Identity Skills is a Training and counseling firm that helps individuals learn niche skills that are in demand in the IT industry, grow in terms of knowledge and grab the most demanding jobs and opportunities in the Industry. www.identityskills.com
Don't wanna be here? Send us removal request.
Text
CyberArk Tutorial for Beginners: A Step-by-Step Guide to Getting Started
In cybersecurity, privileged account security is one of the most important things to do. That is where CyberArk plays its role. If you are a newcomer who would like to have an idea about how CyberArk functions and how you can start learning it, then you are in the right place. This novice tutorial on CyberArk will guide you through the basics of CyberArk, its fundamental parts, and how you can start your training procedure.This CyberArk tutorial for beginner offers a simple and structured path to understand core concepts, making it ideal for anyone starting their cybersecurity journey.

What is CyberArk?
CyberArk Privileged Access Management (PAM) solution secures, monitors, and manages privileged accounts and credentials. These accounts grant immense access to systems, databases, and apps — and thus are the hacker's favorite target.
CyberArk is widely used across sectors to minimize the threat of data breaches by securing credentials and managing access.
Why Learn CyberArk?
Here's why CyberArk is so widely used:
Large corporations such as Wipro, Infosys, Accenture, and Deloitte leverage CyberArk.
CyberArk-certified experts receive plush salaries.
There is an increasing demand for more and more cybersecurity professionals who can handle privileged access.
CyberArk training differentiates you in the cybersecurity, IT management, and DevOps professions.
Core Concepts of CyberArk
Before diving into how to use CyberArk, let’s understand its main components:
1. Vault
The heart of CyberArk. It securely stores passwords and credentials.
2. Central Policy Manager (CPM)
Manages password changes and enforces security policies.
3. Password Vault Web Access (PVWA)
The web-based user interface used by administrators and users.
4. Privileged Session Manager (PSM)
Monitors and records user sessions for compliance and audit.
CyberArk Architecture Overview
CyberArk’s architecture typically includes:
Vault Server for secure storage
Application Servers running PVWA, CPM, and PSM
Active Directory for user authentication
User Workstations for accessing resources
CyberArk Tutorial for Beginners: Step-by-Step Learning Path
Step 1: Understand the Basics
Start with a clear understanding of what PAM is, how privileged accounts work, and the security risks involved.
Step 2: Learn the Architecture
Understand how the Vault, CPM, PVWA, and PSM interact.
Step 3: Install a CyberArk Lab (Optional)
While full installation can be complex, many training platforms offer simulated environments.
Step 4: Hands-On Practice
Add a new user
Store a password in the Vault
Configure policy management
Launch a session via PSM
Step 5: Explore Advanced Topics
Once you're comfortable with the basics, dive into topics like:
CyberArk API Integration
Scripting with PACLI
Managing secrets for DevOps
Step 6: Prepare for Certification
The CyberArk Defender Certification is ideal for beginners. It validates your practical skills in real-world scenarios.
Tips for Effective Learning
Use video tutorials and official CyberArk documentation.
Practice using a lab or training platform.
Join online forums and discussion groups.
Work on real-time scenarios or mock projects.
Where to Learn CyberArk Online?
Looking for a structured way to learn CyberArk from scratch? Check out Identity Skills for:
Instructor-led CyberArk online training
Real-time lab access
Interview preparation support
Certification guidance
Final Thoughts
CyberArk is a valuable skill in today’s security-first digital world. With this beginner-friendly CyberArk tutorial, you now have a roadmap to begin your journey. Whether you're a student, IT administrator, or aspiring cybersecurity analyst, learning CyberArk can take your career to the next level.
Ready to become a CyberArk expert? Enroll in CyberArk Online Training at Identity Skills and start your transformation today.
#cyberark training#cyberark training in noida#identityskills#cyberark training in bangalore#cyberark online training#cyberark certification#cyberark training in india#online cyberark training#cyberark#cyberark course
0 notes
Text
Why Choose CyberArk Training in Bangalore? Course Features, Fees, and Benefits
In today’s cybersecurity landscape, privileged access management (PAM) is critical for protecting sensitive data from breaches. CyberArk, the industry leader in PAM solutions, offers specialized training to help IT professionals master identity security.

If you're in Bangalore—India’s tech hub—enrolling in CyberArk training can fast-track your career in cybersecurity. This guide covers course features, fees, benefits, and why Bangalore is the best place to learn CyberArk.
Why Learn CyberArk in 2024?
CyberArk is the #1 privileged access security solution, used by Fortune 500 companies and governments worldwide. Here’s why training in CyberArk is valuable:
✅ High Demand – 60% of cyberattacks involve privileged credentials (Forrester). ✅ Lucrative Salaries – CyberArk-certified professionals earn ₹10-25 LPA in India. ✅ Career Growth – Roles like PAM Engineer, Security Analyst, and IAM Specialist require CyberArk skills. ✅ Industry Recognition – CyberArk certifications are globally respected.
CyberArk Course Features in Bangalore
Bangalore’s top training institutes offer hands-on CyberArk training with:
1. Comprehensive Curriculum
CyberArk architecture & components
Privileged Account Security
CPM (Central Policy Manager) & PSM (Privileged Session Manager)
Vaulting & credential management
Implementation & troubleshooting
2. Live Lab Access
Real-world CyberArk deployments
Practice on CyberArk PAS (Privileged Access Security)
Simulated cyberattack scenarios
3. Expert Trainers
Certified CyberArk professionals with industry experience
Corporate training background
4. Certification Prep
Covers CyberArk Defender & Sentry exams
Mock tests & interview preparation
Benefits of CyberArk Training in Bangalore
1. Thriving Cybersecurity Job Market
Bangalore has 1,000+ cybersecurity job openings (Naukri.com).
Companies like Wipro, Infosys, Accenture, and IBM hire CyberArk experts.
2. Hands-On Learning
Corporate-grade labs for practical exposure.
Internship opportunities with IT security firms.
3. Networking & Placement Support
Meet industry experts in workshops.
Resume-building & interview sessions.
Who Should Take CyberArk Training?
✔ IT Security Professionals (looking to specialize in PAM) ✔ System/Network Administrators (transitioning to cybersecurity) ✔ Freshers (with basic IT knowledge) ✔ Security Consultants (expanding their skill set)
CyberArk Certification Path
CyberArk Defender (Entry-level)
CyberArk Sentry (Advanced)
CyberArk Guardian (Expert)
FAQs
Q: Is CyberArk training difficult?
A: No—with hands-on labs and expert guidance, beginners can master it.
Q: Can I get a job after CyberArk certification?
A: Yes! Bangalore has 500+ CyberArk job postings monthly.
Q: Does CyberArk require coding knowledge?
A: Basic IT skills are enough—no coding expertise needed.
Final Verdict: Is CyberArk Training Worth It?
If you want a high-paying, future-proof cybersecurity career, CyberArk training in Bangalore is a smart investment. With top institutes, corporate demand, and hands-on labs, you’ll gain skills that employers value.
🔗 Ready to start? with Identity Skills and enroll today!
#cyberark course#cyberark training#cyberark training in noida#cyberark training in bangalore#cyberark online training#cyberark certification#cyberark
0 notes
Text
0 notes
Text
Your Ultimate Guide to CyberArk Training: Expert FAQs
If you're considering CyberArk training or looking to deepen your understanding, you're likely to have some questions. Here, we've compiled answers to the most frequently asked questions about CyberArk training, answered by industry experts.

