Taking a look back in time at some of the most harmful programs designed for our devices and how they have developed in the future.
Don't wanna be here? Send us removal request.
Text
Types of Computer Viruses
Every Virus has what's called a "payload" that performs an action. The "threat actor" (virus coder) can code any malicious activity into the virus payload. This can range from harmless pranks that cause no harm to those that cause damage to the target's system and data. Generally there are 9 main types of viruses in existence:
Boot Sector Virus

Your computer has a sector that is solely responsible for pointing to the operating system and telling it to "boot" (start) into the users interface. A boot sector virus damages or controls that sector on the drive rendering the machine unusable. These are usually spread through USBs.
Web Scripting Virus:
These viruses have the ability to breach web browser security to take over said web browser. Older, unsupported browsers have vulnerabilities that will allow hackers to run code to hijack the browser.

Resident Virus
Has the ability to sit dormant until a payload is delivered. These might stay dormant until a specific time, date or a user performs an action. Can also be referred to as a Trojan horse.

Direct Action Virus
A user activates a seemingly harmless file attached with malicious code and the file delivers a payload immediately. It can also remain dormant until a specific action is taken or a time frame passes.

Polymorphic Virus
Malware authors can use polymorphic code to change the program's footprint making it difficult for an anti virus program to find it.

File infector
To persist on a system, a threat actor uses a file infector to inject malicious code into critical files that run the operating system or important programs. The virus is activated once the user boots the system or it runs on it's own.

Multipartite Virus
These viruses spread across a network or other systems by copying themselves or injecting code into critical computer resources.

Macro Virus
Microsoft files can run macros that can be used to download additional malware or run malicious code. They deliver a payload when the file is opened and the macro runs.
3 notes
·
View notes
Text
Introduction
In the world of today, people everywhere rely heavily on the internet for work or an individual's daily routine. This is a known fact by everyone including computer programmers. One unfortunate aspect of the internet being so prevalent is that there are those who are dedicated to using computers to gain access to personal data, information and personal assets through the use of computer viruses.
Computer viruses have been an ongoing problem for several decades and have been responsible for destroying entire systems through their use. They can be described as a piece of malicious code that has been designed to replicate itself when introduced into any computing environment called the "host". This can be anything from a another computing program, the computers operating system partition, a document or a removable drive. They may be knowingly or unknowingly spread and once it has successfully infiltrated the system, it will attempt to replicate itself in a way that affects the current system's available space and performance.

While there are many viruses that mean no harm other than a slight inconvenience, many of them can be extremely destructive. They have the ability to infect other software on the "host" causing system disruptions, instability , unauthorized modifications or disability of core functions. Along with the ability to copy, delete and encrypt files, some will lay dormant and wait for the user to trigger it while others will activate immediately and commence destruction.
These programs have caused billions of dollars of damages and have had an effect on anyone from everyday PC users to major corporations around the world. As time goes one they have grown to be more advanced and destructive each year.

1 note
·
View note
Text
The Origin of the Computer Virus
At the time of it's creation, it was not referred to as a computer virus but a theoretical concept of a computer virus was presented by Hungarian scientist and mathematician John Von Neuman.

It was presented in a series of lectures titled "The Theory 8 Organization of Complicated Automata." These lectures were conducted at the University of Illinois in 1944 and published by the same university in 1966. The basis of his theory was that as computer programs become more intricate and are able to mirror the human nervous system, eventually it would make sense if it were able to self-replicate just like a biological virus and cause any number of threats to the host system.
First Computer Virus Ever Created In 1971, the first official computer virus was created by Bob Thomas from BBN Technologies. It was called the "creeper" named after a villain from the cartoon series Scooby-Doo.

