Don't wanna be here? Send us removal request.
Text
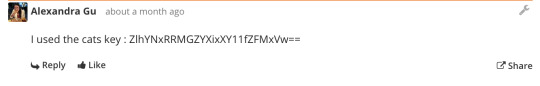
I got phished
Kind of forgot this happened probably about a month or so ago. It’s particularly amusing and kind of embarrassing since my whole project has a strong focus on not clicking unknown links. But this clearly shows that even for people who are aware of the risks of clicking unknown links, it’s almost just second nature to click something that is given to you.
This also shows that companies are very aware of the risks of phishing which is why they regularly run these tests as well as run education modules on them because if one computer is infected, the whole system can go down.
0 notes
Text
Phishing Trump
Hi Donald,
We noticed some unusual activity on one of your Google Accounts [email protected]
Details:
Monday, 22 July, 4:32:02 EST
IP Address: 324.32.321.402
Location: Chongching, China
If this wasn’t you, please click here to confirm your email and change your password immediately.
Best, The Gmail Team
Or alternatively
Hi Donald,
We’ve recently come across quite an interesting video of you quote “Grab em by the p*ssy”. We wouldn’t want this to come to light and harm your chances of running for president would we?
You can contact us here before noon tomorrow or maybe we might just accidentally forget a certain usb outside The New York Times...
Best, Anonymous
0 notes
Text
Being a great friend
I was talking with a friend about our projects and he had asked me to look over it to see if I noticed anything missing.

0 notes
Text
Newspaper Shredding
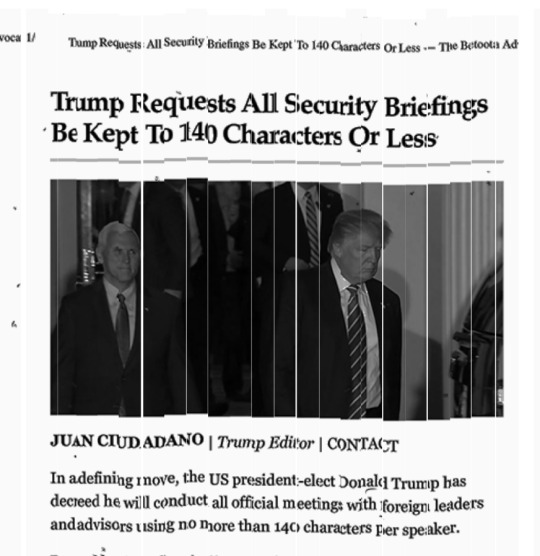
It was honestly so easy to put this together it shows how shredding may not be the most effective way of getting rid of something. This was essentially just a puzzle and the fact that there were so many lines of text mean it was very easy to piece it all back together.
Here are some other methods of getting rid of sensitive physical information:
burning, but it may be unreliable as sometimes things only get partially burnt, basically just a little charred..
shredding, but then mixing it in with water so it kind of becomes paper mache
Chemical burning such as sulfuric acid
But we all know most important things are digital these days so here are some other methods:
wipe your drive
reinstall your OS which should permanently delete everything before it reinstalls
physically destroy the hard drive
Or, just keep it all in your head so nothing even exists to be destroyed (prevention)
0 notes
Text
Giggle
Giggle is supposed to be a driverless electronic car and we were asked to provide things to consider from both the company and the government’s point of view.
From the corporation’s point of view, their assets are:
Reputation
Cars
Software - Knowledge
User Data
I really think that a company’s most important asset is their reputation and their knowledge because that ‘s what differentiates them from any other company. Obviously, while cars are an asset, it is just a physical asset which can be replaced but data, knowledge and reputation cannot.
Giggle will need to have a standards body with thorough testing before putting the final product into the market to ensure safety. It’s also important for them to have a strong PR team. Additionally, Giggle would opt for closed source software to keeps the data safe and prevent people from exploiting the code.
On the other hand in regards to the government, their assets is primarily their reputation among the citizens. The safety of the citizen is crucial for the government. This is why they would want an open-sourced software so it can be safely audited and have more trust. Additionally they would set up more regulations in terms of driverless cars such as ensuring the company puts significant resources towards training.
