Text
6 Ways to Combat Social Phishing Attacks
Phishing is the number one method of attack delivery for everything from ransomware to credential theft. We are very aware of it coming by email, but other types of phishing have been growing rapidly.
In recent years, phishing over social media has skyrocketed by 500%. There has also been a 100% increase in fraudulent social media accounts.
Phishing over social media often tricks the victims because people tend to let their guard down when on social platforms like Facebook, Instagram, Twitter, and LinkedIn. They’re socializing and not looking for phishing scams.
However, phishing scammers are out there looking for you and will reach out via friend requests and direct messages. Learn several ways you can secure your social media use to avoid these types of covert attacks.
Make Your Profile Private on Social Platforms
Phishing scammers love public profiles on social media because not only can they gather intel on you to strike up a conversation, but they can also clone your profile and put up a fake page for phishing your connections.
Criminals do this in order to try to connect with those on your friends or connections list to send social phishing links that those targets will be more likely to click because they believe it’s from someone they know.
You can limit your risk by going into your profile and making it private to your connections only. This means that only someone that you’ve connected with can see your posts and images, not the general public.
For sites like LinkedIn where many people network for business, you might still want to keep your profile public, but you can follow the other tips below to reduce your risk.
Hide Your Contacts/Friends List
You can keep social phishing scammers from trying to use your social media profile to get to your connections by hiding your friends or connections list. Platforms like LinkedIn and Facebook both give you this privacy option.
Just be aware that this does not keep scammers from seeing you as a friend or connection on someone else’s profile unless they too have hidden their friends list.
Be Wary of Links Sent via Direct Message & in Posts
Links are the preferred way to deliver phishing attacks, especially over social media. Links in social posts are often shortened, making it difficult for someone to know where they are being directed until they get there. This makes it even more dangerous to click links you see on a social media platform.
A scammer might chat you up on LinkedIn to inquire about your business offerings and give you a link that they say is to their website. Unless you know the source to be legitimate, do not click links sent via direct message or in social media posts. They could be leading to a phishing site that does a drive-by download of malware onto your device.
Even if one of your connections shares a link, be sure to research where it is coming from. People often share posts in their own feeds because they like a meme or picture on the post, but they never take the time to check whether the source can be trusted.
Don’t Participate in Social Media Surveys or Quizzes
While it may be fun to know what Marvel superhero or Disney princess you are, stay away from quizzes on social media. They’re often designed as a ploy to gather data on you. Data that could be used for targeted phishing attacks or identity theft.
The Cambridge Analytica scandal that impacted the personal data of millions of Facebook users did not happen all that long ago. It was found that the company was using surveys and quizzes to collect information on users without their consent.
While this case was high-profile, they’re by no means the only ones that play loose and fast with user data and take advantage of social media to gather as much as they can.
It’s best to avoid any types of surveys or quizzes on any social media platform because once your personal data is out there, there is no getting it back.
Avoid Purchasing Directly from Ads on Facebook or Instagram
Many companies advertise on social media legitimately, but unfortunately, many scammers use the platforms as well for credit card fraud and identity theft.
If you see something that catches your eye in a Facebook or Instagram ad, go to the advertiser’s website directly to check it out, do not click through the social ad.
Research Before You Accept a Friend Request
It can be exciting to get a connection request on a social media platform. It could mean a new business connection or connecting with someone from your Alma mater. But this is another way that phishing scammers will look to take advantage of you. They’ll try to connect to you which can be a first step before reaching out direct via DM.
Do not connect with friend requests without first checking out the person on the site and online using a search engine. If you see that their timeline only has pictures of themself and no posts, that’s a big red flag that you should decline the request.
Can Your Devices Handle a Phishing Link or File?
It’s important to safeguard your devices with things like DNS filtering, managed antivirus, email filtering, and more. This will help protect you if you happen to click on a phishing link.
Find out how we can help!
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post 6 Ways to Combat Social Phishing Attacks first appeared on .
Originally published here: https://techismything.com/6-ways-to-combat-social-phishing-attacks/
0 notes
Text
4 Interesting Cloud Storage Trends to Watch for in 2022
One area of cloud computing that is used widely, but often isn’t as flashy as the software side is cloud storage. Storing files in the cloud to make them easily accessible and shareable from anywhere was one of the very first uses of the cloud that was adopted widely by many users.
As advances like automation and AI come to other types of cloud services, like team communications and business apps, cloud storage is not being left behind. The industry also continues to evolve to make storing data in the cloudless complex, more reliable, and better secured.
It’s estimated that in 2021, 50% of all company data was stored in the cloud. This is an increase of 15% from just five years earlier. With today’s hybrid teams that may be working from home and be hundreds or thousands of miles away from co-workers, it’s important to centrally locate files in cloud systems that can be accessed by everyone.