1. What is CyberArk Training?
CyberArk training focuses on teaching individuals how to use CyberArk’s suite of identity security solutions, which include tools for protecting privileged access, managing credentials, and securing sensitive systems. The training provides in-depth knowledge of how to deploy and manage CyberArk's products, ensuring that professionals can protect their organization’s digital assets.
CyberArk training programs are designed for a range of skill levels, from beginners to advanced practitioners, and typically cover topics such as:
CyberArk Privileged Access Security (PAS)
CyberArk Vault (Centralized Credential Store)
Session Recording and Monitoring
Threat Detection and Response
Managing Access Control Policies
2. Who Should Take CyberArk Training?
CyberArk training is ideal for professionals working in IT security, system administration, and network management. Specifically, the training is beneficial for:
Cybersecurity Analysts and Engineers: Who need to understand how to protect sensitive systems from threats and mitigate risks related to privileged access.
Network Administrators: Who are tasked with configuring and maintaining IT infrastructures, particularly around secure access.
DevOps Engineers: Who need to integrate security practices, such as identity management, into the DevOps lifecycle.
IT Managers and Directors: Who oversee the implementation and management of cybersecurity practices within an organization.
Auditors and Compliance Officers: Who need to ensure that their organization’s privileged access policies align with regulatory requirements.
3. What Are the Prerequisites for CyberArk Training?
While CyberArk training can accommodate beginners, it is recommended that participants have a basic understanding of cybersecurity concepts. It’s beneficial to be familiar with:
Basic IT systems and network security
Identity and access management (IAM) principles
Basic understanding of Linux and Windows operating systems
Familiarity with security best practices
Some courses may also recommend prior knowledge of other security tools or frameworks, although this is not always mandatory.
4. What Types of CyberArk Training Are Available?
CyberArk offers several training options to suit different learning preferences and career goals:
Instructor-Led Training (ILT): This is the traditional classroom-style training where you learn directly from experts. It includes hands-on labs and real-world scenarios to help you apply your knowledge.
Virtual Instructor-Led Training (VILT): For those who prefer a remote learning experience, CyberArk offers virtual classrooms, which provide the flexibility of online learning with the benefit of direct interaction with instructors.
Self-Paced Training: CyberArk also offers online courses that you can take at your own pace. These courses include video lessons, quizzes, and exercises, making it an excellent option for self-motivated learners.
On-Demand Labs: For those who want hands-on practice with the tools and systems used in CyberArk, on-demand labs are available to simulate real-world environments and apply the training material directly.
5. How Long Does CyberArk Training Take?
The duration of CyberArk training depends on the course type and your experience level. Typically, the instructor-led courses last between 2 to 5 days, while self-paced training can be completed in a few weeks, depending on your schedule and availability.
CyberArk certifications also vary in terms of time commitment. For instance, you may need several weeks of study and preparation before attempting the certification exams.
6. What is the CyberArk Certification?
CyberArk offers a certification program that validates your expertise in deploying and managing CyberArk solutions. The two main certifications are:
CyberArk Certified Trustee (CCT): This entry-level certification focuses on foundational knowledge of the CyberArk Privileged Access Security platform.
CyberArk Certified Defender (CCD): This intermediate-level certification delves deeper into how to manage and implement CyberArk solutions, and is suited for those responsible for the daily operation and troubleshooting of CyberArk systems.
CyberArk Certified Guardian (CCG): This advanced certification is intended for professionals who are responsible for designing and implementing CyberArk solutions at an enterprise level.
Each certification has an exam that tests your practical skills and understanding of CyberArk products.
7. What Are the Benefits of CyberArk Training?
CyberArk training provides several benefits, including:
Enhanced Career Opportunities: As organizations prioritize cybersecurity, certified CyberArk professionals are in high demand. Completing CyberArk training opens up career opportunities in various industries.
Improved Security Posture for Organizations: Trained CyberArk professionals can help organizations implement best practices for identity security and ensure privileged accounts are managed securely.
Industry Recognition: CyberArk certifications are globally recognized, and many organizations require CyberArk-certified professionals to manage their privileged access solutions.
Practical, Hands-On Experience: Training programs are designed to give learners practical skills that can be immediately applied in real-world situations, making you more effective in your role.
8. Is CyberArk Training Worth the Investment?
Yes, CyberArk training is a valuable investment for IT and cybersecurity professionals. With increasing data breaches and cybersecurity threats, organizations are willing to invest in experts who can safeguard their digital infrastructure. CyberArk is a trusted name in the industry, and its training programs prepare professionals to tackle some of the most complex security challenges.
Certified professionals can demand higher salaries and enjoy better job prospects. Moreover, CyberArk’s specialized focus on privileged access management is a critical area of security, ensuring that your training is relevant and highly sought after in the cybersecurity landscape.
9. How Much Does CyberArk Training Cost?
The cost of CyberArk training depends on the course format and level of certification. Instructor-led training can range from $2,000 to $4,000, while self-paced courses may be more affordable, often costing a few hundred dollars. Certification exams also have fees that vary depending on the level of the certification, typically ranging from $250 to $500.
While the initial investment may seem steep, the long-term benefits in terms of career advancement, salary growth, and job security far outweigh the costs.
10. How Do I Get Started with CyberArk Training?
To begin your CyberArk training, you can visit CyberArk’s official website, where you can explore available courses and certifications. You can also enroll in partner-led training programs offered by authorized training centers. It’s a good idea to review the course content and decide which certification level aligns with your career goals.
Many training providers also offer free webinars and demo sessions, so you can get a sense of the curriculum before committing to a full course.
Conclusion
CyberArk training offers invaluable knowledge and skills for cybersecurity professionals who want to specialize in privileged access management. By pursuing CyberArk certification, you gain the expertise to protect your organization's most critical assets from cyber threats, while also advancing your career in the ever-evolving field of cybersecurity.
If you’re looking to secure your career and become an expert in one of the most trusted identity security solutions on the market, CyberArk training in bangalore is definitely worth considering.
Also Read:
How to Prepare for the CyberArk Certification Exam: Tips and Resources
5 Critical Use Cases Where CyberArk Makes a Difference
How CyberArk Course Prepares You for the Future of Cybersecurity
CyberArk Certification Paths in 2025: From Beginner to Expert
0 notes
Text
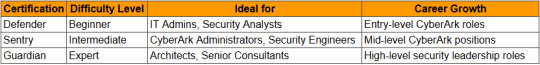
CyberArk Certification Guide: Which Level is Right for You

