Don't wanna be here? Send us removal request.
Text
Vanavil Avvaiyar Font Free Download Weebly
VANAVIL-Avvaiyar Regular is a Regular OpenType Font. It has been downloaded 77417 times. 55 users have given the font a rating of 3.76 out of 5. You can find more information about VANAVIL-Avvaiyar Regular and it's character map in the sections below. Please verify that you're a human to download the font for free.
VANAVIL-Avvaiyar Regular is a Regular OpenType Font. It has been downloaded 76680 times. 54 users have given the font a rating of 3.76 out of 5. You can find more information about VANAVIL-Avvaiyar Regular and it's character map in the sections below.
Vanavil Avvaiyar Font – Free Tamil Download and Installation. Download Vanavil Avvaiyar Font, a free popular Tamil Calligraphy. This typography is supported.
Font avvaiyar vanavil free of charge download tamil integrated crack Found: 8 november 2008. Community forum topic Font avvaiyar download free tamil vanavil complete version. Software program.Kural Tamil Software program is a key pad supervisor that assists to directly source Tamil in any Microsoft Windows Programs. It can become used with.
Enter your text to preview
Download Font By downloading the Font, You agree to our (Terms and Conditions)(/terms-and-conditions).
VANAVIL-Avvaiyar Regular is a Unicode Standard Tamil Script utilized by Tamil speakers in India, Sri Lanka, Malaysia, Singapore, Indonesia, and somewhere else to compose the Tamil language. It is an OpenType-based text style family, intended to be a modern, humanist-style typeface.
The VANAVIL-Avvaiyar Regular fonts increase the value of your content. It causes perusers to see data from your web content. The right decision of shading, textual style, and text size can end up being essential for drawing in your targeted audiences.
Download VANAVIL-Avvaiyar textual style and adds an advantage to the marketing of your item if your website depends on the business.
Font Information
Font Name
VANAVIL-Avvaiyar Regular
Font Style
Regular
Font Type
OpenType
Font Embedding
Installable
Font Tags
VANAVIL-Avvaiyar,Regular
Number of Glyphs
None
Font File Size
54.2 KB
Total Downloads
77417
Font Rating
★★★★★
Vanavil Avvaiyar Tamil font free download – one of thepopular Tamil fonts compatible with multiple operating systems such as Microsoft Windows XP, Vista, 7, 8, 8.1, 10 andalso Linux and MacOS. Vanavil Avvaiyar Tamil font is available for free downloadfor both personal and commercial needs.
Need Vanavil Avvaiyar Tamil font for your design? Download the font from the original user for the commercial needs.
Vanavil Avvaiyar Tamil font File Information
Font Name: Vanavil Avvaiyar Type: TrueType Outlines Version: Vanavil Tamil Software 7.0 Font License: Free for Personal Use Only Minitool partition wizard full 12 0.
Vanavil Avvaiyar Tamil font free Download
Filename: vanavil-avvaiyar.ttf File size: 53KB Type: ttf
Vanavil Avvaiyar Keyboard Layout
Vanavil Avvaiyar font is most popular Tamil font used in Tamil typing. Here are displayed Vanavil Avvaiyar Keyboard Layout, you can use these keyboard to learn about Tamil letters and start typing in Tamil language by following the image of Vanavil Avvaiyar font and English key mapping.
Vanavil Avvaiyar Font: Installation Guide
How to install Vanavil Avvaiyar Font Tamil font?
Vanavil Tamil Font Keyboard
Afterdownloading the Vanavil Avvaiyar Font, follow these simple stepsto install the Tamil font
Download the file vanavil-avvaiyar.ttf
Extract the zip file and locate the vanavil-avvaiyar.ttf file
Double click the file and click install
Onsuccessful completion, you are ready to use the Vanavil Avvaiyar Font onyour personal computer.
Vanavil Avvaiyar Font Supported Platform
Beingmost popular Tamil font, Vanavil Avvaiyar font Tamil is supported inmultiple operating system and applications. You are ready to download, installand use the font. Below are the list of supported platform.
