call me Magpie or Mags. 20 something. chronic bastard and terminal gremlin. If you ask me my name, pronouns, or anything else related to who I am as a person I will just stare at you blankly and maybe scream. humans are weird and gross and I don't like being one. ⚠️ I like some things that the general public may consider "disturbing" or "unsavory" so peruse at your own risk. ⚠️ currently mobile only
Don't wanna be here? Send us removal request.
Text
“What is a personal website even FOR?“
When making a personal website for the first time, you may ask yourself this!
The answer is: fucking anything. Personal websites don’t have to be “presentable” if they’re not tied to your IRL identity or whatever. Look at old captures of geocities, tripod, angelfire sites. You had dedicated single-topic sites, sure, but you also had sites that were arbitrary, slapdash little hoards of the website owner’s Favorite Things, no matter how unrelated they were.
Some suggestions:
links to your 3 favorite other websites.
an essay about how cool hydraulic engines are
a sanctuary for all your favorite images, such as memes, that you’ve collected over the years
facts about centipedes you think everyone should know
competitive hardcore sims 2 speedrunning strategies
a portfolio of your artwork, or links to other people’s artwork you enjoy
elaborate lies and hoaxes (maybe even a whole arg)
useful survival tips specific to where you come from (personal recipes, trustworthy doctors, good music venues, eats that are both good and affordable, hot goss on who’s up to what horseshit on your city council/school board/university faculty/whatever)
original fiction that noone on social media cares about because people only like and reblog about what they already know. explain your entire fictional country that you wanna put in a real novel one day.
making people not have to dig through your tags to know where to find all your dracula meta (including the shipping manifesto you wrote 10 years ago)
speaking of fandom, you know that one piece of media you love that nobody else seems to have heard of? you post into the void and nobody reblogs or likes? nothing in the tags? Yea. Built a shrine to that explaining why EVERYONE should care about it. tell me how that pirated copy of Telefang made you the human being you are today
explaining your personal philosophies on life without worrying that you will get reblogged by randos calling you cringe
just generally being fucking a weird, unrelatable, unmarketable, extremely specific ass human being
7K notes
·
View notes
Text
Otherhearted Ask Game
I've never seen an ask game for hearttypes specifically so I wanted to make one! I did my best! Be sure to specify which hearttype you want to know about if they have more than one!
1. What about you and your hearttype are similar?
2. What about you and your hearttype are different?
3. How did you discover (and confirm) your hearttype?
4. Any headcanons/theories about your hearttype?
5. Any habits you picked up from your hearttype, or any you had before you even knew about it?
6. Any hearttypes that developed from a different thing like a synpath or copinglink?
7. Anything you personally don't like about your hearttype? Could be personality, something that happened/happens to them, how they function, etc.
8. Are you a "deep longing to be", "deep admiration and empathy of", "ideal self", "should have been", and/or other experience 'hearted person?
9. Would you take your hearttype's physical body? Anything you'd change?
10. Do you experience shifts of your hearttypes?
11. Any hearttypes you're questioning at the moment?
12. Do you ever feel desires/urges or emotions that are due to or influenced by your hearttype?
13. What was the hearttype that took you the longest to confirm?
14. What's a song that reminds you of your hearttype?
181 notes
·
View notes
Audio
I really dislike Kawaii Future Bass or whatever this genre is called so I made it sound shitty with a bunch of random samples.
151K notes
·
View notes
Text
You are a long forgotten god. A small girl leaves a piece of candy at your shrine, and you awaken. Now, you must do everything to protect your High Priestess, the girl, and her entire kindergarten class, your worshipers.
69K notes
·
View notes
Text
just learned that magnolias are so old that they’re pollinated by beetles because they existed before bees
392K notes
·
View notes
Text





Recipes from Portland's famous but long-closed Rheinlander restaurant. This cookbook was produced in a limited window before Chef Mager's death. All of these fucking slap.
16K notes
·
View notes
Text
when the capitalists die out either thru global warming or revolution will we be able to start homegrown internet
116K notes
·
View notes
Text
Never ever turn off your phone: rethinking security culture in the era of big data analysis.
Back in the 80′s if you were a pissed off anarchist that wanted to burn down a building, you probably checked your home for listening devices and made a plan. If you were the same kind of pissed off anarchist in the late 90′s, you turned off your phone and encrypted your online traffic. In the 2020′s we’re gonna have to change our strategies once again. Intelligence gathering has adapted and so we must adapt too.
