Text
Security Everywhere: Equifax’s Data Breach
Privacy is such a important part and if that get lost from an important client, then this would be the example that will happen to them. I think everyone heard of a massive data breach from Equifax, one of the world number one credit reporting companies. It has affected for almost 145.5 million US consumers and Equifax was planning to give them 2 years free support for those who are affected. But now with the latest news says, they have lost a court case and the final output is that, those who are affected with this issue will get either a cash of 125$ or a free 10 year service. You actually need to claim it before they chance it.

This shows how important is privacy as in modern world, many of us think like what gonna happen if my personal data is lost as I’m not that important person for an attacker. But once you are affected you will find how important it your data is.
Considering the case of Equifax, they have lost the highly sensitive data which is definitely enough for an attacker to hack into someones system or to black mail them. The best example is to check my blog on what I did for something awesome with dumpster dive. I have got an abandoned laptop which is actually not working. But when I scanned the hard disk, I was able to trace his entire life from 2006 to 2014. You can read through my blog on below link:
SA_Dumpster Dive:- Introduction.
1 note
·
View note
Text
SA_Dumpster Dive:- Conclusion
Last blog, we have gone through the analysis from an attacker perspective part of this project. If you didn’t check that, please click on this link: SA_Dumpster Dive:- Analysis from an attacker perspective
Next lets go through the final conclusion part:
Please please, be careful in handling your personal data. Make sure that its been destroyed properly especially before throwing electronic devices, laptops, phones etc. Laptops, even it you found its not working, it may be the software or hardware issue. The important message you need to consider before throwing a laptop is to check whether the hard disk is working or not. Even if you found its not working, Please take time to destroy it by either crushing it or shredding it. Don't be lazy in protecting you privacy. It’s really important that matter’s you future. For laptops there are encryption, both for MAC and windows. Richard already shared as the windows encryption is not a safe way of encryption, but you should encrypt the hard drive. Because in case, if someone stealing your laptop, he won't be able to access the hard disk data, that easy.
Windows Bitlocker encryption:
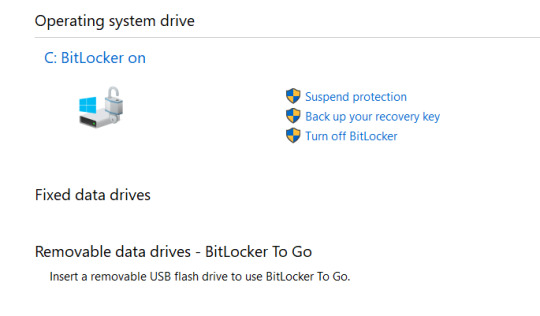
Without encryption it will be easy to check any hard disk as I did for windows laptop now and I have already shared a post with you on MAC. Without encryption, how easy to access someones data.
Mac FileVault encryption:
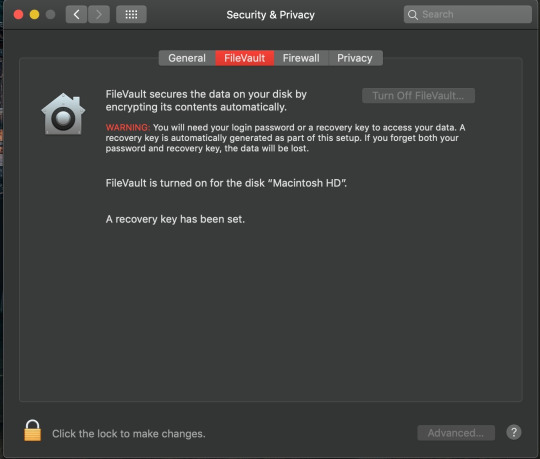
With this hard drive, I have collected screenshots of the folders, data files, without opening any of the data. This is for proof sharing with the tutor for the something awesome project and I will show the hard disk data to Richard after the next lecture on Tuesday. And I will later format the hard-drives and will do a deep formatting so that, even recovery software won't be able to recover the data.
