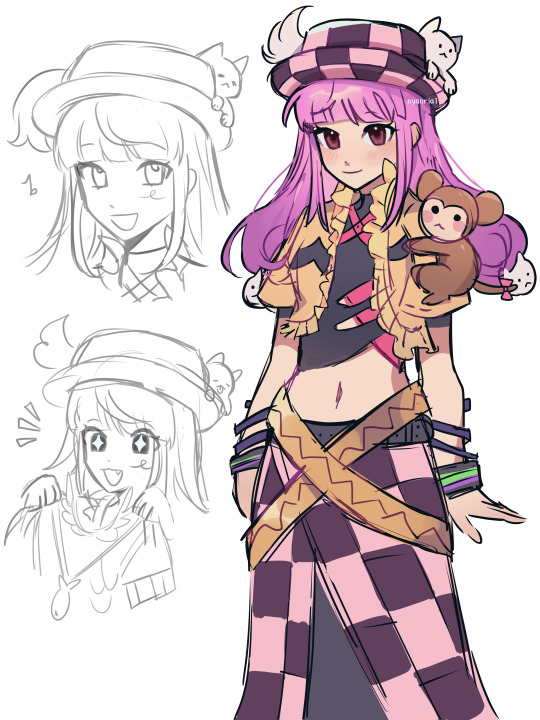
20+ || I draw when I'm in the mood for it || Do NOT repost my art || Not safe for antis || Twt: @utsukani
Don't wanna be here? Send us removal request.
Text

BOY it sure is great when ur illegally downloaded boyfriend comes with absolutely no drawbacks whatsoever :)
3K notes
·
View notes
Text

making it an acrylic stand for myself (i love being delusional)
348 notes
·
View notes
Text








— And so, let the curtain rise on tonight's dream.
Puella Magi Madoka Magica the Movie -Walpurgisnacht Rising- ☆ Winter 2024
11K notes
·
View notes
Text
Please reblog if possible to spread word. If interest isn't huge then I'll like make this a once a year event; in the past three per year were held. But I have a busy life and don't want to commit to something without a lot of interest. Thank you. ~Mod Flik
52 notes
·
View notes
Text

mourning yet again for the tragic loss of Plow and Propose as the rename for the series
directly from xseed’s twitter btw

676 notes
·
View notes
Text
you know that art collab meme where one person does the sketch, one does the lineart, one does colors, shading, etc? it'd be really cool to see artists just. do that and be like "cool I did this part, who wants to take over?"
even if someone already did lines and color and shading, you could still do your own lines. or add color to multiple people's lines. there could be dozens of versions of the same picture, all with different combinations of artists
cause I think sometimes to unwind, artists have a favorite part of the process. some of us just like to do rough messy sketches of an idea. some like to zen out doing lines but don't have the energy to think of a good subject/composition. sometimes adding shadows and glowing light is the fun part!
idk I'm not a big artists able to start trends or anything but I think it'd be cute and fun to have a tag that says "yeah feel free to add to this and pass it on (or finish it)"
like... #opencollab or something? hmm
241 notes
·
View notes
Text


