Text
Breaking In: From lurking the shadows to being employed
For anyone that follows me on Twitter, or knows me from The Many Hats Club, you’ve probably heard that I recently started a job in the information security industry - after three years of what I think of lurking on the periphery and being interested but no idea where to start.
With that being said, a friend of mine recently said that he had been watching how I’ve interacted with the security community online and in person, so he can do similar when he’s ready to try to enter the industry in a professional capacity. I’m not entirely sure that I’ve done much of anything, but I figured writing a piece on what I know I’ve done might help other hopefuls figure out their path.
The core of my advice can be put as follows:
Get stuck in! Interact with people, be friendly, be open to learn
Don’t be afraid to ask questions. Don’t be afraid to say you don’t know something.
Don’t max out your credit card going to conferences, but try to attend some if you can afford to and are able to.
Take a chance - you’ll never get anywhere if you don’t try.
Twitter
I started, like many young hopefuls these days, with Twitter. I had an old, barely used Twitter account that I pivoted the interests and the people I was following to be security-focused. At the time, my Twitter handle was “ChrissiTheFroot”, but that quickly changed to the frootware handle that most know me as now.
I started out by following people I knew of from documentaries I had watched (Mikko Hyponnen), and people from the news (MalwareTech). My first interaction was “Notice me senpai” to MWT, which is something I look back on and ask myself why.
Over time I talked to people about the fact I was interested in security, but didn’t know where to start or what I wanted to do in security. Two of the best people I met in those early days were Wesley McGrew and Rox. Through their advice, I started my journey. Wesley initially started by hearing me out about what I was interested in, what interested me within security, and offering advice about wha to look at, as well as giving me some tips on improving my CV. Rox advised me to look for groups local to me on MeetUp.com - a website that offers a range of groups that meet regularly for various interests or just social activities. Through that, I found Manchester Grey Hats, and met some of my early mentors in security.
Communities
As mentioned above, the first security group I joined was Manchester Grey Hats, where I met Jay and Saskia, and several other wonderful people who are kind and encouraging and welcome newcomers as much as they welcome seasoned professionals. They nurtured my interest and gave me the opportunity to try new things within security in a safe environment where I could ask questions (though... I never really did), and a community of friends who could guide me and support me as I figured my way out through this.
I still fondly remember sitting in a speakeasy-styled bar in Manchester with Jay and another member of MGH, outright saying a sentiment that I’ve carried since I started looking at security as a career: “I feel like I’m having to play catch-up with everyone else”. Jay gave me some of the best advice possible in response - It’s impossible to know everything.
That’s never stopped me from trying though.
Through interactions on Twitter, I got the opportunity to talk to Stuart Peck about my weird and wonderful career history - I’ve tried to be an author, a rockstar, a lawyer, and a chef, all before I tried being a hacker. Following that, Stu invited me to The Many Hats Club and I found another home within security very quickly. I spent a lot of my time in the Discord community as a mod there, and I’ve made a wonderful group of friends who stand by me, and I do my best to offer them the same.
Conferences
Sitting in the break room of my helpdesk job in the summer of 2017, waiting for my shift to start, I saw on Twitter something that made me experience FOMO like I never had before: a conference, barely an hour away from where I was. BSides Manchester 2017. Specifically, I was seeing photos of Andy Gill speaking and thought “that’s where I’d rather be right now”.
The following year, 2018, I spent almost all of my paid leave going to conferences. I also maxed my credit card funding that. I sort of regret that small fact, but overall I think it was worth it. Through going to conferences, I met so many wonderful people and learned so much. I took the opportunity to speak to people, ask questions about what they did, and figure out what sounded fun and interesting.
By the end of 2018, I had attended probably 10 conferences. It was a lot of work by the end of that year, and through a combination of Seasonal Affective Disorder and the amount of effort I was exercising in trying to get into security ASAP (I’ve never been good at waiting...), I was burned out. However, I knew what I wanted to do by then. Thanks to Black Hoodie, a women-focused conference dedicated to reverse engineering, I realised that malware analysis was where I wanted to be. I’m still working on getting there, but at least I had the end goal, and could work out the steps I needed to get there.