Please keep in mind before selling you laptops, desktops, electronic devices etc, you should deep format it. There are many applications available that can do deep formatting. So that no one can access your personal data. You will feel like factory resetting will clear all your data. But it won't. You can recover the data back as I did before on my own laptop. I have completely erased the entire data in my laptop hard disk and before writing data, I have done a recovery on top of it. It was something terrific, as I was able to recover the entire OS, my personal data everything. Please keep in mind.
NONE OF YOU DATA IS GETTING DELETED. IT IS JUST MARKED AS DELETED AND YOU CAN RECOVER THE DATA EASILY.
1 note
·
View note
Text
SA_Dumpster Dive:- Analysis from an attacker perspective
Last blog, we have gone through the information gathering part of this project. If you didn’t check that, please click on this link: SA_Dumpster Dive:- Information Gathering
Next lets go through the Analysis from a attacker perspective:
The data which I collected from the hard disk is more than enough to make an easy attack. But as I mentioned previously, These activity is done under supervision and won't do any harm to anyone.

These are the main threats, that can happen with these data:
Since it contains his personal data, It will be easy to track his most recent activities even with the government documents, passports etc.
Its easy to do blackmailing as this personal documents, company projects documents, personal photos of his family etc
He even can loose his job, by reporting this to his company, as there are important project documents, client mails etc.
Also its easy to track his work details and do a social engineering attack on his business, work place.
We can do social engineering attacks based on this data, to his bank account, landlord etc
Also I was able to track through their daily meals as shopping invoices, list was found
So basically, its easy to do these kind of evil activities on his life and ruin an innocent persons. I know I'm handling a big piece of information andI have secured the laptop and data. Also I have discussed with the tutor on how to handle with the data in hard disk. I have agreed to format all the hard-drive data with any good applications or filling the whole hard disk with some rubbish data so that it will be really hard to recover anything from this hard disk after formatting. Currently I'm the only one have accessed the data and no one else can check into it. And I will be talking to Richard on Tuesday after the lecture on destroying this data.
Lets go to the final stage: The conclusion.
1 note
·
View note
Text
SA_Dumpster Dive:- Information Gathering
Last blog, we have gone through the introduction part of this project. If you didn’t check that, please click on this link: SA_Dumpster Dive:- Introduction.
Next lets go through the information gathering:

This Activity can be tracked as illegal and if I'm violating something, then it would be really bad in my career. I has discussed with my COMP6441 tutor Adam Smallhorn in how I should proceed with this activity and what all stuffs I need to note down and need to take care in doing this, because it was another person's laptop found as a abandoned or thrown away device, It is so exciting to do these kind of digging as we are finding something really awesome. The next thing that need to be done is to mount this hard drive into a PC. Since for my laptop, as part of upgrading, I have removed the DVD drive and mounted an extra(secondary) hard drive. The best part of this is that, I can mount and remove this secondary hard drive by just unscrewing 1 screw and need to pull it out. So this made it more easy to do this activity.


I'm using a licensed version of antivirus, windows and I'm extra confident as since it's an old hard disk, if there is any virus, that would be an old one which should be already there in antivirus library. So with this confidence, I have mounted the hard drive which I got from the abandoned laptop. The next task is to load up the windows and need to do a complete antivirus scan on the hard drive. So I have started with that process and it took long hours as this is a 750gb 5400rpm Hitachi hard drive. It was so slow and the maximum read speed found was 80mb/s. During that time, I have done a serious research on what all task I can do as part of dumpster dive on this hard disk. We can go through anything interesting, such as files, folders, web browser data including history temp files, documents, passwords, downloads, application data etc. I have categorized everything for scanning through the hard disk.So the steps involved in this activity is:
Finding a laptop
Doing a through scan on the laptop, checking whether its working
Mounting the hard drive
Scanning through the hard drive, checking for any interesting data
Collecting all the relevant information
Deleting all the data and formatting the drive
The deep antivirus scan took almost 4 hours and lets start surfing through the hard drive.
OMG!!!!!!!!!!!!!
750gb is almost full with the laptop owner’s personal data. The interesting thing is that, I was able to track his entire life, from 2006 to 2014. This includes:
Starting of his business
Real estate business in New Zealand. So much of business and land property documents. Address
Found to be a really rich guy from this apartment photos, car etc
He meet his life partner and planned to move to Sydney
Address where he stayed for the initial months
Plan for building a new house, Address. Photos of construction, site plan, house plan
Everything about his cute baby, photos starting from 4 months to 3 year old
Changed the apartment to new location, Address
His outlook mail details
Work place mails, project details, shared scripts, codes etc
Almost everything.....
