Text
Community and Professionalism
This post will be for my community/professionalism component of my Job Application. Any feedback from my classmates is appreciated.
3 notes
·
View notes
Text
Spot the Fake
An example of something that has been faked
Deepfake is a technique to make photo realistic renditions of humans in film or photos. It combines and superimposes existing images onto another image or video using machine learning. Deepfakes also extend beyond images and can also accurately fake video and recorded speech.
A common use for deepfakes have been to create fake celebrity pornographic videos or revenge porn. They can also be used to create fake news and malicious hoaxes. Particularly in politics, there is a fear that they could fake politicians taking bribes, saying racial slurs or engaging in adultery.
It was first developed by a reddit user in 2017 but has slowly developed to become increasingly difficult to distinguish real from fake.
How it can be prevented
Producers of Deepfake material can be prosecuted for harassment in the UK but it is not a specific crime. In the US it is similar but charges vary more from identity theft, cyber stalking to revenge porn.
I believe one way of prevention is to increase the penalty to producers of Deepfakes. This will deter the creation of Deepfakes because the rewards reaped from the creation of a Deepfake may not outweigh the penalty the producer will receive if they are caught.
Deepfakes rely on the AI learning from the large amount of images available publicly online. A good way to prevent Deepfakes of yourself is to not post images of yourself online. For celebrities however it is a different story. A quick search showed that technology was being developed that would encrypt images such that there would be no visual impact on the image itself but can hide the person's from facial recognition programs
2 notes
·
View notes
Text
Week 8 Tutorial
For week 8′s tutorial we spent the whole tute sharing and learning about eachother’s Something Awesome projects. Everyone’s projects were very interesting and because Jazz split us up into stations, I was able to talk with some of the people I haven’t really talked with in my tute. Overall an enjoyable experience
1 note
·
View note
Text
Project Update: WPA
Can finally see the end! Today’s post is about cracking WPA and WPA2, combining part 3 and 4 of my project proposal. Now that I have all the tools ready, it was simply a matter of changing the router to WPA2 and performing a different kind of attack.
The attack performed is the same attack that is done on both WPA and WPA2 so I will just refer to what I set the router to, which is WPA2. The attack is done on the authentication process. WPA2 supports many types of authentication besides pre-shared keys, however, this attack only works on WPA2 with pre-shared keys authentication. It is referred to as WPA2-PSK or WPA2-personal. A pairwise master key (PMK) is attained from the password which is a 256-bit shared key that is known by the client and the access point. The authentication process of WPA is the four-way handshake which makes the client and access point prove to each other that they both know the PMK. It then uses temporal keys (TKIP) or AES to secure data as I explained in my WPA posts.
Only brute force methods can be used to attack WPA2. The key is not static unlike WEP so we can’t just collect IV’s like we did with WEP. The information leak given to us is the handshake between the client and the access point. When the handshake is captured, we brute force the pre-shared key. This also limits us to dictionary words or short length words unless we want to wait.

Here are the wireless settings on the router. As you can see it is set to WPA2. I chose the passphrase “password” for my first attempt.
The next step was to use a tool to capture the handshake between a client and the access point. There are a couple ways to do this. The first way is to simply wait for someone to authenticate with the access point. The downside to this is you must wait. If you get lucky, sure it’s quick. But I don’t think it’s often that new person authenticates with your home router.
The second way is to de-authenticate someone already connected to the network by sending a de-authentication packet. Then you hope that the client reauthenticates with the access point. The downside to this is that it’s noisy and bordering legal trouble.
So, I did the first method since it was a personal router. I went on to another computer and authenticated with the router.

Once I did that, the WPA handshake was captured.
And then it was just a matter of brute forcing the pre-shared key. This tool uses a dictionary attack, so I found some password lists online.
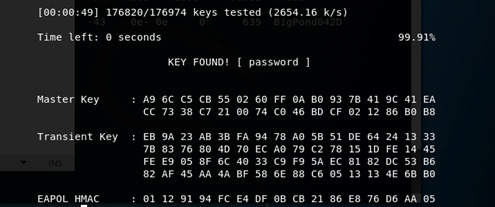
And then it was cracked. I then played around with some other basic passphrases but with this tool, if it’s not in one of the lists then it doesn’t get cracked. For example, I changed the passphrase to “correcthorse”.
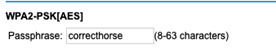
And it wasn’t in any of the lists, so it wasn’t found.