Career History
When I first wanted to come into security, I was a first-line support analyst in a helpdesk call centre. I tried to get a penetration testing internship, but wasn’t successful due to concerns that my technical skills weren’t quite ready - a fair assessment: the year before I’d sworn off IT completely and was edging my way back in because of my interest in security.
From there, after a short stint at KFC to pay bills, I worked a software engineer for a year. That company and I parted ways recently, as they felt that it would be better to let me focus on finding my way in security rather than keeping me in a role more focused on development, something that has never really been my strong suit. The very first job I saw on LinkedIn was a security role, and I took that as a sign from the universe that, whether I felt ready or not, it was time for me to try entering security.
And now... now I’m officially a “cybersecurity analyst” but more accurately, I’m a SOC Analyst. Through the grace of the universe, and a tweet complaining about a junior role requiring CISSP certification, I’ve broken in. By building myself a network of people who believed in my skills and potential (even more than I did for a long time), I was able to make it.
And I believe you can too. Get stuck in, talk to people. Show people who you are just as much as you show them what you know. Don’t be afraid to say you don’t know something, or ask people to explain what they mean by something. You’ll get there.
0 notes
Text
ColourPop & the beauty industry as a whole
At 18:11 BST on June 28th 2018, I received an email from ColourPop Cosmetics. The subject line had one words: HACKED.
This is incredibly irresponsible for a number of reasons, and I said in a previous tweet thread, not a good look.
The beauty industry is no stranger to security incidents. In 2015, Lime Crime Cosmetics faced issues regarding the certificate for the payments server expiring and the consequences that followed led to hundreds - if not thousands - of customers had card information stolen and faced issues with banking fraud because of it. What made this situation worse is that they then attempted to hide it for at least two months while customers complained on their social media about the issues they were facing, asking what LCC was doing to protect and reimburse them and receiving no response.
In 2017, Tarte Cosmetics also faced issues. This time, their databases had an error that caused their entire payment records - including addresses and card information - to be sent out to their mailing lists. Further, their response was to ask everyone to kindly delete the email - but I believe they did also send a recall request across with a command to delete any unread copies of the email.
It seems unsurprisingly common that cosmetic brands, especially independent ones that might not necessarily have a large staff, do not have a good grasp on information security and how they can, or should, respond to incidents and breaches. It happens, and not everyone is going to be security minded so some people may prefer the approach of sweeping the issue under the rug while it gets fixed, and others may opt to rely on compliance with requests.
Moving away from the beauty industry for a second, there are other breaches and incidents that are at the forefront of the public mind.
Take, for example, WannaCry in May 2017 - the ransomware that hit 230,000 companies in 130 countries in one day. It hit major headlines in the UK due to the fact that it infected the NHS and crippled a lot of the service across the country. There’s also the Equifax breach at the end of last year that affected the identity security of 145.5 million people.
Looking at security breaches of 2018:
Under Armor, the creators and owners of the MyFitnessPal app, were breached in March. It’s estimated that the information 150 million people was compromised.
April 2: Panera Bread reported that customer information may have been leaked on their website. This was quickly rectified, but it’s believed that up to 37 million people may have been affected.
April 4: Sears announced a breach that affected the credit card information of up to 100,000 customers. Kmart was also affected in this breach, as they are owned by Sears. Delta, who use the same online service as Sears, also stated that customer information may be vulnerable but did not provide estimates of how many may have been affected. Best Buy were also affected.
Saks Fifth Avenue also reported a breach in April. They did not provide the number of records affected, but it is estimated to be in the millions. Lord & Taylor were also affected.
Most recently, Ticketmaster have been victims to a breach. This may have affected up to 40,000 UK customers.
The reason I go into this detail about recent security breaches both inside and outside of the beauty industry is simple and returns back to the issue I have with the newsletter’s subject.
