Echo Wisdom is a thoughtful and insightful blog dedicated to exploring the depths of wisdom across various facets of life. The blog aims to resonate with readers by providing well-researched, reflective, and engaging content that echoes the timeless principles and contemporary understandings of wisdom.Mission:Echo Wisdom strives to be a beacon of enlightenment, offering readers valuable insights and practical advice to navigate the complexities of modern life. The blog's mission is to foster a community of like-minded individuals who seek to enrich their lives through the pursuit of knowledge and wisdom.Vision:To become a leading platform for wisdom and enlightenment, Echo Wisdom envisions a world where individuals are empowered with the knowledge and insights to lead meaningful, fulfilling lives. The blog aims to inspire a global community of wisdom seekers, united by a shared passion for learning and personal growth.
Don't wanna be here? Send us removal request.
Text
What to Expect from EMDR Therapy in Sydney: A Comprehensive Guide
EMDR therapy, or Eye Movement Desensitization and Reprocessing, has become a popular and effective therapeutic approach for individuals dealing with trauma, anxiety, PTSD, and other emotional distress. If you're considering EMDR therapy in Sydney, it's essential to understand what the process entails, how it works, and what you can expect from the experience. In this comprehensive guide, we will break down the key aspects of EMDR therapy and provide you with insights on how this treatment can help you on your healing journey.
What is EMDR Therapy?
EMDR therapy is a type of psychotherapy that was developed in the late 1980s by Francine Shapiro. It is primarily used to help people process and heal from traumatic memories, as well as other distressing experiences. The therapy works by facilitating the brain's natural healing processes, enabling the individual to reprocess memories in a way that reduces their emotional charge. This, in turn, allows individuals to move past the negative impacts of these memories and experiences, ultimately improving their mental health and emotional wellbeing.
How Does EMDR Therapy Work?
At the heart of EMDR therapy is the concept of bilateral stimulation, which involves engaging both sides of the brain through eye movements or other forms of stimulation, such as tapping or auditory cues. This bilateral stimulation helps to activate the brain's processing system, allowing it to process and reframe traumatic memories more effectively.
The therapy typically involves eight phases:
History and Treatment Planning: The therapist will gather information about your history, including the traumatic events you wish to address. Together, you will identify specific memories and negative beliefs related to those experiences.
Preparation: This phase involves explaining the EMDR process and ensuring you are comfortable with the techniques. Your therapist will also teach you relaxation techniques to help manage any distressing emotions that may arise during the sessions.
Assessment: In this phase, the therapist will help you identify a specific memory to target. You'll be asked to focus on the memory while simultaneously engaging in bilateral stimulation.
Desensitization: As you focus on the memory, your therapist will guide you through bilateral stimulation. This process helps to desensitize the emotional charge attached to the memory, making it less distressing over time.
Installation: During this phase, you’ll work to replace negative beliefs with more positive, adaptive ones. For example, if a person feels worthless due to a traumatic experience, they may replace that belief with a more empowering thought, such as "I am worthy of love and respect."
Body Scan: This phase involves paying attention to any physical sensations that may remain in the body from the traumatic memory. Your therapist will guide you through processing these sensations to release any lingering tension or discomfort.
Closure: At the end of the session, the therapist will ensure you feel stable and grounded. If necessary, relaxation techniques will be used to help you feel calm and balanced before leaving the session.
Reevaluation: In follow-up sessions, your therapist will evaluate how you have been feeling since the last session, ensuring that the memory no longer causes distress and that the positive beliefs are integrated into your life.
The Benefits of EMDR Therapy
EMDR therapy offers numerous benefits, particularly for those who have experienced trauma or emotional distress. Here are some of the key advantages of seeking EMDR therapy in Sydney:
1. Effective Treatment for Trauma
One of the primary benefits of EMDR therapy is its ability to help individuals process and heal from traumatic experiences. Whether it's a single traumatic event or complex trauma accumulated over time, EMDR helps individuals work through the distressing memories, reducing the emotional charge associated with them. This can lead to significant relief for people struggling with post-traumatic stress disorder (PTSD) and other trauma-related conditions.
2. Reduces Anxiety and Stress
EMDR therapy can also help individuals manage and reduce anxiety. By targeting the root causes of anxiety, which are often tied to past experiences, EMDR can help reframe negative beliefs and reduce the emotional intensity associated with anxious thoughts. Many individuals who undergo EMDR therapy report feeling calmer, more centered, and less overwhelmed by stress.
3. Improves Emotional Regulation
For those who struggle with emotional regulation, EMDR therapy can be incredibly helpful. By processing unresolved emotions and memories, EMDR helps individuals gain greater control over their emotional responses. This can lead to improved relationships, better coping strategies, and an overall sense of emotional balance.
4. Enhances Self-Esteem
One of the goals of EMDR therapy is to help individuals replace negative beliefs about themselves with more positive and empowering ones. For example, someone who has experienced emotional abuse may have internalized beliefs such as "I am not worthy of love" or "I am broken." EMDR therapy works to shift these beliefs, helping individuals cultivate a healthier self-image and increase their self-esteem.
5. Faster Results Compared to Other Therapies
While traditional talk therapies can take years to produce significant results, EMDR therapy tends to produce quicker and more lasting outcomes. Many individuals experience a reduction in symptoms after just a few sessions, making it an efficient choice for those seeking relief from emotional distress in a timely manner.
What to Expect During Your First EMDR Session in Sydney
If you're considering EMDR therapy in Sydney, you may be wondering what to expect during your first session. Here’s a breakdown of the typical process:
Initial Consultation
Your first session will usually begin with an initial consultation where your therapist will ask you about your background, including any traumatic experiences you wish to address. They will also ask about your current emotional state, mental health history, and any previous therapies you may have tried. The therapist will use this information to tailor your treatment plan and help you set goals for your sessions.
Understanding the EMDR Process
The therapist will then explain how EMDR therapy works, including the eight phases of treatment. They will also take the time to answer any questions you may have about the process. This is an important step, as it ensures that you feel informed and comfortable with the therapy before it begins.
Setting Goals
Together, you and your therapist will identify specific memories or experiences that you would like to target during therapy. These memories will be the focus of your treatment, and the therapist will help you set realistic goals for processing them.
Relaxation Techniques
Since EMDR therapy can bring up intense emotions, your therapist will teach you relaxation techniques to help you manage any distress that may arise. These techniques may include deep breathing exercises, grounding exercises, or mindfulness practices to help you stay calm and centered throughout the session.
How Long Does EMDR Therapy Take?
The length of EMDR therapy sessions can vary depending on the individual and the complexity of the issues being addressed. Typically, each session lasts between 60 to 90 minutes. The number of sessions required also varies; some individuals may experience significant relief after just a few sessions, while others may require more extensive treatment. Your therapist will work with you to determine the appropriate course of treatment based on your needs and progress.
Why Choose EMDR Therapy in Sydney?
Sydney is home to a diverse and experienced community of therapists who specialize in EMDR therapy. Whether you're dealing with trauma, anxiety, depression, or other mental health concerns, seeking EMDR therapy in Sydney can offer you access to high-quality care and support. The city's therapists are well-versed in the latest therapeutic techniques and can provide you with the guidance you need to heal and move forward.
EMDR Therapy Sydney provides a supportive and healing environment for individuals who are ready to take the next step toward emotional wellness. The therapeutic process is personalized to each individual’s unique needs, ensuring that every client feels seen, heard, and empowered in their journey to recovery.
Final Thoughts
EMDR therapy can be an incredibly effective treatment for those dealing with trauma, anxiety, or other emotional challenges. With its proven ability to reduce distressing memories and promote healing, it's no wonder that so many people turn to this therapy for relief. If you're considering EMDR therapy in Sydney, know that you're taking a courageous step toward healing and personal growth. With the support of a skilled therapist, you'll have the tools you need to overcome emotional hurdles and live a more balanced and fulfilling life.
For more information on how EMDR therapy can help you, visit https://www.psychologyinbalance.com/.
0 notes
Text
How to Swap Tokens on SushiSwap: A Step-by-Step Guide
Cryptocurrency and DeFi have taken the financial world by storm, offering new ways to trade, earn, and participate in decentralized markets. One of the most innovative and community-driven platforms in this space is SushiSwap. Whether you're a complete beginner or someone who's just starting to dip their toes into decentralized exchanges (DEXs), learning how to swap tokens on SushiSwap can be a game changer.
This guide will walk you through the entire process in a simple, friendly, and easy-to-follow way. Plus, you'll find tips to help you avoid common mistakes and make your experience smoother and safer.
What is SushiSwap and Why Use It?
SushiSwap is a decentralized exchange (DEX) that lets users trade tokens directly from their wallets—no need for a central authority or third-party involvement. Built on the Ethereum blockchain and later expanded to other chains, it uses what's called an automated market maker (AMM) system. This means trades are executed against liquidity pools instead of traditional order books.
Here’s why SushiSwap stands out:
Decentralized and Non-Custodial: You keep control of your crypto—always.
Multi-Chain Support: Ethereum, Polygon, Arbitrum, Optimism, and more.
Yield Opportunities: You can earn from liquidity mining, staking, and farming.
Community Driven: Governance is in the hands of token holders.
So if you’re looking for an efficient, cost-effective way to trade crypto, SushiSwap is a solid pick.
Why Swap Tokens on SushiSwap?
Swapping tokens is one of the most basic yet essential activities in DeFi. Whether you want to invest in a new project, provide liquidity, or simply move assets around your portfolio, token swaps are the gateway.
SushiSwap offers several key benefits:
Lower Fees Compared to Centralized Exchanges
Fast Transactions
No Need for KYC or Personal Info
High Liquidity Across Popular Tokens
Integrated Wallet Support (MetaMask, WalletConnect, Coinbase Wallet, etc.)
What You’ll Need Before You Start
Before diving in, make sure you’re ready with the following:
A Web3 Wallet (e.g., MetaMask)
Some ETH or another supported token to pay for gas fees
Your tokens ready for swapping
An internet connection and a bit of patience for your first try!
Now, let’s jump into the actual steps.
Step-by-Step: How to Swap Tokens on SushiSwap
Swapping tokens on sushiswap is easy once you get the hang of it. Follow these simple steps to get started:
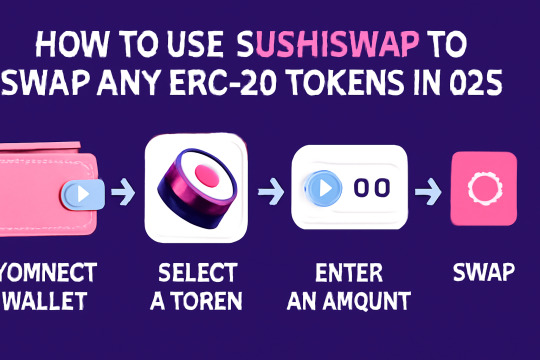
1. Connect Your Wallet
When you land on the SushiSwap site, the first thing you'll need to do is connect your wallet.
Click “Connect Wallet” at the top right.
Choose your preferred wallet provider (MetaMask is the most popular).
Approve the connection in your wallet popup.
Once connected, you’ll see your wallet address at the top, indicating you're good to go.
2. Choose the Tokens You Want to Swap
Next, head to the "Swap" tab.
In the “From” field, select the token you want to trade.
In the “To” field, choose the token you want to receive.
SushiSwap will show you the exchange rate and the minimum amount you’ll receive after slippage.
Pro tip: Make sure your wallet has enough ETH or other chain-native tokens to cover transaction fees. Otherwise, your swap will fail.
3. Set Slippage Tolerance and Gas Fees
Sometimes, prices change rapidly due to volatility. Slippage is the acceptable difference between the price you see and the price you get.
Default slippage is usually set at 0.5%–1%.
For highly volatile tokens, you may need to increase it to 2%–3%.
You can adjust these settings by clicking the gear icon near the swap interface.
4. Approve the Token for Trading
Before swapping certain tokens, you may need to approve them first. This gives SushiSwap permission to access that token in your wallet.
Click “Approve” when prompted.
Confirm the transaction in your wallet.
Wait for the approval to go through (this usually takes less than a minute).
Once done, you're ready to swap.
5. Execute the Swap
Click the “Swap” button and then confirm the transaction in your wallet.
Double-check all the details before confirming.
Once confirmed, the transaction is sent to the blockchain.
You’ll get a transaction hash which you can use to track the progress on a block explorer.
6. Wait for Confirmation
After a few seconds (or minutes, depending on network traffic), your transaction will be confirmed.
You’ll see a success message on the screen.
The swapped tokens will now appear in your wallet.
Heads up: If you don’t see the token right away, you might need to manually import its contract address into your wallet.
7. Tips for a Better Experience
Check Gas Prices: Use tools like Etherscan’s gas tracker to swap when fees are low.
Stay Safe: Always verify you’re on the official site and not a phishing clone.
Double-Check Token Contracts: Use trusted sources or official project websites.
Keep Private Keys Safe: Never share your seed phrase with anyone—ever.
Common Mistakes to Avoid
Swapping without enough ETH for gas fees.
Entering the wrong token contract address.
Falling for phishing links or scam tokens.
Approving unlimited token access (always review what you're approving).
SushiSwap Isn’t Just for Swapping
Once you’re comfortable swapping, SushiSwap opens the door to so much more:
Provide Liquidity: Earn a cut of trading fees.
Stake SUSHI: The platform's governance token.
Explore Onsen Pools: Yield farming with boosted rewards.
Try BentoBox and Kashi: Lending and borrowing made efficient.
Final Thoughts
Swapping tokens on SushiSwap is more than just a transaction—it’s a step into the future of finance. With full control, flexibility, and a community-powered ecosystem, you’re not just trading; you’re participating in a revolution.
Whether you're after low fees, great token support, or simply more transparency, SushiSwap delivers a user-friendly, secure experience that fits the modern DeFi lifestyle. It’s easy to get started, and once you do, you'll likely never go back to centralized exchanges. To get started, visit https://sushiswap-v2.com/
0 notes
Text
The Risks of Ignoring URL Safety: Why You Need to Check URLs

In today’s digital age, browsing the web has become an integral part of daily life. Whether it's for work, shopping, entertainment, or socializing, we visit hundreds of websites each day. However, behind every click, there’s a risk—one that many of us tend to ignore: the safety of the URLs we visit. Ignoring URL safety can lead to serious consequences, from identity theft to losing valuable data. Let’s take a closer look at why you need to be cautious and always check URL safety before clicking on any link.
Understanding the Importance of URL Safety
At its core, URL safety refers to ensuring that the website you are about to visit is secure, authentic, and free from malicious intent. A URL, or Uniform Resource Locator, is essentially the web address of a page. Just like you wouldn’t walk into a sketchy store without a second thought, you shouldn’t blindly trust every website you click on.
Cybercriminals have become highly skilled at creating fake, malicious URLs that look legitimate at first glance. They may trick you into downloading malware, stealing your personal information, or even causing financial loss. This is why being vigilant about URL safety is crucial. By checking URLs before visiting them, you can safeguard your online presence and avoid falling victim to cyber threats.