To get a head start at this, let’s look at how big data analysis is being used. To do this, we’ll need to talk about 3 things: metadata, patterns and networks. Those sound boring and complicated but I’m not a techy and I won’t bore you with tech language, I’ll keep it as easy as I can.
Metadata: In the context of online activity, ‘content’ means ‘the message you send’ and ‘metadata’ means ‘everything other than the content’. So, for example, if you send your friend a text about lunch, the content might be “Let’s go out for lunch” and the metadata might be “Message send at 01/04/2018 11.32 from phone 0478239055 to phone 079726823 using Signal”.
This information is registered by your phone even if the app encrypts your actual message. Your metadata is very badly protected by technology and very badly protected by the law. No matter which country you are in, most of your metadata if freely available to intelligence agencies regardless of whether you are a suspect in anything.
Patterns: Whether you realize it or not, your metadata has a pattern. If you have a daily job you might have a very consistent pattern, if you do not your pattern might be more flexible but you have a pattern. If someone wanted to know the rhythm of your day, they could very easily do so because your pattern is in the metadata.
For example: Maybe you use the wifi at your favourite bar on most Sunday nights until about midnight, you wake up around 10 AM and check your Signal, you use your public transport card to get to class every Monday afternoon and you spend on average 1 hour on Tumblr twice a day. All this is part of your pattern.
Networks: You have online networks. Your facebook friends, the people in your phone adress book, the dropbox you share with coworkers, everyone who bought online tickets to the same punk band you attended, the people using the same wifi points as you. Take your networks, combine them with other people’s networks, and clusters reveal themselves. Your work community, your family, your activist scene, etc.
If you are in an anarchist community that will probably be abundantly clear from all your minor network connections like going to the same band and knowing the same people as other anarchists. Even if you never liked an anarchist facebook page or pressed ‘going’ on an anarchist facebook event, your network is hard to hide.
Now, let’s say you commit a crime,
the kind that would result in some serious research. Let’s say that on Sunday night 3 AM, you are your friends go out and burn down a nazi’s house. It’s obvious that anarchists did it but there are no other clues. You use traditional style security culture: you burn your notes, you are careful not to communicate about your plans near technology and you do not leave physical traces.
But because you commited the crime that night, your metadata will vary strongly from your usual rhythm: you stay at your usual bar until 2 AM to wait for your friends, you do not wake up at 10 AM in the morning so you do not check your Signal or Tumblr until 1 PM. You do not go to class. Your metadata pattern is very different from your usual pattern. The metadata patterns of your friends are different too. If one of you is clumsy, they might generate a super suspicious metadata signal like a phone being switched off at 2.30 AM and activated at 4AM. You wouldn’t be the first.
If I wanted to solve this crime using data analysis, what I would do is:
let a piece of software run a pattern analysis of the local anarchist scene to generate the 300 people most connected to the anarchist scene.
let a second piece of software analyse the metadata patterns of those 300 people over the last months and identify the biggest metadata variations around Sunday night as well as very suspicious metadata activity
Illiminate pattern variations with an obvious cause or an obvious alibi (people who are on vacation, people who are in the hospital, people who lost their job, etc).
Do indepth research into the ones that remain.
Which is how, out of a massive amount of people that I couldn’t possible all listen to at the same time, I could quickly identify a few to monitor closely. This is how I could find and catch you.
So, now what?
If traditional security culture doesn’t protect us as well as it used to, how do we adapt? Well, I don’t have all the answers but for a start, I’d say: know your network + know your pattern.
In the case of the crime above: leave the bar at midnight, return home and put your phone on your bedside table. Check the apps you check before going to bed and set your alarm to 10AM. Return to the bar without your phone. Commit the crime. Wake up at 10AM and check your Signal. Drag yourself to class or ask a comrade to make the trip with your travel card and do not use technology in your home while the comrade is taking your travel card to class. Stick to your pattern. Never ever turn off your phone.
You might also be able to manipulate your network but that seems much harder to do. Not having a smartphone and dropping out of all social activity online is a big commitment. Knowing your data pattern and making sure your data pattern doesn’t look out of the ordinary? Much less commitment.
Some of the old rules will still apply: don’t talk about a crime around devices with microphones, don’t brag after a succesful action, etc. Other rules, like ‘turn off your phone when planning an illegal act’ need to change because their metada looks too out of the ordinary. No one switches off their phone anymore. We look suspicious as fuck when we do.
This is just one idea on how we could update our security culture. There are probably other people with other, better ideas about updating our security culture. If we start the conversation, we may get somewhere.
Finally: we need to keep adapting.
