to get rid of. So what if similar situations arise?
My side was the one supporting less surveillance and the like. Which I agree to an extent. But actually, i’m more indifferent. I feel like the current system we have now is enough. It works and it strikes the right balance to me.
We could look at China’s social credit score and the Uyghur’s situation right now as a ‘warning’ as to the downfalls of an all consuming big brother like situation. Sure right now, criminals are labelled as ‘murders’ or ‘thieves’. But the issue that we brought up was that, different groups have different versions of right and wrong. If corruption occurs, governments shift. If Pauline Hanson became Prime Minister, a big brother situation could lead to an entire group of people to maybe go down the same right as China’s ethnic minorities. And that to me, is not okay.
0 notes