It was initially an experimental program with malicious intent was ingrained in its code. When a computer was infected with the program, it would print this message on their machine:
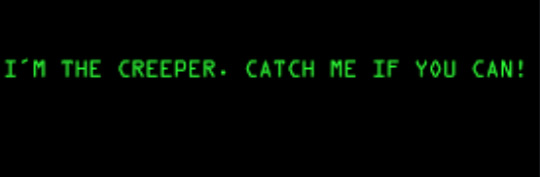
Then, it would move along in the network and find another computer to display the same message without damaging any files. That same year a colleague of Bob's would create a similar program called "Reaper". However, instead of displaying any messages it would look for copies of Creeper and and delete them. Regarding this program the first "anti-virus" solution.

The Rabbit Virus
In 1974, the "Rabbit" virus was created. Given this name because of speed at which it replicated itself. This was different from the previous virus mentioned because it was contained to one machine and created with malicious intent. It was created by a disgruntled employee and mainly intended to replicate itself until the system ultimately crashed.

"Animal" A Year later, the first "Trojan Horse" was developed. This is a type of malware that will disguise itself as a non-threatening program in order of not being detected and deleted by a user or anti-virus program. They cannot be replicated, but can attach itself to user program files or games that are exchanged then executed by end-user activity.

A computer programmer named John Walker created a program called "animal" which initially looked like a game that asked the user 20 questions to determine the animal they were thinking of. In the background, it was using a program called pervade which was a piece of code he programmed to copy this game into every single directory that user had access to.
Elk Cloner
In 1982, another virus emerged created by a 15-year-old high school student in Pittsburg, Pennsylvania named Rich Skrenta. This virus is considered to be one of the first viruses to leave the confines of where it was created and first ever personal computer (PC) viruses. It was transmitted through floppy disks and would copy itself to run in the memory of the computer it was installed in. It would also copy itself onto any floppy disk inserted into the PC. This viruses was initially intended to be a joke and was not programmed with any malicious intent, but was noted for how quickly it spread. The only notable thing it did was display a message when the system was booted for the 50th time:
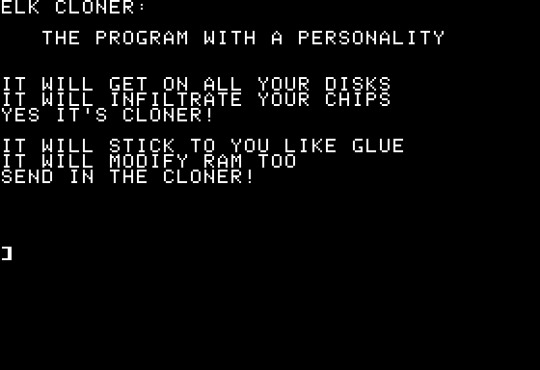
The "Brain" Virus
In 1986, there were two brothers based in Pakistan named Basit and Amjad Farooq.

They ran a computer store at that time and were growing frustrated at customers using pirated copies of their computer program. They created this virus to get back at those users. This was considered a boot sector virus which would alter the boot sector of any floppy disk used to copy their software. It was referred to the brain virus due to the name of the brother's company and the logo printed on their personal floppy disks. It is regarded as the first IBM PC virus. When users would try to boot their system they were presented with a message that read "welcome to the dungeon" along with binary editing code.
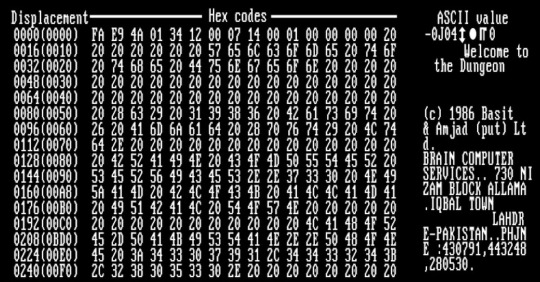
The brothers insisted that this virus was simply created to bring awareness to the user that they were using a pirated version of their program, however it was reported that some users experienced data loss and other issues. This was most likely caused by variants of the virus being spread. This is the virus that would go on to inspire the creation of the anti-virus software Mcafee since it caused the creator of the software to lose their personal work files.
12 notes
·
View notes
Text
Computer Viruses In the 90s
As technology continues to develop past the 80s era of technology, viruses began to advance at the same rate. now more than before they were able to spread themselves farther and faster using programs designed for the everyday computer such as E-mail or website links. There were 2 main viruses that emerged in those years causing world wide panic and destruction.