The Dangers of Ignoring URL Safety
Ignoring URL safety can expose you to a variety of threats. Here are a few of the most common risks associated with unsafe URLs:
1. Phishing Attacks
Phishing is one of the most common and dangerous threats in the digital world. Cybercriminals create fake websites that closely resemble legitimate ones, hoping to trick you into entering sensitive information, such as your login credentials, credit card details, or social security number. These fake websites often look identical to popular online banking portals, shopping websites, or social media platforms.
Once you enter your details, the criminals can use them for fraudulent purposes, such as making unauthorized purchases or accessing your bank account. By checking URLs before clicking on them, you can reduce the risk of falling victim to phishing.
2. Malware and Ransomware
Malware and ransomware are malicious software programs designed to harm your device or steal your information. Clicking on an unsafe URL can lead to the automatic download of these harmful programs. Malware can damage your files, steal your data, or even hijack your device, while ransomware can lock your files and demand payment to unlock them.
In many cases, cybercriminals use URLs to distribute malware through seemingly harmless links, such as pop-up ads or email attachments. Ensuring the URL you’re about to visit is safe can help prevent these types of attacks and keep your devices secure.
3. Data Theft and Identity Fraud
With the increasing amount of personal information shared online, data theft is a significant risk. Hackers can exploit unsecured websites to steal your personal details, including your name, email address, and even your social media accounts. A compromised URL can redirect you to a site where all your personal information is harvested and sold on the dark web.
This can lead to a range of issues, including identity theft, unauthorized financial transactions, and a long-term loss of privacy. Being cautious about the URLs you visit and ensuring they are secure can help protect your personal data from being stolen.
How to Check URL Safety
Now that we’ve established why URL safety is crucial, it’s time to learn how to check URLs effectively. Here are some simple tips to help you assess the safety of a website before you visit it:
1. Look for HTTPS
One of the easiest ways to verify if a URL is secure is by checking for “HTTPS” at the beginning of the web address. The “S” in HTTPS stands for secure and indicates that the website encrypts your data during transmission. This is especially important when entering personal or financial information, as it helps prevent hackers from intercepting your data.
While HTTPS is not a guarantee that a website is safe, it is an essential feature for any secure website. If a website doesn’t have HTTPS, it’s best to avoid it altogether.
2. Double-Check the URL Structure
Malicious websites often use URLs that resemble legitimate ones but have subtle differences. For example, instead of “https://www.example.com,” a scam site might use “https://www.exarnple.com” or “https://www.ex-ample.com.” These small variations can be easy to overlook, but they can have devastating consequences.
Take the time to carefully inspect the URL for any unusual characters or misspellings before clicking. If you notice anything suspicious, it's best to stay away.
3. Use a URL Checker Tool
To make URL safety checks even easier, you can use online tools to verify whether a website is safe. These tools analyze the URL and check it against databases of known malicious sites. They can provide you with an instant report on whether the website is trustworthy or not.
One such tool allows you to check URL safety before visiting any site, giving you peace of mind and reducing the risk of exposure to harmful websites.
4. Be Cautious with Shortened URLs
URL shortening services like Bit.ly or TinyURL can make long web addresses easier to share. However, they can also hide the true destination of a link. Shortened URLs often obscure the website’s real address, making it difficult to determine if a link is safe or not.
If you come across a shortened URL, it’s essential to check the link carefully before clicking on it. Many URL shorteners offer preview features, which allow you to view the full URL before visiting the site.
5. Avoid Clicking on Suspicious Links
In general, avoid clicking on any link that seems suspicious. If you receive an unsolicited email with a link or a message from an unfamiliar source, be extra cautious before clicking. Scammers often use emails or social media messages to send malicious links disguised as legitimate offers, such as free downloads or prizes.
Even if the email looks like it came from a reputable source, double-check the URL to ensure it’s authentic. If in doubt, contact the sender through a trusted communication channel to confirm the link’s legitimacy.
The Role of Anti-Virus Software in URL Safety
In addition to manually checking URLs, using antivirus software can add another layer of protection to your online activities. Many modern antivirus programs come equipped with features that block dangerous URLs or warn you if you’re about to visit a harmful site.
By enabling these features, you can proactively protect yourself from potential threats while browsing. Antivirus software also scans your device for any malware or other threats that may have already been introduced, providing you with real-time protection against malicious URLs.
The Growing Threat of URL-based Cyber Attacks
As the internet becomes more integrated into daily life, cybercriminals are constantly evolving their tactics. URLs have become a primary weapon in their arsenal, and the stakes are higher than ever. With the rise of e-commerce, online banking, and remote work, the potential for damage caused by malicious URLs is greater than ever.
Hackers and cybercriminals are using increasingly sophisticated methods to disguise dangerous URLs, making it more difficult to spot them. As a result, it’s essential to stay informed about the latest trends in cyber threats and continuously educate yourself on how to identify risky URLs.
Conclusion
URL safety is an essential aspect of online security that many people overlook. By ignoring the potential risks of clicking on malicious links, you open yourself up to a variety of cyber threats, including phishing attacks, malware, data theft, and identity fraud. However, by taking simple precautions such as checking for HTTPS, verifying the URL structure, and using tools to check URL safety, you can reduce the risks and protect yourself from harm.
In today’s increasingly connected world, it’s more important than ever to be proactive about URL safety. Stay vigilant, and always think twice before clicking on a link—your security and privacy depend on it.
For a comprehensive tool to check URLs and keep your browsing experience secure, visit https://phishs.com/.
0 notes
Text
Packing for the Trail: Backpacking Essentials for Any Journey

Embarking on a backpacking adventure is a thrilling experience that takes you into the heart of nature, providing a sense of freedom and self-reliance. Whether you're a seasoned hiker or a first-time adventurer, packing the right gear is key to ensuring your journey is both enjoyable and safe. Knowing what to bring and how to pack efficiently can make all the difference. Let's dive into the backpacking essentials that will have you prepared for any journey, from a weekend hike to a multi-day expedition.
The Foundation of Any Backpacking Trip
When preparing for a backpacking trip, there are several foundational aspects that you need to get right. One of the most crucial elements is choosing the right backpack. It should be comfortable, durable, and spacious enough to carry all your essentials without feeling too heavy. Look for a pack that suits your trip's duration, whether it's a smaller daypack for short hikes or a larger pack for multi-day treks.
Another essential is the right clothing. Weather can be unpredictable in the wild, so layering is key. Start with moisture-wicking base layers that help regulate your body temperature, followed by insulating layers for warmth, and finally a waterproof, breathable outer layer to protect against the elements. Don't forget a good pair of hiking boots that provide support and traction, as well as a pair of socks that are comfortable and moisture-wicking to prevent blisters.
Water is another vital resource to consider. Depending on the location, you may not have access to fresh water along the trail. Always carry enough water to stay hydrated and bring a reliable water filtration system or purification tablets in case you need to refill from streams or lakes. Having a good water storage system, like a hydration bladder or water bottles, ensures you won't run into trouble when you’re on the move.
Backpacking Essentials for Comfort and Safety
Backpacking essentials go beyond just basic survival needs. Comfort and safety should be at the top of your priority list. First, a well-suited sleeping system is crucial. A lightweight sleeping bag, paired with a sleeping pad or inflatable mattress, will help you rest after long days of hiking. A good night's sleep will keep you energized for the next day's adventure.
When it comes to shelter, the right tent can make all the difference. Look for a lightweight, easy-to-pitch tent that provides ample space and protection from the elements. There are various types of tents, such as freestanding or non-freestanding, and selecting the right one depends on your preferences and the terrain you'll be hiking in. A good tent can also help protect you from insects and provide a sense of privacy in more remote locations.
Additionally, a first aid kit should always be part of your backpacking gear. Accidents happen, and being able to address minor injuries can prevent them from becoming bigger problems. Your first aid kit should include bandages, antiseptic wipes, blister treatment, pain relievers, and any personal medications you may need.
A headlamp or flashlight is another must-have. A reliable light source is essential for navigating the trail in low light conditions, whether you're setting up camp in the evening or finding your way after sunset. Make sure to pack extra batteries as well to ensure you’re never caught in the dark.
Navigating the Wild with Confidence
One of the most important aspects of backpacking is knowing where you're going. A map and compass (or GPS device) should always be included in your essentials list. Knowing how to read a map and use a compass is an invaluable skill for any backpacker, helping you stay on track and avoid getting lost. In some areas, you may have access to marked trails, but there will be times when you have to navigate off-trail, making your navigation tools even more critical.
It’s also a good idea to familiarize yourself with the route ahead of time. Study the terrain, potential hazards, and any emergency exits or alternatives. Let someone know your itinerary and estimated return time. This small step can be a lifesaver if things don’t go as planned.
Another great addition to your pack is a multi-tool. A knife or multi-tool can be helpful for everything from food preparation to cutting rope or dealing with any gear malfunctions. It’s a lightweight and compact tool that can save you in a variety of situations, from building a shelter to simply fixing a broken strap.
Food and Snacks: Fuel for the Journey
Food is fuel, and when you're on the trail, it becomes even more important. You need to have enough energy to keep you going without weighing down your pack with too much food. Dehydrated or freeze-dried meals are great for backpacking as they are lightweight, compact, and easy to prepare. They typically just require boiling water, making them a quick and convenient option after a long day of hiking.
In addition to your main meals, don't forget to pack energy-rich snacks. Nuts, trail mix, energy bars, and dried fruits are excellent for quick snacks during the day when you need a little boost. These foods provide long-lasting energy and are easy to carry in your pack. You’ll be glad to have them on hand when you’re miles away from the nearest convenience store.
Another essential when it comes to food is a portable stove. A compact stove allows you to cook meals, boil water for drinks, or make hot food. Choose a stove that’s easy to use and fuel-efficient, and be sure to bring a small fuel canister if necessary. A stove can make your backpacking experience more comfortable, especially in cold weather.
Leave No Trace: Practicing Sustainability on the Trail
One of the most important aspects of backpacking is preserving the natural environment. As a responsible backpacker, it’s crucial to follow Leave No Trace principles. This means minimizing your impact on the environment, leaving the trail as pristine as you found it, and respecting the wildlife around you.
Make sure to pack out all your trash, including food scraps, wrappers, and any other waste you may have. If you need to use the bathroom, always dig a cat hole at least six inches deep and bury your waste properly, or carry a trowel and follow local guidelines. Bringing biodegradable soap for washing dishes or yourself is a small but important step toward reducing your environmental footprint.
Be mindful of your campsite, choosing an established area to camp to avoid damaging fragile ecosystems. Stay on designated trails to protect the landscape, and avoid disturbing wildlife. Keep a safe distance from animals, and never feed them. By following these principles, you'll ensure that others can enjoy the beauty of nature for years to come.
Packing Smart: Tips for Organization and Efficiency
Efficient packing is key to enjoying your backpacking trip. When organizing your gear, pack the heaviest items closer to your back and near the center of the pack. This helps distribute the weight evenly and prevents your pack from feeling unbalanced. Use stuff sacks or dry bags to keep your gear organized and dry, especially if you’re expecting wet weather.
It’s also important to pack only what you’ll truly need. The goal is to keep your load as light as possible without sacrificing essential items. Check the weather forecast before your trip and adjust your packing list accordingly. If rain is expected, add a rain cover for your pack or waterproof bags for your clothing and electronics. Don’t forget a repair kit for any gear that might break on the trail.
Incorporating quick-access pockets in your pack is another great tip. Store items you’ll need frequently, like snacks, sunscreen, or a map, in easily accessible spots. This prevents you from having to dig through your entire pack every time you need something.
Conclusion
Packing for a backpacking trip requires careful planning and consideration. From choosing the right gear to organizing your pack efficiently, the key is to be prepared for the unexpected while keeping comfort and safety in mind. By focusing on the essentials, you can ensure your journey is enjoyable and memorable. Whether you're hiking for a few days or venturing into the wilderness for weeks, having the right tools, food, and gear is essential for a successful adventure.
For more information on the essential gear you'll need for any backpacking journey, take a closer look at this helpful guide: https://www.outdoortechlab.com/backpacking-big-3/
0 notes
Text
Top Reasons Business Professionals Choose Executive Chauffeur London

In today’s fast-paced world, where time is money, business professionals need a service that guarantees efficiency, reliability, and comfort. One of the most favored choices for busy executives is opting for an executive chauffeur service. It provides a range of benefits, not just for the commute, but also in terms of enhancing the overall professional experience. In this blog, we’ll explore why many business professionals in London choose an executive chauffeur for their daily commute and corporate events.
1. Time Efficiency: Get to Your Destination Faster
Time is arguably one of the most valuable assets for business professionals. With hectic schedules and meetings packed throughout the day, getting from one place to another efficiently is crucial. Executive chauffeur services in London offer the advantage of avoiding traffic stress and unnecessary delays.
Unlike using public transport or driving yourself, where you can be at the mercy of London's notorious traffic, an executive chauffeur knows the city well. They can take you through the quickest routes, helping you avoid traffic jams and roadblocks. Additionally, these services often have access to exclusive lanes, making your travel more efficient.
The time saved can be put to better use—whether it's reviewing important documents, making calls, or preparing for your next big meeting. As a business professional, the ability to remain productive during travel is a significant reason why many opt for an executive chauffeur service.
2. Comfort and Relaxation on the Go
Business professionals spend a significant portion of their day traveling between meetings, airports, and corporate events. The journey can be tiring, especially if you have to sit in uncomfortable settings like crowded public transport or a rental car. An executive chauffeur offers an entirely different experience.
The vehicles used for executive chauffeur services are typically high-end, well-maintained, and equipped with luxury features. Whether it’s a sleek sedan, an SUV, or even a spacious limousine, these vehicles are designed to provide maximum comfort.
Leather seats, climate control, ample legroom, and privacy screens create a soothing environment where you can sit back, relax, and prepare for your next task. Some chauffeurs even offer refreshments, Wi-Fi, and in-car charging facilities to make your journey even more comfortable. Having a stress-free travel experience can set the tone for the rest of your day, helping you stay refreshed and focused on the tasks ahead.
3. Professionalism and Image
In the business world, presentation matters. How you present yourself often impacts the way others perceive you, and this extends to how you arrive at your meetings and events. Executive chauffeur London services provide a sense of professionalism and sophistication that can positively affect your business image.
Imagine arriving at a high-profile meeting in a luxury car with a professional chauffeur who opens the door for you. It’s an image of success and status that speaks volumes about your professionalism and attention to detail.
For business executives, it’s not just about getting to the destination—it’s about making an impression. Opting for an executive chauffeur service elevates your image and reinforces your professionalism. Whether it's arriving at a client meeting, a conference, or a business dinner, you can be sure that you will make an impact with a premium chauffeur service.
4. Personalization and Convenience
Executive chauffeur services are highly flexible and personalized to suit the specific needs of each business professional. When you book an executive chauffeur, you're not just getting a ride from point A to point B. You get a bespoke service designed around your schedule and preferences.
If you have multiple stops, need to adjust your timing, or require specific amenities during your ride, a chauffeur service can accommodate these requests with ease. Whether it's a car with extra space for documents or a service that ensures you arrive in time for a last-minute meeting, the flexibility and convenience of an executive chauffeur service make it a perfect choice for busy professionals.
Moreover, many chauffeur services offer the option of having the same driver regularly. This helps to build rapport and trust, adding another layer of convenience as your driver becomes familiar with your preferences, schedules, and routes.
