Don't wanna be here? Send us removal request.
Text
Week 8-7: Tutorial
After we presented our Something Awesome projects, we began discussing the case study; you’re a major, and your cadet has returned from a scouting mission with an alien from another planet and a lot of valuable intelligence. However, he became invisible on the return trip, and you’re now tasked with extracting the report and determining whether the alien can be trusted.
For this particular problem, it was quickly identified that a One-Time Pad will be most effective in confirming the presence of the cadet. This can be done in a number of ways, but the most straightforward would be to invite only the cadet to a room, provide him with the codes, and then return without the alien knowing about the transfer. In addition to this, the major and cadet could agree on a form of validation to ensure the alien’s truth. For example, agree on what the first X messages from the cadet will be, or have a specific message every X messages to ensure that the alien isn’t lying. This way, if the alien lies at any stage, we can assume that it has malicious intent and blast the fucker to kingdom come.
An alternative to the above involves some less Orthodox methods. The alien could be imprisoned and detained; the cadet can be assumed dead and the alien hostile until proven otherwise. The alien can be coerced by means of torture, so that it’s incentivised to tell the truth. The cadet’s existence can be proven when the alien conveys some information that only the cadet knew and it having no way of knowing. And then we blow the fucker up.
0 notes
Text
Week 8-6: Lecture
Cyber issues can always be attributed to human error.
Humans are inherently fallible, and will lie at any opportunity they get.
People are bad at picking the right features to focus on - usually our attention is fragmented.
People should focus on what is logically important, but instead focus on what is evident.
Similarity Matching - When people look for similar situations that happened to them in the past that they are familiar with and applying it to the current situation.
Frequency Gambling - If many patterns match, you pick the one which you have the most experience with.
Bounded Rationality - How we have a limited amount of information, meaning our ability to make decisions is bounded by that information (or lack thereof).
People harbour a bias toward positive statements, and often subconsciously avoid evidence that might suggest otherwise.
People have a tendency to keep the peace when in a group - good for system analysis.
Confirmation Bias - Preferring the evidence that confirms what we believe.
Intent is the determining factor for something being categorised as an accident or attack.
People also have a tendency to simplify situations to have only one cause.
Coding principles -
Simplicity is desired; complexity begets confusion
Coupling is not desired; dependencies can lead to complications
Cohesion is desired; similar components utilise each other more
The system itself isn’t faulted if it doesn’t fail at every level.
Cassandra Syndrome - Knowing the truth but nobody believes you.
Chekhov’s Gun - Anything in a scene is there for a purpose, and must be used in the following scene.
0 notes
Text
Week 8-5: Authentication (Activity)
TOTP
If there are no restrictions on login attempts, the passwords can be brute forced. Additionally, the passwords themselves can be phished from Barbara’s phone.
OAUTH
Susceptible to a man-in-the-middle attack. Someone could intercept the signal and fabricate a response that could phish Barbara for the password to her account.
S/KEY
Also susceptible to a man-in-the-middle attack. This method is also at risk of race condition attacks, as well as the identification of collisions in the hashing function.
0 notes
Text
Week 8-4: Spot the Fake (Activity)
Find an example of something in everyday life that could be easily faked and explain how it might be achieved.
Any form of an online presence can be fabricated easily. For example, one might notice that the target individual doesn’t have an account (and therefore presence) on a particular platform. One may then be inclined to create a false account on behalf of the targeted individual, and pretend as if they’re them. This form of identity theft is remarkably common, and was the catalyst - among other reasons - for social platforms designing a verification system for their users. Although common occurrences of identity theft (those that target non-celebrities or individuals that are overall inconspicuous) are still persistent, the verification system has prevented the theft of popular and well-known personalities.
0 notes
Text
Week 8-3: Security Everywhere
https://edition.cnn.com/2019/07/21/europe/bulgaria-hack-tax-intl/index.html
This week, records of more than 5 million Bulgarians got stolen by hackers from the country’s tax revenue office. Taking into account the fact that the population of Bulgaria hovers around 7 million, the scale of the hack means that just about every working adult has been affected. The compromised data can be found online quite easily, without a background in IT. The data is considered highly valuable, and is expected to be useful to the hackers for years to come.