What can you expect to see in the cloud storage market this year? Here are some of the most interesting trends to keep an eye on.
1. Built-in Ransomware Defenses
Ransomware can impact data no matter where it is stored. Whether on a computer, server or in a cloud storage platform, this malware can encrypt the information and make it unreadable to the business that owns it.
In 2021, the average ransomware payment increased by 82% and ransomware incidents rose 64% during the first half of the year. A survey of CISOs found that over the last 18 months, 98% of organizations suffered a cloud data breach.
To combat ransomware, you’ll begin seeing cloud storage services offering ransomware recovery protection. This involves sophisticated systems that can help prevent files from being encrypted by code as well as those that take a copy of files and store it securely away, so files can be restored at the click of a button.
With ransomware showing no sign of stopping, this is a welcome addition in the cloud storage arena.
2. “The Edge” Becomes More Key in Cloud Storage
One of the new buzzwords of the last few years has been “Edge” or “Edge computing.” This means bringing data applications and storage resources geographically closer to the user that needs to connect to them.
As reliance on cloud storage and other cloud applications has increased, so has the need to improve response times from user to server. When data must travel across large distances, it becomes more difficult to quickly and economically deliver the best user experience. Thus, cloud service providers have been moving to an Edge computing model.
What this means for you is better reliability and faster response when accessing or searching on files because your provider is going to work to provide your service from one of the company’s cloud servers that is geographically closer to your location.
For companies with offices spread out around a country or throughout the world, this means that you’ll want to keep service location in mind when signing up for cloud storage and have a discussion with the provider about distance and how Edge computing factors in.
3. Expect More Help from AI and Machine Learning
AI and machine learning are making just about every area of technology smarter. Microsoft Word and text message apps now predict what you might type to help you fill in the blanks and type faster. Programs like Photoshop can crop around a person in an image in seconds using AI.
AI is also going to become more prevalent in cloud storage this year. You can expect help with automatic organization of your files based on your cloud storage patterns.
Look for features designed to eliminate manual or repetitive tasks to free up more time. This includes AI helping to automate things like provisioning, obtaining, and importing data (known as “ingesting”), managing data retention, and more.
4. Legacy Vendors Begin Offering More Cloud Options
2022 is going to bring more cloud storage options coming from legacy technology providers. For example, Hewlett-Packard Enterprise recently introduced a new Data Services Cloud Console, and Dell Technologies just announced a new APEX multi-cloud design that it is working on to improve the cloud ecosystem.
More cloud storage options mean you may need more help deciding which model will work best for you, as pricing will vary widely. You don’t want to end up with more storage than you need or be paying a lot for a smaller amount of space.
It pays to keep on top of new offerings and understand that every new cloud storage option might not be a fit for your organization’s specific data storage needs.
Get Help Optimizing Your Cloud Storage & Backup Environment
Your business data is what runs your company, and it needs to be stored securely and in a way that’s accessible. Find out how we can help you optimize your cloud storage to improve cost efficiency.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post 4 Interesting Cloud Storage Trends to Watch for in 2022 first appeared on .
Originally published here: https://techismything.com/4-interesting-cloud-storage-trends-to-watch-for-in-2022/
0 notes
Text
5 Things You Should Never Do on a Work Computer
Whether you work remotely or in an office, the line between personal and work tasks can become blurred when working on your company computer. If you’re in front of a computer for most of your time during work, then it’s not unusual to get attached to your desktop PC.
Over time, this can lead to doing personal things on a work computer. At first, it might just be checking personal email while on a lunch break. But as the line continues to get crossed, it can end up with someone using their work computer just as much for personal reasons as work tasks.
In a survey of over 900 employees, it was found that only 30% said they never used their work PC for personal activities. The other 70% admitted to using their work computer for various personal reasons.
Some of the non-work-related things that people do on a work computer include:
Reading and sending personal email
Scanning news headlines
Shopping online
Online banking
Checking social media
Streaming music
Streaming videos/movies
It’s a bad idea to mix work and personal, no matter how much more convenient it is to use your work PC for a personal task during the day. You can end up getting reprimanded, causing a data breach at your company, or possibly losing your job.
Here are several things you should never do on your work PC.
1. Save Your Personal Passwords in the Browser
Many people manage their passwords by allowing their browser to save and then auto-fill them. This can be convenient, but it’s not very secure should you lose access to that PC.
When the computer you use isn’t yours, it can be taken away at any time for a number of reasons, such as an upgrade, repair, or during an unexpected termination.
If someone else accesses that device and you never signed out of the browser, that means they can leverage your passwords to access your cloud accounts.
Not all older PCs are stored in a storeroom somewhere or destroyed. Some companies will donate them to worthy causes, which could leave your passwords in the hands of a stranger if the PC hasn’t been wiped properly.