5. Safety and Security
For many business professionals, safety is a top priority. Whether traveling alone or with colleagues, ensuring a secure and protected journey is essential. Executive chauffeurs are highly trained to handle not only the driving but also any unforeseen situations that may arise during the trip.
These services provide insured vehicles, so you can travel with peace of mind knowing you're covered in the unlikely event of an accident. The chauffeurs themselves often undergo thorough background checks, ensuring you're in safe hands.
Additionally, the vehicles used are equipped with the latest safety features, including airbags, GPS tracking, and real-time monitoring systems. When you're on the move for business, safety and security should never be compromised, and an executive chauffeur service ensures these standards are upheld.
6. Stress-Free Travel for Important Business Events
Business events like conferences, meetings, and seminars often require you to be at your best—mentally and physically. The stress of navigating unfamiliar routes, finding parking spaces, or dealing with delays can be a major distraction. Executive chauffeur services take all the stress out of your travel, leaving you to focus on what's most important: the event itself.
Whether you're heading to an important presentation, a networking event, or a crucial business dinner, having a professional chauffeur handle the logistics ensures you arrive in a calm, composed state. Knowing you have reliable transportation allows you to focus on your goals and make the most of your time at the event.
7. 24/7 Availability and Flexibility
Business doesn't always happen during regular office hours. Late-night meetings, early-morning flights, or even international events that require you to travel outside the typical 9-5 schedule are all part of a business professional's life.
One of the standout features of executive chauffeur services is their 24/7 availability. No matter when you need to travel, you can count on a chauffeur service to be at your disposal. Whether it's a last-minute meeting or an early morning airport pickup, these services cater to your unpredictable schedule. The flexibility to choose your pickup times, locations, and vehicle type means you have the freedom to manage your time as efficiently as possible.
8. Efficient Airport Transfers
For many business professionals, travel often includes trips to and from airports. An executive chauffeur service ensures a smooth, hassle-free journey to your departure gate. From checking your flight status to providing timely updates on potential delays, the service allows you to remain relaxed and organized during your trip.
The chauffeur will monitor your flight schedule and adjust the pickup time to ensure they arrive exactly when needed, so you don’t have to wait at the airport. With luggage assistance and guidance to the check-in counter, you can rest assured that every aspect of your journey will be taken care of.
9. Enhanced Privacy and Confidentiality
In business, confidentiality is often key, whether you're discussing sensitive information, negotiating contracts, or simply making calls on the move. One of the advantages of an executive chauffeur service is the level of privacy it offers.
You can rest easy knowing that your personal and business conversations will remain confidential during your travel. Unlike public transportation, where your conversations could be overheard, a private chauffeur ensures that you have the space and quiet you need to conduct business without worrying about your privacy.
10. A Better Work-Life Balance
Lastly, an executive chauffeur service contributes to a better work-life balance. By removing the stress of driving, navigating, and managing traffic, you free up time for other activities. Whether it’s spending more time with your family, relaxing, or indulging in personal hobbies, the convenience of a chauffeur service can make a noticeable difference in your quality of life.
Conclusion
Choosing an executive chauffeur service in London is more than just about transportation—it’s about creating an experience that supports the busy, high-paced lifestyle of business professionals. From time-saving benefits and luxury comfort to personalized service and enhanced security, the reasons to opt for a professional chauffeur service are compelling.
When you combine efficiency, convenience, professionalism, and comfort, it’s easy to see why many top executives choose this option to navigate through the demands of their business schedule.
For more information on reliable chauffeur services, visit https://www.cronychauffeurservices.com/.
0 notes
Text
Top Reasons to Use a Bitcoin Blender for Enhanced Security
The digital age has brought along numerous innovations, and one of the most revolutionary is Bitcoin. As one of the most popular cryptocurrencies, Bitcoin offers a decentralized, secure, and efficient method for financial transactions across the globe. However, with great power comes great responsibility. The more valuable your assets, the more crucial it becomes to ensure their safety. One way to safeguard your Bitcoin is by using a Bitcoin blender. In this article, we'll explore why using a Bitcoin blender is an excellent decision for anyone looking to protect their digital assets and enhance security.
1. What is a Bitcoin Blender?
Before delving into the reasons why you should use a Bitcoin blender, it’s important to understand what it is. A Bitcoin blender (often referred to as a Bitcoin mixer) is a service designed to enhance the privacy of Bitcoin transactions. It works by mixing your Bitcoin with others in a pool, making it more difficult to trace your transaction history. This process is often referred to as “CoinJoin,” where the original coins are mixed with new ones, breaking the link between the sender and the recipient.
Bitcoin blenders are essential tools for those who value their privacy and wish to prevent any unwanted tracking of their transactions. With the increasing sophistication of blockchain analysis, it's easy to see why someone might want to anonymize their Bitcoin activity.
2. Enhanced Privacy and Anonymity
The primary reason to use a Bitcoin blender is the enhancement of privacy and anonymity. By default, all Bitcoin transactions are stored on a public ledger called the blockchain. While this provides transparency, it also makes it easy for anyone to trace the flow of funds from one address to another. This openness can be a double-edged sword. For example, anyone who knows your wallet address can track your transaction history, which could expose sensitive financial details.
This is where a Bitcoin blender comes into play. When you use a Bitcoin blender, your transaction is mixed with others, obfuscating the source and destination addresses. As a result, it becomes nearly impossible for third parties to track the origin of the funds. By using a Bitcoin blender, you can send and receive Bitcoin without leaving a trail, ensuring your financial activities remain private.
The Growing Need for Privacy
With more and more people becoming aware of the need for digital privacy, services like Bitcoin blenders are becoming increasingly popular. Many users are wary of government surveillance, hackers, or even advertisers that might want to track their spending habits. The more you transact with Bitcoin, the more exposed your wallet becomes to such scrutiny.
For those who prefer to keep their financial dealings private, a Bitcoin blender can act as a safeguard, ensuring that sensitive information does not end up in the wrong hands.
3. Mitigating the Risk of Theft or Hacking
Another significant advantage of using a Bitcoin blender is that it helps mitigate the risk of theft or hacking. Cryptocurrencies, including Bitcoin, are often targeted by cybercriminals looking to steal digital assets. If your wallet address becomes publicly known, malicious individuals might target your account, especially if they see a large balance.
When using a Bitcoin blender, your Bitcoin is mixed with a pool of others, making it much harder for hackers to target your assets. Even if a hacker manages to obtain part of the transaction history, they will only find mixed coins, making it nearly impossible for them to steal your Bitcoin.
Additionally, blending Bitcoin reduces the risk of “address reuse,” which is another security concern. When you consistently use the same wallet address, it becomes easier for hackers to track your transactions and attempt to steal funds. A Bitcoin blender allows you to generate fresh, anonymous addresses, reducing the likelihood of being targeted.
Bitcoin blender services play a pivotal role in securing your funds, especially if you are concerned about the increasing number of cyberattacks targeting cryptocurrency holders.
4. Protection Against Surveillance and Monitoring
Governments and corporations have become more interested in monitoring cryptocurrency transactions. While some countries are still uncertain about how to regulate digital currencies, others have taken a more aggressive stance by implementing blockchain analysis tools that can trace Bitcoin transactions. These tools can tie specific addresses to individuals or entities, which could expose personal information, tax obligations, or even provide evidence for criminal investigations.
By using a Bitcoin blender, you are essentially masking your transaction history from any third-party observers. Blenders make it nearly impossible for any external entity to trace the original source or destination of your Bitcoin. This added layer of protection ensures that your transactions are free from prying eyes.
In some cases, individuals may be concerned about their transactions being linked to illegal activities, such as money laundering or fraud. Using a Bitcoin blender makes it much harder for authorities or anyone else to trace the origins of your Bitcoin, providing peace of mind to those who prefer to operate under the radar.
5. Reducing the Risk of Address Linking
One of the most significant threats to Bitcoin users is address linking, a technique used by blockchain analysis companies and governments to connect transactions to specific individuals. These analysis techniques can identify patterns in Bitcoin transactions, such as repeated use of certain wallet addresses, which can link several transactions to the same person.
By using a Bitcoin blender, you can break the link between your wallet and any past transactions. The blender service mixes your Bitcoin with other users’ coins, which means that each output is associated with a different wallet. This process effectively severs any links between you and previous transactions.
In simple terms, by blending your Bitcoin, you create multiple layers of obfuscation that make it more difficult for anyone to connect the dots between your wallet and specific transactions.
How to Reduce Address Linking with Blenders
When choosing to use a Bitcoin blender, it’s crucial to follow best practices to ensure maximum security. First, avoid reusing the same wallet address, as this increases the chances of being linked to other transactions. Additionally, make sure to use a blender that offers a robust mixing algorithm, ensuring that your Bitcoin is thoroughly mixed with others.
6. Ensuring Secure and Fast Transactions
Bitcoin blenders are not just about privacy – they also improve transaction efficiency. Traditional Bitcoin transactions can be relatively slow, especially when there are multiple participants involved. However, using a mixer service speeds up the process by ensuring that your Bitcoin is anonymized and transferred in one swift operation.
Many Bitcoin blenders offer a high level of efficiency and reliability, ensuring that your coins are mixed and sent to the desired destination without unnecessary delays. This allows for faster transactions without compromising security or privacy.
7. Supporting the Growth of Decentralized Finance
The rise of decentralized finance (DeFi) has changed the way people think about finance. Traditional financial institutions are becoming less relevant as more people turn to decentralized platforms for banking, lending, and investment. Bitcoin blenders are an integral part of this ecosystem because they help maintain the core principles of decentralization, such as privacy, autonomy, and security.
By using a Bitcoin blender, you contribute to the growing decentralized financial ecosystem. These tools ensure that privacy remains a cornerstone of the digital economy. Without services like Bitcoin blenders, the risk of surveillance, hacking, and financial control would increase, ultimately stifling the growth of decentralized finance.
8. Protecting Your Investment Portfolio
Many individuals view Bitcoin as an investment, holding large quantities of the cryptocurrency in the hopes that it will increase in value over time. As with any investment, protecting it is a top priority. Using a Bitcoin blender offers a simple way to enhance the security of your digital investment.
By obfuscating your transaction history, a Bitcoin blender reduces the risk of unwanted exposure. This can help ensure that your investment is shielded from any potential threats, whether they come from hackers, market manipulators, or government entities.
Conclusion
In a world where digital privacy and security are becoming increasingly important, using a Bitcoin blender is one of the best ways to protect your cryptocurrency assets. Whether you are concerned about privacy, security, or simply want to avoid the risks associated with traceable transactions, Bitcoin blenders provide a practical and effective solution. As cryptocurrency continues to grow in popularity, these services will only become more essential in ensuring that your financial activities remain anonymous and safe.
If you're looking to enhance the security of your Bitcoin transactions, using a trusted Bitcoin blender is the way forward.
0 notes
Text
The Ultimate Guide to Planning a Party with Party Rentals

Planning a party can be an exciting yet overwhelming experience, especially when it comes to making sure everything runs smoothly and your guests have a great time. Whether you're organizing a birthday bash, a wedding reception, or a corporate event, the success of your party lies in the details, and a big part of that is making sure you have all the necessary equipment and decor. This is where party rentals come into play, offering you an easy and convenient way to get everything you need without having to purchase expensive items you’ll only use once.
Why Party Rentals Are Essential for Your Event
Party rentals are more than just a convenient solution—they’re a game-changer when it comes to ensuring your event is both stress-free and memorable. When you choose to rent party supplies, you’re not just saving money, you’re also gaining access to high-quality, professional-grade equipment that can elevate the atmosphere and function of your event. From tents to tables, chairs, linens, lighting, and even entertainment options, renting allows you to create the perfect setting without having to invest in permanent items that may take up space in your home or office.
Planning Your Event with Party Rentals
The first step in planning your party with rentals is to understand what you need for your specific event. This can depend on the venue size, the type of event, and the number of guests. Here’s a breakdown of how you can approach the planning process with rentals.
1. Choose a Theme or Style
Every great party starts with a theme. Whether it’s a formal black-tie affair, a laid-back backyard barbecue, or a whimsical kids’ birthday party, your theme will set the tone for all other decisions, including what types of party rentals you’ll need. For example, a wedding will require elegant seating, formal dinnerware, and floral arrangements, while a corporate event may need podiums, chairs for speeches, and lighting that emphasizes the mood.
2. Determine the Number of Guests
Knowing the number of guests you expect will help you decide on the amount of rental items you’ll need. You can avoid over-ordering or under-ordering by getting an accurate headcount early. Think about all the seating, tables, and even bar stations you might need. For larger events, consider a party tent to accommodate your guests in case of bad weather.
3. Consider Functionality and Flow
You’ll also want to think about the flow of your event and how guests will move through the space. Renting the right equipment can help create a comfortable, efficient layout. Renting furniture like chairs and tables allows you to customize the arrangement based on your venue, so you can optimize the space for mingling, dining, and entertainment. Consider lighting and sound equipment rentals for added ambiance and functionality. You don’t want to overcrowd the space, but you also don’t want it to feel sparse—renting allows you to find the right balance.
Party rental services are designed to provide you with all the essentials you need to make your event run smoothly. These rentals can be delivered right to your door or venue, set up, and even taken down afterward. For events such as weddings, corporate gatherings, or large celebrations, this service eliminates a lot of the hassle and lets you focus on the fun.
4. Budgeting for Party Rentals
One of the biggest advantages of using rentals is how cost-effective they can be compared to purchasing items outright. When determining your budget, keep in mind that rentals allow you to get high-end items without the hefty price tag. Your budget should cover the cost of your rentals, delivery fees, setup, and any extra services like catering equipment or entertainment gear.
Types of Party Rentals to Consider
There’s a wide variety of party rental items available to suit the needs of any event. Here’s a look at some of the most popular types of rentals you can incorporate into your party planning:
1. Furniture Rentals
Furniture is one of the first things you'll need for any event. Consider renting tables, chairs, sofas, and bar stools. Depending on the occasion, you may want formal dining tables or casual cocktail tables for mingling. Lounge areas with comfortable sofas or unique seating arrangements can also set the tone for your event.
2. Tent and Canopy Rentals
Outdoor events are always a hit, but unpredictable weather can make them tricky. Renting a tent or canopy provides shelter for your guests, protecting them from rain or excessive sun. Tents come in a range of sizes, from intimate party tents to large, event-sized tents that can accommodate hundreds of people. They can also be decorated to match your event’s theme, with drapes, lighting, and flooring to create the perfect atmosphere.
3. Tableware and Linens
If you’re hosting an event with a meal or drinks, party rental services often offer stylish tableware and linens. From elegant fine china and glassware to practical plasticware for casual gatherings, you can find a rental option that fits the mood and needs of your event. Linens like tablecloths, napkins, and chair covers can also enhance the visual appeal of your tables and seating arrangements.
4. Lighting and Sound Rentals
Lighting and sound play a huge role in setting the mood for your event. Depending on the type of party you’re hosting, you may need ambient lighting for a relaxing vibe or bright, colorful lights for a lively dance floor. Party rentals include everything from chandeliers and string lights to spotlights and LED setups. Renting sound systems for music or speeches ensures that your guests can hear and enjoy the atmosphere without any hiccups.