Sending an email with the subject line of “HACKED” is likely to put people in the mind of their personal or payment information being leaked or stolen. When mentioning this newsletter to two friends who are not involved with the information security industry (though they are, like me, very interested in cosmetics), they each had something to say that followed the same lines:
“I would’ve had a heart attack”
“I’d be freaking out that my information got stolen”
I’ll admit that my initial reaction was feeling my heart in my throat upon seeing the subject line, as I had just made my first ColourPop order two weeks ago. To find that the newsletter was just makeup tips was both relieving and disappointing. I was relieved, as it meant my information hadn’t been stolen. I was, however, disappointed to find this flagrant disregard for customer responsibility - exactly because of everything listed above. Breaches happen. It’s the responsibility of the businesses that may be affected to disclose this; there is also some legal requirement under GDPR to disclose a breach to customers, depending on the nature of the breach.
I don’t think this was done to undermine the serious nature of security breaches; in fact, I think it was done from a place of misunderstanding. I don’t want to vilify ColourPop Cosmetics in any way, just bring to light an issue that may not have been considered.
1 note
·
View note
Text
Creating projects that challenge without crushing
One way to build a portfolio of technical expertise without necessarily having the job experience to back it up is to create projects surrounding topics that interest you. Creating those projects to a level where they’re reasonable to complete can be a challenge in and of itself, especially if you’re looking to challenge yourself or if you want to show growth from previous projects.
For any project, it’s worth finding a point of interest in a topic - this can be narrow or broad. The broader the topic, sometimes, the more depth you can go into with it. It’s worthwhile having a mix of projects available for you too, if you’re looking into a broader spectrum of possible career opportunities. The project doesn’t necessarily have to be scripting or programming, or even creative - it could be looking at previous malware attacks or existing exploits and analysing the attack, the malware, its effectiveness, anything relating. Even creating a short term research project looking into the timeline of connected malware is good as a project.
While the project itself doesn’t matter outside of your personal interest, the documentation of your progress and your thought processes surrounding the project. Being able to present these accurately is a good sign of understanding how you’re approaching this project. It’s important to show intent of the project, explain the processes throughout, reflect on what was done for the project. A further way to reflect would be to consider what went well with the project and how you could improve for your next one.
It’s important to remember that projects that do not push you will be unlikely to help you grow. In my opinion, a project should contain aspects that you don’t know but can learn; likewise, some aspects of the project should be easier for you. There needs to be a balance between “I can do this” and “I don’t know this yet”. A project entirely composed of the latter is less likely to be completed and may lead to feeling like if you can’t do this project, then you won’t be able to cope in a job role that incorporates similar aspects to the project. Overreaching is never a good idea.
Also important to remember is that a project does not need to contribute something entirely new to your industry. You can use a project to show practical understanding and theoretical knowledge of the topic behind the project, or you can use it to show learning and growth. The best projects do both, but finding something new to contribute isn’t necessary.
On the back of that, a project also doesn’t need to be entirely of your own design. Taking suggestions from other people that you know, or hearing things people would like to see and trying to meet those hopes, is also good. You could expand on projects you’ve already done, or used another person’s project or research and try to expand it in another way to show understanding, learning, and growth. Of course, if you’re going to use another person’s project or research as your starting point, it’s always polite to ask first - and if they say they’re fine with it, then credit back to them as well. If it’s a past project of your own, linking back to the past project can help with showing the extended growth since that project.
0 notes
Text
Where do we go from here? Developing a personal learning plan for an unstructured industry
When entering an industry on your own - no university plan to follow, no teachers to hold your hand - it can sometimes be overwhelming to see just how many topics relate to that industry, and it can sometimes be overwhelming to find quite where you feel like you’d belong best in that industry.
This case definitely applies to Information Security. InfoSec has so many different fields that fall under its umbrella that it can be daunting to find where to start, what to look at first. So how to go about it?
In the past year that I've involved myself with the infosec community, I've done my best to stay as open to everything as I can. No avenue is left unwalked, no stone is left unturned. Of course, it's impossible to keep that up but a broad focus that gets narrowed down and wittled into shape is probably the best way to venture into a new industry unguided.
1. Watch your industry
Watching your industry is a really good way to see what information is being made available and what knowledge is needed. Keeping up to date with what your industry is doing is valuable and can provide a lot of insight to yourself, what you’re most interested in, and your place in your industry of choice.