2. Store Personal Data
It’s easy to get in the habit of storing personal data on your work computer, especially if your home PC doesn’t have a lot of storage space. But this is a bad habit and leaves you wide open to a couple of major problems:
Loss of your files: If you lose access to the PC for any reason, your files can be lost forever
Your personal files being company-accessible: Many companies have backups of employee devices to protect against data loss. So, those beach photos stored on your work PC that you’d rather not have anyone else see could be accessible company-wide because they’re captured in a backup process.
3. Visit Sketchy Websites
You should assume that any activity you are doing on a work device is being monitored and is accessible by your boss. Companies often have cybersecurity measures in place like DNS filtering that is designed to protect against phishing websites.
This same type of software can also send an alert should an employee be frequenting a sketchy website deemed dangerous to security (which many sketchy websites are).
You should never visit any website on your work computer that you wouldn’t be comfortable visiting with your boss looking over your shoulder.
4. Allow Friends or Family to Use It
When you work remotely and your work computer is a permanent fixture in your home, it can be tempting to allow a friend or family member to use it if asked. Often, work PCs are more powerful than a typical home computer and may even have company-supplied software that someone wouldn’t purchase on their own.
But allowing anyone else to use your work computer could constitute a compliance breach of data protection regulations that your company needs to adhere to.
Just the fact that the personal data of your customers or other employees could be accessed by someone not authorized to do so, can mean a stiff penalty.
Additionally, a child or friend not well-versed in cybersecurity could end up visiting a phishing site and infecting your work device, which in turn infects your company cloud storage, leaving you responsible for a breach.
At least 20% of companies have experienced a data breach during the pandemic due to a remote worker.
5. Turn off Company-Installed Apps like Backups and Antivirus
If you’re trying to get work done and a backup kicks in and slows your PC down to a crawl, it can be tempting to turn off the backup process. But this can leave the data on your computer unprotected and unrecoverable in the case of a hard drive crash or ransomware infection.
Company-installed apps are there for a reason and it’s usually for cybersecurity and business continuity. These should not be turned off unless given express permission by your supervisor or company’s IT team
How Secure Is the Device You Use to Work from Home?
Whether you’re working remotely and worried about causing a data breach or are a business owner with multiple remote team members to secure, device protection is important. Schedule a device security checkup today.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post 5 Things You Should Never Do on a Work Computer first appeared on .
Originally published here: https://techismything.com/5-things-you-should-never-do-on-a-work-computer/
0 notes
Text
Alarming Phishing Attack Trends to Beware of in 2022
In 2020, 75% of companies around the world experienced a phishing attack. Phishing remains one of the biggest dangers to your business’s health and wellbeing because it’s the main delivery method for all types of cyberattacks.
One phishing email can be responsible for a company succumbing to ransomware and having to face costly downtime. It can also lead a user to unknowingly hand over the credentials to a company email account that the hacker then uses to send targeted attacks to customers.
Phishing takes advantage of human error, and some phishing emails use sophisticated tactics to fool the recipient into divulging information or infecting a network with malware.
Mobile phishing threats skyrocketed by 161% in 2021.
Your best safeguards against the continuous onslaught of phishing include:
Email filtering
DNS filtering
Next-gen antivirus/anti-malware
Ongoing employee cybersecurity awareness training
To properly train your employees and ensure your IT security is being upgraded to meet the newest threats you need to know what new phishing dangers are headed your way.
Here are some of the latest phishing trends that you need to watch out for in 2022.
Phishing Is Increasingly Being Sent via Text Message
Fewer people are suspicious of text messages than they are of unexpected email messages. Most phishing training is usually focused on the email form of phishing because it’s always been the most prevalent.
But cybercrime entities are now taking advantage of the easy availability of mobile phone numbers and using text messaging to deploy phishing attacks. This type of phishing (called “smishing”) is growing in volume.
People are receiving more text messages now than they did in the past, due in large part to retailers and service businesses pushing their text updates for sales and delivery notices.
This makes it even easier for phishing via SMS to fake being a shipment notice and get a user to click on a shortened URL.
Business Email Compromise Is on the Rise
Ransomware has been a growing threat over the last few years largely because it’s been a big money-maker for the criminal groups that launch cyberattacks. A new up-and-coming form of attack is beginning to be quite lucrative and thus is also growing.
Business email compromise (BEC) is on the rise and being exploited by attackers to make money off things like gift card scams and fake wire transfer requests.
What makes BEC so dangerous (and lucrative) is that when a criminal gains access to a business email account, they can send very convincing phishing messages to employees, customers, and vendors of that company. The recipients will immediately trust the familiar email address, making these emails potent weapons for cybercriminals.