5. Entertainment and Games
For many events, especially those like kids’ parties or corporate celebrations, entertainment options are a must. Renting items like photo booths, carnival games, or even inflatables can keep your guests entertained. Interactive entertainment can break the ice and ensure that everyone has fun, regardless of their age.
6. Decor Rentals
Party decor sets the tone and vibe of your event. Rentals allow you to create a stylish and cohesive look without needing to buy everything. Renting decorative items such as floral arrangements, arches, backdrops, and centerpieces will save you time and money while enhancing the overall theme.
The Benefits of Renting vs. Buying
Renting party supplies offers numerous advantages over purchasing items for one-time use. Here’s why rentals make more sense for most event planners:
Cost-Effective: Renting is far more affordable than buying, especially for items you’ll only use once or twice.
Convenience: Party rental companies handle delivery, setup, and takedown, which means less stress for you on the day of the event.
Variety and Quality: Rentals give you access to a wide variety of high-quality products, often at a fraction of the cost of buying them outright.
Customization: You can easily customize your event with rented items to fit your specific theme and needs.
Tips for Choosing a Party Rental Service
When selecting a party rental service, here are some factors to consider to ensure you get the best experience:
Reputation: Look for reviews or ask for recommendations to find a reputable rental company with a good track record of delivering quality products and excellent customer service.
Availability: Check that the items you need are available on your event date and inquire about delivery and setup times.
Flexibility: Choose a company that offers flexibility in terms of rental duration, delivery, and setup times. Some events may require special timing or additional services.
Package Deals: Many rental companies offer discounts or package deals if you’re renting multiple items. Look for bundled packages that fit your event’s needs.
Conclusion
Planning a party can be a lot of work, but it doesn’t have to be stressful. Party rentals can simplify the process by providing you with everything you need, from furniture and lighting to decor and entertainment. By renting, you not only save money but also gain access to high-quality items that can elevate the look and feel of your event. So, whether you’re planning an intimate gathering or a grand celebration, don’t hesitate to take advantage of party rental services to make your event truly unforgettable.
For all your party rental needs, consider visiting https://chrispartyrental.com/.
0 notes
Text
How Crypto Scam Recovery Experts Can Help You Regain Lost Funds

Cryptocurrency has revolutionized the world of finance, but it has also attracted a darker side. The rise of digital assets has led to an increase in crypto scams, leaving countless individuals vulnerable to fraudulent schemes. These scams often prey on the uneducated or overzealous, causing significant financial loss. Thankfully, crypto scam recovery experts are here to help individuals recover their lost funds and seek justice. In this article, we will explore how these professionals can assist victims in their journey to financial recovery.
What is a Crypto Scam?
A crypto scam involves fraudulent activities aimed at deceiving individuals into investing in fake or non-existent cryptocurrency ventures. These scams come in various forms, including Ponzi schemes, fake initial coin offerings (ICOs), phishing attacks, and fraudulent trading platforms. While cryptocurrencies like Bitcoin, Ethereum, and others offer legitimate investment opportunities, the lack of regulation in the space makes it an attractive target for scammers. The anonymity and decentralization of crypto transactions make it difficult to trace the perpetrators.
Scams often promise high returns with little risk, a hallmark of deceptive practices. The victims, driven by the fear of missing out (FOMO) on the next big thing, quickly get involved. Once they deposit their funds, they either see no return or find that they are unable to withdraw their investments. In many cases, the scammer disappears with the funds, leaving victims with little to no recourse.
How Do Crypto Scam Recovery Experts Help?
When victims of cryptocurrency scams realize they have fallen prey to fraudulent schemes, they often feel helpless. However, they don’t have to navigate the process alone. Crypto scam recovery experts specialize in helping individuals regain their lost funds. These professionals have a deep understanding of the complex world of cryptocurrency transactions and the tools necessary to trace, track, and recover stolen assets.
One of the most significant advantages of hiring crypto scam recovery experts is their experience. These professionals are well-versed in identifying and investigating crypto scams. They understand how different scams work and know how to gather the information required to initiate a recovery process. Most importantly, they have the expertise to help victims understand their legal rights and navigate the complicated process of recovery.
Crypto Scam Recovery Experts employ advanced tools and methodologies to track down stolen assets. They use blockchain analysis software, which can trace transactions and identify the movement of funds through various crypto wallets. This technology makes it possible to follow the trail of stolen funds and potentially recover them. In some cases, recovery experts can work with law enforcement or regulatory authorities to bring the scammers to justice.
Common Types of Crypto Scams
The crypto world is rife with different types of scams. Here are a few common examples:
1. Ponzi Schemes
Ponzi schemes are one of the oldest forms of investment scams, and they have found their way into the world of cryptocurrency. These schemes promise high returns with little risk and rely on new investors’ funds to pay returns to earlier investors. Eventually, the scheme collapses when there are not enough new investors to sustain it. Victims lose their money, and the scammer typically vanishes.
2. Fake ICOs
Initial Coin Offerings (ICOs) are a legitimate way for blockchain projects to raise funds by offering new cryptocurrencies to the public. However, scammers have also taken advantage of this fundraising method. They create fake ICOs, offering non-existent coins or tokens to unsuspecting investors. Once the funds are raised, the scammers disappear, leaving investors with worthless digital assets.
3. Phishing Attacks
Phishing attacks involve fraudulent messages or websites designed to steal sensitive information, such as private keys or login credentials. Scammers often impersonate legitimate cryptocurrency exchanges or wallet providers to trick users into revealing their information. With this information, the scammers can access the victim’s crypto wallet and steal their funds.
4. Fraudulent Trading Platforms
Scammers may also create fake trading platforms that mimic legitimate exchanges or services. These platforms promise high returns on crypto investments but are designed to deceive users. After users deposit funds into these platforms, they find that they cannot withdraw their money, or the platform simply shuts down.
5. Pump and Dump Schemes
In a pump and dump scheme, a group of people manipulates the price of a cryptocurrency by artificially inflating its value (the “pump”). Once the price reaches a peak, they sell off their holdings, causing the price to crash. The victims, who purchased the asset during the inflated price, are left with worthless tokens.
Steps Involved in Recovering Lost Crypto
If you’ve fallen victim to a crypto scam, there are several steps that recovery experts will take to help you recover your funds:
1. Assessing the Situation
The first step in the recovery process is understanding the nature of the scam. Recovery experts will assess the situation and gather all relevant details, such as the type of scam, the amount of money lost, and the transaction history. They will also identify any evidence that can be used to trace the funds.
2. Identifying the Movement of Funds
Using blockchain analysis tools, recovery experts will track the movement of the stolen funds. Since all crypto transactions are recorded on the blockchain, it is possible to trace where the funds went and, in some cases, identify the wallets or exchanges involved.
3. Contacting Authorities
Depending on the nature of the scam, recovery experts may contact law enforcement or regulatory authorities. They will provide all the relevant evidence to assist in the investigation. In some cases, international authorities may be involved if the scammer operates across borders.
4. Attempting to Recover Funds
Once the movement of funds has been traced, experts may attempt to recover the stolen funds. This process can be complex and may require working with exchanges or wallet providers to freeze or reverse transactions. However, in some cases, recovery may not be possible if the scammer has already converted the funds into untraceable assets.
5. Legal Action
In certain cases, victims may have the option to pursue legal action against the scammer. Recovery experts can guide victims through the legal process, helping them understand their rights and the potential for restitution. Legal action can be a lengthy and costly process, but it may result in the recovery of funds and justice for the victim.
How to Protect Yourself from Crypto Scams
While crypto scam recovery experts can help victims regain their lost funds, prevention is always better than cure. Here are a few tips to protect yourself from falling victim to crypto scams:
1. Research Before Investing
Before investing in any cryptocurrency or crypto project, do your due diligence. Research the project, its team, and its goals. Look for reviews, feedback, and any potential red flags. If something sounds too good to be true, it probably is.
2. Be Cautious of Unsolicited Offers
Be wary of unsolicited offers, especially those that promise high returns with little risk. Scammers often reach out to potential victims via social media, email, or even phone calls. Never share your private keys or login details with anyone.
3. Use Reputable Platforms
Always use reputable exchanges and trading platforms when buying or selling cryptocurrencies. Stick to platforms with a strong track record of security and customer support. Avoid platforms that don’t provide sufficient information or seem unprofessional.
4. Enable Two-Factor Authentication (2FA)
Use two-factor authentication (2FA) on your crypto accounts to add an extra layer of security. This will require a second form of identification (such as a code sent to your phone) when logging in, making it more difficult for hackers to gain access to your account.
5. Keep Your Private Keys Secure
Your private keys are the keys to your cryptocurrency wallet. Never share them with anyone, and store them in a secure location. Use hardware wallets or other secure methods to keep your keys safe from hackers.
Conclusion
Crypto scams are a growing problem in the world of digital finance, and unfortunately, many individuals fall victim to these fraudulent schemes. However, crypto scam recovery experts offer hope to those who have lost their funds. Through advanced tracking methods, legal action, and expert guidance, these professionals can help victims recover their stolen assets and navigate the complex recovery process.
By following basic security practices and being aware of the common types of scams, you can protect yourself from falling prey to scammers. Remember, if you do fall victim to a crypto scam, don’t give up hope. Crypto scam recovery experts are available to help you recover your funds and hold the perpetrators accountable. Crypto scam recovery experts can assist in recovering lost funds by utilizing advanced tracking methods and working with law enforcement to trace stolen assets, as detailed on https://fiordintel.net/.
0 notes
Text
Top Benefits of Using CNC Machining Services
In the world of modern manufacturing, precision, speed, and efficiency have become paramount. To meet these demands, many industries have turned to CNC machining services as their go-to solution for producing high-quality parts and components. CNC, or Computer Numerical Control, machining revolutionizes the way products are made by automating the manufacturing process through computer-controlled machinery. This technology not only enhances accuracy but also allows for intricate designs that would be nearly impossible to achieve by hand.
Traditional machining methods, though reliable in their time, often involved a lot of manual labor, human error, and slower production rates. With CNC machining, these limitations are significantly reduced or eliminated. The seamless integration of computers in the machining process has transformed production lines, improving consistency and productivity while reducing costs. This article will dive into the top benefits of using CNC machining services, highlighting why they are indispensable in today’s manufacturing landscape.
When it comes to advanced manufacturing techniques, cnc machining services stand out for their precision and reliability. These services allow manufacturers to create components with exceptional accuracy, which is crucial for industries such as aerospace, automotive, medical devices, and electronics. CNC machines operate using pre-programmed software that guides cutting tools with pinpoint accuracy, ensuring each part meets exact specifications. This level of precision surpasses manual machining and minimizes defects that could lead to costly reworks.
Moreover, CNC machining provides unparalleled consistency and repeatability. When producing a large batch of parts, it’s essential that each piece is identical to maintain quality standards and ensure seamless assembly. CNC machines excel at this because they follow the same programmed instructions for every run, eliminating variability caused by human factors. This consistency is a massive advantage for manufacturers who require uniformity in their products to maintain brand reputation and customer satisfaction.
Another standout benefit of CNC machining services is the speed and efficiency they offer. Unlike manual machining, which depends heavily on operator skill and time, CNC machines can work continuously and complete complex tasks in a fraction of the time. The automation reduces the need for frequent adjustments and allows for faster turnaround times. This efficiency not only accelerates the manufacturing process but also helps companies meet tight deadlines and respond quickly to market demands.
Versatility is yet another reason CNC machining is widely favored. These machines can handle a broad range of materials—from metals like aluminum, steel, and titanium to plastics and composites. This adaptability makes CNC machining services applicable across multiple sectors, providing solutions for everything from heavy-duty industrial parts to delicate medical instruments. The ability to switch between materials without compromising precision enhances operational flexibility and opens doors for innovative product development.
CNC machining also shines when it comes to producing complex designs. Manual machining often struggles with intricate shapes, tight tolerances, and detailed geometries. CNC machines, on the other hand, use sophisticated software to carve out complex patterns with ease. This capability not only expands the creative possibilities for engineers and designers but also reduces the need for multiple manufacturing steps, thereby saving time and money.
From a financial perspective, CNC machining is highly cost-effective. While the initial investment in CNC machinery might be significant, the long-term savings are considerable. Automation reduces labor costs by minimizing the need for manual intervention and supervision. Additionally, the precision of CNC machines means less material waste, lowering overall production expenses. The combination of these factors results in improved profitability for businesses that incorporate CNC machining into their processes.
The automation and control inherent in CNC machining services also help minimize human error, which is a common challenge in traditional manufacturing. Human mistakes can lead to defective parts, delays, and increased costs. CNC technology reduces this risk by executing tasks exactly as programmed without deviation. This leads to higher product quality, fewer defects, and enhanced reliability—a win-win for both manufacturers and customers.
Safety is another critical advantage of CNC machining. Operating traditional machinery often involves exposure to sharp tools and moving parts, increasing the risk of accidents. CNC machines operate within enclosed environments, and much of the process is automated, which significantly reduces the chance of injury to operators. This safer work environment contributes to better employee wellbeing and fewer workplace disruptions.
Scalability and flexibility are key strengths of CNC machining services. Whether a company needs a single prototype or thousands of units, CNC machines can handle varying production volumes with minimal adjustment. Moreover, design changes can be easily implemented by updating the software program without altering the physical setup drastically. This responsiveness allows manufacturers to adapt quickly to changing customer needs and market trends, keeping them competitive and agile.
The integration of CNC machining with modern technologies such as CAD (Computer-Aided Design) and CAM (Computer-Aided Manufacturing) systems further enhances its advantages. These tools allow seamless transition from design to production, minimizing errors and accelerating the manufacturing timeline. As technology evolves, CNC machining services continue to improve, offering even greater precision and efficiency, which future-proofs manufacturing operations against upcoming challenges.
From an environmental standpoint, CNC machining offers several benefits. The precision of CNC cuts reduces waste by optimizing material usage, which helps conserve resources. Additionally, CNC machines are generally more energy-efficient than older manual equipment, contributing to lower carbon footprints. These eco-friendly aspects align well with growing global demands for sustainable manufacturing practices.
In conclusion, the benefits of using CNC machining services are vast and compelling. From precision and speed to cost savings and environmental impact, CNC machining has transformed manufacturing for the better. Businesses looking to improve product quality, enhance efficiency, and remain competitive should strongly consider integrating CNC machining into their operations. As industries continue to innovate, CNC technology will undoubtedly play a pivotal role in shaping the future of manufacturing.
0 notes
Text
Step-by-Step Guide to Mastering Active Directory Pentesting Techniques

Active Directory (AD) is the backbone of almost every modern corporate IT environment. It stores all critical user and system information and governs access across an enterprise. With its central role in network infrastructure, it also becomes a prime target for attackers. That’s why mastering Active Directory pentesting techniques is crucial for cybersecurity professionals who want to stay ahead of threats.
This blog walks you through a positive, step-by-step guide to becoming proficient in Active Directory pentesting. Whether you're a beginner or looking to sharpen your skills, these insights and tips will set you on the right path.
1. Understand the Basics of Active Directory
Before diving into pentesting, you need a solid understanding of what Active Directory is and how it functions. Active Directory is essentially a directory service that manages user data, authentication, and access permissions in a networked environment.