OMG!!!!!!!!!!!!!!
Since its illegal to go through all these data and sharing in internet. So I'm not sharing any of the photo's or details, but for proof, I'm sharing the file explorer, folder details etc.
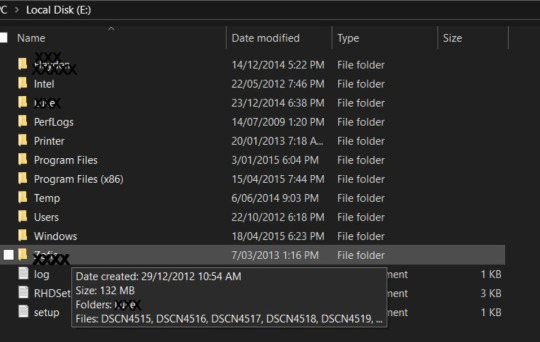

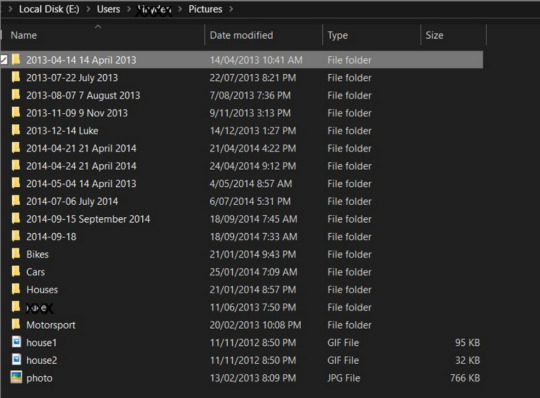

Important documents which I found from this hard disk includes:
Owner, wife, kid passport
House plan, photos, different stages of house construction
Insurance, invoices, Center link request papers
Business documents
Real estate land property documents
Office projects, scripts, codes
Account information, passwords, including his google password (Key for everything)
Personal Photos, Videos
Take a deep breath. This is what gonna happen if you abandoned you electronic device like this. Not yet done: Lets go to the next blog for the next part of the project: SA_Dumpster Dive: Analysis from a attacker perspective
1 note
·
View note
Text
SA_Dumpster Dive:- Introduction
Hi All,
I’m super excited to share with you about my Something Awesome Project which I did a dumpster dive for electronics devices along with my second something awesome project as research on cyber security certifications. You all will get excited after checking the data which I found from a laptop while doing dumpster dive.
I will post series of blogs on my something awesome project dumpster dive and lets dive:
If you haven’t checked my 1st blog on dumpster dive, please go to this link: SA: Dumpster Dive. Lets start with introduction to my project:

Dumpster Diving Research: Introduction As part of extending my something awesome project, I did something really awesome. Guess what, after my second lecture in COMP6441, Richard gave us a theme in doing dumpster dive. The dumpster dive idea, he gave is to find something, without violating any ethics,which will crack in security. It can be a thrown away computer, may be an electronics device like google home or a letter that reveals someones privacy, anything than can trace something interesting in security. So on 4th week of Term 2, I went out for a dive and found a laptop on roadside, kept side to a full bin. Laptop seems to be okay, but when I checked it was not working. May be the owner through its completely gone as the laptop is not turning on. Then I did a complete scan on laptop, including the model number, spec and start digging more into the laptop. I have mounted the hard-drive on my laptop and done thorough scan. I was totally surprised with the data I found from the laptop hard drive.