Small Businesses Are Being Targeted More Frequently With Spear Phishing
There is no such thing as being too small to be attacked by a hacker. Small businesses are targeted frequently in cyberattacks because they tend to have less IT security than larger companies.
43% of all data breaches target small and mid-sized companies, and 40% of small businesses that become victims of an attack experience at least eight hours of downtime as a result.
Spear phishing is a more dangerous form of phishing because it’s targeted and not generic. It’s the type deployed in an attack using BEC.
It used to be that spear-phishing was used for larger companies because it takes more time to set up a targeted and tailored attack. However, as large criminal groups and state-sponsored hackers make their attacks more efficient, they’re able to more easily target anyone.
A result is small businesses receiving more tailored phishing attacks that are harder for their users to identify as a scam.
The Use of Initial Access Brokers to Make Attacks More Effective
We just discussed the fact that large criminal groups are continually optimizing their attacks to make them more effective. They treat cyberattacks like a business and work to make them more profitable all the time.
One way they are doing this is by using outside specialists called Initial Access Brokers. This is a specific type of hacker that only focuses on getting the initial breach into a network or company account.
The increasing use of these experts in their field makes phishing attacks even more dangerous and difficult for users to detect.
Business Impersonation Is Being Used More Often
As users have gotten savvier about being careful of emails from unknown senders, phishing attackers have increasingly used business impersonation. This is where a phishing email will come in looking like a legitimate email from a company that the user may know or even do business with.
Amazon is a common target of business impersonation, but it also happens with smaller companies as well. For example, there have been instances where website hosting companies have had client lists breached and those companies sent emails impersonating the hosting company and asking the users to log in to an account to fix an urgent problem.
More business impersonation being used in phishing attacks mean users have to be suspicious of all emails, not just those from unknown senders.
Is Your Company Adequately Protected from Phishing Attacks?
It’s important to use a multi-layered strategy when it comes to defending against one of the biggest dangers to your business’s wellbeing. Get started with a cybersecurity audit to review your current security posture and identify ways to improve.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post Alarming Phishing Attack Trends to Beware of in 2022 first appeared on .
Originally published here: https://techismything.com/alarming-phishing-attack-trends-to-beware-of-in-2022/
0 notes
Text
Important Steps to Take Before You Recycle a Mobile Phone Number
It’s not unusual to change a mobile number from time to time. For example, when you move, you may want a number that is local to the area you just moved to. Companies also may end up recycling mobile numbers throughout their staff as people come and go.
If you don’t properly detach your mobile phone number from all the accounts it’s used with, you can leave yourself open to identity theft, credit card fraud, and other crimes.
In a 2021 Princeton University study, it was found that 66% of mobile numbers listed as available by major mobile service providers were still connected to accounts on popular sites (Amazon, PayPal, etc.).
So, after the former owners had turned in the number, it was available for someone else to use when signing up for mobile service. And that number was still being used on the former owner’s cloud accounts, allowing those accounts to easily be breached.
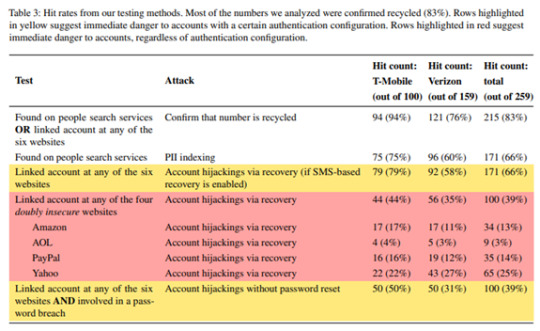
Princeton University study on the risk of recycling mobile numbers.
Because our mobile numbers are connected to much of our online and offline life, it’s important to take certain steps to ensure that you don’t leave yourself at risk when recycling your phone number.
Change Your Phone Number for Online Accounts
We all generally have more online accounts than we immediately remember. The average person must juggle 100 passwords, and most of those passwords will be to a website or cloud app service of some kind.
The first thing you want to do is begin visiting your online accounts and cloud applications to update your mobile phone number. Many of these apps now use a text message to your number as a form of verification if you’ve lost your password.
You want to ensure any password reset messages go to you and not someone that has requested your old number for the express purpose of identity theft or account compromise.
Change Your Number for Social Media Accounts
Technically, a social media account is also an online account, but many people think of them as a separate entity. When a Facebook or LinkedIn account is compromised, the hacker often will send social phishing messages out to your friend connections to try to gain access to sensitive data or scam them out of money.
Make sure to change the phone number listed in your social media accounts. If you are using WhatsApp, which is tied directly to your mobile number, make sure to follow their instructions on changing your number so your communications will remain secure.