Start by learning about the core AD components:
Domain Controllers
Users and Groups
Organizational Units (OUs)
Group Policy Objects (GPOs)
Trusts and Forests
Having a strong grasp of these elements lays the groundwork for effective pentesting. Without understanding the architecture and how it operates, it’s nearly impossible to identify potential weaknesses or attack vectors.
2. Set Up a Lab Environment
The best way to learn AD pentesting is through hands-on practice. Set up a lab environment where you can safely explore and test your skills without risking real systems. Use virtual machines to simulate a Windows domain environment with various user roles and permissions.
In this lab, practice key AD functions like:
Creating users and groups
Applying Group Policies
Configuring Domain Controllers
Simulating common configurations
This setup helps you understand what’s considered “normal” behavior in AD, making it easier to spot and exploit vulnerabilities during a pentest.
3. Learn the Attack Surface of Active Directory
Once you're comfortable with the basics, it's time to explore how attackers view Active Directory. The AD attack surface is vast. From misconfigured permissions to outdated patches, there are numerous paths an attacker might take.
Common AD attack vectors include:
Password Spraying
Kerberoasting
Pass-the-Hash
NTLM Relay Attacks
DLL Injection
Credential Dumping
Each of these techniques targets a specific AD weakness, and knowing them is vital for both red teamers and defenders. Familiarize yourself with these vectors in your lab to see how they work and how they can be mitigated.
4. Master Enumeration Techniques
In AD pentesting, enumeration is one of the most critical initial phases. This is where you gather information about the target network without triggering alarms. The more intel you have, the more precise your attacks will be.
Key enumeration tasks include:
Listing domain users and groups
Identifying admin accounts
Mapping network shares
Discovering service accounts and permissions
Tools and scripts can help with enumeration, but the knowledge of what data to look for and how it can be used is what separates beginners from experts.
5. Understand Privilege Escalation Methods
Once you’ve successfully enumerated a domain and identified weak points, the next step in pentesting is privilege escalation. This phase focuses on moving from a regular user account to higher privileges, ideally reaching domain admin status.
Common privilege escalation techniques include:
Exploiting misconfigured service permissions
Abuse of Group Policy Preferences
Exploiting token impersonation
Over-permissioned Active Directory Delegation
Practicing these in a safe environment helps you develop intuition for privilege misconfigurations and how to use them to your advantage in a pentest.
6. Learn Lateral Movement Strategies
After escalating privileges, attackers often move laterally across systems to expand access and maintain persistence. As a pentester, understanding and practicing lateral movement techniques is key to assessing how far a compromise can go.
Typical lateral movement tactics involve:
Remote Desktop Protocol (RDP)
Windows Management Instrumentation (WMI)
PsExec
SMB and PowerShell remoting
Each method can be used to pivot from one machine to another, and each leaves specific traces. Being proficient in these strategies helps you mimic real-world attack paths and understand how to detect them.
7. Explore Credential Access and Dumping
One of the most sensitive areas in AD pentesting is credential dumping—extracting usernames and passwords from memory or files. This technique is powerful because it can provide direct access to high-value accounts.
Tools often target:
LSASS process memory
SAM database
Cached credentials
Registry hives
It's vital to practice this responsibly. In your lab, you’ll see how easy it is for a determined attacker to get credentials and why protecting this area is so crucial for security teams.
8. Study Persistence Mechanisms
Attackers who gain control of AD often seek to maintain long-term access. Learning persistence mechanisms helps you understand how an attacker could stay hidden in a network even after reboots or password changes.
Some common persistence techniques include:
Backdooring Group Policies
Modifying user attributes
Planting scheduled tasks
Creating rogue trust relationships
By studying these, you’ll become skilled at identifying traces left behind and designing better defensive strategies for detection and removal.
9. Simulate Realistic Attack Chains
It’s one thing to know individual techniques—it’s another to chain them together into a realistic attack scenario. Practicing full attack paths from initial access to domain admin gives you a comprehensive view of how real-world breaches unfold.
Example scenarios to try in your lab:
Compromising a low-privileged user → Kerberoasting → Privilege escalation → Lateral movement → Domain admin
Exploiting an exposed service → Dumping credentials → Creating persistence
Simulating these chains strengthens your situational awareness and helps you think like an attacker planning a complete campaign.
10. Practice Blue Team Countermeasures
Even though your focus is on pentesting, understanding how defenders operate makes you a better attacker. Try to detect your own attacks using security monitoring tools, logs, and behavior analytics.
Ask yourself:
What logs are generated during this attack?
How could a security team detect this movement?
What could block or alert on this technique?
This dual perspective is incredibly valuable in professional settings, where many pentesters also offer remediation advice post-assessment.
11. Document Your Findings Professionally
Pentesting isn’t just about breaking things—it’s about clearly communicating what you found and how to fix it. Learning to write detailed, organized, and actionable reports is essential.
A great report includes:
Executive summary for non-technical stakeholders
Technical breakdowns of each finding
Screenshots and proof-of-concept evidence
Remediation recommendations
Practice writing reports after each lab or simulation. It’s a skill that makes you stand out and shows you can deliver value beyond just identifying issues.
12. Stay Updated with New Techniques
Cybersecurity is always evolving, and so are the tactics used to breach Active Directory. Following security blogs, online communities, and research papers helps you stay on top of the latest developments.
Also, make sure to revisit your lab regularly and test out newly discovered vulnerabilities or techniques. The more proactive you are, the sharper your skills become.
For a structured and comprehensive approach to Active Directory pentesting, many learners have benefited from training like https://academy.cyberyozh.com/courses/active-directory/.
13. Test Yourself with Capture The Flag (CTF) Challenges
Once you're confident in your skills, put them to the test with CTF-style challenges. These simulations present realistic AD scenarios with hidden “flags” that you must uncover using your pentesting knowledge.
CTFs are fun, competitive, and immensely educational. They also help you benchmark your progress and identify areas to improve.
14. Network with the Community
No one masters pentesting alone. Engage with cybersecurity communities where you can exchange ideas, ask questions, and learn from others’ experiences. Forums, discussion groups, and meetups are great places to stay inspired and informed.
Surrounding yourself with like-minded individuals also opens doors to mentorship, collaboration, and even job opportunities in ethical hacking and red teaming.
15. Keep Practicing and Repeating
Mastery comes with repetition. Go back to earlier steps, rebuild your lab with new configurations, and keep exploring. Every iteration will sharpen your instincts and deepen your expertise.
Remember, the goal isn’t just to pass tests or run tools—it’s to think critically, adapt quickly, and understand the full picture of securing an Active Directory environment.
Conclusion
Active Directory pentesting is a skill set that demands a balance of technical knowledge, practical experience, and a security-first mindset. By following this step-by-step guide, you’ll build a strong foundation in the core techniques that attackers use—and defenders must prepare for.
From setting up a lab and understanding enumeration, to mastering privilege escalation and lateral movement, each step brings you closer to becoming a proficient AD pentester. Keep practicing, stay curious, and always think a step ahead. The more you hone your skills, the more valuable you become in protecting today’s digital environments.
0 notes
Text
How to Get a Loan with a Credit Rating of 400? A Step-by-Step Guide

Having a low credit score can feel like a huge barrier when trying to secure a loan, but the reality is that you can still get access to funds, even with a credit rating of 400. A credit score that low indicates a history of missed payments, defaults, or other negative marks, but it's not an automatic roadblock. Many individuals find themselves in this position due to unforeseen circumstances, such as medical emergencies or job losses, and still need access to loans. If you’re wondering how to navigate this process, you're in the right place. In this step-by-step guide, we’ll discuss how to increase your chances of getting approved for a loan with a low credit score, and what steps you can take to secure the financial assistance you need.
Understanding Your Credit Rating
Before diving into the ways to secure a loan with a credit rating of 400, it's essential to understand what that number really means. Credit scores typically range from 300 to 850, and a score of 400 is considered poor. Lenders use this score to assess your creditworthiness, or how likely you are to repay a loan. A score of 400 indicates that you have a high risk of defaulting on payments. This doesn’t necessarily mean that you are unable to get a loan; it just means that you’ll have to be more strategic and take some additional steps to make yourself a more attractive borrower.
To get a better idea of your financial health, you can review your credit report. Look for errors, identify any outstanding debts, and assess how you can improve your credit score in the future. While your goal may be to improve your credit score, it’s still possible to secure a loan with a credit rating of 400 by taking a few key steps.
Step 1: Start by Understanding Your Loan Options
When you have a credit score of 400, not all types of loans will be available to you. Traditional financial institutions, like banks or credit unions, are less likely to approve loans for individuals with such a low score. However, there are still options to explore, including personal loans, payday loans, and even alternative lenders who are more willing to work with individuals who have low credit scores.
Additionally, you could consider other forms of borrowing, such as using a co-signer, offering collateral, or opting for a secured loan. Each of these options presents its own risks and benefits, so it’s important to weigh your options carefully and choose the path that best fits your financial situation and needs.
For example, a secured loan requires you to put up an asset, such as a vehicle or property, as collateral to secure the loan. This reduces the lender’s risk and may make them more likely to approve your loan, even if you have a low credit score. However, be cautious—if you fail to repay the loan, the lender may seize your asset.
Step 2: Explore Alternative Lenders and Online Platforms
If you're struggling with traditional lenders due to your low credit score, alternative lenders may be your best option. Online lending platforms often have fewer strict requirements and are more willing to work with borrowers who have poor credit histories. They may also offer more flexible terms, allowing you to customize your repayment plans.
These online platforms may provide loans with higher interest rates, but they could still be a viable option if you need funds quickly. It’s crucial to compare different offers from alternative lenders and ensure you understand the terms, including the interest rate, repayment period, and any fees that may be attached to the loan.
If you are considering an online loan, be sure to read reviews of the platform and ensure they are reputable. Online loans with a credit rating of 400, for example, can sometimes come with hidden fees, so be diligent in your research.
Step 3: Consider Peer-to-Peer Lending
Peer-to-peer (P2P) lending platforms are another option for individuals with low credit scores. These platforms connect borrowers with individual investors who are willing to fund personal loans. The benefit of P2P lending is that the investors may be more flexible in terms of credit score requirements, and they might be willing to take on a bit more risk than traditional lenders.
On P2P platforms, the loan approval process is often faster, and the rates can sometimes be more competitive. However, as with any loan, it's important to ensure you’re fully aware of the terms and obligations. Remember that while P2P lending can be a good option, it might come with higher interest rates and fees, so make sure to review all of the fine print before committing.
If you're in need of a loan but worried about your credit rating, a займ с кредитным рейтингом 400 may be an option worth exploring. This type of loan is specifically tailored for individuals with low credit scores, offering them a chance to access the funds they need while dealing with poor credit. It's a suitable option when more traditional routes aren't available to you, but it’s essential to shop around and find the best rates.
Step 4: Consider a Co-Signer
A co-signer can significantly improve your chances of getting approved for a loan. A co-signer is someone with better credit who agrees to take on responsibility for the loan in case you fail to make payments. Lenders see the co-signer as a form of security, knowing that the loan will still be repaid even if you default.
Having a co-signer can not only improve your chances of approval but also help you secure better loan terms, such as a lower interest rate. However, asking someone to co-sign a loan is a big ask. It’s important to consider the potential impact on your relationship and the co-signer’s financial situation. Make sure that both parties fully understand the responsibilities before proceeding with this option.
Step 5: Offer Collateral for a Secured Loan
If you have valuable assets like a car or property, offering collateral could be an excellent option to secure a loan with a low credit score. With a secured loan, the lender has the right to seize the collateral if you fail to repay the loan. This significantly reduces their risk, making them more likely to approve your application, even with a poor credit history.
Secured loans typically come with lower interest rates compared to unsecured loans, making them an attractive option for borrowers with low credit scores. However, keep in mind that putting up collateral means risking your valuable assets. If you're unable to make the required payments, the lender may take your collateral to recoup their losses.
Step 6: Be Prepared for Higher Interest Rates
When you have a credit rating of 400, it’s important to understand that the loan you’re offered will likely come with higher interest rates. Lenders see you as a higher risk, so they charge more to offset the potential for default. While it’s disappointing to face higher rates, this is a reality that many borrowers with low credit scores must navigate.
To ensure that you’re not overwhelmed by the interest rates, try to shop around for the best deal. Compare offers from various lenders, and see if you can negotiate better terms. You might also want to consider borrowing smaller amounts that you’re confident you can repay quickly, reducing the total amount of interest you’ll pay over time.
Step 7: Improve Your Credit Score
Even if you need a loan now, it’s always a good idea to start working on improving your credit score. Although this won’t help you immediately secure a loan, it will increase your chances of getting approved for better terms in the future. Focus on paying down outstanding debts, avoiding missed payments, and regularly checking your credit report for any errors.
Improving your credit score can take time, but every small step counts. The higher your score, the more loan options you will have available to you in the future, and the better the terms will be.
Conclusion
Getting a loan with a credit rating of 400 is not an impossible task, but it requires a bit more effort and strategy. By understanding your loan options, considering alternative lenders, exploring co-signer options, or offering collateral, you can significantly improve your chances of approval. It’s also important to be prepared for higher interest rates and to always shop around for the best deals. Most importantly, continue working on improving your credit score to increase your financial flexibility and access to better loan terms in the future.
0 notes
Text
Unlock Greater Control and Security with an On-Premise CRM

In today’s business environment, managing customer relationships and sensitive data is more important than ever. Companies across industries are seeking solutions that allow them to stay competitive, enhance productivity, and secure sensitive customer data. One such solution that offers greater control and security is an on-premise customer relationship management (CRM) system. Unlike cloud-based alternatives, on-premise CRMs are hosted directly within an organization's infrastructure, providing enhanced customization options, better security, and full control over the system.
In this blog, we will explore the key benefits of using an on-premise CRM, including the heightened security, control, and customization it provides. We will also address how this CRM type ensures that your data remains in safe hands while offering scalability to meet your organization's needs.
1. Full Control Over Your Data
One of the most significant advantages of using an on-premise CRM is the ability to have complete control over your company’s data. When you use a cloud-based CRM, your data is stored on external servers maintained by the service provider. While this may seem secure, you are essentially trusting an external company to protect your sensitive business data. With an on-premise CRM, however, all data is stored within your organization's infrastructure, giving you full control over who has access to it and how it is managed.
This level of control ensures that your data remains within your premises, reducing the risk of breaches due to third-party vulnerabilities. For businesses dealing with highly sensitive data, such as healthcare, finance, or legal sectors, having this control is non-negotiable.
2. Enhanced Security Measures
Security is always a top concern for businesses dealing with customer information. An on-premise CRM gives your organization the power to implement advanced security protocols that are tailored to your specific needs. You can install firewalls, encryption systems, and access control mechanisms that suit your internal security requirements. Additionally, because the system is housed within your own premises, you can closely monitor and control access, ensuring that only authorized personnel are able to interact with critical business data.
Another key security feature of an on-premise CRM is the ability to conduct regular security audits. You can continuously review your system's vulnerabilities and patch any potential weak spots before they become an issue. This level of proactive security control helps mitigate the risk of cyber-attacks and data breaches, offering peace of mind for both businesses and customers alike.
3. Customization and Flexibility
Every business operates differently, and what works for one may not work for another. An on-premise CRM provides greater flexibility and customization than its cloud counterparts. With an on-premise system, you can adapt the software to suit your unique business processes and workflows. From the user interface to the integration of third-party tools, the system can be tailored to meet your specific needs, ensuring it supports your operational goals.