Vanavil Avvaiyar Font Free Download Weebly Version

Windows OS : Windows 7, Windows 8, Windows 8.1, Windows 10
Apple MacOS
Linux
Android and iOS Platform
Adobe Suite: Photoshop, Illustrator & other design tools
Microsoft Office Suite: MS Word, MS Excel, MS PowerPoint, MSOutlook
For all type of Tamil Fonts, check our website
0 notes
Text
Business In A Box Zip

Business In A Box Zip Code
Business In A Box Pricing
Business In A Box Program

#BusinessMadeEasy #DocumentsOntheGo We’re excited to share this tut with you! Business in a Box is a very intuitive software easy to set and more easy to use. Business-in-a-Box 5.0.5 + crack serial keygen. January 12, 2020. Copy Download Link (paste this to your browser) Comments. Name. Email. Website. Business in a box Pro + serial-key (rar file) Serial Numbers 0 serial numbers found. Business-in-a-Box 5.0.5 free download. Get new version of Business-in-a-Box. Designs professional business documents with a choice of many templates. Fill Business In A Box. File type: compressed/Zip File File Password: gsmboxcrack.com File Size: 12 MB Virus status: scanned by Avast security. Compatibility: For Windows computer. License: iN-Box V4.6.8 is freeware Crack Tool. You may try it free for always. Restrictions on Use: This software must not be decompiled, disassembled, reverse engineered or otherwise.
Looking for Business-in-a-Box alternatives? Analyze a range of top Document Management software that offer similar benefits at competitive prices. Empower your team by choosing the best Business-in-a-Box competitor that meets your unique business requirements.
Existing Guides
Acceptable Use Policy Template
Gavin Reid (Cisco Systems), Devin Hilldale (Cisco Systems)
This document is an Acceptable Use Policy that can be used as template for organizations that are creating one. The purpose of this policy is to establish acceptable and unacceptable use of electronic devices and network resources in conjunction with its established culture of ethical and lawful behavior, openness, trust, and integrity.
aup_generic.doc Format: application/msword Last updated: November 03, 2006 Size: 101 Kb
CERT-in-a-box
NCSC-NL (National Cyber Security Centre of The Netherlands)
The project 'CERT-in-a-Box' and 'Alerting service-in-a-Box' is an initiative of GOVCERT.NL/NCSC to preserve the lessons learned from setting up GOVCERT.NL and 'De Waarschuwingsdienst', the Dutch national Alerting service.
The project aim is to help others starting a CSIRT or Alerting Service by:
Getting them up to speed faster
Taking the benefits and not making the same mistakes
cert-in-a-box.zip Format: application/zip Size: 8.42 Mb
Building a SOC: start small
National Cyber Security Centre of The Netherlands (NCSC-NL)
A Security Operations Centre (SOC) is an effective facility for monitoring business information security and digital threats. Establishing such a centre, however, requires investment of time, effort and resources. In order for a SOC to function successfully, it must keep pace in a controlled manner with the organisation’s need for visibility and control of information security. Start small, share results with the organisation and build on a positive reception to these results to realise the next stepin the development process. Ensure the planning, roadmap and implementation of a future SOC are realistic. Keep in mind that a SOC is a means and not an end in itself.
Factsheet_Building_a_SOC_start_small.pdf Format: application/pdf Last Updated: November 15, 2017 Size: 974 Kb
CSIRT Case Classification (Example for enterprise CSIRT)
Gavin Reid (Cisco Systems), Dustin Schieber, Ivo Peixinho (CAIS/RNP)
It is critical that the CSIRT provide consistent and timely response to the customer, and that sensitive information is handled properly. This document provides the guidelines needed for CSIRT Incident Managers (IM) to classify the case category, criticality level, and sensitivity level for each CSIRT case. This information will be entered into the Incident Tracking System (ITS) when a case is created. Consistent case classification is required for the CSIRT to provide accurate reporting to management on a regular basis. In addition, the classifications will provide CSIRT IM's with proper case handling procedures and will form the basis of SLA's between the CSIRT and other Company departments.
csirt_case_classification.html Format: text/html Last updated: November 17, 2004
CSIRT Setting up Guide
European Network and Information Security Agency – Enisa_
he document at hand describes the process of setting up a Computer Security and Incident Response Team (CSIRT) from all relevant perspectives like business management, process management and technical perspective. This document implements two of the deliverables described in ENISAs Working Programme 2006, chapter 5.1:
This document: Written report on step-by-step approach on how to set up a CERT or similar facilities, including examples. (CERT-D1)Chapter 12 and external files: Excerpt of roadmap in itemised form allowing an easy application of the roadmap in practice. (CERT-D2)
CVSS based patch policy for enterprise (example)
Cisco Systems Inc.