Change Your Phone Number for Service Providers That Send You Texts
Text messaging is beginning to replace email for many types of communications. This includes things like shipping notices, confirmations of payments from utility companies, appointment reminders, and sale notices from retailers.
This puts you more at risk if you change your mobile number because the texts you receive from various service providers can be used for identity theft.
Make sure to connect with any services you use that contact you by calling or texting your mobile number to update your information. These offline services could be a:
Plumbing or HVAC company
Dentist or doctor’s office
Pharmacy
Local retailer
Utility company
Double Check All Your Multi-Factor Authentication Prompts
One of the big dangers of having a stranger able to receive your text messages is that they could have access to your codes for multi-factor authentication (MFA).
MFA is designed as a safeguard to help prevent an account breach, even if the perpetrator has your username and password. But if the criminal gets the MFA codes sent to your old number, they can easily get in and change your password, locking you out of your own account.
As you go through the process to update your mobile number in your online accounts, double-check the MFA prompt for any that use this form of authentication security. You want to make sure it’s been properly changed to send a message to your new number.
Review Your Text Message History for Anything You’ve Missed
Inevitably, there will be online accounts or service providers that you’ve missed. For example, that place you always order flowers for on a loved one’s birthday every year but never visit at other times.
Scroll through your text message history to find any other accounts that you may have forgotten to update.
Text Friends, Family & Colleagues from the New Number
Once your online security is taken care of, you want to stop friends, family, and colleagues from accidentally texting your old number. This can happen in both one-on-one and group SMS chats.
Send a text message from your new number asking them to immediately update your contact with that number when they receive it. Then go the additional step by asking them to delete any messages that used your old phone number. This can help prevent them from accidentally grabbing that message instead of your new one when texting you in the future.
How Secure Is Your Mobile Device?
Mobile devices are increasingly being attacked by malware and phishing. Is your device properly secured? Don’t leave yourself at risk, request a mobile security check to protect your personal data and identity.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post Important Steps to Take Before You Recycle a Mobile Phone Number first appeared on .
Originally published here: https://techismything.com/important-steps-to-take-before-you-recycle-a-mobile-phone-number/
0 notes
Text
These Google Search Tips Will Save You Tons of Time!
Over 2.4 million searches happen every minute on Google. It’s often the first stop people make when they go online.
We search daily for both personal and work needs, and often searching out the right information can take a lot of time if you have to sift through several irrelevant results.
One study by consulting firm, McKinsey, found that employees spend an average of 1.8 hours daily, or 9.3 hours each week, searching and gathering information. This can be a productivity sinkhole as more web results keep getting added to the internet every day.
One way you can save time on your personal and work-related searches is to learn some “secret” Google search tips. These help you narrow down your search results and improve productivity by helping you find the information you need faster.
Search a Specific Website Using “site:”
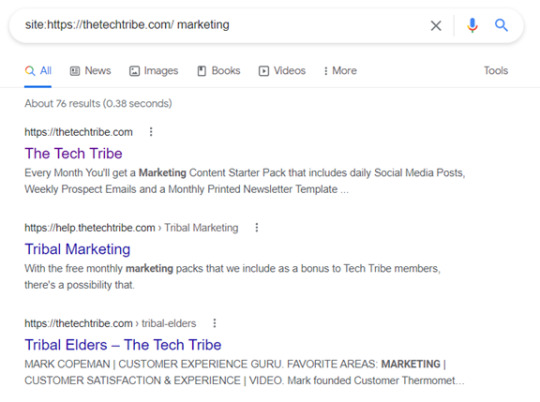
Image Credit
Sometimes you need to find information on a specific website. For example, you might need to locate a government statistic that you know is out there but can’t seem to bring up on a general search.
You can use Google to search keywords on a specific website by using the “site” function.
In the search bar use the following: site:(site url) (keyword)
This will bring up search results only for that one specific URL.
Find Flight Information Without Leaving Google
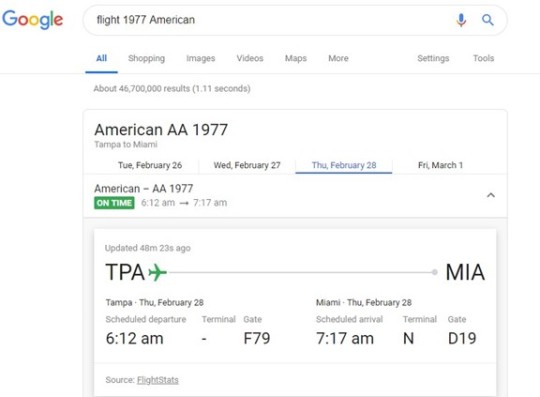
Image Credit
When you need to access flight information, you’re often on the go. Either getting ready to head to the airport or waiting for someone to arrive. Having to load multiple site pages in your browser can take valuable time. Instead, get your flight results directly from Google.