The "Melissa" Virus
This was a macro virus that began to spread on March 26th 1999. This was the first virus that used E-mail to spread itself to other users. At the time, it was one of the fastest spreading viruses of all time.

A message was sent by the virus from the email account of the person infected (or someone who had the recipient's email) with the subject "important message from <username> with a malicious Microsoft word attachment.
It was designed to send a malicious email to the first 50 addresses in each of the address books of each user that received it but only would be installed if that user has outlook installed on their computer. once sent it would scan the list of the next recipient of the virus and send itself to the first 50 people on that person's address book and so on. Once activated, the virus would modify the document by displaying comments from the TV show "The Simpsons" and would inadvertently send confidential information located on the computer to subsequent potential victims.

In the US, it is Estimated that this virus caused losses of more than $80 million and cause the creator of the program to receive a prison sentence of 20 months and a $5000 fine.
The Michelangelo Virus

First discovered in 1991 in New Zealand and considered to be one of the greatest sources of hysteria in the history of viruses. Despite having a malicious payload, it did a small amount of damage. What the payload was programmed to do was overwrite all data on the hard drive with random characters making recovery of any data unlikely if not impossible. However, this virus was only programmed to work if the computer was booted on March 6th (Michelangelo's birthday).
*Ironically, one of the vendors that sold the software with the virus was called Da Vinci systems*
Despite the panic surrounding this virus from major news outlets, the damage was minimal and was mostly only found accidently installed on vendor software disks and in an incident where a company names leading edge shipped 6,000 PCs with the virus installed in January 1992.
This was the 1st virus to receive the media attention it did at the time.
0 notes
Text
Y2K Bug: The Virus that Never Existed
Y2K is the shorthanded term for the year 2000. It was used to refer to a widespread computer programming shortcut that expected to cause extensive havoc as the year changed from 1999 to 200. At the time, many computers only allowed two digits for the year instead of four (ex: 99 instead of 1999). This lead to the widespread belief that computers would be unable to operate at the turn of the millennium when it changed from 99 to 00. It was expected to bring down the computer system's infrastructure such as those for bank systems and powerplants. It was also expected to wreak havoc on airline reservations and systems. Millions of dollars were spent in the lead up to the year 2000 in IT and software development to create patches and workarounds to squash the bug.
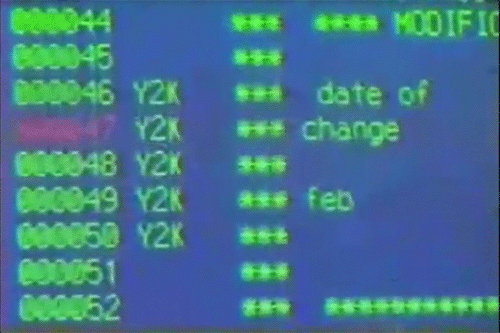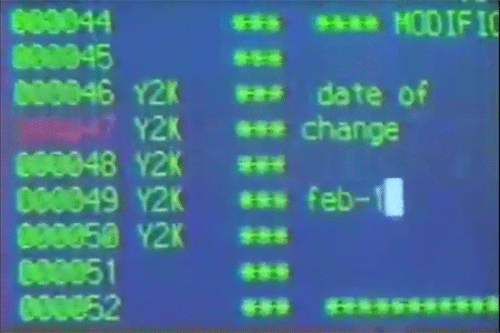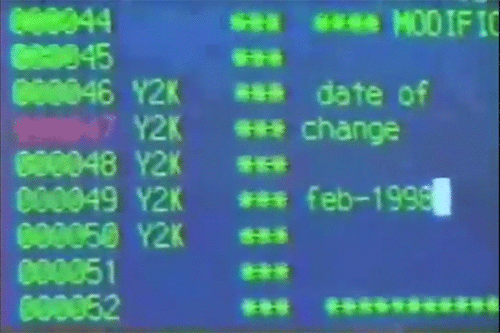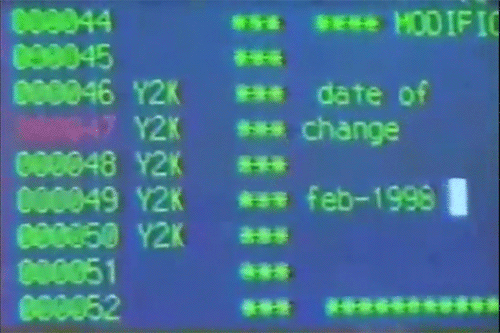
However, while there were a few minor issues once the year 2000 arrived there were no massive malfunctions. Some say because of the efforts major corporations put in to combat the effects of the bug, and others say it's because it posed no major threat in the first place the damage it could've cause was completely overstated.