Now lets check through the hard disk. But remember, before opening any files, it can be virus affected. Even an attacker can leave his laptop for catching someones else data. So to know what I did next is to: Lets go to my next blog for next step: Information Gathering
1 note
·
View note
Text
Week 8 Tutorial and Case Study
Case Study: Ghost
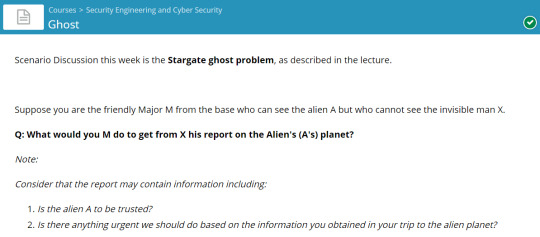
Q: What would you M do to get from X his report on the Alien's (A's) planet? Note: Consider that the report may contain information including: 1. Is the alien A to be trusted? 2. Is there anything urgent we should do based on the information you obtained in your trip to the alien planet?
For this case study, we have discussed a number of things, authentication methods on whether we should believe in alien, if so how we will authenticate whether we can trust alien or not
One of the method we discussed is the Order of the questions
If we are using some kind of authentication, alien can drag the invisible man to the location and torture him and will able to crack the cipher. So we can't trust the alien, whether he is saying the right words.
Even if after the authentication, alien can lie after that. So another method we through of that is, Alien to send the message to us and m will ask the alien some questions. if the authentication is able to pass, then its a success. Since he has already shared the message and if its not correct, then the invisible man can lie to alien and alien's life will be in trouble.
Get separate room, alien will be on one room and invisible man to another room with the M. President will write the question, for authentication, invisible man will go to the room and will say to the alien and the alien will share it with the president. So authentication will get the pass. You need to ask number of times and in between the conversations also, so that the validation is made each time and will be confirmed.
Example: is your name tim, if yes and X will go to that room and will tell alien. So Alien can't change it to no and the authentication will get the wrong.
But the doubts we got is, You can't see him,but whether we can hear him or he can do something like punching Alien or anything. Using the pre-shared the key. Aliens whether it can read the mind.
Using some sort of protocol, like to use the mos code. To authenticate the ghost. This is assumed like the alien and invisible man are in different dimension.
Also there is chance like Alien can scan the brain and can do any sort of authentication.
Using a bomb,need to get the correct code from invisible man, Alien need to share the correct message with the president or both the alien and invisible man will die.
Another method of authentication, which we have gone through is that, M will ask the Alien and Alien will get the replies from X, when the bomb will get explode. If it is the correct data shared, then say the city where we met. Say the fake city. Invisible man say the harbor bridge is having the key. Alien will pass it to the M.
After the case study we have discussed on the following topics as a revision:
PKI, X509
Diffie hellman key dogschange
One time pads -> Steam ciphers v block cipher
Block cipher
- DES, 3DES NSA tweaks
- AES
Cipher Block modes
-CTR
-CBC
-ECB
Difference between encryption and hashing
Knowledge based authentication
Block Cipher: AES, Blowfish, DES, 3DES, Cipher block chaining (CBC) One time pad: XOR the message with the random key
1 note
·
View note
Text
Week 8 Lecture: Errors
Human error mistakes accidents disasters:
If you know the mistakes, you won't repeat those mistakes.
Movie for the exam: The China Syndrome
Root cause analysis: 1. Using that error: Most cases it will be due to Human error and blaming others is the normal human tendency. Every cyber attacks happened because of human error. It won't be one human's mistake. Like in airplane industry, its not just one person's error. In early centuries the last person sign the inspection will have to face the consequences
2. Most sophisticated one is due to Culture. We don't have the right culture. Sor errors are happening due to bad culture. And it is difficult to change. We can correct with training. It is difficult to change Human weakness: Honesty.
Don't lie to others. Always tell the truth to every one, even to your kids.
As a security engineer, you need to go through the situation and need to find how to solve the situation with you experience
Frequency gambling: When you got a match, we try to recall what we did previously and will repeat the same. Brain will find the pattern and find the one which is picked most often. It is basically the pattern matching the problem. We do the pattern matching with what happened in the past.
Fix the human error with training, education and desiging the system
Good design, means less complex. When we break the program into components, we should be able to break the program into components without any issues. If its hard to add new module, its a bad design and if its easy on adding a new module with the existing code, its a good design.
Humans belief events has only significant cause. People belief that they have the ability to control outcomes. Hindsight bias: case study on new issues will be given more outcome causes, which was actually happened previously. Just giving higher values Defense in depth, Something goes wrong, something else will help to solve it Bopal issue, Human error, causing hundreds and thousands of people dead. Miss of culture and less concern on safety. No inspection.