I started with reading all the news stories on Bleeping Computer, reading every new security story every day. Last year, of course, was a year rife with ransomware, so this filled a lot of the stories I read. But it was a key point of interest to me; I found the ransomware hit stories more interesting than the stories about cryptojacking. Finding that interest point was the starting step to developing some of my progress intentions with infosec.
2. Pinpoint a broad topic
Once you’ve kept an eye on your industry for a little bit, you’ll probably find that one or two topics are drawing your interest more than others; use this as a pinpoint basis to begin narrowing down your quest for knowledge.
As I said before, reading Bleeping Computer articles led me down the path of ransomware - articles about this drew my attention a lot more than other articles. From here, I started trying to understand how ransomware worked, trying to piece together how an infection might take place. With ransomware last year, there was obviously the set of malware attacks that utilised NSA tools to propagate; this gave me an opportunity to learn about how those tools worked, and why they were so effective.
3. Break it down
A broad topic is great, a finite point of exploration is better. Broad learning should accompany more focused, in-depth learning; take your broad topic and break it down into smaller concepts.
For ransomware, I thought about the key aspects of most of the more noted ransomware attacks. While ransomware originally just locked down functionality without encrypting files, file encryption became popular and more common following CryptoLocker in 2013. So of course, a smaller concept to ransomware would be encryption and cryptography. Other topics may involve cryptocurrencies and how blockchains work and can be traced (as cryptocurrency is a popular ransom demand), and the aspects of social engineering that can make a ransomware attack successful (after all, they have to convince their victims that the files or functionality will be freed once payment is made - even if they have no intention of it).
4. Do it all again
I feel like it’s really important to keep a broad mind on industry learning. Keeping as up to date as you feasibly can is vital to be able to find out about new technologies or concepts that may be of interest; once you’ve finished your topic breakdowns as far as you want to take them, it can be time saving to know where you want to go next.
2 notes
·
View notes
Text
I’m not really a fraud - I promise.
Imposter syndrome. It's only two words but it's the bane of many people's lives, not just people involved in infosec or technology.
It's so easy to turn around and think so-and-so is so much better at a certain subject, or you'll never catch up to so-and-so's knowledge of this area of interest.
For someone breaking into an industry, this can easily be the make-or-break point. Turning around and running away seems like an easy choice when you're staring up at this great wall of information and experts and people with more knowledge of the things that interest you. It's intimidating to join a community and feel like you have nothing important to say.
Here's the thing: Every perspective on a subject is different. What you have to say is just as important as what someone else has to say; you may provide a view point not considered yet. Fresh eyes to existing problems, that sort of thing. And just sometimes, you'll be talking about a topic that interests you, even in just a basic way, and you'll be opening a door for someone else who doesn't have the expert elite knowledge yet either. There's no harm in multiple explanations of the same thing for different audiences.
It’s okay to not know things. No one will know everything. I regularly introduce myself with saying “I know absolutely none of the things” - and that’s my demons talking more than it is fact.
When I started going into infosec, I started with the idea that I'm playing catch up. That I'll always be playing catchup, because I started late. I haven't been hacking in my bedroom since I was 13, and I haven't got the programming background that some of my friends have. I spent my first CTFs feeling useless, because I didn't know how to do anything.
Right now, there isn't a day that goes by that I wonder if I'll ever make it to that first life goal of mine, if I'll ever be able to get a job in the industry I feel so at home in. I wonder if I'll ever have anything worthwhile to contribute to this industry.
Every hindrance is an opportunity to do better, to learn new things.
In the past, I've described myself and infosec as the young puppy and its ball, the small child in a museum full of dinosaurs and other interesting history things. Where do I even start? What wing of the museum am I going to run into first? What exhibits am I going to stare at with wonderment in my eyes, glee in my heart? How am I going to quench this thirst for knowledge the first time around? There's so much to do, so much to see! Don't be afraid to ask people you admire how they started out. They may have some great pointers to help you begin your journey.
I'm not going to sit here and pretend that it's always going to be super interesting and that every topic you look at will capture your mind entirely. Even with the topics that interest me, I find some of the theory behind them boring. I still try to learn it, because I like understanding why things work.
