Don't wanna be here? Send us removal request.
Text
Final Report and Video Presentation
Project Plan
Final Report
Video Presentation
0 notes
Text
Progress Update - 3
This week’s progress is as follows:
Started to analyse the file backdoor.exe file supplied by my tutor Adam which was more interesting than the stager.exe file I previously started analysing.
Performed the following tasks:
CFF Explorer
Check on Virus Total
Google search
Detonation
Wireshark trace
Create video for each of the tasks listed above
Started creating the presentation due for Tuesday
0 notes
Text
Project Plan - Updated
Update of scope due to submission in Week 8.
Analysis of Malware
The idea for this project is to perform analysis on some malware and present the results.
Week 3
· Investigate methods for analysing malware (e.g. static and dynamic analysis)
· Setup environment
Week 4
· Document methodology (~1 page)
· Acquire malware (2 different malware)
Week 5
· Install malware 1 and perform dynamic analysis
· Document analysis for malware 1 (~1 page)
Week 6
· Reverse engineer binary of malware 1
· Static analysis of code for malware 1
Week 7
· Analysis of code for malware 1 continued
· Document static analysis of malware 1 (~1-2 page)
Week 8
· Finalise paper and presentation (paper will consist of analysis and commentary of the process and results, the presentation will summarise the whole experience and may include some video)
Marking Criteria:
HD - complete all of the tasks mentioned in the plan and include video in the presentation
D - complete all of the tasks mentioned in the plan but no video in the presentation
C - complete static analysis of malware no video in the presentation
P - complete dynamic analysis of malware no video in the presentation
0 notes
Text
Progress Update - 2
This week I have made some good progress with the project.
1. Finalised setup of the victim and sniffer environments
2. Installed the analysis tools
3. Taken the tutorial on Malware Unicorn
4. Received some malware from my great Tutor Adam
5. Started analysing the stager malware
The following are some of the screenshots from my initial triaging
I initially opened the file using HxD editor to view the header information. MZ indicates that the file is a PE binary. This file runs in the Windows OS.

Opening the file in CFF Explorer shows more information on the file including the checksum.

The MD5 hash can be entered into a website virustotal.com to see if there is any other information about it
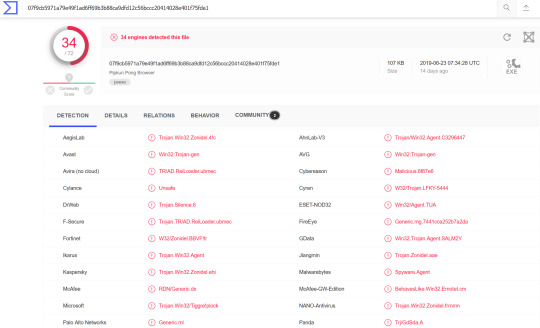
Performing a quick dynamic analysis using Wireshark, procmon and procexp to trace and log the activity