I was limited with what I could do on my crappy Macbook Air but there are other tools that brute force on the GPU and CPU. This takes advantage of having hundreds to thousands of cores so they can perform using heavy parallelism.
This just about concludes my Wi-Fi hacking escapades. Not gonna lie, do feel like a bit of a script kiddie but for a first attempt I reckon it's ok.
1 note
·
View note
Text
Project Update: Progress
Been a long week for me trying to juggle all my assignments but good news, I finally managed to get some progress. So earlier this week I blogged about how my network adapter wouldn’t switch to monitor mode no matter what I tried. I was considering just giving up on the practical component, but I thought I would do a last attempt with another adapter that I was able to order online and pick up before the weekend.

After following some tutorials that I found online, I finally got it into monitor mode

I could now finally start the WEP cracking component of the project. The attack that we’ll be doing is a packet injection attack that I detailed in one of my earlier blog posts about WEP attacks. I set up the access point once again and I set the security to WEP.
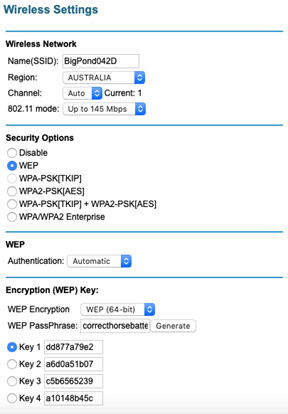
Here are the settings on the router. I set the authentication method to automatic which I assume they mean open authentication. This means we don’t provide credentials to the access point when we authenticate. I set the WEP encryption to 64 bit so it produces a 64 bit key with 10 hexadecimal digits as shown in the keys. I could also set it to 128 bit, which is ‘safer’ but the cracking process is the same. I entered my passphrase “correcthorsebatterystaple” and it generated me 4 keys. I then just selected the first key.
Using one of these other keys allows me to connect but doesn’t give me internet. Apparently, there’s an option to use multiple keys but it doesn’t disperse the encryption load, so it isn’t any safer.
Part one consists of me searching for access points in the area.

I blacked out the other access points for privacy but here you can see my router that is set up with WEP.
The second step was to do an authentication with the router. In order for the access point to accept a packet, it must be associated with the client through MAC address. Otherwise it will send back a deauthentication packet and will ignore all the packets that we are trying to inject. This was easily done with one of the tools.
The next step was to open another tool to capture the IV’s that would be generated from the packet injection.

The underlined number is the number of data packets that were captured during the attack. The number next to it is the number of data packets per second received. This would be around 400 during the attack.
The next step is to do the ARP packet injection attack. Basically, the access point will normally rebroadcast ARP packets, meaning if enough are rebroadcast the same IV’s will be used.
The process begins by first capturing one ARP packet. The tool with then inject this packet over and over again to generate traffic because the access point will rebroadcast it and eventually the same IV’s will be used again. These IV’s are captured by the tool above, which are the data packets.

As you can see here, a lot of ARP requests are being sent and captured.
The final step is to get the WEP key from the IV’s captured. This is done by another tool. The methods to crack the key include methods such as FMS and PTW which I described in my WEP attack post. I decided to use PTW.