Just type in the flight number and the name of the airlines, and you’ll get a listing of flight information without having to click to another page. You can even tab to choose flight info for that same flight on different days.
Look for Document Types Using “filetype:”
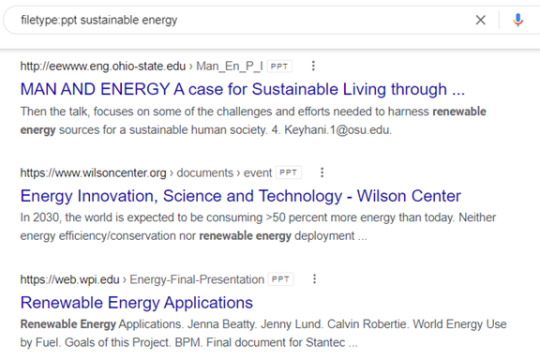
Image Credit
If you’ve just been tasked with coming up with a presentation on sustainable energy, it can be helpful to see what other people have done on the same subject.
Searching websites can give you a lot of details to sift through but searching for another PowerPoint presentation can provide you with even more insight into how others have distilled that information down into a presentation.
Google has a search function that allows you to search on a file type, so instead of webpages showing up in your results, files of the file type you searched will appear.
To use this function, type in the following: filetype:(type) (keyword)
In the case of wanting to find a PowerPoint on sustainable energy, you could use the following in the search bar: filetype:ppt sustainable energy.
All the results will be PPT presentations.
You can also use this function for other file types, such as:
DOC
PDF
XLS or XLSX
SVG
and more
Narrow Down Timeframe Using the “Tools” Link
One frustration is when you’re looking up something like a population or cybersecurity statistic and you end up with results that are too old to be relevant. You can spend valuable time paging through the search results, or you can tell Google what time frame you’d like to search.
To narrow your search results by a specific timeframe, do the following:
Enter your keyword and click to search.
Under the search bar, click the “Tools” link.
Click the “Any time” link.
Choose your timeframe.
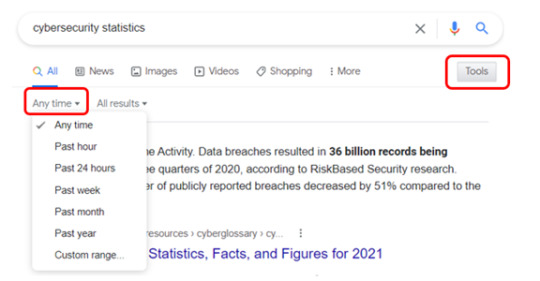
Image Credit
You can choose from preset timeframes, like past hour or past year, or you can set a custom date range for your results.
Locate Similar Sites Using “related:”
When you’re researching a topic online, it’s often helpful to find similar websites to the one you are viewing. Seeing related sites can also be used if you’re trying to find a specific product or service online and want to do some comparison shopping.
Google can provide you with a list of related websites when you use the “related” function.
In your search bar, type the following: related:https://website.com
One more way that you can leverage this search tip is to look for competitors by entering your own website URL in the search.
Get Rid of Results You Don’t Want Using “-(keyword)”
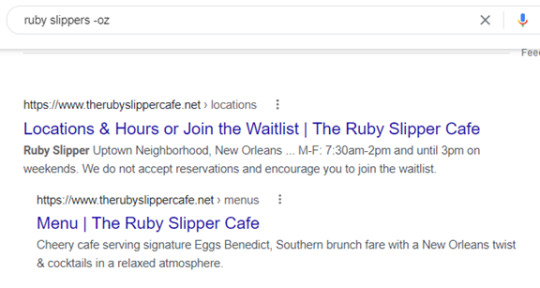
Image Credit
Non-relevant results are one of the main timewasters of online searching. You have to page through results that have nothing to do with what you really want to find, just because they use a related keyword.
For example, say you were searching the Ruby Slipper Cafe in New Orleans. But in your search results, you keep getting pages related to the movie the Wizard of Oz. You could eliminate those irrelevant results by using the negative keyword function.
Just type: (keyword) -(keyword)
Basically, you are just putting a minus sign in front of a keyword that you want to exclude from your search. In the example above, you would type: ruby slippers -oz.
Looking for More Ways to Boost Productivity & Save Time?
IT consultants aren’t just for large projects, we can also help you boost productivity in your everyday workflow to make your life easier.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post These Google Search Tips Will Save You Tons of Time! first appeared on .
Originally published here: https://techismything.com/these-google-search-tips-will-save-you-tons-of-time/
0 notes
Text
Top 5 Cybersecurity Mistakes That Leave Your Data at Risk
The global damage of cybercrime has risen to an average of $11 million USD per minute, which is a cost of $190,000 each second.