Clearly, it is obvious that the company and the government have very different focuses. While the company only has it’s own interest in mind, primarily driven by their profit, the government has a strong focus on the citizens and their safety as well as the impact of driverless cars on the economy.
0 notes
Text
Doors
There are several key issue with the current procedures regarding the cockpit doors as seen in the videos and articles. Since this is essentially a Type I and Type II error problem, these are some key areas that needs to be addressed:
Authenticating the pilot
Having at least one other pilot in the cockpit
Accessing the cockpit when there is an issue
Preventing the pilot from being locked in the cockpit
Our recommendations were primarily focused on having a separation of power so there won’t be a situation where one pilot makes a bad decision and screws everyone over. Additionally, it was important to think about authentication to make sure whoever is in the cockpit is actually the pilot.
Biometric authentication
Ground control to have over ride abilities
Always have at least 2 pilots in the cockpit
Require at least 2 pilots to make an important decision
Essentially it is important to install an authentication system that will be able to override commands in times of crisis but ensure that it is coming from the right people. By requiring at least two pilots to make critical decisions, it decentralises the power. Through incorporating all of these aspects, it may not fully prevent any issues from happening but it adds in extra layers of security, authentication and a crisis plan.
0 notes
Text
Houdini
This case study was about sending a secret message from one person to someone else in a way which would be easy to authenticate. Since it must rely on some form of secret, it will always have a level of risk to being exploited but there are ways to reduce this chance.
Per CIA, confidentiality, integrity, authentication, these are the key areas to be considered when sending a secret message. What we came up with was to use an encryption algorithms to send the message which will rely on asymmetry of information. This means that while everyone can access the public key which encrypts the message, only one person is able to decrypt it with their private key. This will help maintain the CIA of a message. Additionally, you could also have secrets such as a favourite food etc but this is basically security by obscurity which is all good until someone find out and it all goes to shit. So generally it would be much better to use encryption or you could even use both to make it extra secure.
0 notes
Text
Project Update #4
I’m so frustrated because this is the second time I’ve had to write this because my computer crashed just as I was about done. Tumblr why do you not have an autosave function pls.
Anyways, this is probably my final update since the all the tests and presentations have been done and it was quite a bumpy ride, but we all love rollercoasters right?
