She/they, late bloomer, though I am exploring living without any gender
Last active 2 hours ago
Don't wanna be here? Send us removal request.
Text
STARTING TOMORROW

Scientists in weather and climate are live streaming for 100 hours to make their case to the American public.
They are live streaming, but engagement is necessary for it to work. SHARE THIS WITH PEOPLE, RECORD THE STREAM, POST CLIPS OF IT THAT ARE FUNNY, if you can tune in, PLEASE DO!

This is something that has to be heard by as many people as possible. Put it on in the background! See if you can get other people to watch it! Do whatever you can do support those who are trying to be supported! Anything and everything helps!
TUNE IN HERE
article I posted screenshots of here
71K notes
·
View notes
Text
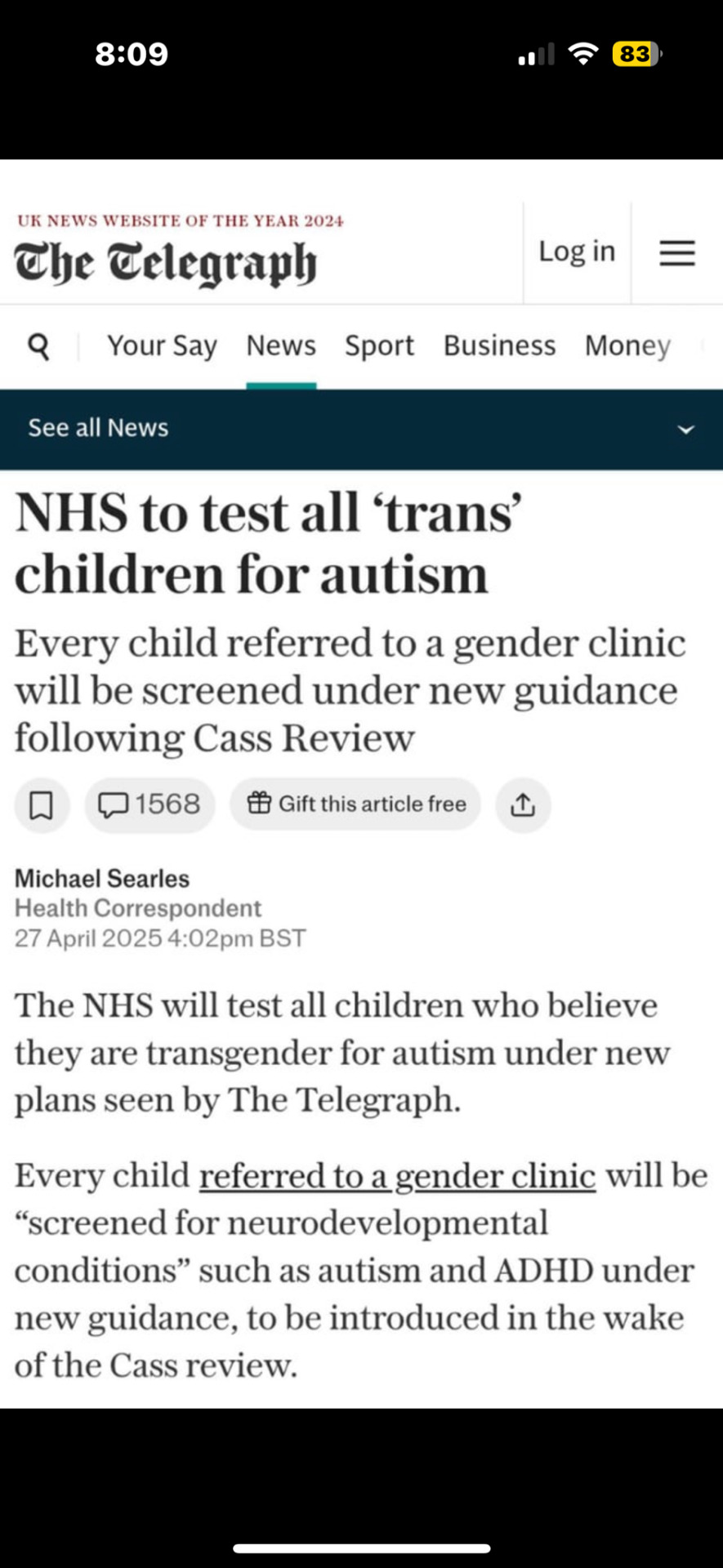
Saw this on Reddit today. Things just keep getting worse.