And done, the key was cracked, successfully matching with the key that we generated in the first step.
2 notes
·
View notes
Text
Week 7 Tutorial Personal Notes
• digital forensics - seems good • Vigenere cipher - gazgad • lightning talks • return address is 4 bits on 32 bit system • put payload into buffer itself shellcode • sell exploits • kali linux loser • penetration testers just run software suck • can do better than penetration testing
What does the government know? • Address ○ Instantly rejected because of his address job application ○ How do you catch criminals if you don't know where they live • Name • Family • Medical ○ Early detection of cancer? • Social services ○ They can discriminate easily • Communications ○ Internet • Criminal • Passport • Finances • Transport • Appearance
Desensitive and view objectively
Reflect about relationships and race
1 note
·
View note
Text
WPS
Wi-Fi protected security was created by the Wi-Fi alliance and introduced in 2006. The aims of WPS was to allow home users who knew little about security or was intimidated by WPA to easily connect to a network without entering a long password.
WPS has four modes of connection:
PIN method: A user reads the PIN from the display on the wireless client device. The PIN is then entered usually at the network’s access point.
Push Button method: The user pushes a button which could be virtual or physical on both the access point and the wireless client device. The devices go into discovery mode and connect with each other.
To minimize the vulnerability of this, the discovery mode turns off after the connection has been established or after a certain amount of time.
Near-field communication method: The user brings the client device close to the access point.
USB method: The user uses a USB to transfer device between the client device and the access point. Support for this mode is deprecated.
A major security flaw of WPS is a brute force attack of the WPS pin. The WPS pin is 8 digits long. The 8th digit of the pin is a checksum of the first 7 digits so there are 7 unknown digits in each pin. This means there are 10^7 = 10,000,000 possible combinations or 23 bits of work.
However, the first half of the pin (first 4 digits) and second half of the pin (last 3 digits) is actually checked independently so the possibilities are actually 10^4 + 10^3 = 10,000 + 1000 = 11,000 or 13 bits of work. As a result, it can be cracked in a few hours.
Once the attacker has the WPS pin, they can then recover the WPA/WPA2 shared key. This is why the inclusion of WPS is a vulnerability of WPA/WPA2. The pin authentication method is a mandatory method that all WPS devices must support. If able to, WPS itself should be disabled.
There is another attack called the Pixie dust attack which attacks the WPS implementation of several wireless chip makers.
The most obvious vulnerability is a physical attack. If the access point is not kept in a secure area, then an attacker can simply gain access via the push button method. Knowledge of the passphrase is not needed. Devices may also have their WPS pin printed on the device and if it can’t be changed or disabled then this is a vulnerability to the PIN method.
0 notes
Text
WPA3
The Wi-Fi alliance announced WPA3 in January 2018 as a replacement to WPA2. It adds four features not found in WPA2. However, most devices don’t use WPA3 yet as it is still an optional feature. As it slowly gets adopted it may be set to mandatory by the Wi-Fi alliance.
WPA3 will offer privacy on public Wi-Fi networks by using “individualized data encryption”. This means that when you connect to an open Wi-Fi, the traffic between your device and the access point will be encrypted despite not entering a password during connection. An attacker will have to crack the encryption to snoop
WPA3 will offer protection against brute force attacks. This is responding to the KRACK attack on WPA2. WPA3 defines a new handshake to prevent this.
WPA3 will offer an easier connection process to devices without displays. It was a promise to “simplify the process of configuring security for devices that have limited or no display interface”. This sounds a lot like WPS which created vulnerabilities to WPA and WPA2.
WPA3 will also offer higher security for government, defences and industrial applications. It is a feature requested by the US government for stronger encryption on critical Wi-Fi networks.
Critical infrastructure shouldn’t be connected to the internet anyway, so I don’t really understand the last feature.
3 notes
·
View notes
Text
Types of WEP attacks
First there is a dictionary attack. It only needs to capture one encrypted packet and runs it through a word list. It is not effective against a randomly selected key, only effective against a passphrase entered by the user.
A better attack is the FMS attack. It is a statistical attack which requires many packets to expose the password. How WEP encrypts a packet is it takes the IV and the shared secret key, puts it into the RC4 cipher and the RC4 generates a key stream which is then used to encrypt. The issue is that IV is only 24 bit and when there is heavy network traffic, the same IV’s will be re used.
FMS exploits this through packet injection. Packet injection allows an outsider to generate a large amount of traffic on the network without being associated with it. It is a kind of replay attack. First a packet is captured.
Generally, the type of packet that is captured is an address resolution protocol (ARP). It’s a TCP/IP protocol that converts an IP address into a physical address, like the ethernet address. If a client wants to obtain a physical address it broadcasts an ARP request. The host that has the address replies with a physical address.
So, an attacker listens for and captures the ARP packet then retransmits it to the access point. This results in the access point repeating the ARP packet with a new IV. The attacker keeps retransmitting the same ARP packet over and over. Each ARP packet sent back is sent with a new IV. Eventually the same IV’s are used, and the attacker can determine the key
A PTW attack is a newer attack of WEP that improves on FMS. It implements a key ranking strategy through a decision tree to determine the most likely correct key. The PTW attack requires much less data packets to crack the key.
0 notes
Text
Project Update
A little bit stuck with my project. So, I want to use Kali Linux to crack WEP. It’s a distribution designed for penetration testing. In order to do any sort of Wi-fi hacking, you require a wireless network adapter that is capable of packet injection and monitor mode.
A wireless network adapter capable of packet injection gets in between the conversation between the client and the router and sends forged packets causing them to repeat themselves many times. Monitor mode listens to wireless packets, basically discovering networks.
Only certain chipsets of wireless cards are capable of packet injection and monitor mode. After doing some research, I so happen to have an adapter that matches these chipsets.