60% of small and mid-sized companies that have a data breach end up closing their doors within six months because they can’t afford the costs. The costs of falling victim to a cyberattack can include loss of business, downtime/productivity losses, reparation costs for customers that have had data stolen, and more.
You may think that this means investing more in cybersecurity, and it is true that you need to have appropriate IT security safeguards in place (anti-malware, firewall, etc.). However, many of the most damaging breaches are due to common cybersecurity mistakes that companies and their employees make.
The 2021 Sophos Threat Report, which looked at thousands of global data breaches, found that what it termed “everyday threats” were some of the most dangerous. The report stated, “A lack of attention to one or more aspects of basic security hygiene has been found to be at the root cause of many of the most damaging attacks we’ve investigated.”
Is your company making a dangerous cybersecurity mistake that is leaving you at high risk for a data breach, cloud account takeover, or ransomware infection?
Here are several of the most common missteps when it comes to basic IT security best practices.
Not Implementing Muti-Factor Authentication (MFA)
Credential theft has become the top cause of data breaches around the world, according to IBM Security. With most company processes and data now being cloud-based, login credentials hold the key to multiple types of attacks on company networks.
Not protecting your user logins with multi-factor authentication is a common mistake and one that leaves companies at a much higher risk of falling victim to a breach.
MFA reduces fraudulent sign-in attempts by a staggering 99.9%.
Ignoring the Use of Shadow IT
Shadow IT is the use of cloud applications by employees for business data that haven’t been approved and may not even be known about by a company.
Shadow IT use leaves companies at risk for several reasons:
Data may be used in a non-secure application
Data isn’t included in company backup strategies
If the employee leaves, the data could be lost
The app being used might not meet company compliance requirements
Employees often begin using apps on their own because they’re trying to fill a gap in their workflow and are unaware of the risks involved with using an app that hasn’t been vetted by their company’s IT team.
It’s important to have cloud use policies in place that spell out for employees the applications that can and cannot be used for work.
Thinking You’re Fine With Only an Antivirus Application
No matter how small your business is, a simple antivirus application is not enough to keep you protected. In fact, many of today’s threats don’t use a malicious file at all.
Phishing emails will contain commands sent to legitimate PC systems that aren’t flagged as a virus or malware. Phishing also overwhelmingly uses links these days rather than file attachments to send users to malicious sites. Those links won’t get caught by simple antivirus solutions.
You need to have a multi-layered strategy in place that includes things like:
Next-gen anti-malware (uses AI and machine learning)
Next-gen firewall
Email filtering
DNS filtering
Automated application and cloud security policies
Cloud access monitoring
Not Having Device Management In Place
A majority of companies around the world have had employees working remotely from home since the pandemic, and they’re planning to keep it that way. However, device management for those remote employee devices as well as smartphones used for business hasn’t always been put in place.
If you’re not managing security or data access for all the endpoints (company and employee-owned) in your business, you’re at a higher risk of a data breach.
If you don’t have one already, it’s time to put a device management application in place, like Intune in Microsoft 365.
Not Providing Adequate Training to Employees
An astonishing 95% of cybersecurity breaches are caused by human error. Too many companies don’t take the time to continually train their employees, and thus users haven’t developed the skills needed for a culture of good cybersecurity.
Employee IT security awareness training should be done throughout the year, not just annually or during an onboarding process. The more you keep IT security front and center, the better equipped your team will be to identify phishing attacks and follow proper data handling procedures.
Some ways to infuse cybersecurity training into your company culture include:
Short training videos
IT security posters
Webinars
Team training sessions
Cybersecurity tips in company newsletters
When Did You Last Have a Cybersecurity Checkup?
Don’t stay in the dark about your IT security vulnerabilities. Schedule a cybersecurity audit to uncover vulnerabilities so they can be fortified to reduce your risk.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
The post Top 5 Cybersecurity Mistakes That Leave Your Data at Risk first appeared on .
Originally published here: https://techismything.com/top-5-cybersecurity-mistakes-that-leave-your-data-at-risk/
0 notes
Text
Computer Network Security Info Tech Services Group
What Is Computer Network Security?
Computer network security is comprised of the policies, processes, and practices that are used to prevent, detect, and monitor unauthorized access, misuse, modification or denial of computer networks and other network-accessible resources. Network security is also known as Cybersecurity. For businesses, a network administrator controls network security and one aspect of network security is the authorization of data access. The network administrator can assign users an ID and password, or any other authentication information that will allow them to access information and programs.
