Text

Cybersecurity in the Digital Age
This image portrays a figure standing in a futuristic virtual environment, reminiscent of a scene from a sci-fi thriller. The silhouette of a person dressed in a long coat and holding what appears to be a mobile device stands in the foreground. They are facing a vibrant digital interface that displays a variety of cyber-themed icons and holographic projections. Key among these is a prominent digital lock symbol, representing the concept of cybersecurity. The cool neon blue and green color palette suggests a digital world, underlining themes of technology, security, and the challenges of protecting information in the contemporary digital landscape. The environment is filled with flowing data streams and digital wave patterns, suggesting the constant flow of information across global networks. The person's stance implies they are an orchestrator or guardian in this space, wielding the tools and knowledge necessary to navigate and safeguard this complex digital realm.
3 notes
·
View notes
Text
3 notes
·
View notes
Text
1 note
·
View note
Text
Who is Dame Luthas?
Meet Dame Luthas: tech leader turned philanthropist. Ex-UN, Microsoft, now empowers women & children. Read his inspiring story. #techforgood #philanthropy
Dame Luthas is a technology expert, entrepreneur, and philanthropist driven by a passion for empowering underserved communities. With over 25 years of experience, including a significant tenure at the United Nations, Dame Luthas has dedicated his career to leveraging technology for positive change. His expertise spans IT strategy, business development, information security, and management…

View On WordPress
1 note
·
View note
Text
Weekly output: T-Mobile adds fixed-wireless plans, FTC bans non-compete clauses, ransomware prevention, Mark Vena podcast
This week featured vastly less travel than last week, but it also afforded me the rare experience of hearing an executive-branch appointee burst into song. 4/23/2024: T-Mobile Adds New Fixed Wireless Plans: One for Home, One for the Road, PCMag Of all of T-Mobile’s announcements Tuesday, the unlimited-data version of its new Away fixed-wireless plan was easily the most interesting. 4/23/2024: FTC…
View On WordPress
1 note
·
View note
Text
1 note
·
View note
Text
some exciting privacy news for your thursday
On August 24, 2022, the California Attorney General announced a settlement with Sephora, Inc., resolving allegations that the company violated the California Consumer Privacy Act (CCPA).
This is great news. For starters, it shows that California will enforce the CCPA, and to a meaningful degree - hella important because companies rarely bother to expend effort to comply with laws if there’s no punishment for not doing so.
The attorney general also announced that his office notified “a number of businesses” of non-compliance, meaning that all notified businesses have 30 days to fix the violations, or get enforcement action taken against them, too. So over the next month, a bunch of businesses are either going to shape up their privacy practices, or get slapped with serious fines.
In my opinion, though, the most important part of the settlement announcement is that it mentions what Sephora was doing with the data it collected (emphasis mine):
in Sephora’s case, the third parties could create profiles about consumers by tracking whether a consumer is using a MacBook or a Dell, the brand of eyeliner or the prenatal vitamins that a consumer puts in their “shopping cart,” and even a consumer’s precise location. Retailers like Sephora benefit in kind from these arrangements, which allow them to more effectively target potential customers.
The bit about precise location is incredibly important. Most people don’t realize how easy it is to identify someone based on location data alone - and it doesn’t even need to be precise. This study from 2013 proved that you can identify 95% of people using just four imprecise data points taken randomly over twelve hours. In other words, any company that both collects location data and claims that they only collect anonymous data, is lying. It makes absolutely no difference whether your name is attached to the data - you can be identified from it. (If you want to know more about how easily you can be identified by these third-party profiles, check out this talk from the Crypto & Privacy Village at this year’s DEF CON.)
Until the CCPA, consumers had no way to even know what data companies collect about them, much less to whom those companies sell that data or how it gets used to precisely target and manipulate them. This first enforcement action by the AG shows that California is serious about making the CCPA effective and giving consumers the ability to take back control of our own data.
Also: if you want to help this along, you can report non-CCPA-compliant businesses to the CA AG using this form. As far as I can tell, you don’t have to be a CA resident to report, so non-Californians can also report noncompliant businesses if you see them. You can also use this other form to draft a notice directly to the business, which may count as the same 30-day notice the AG uses. So if you send a notice and the business hasn’t complied within 30 days, the AG may be able to take immediate action when you report them.
13 notes
·
View notes
Text
Microsoft Windows software and machines behave as if they were natively designed to leak information into negative dimensions.
3 notes
·
View notes
Text

BTSARMY Security Awareness Edition
Securing Mobile Devices Part 1: Identifying Fake Apps (with Mister World Wide Handsome Kim Seokjin)
Contributors:
ddaengsec
emandro1d
ArmyCompsci
Devika⁷
btsarmysafety
ManelleBTS
13 notes
·
View notes
Text
Fortunately for affected customers though, it appears that only personal information was stolen during this attack and financial information wasn’t accessed.