CyberArk is a driving cybersecurity company specializing in Favored Get to Administration (PAM). With organizations prioritizing security, CyberArk certifications have ended up exceedingly profitable for IT and security experts. But which certification ought to you pursue?
This direct will break down the three fundamental CyberArk certification levels—Defender, Sentry, and Guardian—covering their prerequisites, trouble level, perfect candidates, and career opportunities.
CyberArk Protector Certification
Overview
The CyberArk Guard Certification is the entry-level certification that approves your capacity to work with the CyberArk Advantaged Get to Security (PAS) arrangement. It is appropriate for security experts who oversee and keep up CyberArk environments.
Who Ought to Take It?
IT Administrators
Security Analysts
Help Work area Professionals
Anyone unused to CyberArk
Exam Details
Format: Multiple-choice
Duration: ~90 minutes
Topics Covered:
CyberArk Vault administration
Managing advantaged accounts
CyberArk architecture
Safe administration and account policies
Career Openings After Guard Certification
Junior CyberArk Administrator
Security Operations Analyst
IT Security Specialist
CyberArk Sentry Certification
Overview
The CyberArk Sentry Certification is an intermediate-level certification outlined for security experts who design, troubleshoot, and keep up CyberArk environments.
Who Should Take It?
IT Security Engineers
CyberArk Administrators
Cybersecurity Consultants
Prerequisites
Must as of now hold the CyberArk Shield certification.
Advanced information of CyberArk PAS solutions.
Experience working with CyberArk Vault, CPM, and PSM components.
Exam Details
Format: Scenario-based multiple-choice questions
Duration: ~90 minutes
Topics Covered:
Advanced investigating and log analysis
Integration of CyberArk with other security solutions
Secure session monitoring
Risk relief strategies
Career Openings After Sentry Certification
CyberArk Engineer
Security Arrangements Architect
Identity and Get to Administration (IAM) Specialist
Get More Information For With Identity Skills : Cyberark Training
CyberArk Gatekeeper Certification
Overview
The CyberArk Gatekeeper Certification is the most noteworthy level of certification, implied for specialists and designers planning and executing enterprise-level CyberArk security solutions.
Who Ought to Take It?
Cybersecurity Architects
IAM Specialists
Senior Security Consultants
IT Directors and Group Leads
Prerequisites
Must as of now hold both CyberArk Protector and Sentry certifications.
Extensive hands-on involvement with CyberArk organizations in huge environments.
Deep information of favored get to security strategies.
Exam Details
Format: Hands-on lab evaluations and progressed scenario-based questions
Duration: Changes based on test format
Topics Covered:
Enterprise-level CyberArk plan and architecture
Risk appraisal and compliance
Implementing zero-trust security with CyberArk
Customizing CyberArk arrangements for large-scale organizations
Career Openings After Gatekeeper Certification
CyberArk Security Architect
Privileged Get to Administration (PAM) Consultant
Enterprise Security Manager
Which Certification Ought to You Choose?
Conclusion
CyberArk certifications boost your career prospects in cybersecurity and advantaged get to management.
If you're fair beginning, go for CyberArk Defender.
If you're an experienced admin, CyberArk Sentry is the another step.
If you're pointing for authority and enterprise-level security, seek after CyberArk Guardian.
Would you like offer assistance planning for your CyberArk certification exams? Let me know!
#cyberark certification#cyberark online training#online cyberark training#cyberark training in bangalore
0 notes
Text
The Importance of CyberArk Training for IT Security in 2025
One of the biggest challenges for organizations in the digital age is to prevent security threats. Many organizations pour in a significant amount of money in security solutions to protect their sensitive data from being hacked. Privileged Access Management is most essential and the area in which CyberArk was the first to place itself as a leader. As an IT professional, you would be able to get a remedy for your lack of skill in CyberArk by getting CyberArk Training from India or Tell Your manager to arrange for you any other country of the world. The purpose of this article is to discover why in 2025 CyberArk training, CyberArk courses, and CyberArk certification will be required for IT security professionals.

Growing Demand for Cybersecurity Experts
As cyber threats just do not seem to end, the need for skilled cybersecurity professionals has only seen a growth. According to recent industry reports, the cybersecurity market in the world will expand exponentially and privilege access security will hold the majority of the focus. Current firms become highly inclined towards the requirement of employees with knowledge regarding privilege account management, thus value training CyberArk holds becomes critical .
Why CyberArk?
CyberArk’s one is privileged access management that is one of the best-developed solutions. It can ensure the required constancy of the company’s critical infrastructure against potential threats from inside and cyber-attacks. Virtualization and advanced mobility, as the innovative technologies, have become the cornerstone of modern businesses as digital transformation has gained acceptance. CyberArk certification professionals play a significant role in companies to provide them a clean-slate-freshbeginning that steers away all illegal activities. Hence, CyberArk classes are structured to provide practical IT professionals with the required skills in the management of privileged accounts and the reduction of the risks of security.
How CyberArk Training Enhances Job Prospects
The advantages of joining CyberArk training are:
Career Advancement
There are many large companies that demand professionals with CyberArk certification for privileged access security system management. CyberArk certification professional is highly demanded in the finance, healthcare, and IT services sectors.
High Salaries
Professionals with the expertise of CyberArk are always paid more. Industry reports reveal that CyberArk-certified professionals can earn up to ₹8-20 LPA in India and beyond in other countries.
Industry Recognition
Upon finishing the CyberArk course and being certified, you will turn into a certified privileged access security expert, thus making you as a highly valuable candidate for employers.
Career Growth and Stability
Cyber security threats are mutating and with the ongoing PAM solution investments by companies, the cybersecurity sector will continue to have a variety of job opportunities for the professionals CyberArk trained.
Industry Trends Supporting CyberArk Training
Rise in Cyber Threats
Nowadays, the world is facing more and more complicated cyber attacks, and therefore, the level of requirement for PAM tools that have not been exposed to attack, e.g., CyberArk, has risen.
Stringent Compliance Regulations
Data protection laws such as GDPR, HIPAA, and PCI-DSS, are the ones an organization must abide by and these laws require tight privileged access controls.
Cloud and Hybrid Security Adoption
As businesses transition to cloud environments, the need for CyberArk-certified professionals to manage cloud-based security increases.
Conclusion
The use of this smart move for IT Specialists to become CyberArk experts in India, or around the globe, they will become vital as the dependence on cybersecurity keeps increasing day by day. The CyberArk course not only hones your skills but it also adds to job opportunities in the field that is set to grow. For a futuristic and satisfying career in cybersecurity, it is a good decision to get a CyberArk certification.
So, are you up for a cybersecurity career boost? Begin your CyberArk training today!
#cyberark online training#cyberark course#cyberark training in noida#cyberark training in india#cyberark certification#identityskills
0 notes
Text
Must-Have CyberArk Skills for 2025