"Your date of birth is not going to change, you're not going to move house tomorrow," said Guy Bunker, an information security expert and the chief technology officer at Clearswift, a cybersecurity company. "A lot of the information that was taken was valid yesterday, is valid today, and will probably be valid for a large number of people in five, 10, 20 years' time."
The incident can be attributed to a number of factors, one of which being outdated systems. Many governments use private companies to manage the data they collected, but do not pay attention to cyber-security. As a result, third parties still have access to old data that is still relevant at this time, and can be very easily compromised.
0 notes
Text
Week 8-2: Security Everywhere
https://www.forbes.com/sites/zakdoffman/2019/07/20/russian-intelligence-has-been-hacked-with-social-media-and-tor-projects-exposed/#790b6ea66b11
News has spread that hackers have successfully targeted the FSB - Russia’s Federal Security Service. The attack was successful in leaking 7.5 terabytes of data from a major contractor. This leaked data revealed secrete projects intending to de-anonymize Tor browsing, scrape social media and help the state split its internet off from the rest of the world.
Tor is a commonly used browser, made popular by the fact that it stores no cookies and is, for all intents and purposes, impervious to attacks and data breaches. Tor essentially provides full anonymity to its users. The intention to de-anonymize this browser cannot be considered as anything other than nefarious, and can have devastating consequences for the digital privacy of Russia’s citizens.
0 notes
Text
Week 8-1: Google Yourself (Activity)
I downloaded my data from Google, and was surprised to see the extent and detail of their records of my activities. There were a few files that struck me as most surprising and concerning.
Map Location Data
Stored with JSON formatting, this file contained just under 9 MILLION LINES OF CODE. Each object contained data fields such as the timestamp, the latitude and longitude, altitude and an inner object storing its own timestamp, along with the predicted activity at the time (UNKNOWN, STILL, IN_VEHICLE, ON_FOOT, WALKING, ON_BICYCLE and RUNNING were the values I could find), as well as a confidence interval for each guess summing up to 100. Having access to this file would mean knowing where I’ve been at what time, making it ridiculously easy to be tracked and also predicted.
Profile Data
A small file that contained my full name, birthday and gender, among other minor fields. Although this may seem quite inconspicuous at first, the usefulness of the file can be understood by exploring a hypothetical; if an attacker were to access this file without knowing anything about me, they would have a considerable advantage to brute forcing my passwords (as an example). Knowing my full name, preferred nicknames and date of birth are significant clues to guessing my passwords. Any advantage a hacker has could potentially be catastrophic, and be the reason for their success in breaching my privacy.
Internet History Data
This was a HTML file containing all the websites I had visited. There was one specifically for YouTube, as well as one for Chrome in general. The actual data stored was the name of the website and a direct link to it. However, the most concerning thing about this file was that it had traced back to up to 6 years in the past. Holy shit. Websites I had visited and YouTube searches I had made in 2013 were popping up, many of which were highly incriminating.
Phone Installation History Data
Another JSON file, containing all the files and apps I’ve downloaded on my phone since it first booted. This included the very first core apps (such as Google Play, Photos, Camera, etc) all the way to recent installations - it even contained a game I had installed yesterday.
Conclusion
Needless to say, knowing they’ve got THIS much data about me makes me want to assume the fetal position and just die. That’s it. Thanks for coming to my Ted talk.
0 notes
Text
Week 7-10: Security Everywhere
https://www.popularmechanics.com/technology/security/a28424868/faceapp-challenge-security-risks/
The FaceApp challenge involves downloading the FaceApp app and applying a filter to a picture of yourself. The filter is applied by a neural network, and appears to age you considerably. However, the company behind the app - Wireless Lab - have raised a number of privacy concerns with their expansive Terms of Service.
The Terms of Service grant FaceApp a “perpetual, irrevocable, nonexclusive, royalty-free, worldwide, fully-paid, transferable sub-licensable license to use, reproduce, modify, adapt, publish, translate, create derivative works from, distribute, publicly perform and display your User Content and any name, username or likeness provided in connection with your User Content in all media formats and channels now known or later developed, without compensation to you”. Although this degree of content ownership is common for app services, FaceApp’s TOS is exceedingly vague.