Oh, nice. Apparently data breaches have become so commonplace that “only personal information was stolen” is regarded as A-OK now. 🙄
6 notes
·
View notes
Text
idk when they did it, but I logged on to my youtube account today to see that Google had CHANGED MY FLIPPING ACCOUNT NAME from the one I CHOSE for it to some unholy amalgamation of numbers and the fakename I used to make that account and I am Annoyed >:( >:( >:(
anyway I spent the morning fiddling with personal info to try and get it to display the account name instead but idk -_- -__- Obvsl there's SOME way to get it back cuz other ppl have old-style pseuds but either it's through some other method or it takes awhile for google to update their unholy spyware cuz my comments are still displaying under that stupid appellation. Gods, I cant imagine how frustrating that must be to ppl who used their actual assigned names when making gmail accounts 15 fucking years ago; the info I put there isn't even 'real' and it STILL feels like a violation X| WHO THE FUCK IS GOOGLE TO DECIDE HOW I SHOULD BE SEEN BY OTHERS?!?!?!
39 notes
·
View notes
Text
Do NOT send pictures of your ID card to discord bots!!!!
Or, like, any online rando.
I ran into a server that wanted to make sure that members are over 18 years old. They wanted to avoid the other thing I've heard of, which is asking you to verify your age by sending pictures of your ID card to a moderator. Good! Don't do that!
However, ALSO don't do this other thing, which is using a discord bot that would "automatically verify" you from a selfie and a photo of your ID card showing your birthday. The one they used is ageifybot.com. There's a little more information on its top.gg page. Don't like that! Not using that!
Why not? It's automatic! Well, let me count the ways this service skeeves me out:
How does the verification process work? There is no information on this. Well, okay, if you had more info on what kind of algorithms etc were being used here, that might make it easier for people to cheat it. Fair enough. But we need something to count on.
Who's making it? Like, if I can't understand the mechanics, at least I'd like to know who creates it - ideally they'd be a security professional, or at least a security hobbyist, or an AI expert, or at least someone with some kind of reputation they could lose if this turns out to not be very good, or god forbid, a data-stealing operation. However, the website contains nothing about the creators.
The privacy policy says they store information sent to them, such as your selfie and photo of an ID card, for up to 90 days, or a year if they suspect you're misleading them. It sure seems like even if they're truly abiding by their privacy policy, there's nothing to stop human people from looking at your photos.
The terms of service say they can use, store, process, etc, any information you send them. And that they can't be held accountable for mistakes, misuse, etc. And that they can change the bot and the ToS at any times without telling you. The terms of service also cut off midway through a sentence, so like, that's reassuring:
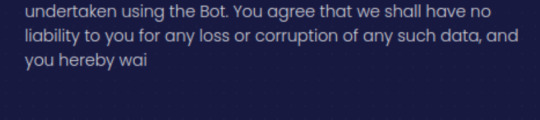
In conclusion, DO NOT SEND PICTURES OF YOUR ID CARD TO RANDOM DISCORD BOTS.
Yes, keeping minors out of (say) NSFW spaces is a difficult problem, but this "solution" sucks shit and is bad.
Your ID card is private, personal information that can be used by malicious actors to harm you. Do not trust random discord bots.
171 notes
·
View notes
Text
Appeal to authority is such a funny concept because on one hand as a society we must. I cannot know all things so there are people I know I can trust because they've studied things, of course I'll defer to them on things. On the other hand, I had a professor who was brilliant, helped create the internet on the DARPAnet project his email was literally his first name @ darpanet. but also, he thought JAVA was the worlds greatest coding language and constantly referred to "the wizards at Sun" Sun being the company that made and maintained java. but like, java sucks. bad.
1 note
·
View note
Text
3 notes
·
View notes
Text
Exploring Java's Built-in Data Structures: A Beginner's Guide

Introduction:
Java, a versatile and widely used programming language, offers a rich set of built-in data structures that form the backbone of many applications. Understanding these data structures is fundamental for any Java developer, as they provide efficient ways to organise and manipulate data. In this beginner's guide, we'll delve into some of Java's core data structures, exploring their features, usage, and best practices.
Arrays: The Foundation
Arrays are one of the simplest and most fundamental data structures in Java. They represent a fixed-size collection of elements of the same type. Declaring an array in Java is straightforward:
This line of code creates an array of integers with a length of 5. Arrays in Java are zero-indexed, meaning the first element is accessed at index 0, the second at index 1, and so on. You can access and modify elements using square brackets notation:
Arrays are efficient for random access but have a fixed size, which cannot be changed dynamically. Java provides other data structures like ArrayList and LinkedList to overcome this limitation. To kickstart your programming career, consider enrolling in Java Training In Chennai for comprehensive learning and skill development.