As our world becomes increasingly interconnected, cybersecurity challenges are becoming more sophisticated and pervasive. Cybercriminals exploit vulnerabilities through advanced ransomware, phishing attacks, and even state-sponsored espionage. The rapid pace of technological innovation, from cloud computing to artificial intelligence (AI), has transformed the digital ecosystem into a high-stakes battlefield where every device, network, and system is a potential target.
This article explores the top skills every cybersecurity expert must master in 2025 to stay ahead in a rapidly evolving digital landscape.
Core Technology Skills
1. Cloud Security Expertise
The adoption of multi-cloud infrastructures has brought significant opportunities for businesses but also increased complexity. Cybersecurity professionals must master dynamic identity governance, shadow data management, and edge computing security. For example, using advanced tools to detect anomalies like unauthorized access or privilege misuse can prevent breaches before they occur. Additionally, real-time encryption and consistent security policies across platforms are crucial for safeguarding data.
2. Incident Response and Forensics in Hybrid Environments
In hybrid environments, identities often span on-premises and cloud systems, increasing the risk of breaches. Experts need skills in adaptive risk assessments and real-time monitoring to mitigate risks at the access point. When incidents occur, quick containment through tailored playbooks and forensic analysis tools, such as Splunk or Magnet AXIOM, can trace and address the root cause efficiently.
3. AI and Machine Learning for Threat Detection
AI-powered tools have revolutionized threat detection by analyzing massive data streams in real time. Systems like Darktrace can identify and neutralize threats automatically. Adaptive learning and predictive analytics further enable professionals to anticipate and mitigate potential risks. Adding CyberArk online training to a cybersecurity skillset ensures familiarity with automation techniques for privileged access management, enhancing AI-driven threat response strategies.
4. Zero-Trust Security Implementation
The zero-trust model assumes no user or device is trustworthy by default. Implementing multi-factor authentication (MFA), segmenting networks, and continuously monitoring access ensure secure systems. Cybersecurity experts must design zero-trust architectures that protect both on-premises and cloud resources.
CyberArk Certification plays a crucial role here, providing comprehensive knowledge on implementing zero-trust principles for privileged identities and safeguarding sensitive resources effectively.
5. Quantum-Resilient Cryptography
The emergence of quantum computing poses a threat to traditional encryption methods. Cybersecurity professionals must transition to post-quantum cryptographic standards, such as Quantum Key Distribution (QKD). This ensures sensitive data remains secure against potential quantum-powered attacks.
6. Critical Thinking
Modern cyber threats require strategic problem-solving. Critical thinking enables experts to predict attacker behaviors and develop proactive defenses. Techniques like adversarial simulation help professionals think like hackers, identifying vulnerabilities and strengthening systems before attacks occur. CyberArk training provides insights into critical thinking frameworks to mitigate risks tied to privileged accounts.
7. Collaboration and Communication
Cybersecurity is a team effort involving IT staff, executives, and employees. Professionals must explain technical risks in simple terms to ensure everyone understands their role in protecting digital assets. Clear communication fosters trust and promotes a culture of security within organizations.
Why These Skills Matter
The cybersecurity landscape is evolving faster than ever. The rise of IoT devices, AI-driven attacks, and complex hybrid environments demands that professionals not only adapt to new technologies but also anticipate future threats.
In 2025, technical expertise alone will not suffice. Emotional resilience, strategic thinking, and effective collaboration will define the next generation of cybersecurity leaders. Mastering these skills ensures not just the safety of systems but also the trust and continuity of businesses in an increasingly volatile digital world.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
0 notes
Text
Solving 10 Simple Cybersecurity Issues with CyberArk Expertise

In the modern digital landscape, cybersecurity has become an essential priority for businesses, regardless of their size. As cyber threats evolve, so must the strategies and tools used to protect data, systems, and sensitive information. In this blog, we explore 10 common cybersecurity issues and how expert solutions can help organizations address them effectively. For those interested in mastering these solutions, CyberArk online training offers in-depth learning opportunities for individuals looking to gain a competitive edge in the cybersecurity space.
1. Weak and Stale Credentials
Weak passwords and credentials are one of the most common entry points for cyber attackers. A simple yet effective solution is the enforcement of strong password policies and the regular updating of credentials. Automated credential management systems ensure that passwords are changed frequently, are complex, and are not reused across different systems, which significantly reduces the likelihood of a breach.
2. Unauthorized Access to Sensitive Data
Gaining unauthorized access to sensitive data can lead to severe repercussions, such as data breaches and significant financial damage. To combat this, implementing strict access controls ensures that only authorized personnel can access confidential information. This approach helps minimize the risk of unauthorized users gaining access, whether through insider threats or external attacks.
3. Lack of Continuous Monitoring
Cyber threats don’t wait for convenient hours, which is why continuous monitoring of systems is essential. By setting up real-time tracking of user activities, businesses can quickly identify and respond to suspicious behaviors. With tools designed to alert security teams to anomalies, any potential threats can be addressed before they escalate.
4. Failure to Detect Insider Threats
Insider threats are often difficult to detect because the perpetrators already have trusted access to the systems. To mitigate this, monitoring all user activity—especially those with elevated privileges—provides transparency and early detection of any abnormal or unauthorized actions. Logging and recording these activities ensures that if a security breach occurs, it can be traced back and investigated thoroughly. A CyberArk course can teach professionals the skills required to monitor and track privileged access effectively, preventing insider threats.
5. Inadequate Privilege Control
Organizations often struggle to manage who has access to which resources. Without proper privilege control, employees may have more access than necessary, which increases the risk of potential misuse or accidental breaches. A solution to this is implementing the principle of least privilege, ensuring that employees only have access to the resources needed to perform their specific duties.
6. Unmonitored Third-Party Access
Third-party vendors and contractors often require access to internal systems, but this access can introduce vulnerabilities if not properly managed. By monitoring and controlling the scope of third-party access, businesses can ensure that external parties only have access to the specific systems and data they need for their work. Additionally, setting up monitoring for all activities carried out by third-party users provides an additional layer of security.
7. Failure to Track Critical System Changes
Tracking and auditing changes to critical systems are essential for maintaining a secure environment. Untracked changes can lead to vulnerabilities or undetected system compromises. Implementing a system that logs all changes to key infrastructure and provides alerts on unauthorized modifications ensures that businesses can quickly detect any unauthorized activity and respond promptly.
8. Data Loss from Compromised Credentials
Compromised credentials are often the primary cause of data breaches, as attackers can access sensitive information and systems with stolen login details. To mitigate this risk, organizations should implement stronger authentication methods, such as multi-factor authentication (MFA), to protect sensitive accounts. This added layer of security ensures that even if credentials are stolen, unauthorized access remains blocked.
9. Lack of Incident Response Readiness
Having a clear, well-defined incident response plan is crucial in the event of a cyberattack. Many businesses struggle with responding quickly to threats, which can allow damage to escalate. By establishing a comprehensive incident response framework, organizations can ensure that security teams know how to react swiftly, minimizing the impact of an attack and reducing recovery time.
10. Compliance Violations
Many industries face strict regulations regarding the protection of sensitive data. Failing to comply with these regulations can result in hefty fines and damage to an organization’s reputation. By setting up automated systems that track user access and generate detailed reports, organizations can ensure they meet compliance requirements without manual oversight, making audits and reporting much easier. CyberArk training in India helps professionals understand the importance of compliance in cybersecurity and teaches how to ensure that systems stay compliant with industry standards.
Conclusion
Addressing common cybersecurity issues requires a strategic approach that balances technology, policies, and proactive monitoring. From securing credentials and controlling access to detecting insider threats and ensuring compliance, there are a variety of expert solutions available to help businesses safeguard their systems. By implementing these solutions, organizations can significantly reduce the risk of cyberattacks and data breaches, ensuring the security and integrity of their operations.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
0 notes
Text
CyberArk and Zero Trust: A Powerful Combination for Modern Security