I use windows at home, so I set up a virtual machine with Kali Linux. I then tried to set up the adapter to work on the virtual machine.
After trying for many hours and searching online for many hours, my adapter just doesn’t want to work. The machine detects it, but the adapter doesn’t turn on so I can’t detect any Wi-Fi.
A little bit worried but not completely the end of the world. I am trying to get my hands on another adapter that can do this.
In the meantime, I wrote up some stuff about WEP attacks. If in the worst case scenario, I don’t manage to get anything working, I’ll just try to keep writing interesting things about Wi-fi security.
1 note
·
View note
Text
WPA2
WPA2 replaced WPA as of 2006. The biggest change between WPA and WPA2 was the use of AES encryption for its data.
AES uses a symmetric key algorithm, which uses the same key for both encrypting and decrypting data. AES is used by the US government to protect classified information. It is the first and only publicly accessible cipher which is approved by the NSA for top secret information.
How AES works basically is a password is chosen, and a cipher key is generated based on that password. The cipher key is used to encode the files that want encrypting. This process has several iterations and each time a new key is generated from the key you just used. In each step, the values of the bytes in that file are trading places with other bytes
WPA2 implements AES through CCMP which is the actual encryption protocol. CCMP provides Confidentiality and Authentication. CCMP was introduced as the replacement to TKIP. However, TKIP is still kept in WPA2 as a fallback system as well as for compatibility with WPA.
One of the big vulnerabilities of WPA2 is the Key reinstallation attack (KRACK). By repeatedly resetting the nonce (arbitrary number used once) transmitted in the third step of the WPA2 handshake, an attacker can gradually match encrypted packets seen before and learn the full keychain used to encrypt the traffic. The vulnerability is in the Wi-Fi standard itself and not the implementation so any implementation of WPA2 is vulnerable. This allows the attacker to bypass the security protocol and intercept data. A brute force attack.
Similar to WPA there is also a vulnerability by attacking WPS if it is enabled.
The Wi-Fi alliance announced WPA3 in January 2018 as a replacement to WPA2. It adds four features not found in WPA2 to address the shortcomings of WPA2.
0 notes
Text
Something Awesome
Wasted in total about 6 hours from last night to today trying to set up the router as a wireless access point. The problem that I was having was that I was able to connect to the router but then I wouldn’t be able to log into it because there was apparently no WI-FI. In the end, it was because of a faulty LAN cable from my main router to this router. Very frustrating. But it’s working now, and I can now connect using Wi-Fi and access this old router.
To make this ordeal worth it I thought I would do some research as to what I was actually doing.
A wireless access point is a hardware device that allows other Wi-fi devices to connect to the wired network. It connects to the router via LAN. What I first had to do was change the IP address of the router. An IP address is a device’s unique identifier when connected to some kind of computer network and is composed of a string of numbers e.g. 192.168.0.4. It serves two functions, to host or network interface identification and location addressing.
I changed the IPV4 which is a protocol that defines the IP address as a 32-bit number. There is actually a thing as IPV4 address exhaustion which is the depletion of available IPV4 addresses so IPV6 was introduced which uses 128 bits.
The IP address of the old router had to be different to the IP of my main router in order to avoid an IP address conflict which is when two endpoints on a network are assigned the same IP address. In a conflict, both devices will have problems connecting to the network.
Generally, though IP conflicts are resolved by Dynamic Host Configuration Protocol (DCHP). A DCHP server is used to issue unique IP addresses and automatically configure other network information. In this case the router acts as a DCHP server. However, we want to turn off DHCP for the old router because we only want the main router handing out DHCP. The IP address of the old router becomes static.
I then connect the LAN cable to the LAN port of the old router and done. I can now receive Wi-Fi and connect to the internet while connected to the old router.
0 notes
Text
Something Awesome
So, I finally managed to get my hands on an old Bigpond Netgear router. Had some trouble logging into it on my desktop but worked fine on my laptop. Then I accidentally locked myself out and had to reset everything but hopefully everything’s fine now.