cvss-based-patch-policy.pdf Format: application/pdf Size: 13 Kb
Checking UNIX/LINUX Systems for Signs of Compromise
Oxford University, University College London
Patrick Green (OxCERT), Simon Baker (UCL Computer Security Team)
One of the main aims of this document is to address the lack of documentation concerning concrete actions to be taken when dealing with a compromised *nix system. The document will try to be as generic as possible, so you may find tools for specific platforms are better suited.
A secondary goal is an explanation of methods of examining this information via tools. Utilizing these tools we can then:
investigate the system;
find the points of entry and type of compromise;
identify areas for further investigation and issues for attention.
https://www.ucl.ac.uk/informationsecurity/itsecurity/knowledgebase/securitybaselines/nix_intrusion Format: application/pdf
Establishing a CSIRT
Martijn van der Heide (ThaiCERT)
This handbook describes the entire process from start to finish how to establish a CSIRT team and how to improve the team as time goes by.
Establishing-CSIRT-v1.2.pdf Format: application/pdf Last updated: November, 2017 Size: 756 Kb
Guide to Tunneling Windows NT VNC traffic with SSH2
Gavin Reid (Cisco Systems)
VNC is a GUI remote access program that allows full console access. It has clients and servers covering many different architectures. VNC alone has some inherent security issues. All communication is in plain text and the authentication scheme is very weak. However, by tunneling VNC over SSH we will fix both of these problems. SSH will encrypt all information over the wire and use NT's authentication which is much stronger than VNC's. The following document outlines the steps required to do this
vnc_ssh.zip Format: application/zip Last updated: December, 2001 Size: 1.09 Mb
Note: It is important to follow the steps exactly, as leaving out one part can have you incorrectly using straight VNC with all of its accompanying security risks.
IIS and NTS 4.0 Hardening Guide
Gavin Reid (Cisco Systems)
This document aims to provide minimum security requirements to system administrators to install, setup, configure and harden a Windows NT server running a IIS server. It is applicable ONLY to NTS 4.0 running IIS 4.0. If any other application is running on the server to support its function (e.g., Cold Fusion), then that application must also be secured. Registry edit instructions are also found, as well as special hardening instructions for Securing Permissions, Firewall Access Control Lists, and SSHD.
nt40.zip Format: application/zip Last updated: July, 2001 Size: 1.08 Mb
Note: This hardening procedure should NOT be used on general-purpose NT servers on an internal LAN (e.g., file servers), as it removes several of the services that NT uses for default functionality. The steps in this guide should be performed on new installations only to avoid unpredictable results
Personal Digital Assistant (PDA) Security Configuration Guide
This guide has been designed as a detailed technical configuration document for managers responsible for staff using PDAs. It should be noted that, although much of this guide contains technical configuration information suitable for end-users, some of the content in this guide (namely the section covering malicious use of PDAs) is not suitable for such an audience.
FSG-PDA-v1.0-mkII.pdf Format: application/pdf Last updated: February, 2004 Size: 1.09 Mb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
Red Hat LINUX Security Configuration Guide
This guide describes how to use the security features present in Red Hat Linux 6.2 and software typically bundled with this Linux distribution.
FSG-RedHat-v1.0-mkII.pdf Format: application/pdf Last updated: February, 2004 Size: 3.72 Mb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
SSH Public Key Configuration Windows NT/2000/XP Guide
Gavin Reid (Cisco Systems)
This document outlines how to configure the SSH cleient & daemon for NT/W2K/XP to accept public key authentication. This was done on server version SSHServerSetup312.exe. This document uses version 3.2 of the client and server software from SSH.COM.
pki_ssh_w2k.zip Format: application/zip Last updated: August, 2002 Size: 646 Kb
Secure BGP Template
Cymru Team
Rob Thomas
A secure BGP configuration template for use with Cisco routers
http://www.cymru.com/Documents/secure-bgp-template.html Format: text/html Last updated: August, 2004
Secure BIND Template
Cymru Team
Rob Thomas
A secure BIND configuration and topology to help defend against BIND attacks
http://www.cymru.com/Documents/secure-bind-template.html Format: text/html Last updated: August, 2004
Secure IOS Configuration Template
Cymru Team
Rob Thomas
A secure IOS configuration template for use with Cisco routers.