In an era where cybersecurity threats are growing more sophisticated, businesses need robust security strategies that keep up with the evolving landscape. One approach gaining significant traction is the Zero Trust security model, which operates on the principle of "never trust, always verify." IdentitySkills, a leader in identity security, pairs exceptionally well with Zero Trust, offering organizations a dynamic approach to protecting sensitive assets.
The Role of Cyberark in Supporting Zero Trust
CyberArk Training focuses on identity security, which is central to implementing Zero Trust. A strong security platform provides organizations with the tools to manage and control who can access specific resources and track what they do once they’re in. By managing credentials, enforcing authentication policies, and monitoring user activity, becomes a critical component of a Zero Trust strategy.
Key features in an identity security platform that align with Zero Trust include:
Identity Authentication and Access Management: Secure, multi-layered authentication helps ensure that only verified users gain access to sensitive resources.
Password Vaulting and Credential Management: Managing and rotating passwords reduces the risk of compromised credentials and unauthorized access.
Continuous Monitoring and Risk Detection: Real-time tracking of user behavior enables quick identification of unusual activity, allowing security teams to respond swiftly.
With these capabilities, an identity security platform provides the structure needed to implement Zero Trust effectively.
How Cyberark Course Enhances Zero Trust
Deploying Zero Trust principles requires a methodical approach to identity and access management. A online cyberark training plays a critical role in several aspects:
Enhanced Identity Verification Zero Trust emphasizes strict verification at every step. Identity security solutions provide tools for multi-factor authentication, risk-based access, and other forms of identity verification, ensuring only authorized users can access resources.
Strict Access Control and Least Privilege In Zero Trust, the principle of least privilege is essential. Users should only have the minimal access needed to perform their roles. Identity security platforms enable fine-grained access controls based on user roles, time of day, location, and other factors, reducing the risk of insider threats by limiting excessive access.
Continuous Monitoring and Threat Detection Continuous verification is crucial for Zero Trust. Identity security platforms continuously monitor user behavior, detecting and flagging anomalies that could indicate potential security issues. Security teams can then quickly investigate and respond to any suspicious activity, maintaining trust only where it is warranted.
Incident Response and Threat Containment Zero Trust requires organizations to be ready to respond immediately to any incident. Identity security solutions provide automated threat detection and response tools, which can contain threats by locking down accounts or enforcing additional security checks in real-time. This rapid response helps prevent a small issue from becoming a significant security breach.
Adaptability in Hybrid and Multi-Cloud Environments As companies increasingly operate in cloud-based and hybrid environments, security becomes more complex. A strong identity security platform supports Zero Trust across on-premises, cloud, and hybrid environments, helping companies maintain a consistent security posture and ensuring that Zero Trust principles apply across their entire digital landscape.
With cyber threats constantly evolving, businesses need a security framework that is both dynamic and resilient. Combining a Zero Trust model with a Cyberark Certification provides organizations with a powerful, proactive approach to security. This integration allows companies to strictly verify users, control access, and continuously monitor activities, all of which are essential for effective Zero Trust implementation.
For organizations committed to staying ahead of cyber threats, the pairing of identity security and Zero Trust offers an adaptable, modern solution that enhances security and builds trust with stakeholders.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
#cyberark certification#cyberark training#identityskills#cyberark online training#online cyberark training#cyberark course#cyberark training in noida#cyberark training in bangalore#cyberark training in india
0 notes
Text
Transforming into an AWS Solution Architect Expert with IdentitySkills CyberArk Training

An AWS Solution Architect is a cloud computing professional responsible for designing, architecting, and implementing cloud-based solutions on the Amazon Web Services (AWS) platform. They work closely with business stakeholders to understand their requirements and translate them into technical solutions that leverage the full potential of AWS services.
The Importance of CyberArk Training for AWS Solution Architects
While IdentitySkills is primarily known for its privileged access management solutions, its training programs can also be highly beneficial for AWS Solution Architects. Here's why:
Comprehensive Understanding of Security Best Practices: CyberArk training programs often incorporate a strong focus on security best practices. This knowledge is essential for AWS Solution Architects who are responsible for designing secure and compliant cloud architectures.
Deep Dive into Identity and Access Management (IAM): IAM is a fundamental component of AWS security. CyberArk Course can provide a deep dive into IAM concepts, helping AWS Solution Architects understand how to effectively manage user identities, permissions, and access controls in their AWS environments.
Hands-On Experience: Many programs include hands-on exercises and labs, allowing AWS Solution Architects to gain practical experience with IAM and other security-related tools and techniques.
Certification Preparation: It can also help prepare AWS Solution Architects for industry certifications, such as the AWS Certified Solutions Architect Associate or Professional.
Key Areas Covered in CyberArk Course for AWS Solution Architects
CyberArk training programs for AWS Solution Architects typically cover the following key areas:
IAM Fundamentals: Grasping the essential concepts of Identity and Access Management (IAM), which includes users, groups, roles, and policies.
IAM Best Practices: Understanding how to apply best practices for Identity and Access Management (IAM) to maintain secure and compliant AWS environments.
Single Sign-On (SSO): Integrating SSO solutions with AWS to provide a centralized authentication and authorization mechanism.
Multi-Factor Authentication (MFA): Implementing MFA to enhance the security of AWS accounts.
Access Control Lists (ACLs): Understanding how to use ACLs to control access to AWS resources.
Security Groups: Using security groups to control network traffic to and from AWS instances.
Benefits of CyberArk Online Training for AWS Solution Architects
By completing a cyberark training in noida, AWS Solution Architects can:
Enhance their security expertise: Gain a deeper understanding of security best practices and how to apply them to AWS environments.
Improve their ability to design secure architectures: Create cloud solutions that are resistant to security threats.
Demonstrate their security credentials: Obtain industry certifications to validate their skills and knowledge.
Increase their career opportunities: Position themselves as valuable assets in the competitive cloud computing market.
IdentitySkills cyberark training in bangalore can also provide significant benefits for AWS Solution Architects. By gaining a comprehensive understanding of security best practices and IAM concepts, AWS Solution Architects can design more secure and compliant cloud solutions, enhance their career prospects, and contribute to the success of their organizations.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in bangalore#online cyberark training#cyberark training in india#identityskills
0 notes
Text

Cyberark Certification - IdentitySkills
The CyberArk certification provides banking professionals with essential skills in access management, data security, and regulatory compliance. Tailored for the banking industry, this certification strengthens the protection of sensitive data and equips institutions to confidently address the growing challenges of cybersecurity.
For More Details Call us at: +91 6204012089 Email: [email protected] Visit Our Website: www.identityskills.com
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
Financial Cybersecurity: Key Features in CyberArk Certification for Banking