Current conversations about facial recognition software and deep fakes are highlighting the dangers of individual companies owning large datasets. This kind of information can be weaponized by actors who are interested in doing harm through a cyber-attack or a propaganda campaign. Education about personal security is becoming a necessity, and will likely be the most effective method of preventing a breach of personal privacy.
0 notes
Text
Week 7-9: Security Everywhere
https://nakedsecurity.sophos.com/2019/07/17/germany-bans-schools-from-using-tech-giants-clouds/
Recently, Germany has banned its schools from using cloud-based productivity suites from Microsoft, Google and Apple. This decision was made because the tech companies had failed to satisfy Germany’s privacy requirements and policies in regards to their cloud-based services.
The Hesse Commissioner for Data Protection and Freedom of Information (HBDI) explained that the primary source of concern was that Microsoft was storing personal data (including that of children) in a European cloud that could be accessed by US authorities. In addition to this, they stated that “With the use of the Windows 10 operating system, a wealth of telemetry data is transmitted to Microsoft, whose content has not been finally clarified despite repeated inquiries to Microsoft. Such data is also transmitted when using Office 365”. The HBDI are confident that this problem cannot be rectified with consent, due to the uncertainty related to which data is being collected or how it will be used.
The HBDI went on to include Google and Apple within their criticism of Microsoft. All three tech giants had the same responsibilities and, by extension, issues present. Personally, I believe that Germany have made an excellent move in preserving their country’s digital privacy. There is no expectation whatsoever to compromise one’s privacy for the use of a product. Bastards.
0 notes
Text
Week 7-8: Tutorial
This week, we had to discuss whether we were in favour of the government having more of our personal data or less. Lots of valid points were raised, some of which are listed below. Personally, I’m more inclined to think that governments should have the absolute minimal amount of personal information from their citizens.
For
Having extra information can improve the security and safety of the public. The added surveillance will act as a deterrent for criminals.
The government would be able to make informed decisions that would help the community and society as a whole.
That’s about it. This is a terrible argument to make. Booooo.
Against
Providing the government with personal information will mean that an individual’s privacy would be compromised heavily.
If the data kept within the government is leaked or accessed by a malicious party, the consequences can be devastating.
Humans within the government are susceptible to social engineering and corruption, and so can put our personal data at risk of being exposed.
Anything can be sufficiently justified within the scope of data collection, and so can lead to a slippery slope of using unethical means of data collection under the facade of public safety.
The leaking of information can lead to biases in various facets of public domain, including job prospects and personal safety (as a result of identifying with a particular ethnic or religious group).
0 notes
Text
Week 7-7: Lecture
Richard went over the mid-semester exam. He ended up giving everyone an extra mark for an ambiguous question.
Diffie-Hellman Algorithm - A way of generating a shared secret between two people.
Choose a prime number p and a number g which is coprime to p-1 and tell your partner.
Your partner picks a secret number a, computes g^a mod p and then sends the result to you (known as A).
Repeat the process yourself, call the result B and send it over.
Your partner takes B and does B^a mod p.
You take A and do A^b mod p.
The answer from step 4 is the SAME as step 5.

Vulnerabilities
Buffer Overflow - Attack on the stack, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations.
Functions in C freeze their information when a new function is called. The instruction pointer saves the location of the parent function.
Shell code grants terminal console on remote device.
NOP Sled - Create a long list of No-Ops (0x90) to slide down to malicious code.
Responsible disclosure - Consult the vendor first, then escalate to CERT.
Asset Protection
Important to identify the right things to protect.
Strategies for asset protection:
Ask lots of people.
Underestimate how thorough you are.
Regularly survey the values of people involved in what you are protecting.
Develop a sensible plan.
Re-evaluate the current list of assets.
Bug Bounties
Tend to have a criteria of what’s in and out of scope, as well as what kind of bugs they won’t accept.
Fuzzing - A program that continually adds input.
Some fuzzers are aware of input structure.
They aren’t precise, but can test a large amount of inputs.
Strategies for mutation - Bit flips, byte flips, arithmetic, combination, etc.