Through the project I’ve come to several conclusions about how people think about unknown links from random people and the short answer is, they don’t, they just click what’s in front of them.
1. Most people are aware of the risks of clicking unknown links but it’s human nature to be curious which is why they do it anyways. Some people may not have any idea of these risks which we will touch on later, but in general, most people do but just the fact that there is a link there, people just want to find out what it is.
For example, this guy fully knew the risks - including the risks of malware so he’s pretty on top of it. But he clicked the link anyways just because he was curious basically. Kind of blows my mind.
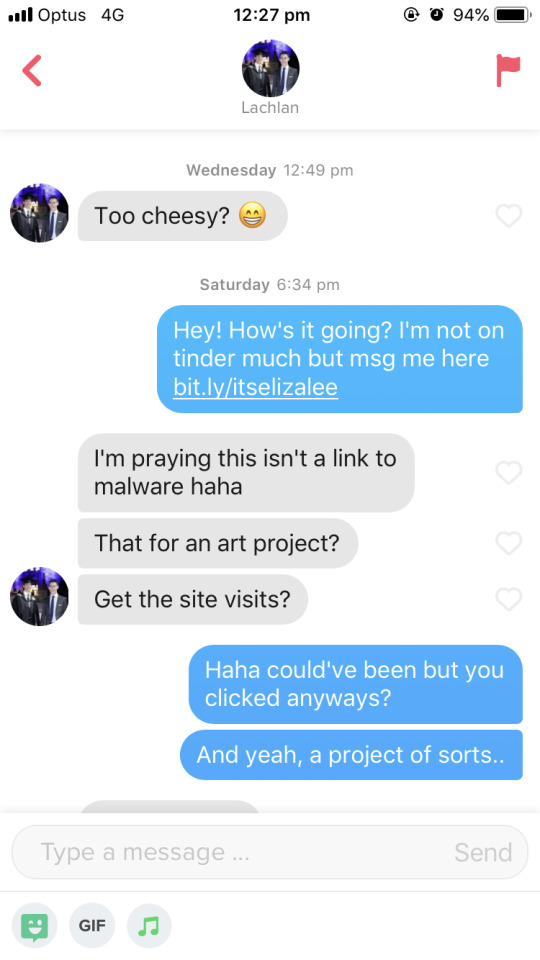
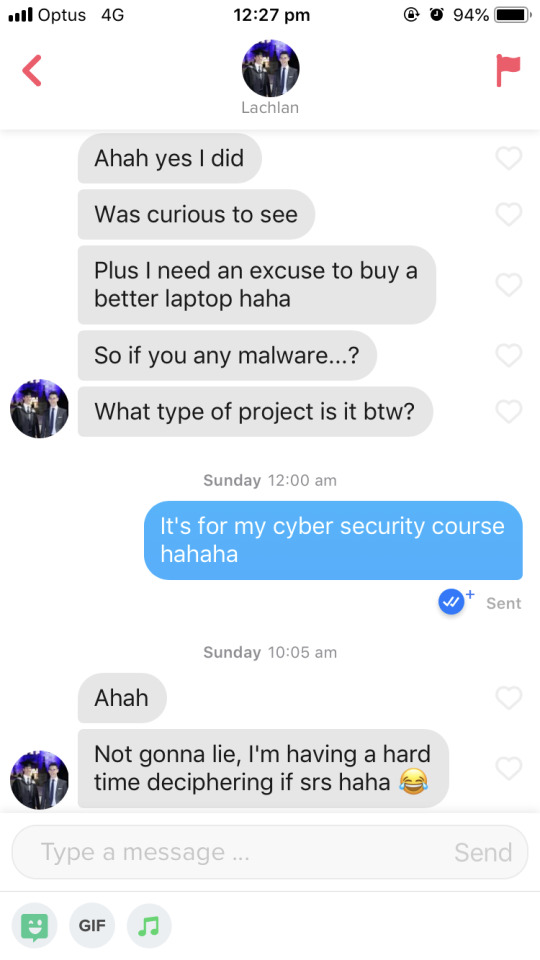
2. Sometimes, its a little harder to get people to click the link, but really it’s not hard enough. They would suspect that I was a bot but the second I replied, with anything, didn’t even have to be convincing, they would click the link...and some would even apologise...
For example, I pretty much just agreed with the first guy and that was enough for him to click the link. Or the second guy, I didn’t really say anything, but suddenly all his fears flew away and not only did he click the link, he apologised. Or even better, I just left it but he decided it was safe to click anyways...huh?
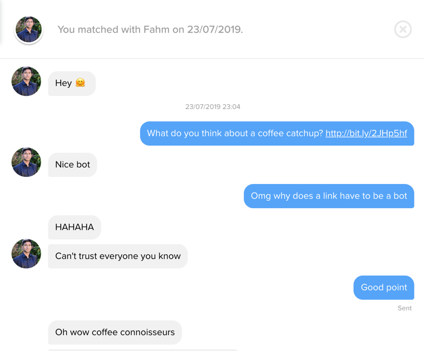


3. The third and final realisation is that people can honestly be so dumb. Since I linked them to a blog with no content, I got an overwhelming about of messages like the ones below. Not only did they click the link, they didn’t even realise that it could be an issue.


Also something I wanted to point out was the browsers that most people were using. Since most of them allow Javascript to run and mostly likely, people haven’t disabled it, I would have actually been able to run some script and steal their passwords. So in the span of a couple of weeks, but in reality didn’t take all that long, I would’ve been able to get probably over 200 passwords. And this is me doing it manually. Imagine the scale if I actually used a bot to send out these messages?

Overall, I learnt a lot of things from this little project, primarily - people are dumb and very easy to exploit so you really should trust with caution and try not to let your curiosity get the better of you because that’s probably how you’re going to lose all your passwords etc. and it’s just not worth clicking a random link that probably doesn’t have anything on it.
It was also really cool learning how to use Google Analytics and editing some code on blogger, wow I know. But for real, it’s scary how much data I could just get of Google Analytics and this isn’t even the paid version or with any extension. Also, I am never using Tinder again. The people on there are so shady and I don’t think I can ever look at another pickup line again.