Managing sensitive financial information is becoming increasingly dependent on technology. This shift has increased the risk of cyberattacks, making strong cybersecurity measures a top priority for financial institutions. One of the most effective solutions for safeguarding banking operations is CyberArk, a leading platform that focuses on securing access to critical systems and information.
The CyberArk certification program allows banking professionals to enhance security and protect sensitive data. Our blog explores the key benefits of certification and why strengthening the banking industry requires it.
1. Controlling Access to Critical Systems
Banks manage vast amounts of sensitive financial information, making it essential to control who can access critical systems. These certificates helps banking professionals understand how to manage these access points effectively. By learning how to restrict and monitor access, they can reduce the risk of unauthorized users gaining entry to sensitive systems, ensuring data remains secure.
This level of control is vital for preventing both internal and external threats. Employees or hackers with access to key systems pose significant risks, and equips professionals to mitigate these threats through robust access control strategies.
2. Securing Credentials and Passwords
The management of credentials is a cornerstone of any security strategy, especially in the banking industry. This kind of training teaches professionals how to store and handle credentials securely. It ensures that passwords are regularly updated, strong enough to resist attacks, and never stored in unsecured locations.
This knowledge is particularly valuable in the financial industry, where weak or compromised passwords can lead to significant security breaches. With CyberArk's credential management tools, certified professionals can automate password rotation and enforce strict password policies, helping to safeguard sensitive banking information.
3. Monitoring User Activity
Keeping track of who is logging into sensitive systems and when is an essential aspect of banking cybersecurity. The Cyberark training provides tools that allow for real-time monitoring of user activity, offering visibility into what users are doing and whether their actions align with security policies.
Also trains banking professionals to configure and use these monitoring tools effectively, ensuring any suspicious activity is detected early. By recording user sessions, banks can also create a digital audit trail, making it easier to investigate any security incidents that occur.
4. Detecting and Responding to Threats
Banks are high-profile targets for cybercriminals, making it crucial to detect threats quickly and respond appropriately. As well as that, it is equipped with built-in tools to identify unusual behavior that may indicate a security breach. Whether it's an insider threat or an external hacker, these tools alert administrators to take immediate action.
Certified professionals are trained in threat detection and incident response, enabling banks to act swiftly when a threat is detected. This proactive approach can prevent small issues from escalating into significant breaches, protecting the bank's assets and reputation.
5. Ensuring Compliance with Regulations
Financial institutions operate under strict regulatory standards, including the Payment Card Industry Data Security Standard (PCI DSS) and various local and international banking laws. During this course, professionals learn how to adhere to these regulations while implementing security measures.
By aligning security strategies with regulatory requirements, banks can avoid fines, legal issues, and damage to their reputation. The tools also make it easier to maintain compliance by offering detailed reporting and auditing features that regulators often require.
6. Integrating with Existing Banking Infrastructure
Banks often use a mix of legacy systems and modern technologies, which can create challenges when implementing new cybersecurity solutions. CyberArk is designed to integrate seamlessly with various systems, whether they're on-premise, cloud-based, or hybrid.
The trained professionals learn how to incorporate the platform into a bank's existing infrastructure without causing disruptions. This allows banks to strengthen their cybersecurity posture without affecting day-to-day operations or requiring a complete overhaul of their IT systems.
7. Securing Remote Access
As remote work becomes more common in the banking industry, securing remote access to critical systems has become a top priority. Cyberark training in india provides secure solutions for managing remote access, ensuring that employees and third parties can connect to sensitive systems without compromising security.
Furthermore, it covers how to implement secure remote access protocols, protecting the bank from potential breaches that could occur when users access systems from outside the organization's network. The importance of this is heightened because remote access can be a vulnerability if not properly protected.
Conclusion
The certification offers a range of benefits for banking professionals looking to strengthen their institution’s cybersecurity framework. From securing access to critical systems and protecting credentials to detecting threats and ensuring regulatory compliance, they equips professionals with the tools and knowledge needed to protect sensitive financial data.
In a rapidly evolving digital landscape, where cyber threats continue to grow more sophisticated, having certified CyberArk experts on board is essential for any financial institution. By investing in these services, banks can enhance their security strategies, protect their assets, and ensure the trust of their customers remains intact.
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
Public Sector Security: The Role of CyberArk Online Training

Public sector institution security has become essential in an increasingly digital world. Government agencies manage a vast array of sensitive data, from personal information of citizens to critical national infrastructure. With the rise of cyber threats, protecting this information is not only crucial but imperative for maintaining public trust and ensuring the smooth functioning of essential services. IdentitySkills, a leading cyberark solution, plays a significant role in safeguarding public sector security.
Understanding Public Sector Security
Public sector security encompasses the strategies and measures used to protect government agencies and public services from cyber threats. This includes safeguarding the integrity of communication networks, protecting sensitive data, and ensuring that public services remain operational even in the face of cyber attacks. Unlike private sector security, public sector security deals with information and infrastructure that, if compromised, could have far-reaching implications, potentially impacting national security, economic stability, and public welfare.
Cyberark breaches in the public sector can lead to catastrophic consequences. For example, an attack on a healthcare system could disrupt medical services, or a breach in a government database could expose millions of citizens’ personal information. These risks make it essential for public sector organizations to implement robust cybersecurity measures.
The Public Sector's Increasing Need for Cybersecurity
The public sector has increasingly become a target for cybercriminals due to the valuable and sensitive nature of the information it holds. The urgency of strengthening cybersecurity measures has been brought to light by the increase in the frequency and sophistication of cyberattacks against government institutions in recent years.
Inadequate security in government agencies can have serious repercussions, such as interrupted services, monetary losses, and eroded public confidence. Furthermore, government agencies are often required to comply with stringent regulations and standards, which mandate the implementation of advanced security solutions. This makes the adoption of tools like CyberArk not just beneficial but necessary.
The Role of CyberArk in Public Sector Security
CyberArk's ability to safeguard sensitive accounts and systems is essential in improving the security of public sector organizations. For government agencies, which handle critical infrastructure and confidential data, the ability to control and monitor access is essential. Further, it provides the necessary tools to enforce strict access controls, monitor all activities, and respond rapidly to any security incidents.
For instance, consider a government agency responsible for managing national transportation systems. If a cybercriminal gains access to the systems controlling these networks, the consequences could be disastrous, leading to significant disruptions and safety risks. CyberArk helps prevent such scenarios by ensuring that only authorized personnel can access these systems, and any suspicious activity is detected and addressed immediately.
Why Online Training is Essential for CyberArk Users
While CyberArk is a powerful tool, its effectiveness depends on how well it is implemented and utilized by public sector employees. Continuous learning is critical in the field of cybersecurity, given the constantly evolving threat landscape. This is where Online Cyberark Training becomes invaluable, providing public sector employees with the knowledge and skills needed to effectively use CyberArk.
Also this training offers several benefits, particularly in the public sector, where resources are often limited, and schedules are tight. It allows employees to learn at their own pace, from anywhere, making it easier to fit training into busy workdays. Moreover, it helps bridge the skills gap by providing access to up-to-date information and practical, hands-on experience in using tools.
Features of CyberArk Online Training
The features of Cyberark online training are as follows: :
Comprehensive Coverage: Offers training for all user levels, from beginners to advanced users.
Varied Topics: Includes setup, configuration, management, and troubleshooting of CyberArk.
Interactive Learning: Features hands-on labs and real-world scenarios to enhance practical understanding.
Security Focus: Emphasizes security best practices, managing access controls, and threat detection.
Regulatory Compliance: Covers how to ensure compliance with relevant regulations.
Certification: Provides certifications upon completion, validating expertise in CyberArk.
Career Advancement: Certifications can enhance career prospects, especially within the public sector.
How CyberArk Training Enhances Public Sector Security
Effective cyberark training in noida ensures that employees are well-prepared to implement and manage security measures within their organizations. This results in improved incident response times, as trained employees can quickly identify and address potential security threats. Additionally, well-trained employees are more likely to adopt proactive security measures, reducing the chances of successful cyber attacks.
For example, a government IT specialist who has undergone CyberArk training will be better equipped to manage access controls, monitor for unusual activity, and respond to security incidents. This enhances the overall security posture of the organization, ensuring that critical services remain operational and secure.
Future Trends in Public Sector Security and CyberArk’s Role
Increasing Need for Security: The sector will require more advanced security solutions as cyber threats evolve.
Emerging Threats: New threats targeting critical infrastructure and utilizing technologies like artificial intelligence will demand sophisticated security measures.
CyberArk’s Role: It will continue to be essential in helping public sector organizations tackle these emerging challenges.
Promising Future of Cybersecurity Training: The future of training looks promising, with growing recognition of the need for continuous learning in the government sector.
Growing Demand for Training: As more organizations understand the importance of training, the demand for flexible and accessible options will increase.
Expansion of CyberArk Training: CyberArk is likely to expand its online training programs to include more advanced and specialized courses, keeping pace with the evolving threat landscape.
Conclusion
CyberArk is a vital tool in the arsenal of public sector organizations, helping them protect sensitive data and critical infrastructure from cyber threats. However, the effectiveness depends on how well it is implemented and used, which makes online training an essential component of public sector security. By investing in comprehensive training, public sector organizations can enhance their security posture, improve incident response, and ensure compliance with regulatory requirements. In an era where cyber threats are increasingly sophisticated, staying ahead of the curve with tools like CyberArk and continuous learning is not just an option—it’s a necessity.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
CyberArk Training: The Key to Business Protection in 2024