The level of customization available allows you to design a CRM that aligns perfectly with your company’s objectives. Whether you need specific reports, customer service workflows, or integration with legacy systems, an on-premise CRM offers a higher degree of flexibility to meet these requirements. This customization empowers you to optimize the CRM for your team, ensuring they have all the tools they need to maximize their efficiency and improve customer relationships.
4. Compliance and Regulatory Adherence
Different industries are bound by varying compliance regulations regarding data management and protection. For example, the healthcare sector is governed by laws such as HIPAA, while financial organizations are subject to strict regulations on customer data handling. When choosing a CRM system, it's crucial to ensure that the platform meets the necessary regulatory standards for your industry.
An on-premise CRM allows you to maintain compliance with these laws more easily. You have the ability to implement the exact security measures required to meet industry regulations and audit requirements. Furthermore, by keeping your data on-site, you avoid potential data sovereignty issues that can arise with cloud-based systems. This ensures that your business remains compliant with industry standards, protecting both your company and your customers.
5. Improved Performance and Speed
When using a cloud-based CRM, the speed and performance of the system can be affected by several factors, such as internet speed, cloud server performance, or the geographic location of the server. However, with an on-premise CRM, the system is hosted within your organization’s own infrastructure, which generally ensures faster processing times and more reliable performance.
Because all data is stored locally, your team can access and update the CRM system without being affected by external factors like server latency or internet connection issues. This leads to better overall efficiency, particularly for organizations that require a high level of data processing and need their CRM to perform at optimal speeds throughout the day.
6. Cost-Effectiveness Over Time
While the initial investment in an on-premise CRM may be higher than opting for a cloud-based alternative, many businesses find it to be more cost-effective in the long run. Cloud-based systems typically involve recurring subscription fees that can add up over time. On the other hand, an on-premise CRM is a one-time investment, and once it's installed, you won’t have to worry about ongoing monthly or yearly costs.
Additionally, because the on-premise CRM is hosted within your own infrastructure, there are fewer ongoing costs for bandwidth and server usage. Many organizations also find that once the system is up and running, it significantly reduces the costs associated with downtime, slow performance, or connectivity issues that can arise with cloud-based systems.
7. Scalability for Future Growth
As your business grows, your CRM system needs to be able to scale to accommodate the increasing volume of data and users. On-premise CRMs are highly scalable, as they can be easily expanded to meet the demands of a growing business. Whether you need more storage, additional users, or more powerful processing capabilities, on-premise systems can be upgraded to meet these needs without the limitations of cloud storage or bandwidth restrictions.
With cloud-based CRMs, scalability may involve additional fees, and there might be limitations on how much you can scale depending on the provider's infrastructure. In contrast, on-premise CRMs offer greater flexibility and cost efficiency when it comes to scaling your system to meet future requirements.
8. Independence from Third-Party Service Providers
Using a cloud-based CRM often means depending on a third-party provider for system maintenance, uptime, and support. If your CRM provider experiences an outage, your business could be left in the dark. However, with an on-premise CRM, you are not reliant on a third party to ensure the system is running smoothly. This gives you more control over when updates are applied, when maintenance occurs, and how the system is managed.
Moreover, on-premise systems can provide more transparency when it comes to handling support issues. You have direct access to your IT team or third-party contractors, allowing you to resolve issues faster without waiting for external support.
9. Streamlined Data Backup and Disaster Recovery
Disaster recovery planning is crucial for any business. Whether it's a natural disaster, hardware failure, or cyber-attack, businesses need to have a solid plan in place to recover from data loss. With an on-premise CRM, you have the ability to create and implement your own backup and disaster recovery protocols. This means you can ensure that your data is regularly backed up and stored in secure locations, ready to be recovered in the event of a disaster.
Moreover, with an on-premise CRM, you can maintain control over how often backups are conducted and where the backup data is stored, giving you peace of mind knowing that critical business information is protected.
For more information on how an on-premise CRM can enhance your business operations, visit https://alexv.pro/en/catalog/bitrix24-crm/on-premise/.
10. Seamless Integration with Legacy Systems
Many businesses have legacy systems that they rely on to carry out critical processes. Integrating new technologies with older systems can be a challenging task, especially when those systems were not designed to communicate with modern software. On-premise CRMs offer better integration options with legacy systems because they are hosted within your own infrastructure, allowing for more customization and flexibility when it comes to data exchanges.
With an on-premise CRM, you can ensure that it integrates smoothly with your existing tools, minimizing the disruptions that often come with transitioning to new systems.
Conclusion: The Future of CRM Systems
In conclusion, an on-premise CRM provides numerous advantages for businesses looking for greater control, security, and customization. From enhanced data security to the ability to integrate with legacy systems, on-premise solutions offer the flexibility and scalability needed for modern businesses. While the initial setup costs may be higher, the long-term benefits in terms of performance, compliance, and cost-effectiveness make it a worthy investment. As businesses continue to prioritize data security and control, on-premise CRMs will undoubtedly remain a key solution for those looking to unlock greater value from their customer relationship management systems.
0 notes
Text
What You Need to Know About Canadian Criminal Law

Canadian criminal law is a critical part of the country's justice system, ensuring that laws are enforced to protect the rights and safety of its citizens. With a focus on fairness, equality, and respect for individual rights, the system seeks to balance the need for justice with the protection of civil liberties. Understanding the basics of Canadian criminal law can help individuals make informed decisions should they ever find themselves involved in legal matters.
An Overview of Criminal Law in Canada
Criminal law in Canada is designed to deter criminal behavior and promote a safe, orderly society. It covers a wide range of offenses, from minor infractions to serious crimes such as theft, assault, and murder. The foundation of criminal law in Canada is based on the Criminal Code of Canada, which outlines the offenses, procedures, and penalties associated with criminal activity.
In Canada, criminal offenses are classified into three categories: summary offenses, indictable offenses, and hybrid offenses. Summary offenses are less serious crimes, and the penalties are usually lighter, such as fines or short prison sentences. Indictable offenses are more severe crimes, such as murder or robbery, and they carry harsher penalties, including longer prison sentences. Hybrid offenses are crimes that can be prosecuted either as a summary or indictable offense, depending on the circumstances of the case.
The Role of Lawyers in Canadian Criminal Law
When facing criminal charges, it’s essential to understand the role of canada lawyer in the legal process. A criminal lawyer in Canada provides crucial legal advice and representation to individuals accused of committing crimes. Whether someone is facing a minor offense or a serious criminal charge, having an experienced lawyer by their side can make a significant difference in the outcome of the case.
A criminal defense lawyer’s role is to assess the evidence, provide legal counsel, and represent their client in court. Lawyers specializing in criminal law have a deep understanding of the Canadian legal system and work to ensure that their clients' rights are protected throughout the legal process. They can help negotiate plea deals, represent clients during trials, and, in some cases, appeal convictions if there has been an error in the trial process.
In addition to defending individuals accused of crimes, a Canada lawyer can also help victims of crime navigate the legal system. Whether it's providing support in filing charges or helping with victim impact statements, a criminal lawyer can assist in ensuring that justice is served for those harmed by criminal activity.
Understanding Criminal Offenses in Canada
The Canadian Criminal Code defines a wide range of offenses, and understanding the types of crimes that fall under its jurisdiction is essential for anyone interacting with the legal system. The following are some of the main categories of criminal offenses in Canada:
1. Property Crimes
Property crimes involve offenses that result in the destruction, theft, or damage of property. Some common examples include:
Theft: Stealing someone's property, whether it's physical goods or intellectual property.
Vandalism: Deliberately damaging someone else's property.
Burglary: Entering a building with the intent to commit a crime, usually theft.
Property crimes may be prosecuted as either summary or indictable offenses, depending on the value of the property stolen or damaged.
2. Violent Crimes
Violent crimes in Canada include offenses that cause physical harm to individuals. These offenses carry serious penalties, as they often result in lasting harm to victims. Examples of violent crimes include:
Assault: This can range from minor physical contact to more severe forms, like aggravated assault that causes significant injury.
Murder: The unlawful killing of another person, classified as either first-degree (planned and deliberate) or second-degree (unplanned but intentional).
Domestic violence: Crimes involving violence in intimate relationships, such as spousal abuse or child abuse.
What Happens If You're Charged with a Crime in Canada?
If you are charged with a crime in Canada, the legal process begins with your arrest and booking. After an arrest, the accused has the right to remain silent and the right to an attorney. The Criminal Code of Canada ensures that an individual’s rights are upheld during the legal proceedings. In most cases, a person charged with a crime will appear in court, where the charges are read, and bail may be considered.
If you’re facing criminal charges, it is vital to get in touch with a canada lawyer as soon as possible. Your lawyer will help guide you through the entire legal process, including:
Preliminary hearing: A judge will decide if there is enough evidence to proceed with a trial.
Trial: The case will be heard in court, where the defense and prosecution will present their arguments.
Sentencing: If convicted, the judge will impose a sentence based on the severity of the crime.
Penalties and Sentences in Canadian Criminal Law
Sentences for criminal offenses in Canada vary widely based on the nature and severity of the crime. The criminal justice system aims to balance the need for punishment with the goal of rehabilitation. Some common forms of penalties include:
Fines: A financial penalty paid to the government.
Probation: A period during which the offender must comply with certain conditions set by the court.
Imprisonment: Incarceration in a jail or prison, depending on the seriousness of the crime.
Restitution: The offender may be required to compensate the victim for their loss or injury.
For more severe crimes, such as murder or large-scale drug trafficking, the sentences can be life imprisonment, sometimes with the possibility of parole after serving a set number of years.
Defending Criminal Charges in Canada
Defending against criminal charges in Canada can be a complex and nuanced process. A skilled criminal defense lawyer can develop a strategy tailored to the unique circumstances of the case. Common defenses include:
Self-defense: Arguing that the defendant acted to protect themselves from imminent harm.
Alibi: Providing evidence that the defendant was not at the scene of the crime.
Lack of intent: Showing that the defendant did not have the mental state required to commit the crime.
Mistake of fact: Claiming that the defendant was unaware of certain facts, which led to the commission of the crime.
In some cases, a lawyer may also negotiate a plea bargain with the prosecution to reduce the charges or penalties.
The Importance of Understanding Criminal Law in Canada
Navigating Canadian criminal law can be overwhelming, especially for those who have never been involved in the legal system. However, understanding the basics can help individuals know what to expect and what steps to take if they find themselves in a legal bind. For instance, https://www.canadalawlist.com/ provides a directory of experienced lawyers who can guide individuals through the complexities of the legal process.
It's essential to take criminal charges seriously and seek legal advice promptly. The outcome of a criminal case can have far-reaching consequences, affecting one’s freedom, reputation, and future. By working with an experienced lawyer, individuals can better understand their rights and the options available to them.
Conclusion
Canadian criminal law is designed to maintain public safety while ensuring fairness and justice for all individuals involved. Understanding the legal process, the types of offenses, and the importance of legal representation can make a significant difference in the outcome of a case. Whether you are a victim of crime or facing criminal charges, a knowledgeable lawyer can guide you through the process and help you navigate the complexities of the Canadian justice system.
0 notes
Text
Unlocking TikTok’s Potential: How to Drive Massive Views to Your Content

TikTok has rapidly become one of the most influential platforms in the world of social media. Whether you're a creator, business, or simply someone who enjoys sharing moments, the potential to reach millions of viewers is tantalizing. But how do you make your content stand out in a sea of videos? How can you drive massive views to your TikTok content?
In this article, we’ll explore actionable strategies to help you grow your TikTok presence, increase views, and ultimately unlock the platform’s full potential.
1. Understanding TikTok’s Algorithm: The Key to Massive Views
Before diving into strategies, it's essential to understand how TikTok’s algorithm works. Unlike other social media platforms, TikTok focuses heavily on engagement, making it relatively easier for new accounts to gain visibility. The key factors influencing the algorithm include:
Engagement: Likes, comments, and shares are crucial in determining the success of your content.
Watch Time: Videos that are watched in their entirety or even looped are more likely to be pushed to a wider audience.
Relevance: TikTok tailors content based on user behavior, so if your video resonates with a particular group, the platform will continue recommending it.
By understanding these basic principles, you can better optimize your content to match what the algorithm favors. The more engagement your videos get, the higher the chances they’ll be shown to a larger audience.
2. Create Attention-Grabbing Content from the Start
The first few seconds of your video are critical. TikTok is a platform designed for fast consumption, and if your video doesn’t hook viewers instantly, they’ll likely scroll away. Here’s how you can create videos that grab attention from the start:
Start with a bang: Begin with an exciting or intriguing moment. This could be a question, a surprising fact, or a visual element that sparks curiosity.
Use captions: Many users watch TikTok with the sound off, so captions help ensure your message gets across even without audio. Make sure the text is clear and impactful.
Keep it short and sweet: While you can post longer videos, TikTok thrives on short-form content. Aim for snappy, quick videos that maintain the audience's interest.
When crafting your content, make sure to keep your target audience in mind. Understanding who you’re trying to reach and what resonates with them will improve your chances of getting noticed.
3. Leverage Trending Sounds and Hashtags
TikTok’s trending sounds and hashtags are powerful tools for boosting your visibility. By tapping into trends, you align your content with what is currently popular, and TikTok is more likely to feature your videos on users' "For You" page.
Use trending sounds: Sounds are an integral part of TikTok culture. If a particular sound is gaining traction, consider creating content around it. But don’t just jump on trends blindly—ensure your content still aligns with your style and message.
Hashtags matter: Using relevant and trending hashtags increases the chances of your content being discovered. However, don't just use popular hashtags for the sake of it. Select hashtags that genuinely describe your content to ensure the right audience sees your video.
By consistently using trending sounds and relevant hashtags, your videos are more likely to appear in users’ feeds, boosting your overall reach and engagement.
4. Engage with Your Audience
TikTok is a highly interactive platform, and the more you engage with your audience, the more likely they are to engage back. Interactions build a community around your content and keep viewers coming back for more.
Reply to comments: Take the time to respond to comments on your videos. This not only increases your engagement rate but also fosters a deeper connection with your followers.
Host challenges or Q&A sessions: Encourage your audience to participate in challenges or ask questions. The more interactive your content is, the more likely it will go viral.
Collaborate with other creators: TikTok thrives on collaboration. Partnering with other creators, whether in a duet or a stitch, exposes your content to their followers, which can dramatically increase your views.
Engagement is a two-way street, and by nurturing your audience relationships, you can create a loyal community that supports your content long-term.
5. Optimize Your Posting Time
Timing is everything when it comes to TikTok. Posting at the right time can significantly impact the performance of your videos. Each audience has peak hours when they are most active, and posting during these times ensures that your content has the maximum potential to be seen.
To determine the best times to post:
Analyze your audience: Look at when your followers are most active. TikTok provides insights that help you understand when your content performs best.
Experiment: Test different posting times and track the results. Over time, you'll identify patterns that allow you to post when your audience is most engaged.
Timing your posts carefully ensures that your content doesn't get lost in the shuffle and is seen by as many people as possible.