Operator deskilling due to automatic safety devices. Less number of time, pilots are touching the controllers in a plane. Rest all its controlled by the machines. Need to research on the 3 accidents. examinable
Extended Notes:
Methods of prevention Incognito mode in browser: It won't do much, will delete the cookies. Using the browsers like DuckDuckGo will give you more safe privacy.
Don't signup using another account like the google account. Signup by giving lie’s, just lie to most of the questions Use the VPN Can't trust anybody. Even we can't trust the vpn. Like, nordpn.com Onion routing: diverting your request to different node. It will sent to number of intermediator nodes Facebook will also track you even after using Onion routing
Digital forensic: Need to take backup of the hard disk and need to analysis
Acyuistion/imaging: backing up of the hard disk Analysis: keyword search Types of forensics: Computer forensics: taking the flash of the ram will give the data it was using before Network forensics: router, switches, packet capture
Drive and partitioning (FAT32): Allocates memory in clustres The FAT record stores the status of each cluster
0 notes
Text
SA: Encryption Algorithms :- AES: Advanced Encryption Standard
Advanced Encryption Standard AES, is a Symmetric-key based algorithm, which means, it uses the same key for cryptocurrency and decryption. This encryption encryption was established by US NIST standard replacing the DES on Nov 2001. This is done by processing the data in 128 bit blocks using 128, 192, or 256 bit keys. The advantage of using AES is the better encryption and Brute force for decryption takes few secs on DES, but it takes 149 trillion years for AES. Universe lifetime: 100 billion years
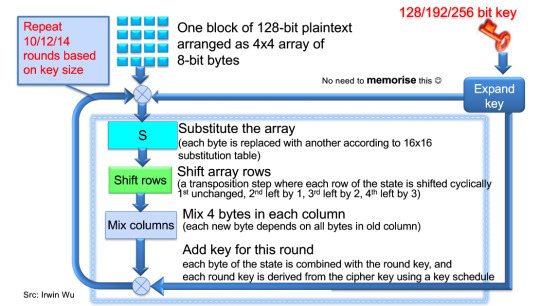
There are five confidentiality modes of operation for symmetric key block cipher algorithms:
Electronic Codebook (ECB), – This works by spiting the plaintext into blocks and encrypting each one separately using the block cipher
Cipher Block Chaining (CBC) mode:- In this, it splits plaintext into blocks and XOR each block with the result of encrypting previous blocks
Cipher Feedback (CFB), Output Feedback (OFB), and Counter (CTR) modes: stream ciphers based on block cipher
Source: Notes from Wireless security
0 notes
Text
SA: Cyber Security Certifications :- CAP (certified Authorization professional)

This is another certification program from (ISC)2. (ISC)2 professionals certifies that, they can help you to prepare for, prevent and recover from cyber attacks. Always human beings are the main assets. With the CAP certification, the CAP professionals are certified as, they are really good in advanced technical skills, knowledge and maintain the security with best practices, policies and procedures.
CAP is the only certification under the DoD8570 mandate that aligns with each RMF step.
Requirement: You should be having at least 2 years of work experience in any of the main domains. Below mentioned are the main CAP domains:
Domain 1 Information Security Risk Management Program
Domain 2 Categorization of Information Systems (IS)
Domain 3 Selection of Security Controls
Domain 4 Implementation of Security Controls
Domain 5 Assessment of Security Controls
Domain 6 Authorization of Information Systems (IS)
Domain 7 Continuous Monitoring
Also you need to agree to (ISC)2 code of Ethics
Training materials: There are a number of online training websites and YouTube channels available. This includes Lynda, Pluralsight, Udemy etc:
Source: Link
0 notes
Text
SA: #FaceApp- AI Face Editor

[1]
Face app which uses an AI filter making an image of your very old and young state. It has gone viral and has become an hit in short time. Social media is now flooded with face app pictures. Forbes on 17th July stated that, Face app now owns access to more than 150 million people faces and names. This has raised an increase in concerns related to privacy as number of international security agencies has stated as this application can have a back door to Russia. This is because the application is developed by a Russian company named Wireless Lab.