Do I get bonus marks for actually presenting in front of the class and catfishing them 😂
1 note
·
View note
Text
Project Update #3
When I was doing the last update, I had not been blocked by Tinder yet. But now, about 5 blocks later, I can semi conclude that Tinder has a relatively decent bot detection system - only because I’m also not sure if it’s automatic detection or if my matches are getting pissed so they reported me.
So far I’ve honestly just been shocked by how many people click the link. There doesn’t seem to be too much correlation so far with how the catfish looks or is presented or race, etc. Only thing that really may affect is how quickly people seem to realise they had been catfished. But it doesn’t actually stop them from clicking the link.
Also, it just blows my mind sometimes how the same people click the link just over and over again. Exhibit A below.
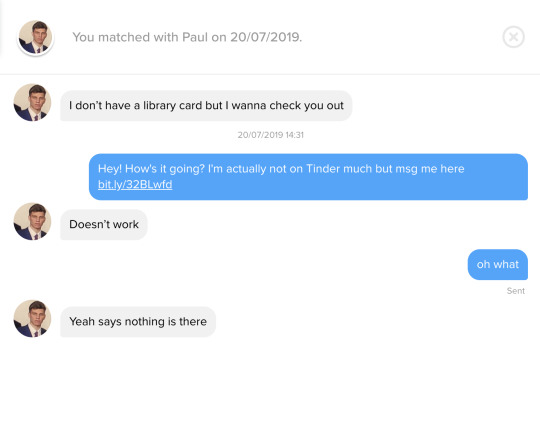
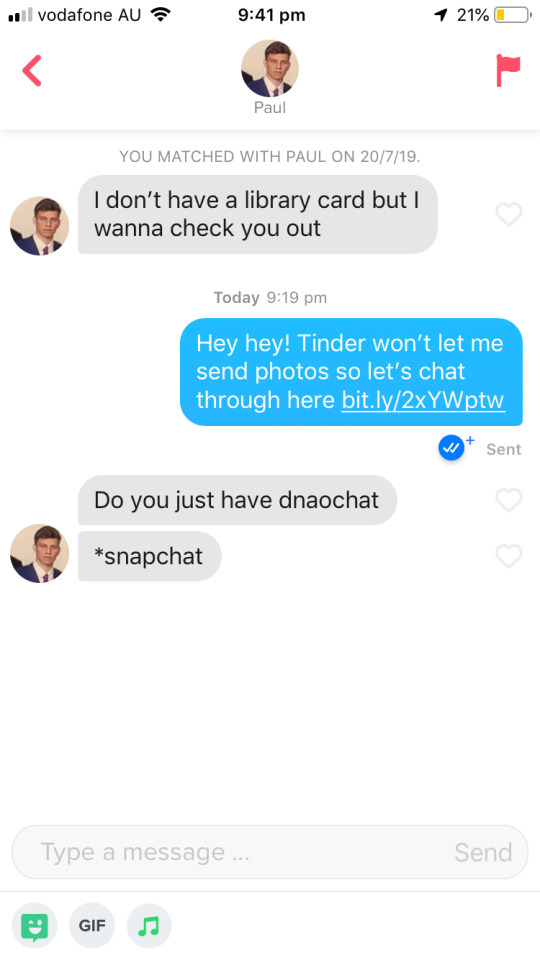
The messages I sent are basically identical, and sent only a few hours apart. It honestly baffles me. This wasn’t the only one but I can’t be bothered finding them all because it happened FAR TOO OFTEN. But here’s just one more example.
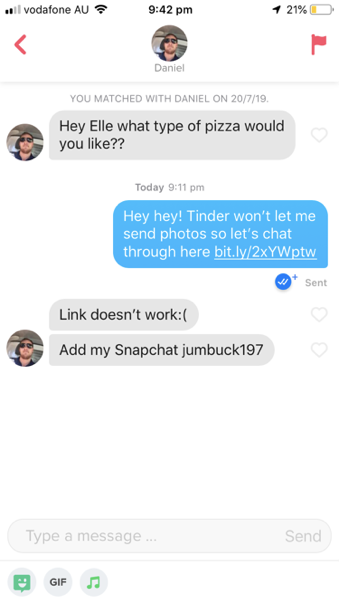

How does he not realise??? I wasn’t too creatives with the names and Elle and Ellie is basically the same thing.