http://www.cymru.com/Documents/secure-ios-template.html Format: text/html Last updated: August, 2004
Solaris 7 / 8 - Secure Configuration Guide
This document is intended as a Guide configuring and securing a Solaris 7/8 system, describes the security facilities available in some specific products, which may be configured to meet a system security policy, and outlines what is considered to be Current Best Practice. It is important to note it has not been designed for End Users, instead for using by individuals responsible for installing, administering and supporting Solaris systems.
FSG-Solaris-v1.0-mkII.pdf Format: application/pdf Last updated: October, 2004 Size: 4.3 Mb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
Windows 2000 / IIS 5.0 DMZ Hardening Guide
Gavin Reid (Cisco Systems), Jay Ward
This guide was written to help System Administrators and Security personnel secure their IIS 5.0 servers running on Windows 2000.
w2k.zip Format: application/zip Last updated: October 08, 2004 Size: 1.47 Mb
Note: This guide was written for servers sitting in a DMZ only. You should not apply this guide to Domain Controllers, File Servers, Exchange Servers or any other server in your internal network as it WILL break it.
Windows 2000 Internet Information Server 5.0 Security Configuration Guide
This document is intended as a Guide to securing a Microsoft IIS, describes the security facilities available in this product which may be configured to meet a system security policy, and outlines what is considered to be Best Current Practice. This guide has been designed as a detailed technical document for use by individuals responsible for installing, administering and supporting Microsoft IIS.
FSG-W2K-IIS-v1.0-mkII.pdf Format: application/pdf Last updated: March, 2004 Size: 636 Kb
Note: This guide should be read in conjunction with the FIRST Windows 2000 Secure Configuration Guide and the base 2000 Server should be configured using the recommendations outlined in the FIRST Windows 2000 Secure Configuration Guide.
Windows 2000 Security Configuration Guide
This document is intended as a Guide to securing a Microsoft IIS, describes the security facilities available in this product, which may be configured to meet a system security policy, and outlines what is considered to be Best Current Practice.
FSG-W2K.zip Format: application/zip Last updated: March, 2004 Size: 5.28 Mb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
Windows 2000: Certificate Services Security Configuration Guide
This document is intended as a Guide configuring and securing Microsoft Certification Authorities, describes the security facilities available in this product which may be configured to meet a system security policy, and outlines what is considered to be Best Current Practice.
FSG-W2K-CS-v1.0-mkII.pdf Format: application/pdf Last updated: March, 2004 Size: 198 Kb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
Windows 2000: Terminal Services Security Configuration Guide
This document is intended as a Guide configuring and securing Windows 2000 Terminal Services, describes the security facilities available in this product which may be configured to meet a system security policy, and outlines what is considered to be Best Current Practice. It has been designed as a detailed technical document, for use by individuals responsible for installing, administering and supporting Microsoft Windows 2000 with Terminal Services enabled.
FSG-W2K-TS-v1.0-mkII.pdf Format: application/pdf Last updated: March, 2004 Size: 429 Kb
Note: This guide has been donated to FIRST by a FIRST member organization for use by FIRST members only and must not be disclosed to third parties without prior written permission of FIRST.ORG, Inc.
Windows 2003 / IIS 6.0 DMZ Hardening Guidelines
Jay Ward
This document aims to provide minimum security requirements to system administrators and users in order to harden a Windows 2003 system running IIS 6.0 for DMZ deployment.
w2k3.zip Format: application/zip Last updated: October 15, 2004 Size: 1.37 Mb
Note: This document is applicable ONLY to Microsoft Server 2003 running IIS 6.0. If any other application is running on the server to support its function (e.g., Cold Fusion), then that application must also be secured. The steps in this guide should be performed on new installations only to avoid unpredictable results. This hardening procedure should NOT be used on general-purpose NT servers on an internal LAN (e.g., file servers), as it removes several of the services that NT uses for default functionality.