According to there terms and conditions (from www.forbes.com):
You grant FaceApp a perpetual, irrevocable, nonexclusive, royalty-free, worldwide, fully-paid, transferable sub-licensable license to use, reproduce, modify, adapt, publish, translate, create derivative works from, distribute, publicly perform and display your User Content and any name, username or likeness provided in connection with your User Content in all media formats and channels now known or later developed, without compensation to you. When you post or otherwise share User Content on or through our Services, you understand that your User Content and any associated information (such as your [username], location or profile photo) will be visible to the public.
The application ask for the permission to access your camera and the galary and file system. Also they are mentioning it as they will be uploading data to there cloud for processing. These statements and permissions raises concern as what the company or the Russians behind this app can do with the data. As the modern world is more changing into bio-metric passwords than the passwords which we enter, these photos can be easily used for bio-metric access raising to an importanat vulnerability with this application. Since they are uploading the data into their cloud. Until we are not sure on whats happening in the background, its so hard to get part into the #facechallenge.
[1]: Image source: https://faceapp.com/app
0 notes
Text
Week 7: Tutorial & Case Study
This week we started with the lighting talk about destroying papers or data in different methods Its easy to destroy data in hard disk better than using paper.
Boiling paper in lemon juice or some kind of acidic water will destroy the water
Boiling in water won't work
Burning also won't destroy the paper, or the data in the paper
Whats App vulnerability: bug in Whats App user level code which enables the attacker to switch on voice and can listen to you
And this week's topic was to debate on privacy. The arising new issues with terrorism is the unbreakable encryption. They are using the same military graded encryption standard. So this makes its hard to arrest those people. Prism: Data traffic gone to google, Facebook, Microsoft etc through optic cable are tapped. Government proposed spying team Pine gap: This facility is in Australia, to get the radio waves around the world. To get all satellite communication, to tap all the communications around the world. Its near Alice springs part of US. GCHAQ, Tempora is a secret computer facility to saves 3 days data traffic which is stored in UK. This includes all the Optic fiber communications and 30 days of metadata shared with USA. This will help them to track back or monitor illigel or terrorist activities.
With the debate we have the topic as whether the government should be given license to check into individuals privacy. Supporting access to privacy:
This will help to reduce the terrorism activities by constant monitoring.
UK can go back to footage to find the terrorist checking the footage saves in 3 days
To access they need a warrant
There will be a trade off between privacy and safety
Government is doing this for the safety of its citizens
Against:
Leaking of data from government data centers make the situation worse.
Insider attacks can easily be possible and causing the individual privacy getting compromised
Privacy is everyone's right. Privacy is the right to individuals right.
Increasing the footage checking individuals
Real life, searching a house is invasion of privacy.
State surveillance has changed to target surveillance. This created the situation of targeting some specific community and killing individuals.
Need to be more transparent
There is a physical place or drive which can be accessed for the data. The saved data of everyone's privacy.
Incident in us as in CCTV camera installed in schools and used for other purpose
0 notes
Text
Security Everywhere: Vulnerability in Macbook
Apple is know for data privacy and security. This week one of my friends did an in-class presentation on vulnerability in Macbook and I was totally amazed. So I through I will try on my Macbook Pro, and this is what I got:

After pressing the power button, you need to press both the command and S button. This is the single user mode in macbook, when you will get the root access.
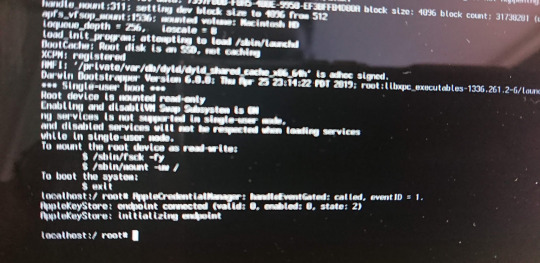
This causes, you can delete the profile and after restarting, macbook will start into profile creation. So you can create the profile with admin access. This will help you to rest the password of the old user. So now you can access the other persons data.
So to protect you macbook or windows, please do encryption of your hard drive. This is the only way you can stop the attacker from removing the profile.