5K notes
·
View notes
Text
Funny how the same people would not accept terms like 'person who menstruate' on menstrual products but advertise themselves as someone with "large gametes". Being reduced to their gametes is just fine with them!

Such a great, revealing peek into the transmisogynist’s mindset
5K notes
·
View notes
Text
Hey did you know there's a tell all book about the behind the scenes of Meta and the author is forbidden from promoting it?
The good news is however that it's already published and can't be stifled and whoever didn't sign the NDA can promote it as much as they want.
82K notes
·
View notes
Text
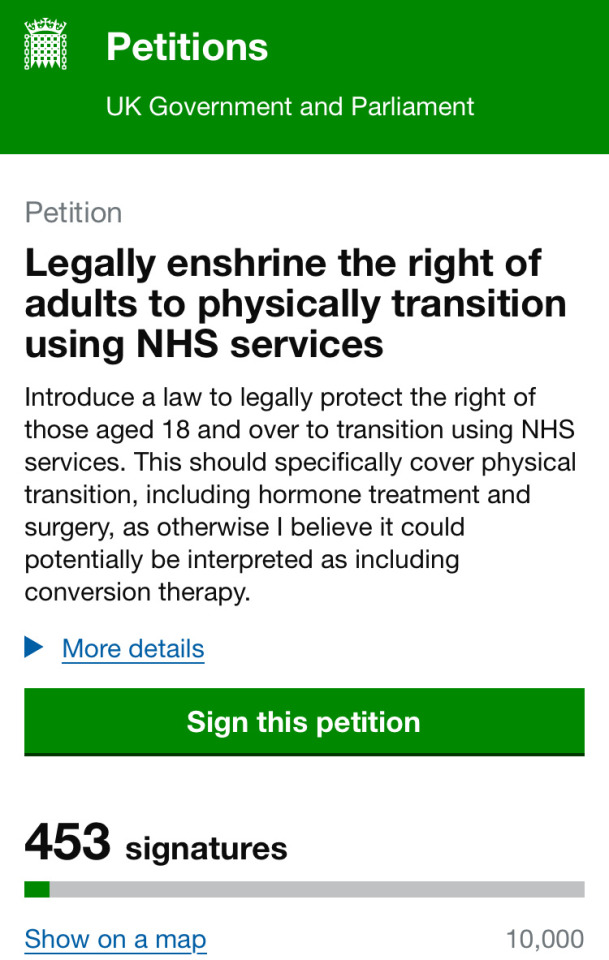
Uk peeps!! Let’s get this going! 🏳️⚧️🇬🇧
85K notes
·
View notes
Text
HEY GUYS!!
GUYS!!!
FRANCE HAS REACHED THE REQUIRED NUMBER OF SIGNATURES ON THE CITIZEN'S INITIATIVE AGAINST CONVERSION THERAPY IN THE EU!!

ONE COUNTRY DOWN, SIX TO GO!!
We also need still quite a few signatures in order to reach the one million required.
As to date, the six other countries with the most signatures are:
Spain - 38.72%
Finland - 30.31%
Ireland - 24.86%
Netherlands - 24.15%
Germany - 23.54%
Belgium - 23.09%
So yeah, still a long way to go, but we ARE slowly getting closer. Don't stop now! Don't let this stay within the community, either, if you have any friends or family who are open to queer rights, get them to sign, too!
54K notes
·
View notes
Text
Skip Google for Research
As Google has worked to overtake the internet, its search algorithm has not just gotten worse. It has been designed to prioritize advertisers and popular pages often times excluding pages and content that better matches your search terms
As a writer in need of information for my stories, I find this unacceptable. As a proponent of availability of information so the populace can actually educate itself, it is unforgivable.
Below is a concise list of useful research sites compiled by Edward Clark over on Facebook. I was familiar with some, but not all of these.
⁂
Google is so powerful that it “hides” other search systems from us. We just don’t know the existence of most of them. Meanwhile, there are still a huge number of excellent searchers in the world who specialize in books, science, other smart information. Keep a list of sites you never heard of.
www.refseek.com - Academic Resource Search. More than a billion sources: encyclopedia, monographies, magazines.
www.worldcat.org - a search for the contents of 20 thousand worldwide libraries. Find out where lies the nearest rare book you need.
https://link.springer.com - access to more than 10 million scientific documents: books, articles, research protocols.
www.bioline.org.br is a library of scientific bioscience journals published in developing countries.
http://repec.org - volunteers from 102 countries have collected almost 4 million publications on economics and related science.
www.science.gov is an American state search engine on 2200+ scientific sites. More than 200 million articles are indexed.