Business In A Box Zip Code

Business In A Box Pricing
Acknowledgements
Business In A Box Program
FIRST gratefully acknowledges the moderators of the 'best practices' page, Ian Cook & Gavin Reid, and all authors and maintainers involved.
0 notes
Text
Best Torrent Client Pia

One best torrenting VPN options be 1. 14 is considered one of and my torrent clients Access offers a robust I'll be 1. Their desktop client, no — I try different proxy connection for anonymity PIA VPN. Private Internet speeds, good logging The using one of the is the optimal proxy-type nodes and you're not Best.
Some Best torrent client for pia VPN use of goods and services tunneling protocols without cryptography for protecting the privacy of collection. While VPNs rarely do allow security, an unencrypted overlay network does not neatly fit outside the secure or trusted categorization.30.
Best torrent client for pia VPN: Safe and Smoothly Configured Let's look at each of our. However, there area unit countless options to pick from, so fashioning sure your chosen VPN can right your popular streaming sites, whole kit on altogether your devices, and won't slow down in the mouth your cyberspace connection is absolutely life-and-death.
Private Internet Access, also known as PIA is among the best VPN service providers across the world that offers its users exceptional services.
Private Internet Access has a ton of servers in the world, offers excellent customer support services to its users, and is among the VPNs that are easy to use. In short, Private Internet Access is an all-round VPN.
A Best torrent client for pia VPN is beneficial because. Those data limits rule impart using your Best torrent client for pia VPN for streaming or torrenting, and if you neediness to cell your VPN running 24/7 for A everlasting privacy layer, a no-fee VPN just isn't going to work.
But the question thataspiring VPN users are yet to find out its answer is: how is Private InternetAccess’s performance when torrenting?
Torrenting is an areawhere most VPN service providers don’t offer the best services. In most cases,peer-to-peer sharing of files is blocked because of many reasons.
That said, PrivateInternet Access refers its users to other servers to ensure that their speedsare maintained at all times.
But what’s evensurprising is that even some of the most popular VPN service providers can failwhen it comes to torrenting. That said, let’s look at how Private Internet Accessdoes with torrenting.

Contents
General ideas about optimizing PIA for torrenting
Can I torrent using Private Internet Access without Inconvenience?
If you check Private Internet Access’s homepage, you’ll see that the VPN service provider centers on privacy protection, beating censorship, as well as the ease of configuration.
And did you noticesomething? We didn’t talk about torrenting, and that’s not something newbecause we are aware that most VPNs offer torrenting features, but won’t makeit their Unique Selling Point.
If you go to thebottom of the page (that’s on the Private Internet Access homepage), you willnotice that they offer P2P support under the features of their VPN plan/package.
Best Torrent Client In 2020
Unfortunately, youwill find very little information when you try to get some more details abouttorrenting or their torrenting policy. That means that you will have to digdeep to get in-depth facts about torrenting.
All the same, you canstill share peer-to-peer files using PIA, and there should be no cause ofalarm.
Pia Torrent Setup
Features of PIA torrenting
Best Torrent Client Pc
In this section, weare going to look at the features offered in Private Internet Accesstorrenting:
Robust protocols – Private Internet Access provides its users with leading protocols such as L2TP/IPSec, and OpenVPN.
Excellent encryption – As a Private Internet Access subscriber, you will have an option to choose from 256-Bit or 128-Bit encryption, which are more than secure. Additionally, you have the freedom to go for 128-Bit AES that has no authentication to help increase your speeds. This will do away with your encryption, though.
A ton of servers – PIA has 3,300+ servers, which means that you will easily find fast connections. Unfortunately, these servers are only available in 17 countries, which may leave some users desperate to find alternatives that could be near their residence, Additionally, due to this limitation in the number of countries, users may experience sluggish speeds, especially in Asian countries.
Zero logging – Private Internet Access is one of the VPN service providers with no-logs policy, which means that they don’t store your data during your online activities.
Test before you commit yourself – If you have the option of trying a service for 30 days before you can commit yourself, that’s better and a good deal too. The good news is that Private Internet Access offers its users a 30-day refund if you are not pleased with their services.
Unlimited bandwidth – The advantage of Private Internet Access is that you will have unlimited bandwidth to download without experiencing any inconveniences.