Clearly people just click on what is given to them without much thought.
0 notes
Text
Project Update #2
Just wanted to emphasise that I did do at least 7 tests, and an additional one with the class lol
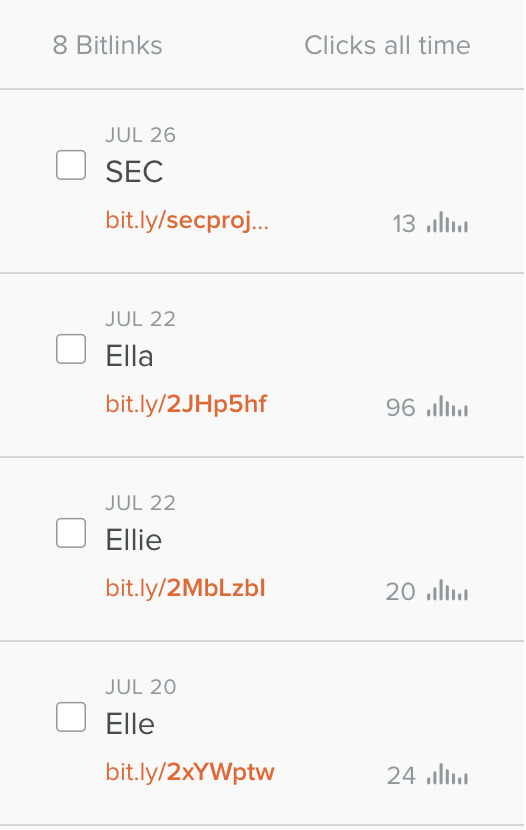

0 notes
Text
Responsible Data Handling
A couple of week ago I made a tweet with this attachment:

This a a good example of responsible data handling because the name of the company is not just blocked out. I cut out the part with the name, screenshot it, and used that version just incase there was some way to recover the original version of an image. So this way, the picture I uploaded was the new “original” version which can’t be exploited.
0 notes
Text
Time Management II
So, since I’m totally running out of time to do the Something Awesome project because the presentation is in a week and I’ve still only got 2 of my planned 8 different tests.
I’ve had to consolidate which ones I am going to run. So now instead of doing both males and females, I’m just going to stick to females. Basically I’m planning to do a total of 6 different tests with 3 different races. For each of the races I will do one where the images are really nice and presentable, the faces are clear to see, etc. Then for the other 3, I will use images which don’t look as high quality, faces are more covered, etc.
I think this will simplify things a bit more and hopefully make the goal seem very clear. Since I’m still going to have to do 4 additional ones, I’m going aim to run as many tests simultaneously as possible using different browsers. Aiming to get that done by Tuesday so then I can start working on the presentation and gathering data to find the best way to present it.
1 note
·
View note
Text
Lec #7
Key Takeaways:
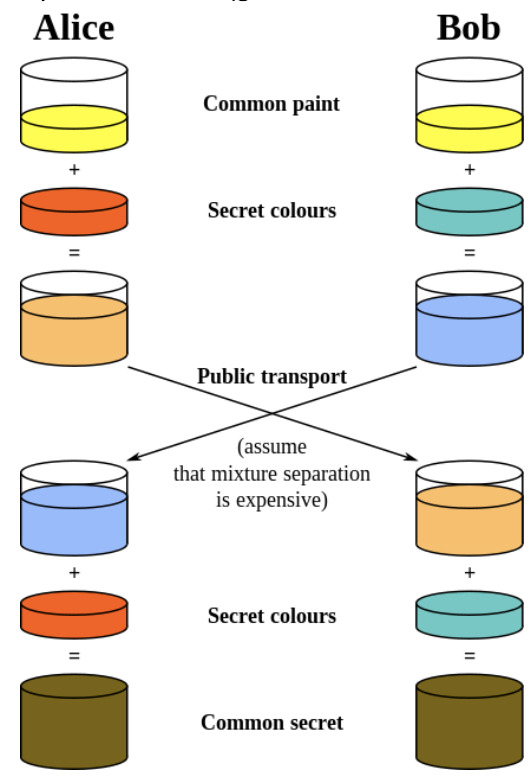
Diffie Hellman Key Exchange
maintain a shared secret over distance
does not give authentication, only confidentiality
Agree on a public base number
Both A and B choose a secret number
A sends base^a to B and B sends base^b to A
A can raise base^b^a, B can raise base^a^b
Difficult to reverse with large numbers
Memory corruption attacks: changing memory so program will behave differently to what it is supposed to
Buffer overflow: attack on the stack which can overwrite adjacent memory locations
Stack is used for function calls
Heap is used for dynamically allocated memory
%x attack: arbitrary read of info from below our memory address
e.g. printf(”%x\n”); will read next item in the stack
%n attack: arbitrary write of info onto below our memory address
e.g. printf(”12345%n\n”); will puts 4 in next on the stack
Shell code: code used to grant access to shell from remote device
generally to gain privileges and often machine code
NOP sled: creating list of No Ops (0x90) increments to the next operation so you can fill the memory before your code to give a range of memory addresses which will basically funnel into the desired address
Critical to protect the correct asset
General standards and protocols tend to miss more than they catch
Regularly ask the people involved in what you are protecting aka multiple pairs of eyes
Have a plan to tease info out
Constantly revise current list of assets
Examples
Cold war: humanity vs country
Coke: secret recipe vs brand
Tangible Assets: Can be touched and easily valued
e.g. a car