Fuzzing can be used to test software effectively.
0 notes
Text
Week 7-6: Update
I’ve finished off the rest of my Something Awesome project and blogged about it. Unfortunately I didn’t have enough time to fulfil the extended portion of the project, but that can be likely attributed to my underestimation of the amount of work it required. Nevertheless, everything’s done and I’ll be aiming to get the job application done this week as well.
0 notes
Text
Week 7-5: Phishing Trump (Activity)
Hi Donald,
We’ve just received a new batch of illegal immigrants for you to try out! Simply click the link below, fill out the required details, and start deporting as many immigrants as you want!
Click here to get started.
The team at Immigrant Source
0 notes
Text
Week 7-4: Email Phishing (Activity)
Facebook Flag
COMP6441{MakeSureYouSetUpTwoFactorAuthToPreventThis!!}
Payment Flag
COMP6441{paymentfraudisreal!}
0 notes
Text
Week 7-3: AES (Activity)
Definitions
Confusion - Each binary digit (bit) of the ciphertext should depend on several parts of the key, obscuring the connections between the two.
Diffusion - A single bit of the plaintext is responsible for half of the bits in the ciphertext, and vice versa.
Avalanche Effect - If an input is changed slightly, the output changes significantly.
SP Boxes - A series of linked mathematical operations used in block cipher algorithms (substitution-permutation network).
Fiestel Networks - A symmetric structure used in the construction of block ciphers. Encryption and decryption require only a reversal of the key schedule.
Block Ciphers - A deterministic algorithm operating on fixed-length groups of bits (blocks) with an unvarying transformation that is specified by a symmetric key.
Stream Ciphers - A symmetric key cipher where plaintext digits are combined with a pseudorandom keystream.
Block Cipher Modes
ECB.
CTR.
CBC.
CBC.
ECB.
0 notes
Text
Something Awesome Sub-Chapter 4.1: Self-Replicating Malicious Code
This sub-chapter focuses on malicious code with the ability to self-replicate, and the distinction between the two most common forms - worms and viruses.
4.1.1 - Worms
Malicious code that spreads to other systems by duplicating itself without attaching to other files.
Worms have two roles, which include spreading to additional computers and carrying a payload.
A payload is what the attacker programs the worm to accomplish after spreading.
Email worms spread by sending a message designed to entice the recipient into clicking a link or downloading an attachment that contains a copy of the worm.
Network worms infect computers by exploiting vulnerabilities in software or by attempting to guess passwords to systems.
P2P worms rename themselves so they appear to be popular movies or software.
USB worms configure the infected drives to execute the worm as soon as an unsuspecting user plugs it into a computer.
The threat of worms can be mitigated by:
Using antivirus products to scan incoming emails and messages for malicious links.
Disabling autorun functionality for USB devices.
Apply patches for vulnerabilities in network services.
Disable access to P2P networks.
Educate users on the dangers of worms that use social engineering techniques.

4.1.2 - Viruses
A virus refers to a specific type of malware that spreads by infecting other files with its malicious payload.
A Trojan is a piece of malicious software that appears to be a legitimate application.
Viral code has three distinct parts; the discovery module, the replication module, and the payload.
The discovery module enables the virus to locate host files.
The replication module carries out the infection by copying the entire viral code into the host file.
The payload contains code to perform addition actions on the infected system aside from file discovery and replication.
Two types of viruses; resident and non-resident.
Non-resident viruses infect other files only when the infected file runs.
Resident viruses load themselves into memory and continue to run after the infected files close. Resident viruses also have two categories; fast and slow infectors.
Fast infectors infect many files very quickly. Lacks stealth, becomes obvious to the victim.
Slow infectors have specific criteria with which they infect other files. Can include time- and access-based criteria. Inconspicuous and harder to detect.
Cavity viruses; Write the virus code within empty or unused space within the file (without changing the file's size).
Antivirus products use specific pattern matches to detect discovery modules, replication modules, or the payload in files or executables.
Encrypted viruses start with a routine to decrypt the virus followed by the execution of the now decrypted virus.
A polymorphic virus has a polymorphic engine within its code that changes the encryption and decryption routines each time the virus infects another file.