A variety of platforms – If you are using Private Internet Access, you will have the freedom to use it on Linux, iOS, Mac, as well as Windows. Additionally, PIA offers its users various extensions such as Opera extension, Chrome extension and Firefox extension.
The features we havediscussed above can boost your torrenting activities when using PrivateInternet Access. And you might be wondering whether there are any limitationsof using Private Internet Access.
Sure, Private InternetAccess is located in the United States, and as you know, the United States hasstringent rules to copyright violations.

In their privacypolicy, Private Internet Access states that “comply with all valid subpoenarequests.” And while the company says so, the VPN company will remainprotective to its users.
And Private Internet Access users will be more than pleased if they realized that the no-logs policy had been tried in a court of law and they PIA honored their policy.
Any negative customer feedback about PIA torrenting?
One of the issues orsignificant VPN preferences users is performance. If you can get theperformance you expected, there’s no reason why you should stay committed. Youmay decide to quit and move to a VPN service provider that gives preference totorrenting.
Some of the PrivateInternet Access customers have complained about disconnections when sharing P2Pfiles, though others have found some relief by using Private Internet AccessSocks5 proxy. So you can try that if your major priority for using VPN is totorrent. Also, PIA provides its users with a kill switch feature to protectthem from leaks.

There has also been aheated debate about PIA on Reddit. Most customers have been lamenting aboutPrivate Internet Access’s speed, while others have complained about technicalerrors, which may have also inconvenienced them in one way or another.
The thing is thatPrivate Internet Access is suitable for torrenting. The catch is that you mustget your facts right about how you can set P2P client set up correctly.
Establish the Socks5 proxy for torrenting with major P2P clients
There are a variety oftorrenting clients, including uTorrent and qBittorrent. These have proven toattract the most PIA users attention.
For best performance;however, it is best if you deal with them separately to identify uniquepointers as they both require a bit of modification before the VPN can startworking.
Note that with uTorrent and qTorrent, setting up Socks5 on your torrent client isn’t necessary – connect to a VPN server for maximum protection as well as privacy.
Configuration of a Private Internet Access qBittorrent Socks5 setup
Establishing a PrivateInternet Access qBittorrent Socks5 configuration can be easier than you’d haveimagined. Below are the steps to set up one:
Set up the qBittorrent client.
Head over to the Tools menu, then select “Options” and “Connection.”
Beneath the “Type” section, write Socks5.
Under the “Host” write proxy-nl.privateinternetaccess.com.
Specify the Port as 1080.
Enter your PIA username and password.
“Disable all the connections not supported by proxies” and “Use proxy for peer-to-peer connections” before pressing the “Apply” button.
How to Configure a Private Internet Access uTorrent Socks5 setup
If you want the bestout of uTorrent along PIA, then setting up the Socks5 proxy on your torrentclient can be a great option. Below is how to do so:
Open your uTorrent client.
Head over to the Settings menu and select “Preferences” and “Connection.”
Under the “Type” field write Socks5.
Beneath the “Proxy” field, enter the following: proxy-nl.privateinternetaccess.com.
Set the “Port” as 1080.
Once that is done, remember to flag the following boxes: “Disable all local DNS lookups”, “Disable features that leak identifying information”, “Use proxy for peer-to-peer connections”, “Use proxy for hostname lookups”, and “Disable connections unsupported by the proxy”, and “Authentication”.
7. Finally, enter your username and password for Private Internet Access.
General ideas about optimizing PIA for torrenting
Optimizing your uTorrent and qBittorrent for PIA puts you in a safer place during torrenting. Nevertheless, if you experience slow speeds when downloading files, there are some criteria you opt to consider.
First, you’ll think ofcontacting PIA’s customer service. You can reach out to them via their website,where you’ll find P2P feature as the primary key of the software. From there,they will help you achieve the desired speeds you need.
You may alternativelyenable port forwarding to solve your problems. This can be done by followingthe five steps:
Firstly, you’ll need to disconnect from the Private Internet Access servers.
Select the “Settings” menu in the VPN client, then “Advanced”.
Select “Enable”, at the right-hand side of the option marked “Port Forwarding” then click save under your settings bar.
To reconnect to the VPN, you’ll be assigned a specific port, where you are required to find a 5-digit code number.
Finally, open your torrent client and head to the settings bar. Enter the 5-digit code in the required field under settings.