1 palette 2 artists challenge I did with @ kouwarra on twitter ft. Caeheng!!
372 notes
·
View notes
Text
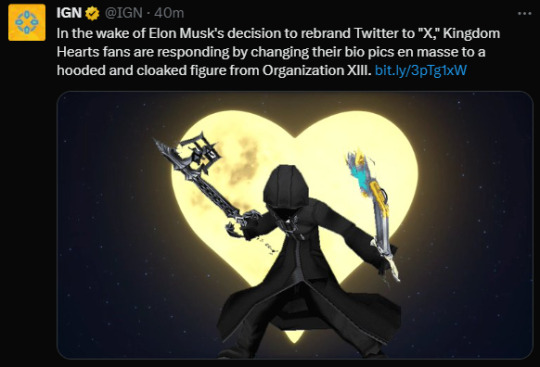
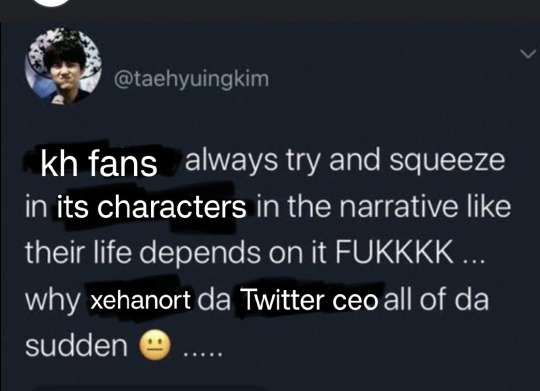
im loving watching the downfall of twitter as a kh fan bro
11K notes
·
View notes
Text
The Denial of Service
So as we all know, malware are a really big headache to deal with when it comes to computers. But there’s another threat to our ability to post on tumblr or watching carrot farming tutorials on youtube: Denial of Service attacks.
This threat has, just like malware, pretty much always been present since the dawn of internet. But only recently has it reached Really Bad Levels. As usual, no prior computer science education needed.
What is it?
A Denial of Service attack, often abbreviated as DoS, occurs when a large amount of junk data is sent to a server or network to deal with. Basically overloading the server so it can no longer be used by anyone. Think of it as if you entered a store and stand in line to make your purchase, but the customer currently making their purchase is spamming the poor cashier with useless questions like “do you know what the time is?”, “do you have this shirt in a pink shade?”, “what time do you close on December 13th next year?”, etc. For hours. Literally until the store closes, and you have to leave the place without having made the purchase. In a computer you will see this as an error of being unable to connect to the server after waiting a long time for a site to load.
Today it’s hard to pull off a DoS attack by yourself - back in the day when the internet wasn’t very fast and servers didn’t have a lot of capacity, one person could cause servers going down using only one computer, comparable to how stores usually only had one cash register. But today servers and networks have a much higher capacity to deal with connection requests, just like how many stores have multiple checkouts. And it’s also fairly easy to stop a DoS in progress by blocking the source IP address from connecting or through other means. Therefore DoS attacks have evolved into what’s known as Distributed Denial of Service (DDoS) attacks.
A DDoS is a coordinated attack from multiple sources (IP-addresses) that’s simultaneously sending a large amount of junk data to the same target server or network, so that instead of the store having one annoying customer taking their sweet time at one cash register, it’s instead flooded by literally thousands of identical annoying customers occupying the cash registers. But how can this be done? Well, one of the most common ways is…
DDoS botnets
In order to achieve a large scale DDoS you of course need a large amount of devices capable of sending requests to the target server. I briefly wrote in this post about a few types of malware, where trojans are often responsible for zombifying your computer into a botnet, where it is remotely controlled to perform tasks you have no idea about. One of the first and most famous malwares capable of performing DDoS attacks was the worm MyDoom, that back in 2004 spread through pirated music sites like Kazaa or email, and ended up infecting so many machines that it was estimated to be the consumer of 20 - 30% of the worlds internet traffic during its spreading. It was programmed to on specific dates initiate a DDoS from the infected machines to the sites www.sco.com followed by www.microsoft.com, and successfully brought down those sites to their knees, prompting other large sites at the time to temporarily or permanently change their addresses, just in case they were the next target in the devastating MyDoom’s code.
Today we have a serious security issue with what’s known as the Internet of Things (IoT), these are non-computer devices connected to the internet, such as surveillance cameras, baby monitors, routers, even refrigerators and cars. Security for these appliances are usually nothing more than decorational or even non-existant. Due to people not deeming it important to have their IoT devices secure - after all, there’s no personal data or files stored in a baby monitor so what’s there to protect - it’s ripe for the taking when it comes to new members of botnets. IoT devices usually come with a standard admin login username and password, such as “admin” with “12345″ as password. Very few people change this. For example, the routers of a Danish internet service provider TDC once delivered their routers all with the same standard username and password, which means that if you only knew what that was, you could log in to every TDC-provided router in Denmark unless the user had changed it, which very few did.
This type of shit security led to the largest DDoS attack in history, caused by the Mirai botnet that infected millions of IoT devices, mostly cameras, using nothing more than a list of standard usernames and passwords to break into them. The attack was carried out against Dyn’s servers, which are a DNS service (basically responsible for upholding addresses to sites, not unlike a phone book - this is where you go after entering an address, which your browser checks up with the DNS service handling that address and translates it to the IP of the site) to many large companies such as Spotify, Netflix, Reddit, Amazon and many more, which means these sites and services were unavailable or extremely slow for several hours during Friday and Saturday on October 21 - 22 (as of 2016 when this post was written. A new record was detected on February 14th of 2023).
Denial of Service as a service
So Why are these attacks occurring? What’s the gain? Well there’s usually a few reasons behind them. it could be for monetary gain, either to beat the competition or to extort. For example, say that you have an unscrupulous seller of fireworks, and to hog all the customers, they launch a DDoS attack against their competitors just days before new years, ensuring that nobody can order from the competing sites. DDoS attacks can also be in extortion, threatening to keep up the attack unless the victim pays.
Revenge or simply as a form of activism have also been reasons behind DDoS attacks. It’s rumoured that users from WikiLeaks were behind the Mirai botnet attack as a protest against Julian Assange being deprived of an internet connection. Yeah…
DDoS attack kits are bought and sold quite openly, usually under the disguise of “stress testing software” for legitimate testing on how much traffic a service or server can handle, or you can even pay like a subscription to have a DDoS carried out against a desired target for X amount of money per month. Digital crime as a service is rapidly expanding and with the introduction of ransomware, it even surpassed the illegal drug trade in revenue. This means your devices are gold mines if accessible to criminals and the reason why security for even the seemingly most insignificant device is so important.
DDoS attacks are usually very tricky to stop, but the thing you can do as a mere user is making sure botnets don’t become strong enough to carry out such large scale attacks. Always change the standard password for your devices and keep your systems updated and protected by antivirus software if possible.
That’s all I had to write about this for now. It’s a very complex and intricate subject really, but I hope I managed to convey at least some basics in a way that made sense and also not 300 pages long. But if you have any questions, my inbox is open. :)
2K notes
·
View notes
Text

Old sketch I did for a sketch trade with a friend :). They did such a great job, check out their -> work!
115 notes
·
View notes