0 notes
Text
Viruses in the 2000s
These times were considered some of the most destructive years for computer viruses ever. With the introduction of new operating systems such as Windows 2000 and Windows XP and computers for personal use becoming more commonplace, hackers were able to gain access to personal devices faster and more easily.

Year 2000 - ILOVEYOU Bug
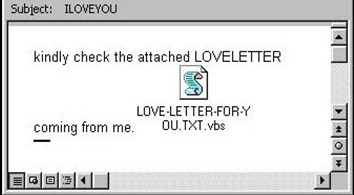
This is sometimes referred to as the love bug or love letter for you virus. This virus was created by 2 men located in the Philippines named Onel Guzman and Reonel Ramones. It was initially intended to steal the passwords of the person they sent the virus to because at the time they was struggling for money and wanted to gain access to the internet without having to pay for it. However, this virus managed to spread through multiple email addresses and eventually became a worldwide issue. It was able to infect over ten million windows PCs on and after May 5th 2000.
It would present itself in the form of an email sent by a user's contacts with the subject line "ILOVEYOU" attached with a .vbs file.
Once it was opened the following tasks were performed:
Made multiple copies of itself and overwrite personal files Made changes to the user's registry key Send itself to everyone in that user's contact list Downloaded a file call "WIN-BUGFIX.exe" designed to steal passwords
The destruction it cause was attributed to the it's design, since it was a visual basic script it was easy for a user to access the source code and have the virus do whatever they wanted it to do. It was said that it caused US$5.5 - $8.7 billion in damages worldwide and estimated to cost US$10-15 billion to remove the worm. within 10 days, over 50 million infections had been reported.
The two creators eventually were the targets of a criminal investigation by agents of the Philippines (NBI) due to the number of reports made to Sky Internet provider from European computer users alleging it was sent to them.
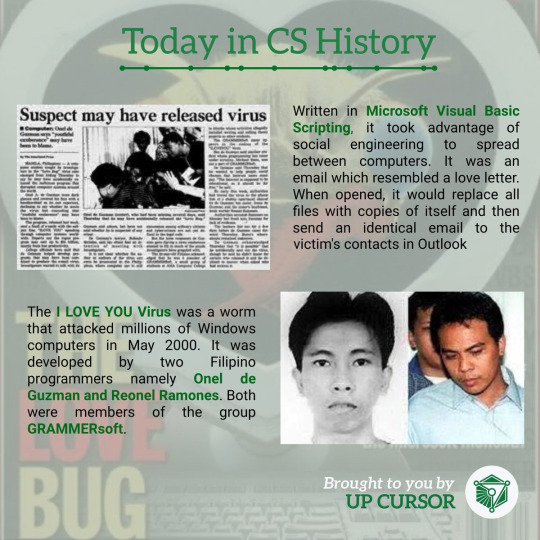
The creators were later arrested and placed under investigating but because there were no laws against writing malware in the Philippines at the time, both of the creators were released with all charges dropped. To this day, the creator states that they never intended for the virus to spread as far as it did and was shocked to find out how much damaged was caused.
Notable Virus from this Time Period:
Blaster Worm
Hackers exploited a vulnerability in windows software and had the virus spread itself without the end user having to open any attachment
Would turn a user's computer in a "zombie" and render it unusable while recruiting other computers for self-propagation
- Able to launch DDos attacks against the microsoft corporation's own websites.