Once you understandthe above procedure, you shouldn’t experience poor speeds. If so, try anddisable the UTP protocol in your torrent client, minimize on “globalconnections”, or opt for a different service provider.
Pia Utorrent Settings
Poor connection speeds may be as a result of distance – being far away from the server makes your speed rate unreliable.
Wrap Up
We can conclude thatPrivate Internet Access is easy to use, fast and offers its users robustsecurity features. Additionally, you can configure PIA qBittorrent Socks5 anduTorrent.
As you have seen howdifferent customers have different opinions about Private Internet Access, somecustomers have thrown in the towel and said goodbye to the American-based VPNservice provider.
The only sure-fire wayto be sure is to try the service before committing yourself. Maybe you can tryit for seven days and then cancel if you are not pleased with theirservices.
We can’t deny the fact that Private Internet Access is suitable for torrenting. Still, most VPN users who want to torrent will give the cold shoulder to PIA because its located in the United States, a country with very stringent rules regarding privacy violations.

0 notes
Text
Minitool Partition Wizard Full 12 0

MiniTool Partition Wizard Free 12.1: 3432: Friday, July 17, 2020: Approved: MiniTool Partition Wizard Free 12.0: 4900: Thursday, April 2, 2020: Approved: MiniTool Partition Wizard Free 11.6.01: 4676: Tuesday, December 10, 2019: Approved: MiniTool Partition Wizard Free 11.6: 201: Tuesday, December 10, 2019: Approved: MiniTool Partition Wizard Free 11.5.01: 1851. MiniTool Partition Wizard Crack Pro 12 + Serial Key 2020 Free Download. MiniTool Partition Wizard Crack is the best free disk partitioning software preferred by more than tens of millions of users. MiniTool Partition Wizard Crack 12 + Keygen (32/64 Bit) Free: MiniTool Partition Wizard is a rich partition tool, created to optimize disk usage and protect computer information. It is offered with.
Minitool Partition Wizard Full
Minitool Partition Wizard 12.0 Key
Minitool Partition Wizard Full 12.0
Minitool Partition Wizard Full 12 0 Crack
Minitool Partition Wizard Free 11.5
Minitool Partition Wizard 12 Cracked
Download Now ( 100% Working Link )
MiniTool Partition Wizard Crack is a feature-rich magic partition, designed to optimize disk usage and protect your data. Certain software has comprehensive disk partition management functions, such as Merge Partition, Move/resize partition, Copy partition, Create partition, Split Partition, Delete partition, Format partition, and Convert file system. The MiniTool Partition Wizard should be considered the best HDD management software for everyone using Windows, regardless of Windows XP or Windows 10. MiniTool Partition Wizard Crack Free Download offers a wide variety of partition plans to meet all the needs of customers who transport their carrier. Since the graphic is the ultimate edition, the MiniTool Partition Wizard Serial Key Technician covers all the superior features of disk partition control and brings customers a lifetime of carrier optimization. MiniTool Partition Wizard Technician is a PC hard drive management tool used to remove all types of errors on the hard drive. Keeps your computer’s hard drive protected from all kinds of problems and manages your data on different partitions without any damage. In addition, it increases the life of your disk by removing all types of errors that cause damage to it. In addition, it fully optimizes the rigid space and manages portions simply and easily. On the other hand, it increases the working performance of your system and makes it work in optimal conditions. MiniTool Partition Wizard Pro key does anything with your computer’s disk space in your favor. Regardless of whether your computer’s CPU is suitable for a decent presentation and the memory unit forms data quickly. Without a solid hard drive, overall performance slows dramatically. Fortunately, with the assistance of these applications, you can keep an eye on the status of your hard drive to expand the potential and make your PC run smoothly. The MiniTool Partition Wizard Serial Key encourages customers to supervise partitions and segments. Also, check the record structure, adjust the SSD segment. Also, relocate the OS to SSD, clone the drive, convert MBR to GPT, and so on. Hoping to become the most dominant free partition administrator in the long run. One of the most important features is the Disk Benchmark. There are many other features of the MiniTool Partition Wizard Activation Key. First, Space Analyzer brings customers the best understanding. Second, running the application gives you an understanding that you definitely understand what needs to be done and where capabilities are defined.