Metamorphic viruses use an embedded engine to alter their code directly, resulting in a different binary composition of the virus between infected files.
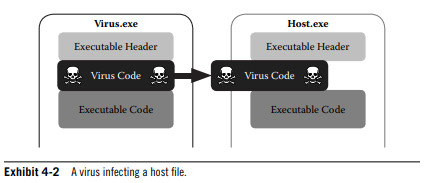
0 notes
Text
Something Awesome Sub-Chapter 3.2: Misdirection, Reconnaissance and Disruption Methods
3.2.1 - Cross-Site Scripting (XSS)
XSS refers to attacks that attempt to sidestep the same-origin policy by causing malicious script code to run within the context of the original site.
For an attack to occur, a website must accept input from an untrusted source and serve the submitted input on a Web page.
Attackers can steal information from a victim's browser related to the vulnerable page.
Type-1 attacks only alter the page once, when the victim visits the specially crafted URL.
Type-2 attacks make changes to the page content that are stored in a database, which then affects every subsequent user who visits the page.
The key to preventing XSS is treating all user input as suspicious and sanitizing it before returning it with other dynamic content.

3.2.2 - Social Engineering
Social engineering is the art and science of attacking the human element of a system to gain sensitive information or access to restricted areas or systems.
Trust can be built with a target with nonpublic information - anything the target believes the public in general does not know.
Eliciting empathy and appealing to the target's wants or needs are effective social engineering techniques.
No technology or simple solution can defend against social engineering attacks.
Alerting users or widespread attacks as they occur, and giving them regular instructions, will give them the tools to detect social engineering schemes before the schemes can do any harm.
3.2.3 - WarXing
War Dialling; The act of dialling numbers to discover listening modems.
War Driving; The act of mapping out the location of Wi-Fi networks. War drivers drive around with Wi-Fi-enabled laptops to record the location and name of each network they detect.
Information gathered during WarXing reconnaissance can support destructive and criminal activities.
War dialling may lead to attacks on systems connected to the phone system via modems.
War driving can allow an attacker to find open networks that they could use to launch criminal activity without being traced, or to sniff the traffic of the unencrypted network to steal personal information.
War spyers could use security cameras to scout a location before a physical break-in.
There is very little that an organization can do to keep war drivers from mapping their networks, but administrators should ensure that they properly secure any wireless devices.
3.2.4 - DNS Amplification Attacks
Utilizes the DNS (or misconfigures DNS servers) to launch DoS attacks while using minimal amounts of bandwidth on the part of the attacker.
DNS amplification attacks rely on the ability to spoof the originating IP address in UDP packet, thereby instructing a DNS server to reply to a specific address (reflection attack).
Reflection Attack; When the original packet sent over UDP reflects an intermediate system before striking the targeted system.
Smurf Attack; Initiator sends a ping to the IP broadcast address, falsifying the victim's IP address.
Open Resolvers; DNS servers that will perform recursive queries and return a larger amount of data than was in the original request.
DNS amplification attacks rely on two principals:
UDP packets can carry falsified IP addresses, allowing attacks to reflect traffic off DNS servers.
The cooperation of one or many DNS servers.
An ISP can inspect packets leaving their network to ensure that the source IP address could actually reside within that network, preventing a potential attack.
Administrators should configure servers to either not reply to requests for the root domain or limit the systems allowed to request this information to those on a trusted network.
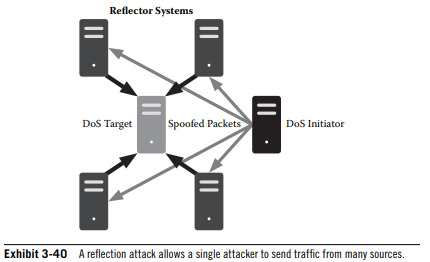
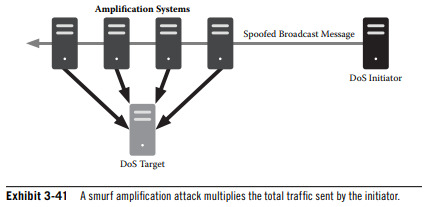
0 notes