Netsky:
Created in 2004 by Sven Johnson in June 2004
29 variants of the virus roamed the internet and was the source of many DDos attacks spread via email and copied itself onto the victim's local hard drive
at one time 25% of all viruses on the internet were all Netsky variants.
This lead to the creator being arrested but only received probation due to their age.
MyDoom:
Was considered a massive threat as the worm hit thousands of computers through what was called a "peer to peer" network where files were shared through one network to another.
Notable P2P sharing site example - Limewire
At the time, it was the fastest spreading email worm in history
Was thought to have disappeared but reappeared in 2009 targeting countries like South Korea and the US.
Sasser:
Created by the creator of the Netsky virus
Did not require email to spread, simply placed itself on an infected machine and started looking for vulnerable systems. Once found, it would contact those systems and tell them to download the virus.
Conficker:
Derived from the words "configuration" and "ficker"
Exploited vulnerabilities in windows and used the standard dictionary to crack administrator passwords
Over 200 countries were affected and it affected everyone from average users to major corporations and government organizations
Attacked the ministry of defense in the UK
Each variant is named after a letter (Conficker A,B,C,D and E)

3 notes
·
View notes
Text
2010s to Now
As of the present day, this is officially the time period where viruses are their most advanced. In this time period, this is the most dependent we have ever been on technology not only for ourselves but most public services completely digital.