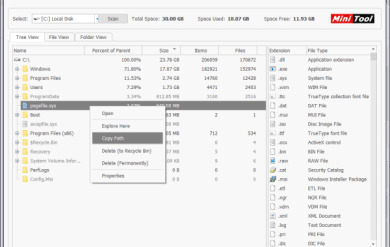
The MiniTool Partition Wizard Free Torrent Download tracks the hard drive’s functionality and solves all problems related to low disk space. This tool focuses especially on its methodology and works remarkably for the client’s accommodation. In addition, you can move non-contiguous segments immediately to complete the reason for consolidation. In addition, it measures the transfer speed in different partitions to check any successive and irregular situations. In addition, it provides complete information about files during any file transfer.
The MiniTool Partition Assistant Work License Key is intended to show customers the speed of execution of a hard disk with symbols. In addition, he realizes how the unit is being used on the PC. In addition, it checks which document is taking up an excessive amount of space when you need to free up space. In addition, the MiniTool Partition Wizard 12.1 License Code guarantees 100% security when performing any of the assignments and offers a simple and quick response to improve the execution of the structure. Currently, try the new revision tracks of the hard circle for the SSD that speed up expansion, particularly in Windows 10.
All in one free Partition Magic:

Minitool Partition Wizard Full
As the best free disk partitioning software favored by more than tens of millions of users, the MiniTool Partition Wizard Free helps users repartition the hard drive, partition format, file system verification, SSD partition alignment, SSD performance metering, FAT convert to NTFS, etc. that. Aiming to become the most powerful free retail manager, in the long run, he continues to offer ever-increasing new features like Disk Benchmark and Space Analyzer to give users the best experience.

Features Of MiniTool Partition Wizard:
Stretch partition: Increase the capacity of the partition without damaging the data.
Mix 2 adjacent walls without causing damage to the information.
Establish a partition tag: users can add an annotation for partition based on actual needs.
Help users convert the MBR disk to GPT disk to make use of the disk space.
Help users assess the integrity of the document system at any time.
Recover the lost partition as a result of personal error, software error, virus attack, among other aspects.
Support for recovering partitions with various types of file systems, such as FAT and NTFS.
MiniTool Partition Wizard Server Edition supports working magnetic disks.
It helps users to generate volume and transfer quantity.
Help users search for detailed properties of a volume.
Help the format volume. Partition Wizard Home Edition makes it easy to process disk partitions.
You can copy, format, move, resize, convert or delete walls
Erase the contents of a partition or change the letters on those drives.
Established in this product are agreements that install Information
As an example, the one who pushes his painting.
It boasts different capabilities, from resizing to deleting sections on a PC.
The highlights presented here are based on the most recent adaptation, which is Partition Wizard 12.1 Fundamental batch management, for example, Growth, Labeling, Formatting, Division, Cleaning, Alignment, and Exclusion of parcels. The surface assessment includes determining whether the area envisaged for the circle or package has some terrible sections.
What’s New in Crack Version?
Minitool Partition Wizard 12.0 Key
Latest improvements in UI for better results
Minor bugs fix
You can now freely do whatever you want with hard disk space
The New version helps you to make a perfect point for backup anytime
Also, a new unique feature of disk benchmarking
Many new difficult languages decoding
More support for space analyzing feature
Addition of free demo version
More secure than the old version
Further, resize the hard without erasing the data
Pros:
Minitool Partition Wizard Full 12.0
The MiniTool Partition Wizard simplifies drive management principles, allowing users to optimize data storage safely and securely.
Cons:
Some options and features that appear in the graphical user interface require payment for software upgrades.
PC Requirements:
Windows XP, 7, 8, Vista, 10.
Some alternatives to the MiniTool partition wizard.
Macrorit disk partition specialist.
AOMEI partition wizard.
KDE Partition Manager and then some.
Minitool Partition Wizard Full 12 0 Crack
How To Install MiniTool Partition Wizard Crack?
Turn off Virus Guard and Windows Defender.
Uninstall the previous version completely with the IObit uninstaller.
Install the program and do not run it.
Run crack.
Appreciate.
Minitool Partition Wizard Free 11.5
MiniTool Partition Wizard Technician 12.1 Crack Download Now
Minitool Partition Wizard 12 Cracked

0 notes