0 notes
Text
Week 7 Lecture
Diffie Hellman key exchange is used for key exchange as it involves complex calculations compared to other key exchange methods. It is used for sharing secret key using the public private key. Using exponentiation method. (A^b)^c = a^bc = (a^c)^b. Below is the image that well explains about Diffie- Hellman key exchange:
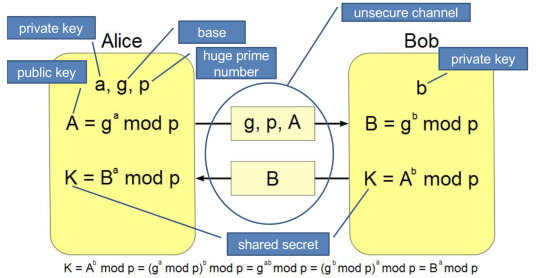
For example:
Alice’s private key = 5, Bob’s private key = 4, g=3, p=7
Alice’s public key=35 mod7=5, Bob’s public key=34 mod7=4
Alice’s shared key=45 mod7=2,Bob’s shared key=54 mod7=2
The issue with this key exchange method is the insecure channel causing Man in middle attack:
Diffie Hellman is good in confidentiality, but there is No authentication. So for man in middle, attacker can change the public key Web of trust(PgP) pretty good privacy
If Eve can tamper with the channel, she can discover Alice, and Bob’s secret.
Vulnerability is potentially a weakness and bug sometimes is a vulnerability sometimes is not. Below are the types of bugs or vulnerabilities
Memory corruption attack: under the control of bad guy, change the control flow of memory . Simple example is buffer overflow Stack and heap. Heap is less controlled, need to free up the memory. Opening up lots of tabs in browser is an example to heap Integer overflow, integer got allocated memory and if increasing the integer again and again, will overflow the memory.
Printf vulnerability:
Printf("%s","hello world") Printf("hello world") , error as need to enter the format Name <- %sphilip Printf(name) Printf("%sphilip") print the stake, the null character Printf("%x") print the next bit Printf for memory leak. You can get the address of the memory and can jump into %n: write to memory. Print you can do arbitrary write or ease of memory. gives root access
Shell code: Attackers use Shell pop up. Using built in OS, using this to write shell code. Put that to the buffer and program to run it
PKI public key infrastructure will solves man in middle
Government Passport links photo to the date of birth and name and is certified. Like this PKI link pubic key link to something and is certified that this public key belongs to this person. So that no one can fake the certificate. Linking the public key with the web domain, like www.google.com. This information is signed. The receiver can check its signed by checking the signature of the signer.
Browsers are preloaded with the certificates and shows a padlock when you load up the page. So you can confirm using SSL
The issue with this is that, there are number of Certification authorities available and they need to get money to get the domain certified. So if you make a website and request the certification authority to certify it by giving the fee.
www.google.com to www.goooogle.com
Browser need to load with the certifications.
Conflict of interest:
giving higher class of certification known as Extended verification. Browser will shows green bar.