Biggest Threat We Face - Ransomware
The biggest threat we face in cyber security is ransomware. This time, viruses have the ability to significantly affect whole societies and economies with the attacks being unrelenting.
Even though it seems like a new concept, the idea of taking users files and holding them hostage is not new. For example there was a virus circulating in the 1980s called the "AIDS" trojan. which had victims send $189 to a PO box in Panama to restore access.
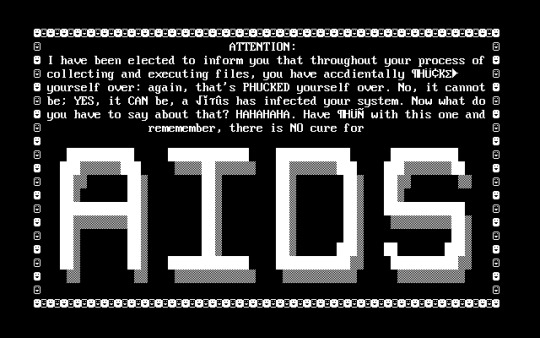
However, we would not see them be wide spread until way into the 2000s. The emergence of bitcoin changed that and now hackers had a easy untraceable method to receive their payment.
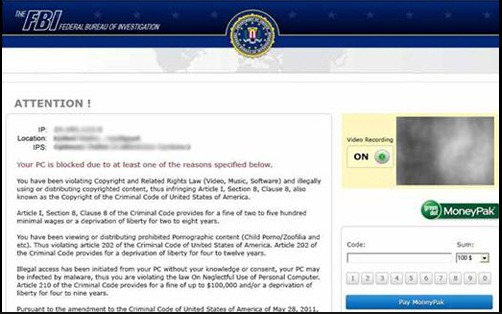
This resulted in ransomware being more and more prevalent in the beginning 2012. An example would be the FBI Moneypak virus. In which the virus would hijack a users device and display a message saying they were involved in illegal activity and the FBI had locked their computer until they pay the ransom listed on the screen.
Cryptolocker
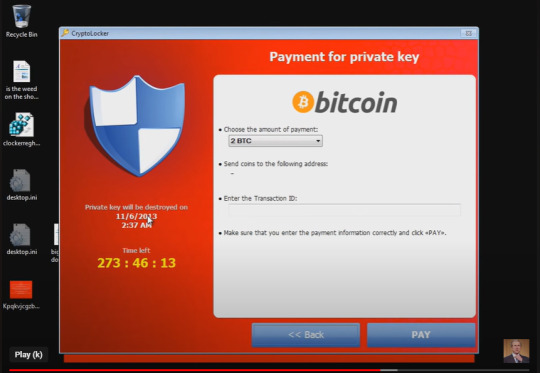
This was considered a revolutionary breed of ransomware at the time of its creation. It not only harnessed the power of Bitcoin transactions, but combined it with more advanced forms of encryption. How it would work is that once it reached a device through a link or through email attachment, it would immediately encrypt a users files to a point were they were rendered essentially useless. once every file on the system was encrypted, it would display a message saying the files were encrypted and the only way to get their files back was to pay the fine.
The encryption was so intricate that it made it virtually impossible to decrypt a user's files without paying the fine.
While this was a big threat at the time, the creators of this virus were arrested by the FBI and the the GameoverZeus botnet distributing the virus was shutdown making this program obsolete.
Unfortunately that did not stop the problem seeing that researchers were able to find copious amounts of Cryptolocker clones in the wild run by various cyber criminals.
WannaCry
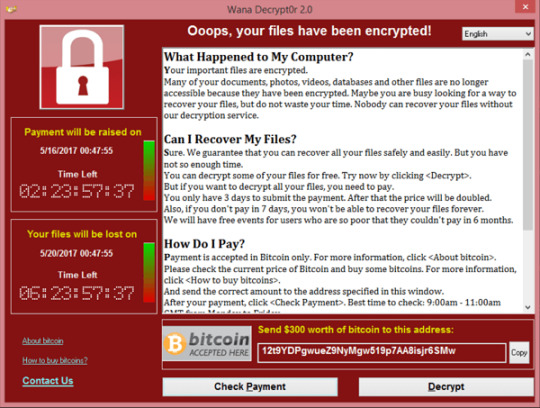
The biggest threat after the Cryptolocker outbreak was the Wannacry virus. It operated in the same manner that Cryptolocker functioned, but was able to infect more than 200,000 machines and did significantly more damage than the previous program. It is estimated to have hit over 150 countries and caused up to US$4 billion in damages.
The Future of Ransomware
The technology used to create these programs have advanced rapidly in terms of capabilities and sophistication. We can expect to see more attacks as stated at rapid rates and demanding larger amounts in extortion money.

It is also believed that hackers will continue to refine their data leek extortion ransomware tactics, develop tooling that can be deployed widely and and automate data exfiltration by searching for, identifying and exfiltrating sensitive data by using keywords. As it stand we can stand to see a lot more attacks like these in the future.
0 notes
Text
Sources
Crowdstrike. (2022, October 10). HISTORY OF RANSOMWARE. Retrieved from Crowdstrike: https://www.crowdstrike.com/cybersecurity-101/ransomware/history-of-ransomware/
Griffin, L. (2022, March 14). The History of Computer Viruses. Retrieved from Study.com: https://study.com/academy/lesson/the-history-of-computer-viruses.html
HALTON, C. (2021, September 13). The Truth About Y2K: What Did and Didn't Happen in the Year 2000. Retrieved from Investopedia.com: https://www.investopedia.com/terms/y/y2k.asp
https://www.youtube.com/watch?v=q6t9aNRQBG0&ab_channel=TheTWSChannel, Y. V.-L. (Director). (2022). TechHistory: Origins of the Computer Virus (Documentary) [Motion Picture].
KumarPatel, N. (2020, November 25). Web Scripting and its Types. Retrieved from GeeksforGeeks.com: https://www.geeksforgeeks.org/web-scripting-and-its-types/
Techopedia. (2011, September 6). Blaster Worm. Retrieved from Techopedia.com: https://www.techopedia.com/definition/27295/blaster-worm
Wikipedia. (2022, November 6). Timeline of computer viruses and worms. Retrieved from Wikipedia.com: https://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms#2000s
0 notes