Sometimes, you can think "I really like this broad topic!" and that's totally okay. Learn about that broad topic. Maybe break it down into smaller chunks and the fundamentals of it. For me, my broad topic started out as ransomware. It's what got me into infosec to start with. When I decided I wanted this as a career, I sat down and I read every article listed in Wikipedia's list of notable computer worms and viruses. After that, I opted to break down ransomware into its components. Cryptography is my current topic, and I'll look at how various attack vectors work next. But ransomware isn't all I'm going to go for; I've got other topics far away from this to look at when I want to as well. I like having backup plans, and information security in general interests me, so I'll look at almost anything in the field right now while I find my path. There's nothing wrong with exploring your industry to your heart's content.
It's easy to get caught up in the superficial aspects of "If I beat this malware, I'll be famous". It's easy to get caught up in the starry-eyed "You're so amazing! I'll never be like you!" thought processes with people in your industry.
When I went to my first internship interview, I worried endlessly about the research aspect. My mother said to me "Look at how much you've learned in the past year. Think about how much you can learn in the next one."
So that's what I ask you to do now.
Think about how much you've learned since you've started your journey.
Think about how much you can learn in the same amount of time to come.
Hi, my name’s Frootware. Sometimes I know some of the things.
0 notes
Note
Hello, good though this content is, are you not concerned that whilst most folks can actually use this level (or components of it) of filtration on current phishing attempts, giving the phishers feedback will, over time, allow them to learn and improve their future effectiveness? That's why I never allow them feedback on anything they try on me.
Honestly, this thought did cross my mind while I was writing the post.
What led to me still posting it is the fact that a lot of these elements I’ve spoken about have been spoken about for years - or at least, I’ve recognised them for a long time and I’m sure it’s been mentioned to me in the past regarding elements of “dodgy” emails to avoid responding to. I’d like to think that most of these elements are primarily common knowledge (though from personal experience I know it isn’t a knowledge as common as I would like it to be). I think if they were going to have improved based on this sort of information, it would’ve happened already.
Of course, a breakdown like this might contribute to future improvements, and if my post ends up a contribution to that then I’ll accept the part I’ve played.
0 notes
Photo
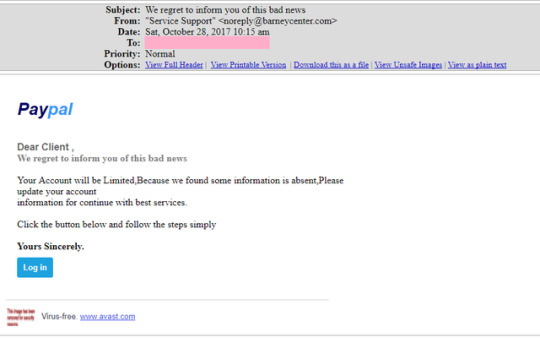
I tweeted this photo last night because I like to mock some of the phishing emails that come through on one of the several email addresses I have. As per usual with my tweets regarding those emails, I made some sarcastic commentary about things I noticed with it. These emails will always be coming into one mailbox: this is an email address I’ve had since I was 13, and it is an email address that is likely to be on a lot of various mailing lists both good and bad due to the extent of usage it’s had. I’ve accepted that. Most nefarious emails do get blocked, but there will always be some that get through the net. Things happen.
Now I have this blog set up and running, I figured I might break it down a little bit more - hopefully leaving out the sarcasm, but I can’t make any promises about that.
I’ll start by looking at how the email appeared when looking at my Inbox in the client - before even viewing the message. I don’t have any screenshots of this, sadly, but it was something that caught my eye anyway.
From: Service Support | Sbj: We regret to inform you of this bad news
This sort of subject line catches attention quickly. People don’t like bad news. Seeing it from a sender reporting to be a Service Support also may mean a number of things - termination of a critical service, loss of a loved one in the case of said loved one being in an assisted living situation. Another possibility, of course, given news running rampant with Equifax and, less recently, WannaCry, is a technical service emailing customers to report a security breach. The purpose is still the same: get the victim to click the email.