www.pdfdrive.com is the largest website for free download of books in PDF format. Claiming over 225 million names.
www.base-search.net is one of the most powerful researches on academic studies texts. More than 100 million scientific documents, 70% of them are free
301K notes
·
View notes
Text
I wish Americans fucked with more foreign music. You don’t have to know the language to appreciate a good record. Folks in other countries listen to our music and don’t speak a lick of english. Music needs no translator
237K notes
·
View notes
Text
I don’t know who needs to hear this, but please don’t break promises you make to yourself just because it’s you the promise is being made to. You told yourself you’d go on a walk tomorrow morning? Do it. You said you’d get more consistent with your skincare routine? Make it happen. You promised yourself you would work on establishing boundaries regardless of who’s on the other side of them? Follow through with that. Don’t wake up the next day and go “well I don’t HAVE to do this” “it wouldn’t hurt to postpone this” “this isn’t a big deal” because it literally is. Every promise broken is another nail in the coffin of your self-actualization. It’s another major roadblock to developing healthy self-love and self-respect. Weigh promises you’ve made to yourself the same way you would weigh promises you’ve made to others.
20K notes
·
View notes
Text
Evil Malware
Welcome back to another episode of An Actual Post. As usual, no prior computer science education needed. Today I'm going to talk about the worst of the worst malware. A lot of things has happened since what the general population consider to be viruses; annoying and maybe steals some money or logins. Unfortunately it's nowadays way way way worse than that so prepare for some uncomfortable reading!
Since the dawn of Stuxnet (which I wrote about here), malware has gotten increasingly more real-life, with real-life complications. It could be the Pegasus spyware, that targets political activists in authoritarian regimes, or disruptive infections that put a stop to Copenhagens metro trains for a few hours. But we're merely in the beginning, because in the last few years, some nasty shit has been going down. I'm going to write about two (technically three but I'll group the first two together for obvious reasons) of the worst incidents we've seen today.
BlackEnergy and CrashOverride
This piece of malware has been around since early 2000's, for the intention of creating DDoS attacks (which I wrote about here) from infected computers. It has since then branched out in its usage, particularly into targeting infrastructure environments. Most notable is the 2015 Ukrainian powergrid incident, which occured when the Russian hacking group known as "Sandworm", infected three Ukrainian energy companies, wiping out systems and causing a power outage for over 250 000 households during winter. The attack began with just one infected document being opened in the affected companies. When BlackEnergy infected their systems, it opened up a remote connection to the attackers, making them able to control the entire powergrid opreation from inside Russia, and thereby switching it off.
That was not enough though, as the attackers also implanted another piece of malicious software known as KillDisk, which wiped out many of the ciritical operation systems, as well as cutting off the connection to the UPS units, which are backup generators in case of system outage. To add a cherry on top, BlackEnergy did what it was originally intended to do - DDoS attacks - towards the energy companies call-centers, so that customers were not able to call and ask what was happening.
The Ukrainian powergrid is quite outdated, which made the attack easier, but it was also the saving grace, as they still had manual power-switches (as opposed to purely digital, which were under the attackers control), so power was eventually restored before they had to rebuild all of their digital systems. This is more concerning for countries with modern powergrids, as manual switches have all been replaced by only digital, meaning power restoration could take weeks or months in case of a similar attack.
Besides the energy companies, three other critical Ukrainian infrastructure organisations were hit by BlackEnergy, but did not result in any operational outages.
But it didn't stop there. Just one year later, in December 2016, a similar attack struck Kiev, successfully taking down one-fifth of the countrys electrical power. Like with the BlackEnergy incident, it was quite quickly restored, but there was a far more horrifying infection this time. Named CrashOverride, the malware was much more sophisticated than BlackEnergy, did more things automatically without the need of input from a remote attacker. It was also modular, meaning that functionalities could just be added to it like lego-pieces, adapting it to whatever kind of electrical grid it was entering. This meant that it wouldn't just be able to infect only Ukranian electrical grids, but just about any country's. Furthermore, evidence points to the 2016 CrashOverride infection only being a test-run.
Triton
Last but definitely not least - Triton, the first (known) malware designed to kill.
But before we talk about it, we need to look at what happened in Bhopal, India in 1984 when what has since been considered the worst industrial disaster of all time occured. At the Union Carbide India Limited pesticide plant in December 2nd, one of the gas tanks had a fatal malfunction, creating a massive gas leak of methyl isocyanate, which is extremely toxic. The leak spread to the surrounding city of Bhopal, resulting in almost 600 000 injured people, 40 000 temporary injuries, 4 000 permanent or severe injuries and over 8 000 people died within the first two weeks, with an estimated additional 8 000 deaths following due to injuries in the time after.
