Don't wanna be here? Send us removal request.
Text
Customer Success Story: The Little Potato Company
Customer Success Story: The Little Potato Company
What does advanced threat protection and identity management look like in action? Read this customer success story to find out how a family-owned agriculture company uses Microsoft cloud technologies like Azure and Microsoft 365 to apply strict identity and access management controls with advanced threat protection products to revitalize their business. Read More…
View On WordPress
0 notes
Text
Zero Trust Explained
Implementing Zero Trust can reduce risk, build trust and improve protection across the board with Microsoft 365. Today’s enterprise customers need a better security model that adapts to security threats and provides a secure place to store data with Microsoft 365. Watch this video to get an overview of Zero Trust.
youtube
View On WordPress
0 notes
Text
Fortify Your Data Against Threats
Fortify Your Data Against Threats
Unmatched volumes of data inform Microsoft security solutions. Check out this infographic to see how Microsoft helps prevent security risks and protect corporate data regardless of volume. View: Fortify Your Data Against Threats

View On WordPress
0 notes
Text
Want better security with enhanced access control? Monitor apps and services, protect data and control access to resources with @msftsecurity solutions from TEK Virtuoso.
Want better security with enhanced access control? Monitor apps and services, protect data and control access to resources with @msftsecurity solutions from TEK Virtuoso.
Want better security with enhanced access control? Monitor apps and services, protect data and control access to resources with @msftsecurity solutions from TEK Virtuoso.
View On WordPress
0 notes
Text
3 Key Resources to Accelerate Your Passwordless Journey
3 Key Resources to Accelerate Your Passwordless Journey
Every organization faces password-related challenges. Phishing campaigns, productivity loss, and password management costs can quickly balloon before you know it. The risks outweigh the benefits when it comes to passwords. Even the strongest passwords are vulnerable to attacks. It’s time to look at password alternatives that are convenient and secure. This blog provides a few simple steps for…

View On WordPress
0 notes
Text
Introducing Password Removal for Microsoft Accounts
Introducing Password Removal for Microsoft Accounts
Common cyberattacks like phishing, password spray and credential stuffing all rely on passwords. Deleting a password from a Microsoft account can prevent these kinds of attacks. Read this blog post to see how you can protect enterprise resources by removing passwords on a Microsoft account in a few simple steps. Read More…
View On WordPress
0 notes
Text
The Passwordless Future is Here for Your Microsoft Account
The Passwordless Future is Here for Your Microsoft Account
Nobody likes passwords. In addition to being inconvenient, they’re prime targets for attack. Yet for years, they’ve been the most important layer of security in our digital world. What’s the alternative? Thanks to Microsoft, it’s a passwordless future and it’s here! Right now, your employees can remove passwords from Microsoft accounts and reap the benefits of Microsoft Security. This blog…

View On WordPress
0 notes
Text
Break Free from your Password - We Try and Always Seem to Get it Wrong
Break Free from your Password – We Try and Always Seem to Get it Wrong
Who doesn’t want less complication in life? With your Microsoft account, your employees can break free from passwords and better protect accounts from being hacked. Watch this short video to learn how to go passwordless in Microsoft accounts.
youtube
View On WordPress
0 notes
Text
How Cyberattacks are Changing According to the New Microsoft Digital Defense Report
How Cyberattacks are Changing According to the New Microsoft Digital Defense Report
Trends make it clear: Cybercrime is becoming more sophisticated, widespread and relentless. This article takes a deep dive into evolving trends in cybercrime including human-operated ransomware, phishing attacks and malware. Read the article for tips on how to get ahead of these threats before they begin. Read More…

View On WordPress
0 notes
Text
Ransomware by Industry
The more you know about your vulnerability to ransomware, the more prepared you’ll be to mitigate or even prevent attacks. This infographic from the Microsoft Detection and Response Team (DART) gives an at-a-glance of ransomware attacks by industry. View the infographic for a reality check on your own knowledge of ransomware trends.
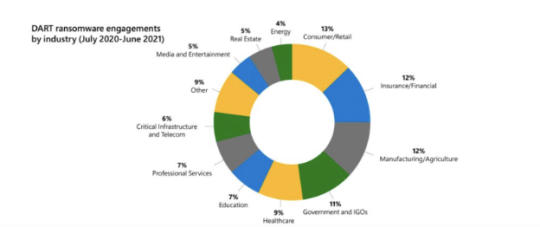
View On WordPress
0 notes
Text
Hacker Hunting and Built-in Protections with Microsoft Azure
Hacker Hunting and Built-in Protections with Microsoft Azure
Microsoft Azure automatically uncovers attack vectors that can lead to broader exploits, offering full protection from any attack on your system. Watch this video showing how Microsoft Azure can detect and stop attacks on your IT infrastructure on demand.
youtube
View On WordPress
0 notes
Text
Ransomware by Industry Image
Ransomware by Industry Image
What 3 industries are hit hardest by ransomware? Take a guess and check back next week for insight. 💡 Like this post if you’d like help assessing your cloud needs and how @Microsoft #Azure can address them with a TEK Virtuoso expert.
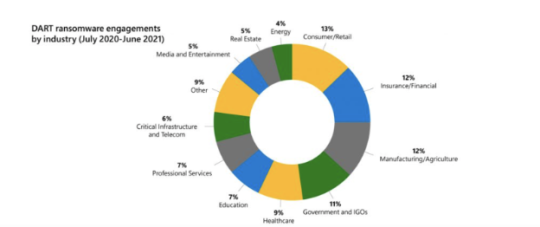
View On WordPress
0 notes
Text
Building the world's computer with Microsoft Datacenters
Building the world’s computer with Microsoft Datacenters
Microsoft Datacenters serve over a billion customers and twenty organizations worldwide, accounting for one of the largest cloud computing structures in the world. Listen to Microsoft experts as they talk about scale, security, innovation and sustainability and how they used it to build a trusted cloud platform for customers.
youtube
View On WordPress
0 notes
Text
Inside a Microsoft Datacenter
Inside a Microsoft Datacenter
In a world that runs on data and cloud, a Microsoft datacenter is more than just a place to store data. Amid the changing nature of work, education and innovation, datacenters are a crucial component of infrastructure. This infographic provides an at-a-glance of the Microsoft datacenter. View it to get a snapshot of how Microsoft datacenters deliver worldwide physical and digital security,…

View On WordPress
0 notes
Text
Beware of malware
Beware of malware. Here are some DIY tricks to evade cyber-attacks.#FTCguides #BeCyberSmart #CyberSafetyhttps://www.consumer.ftc.gov/articles/how-recognize-remove-and-avoid-malware
View On WordPress
0 notes
Text
Beware of malware
Beware of malware. Here are some DIY tricks to evade cyber-attacks.#FTCguides #BeCyberSmart #CyberSafetyhttps://www.consumer.ftc.gov/articles/how-recognize-remove-and-avoid-malware
View On WordPress
0 notes
Text
Transition to Cloud: A journey to Modern Work with Microsoft 365
Transition to Cloud: A journey to Modern Work with Microsoft 365
The digital transformation of the business world has pushed businesses to address new challenges: remote work, cloud migration, and device security is the new normal. Today’s decision makers need to create people connections, address burnout, and work toward consolidating apps. With Microsoft 365, you get a platform boosted with industry-leading apps, intelligent cloud services, and world-class…

View On WordPress
0 notes