The demand for robust cybersecurity measures has reached unprecedented levels. As businesses increasingly rely on digital platforms and cloud-based services, the potential for cyber threats has escalated. In this context, CyberArk training has emerged as a crucial component in fortifying business protection. This article explores the significance of CyberArk training and how it can safeguard businesses in 2024.
The Rising Tide of Cyber Threats
With the advent of sophisticated cyber attacks, businesses face an unprecedented level of risk. They are not only becoming more frequent but also more complex. Hackers are continually developing new methods to infiltrate systems, steal sensitive information, and disrupt operations. The financial and reputational damage caused by these breaches can be devastating.
To counter these threats, businesses must adopt a proactive approach to cybersecurity. This involves not only implementing advanced security technologies but also ensuring that their teams are well-trained in using these tools effectively. It is a key element in this strategy.
The Importance of Training
While implementing solutions is essential, it is equally important to ensure that the personnel responsible for managing these systems are well-trained. It provides the necessary knowledge and skills to effectively utilize the platform’s features and capabilities. Here are some key reasons why this training is vital for business protection in 2024:
Enhanced Security Posture It helps in empowers IT professionals to configure and manage the platform efficiently. This ensures that privileged accounts are secured, monitored, and controlled, significantly reducing the risk of unauthorized access. A well-trained team can quickly identify and respond to potential threats, enhancing the overall security posture of the organization.
Compliance and Regulatory Requirements Numerous industries must adhere to strict regulations concerning data protection and cybersecurity. Further, helps businesses comply with these regulations by ensuring that their access management practices meet the required standards. This not only helps avoid legal penalties but also builds trust with clients and partners.
Operational Efficiency Proper training enables IT teams to utilize CyberArk’s features to their full potential. This includes automating routine tasks, streamlining workflows, and improving the overall efficiency of security operations. As a result, businesses can allocate their resources more effectively and focus on strategic initiatives.
Risk Mitigation It also provides IT professionals with the skills to identify and mitigate potential risks before they escalate into major security incidents. By understanding the intricacies of the platform, they can implement best practices and proactive measures to safeguard privileged accounts.
Adaptability to Emerging Threats The cybersecurity landscape is constantly evolving, with new threats emerging regularly. It ensures that IT teams stay updated with the latest developments and are prepared to tackle new challenges. This adaptability is crucial for maintaining a robust defense against cyber attacks.
Key Components of CyberArk Course
CyberArk offers a comprehensive training program that covers various aspects of management. The training is designed to cater to different roles within the organization, ensuring that all relevant personnel are equipped with the necessary skills. Some of the key components include:
Introduction to CyberArk This module provides an overview of CyberArk’s solutions and their importance in securing privileged accounts. It covers the basic concepts and architecture of the platform, helping participants understand its fundamental principles.
Installation and Configuration This section delves into the installation and configuration of CyberArk solutions. Participants learn how to set up the platform, configure security policies, and integrate it with existing IT infrastructure.
Incident Response and Recovery Includes guidance on responding to security incidents involving privileged accounts. Participants learn how to investigate breaches, mitigate their impact, and implement recovery measures.
Advanced Features and Automation For advanced users, CyberArk offers training on the platform’s more sophisticated features, such as automation and integration with other security tools. This enables businesses to streamline their security operations and enhance overall efficiency.
Implementing in Your Organization
To maximize the benefits, businesses should adopt a structured approach to its implementation. Here are some steps to consider:
Identify Training Needs Assess the current skill levels of your IT team and identify any gaps that need to be addressed. Determine which team members require training and at what level.
Choose the Right Training Program offers various training programs tailored to different roles and skill levels. Select the program that best suits the needs of your organization.
Schedule Regular Training Sessions As cybersecurity is a constantly evolving field, ongoing education is crucial. Schedule regular training sessions to keep your team updated with the latest developments and best practices.
Encourage Certification Encourage your team members to pursue CyberArk certification. This not only validates their skills but also demonstrates your organization’s commitment to cybersecurity.
Integrate Training with Security Policies Ensure that the knowledge gained from training is integrated into your organization’s security policies and procedures. This helps create a cohesive and effective security strategy.
Conclusion
In 2024, the necessity for robust cybersecurity measures is more urgent than ever. Cyberark training in bangalore plays a pivotal role in protecting businesses from the ever-evolving threat landscape. By equipping IT professionals with the necessary skills and knowledge, businesses can enhance their security posture, comply with regulatory requirements, and achieve operational efficiency. Investing is not just a strategic move; it is a crucial step in safeguarding the future of your business.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
#cyberark certification#identityskills#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
Enhancing Data Access Security with CyberArk Course

In today's digital landscape, data security is paramount. Organizations continually seek robust solutions to safeguard their sensitive information from cyber threats. IdentitySkills provides comprehensive tools and solutions designed to protect data by securing access. Leveraging effectively can significantly enhance an organization's data access security.
Cyberark Certification focuses on securing access to critical systems and data within an organization. With threats becoming more sophisticated, ensuring that sensitive information is accessed only by authorized users is crucial. Its solutions are designed to manage and monitor access, reducing the risk of unauthorized access and potential breaches.
The Importance of CyberArk Training
CyberArk training equips IT professionals with the necessary skills and knowledge to manage and utilize security solutions effectively. This training is essential for several reasons:
Comprehensive Understanding: Training provides a thorough understanding of architecture and functionalities. This includes learning how to configure and deploy solutions that align with an organization's security policies.
Real-World Application: Hands-on exercises and real-world scenarios ensure that participants can apply their knowledge practically. This practical experience is crucial for effectively managing and securing access in an operational environment.
Staying Updated with Best Practices: It is an ever-evolving field. They help professionals remain updated with the latest security trends, best practices, and regulatory requirements, ensuring the organization's security measures are current and influential.
Incident Response: The Cyberark Course includes strategies for responding to security incidents. Effectively and promptly responding to potential threats is crucial for minimizing damage and facilitating attack recovery.
Implementing CyberArk in Your Organization
Implementing CyberArk involves several key steps:
Assessment and Planning: Begin by assessing your organization's current security posture and identifying areas where access needs to be secured. Develop a comprehensive plan for deploying solutions tailored to your specific needs.
Deployment: Install and configure according to your organization's security policies. This includes setting up controls for access management and monitoring.
Integration: Integrate CyberArk with existing IT infrastructure, such as directories, ticketing systems, and security information and event management (SIEM) systems, to streamline operations and enhance security.
Training and Awareness: Ensure your IT team undergo training to manage and maintain the system effectively. Additionally, it promotes security awareness among all employees to foster a security culture.
Continuous Monitoring and Improvement: Regularly review and update security policies, monitor access activities, and make necessary adjustments to address emerging threats.
The Role of CyberArk in Enhancing Data Access Security
CyberArk is pivotal in strengthening data access security by:
Protecting Sensitive Information: Managing and monitoring access ensures that sensitive data is only accessible to authorized users, reducing the risk of data breaches.
Enforcing Security Policies: It also enables organizations to implement security policies consistently across all access points. This guarantees adherence to regulatory requirements and internal policies.
Improving Visibility: With detailed monitoring and reporting features, it provides visibility into access activities. This aids in the prompt identification and response to potential threats.
Reducing Risk: Securing access and implementing robust controls reduces the risk of unauthorized access and cyber-attacks.
Conclusion
In an era where data breaches and cyber attacks are increasingly sophisticated, securing access to sensitive information is crucial. This course provides a comprehensive suite of tools to protect data by managing and monitoring access. By training, IT professionals can enhance their skills, ensuring their organizations are well-protected against cyber threats. Investing in CyberArk strengthens data access security and fosters a proactive security culture within the organization. For those seeking to enhance their expertise in this area, CyberArk training in India offers a robust platform for developing advanced skills in securing data access.
For more information, contact us at:
Call: +916204012089/+916207605341
Email: [email protected]
Visit: www.identityskills.com
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
The Benefits of Online CyberArk Training for Network Security Professionals

