Text
Continuous Cloud Security

This post presents a case for placing Continuous Security through automation at the center of an enterprise security plan which competently builds and supports consumer and stakeholder confidence in IT security guarantees. It discusses the inadequacy of annual compliance audits and covers the rise of tools that continuously automate and aggregate security checks into meaningful, holistic reports. This paper is for anyone who is accountable or responsible for securely operating a web-based platform or its component services.
Background
Today’s volume of stored information, the growing number of exchanges, and the velocity of change in technology architectures have together presented a massive opportunity for new cybercrimes, making them ever-present in news headlines. Recent notable examples include the hacking of the Democratic National Committee’s email and campaign analytic data and AshleyMadison.com’s data leak. Many more examples can be found here. The industry notions of adequate security and supporting due diligence are now widely in question and rightly so.
Responsible service providers recognize they are part of a larger interconnected ecosystem of overlapping accountability and responsibility for securely hosting and providing data and services. These trustworthy organizations map coverage to ensure the gaps are filled and publish their report cards against identified policies in order to credibly garner and retain consumer confidence.
Problem: Why Annual Security Audits Fail
Industry leading security compliances for web-based enterprises, such as PCI-DSS and others, mandate an annual audit and remediation. For more than 10 years, it has been a requirement for hosting and processing financial transactions. However, these policies were not designed for how quickly and frequently current architectures evolve. Bolstered by cloud architectures and DevOps tools, and agile methodologies, these audits are frequently invalidated shortly after being performed. The technology platform surveyed evolves and changes many times before the next cycle is due, and as a result, customer data and identity is at risk.
Solution: Continuous Security
In order to truly deliver against the promise of securing data and protecting personally identifiable information, you need to adopt a program of continuous auditing and analysis. By doing this, you maintain situational awareness through constant feedback loops that highlight the durability requirements of changes, and facilitate appropriate responses to perimeter vulnerabilities.
As the centerpiece to a holistic security plan, a mature security solution should automate key functions across your entire platform. Automating these functions central part of the platform’s operational visibility and/or continuous integration orchestration facilities.
Data Loss Prevention
Discovers and risk-profiles stored data assets
Detects and alerts on unencrypted, sensitive data in-flight and at-rest
Ensures required access control to data assets
Configuration Drift Detection
Monitors infrastructure, platform and network configuration
Against known good/expected state
Audit trail logs all access and configuration changes
Perimeter Defense
Detects intrusion attempts
Penetration testing
Inventories asset vulnerabilities
Change Management (Continuously Integrated)
Static code analysis
Infrastructure testing framework
Secure Compliance Data Store
Checks and tests grouped and reported by type and level of compliance
Account of all previous scans and reports run
Access requests
Many notable tools and services have arisen in this space to help bootstrap and cover these functional gaps: CodeClimate, ThreatStack, Dome9, Chef Compliance/Inspec, CloudPassage, ExtraHop, DataGuise, and Evident.io. Open source equivalents do exist, but require more time and expertise to properly implement.
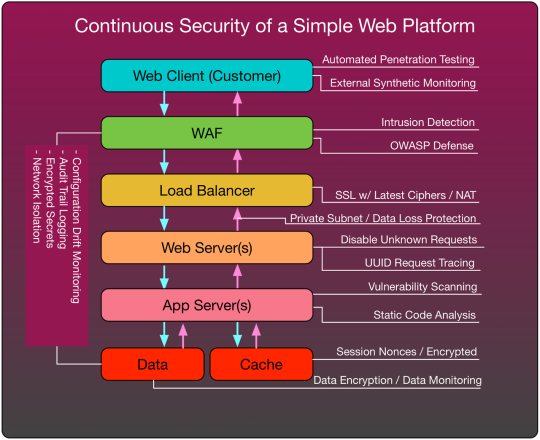
Figure 1: A basic security framework which can be continuously and automatically monitored.
Business Benefits
Predictable Operations: Continuous Security results in fewer surprises and significantly diminished impacts to workflows when it comes to IT risk assessment and management. The visibility of newly identified risks remains constant and the calls to action are small when compared to the annual audit approach.
Brand Loyalty: When automated, the level of effort to publish recurring status reports is relatively small and likely to bolster the trust and confidence of customers.
Mitigated Risk: For some industries, financial and medical, a security incident means shutting down for some period of time. The cost to the organization can easily cross six to nine digits in disrupted revenue. Annual remediation also significantly raise the risk for collateral damage when many changes must be concurrently done and often against inadequate quality assurance procedures.
Summary
Continuous Security means proactive, continuous, automated checking and calls to action resulting in fewer gaps over decreasing time windows, leading to real-time alerting of monitored security incidents. For those organizations serious about safeguarding their customers, it is a must-have.
0 notes