Next steps:
1. Perform some more detailed analysis and log the results
2. Document the results and create a commentary on what looks to be happening
0 notes
Text
SAP - Progress
This week i made a little headway in getting the environment setup. I initially had issues with the Linux VM that was downloaded from Malware Unicorn as I could not get the networking to work properly. I then downloaded another version of Ubuntu 18.04 and was successful in connecting to the internal “Lab” network. This means that I now have to download and install all of the tools required to perform the Reverse Engineering!! I have installed Ida, but the others are difficult to install in Linux so i’m still working on it.
I also started to go through the tutorials from the Malware Unicorn website, they provide a good basic approach that I will try to follow when I do my real analysis.
https://malwareunicorn.org/#/workshops
I am also reading the book Practical Malware Analysis by Michael Sikorski and Andrew Honig (it is very detailed and long)
https://repo.zenk-security.com/Virus-Infections-Detections-Preventions/Practical_Malware_Analysis.pdf
Next Steps
Finalise the environment setup
Acquire some malware
0 notes
Text
Malware Analysis - Draft 1
Rationale We are increasingly reliant on technology which not only includes personal computers and networked servers but network infrastructure (i.e. routers and switches), smart phones, tablets and the increasing use of IoT (Internet of Things) devices (smart devices). People in the form of organised crime groups, political hackers, terrorists, individual hackers and potentially government agencies may want to gain control of your device for their own benefit and without your permission. The reasons can be anything from stealing money, identity fraud, trying to change the outcome of elections, gaining control of infrastructure, tracking your movements, steal data, disrupt governments, steal business information. We need to analyse malware to understand how it works in order to fix security issues in the legitimate software we use. ….
Malware What is malware? Malware is any program or file that intentionally designed to harm, infiltrate, or damage a computer, server or computer network. This software can disable or disrupt the operation of a system, allowing hackers to gain access to confidential and sensitive information and to spy on the computer and the owner of the computer itself. Malware is specifically made to be hidden so that they can remain inside a system for a certain period of time without the knowledge of the system owner. Usually, they disguise themselves into a clean program; even some of the latest malware has the ability to avoid detection of antivirus (1. Wikipedia, 2019).
Types of malware Virus A type of malicious software that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be "infected" with a computer virus. Viruses usually try to modify/corrupt data or files on the host, waste system resources. (2. Wikipedia, 2019) Worm A worm is a program that replicates itself in the computer system and transfers itself through the network. The work itself may not have a payload. If it does have a payload it could be in the form of ransomware that can encrypt files or gain access to password.
Spyware Adware Trojan Trojans can allow the attacker to access the personal, bank account and password details. They can also carry a payload which can delete files and cause a ransomware attack or even take control of the whole device. Trojans do not generally try to replicate themselves like worms and viruses. Rootkit Ransomware Keylogger Backdoor
Malware Analysis Is the process of dissecting the software to understand how it works so you can identify it, see how it works and work out ways of defeating it. This project will be using basic static analysis and basic dynamic analysis. Basic Static Analysis This refers to the process of analysing the structure and if possible the code of the software. This allows us to determine what functions it can perform. This involves reverse engineering the binary using tools such as IDA and Binary Ninja.
Basic Dynamic Analysis This refers to analysing the malware after it has been executed. It allows the observation of actions performed and functionality of the software. Dynamic analysis is performed after static analysis.
Risks There are risk in trying to analyse malware as it may escape the lab environment. Some malware can identify that they are in a virtual environment and can act differently so it can be more difficult to analyse.
Malware to Analyse
...
Tools 1. Virtual Box VM 2. Windows 10 O/S 3. IDA Reverse Engineering software 4. Wireshark 5. Process Explorer
Method (for Dynamic Analysis) Setup environment 1. Set up a clean virtual machine with no malware running on it 2. Transfer malware to the virtual machine 3. Conduct analysis 4. Reinstall clean snapshot of virtual environment
References
1. https://en.wikipedia.org/wiki/Malware, accessed on 23/06/2019.
2. https://en.wikipedia.org/wiki/Computer_virus, access on 23/06/2019.
3. https://en.wikipedia.org/wiki/Computer_worm, accessed on 23/06/2019.
4. https://en.wikipedia.org/wiki/Trojan_horse_(computing), access on 23/06/2019.
0 notes
Text
Something Awesome Project Plan
Reverse Engineer Malware
The idea for this project is to perform analysis on some malware and present the results.
Week 3
· Investigate methods for analysing malware (e.g. Static and dynamic analysis)
· Setup environment
Week 4
· Document methodology (~1 page)
· Acquire malware (2 different malware)
Week 5
· Install malware 1 and perform dynamic analysis
· Document analysis for malware 1 (~1 page)
Week 6
· Reverse engineer binary of malware 1
· Static analysis of code for malware 1
Week 7
· Analysis of code for malware 1 continued
· Document static analysis of malware 1 (~1-2 page)
Week 8
· Reverse engineer binary of malware 2
· Static analysis of code for malware 2
Week 9
· Analysis of code for malware 2 continued
· Document static analysis of malware 2 (~1-2 pages)
Week 10
· Finalise paper and presentation (paper will consist of analysis and commentary of the process and results, the presentation will summarise the whole experience and may include some video)
Marking Criteria:
HD - complete all of the tasks mentioned in the plan for 2 pieces of malware and include video in the presentation
D - complete all of the tasks mentioned in the plan for 1 piece of malware and include video in the presentation
C - complete all of the tasks mentioned in the plan for 1 piece of malware but no video in the presentation
P - complete all of the tasks mentioned in the plan for 1 piece of malware but no presentation
0 notes