Upon opening the e-mail, there’s several issues that pop out.
1. The email address
“noreply@barneycenter[.]com”. That is most definitely PayPal.
Doing a site:barneycenter.com search on Google shows me that this domain is tied to a WordPress site for Alabama based Barney Center Business, which involves itself with History, Law, and Politics. Their site is not accessible.
2. The PayPal logo
This is not the PayPal logo. For starters, it’s written in text rather than an image. Secondly, PayPal branding continuously has the second ‘p’ of PayPal capitalised. The font that PayPal have opted to use for the logo, also, does not use a hooked ‘a’, as can be seen below with a genuine PayPal logo. The ‘Pay’ of PayPal is stretched. In genuine emails, they also use a variation of the logo that involves two overlapping P’s, and with some others the overlapping P’s is the logo that they opt to use - depending on the purpose of the email.

image source: https://www.paypal.com/us/webapps/mpp/logo-center
3. “Dear Client”
PayPal make a point to use the full name of the account holder in all communication that they send. Even with advertising emails that PayPal send, I find that they still have my name on somewhere. As this email, if genuine, would be targeted to an individual account holder, I would definitely be expecting to see the account holder’s (i.e. my) name on the email. You ain’t addressing me, I ain’t clicking your link.
4. Changing fonts (font family and font colour)
There are four different fonts on this email, and the main body of the email changes colour twice (dark grey, mid-grey, black). Ever heard of consistency, phishy boy? It’s very important for branding. No marketing person would have let this out of a mailbox’s drafts, let alone the outbox. Even if this was a genuine security alert message, there would’ve been a template to follow. Business brand and image is incredibly important and to sacrifice it would mean career suicide for whoever sent an email that left it out.
5. Random capitalisation and syntax
“Your Account will be Limited,Because we have found some information is absent,Please” etc.
For once, this is an email where the English itself isn’t that bad. That sounds awfully xenophobic to say, but it is a trend among phishing emails - whether that has something to do with origin of the emails or attempts to get through filters or some combination, I can’t say, but it’s still a trend. The author of this email keeps using commas in strange places or in place of periods, as well. I’d ask if his spacebar broke, too, but he’s used it between words.
I said the English wasn’t bad but I looked at the message again and I saw “for continue with best services”. I stand corrected, even before I post.
6. Line breaks mid-sentence
This is common in an attempt to break up phrases that may be getting filtered by mail clients or spam filters. The phrases that are being broken - “please update” and “account information” - are definitely phrases that I would be watching for if I was a filter. By inserting a line break, probably through the use of <br />, the filter isn’t seeing those phrases any more.
7. Requesting information with little explanation
My PayPal has most of my information on it and has two email accounts linked. I know people who have no information on theirs, with no account limitations. I know people who have had their accounts limited for various reasons.
My first question: What information is missing? When I’ve had a card expire on my PayPal in the past and not added a new one, they’ve asked me specifically along the lines (and this is paraphrasing and awfully informal) “Yo, you want a card on your account? Here’s how to put one back on”
My second question: why is it so vital that my account has been limited until I add it?
My third question: If it’s so important and vital for my account, why wasn’t it asked at registration?
8. “Yours sincerely,” with no name
Who are you????
In all seriousness, it seems odd to begin to sign off an email without actually signing it off. I doubt the person sending the email is a login page with a gibberish URL. Speaking of, the sign-off is a very strange place to put the login button, dear Phisher.
9. The Avast signature
I use PayPal on an incredibly regular basis - being paid weekly and having monthly subscriptions to things that are paid through PayPal, I tend to throw contributions into my PayPal account every week towards those subscriptions to cover the cost of said subscriptions - and I have never seen a declaration from any anti-virus program declaring a PayPal email to be virus-free.
Avast is also the anti-virus program I’m using at the moment. It doesn’t mark emails coming in with this signature; this only happens to outgoing emails. Whoever is running this campaign uses Avast, clearly.
All in all, this was a really obvious phishing email. There’s a lot wrong with it and I’m struggling to see much that could be considered “right” with it. Attempts were made, I guess.
0 notes