Self signed
is another method and will ask the customers to add the certificate to the browser
Pen Tenting:
Testing Firewalls, thinking like an attacker to expose the weekness4 main stages:Recon, planning, exploitation, post exploitation. Some pentesting tools: Nmap, Kali Metasploit, Gobuster
0 notes
Text
SA: Secure Methods of Communication :- Port based Authentication IEEE 802.1X
In this secure method of communication, Involves 3-party communications:
Supplicant which is the User
Authenticator which is either the Ethernet switch or wireless access point
Authentication server which is the RADIUS (Remote access dial-in user service) database, Kerberos, LDAP
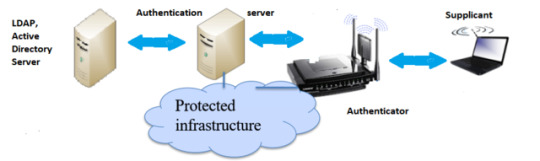
Supplicant is the user device which uses WAP protocol. To access a network service/resource. the device need to be get authenticated. This is connected to the through the authenticator or the access point, AP. This can:
software/app running 802.1X client
OS based supplicants like Microsoft Wireless Zero Conf–WZC or Apple’s airport client
The Chipset vendor’s supplicant software –Intel, Atheros, Broadcom
Authenticator (Access Point): This works as a relay between Supplicant and Authentication Server, There will be two Virtual Ports:
Uncontrolled : allows EAP authentication traffic
Controlled: Only authenticated traffic
Authentication Server: RADIUS provides centralized authentication, authorization and accounting management for user/host to access a network service/resource. This supports AAA (Authentication, Authorization and Accounting). Steps involved in communication:
Both Radius Server and Authenticator are configured with a shared secret
Authenticator sends a RADIUS Access Request message to the RADIUS server, requesting authorization to grant access via the RADIUS protocol. This request includes access credentials (e.g., username and password hash)
Authentication server checks the credentials using the RADIUS server, Kerberos server, LDAP or Active Directory server– returns one of three responses
Access Accept,
Access Reject,
Access Challenge for extra credentials
RADIUS server examples:
Elektron(US$750) is an entry-level and user friendly server
ClearBox(US$599) is designed for small networks, but it also scales to larger networks
FreeRADIUS(open source) is a solid and economical choice for Unix/Linuxadm
Source: Notes from Wireless security
0 notes
Text
SA: Cyber Security Certifications :- CISA (Certified Information System Auditor)

Back again for another week with a new cyber security certification. CISA (Certified Information System Auditor), as the name suggest, is mainly focused on audit, control, monitor and assess information technology and business systems. Also the person will be certified as, they are qualified for IT systems hands-on roles with respect to security tasks.
CISA certification is designed mainly for:
IS/IT Auditors
IS/IT Consultants
IS/IT Audit Managers
Security Professionals
Non-IT Auditors
Exam:
Its a 5 hours exam for 180 questions and you need to get at least 73% for getting certified.
CISA is bit more expensive than Security+ as the exam fee is $1,899. Also the credential holders need to pay a certification maintenance fee of 429$ every 4 years. If you are part of training/bootcamp, then the exam fee will be $769.
CISA Certification:
Confirms your knowledge and experience
Quantifies and markets your expertise
Demonstrates that you have gained and maintained the level of knowledge required to meet the dynamic challenges of a modern enterprise
Is globally recognized as the mark of excellence for the IS audit professional
Combines the achievement of passing a comprehensive exam with recognition of work and educational experience, providing you with credibility in the marketplace.
Increases your value to your organization
Gives you a competitive advantage over peers when seeking job growth
Helps you achieve a high professional standard through ISACA’s requirements for continuing education and ethical conduct
Study materials:
There are a number of online training websites and YouTube channels available. This includes Lynda, Pluralsight, Udemy etc:

Source: Link
0 notes
Text
Busy weeks: 4,5
Last two weeks ( Week 4 and 5 ) of Term 2, was totally a busy week with group assignments, project, quiz, mid term exams. Even for the group assignment, group mate didn’t show up thinking of getting full marks without even contributing. We have reported this to the professor and he will run the peer review on assignment.

These all stuffs made the week 4 and 5 too busy and didn’t get time for blog posting. But I’m back now with my all energy to dig more into security. I will make the most out of my blog and will achieve HD in COMP6441, Security engineering and Cyber security. Thanks for all your support
0 notes
Text
SA: Agent Smith Virus

We all know about Agent smith in Matrix movie. The main villain character who is having the power to clone himself to form hundreds and thousands of same agent smith. Similar to this there is a new malware got spread in android phones and it affected 25million android users. As the name suggest, this malware is having the ability to clone applications and show advertisements. Also the application can take data including the credentials, banking details everything and send the data to the hacker. As the investigation team has found the attacker is from china and they found this by tracking the data transferring from the phone.
It has affected android users in many countries especially India, Pakistan, Bangladesh, Indonesia etc. Those users who have downloaded applications from 9 Apps, an online store for downloading android application files are affected with this malware attack. But after the wide spread of malware, this has been found in some of the google play store application too.
This malware works as, it uses android vulnerabilities to make clone of applications which was there previously and they delete the original application without the user;s permission. Also this makes it hard to track. This malware can track about your activities and send advertisements. It can collect data and send those to attacker location, helping them to access all the important data associated with that user.
So be careful while downloading anything from internet.
0 notes