This was of course not caused by Triton, but it became the inspiration for the creation of the malware In 2017, a new piece of malware was discovered in Schneider Electrics industrial control system (called Triconex) at a Saudi Arabian petrochemical facility, which unravelled a horrible and complex secret. The infection chain for Triton contains many steps, so let's start with a brief overview of what the Triconex ICS and SIS is. ICS (Industrial Control System) are computers that handles all the industrial processes, computers that are programmed to do one thing and one specific thing only, unlike our regular PCs which you can play games or surf the internet and whatever. ICS will be computers who control valves, releases chemicals into vats, spins stuff around, or whatever automated processes may happen at an industrial facility.
SIS (Safety Instrumented System) are a kind of ICS that are responsible to check that everything is going alright and, if needed, will take over the process in case some ICS is failing and may result in damage, fire, injury or other disasters. So a SIS are monitoring failsafes, meant to prevent what happened in Bhopal.
Unless, of course, you program a malware intended to make the SIS malfunction.
What happened in the Saudi Arabian petrochemical facility started as follows:
The attackers successfully implanted a remote access trojan, which just like in the BlackEnergy case, makes the attackers able to control infected machines remotely. However, you can't infect a ICS or SIS this way, you need to enter a regular computer with internet access first, which is what they did. The initial machine was an engineering station, on which ICS and SIS computers are controlled. From there, the attackers wanted to plant their own software on the ICS and SIS machines, but there was a problem; the software can't be installed without someone turning a physical key on the Triconex devices, as a security measure. A second problem is that every time new software changes are made to a Triconex device, the old software will be deleted and replaced entirely by the new, which meant that the malware was at risk of being deleted if any engineer made any software changes.
So a second piece of Triton malware was made to overcome those hurdles. Instead of being save where the software should be saved in the Triconex devices, it saved itself where the firmware was installed (the piece of software that's made to have the Triconex work as opposed to where the software that tells the Triconex what to do), this not only gave Triton persistence even if new software was loaded, but also overrides the physical key as firmware always has administrator privileges. With all this in place, the attacker could execute any commands at the comfort of their home to both the ICS and SIS systems in the facility.
As luck would have it, before the attackers were able to cause any harm, the facility experienced a safety incident, prompting shutdown of the whole operation, and an investigation later uncovered the malware in the systems. Had Triton not been discovered in time, it would have been able to cause catastrophic failures similar to what happened in Bhopal. But just because it was thwarted this time, doesn't mean it's gone for good. There will always be some actor who is willing to try again.
Thank you for reading and sorry if I scared you, but honestly I think people need to be aware of the situation, as for some bisarre reason, events like these are not reported in the news. If you have any questions, feel free to send an ask!
267 notes
·
View notes
Text
the edit itself
this edit is getting taken down from tiktok every time someone reuploads it, its straight up censorship at this point
Im not even american but im having a great time with this
DONT LET THIS DIE
credit to miraculousgastropod for the original
103K notes
·
View notes
Link
Caper in the Castro is a legendary video game, not because legions of die-hard fans continue to play it, but because it was thought to be lost forever. Now, what is largely considered to be the first LGBTQ-focused video game (it was released in 1989) is on the Internet Archive for anybody to play.
The game is a noir point-and-click that puts the player in the (gum)shoes of a private detective named Tracker McDyke who is, in case you couldn’t guess by the name, a lesbian. McDyke must unravel the mystery behind the disappearance of Tessy LaFemme, a transgender woman, in San Francisco’s Castro district, an historically gay neighbourhood.
OOOOOHhh!
The game was released as charityware – freely, with a strong request to give a donation an AIDS Charity of their choice. I’d like to push towards still following that and donating, if you’re able.
(And you might also want to donate to the Internet Archive, who is hosting it now, while you’re at it – they’re in the middle of a donation drive, and could use your support.)
84K notes
·
View notes
Text

tweet 1: "happy international lesbian day, if you use the orange and pink flag i designed and have a few bucks to spare i would really appreciate any help at all"
tweet 2: "ive been skipping meals to afford to see a specialist so even $1 helps. i have no family to ask for help."
This international lesbian day I hope some support can be extended to Emily Gwen. The flag they have made has been used by many corporations and they do not receive any money made from those sales. They are also dealing with housing insecurity and have many financial problems
their ko-fi:
19K notes
·
View notes