To learn more about strategies for increasing views on TikTok, check out this insightful guide https://www.foxy-it.com.ua/blog/kak-nabrat-mnogo-prosmotrov-v-tiktok/.
6. Focus on Quality Over Quantity
In the race for views, many creators believe that posting multiple times a day is the key to success. While consistency is important, quality should always come first. Posting too often just for the sake of posting can lead to content that feels rushed or low-effort, which can ultimately hurt your chances of gaining views.
High-quality production: Invest in good lighting, clear audio, and stable camera work. While TikTok doesn’t require professional-grade production, content that looks polished will naturally attract more viewers.
Attention to detail: Pay attention to your video’s pacing, editing, and overall composition. A well-edited video with smooth transitions is more likely to hold viewers' attention.
Quality content not only engages your current audience but also attracts new viewers. People come back for content that is well-crafted, entertaining, and visually appealing.
7. Be Authentic and Unique
TikTok users crave authenticity. It’s one of the platform’s defining features—people connect with creators who are real, relatable, and genuine. Instead of trying to replicate what others are doing, focus on showcasing your personality and bringing something unique to the table.
Show your true self: Don’t be afraid to be yourself, whether it’s quirky, funny, or raw. Authenticity builds trust and makes your content more relatable.
Bring a unique perspective: While trends are great, add your own twist. Think about how you can offer something fresh that others haven’t done before.
Being unique and true to yourself can set you apart in a sea of content, helping you create a loyal following.
8. Use Visual Effects to Enhance Your Content
TikTok offers a wide array of visual effects, filters, and transitions that can make your videos stand out. When used creatively, these effects can add a fun and dynamic element to your content, increasing its shareability.
Play with filters and effects: Experiment with TikTok’s built-in effects, transitions, and filters to make your videos more visually interesting.
Add text overlays: Use text creatively to emphasize points or add humor to your videos.
Creative visuals not only capture attention but also make your videos more entertaining, encouraging viewers to share them with others.
9. Analyze Your Performance Regularly
To continuously improve your TikTok strategy, it’s essential to track your performance. TikTok provides detailed analytics that can help you understand how well your videos are doing. By reviewing these insights, you can identify what works and what doesn’t.
Track engagement: Look at how many likes, comments, and shares your videos are getting. High engagement indicates that your content resonates with your audience.
Examine watch time: Videos with high watch time are more likely to be recommended to others. Make sure your content holds viewers’ attention.
Adjust your strategy: If you notice certain types of videos or topics perform better, focus more on those areas in your future content.
By analyzing your performance and adjusting accordingly, you can continuously optimize your content to increase views and grow your audience.
10. Be Consistent but Don’t Overwhelm Yourself
Consistency is key on TikTok. Posting regularly keeps you in front of your audience, but don’t feel pressured to post every hour of every day. It’s better to have a consistent schedule that allows you to create content at a pace you can maintain without burning out.
Set a realistic schedule: Whether it’s once a day or a few times a week, find a posting schedule that works for you and stick with it.
Take breaks when needed: If you need to take a short break, do so. Consistency is important, but quality content will always be your priority.
When you strike the right balance between consistency and quality, you’ll be able to maintain a strong presence without overwhelming yourself.
Conclusion: Unlocking the Power of TikTok
Driving massive views to your TikTok content doesn’t happen overnight, but by understanding the platform’s nuances and implementing these strategies, you can greatly increase your chances of success. From leveraging the algorithm to staying authentic and consistent, the possibilities are endless.
Embrace creativity, experiment with new formats, and most importantly, stay true to your unique voice. TikTok offers a wealth of opportunities for those who are willing to put in the effort, and by following these tips, you’ll be well on your way to unlocking your content's full potential.
0 notes
Text
Understanding the IPTV Subscription Model: What’s Included?

In the world of entertainment, we’ve seen traditional cable and satellite TV slowly being replaced by more modern and flexible options. One such option that has gained immense popularity in recent years is IPTV, or Internet Protocol Television. IPTV subscriptions offer viewers the ability to watch television shows, movies, sports, and more, all streamed over the internet. But what exactly is included in an IPTV subscription model, and how does it differ from traditional television services? Let’s explore the details.
What is IPTV?
IPTV stands for Internet Protocol Television. It delivers TV content through the internet, rather than through the traditional satellite or cable methods. This technology allows you to stream television shows, movies, live events, and even exclusive content directly to your device, whether it's a smart TV, tablet, phone, or computer. Unlike traditional TV services that rely on physical cables or satellites, IPTV simply requires an internet connection to work, which is a major advantage in terms of flexibility.
Types of IPTV Subscriptions
Before diving into what’s included in an IPTV subscription, it’s essential to understand that there are different types of IPTV services available. Broadly speaking, they fall into three categories:
Live IPTV: This allows users to watch live television broadcasts, much like you would with cable TV. It includes live news, sports, and entertainment channels.
Video on Demand (VOD): VOD IPTV services let you watch movies and TV shows whenever you want. This on-demand feature allows you to choose your content without being tied to a broadcast schedule.
Time-Shifted IPTV: This type of IPTV enables users to pause, rewind, or fast-forward live TV broadcasts. Essentially, it gives you the ability to watch programs at your convenience without missing any of the action.
Each type of subscription offers its unique benefits, so understanding which one best suits your needs is key to getting the most out of your IPTV service.
What’s Included in an IPTV Subscription?
Now that we’ve outlined the different types of IPTV, let’s delve into what is typically included in an IPTV subscription. These features can vary from provider to provider, but most IPTV services offer the following:
1. Access to a Wide Range of Channels
One of the major draws of IPTV subscriptions is the sheer number of channels available. With IPTV, you have access to channels from all over the world. Whether you're interested in sports, news, entertainment, or niche programming, IPTV offers a broad spectrum of options. Unlike traditional cable or satellite subscriptions, which are often limited by regional availability, IPTV gives you access to international content.
For example, you could be watching a popular TV show from the UK while living in the United States. This global reach makes IPTV an attractive option for people who want to expand their entertainment options and explore content from different countries.
2. Video on Demand (VOD)
As mentioned earlier, VOD is a significant feature of most IPTV services. With VOD, you have the freedom to watch movies and TV shows on your schedule. Whether you want to binge-watch an entire season of a show or catch up on the latest movies, you can do so without being tied to a fixed broadcast time.
The VOD library is typically vast, with everything from the latest blockbuster films to older, classic movies. Many IPTV providers also offer access to exclusive content, such as new releases and shows that might not be available through traditional TV channels.
3. Catch-Up TV
Catch-Up TV is another popular feature included in many IPTV subscriptions. This feature allows you to watch programs that you missed during their original broadcast. You can simply go to the channel’s section within the IPTV interface and watch episodes of your favorite shows that aired in the past week or month.
This is especially useful for people who have busy schedules or for those who live in different time zones and want to catch shows from a specific region. Catch-Up TV ensures that you never miss a show and gives you the flexibility to watch content at your own pace.
4. Live Sports and Events
For sports enthusiasts, IPTV services often provide access to live sports broadcasts from around the globe. Whether it's soccer, basketball, football, tennis, or even niche sports, IPTV services offer a wide range of live events. You can catch every goal, touchdown, or match point as it happens, no matter where you are.
Live sports coverage is one of the key reasons many people turn to IPTV. The high-definition streaming ensures that you don’t miss any details, and the convenience of watching on your preferred device makes it even more appealing. Additionally, you can often access replays, highlights, and even alternative broadcasts, such as commentary in different languages.
https://falconiptvpro.shop/ is one such example of an IPTV provider that specializes in delivering live sports channels to its subscribers, offering comprehensive coverage of various events.
5. DVR Functionality
Many IPTV services offer Digital Video Recording (DVR) functionality, which is another feature that sets it apart from traditional cable services. DVR allows you to record live TV and save it for later viewing. This is particularly useful if you're unable to watch a program as it's airing but don’t want to miss it entirely.
With DVR functionality, you can record multiple channels at the same time, which is perfect for households with diverse interests. Whether it's recording the latest news while you watch a live sports event or saving a documentary for later, DVR gives you full control over your viewing experience.
6. Multi-Device Support
Another major perk of IPTV subscriptions is the ability to stream content on multiple devices. Whether you’re at home or on the go, you can access your IPTV service from smartphones, tablets, laptops, and even smart TVs. Most IPTV providers offer dedicated apps for different devices, making it easy to enjoy content wherever you are.
This flexibility is particularly beneficial for people with busy lifestyles or for those who frequently travel. You’re no longer confined to your living room TV to watch your favorite shows—now, you can enjoy high-quality content wherever you have an internet connection.
7. Parental Controls
For families, parental controls are an essential feature. IPTV services typically come with robust parental control features that allow parents to restrict access to specific content based on age or rating. This ensures that children are only exposed to age-appropriate programming and helps maintain a safe viewing environment.
With IPTV, parents can set up profiles for different family members, each with their own preferences and restrictions. This level of customization is particularly helpful for households with young children or teenagers.
8. Customizable Channel Packages
Most IPTV providers offer customizable packages, allowing users to select the channels and services they want. This flexibility is a huge advantage over traditional cable services, where users are often forced to pay for channels they don’t watch. With IPTV, you can pick the channels that matter most to you and avoid paying for unnecessary extras.
Whether you’re into sports, movies, news, or international programming, you can tailor your IPTV package to fit your specific interests. Additionally, many IPTV services offer add-ons and premium content options, such as pay-per-view events or exclusive live concerts.
Benefits of IPTV Subscriptions
There are several reasons why people are making the switch from traditional cable to IPTV subscriptions. Some of the key benefits include:
Cost-Effectiveness
IPTV services are often more affordable than traditional cable or satellite TV subscriptions. With IPTV, you pay for exactly what you want, and there are usually fewer hidden fees. This makes it an attractive option for people looking to cut down on entertainment costs.
Flexibility and Convenience
One of the most significant benefits of IPTV is the flexibility it offers. You can watch your favorite shows, movies, and sports events on any device and from anywhere with an internet connection. The ability to pause, rewind, and record live TV gives you total control over your viewing experience.
Access to International Content
IPTV offers access to content from all over the world. Whether you want to watch a French film, a Japanese anime series, or a Spanish soap opera, IPTV gives you access to a vast array of international channels. This opens up new entertainment possibilities and provides a more diverse viewing experience.
Conclusion
The IPTV subscription model has revolutionized the way we consume television. With access to a vast array of channels, on-demand content, live sports, and customizable packages, IPTV offers a flexible, cost-effective alternative to traditional cable or satellite TV. Whether you're looking for convenience, variety, or affordability, IPTV can cater to your entertainment needs in ways that traditional services simply cannot match.
0 notes
Text
Thermosetting Plastics vs. Thermoplastics: Key Differences Explained

When diving into the world of materials used in manufacturing, one of the most common and important distinctions to understand is the difference between thermosetting plastics and thermoplastics. Both types of plastics have their own unique properties, advantages, and applications, making them suitable for various uses in different industries. Whether you're involved in engineering, product design, or just curious about materials, understanding these plastics' key differences is essential.
In this article, we’ll break down the characteristics, applications, and main differences between thermosetting plastics and thermoplastics, providing you with a clear comparison. By the end, you'll have a better grasp of when and why you would use each type of plastic.
1. What Are Thermosetting Plastics?
Thermosetting plastics are a type of polymer material that hardens or sets permanently when heated and molded into a particular shape. This process is known as cross-linking, where the polymer chains bond to form a rigid structure that cannot be re-melted or re-shaped. Once thermosetting plastics have been set, they cannot be remelted or reshaped, making them ideal for high-heat applications.
Some of the most common examples of thermosetting plastics include epoxies, phenolic resins, and melamine. These materials are often used in applications where durability, heat resistance, and structural integrity are essential.
2. What Are Thermoplastics?
On the other hand, thermoplastics are materials that can be softened by heating and hardened by cooling. Unlike thermosetting plastics, thermoplastics can be melted and reshaped multiple times without undergoing any chemical changes. This makes them incredibly versatile and easy to work with in manufacturing processes.
Examples of thermoplastics include polyethylene, polypropylene, polyvinyl chloride (PVC), and polystyrene. These materials are widely used in industries ranging from packaging to automotive manufacturing due to their flexibility, ease of processing, and wide range of available forms.
3. Key Differences Between Thermosetting Plastics and Thermoplastics
To fully appreciate the differences between thermosetting plastics and thermoplastics, let’s look at the key features and how they affect their respective applications.
A. Chemical Structure and Properties
Thermosetting plastics undergo a chemical change when heated, resulting in a permanent bond that cannot be undone. Once these plastics harden, they form a tightly cross-linked molecular structure. This structure contributes to their high strength and durability, making them ideal for high-stress and high-temperature environments.
In contrast, thermoplastics remain in a linear molecular structure, meaning that their chains are not chemically bonded. This allows them to soften when heated and harden when cooled, which is why they can be repeatedly molded and reshaped.
B. Heat Resistance
Heat resistance is one of the most significant differentiators between thermosetting plastics and thermoplastics. Thermosetting plastics are known for their exceptional heat resistance. Since they undergo a chemical curing process, they are more stable at high temperatures and can withstand exposure to heat without losing their structural integrity.
Thermoplastics, while still heat-resistant to a degree, generally have a lower melting point compared to thermosetting plastics. This makes them less suitable for high-heat applications. However, they can be modified with additives to improve heat resistance when necessary.
C. Durability and Strength
Thermosetting plastics are generally more durable and stronger than thermoplastics. The cross-linked structure created during the curing process gives them superior tensile strength, impact resistance, and overall toughness. These properties make thermosetting plastics ideal for applications such as electrical components, automotive parts, and construction materials that require long-lasting performance.
Thermoplastics, while durable, are typically not as strong as thermosetting plastics in extreme conditions. They are more prone to deformation under heat or stress, although advancements in polymer science have made it possible to create high-performance thermoplastics that are strong and durable for specific applications.
D. Reusability
One of the major advantages of thermoplastics is their reusability. Since they can be melted and reshaped, thermoplastics are ideal for recycling. Manufacturers can reuse thermoplastic materials in a closed-loop system, reducing waste and improving sustainability. This feature is especially important in industries where cost and material conservation are key concerns.
Thermosetting plastics, on the other hand, are not recyclable in the traditional sense. Once set, they cannot be melted down or reshaped. While this can be seen as a disadvantage, the benefit is that they are incredibly stable and durable, making them ideal for long-lasting products.
E. Ease of Processing
Thermoplastics are easier to process compared to thermosetting plastics. Since thermoplastics can be melted, they can be molded, extruded, or injected into various shapes and forms using simple processing methods. The ability to reheat and reshape thermoplastics makes them highly adaptable in the manufacturing process.
Thermosetting plastics require more complex processing techniques because of the curing process. These plastics must be heated to a certain temperature to initiate the cross-linking reaction, and once they are set, they cannot be reprocessed. This makes thermosetting plastics more challenging to work with, but their superior properties justify this extra effort in certain applications.
4. Common Applications of Thermosetting Plastics
Thermosetting plastics are commonly used in situations where high heat, strength, and durability are needed. Here are some industries where thermosetting plastics are prevalent:
Automotive Industry: Thermosetting plastics are often used in parts that require resistance to high temperatures and mechanical stresses, such as engine components, electrical connectors, and parts within the exhaust system.