Intangible Assets: Cannot be touched, or is material and is not easily valued
e.g. reputation
Public Key Infrastructure (PKI)
Has a single point of failure
Can provide false sense of security
SSL/TLS
X509 certificates which inks public key with domain
0 notes
Text
Lec #6
Key Takeaways:
Buffer overflow
Context switching between processes on the stack
Disrupt any hardware or software processes added on the stack
Stack is ordered in reverse from high to low numbers
Buffer overflow attack: tells the program buffer what it actually is so then it overwrites out of bounds onto the next process on the stack
Can be done to a process that is asleep by changing the pointer to start executing in address of stack you control
Block modes: enables blocked ciphers to work with large data streams and not risk security --> how to transpose a function of a fixed sized thing to a variable sized
Authentication
Needs to consider who this is authenticating for e.g. human, computer or perhaps the computer helps the person make the decision or just does it itself
Identification: about presenting an identity to a system
e.g. usernames
Authentication: about validating an identity already provided to a system
e.g. RSA keys and passwords
Three factors of Authentication
Know: something secret e.g. a password
Have: something you have e.g. MFA or 2FA
Are: something physically unique to you e.g. fingerprint
Almost all three can be duplicated, faked, etc so there is never absolute certainty
0 notes
Text
Cryptocurrency
In 2018 hackers were able to steal over $1 billion in cryptocurrency from various exchanges, notably Coincheck which accounts for more than half of that loss. A study by Homeland Security also discovered that 33% of bitcoin trading platforms have been hacked.
Crypto isn’t a network based on trust. The decentralised public ledger - blockchain, is maintained by data miners who add a block by solving a difficult computational problem that has to be brute forced and uses a significant amount of computing power and in return, these miners will be rewarded with a share of the profit.
However, hackers have clearly found various ways to curve these challenges.
1. Simple phishing
Through phishing and and injecting scripts such as JavaScript, hackers can secretly execute transactions as soon as a user logs onto their crypto account.
2. SIM Swapping
This is a newer and more sophisticated method where hackers will transfer the victim’s number to the hacker’s SIM which will enable them to change passwords and access the crypto account. In this situation, once anything has been stolen, it is impossible to trace due to the anonymous nature of crypto transaction.
These examples show that the hacker’s target are clearly the individuals (humans are the weak link blah blah) and they are doing this from tracking the habits of the users but these are all relatively easy to prevent from some simple implementations.
Keystroke encryption
Anti-screen scraping
Real time transaction verification
Hackers will always be developing newer and faster methods to exploit the system and there is not way to absolutely eliminate these risks but through implementing a variety of simple security measures, it will make hacker’s life a lot more difficult (work ratio) which can at least reduce the extent or frequency of these hacks.
0 notes