ArrayList: Dynamic Arrays
A component of Java's Collection Framework, ArrayList offers dynamic arrays that can enlarge or contract in size as needed. Unlike arrays, ArrayLists can hold elements of different types and automatically resize themselves.
ArrayLists offer efficient methods for adding, removing, and accessing elements. They also provide features like sorting and searching, making them versatile for various applications. However, ArrayLists may incur performance overhead due to resizing operations when they reach capacity.
LinkedList: Linked Data Structure
LinkedList is another data structure provided by Java's Collection Framework. In contrast to arrays, elements are stored in linked lists as nodes, each of which has a reference to the node after it in the sequence. Especially in the centre of the list, this structure makes insertion and deletion operations efficient.
LinkedLists excel in scenarios where frequent insertions and deletions are required, but they may have higher memory overhead than arrays due to the additional memory needed for storing references.
HashMap: Key-Value Pairs
HashMap is a data structure that stores key-value pairs and quickly retrieves values based on their keys. It uses a hashing technique to store and retrieve elements efficiently, making it ideal for scenarios where quick access to data is crucial.
HashMaps offer constant-time performance for basic operations like insertion, deletion, and lookup, assuming a good hash function and proper handling of collisions. However, they do not maintain the order of elements.
HashSet: Unordered Collection Of Unique Elements
HashSet implements the Set interface in Java, representing an unordered collection of unique elements. It uses a hashing technique similar to HashMap to achieve fast insertion, deletion, and lookup operations.
HashSet ensures that each element is unique by internally checking for duplicates before adding them. While HashSet does not maintain the insertion order, it provides constant-time performance for basic operations.
Stack And Queue: Linear Data Structures
Java also implements two essential linear data structures: Stack and Queue.
- The latest In, First Out (LIFO) concept is adhered to by Stack, meaning that the latest piece added is also the first to be withdrawn.
- The First In, First Out (FIFO) principle is adhered to by queues, meaning that the first element added is also the first to be deleted.
These data structures find applications in various scenarios, such as expression evaluation, reversing sequences, and managing tasks in computer algorithms.
Best Practices And Considerations
While Java's built-in data structures offer powerful capabilities, it's essential to understand their strengths, weaknesses, and best practices for efficient usage:
- Choose the right data structure based on your application's requirements. Consider factors like the frequency of insertion, deletion, retrieval operations, memory usage, and performance constraints.
- Understand the time complexity of operations for each data structure. For example, ArrayList provides faster random access but slower insertion and deletion than LinkedList.
- Be mindful of synchronisation if dealing with multi-threaded applications. Java provides synchronised versions of some data structures in the `java.util.concurrent` package.
- Utilise generics to ensure type safety and reduce the risk of runtime errors when working with collections.
-Consider using wrapper classes like `Collections.unmodifiableList()` or `Collections.synchronizedList()` for immutable or thread-safe collections, respectively.
- If you're looking for the Best Software Training Institute in Chennai, look no further than our renowned institution, where expertise meets excellence.
Conclusion
Java's built-in data structures form the backbone of many applications, providing efficient ways to organise, manipulate, and access data. From simple arrays to sophisticated HashMaps and LinkedLists, Java offers a versatile toolkit for developers to tackle various programming challenges. By understanding these data structures' features, usage, and best practices, beginners can lay a solid foundation for building robust and scalable Java applications. So, dive into Java's world of data structures and unlock the full potential of your programming endeavours.
2 notes
·
View notes
Text
Java remains a powerful and versatile programming language that continues to evolve. By understanding its core concepts, exploring its wide range of applications, and continually practicing and learning, you can master Java and unlock numerous exciting career opportunities in software development. Whether you aim to build web applications, mobile apps, enterprise solutions, or delve into big data and IoT, Java provides the tools and resources to bring your ideas to life. If you’re looking to enhance your skills, consider enrolling in a best Java course in Thane, Mumbai, Navi Mumbai, Delhi, Noida and other cities to get comprehensive training and hands-on experience.
2 notes
·
View notes
Text
Java 9 Modules: Organizing Code for Better Maintainability
Certainly! Embracing Java 9 modules presents a potent mechanism for structuring code and enhancing maintainability within Java applications. By segmenting code into modules, developers can establish tidier, more navigable codebases, facilitating easier comprehension, testing, and evolution over time. Harnessing the advantages of Java 9 modules not only streamlines development processes but also mitigates maintenance burdens, thereby fostering the creation of sturdier and more scalable Java applications. Enrol today at our Java Training Institute in Gurgaon, Kanpur, Dehradun, Kolkata, Agra, and all cities across India to master these indispensable skills and propel your career to new heights.
2 notes
·
View notes