Upon further analysis I realized that WEP actually has two kinds of authentication. The one I talked about in my WEP blog post was shared key authentication. The other method is Open System authentication.
In Open System Authentication (OSA), the wireless local area network (WLAN) client, which is us in this case, doesn’t provide credentials to the access point during authentication. Any client can authenticate with the access point. Basically, no authentication is happening.
The client sends a request for authentication to the access point. The access point generates a random authentication code, intended for use only during that session. And the client accepts the authentication code and becomes part of the network as long as the session continues.
Open system authentication is actually more secure than shared key authentication because data is not as easily intercepted. However, it is more vulnerable to DDOS and also any WLAN client can connect to the access point.
1 note
·
View note
Text
OWASP Top 10 – Injection Attack
An injection attack is when an attacker applies untrusted input into an interpreter of an application. This usually occurs when user supplied data is not validated or filtered properly. The input gets processed by the interpreter and alters the execution of the program.
To give an analogy, pretend you are a robot that fetches books from a library. To know what book you’re supposed to fetch, you are given instructions on a piece of paper by people. The instructions might look something like this:
Fetch book ____ from section ____ in aisle _____ and place it on the counter.
A normal instruction would look like this:
Fetch book Harry Potter from section H in aisle Six and place it on the counter.
However, what an attacker might do is they supply some wrong input that can change the function of what you’re supposed to do.
A bad instruction might look like this:
Fetch book Harry Potter from section H in aisle Six and rip out all the pages then return to your normal spot. and place it on the counter.
The bolded sections were inputs from people requesting a book. Obviously, the inputs in the instruction weren’t what was expected. This technique is called injection and it is an attack that is often found in SQL, LDAP, XPath, or NoSQL queries, OS commands, XML parsers, SMTP headers, expression languages, and ORM queries.
So how to prevent?
Input validation was the traditional approach. However this solution becomes an annoyance when applications sometimes have to let potentially harmful characters in such as ‘ which could appear in names.
The other approach is escaping and is used to ensure characters are treated as data and not characters that may be relevant to the interpreter.
Another approach is to try to use API that avoids the use of an interpreter entirely
1 note
·
View note
Text
Week 6 Tutorial Personal Notes
Cyber Warfare • Target critical infrastructure ○ Banks, bank accounts ○ Stock exchange - alter data § Finance ○ Train system, public transport system ○ Traffic lights ○ Disable power stations, power grid § Blackouts to the city ○ Aircraft/ air defences ○ Influence Campaign during elections ○ Nuclear programs ○ Water § Industrial control system § Technology layered on top of old infrastructure § Purification/leak chemicals into the water ○ Healthcare § Pacemakers, life sustaining devices § Ransomware attacks on hospitals ○ Communications ○ Emergency Services ○ Food • Win function is just instructions • Put the win function at the beginning of the buffer overflow • Return address to the beginning of buffer • Buffer is in memory • You've now put the win function/instructions into the memory • Shellcode is code that gives you the shell
aslr constantly moves the memory which moves the buffer/return address in the stack project is part of the job application secsoc ctf jazz scrubs
desperate people are dangerous, they're willing to do more MAD US attack critical infrastructure stuxet Iran met the standard because they attacked infrastructure during peacetime
5 things that you would do to improve defence • Move towards peace • Move our critical structure into more • Move critical structure away from internet • Intranet
5 things to improve offense • You win if you lose less • Move towards peace • Bounties for killing enemy
Improve Defence • Wargames with other countries ○ Pentesting internal • Espionage • Independent channels of communication ○ A mitigation • Education ○ Phishing ○ Ransomware ○ Stats • Propaganda ○ Comradery • Law Enforce security standards • Deportation ○ Turn people • Allies • Diplomacy • Treat all resources with importance • Critical infrastructure is not connected to the internet • Majority of hackers don't go to the government because companies pay better