There can be no overstatement of the importance of robust training programs in the ever-evolving field of cybersecurity. A leading provider of cyber security solutions, IdentitySkills, offers comprehensive online cyberark training courses for network security professionals. To effectively secure critical assets against cyber threats, professionals need the knowledge and skills provided by these courses.
A look at the CyberArk online training platform
Training platforms like these provide security professionals with a flexible and convenient way to enhance their skills without having to travel extensively or spend much time away from their offices. A range of courses covering various aspects of security is offered by them, such as:
Introduction to CyberArk: A foundational course that familiarizes participants with solutions and their importance in securing accounts.
Advanced Threat Protection: A specialized course that delves into advanced threat protection strategies and techniques using solutions.
Account Security: A comprehensive course that covers the principles and best practices of securing accounts.
Training with CyberArk online has many advantages
Convenience: Learners can take online courses at their own pace and on their own schedule, making it more convenient for them to balance work and training.
Cost-Effective: Online training eliminates the need for travel and accommodation, reducing overall training costs.
Access to Experts: Participants have access to CyberArk's team of experts, who provide guidance and support throughout the training process.
Interactive Learning: Various elements like quizzes and simulations are included in the online platform, which enhances the learning process.
Certification: Upon completion of a course, participants receive a certification from CyberArk, demonstrating their proficiency in privileged access security.
Aims of CyberArk's training program
Real-World Scenarios: CyberArk online training modules are designed to simulate real-world scenarios, allowing participants to apply their knowledge in practical situations.
Continuous Updates: The training content is regularly updated to reflect the latest cybersecurity trends and threats, ensuring that participants receive relevant and up-to-date information.
Community Support: Participants have access to a community forum where they can interact with peers and experts, fostering collaboration and knowledge sharing.
Conclusion
Online training, including CyberArk training in Bangalore, offers network security professionals a convenient and effective means to enhance their skills and knowledge in access security. By leveraging these training opportunities, professionals can fortify their ability to safeguard critical assets against cyber threats, thereby fostering a more secure digital landscape. The comprehensive approach to training, combined with a commitment to continuous improvement, renders it a valuable resource for network security professionals aiming to remain at the forefront of the rapidly evolving field of cybersecurity.
For more information, contact us at:
Call:+916204012089/+916207605341
Email:[email protected]
Visit:www.identityskills.com
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes
Text
CyberArk Training for Risk Management Professionals

In the modern digital landscape, cybersecurity is a critical component of risk management. For professionals tasked with safeguarding their organizations against cyber threats, understanding and managing privileged access is essential. CyberArk training provides the necessary skills and knowledge to enhance security posture, protect sensitive credentials, and effectively respond to incidents. This blog explores why this training is important and the certifications available to help you advance in your career.
What Makes the Training Important?
1. Enhanced Security Posture: CyberArk training equips risk management professionals with the tools and techniques to strengthen their organization’s security framework. By learning how to manage and monitor privileged access, professionals can proactively prevent unauthorized access and potential breaches. This proactive approach significantly improves the overall security posture, making the organization more resilient against cyber threats.
2. Protecting Sensitive Credentials: One of the primary focuses of CyberArk training is the protection of sensitive credentials. Privileged accounts, which often hold the keys to the kingdom, are prime targets for attackers. CyberArk course are designed to secure these accounts by managing, monitoring, and controlling access. Training ensures that professionals can implement and maintain these solutions effectively, thereby safeguarding critical assets and sensitive information.
3. Incident Response: In the event of a security breach, a swift and effective response is crucial. CyberArk training provides risk management professionals with the skills needed to quickly identify, isolate, and mitigate incidents involving privileged access. This capability not only minimizes potential damage but also aids in faster recovery, maintaining business continuity and protecting the organization’s reputation.
Certifications: Advancing Your Career
Achieving certification in CyberArk not only validates your expertise but also enhances your career prospects. CyberArk offers a structured certification path designed to equip professionals with the necessary skills to manage and secure privileged access.
1. Level 2 (DEFENDER) Exam: The DEFENDER certification focuses on the practical aspects of implementing and managing CyberArk solutions. It covers topics such as configuring the Digital Vault, managing privileged sessions, and implementing security policies. By clearing the Level 2 exam, professionals demonstrate their ability to defend their organization’s critical assets against unauthorized access.
2. Level 3 (SENTRY) Exam: The SENTRY certification is designed for advanced professionals who have a deep understanding of CyberArk’s solutions. This level focuses on complex configurations, troubleshooting, and advanced deployment scenarios. Achieving the SENTRY certification signifies a high level of expertise in managing and securing privileged accounts, positioning professionals as leaders in the field of risk management.
At our training center, we provide comprehensive courses and resources to help you clear both the DEFENDER and SENTRY exams. Our experienced instructors offer hands-on training, real-world scenarios, and personalized guidance to ensure your success.
Best Practices for Implementation
In order to implement effectively, best practices must be followed:
1. A Comprehensive Assessment
Identify your organization's current methods for managing access accounts and perform an assessment of them. Evaluate capabilities to fill these gaps.
2. Phased Implementation
Initiate the implementation process in phases. You should begin with the most critical systems and gradually expand to include all accounts as your organization grows.
3. User Training
Provide comprehensive training for all users, including administrators and end users, on how to effectively use the platform. By using this method, users are less likely to make mistakes and security is improved.
4. Regular Audits
Make sure security policies are followed and keep an eye out for potential security breaches by regularly auditing.
5. Integration with Existing Systems
Enhance threat detection and response capabilities by integrating CyberArk with existing security systems.
Those seeking to strengthen their organization's cybersecurity defenses must take Online Cyberark Training. Mastering this tool will allow professionals to manage and secure important accounts effectively, ensuring compliance with regulatory requirements and preventing cyber threats. To maximize benefits, continuous learning and adherence to best practices are essential.
For more information, contact us at:
Call:+916204012089/+916207605341
Email:[email protected]
Visit:www.identityskills.com
#identityskills#cyberark certification#cyberark training#cyberark online training#cyberark course#cyberark training in noida#online cyberark training#cyberark training in bangalore#cyberark training in india
0 notes