As technology changes, more information is becoming available, including data we have very little control over. Smart-tv’s and ads in public spaces that listen to every word we say and the tone of our voice when we say it are examples. Data analysis projects are currently using license plate reading software on security footage to map the travel patterns of cars. A lot suggests they may soon be ready to do the same with face recognition, at which point the presence of our face in public space becomes part of our metadata. More information means more accurate data analysis. Our metadata may soon be too vast annd too complex to completely map and mirror. Which means we will need to adapt our counter measures if you want to hide something.
How do we keep it all under the radar? I don’t know. But let’s try to figure this shit out. These are some first thoughts about what security culture should look like in the age of modern big data analysis and I’d be very happy for any insights from comrades that have some thoughts on this.
Also: feel free to distribute and rework these words without credit.
29K notes
·
View notes
Text
So, Microsoft is terrible. Yes yes, the oldest claim in the world.
But specifically… I just hate how Windows 10 tries to conflate and confuse web searches with things on one’s own computer. The start menu should never do anything related to web-searching, especially if it purports to try to give examples of things that are on my hard drive!
This will make old, computer-illiterate people more malware-vulnerable. You have to maintain a strong distinction between “things that are on this computer (and maybe even included in Windows)” (safe, one hopes, or you already got pwned by it, probably), and “things on the web” (scary, dangerous, not to be trusted at all).
Eroding that barrier in the UI is awful. It just FEELS like a violation every time I start typing into the start bar, and it tries to show me ANYTHING web-related. My computer is NOT just an internet-portal! It has tons of stuff on it, and when I’m interacting with the OS, I ONLY want to see things that are already on here!
If I wanted to see something online, I would go to my browser! All the online stuff should be segregated into the browser!
Specific programs can access the internet; that’s fine. But my OS’s functions and interface should JUST be about the things that are already on my computer.
133K notes
·
View notes
Text
I said it in the notes on the last post but I’m gonna say it again.
I’m married to someone with severe memory problems. Automation of household appliances & systems helps him a lot and helps me a lot because it reduces the number of things I have to keep in my brain at all times. I love doors that lock themselves, being able to schedule dog food being delivered, a thermostat I can manipulate from wherever. Beyond my little bubble it should be noted that voice controlled appliances can be really good for people with mobility concerns. Appliances that can measure and talk and remember little tasks can be such a blessing for people.
I will never forgive Amazon and Google for taking technologies that could be really helpful and weaponizing them, and fuck everybody who acts like its some kind of conspiracy theory that those devices are spying on you. You absolutely should be distrustful of those devices but just make sure you’re getting angry at the right people.
118K notes
·
View notes
Text
Concept: an apocalyptic or post apocalyptic tv show centred on a group of disabled protagonists
Must include:
-enough details about how they survive that no one can call it “unrealistic”
-mental and physical disabilities
-a character who isn’t necessarily contributing to the survival of the group, but is not abandoned or looked down upon
-at least one character whose disability is actually less of a problem for them now that the world is ending/ended (example: autistic character who used to be constantly overstimulated but no longer is)
Optional features:
-abled person says “the only disability in life is a bad attitude” and gets told where to stuff it
-creatively weaponized mobility aids/assistive devices
-character who abled people think isn’t worth helping because of their disability, but actually has at least one skill essential to the survival of the group
-every time an abled person says something ignorant, all present disabled people look into the camera like they’re on the office
98K notes
·
View notes
Text
nintendo is taking down the 3ds and wii u eshops next year
and they had this lovingly made totally not taunting message to leave about their virtual console legacy they’re destroying
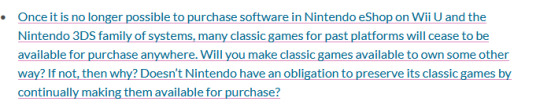

(that they’ve, fun fact, taken down from their site now :])
86K notes
·
View notes
Text
i went to the dentist today and my dentist honest to god said “can i ask you a question…….what the hell is in your mouth”
301K notes
·
View notes
Text
not going to delete this blog but I remade cause I can't figure out my login info for this one and I want to log in to my new blog on my phone but since this is the last place I'm logged in here then that'll be it.
New blg is run a bit different, we each have our own side blogs n the main that follows n likes is mostly empty. for now the icon is the same as this one so if you see that in your notes that's me.
I'm gonna q a bunch of my drafts n some of my likes here and then that will be it for this blog.
1 note
·
View note
Text
btw you can use whatever gender seasonings you want. paint your nails, wear breast forms, wear a binder, pack, tuck, dress however you want, whatever. you are adding ingredients to your gender soup.
70K notes
·
View notes