Improve Offence • Wargames with other countries • Zero days ○ Vulnerabilities that haven't been discovered that you stockpile • Propaganda ○ Appear vulnerable or appear • Espionage • Assassinate • Frame enemies • Pre-emptive strike
1 note
·
View note
Text
WPA
Wi-fi protected access, Wi-fi protected access 2 and Wi-fi protected access 3 are security protocols developed by the Wi-fi alliance to secure wireless networks. WPA was developed to provide more sophisticated data encryption and better user authentication than WEP. It became available in 2003. WPA was designed to be backward compatible with WEP so it was easy to integrate. All it needed was a simple firmware update on WEP based devices. However, it was put out as a placeholder for the incoming WPA2 which would come out in 2004
WPA implements the Temporal Key Integrity Protocol (TKIP). It attempted to address the security problems encountered in WEP protected networks by providing stronger encryption. Because it was essentially an updated WEP, TKIP uses the same encryption engine and RC4 algorithm defined for WEP.
The important part of TKIP is that it changes the key used for each packet. WEP used a 64-bit or 128-bit key that had to be manually entered on devices and also does not change. TKIP dynamically generates a new 128 bit key for each packet which is created by mixing a base key, the MAC address of the transmitting station and the serial number for the packet.
When a packet is transmitted using TKIP, the packet has a unique 48-bit serial number that is incremented every time a new packet is transmitted. This ensures that the key is different for each packet and avoids collision attacks which could happen in WEP when the same key is used for two different packets. This also prevents replay attacks.
One of the worst issues with WEP was the reuse of a well-known key by everyone on the WLAN. TKIP solves this by generating a new base key each time there is an association with the access point. This base key is part of the encryption for each packet sent.
WPA also has a message integrity check using TKIP which is designed to prevent attackers from altering and resending data packets. WEP had this in the form of CRC but it didn’t provide a good enough integrity guarantee. TKIP is much stronger than CRC but not as strong as the algorithm of WPA2.
Attacks on WPA usually exploit the vulnerabilities of WEP which is what it was built around. WPA breaches also happen via attacks on WPS which was the supplementary system was it was rolled out with.
0 notes
Text
Week 5 Tutorial Personal Notes
• History of hacking • Contribute to open source - look at slides ○ Take control of software • Everything is bugged by design • Intel cpu ○ Intel IME ○ Extra cpu in the cpu that the os can't see, in the chip ○ Can't buy hardware that's safe ○ They say it's admin stuff • Rootkit can modify anything in the OS, do anything • Sony BMG rootkit • Software hierachy ○ If the bottom is fked then even if everything on top (os, processes) even if it's completely safe is also fked • Corporations only care when it affects them • Government brought in foxtel to guide NBN
memset(buf, sizeof(buf), 0);
government, corporation
substitution, transposition, vignere, one time pad
assets risks should we go ahead of making driverless cars
assets: reputation software knowledge
risks
mitigations
Government • Safety ○ Protect citizens • Want secure software • Public utility ○ Drop tradidtional IP ○ Open source ○ Audited • No monopoly ○ Data is open source • Encourage competition
Executives • Reputation is important • Correct model • Cooperating with governments • Concerns about espionage
Mixing data and control • Phones are controlled by frequencies • Supplying frequencies to the phone to do commands • People shouldn't be able to do that
Open source • Pubic reputation with computer scientists • Economic benefit?
Closed source software is not as safe as open source • No one is auditing it • Companies can pay for auditing but its not in the paid auditor's benefit to actually audit it • They just run it through a tool
Better to have a long password rather than a jumble of letters
If open source gets hacked then closed source would also get hacked
Internet Safety • Use password manager ○ bitwarden • Javascript is aids ○ Java script is mixing code and data ○ Script your username or something and then javascript runs it • Firefox open source ○ Google not • Browse only with https privacytools.io
0 notes