Electrical and Electronics: Thermosetting plastics such as epoxy resins are commonly used in circuit boards, electrical insulations, and connectors due to their excellent electrical insulating properties.
Aerospace: Components in aerospace systems, such as turbine blades, engine parts, and structural components, benefit from the high strength and heat resistance of thermosetting plastics.
Construction: In construction, thermosetting plastics like phenolic resins are used for fire-resistant panels, adhesives, and coatings.
5. Common Applications of Thermoplastics
Thermoplastics, being versatile and easily processed, find use in various industries. Some common applications include:
Packaging: Materials like polyethylene and polypropylene are widely used for packaging materials, ranging from food containers to shrink wraps.
Medical Devices: Thermoplastics are often used in the production of medical devices, such as syringes, catheters, and IV bags, due to their ease of sterilization and biocompatibility.
Consumer Goods: Items such as plastic bottles, toys, and household items are typically made from thermoplastics due to their flexibility, lightweight nature, and ability to be molded into complex shapes.
Automotive: Thermoplastics are used for interior car parts such as dashboard panels, seat covers, and bumpers due to their lightweight and impact-resistant qualities.
6. Environmental Considerations
As the world moves towards more sustainable manufacturing processes, the environmental impact of thermosetting plastics and thermoplastics has become a critical factor. Thermoplastics are more environmentally friendly in terms of recyclability, while thermosetting plastics, being non-recyclable, pose challenges in terms of disposal.
Manufacturers are increasingly working on creating bio-based thermoplastics and thermosetting plastics that are biodegradable or easier to recycle. This shift towards sustainable plastics helps reduce the environmental impact of both materials.
7. Choice between thermosetting plastics and thermoplastics
The choice between thermosetting plastics and thermoplastics largely depends on the specific needs of the application. Thermosetting plastics offer unmatched strength, heat resistance, and durability, making them perfect for high-performance, long-lasting products. On the other hand, thermoplastics are highly versatile, easy to process, and reusable, making them a go-to choice for industries requiring flexibility and cost-effectiveness.
Understanding the characteristics and uses of these materials allows manufacturers to choose the right plastic for their needs, leading to better products and more efficient production processes.
8. Cost Comparison Between Thermosetting Plastics and Thermoplastics
Cost is always a deciding factor in manufacturing and product design. In terms of raw material cost, thermoplastics generally tend to be more affordable than thermosetting plastics. The lower cost is mainly due to the simpler processing methods and the fact that thermoplastics can be reused multiple times during production.
However, the overall cost depends on the application. While thermoplastics are cheaper in terms of raw material, thermosetting plastics provide superior performance in extreme conditions, often making them a more cost-effective option in the long term for certain high-performance applications. For instance, the durability and heat resistance of thermosetting plastics might outweigh the initial higher cost if the end product needs to last a longer time or withstand harsh environments, saving costs on replacements or repairs.
9. The Manufacturing Process: Thermosetting Plastics vs. Thermoplastics
The manufacturing process of both thermosetting and thermoplastic materials involves distinct steps that impact the final product’s properties.
A. Thermosetting Plastics Process
Thermosetting plastics undergo a curing process, where heat or chemical additives are used to trigger the polymerization (cross-linking) of the plastic. Once the plastic hardens, it cannot be reprocessed, making the initial manufacturing process critical. The process involves molding the material into the desired shape and applying heat, which causes the material to chemically bond into a permanent form.
This manufacturing process gives thermosetting plastics their distinctive properties, such as high dimensional stability and thermal resistance. However, because they can't be reworked, production needs to be precise, and waste can be an issue in industries where intricate shaping is required.
B. Thermoplastics Process
In contrast, thermoplastics can be processed multiple times. The polymer chains in thermoplastics soften when heated, allowing manufacturers to mold and shape the material into a variety of forms. Once cooled, the material solidifies and retains the shape. Thermoplastics can be re-melted and reused, which reduces waste during manufacturing and provides more flexibility for design changes or repairs.
This repeatability and ease of processing make thermoplastics a go-to choice in industries with high production demands or rapid prototyping. Additionally, the cost-effectiveness and efficiency of the process make thermoplastics a more economical option in mass production.
10. Innovations in Thermosetting and Thermoplastic Materials
As industries demand more specialized and high-performing materials, innovations in both thermosetting and thermoplastic polymers continue to evolve.
A. Advances in Thermosetting Plastics
Recent advancements in thermosetting plastics have focused on improving recyclability and expanding their application range. New methods of reprocessing thermosetting plastics are being explored, although they remain challenging due to their cross-linked structure. Innovative composite materials that combine thermosetting plastics with fibers are also helping to enhance their strength while maintaining lighter weights for aerospace and automotive industries.
B. Advances in Thermoplastics
Thermoplastics have seen significant innovation, particularly in bio-based alternatives and high-performance polymers. These innovations help address environmental concerns by reducing reliance on petroleum-based plastics. Additionally, new thermoplastic materials are being developed to withstand higher temperatures and pressures, opening up new possibilities in industries like electronics, aerospace, and automotive manufacturing.
As demand for more sustainable, efficient, and high-performance materials grows, the research into both thermosetting and thermoplastic plastics will likely continue to progress, providing even more specialized solutions for diverse applications.
11. The Future of Thermosetting and Thermoplastics
Looking ahead, the future of thermosetting and thermoplastic materials will likely be shaped by several factors, including sustainability, technological advancements, and evolving industry demands.
Sustainability: One of the biggest challenges facing the plastics industry is environmental impact. As both thermosetting and thermoplastic manufacturers explore more sustainable options, such as bio-based and biodegradable polymers, these materials will continue to evolve to meet global sustainability goals.
Technology: The ongoing development of new processing technologies, such as 3D printing, could significantly affect the manufacturing of both thermosetting and thermoplastic materials. This could make it easier to create customized, high-performance parts while reducing waste and manufacturing costs.
Market Demand: As industries such as automotive, aerospace, and electronics continue to demand lighter, stronger, and more efficient materials, both thermosetting and thermoplastic polymers will see more specialized uses. Future innovations will focus on enhancing the properties of these materials to meet the ever-changing needs of these sectors.
12. Conclusion
In the world of materials, understanding the differences between thermosetting plastics and thermoplastics is crucial for making the right choice for your application. Both materials have their distinct advantages, and the decision to use one over the other will depend on factors such as heat resistance, durability, processing methods, and cost.
Thermosetting plastics, with their unmatched strength and heat resistance, are perfect for applications where high performance and long-lasting durability are required. On the other hand, thermoplastics are ideal for industries that prioritize flexibility, cost-effectiveness, and the ability to reuse and recycle materials.
As technology continues to advance, both thermosetting and thermoplastic materials will evolve, providing even more options for manufacturers looking for the best solutions for their specific needs.
Visit http://incomepultrusion.com/thermosetting-plastics/
0 notes
Text
From Barking to Biting: Addressing Common Dog Behavior Issues

Understanding Dog Behavior: Why It Matters
Dogs are wonderful companions, but just like humans, they can sometimes exhibit behaviors that leave us scratching our heads. Whether it's excessive barking, sudden aggression, or destructive chewing, every dog owner has faced a few puzzling moments. Understanding the root of these behaviors is essential for building a stronger bond with your furry friend and creating a harmonious living environment.
Behavior issues in dogs are rarely about being "bad." More often than not, they’re trying to communicate something—stress, boredom, fear, or even medical discomfort. By learning to read these signs and respond appropriately, you can help guide your dog towards better habits and a more relaxed, happy life.
When it comes to Dog Behavior, it's all about perspective. Dogs don’t think in terms of right or wrong—they act based on their instincts and the reinforcement they receive. So instead of getting frustrated, consider yourself a detective trying to understand the ‘why’ behind each action.
1. Excessive Barking: More Than Just Noise
Dogs bark—it’s their way of communicating. But when barking becomes constant and uncontrollable, it’s time to dig a little deeper. Common triggers include boredom, anxiety, territorial behavior, or the simple need for attention.
What you can do:
Identify the trigger: Is it the mail carrier? Other dogs? Loud noises?
Mental stimulation: Bored dogs bark more. Try puzzle toys or interactive games.
Training techniques: Use commands like "quiet" and reward silence.
Avoid yelling: It only adds to the noise and confusion.
Consistency and patience go a long way here. Over time, your dog will learn there’s no need to raise the alarm every time a squirrel runs by.
2. Chewing Everything in Sight
Puppies chew to explore the world and soothe teething pain, but when adult dogs turn your shoes and furniture into chew toys, it’s a cry for help.
Why it happens:
Boredom or lack of exercise
Separation anxiety
Poor diet or nutritional deficiencies
Lack of boundaries
Solutions to try:
Provide chew alternatives: Durable toys, frozen carrots, or rubber bones.
Supervised freedom: Confine your dog to a safe space when unsupervised.
Plenty of play and walks: A tired dog is less destructive.
Deterrent sprays: These can help discourage chewing on off-limit items.
Remember, scolding your dog after the fact won’t help—they won’t connect the punishment with the action. Instead, focus on prevention and positive reinforcement.
3. Jumping on People
While a dog jumping up might seem cute when they’re small, it can become problematic—or even dangerous—as they grow. This behavior is usually about excitement or seeking attention, not dominance.
Tips to stop jumping:
Ignore, don’t reward: Turn away and avoid eye contact when your dog jumps.
Teach an alternative: Train your dog to sit when greeting people.
Reinforce calm greetings: Reward calm behavior with treats or affection.
Be consistent: Everyone in the household needs to follow the same rules.
With repetition and consistency, your pup will learn that four paws on the ground equals more love and attention.
4. Aggression and Biting
Aggression can be frightening, especially when it escalates to biting. But this behavior often stems from fear, pain, or a lack of socialization—not meanness. Dogs might growl or bite as a last resort when they feel cornered or threatened.
Steps to address aggression:
Observe body language: Watch for warning signs like stiff posture, growling, or raised hackles.
Avoid punishment: It can increase fear and make aggression worse.
Socialization: Gradual exposure to people, animals, and new environments helps reduce fear-based reactions.
Professional help: In severe cases, consult a dog behaviorist.
The following video demonstrates how consistent and calm interactions can improve even the most challenging behavior:
youtube
5. Separation Anxiety: Not Just Missing You
If your dog goes into panic mode every time you leave—barking, whining, chewing, or even having accidents—they might be suffering from separation anxiety. This is more than just missing you; it’s a full-blown stress response.
Help ease the anxiety:
Start small: Practice leaving for short periods and gradually increase time away.
No big exits or entrances: Keep goodbyes and hellos calm and casual.
Comfort items: Leave behind a blanket, piece of clothing, or a toy.
Create a safe space: A cozy crate or room can help them feel secure.
Working through separation anxiety requires patience, but the relief and calm your dog will feel are worth every effort.
6. Digging: More Than Just a Mess
Digging is a natural behavior for dogs, but when your backyard starts to resemble a minefield, it's time to address the issue. Dogs dig for various reasons: to escape, to hunt, to cool off, or simply out of boredom.
Understanding the motivation:
Escape attempts: Dogs may dig under fences to explore or find companionship.
Hunting instincts: Some breeds have a strong prey drive and dig to chase burrowing animals.
Comfort seeking: Digging can create a cool spot to lie in during hot weather.
Entertainment: Without sufficient stimulation, dogs may dig to pass the time.
Strategies to curb digging:
Provide ample exercise: A tired dog is less likely to dig.
Designate a digging zone: Create a sandbox or specific area where digging is allowed.
Use deterrents: Place chicken wire or rocks in areas where digging is unwanted.
Address underlying issues: Ensure your dog isn't digging due to anxiety or separation stress.
By channeling your dog's digging behavior into acceptable outlets and addressing the root causes, you can protect your yard and keep your dog happy.
7. Leash Pulling: Teaching Polite Walks
Walking your dog should be a pleasant experience, but leash pulling can turn it into a tug-of-war. Dogs pull on the leash because they're excited, curious, or haven't been taught proper leash manners.
Why dogs pull:
Excitement: The outdoors is full of interesting sights and smells.
Lack of training: Dogs may not understand that pulling isn't acceptable.
Reinforcement: If pulling gets them where they want to go, they'll continue doing it.
Training techniques:
Stop-and-go method: Stop walking when your dog pulls, and resume only when the leash is slack.
Change direction: If your dog pulls, turn and walk the other way to teach them to pay attention.
Use rewards: Treats and praise can reinforce walking beside you without pulling.
Consistent practice: Regular, short training sessions can build good habits.
Patience and consistency are key. Over time, your dog will learn that walking calmly by your side is rewarding.
8. Inappropriate Elimination: House Training Challenges
Accidents in the house can be frustrating, but understanding the reasons behind inappropriate elimination is crucial. Puppies, newly adopted dogs, or even well-trained dogs can have accidents due to various factors.
Common causes:
Incomplete house training: Puppies need time and consistency to learn.
Medical issues: Urinary tract infections or other health problems can cause accidents.
Anxiety or stress: Changes in the environment or routine can lead to regression.
Marking behavior: Some dogs mark territory, especially in new surroundings.
Solutions:
Establish a routine: Regular feeding and potty times help set expectations.
Supervise closely: Keep an eye on your dog, especially during the training phase.
Positive reinforcement: Praise and reward your dog for eliminating outside.
Clean accidents thoroughly: Use enzymatic cleaners to remove odors and prevent repeat offenses.
With patience and a consistent approach, most dogs can overcome house training hurdles.
9. Resource Guarding: Protecting Valued Items
Resource guarding occurs when a dog becomes possessive over food, toys, or other items, displaying behaviors like growling or snapping when approached. This behavior stems from a fear of losing something valuable.
Identifying resource guarding:
Body language: Stiff posture, intense staring, or growling when approached.
Behavioral signs: Snapping or biting when someone gets close to the guarded item.
Addressing the issue:
Desensitization: Gradually get your dog used to people being near their valued items.
Trade-up technique: Offer something better in exchange for the guarded item.
Avoid punishment: Negative reactions can increase anxiety and worsen the behavior.
Consult professionals: Severe cases may require guidance from a behaviorist.
Understanding and respecting your dog's comfort zones, while gently working to expand them, can reduce resource guarding behaviors.
10. Fear and Phobias: Helping Anxious Dogs
Dogs can develop fears or phobias to various stimuli, such as thunderstorms, fireworks, or specific objects. These fears can manifest as trembling, hiding, or destructive behavior.
Common triggers:
Loud noises: Thunderstorms, fireworks, or vacuum cleaners.
Unfamiliar environments: New places or changes in routine.
Past trauma: Negative experiences can lead to lasting fears.
Supporting your dog:
Create a safe space: Provide a quiet, comfortable area where your dog can retreat.
Use calming aids: Products like anxiety wraps or pheromone diffusers may help.
Desensitization training: Gradually expose your dog to the fear source in a controlled manner.
Stay calm: Your demeanor can influence your dog's reaction.
Empathy and gradual exposure can help your dog build confidence and reduce fear responses.
Conclusion: Building a Harmonious Relationship
Addressing common dog behavior issues requires patience, understanding, and consistency. By identifying the root causes and implementing positive reinforcement techniques, you can guide your dog toward better habits. Remember, every dog is unique, and what works for one may not work for another. Stay observant, be flexible in your approach, and celebrate small victories along the way.
1 note
·
View note