Types Of Network Security
Computer network security (Cybersecurity) also refers to a range of public and private computer networks that are used for everyday tasks such as transactions and communication between individuals, businesses, and government agencies. Private networks can exist within a company or other networks that are open to the public. Organizations, enterprises, as well as other institutions, all have to be concerned with network security. A proper computer network security system protects the computer network and also oversees operations. One method for protecting network resources is implemented by giving the resource unique name and a password.
What Are The Basic Steps For Computer Network Security
Network security begins with authentication. Typically, this involves a username and password. One-factor authentication is often used because it only requires one element to authenticate the user name, i.e. the password. Two-factor authentication allows the user to use something they ‘have’ (e.g. a security token, a ‘dongle’ or an ATM card or a mobile device); while three-factor authentication allows the user to use something they ‘are’ (e.g. a fingerprint scan or retinal scan).
After authentication, firewalls enforce access policies that limit the number of services that can be accessed by network users. Although the firewall is effective in preventing unauthorized access, it may not be able to detect potentially dangerous content like computer worms and Trojans being transmitted over a network. An intrusion prevention system (IPS), or anti-virus software, can detect and block the actions of malware.
A network intrusion detection system that is anomaly-based may also monitor traffic. This data may be logged for audit purposes or for high-level analysis later. Modern systems that combine unsupervised machine learning and full network traffic analysis to detect active network attackers can be used to identify malicious insiders and external attackers who have compromised user accounts or machines. To protect privacy and security, communication between hosts that use a network can be encrypted.
What Is A Honeypot?
Honeypots are decoy network-accessible resources that can be used to monitor and warn of potential threats. They cannot normally be accessed for legitimate purposes. The honeypots are placed in a network at a vulnerable point, yet they can be isolated and monitored.
Attackers who attempt to compromise these decoy resource are examined during and after the attack in order to monitor new exploit techniques. This analysis can be used to strengthen the security of the honeypot’s network. An attacker can be directed away from legitimate servers by a honeypot. Honeypots encourage attackers to focus their energy and time on the honeypot, while diverting their attention from the data on a real server.
What Are The Two Main Types Of Network Attacks?
Malicious sources can attack networks. Two types of attacks can occur: Passive when an attacker intercepts data flowing through the network; and active when an intruder initiates commands that disrupt the normal operation of the network or conduct reconnaissance and other lateral movements in order to gain access to network assets.
What Is A Computer Virus?
A computer virus is a computer program that replicates itself through modification of other programs and inserting its code. The computer virus is a metaphor that comes from biological viruses.
A host program is usually required to combat computer viruses. The virus inserts its code into the host software. The virus code is executed first when the program runs. This causes infection and damages. Because it is an independent program, or code chunk, a computer worm doesn’t need a host. It is therefore not limited by the host program and can operate independently to carry out attacks.
To infect the system and spread the virus, virus writers employ social engineering techniques and exploit security vulnerabilities. The vast majority of viruses target systems running Microsoft Windows, employing a variety of mechanisms to infect new hosts, and often using complex anti-detection/stealth strategies to evade antivirus software.
There are many reasons to create viruses. These include the desire to make money (e.g. with ransomware), to send a political message or to have fun. They may also want to show that software has vulnerabilities. Each year, computer viruses cause economic damage worth billions of dollars.
Computer viruses can infect many subsystems of host computers as well as software. You can classify viruses by analyzing whether they are in binary executables, such as .EXE and .COM files, data files (such Microsoft Word documents or pdf files), or the boot sector on the host’s hard disk (or a combination of both).
When executed, a memory-resident virus (or “resident virus”) is installed as part of the operating systems. It remains in RAM until the computer is turned off. Resident viruses can overwrite interrupt handling codes or other functions. When the operating system attempts access to the target file, or disk sector, the virus code intercepts the request and redirects it to the replication module.
The replication module results in an “infection” on the target. A non-memory resident virus, or “nonresident virus”, on the other hand, scans the target’s disk and infects them before exiting (i.e. It does not stay in memory after the execution.
Common applications like Microsoft Word and Microsoft Outlook allow macro programs to embed in emails or documents so that they can be automatically run when the document opens. A macro virus, also known as “document virus”, is a virus written in a macro language that is embedded in documents. The virus code executes when the file is opened and can infect users’ computers.
Dangerous Email Attachments
It is dangerous to open suspicious or unexpected attachments in e mails. Although it is a good idea to not open attachments in e mails from unknown people or organizations, there are times when the virus appears to have been sent by a trusted organization (e.g. major banks or credit card companies).
Boot sector viruses target the boot sector, and/or Master Boot Record (MBR) of the host’s hard drive, solid-state drive or removable storage media (flash disks, floppy disks etc.).
Can A Computer Virus Be Transmitted Via Flash Drive?
Yes. Physical media is the most common method of transmitting computer viruses to boot sector. The infected USB flash drive or floppy drive will transmit data to the computer and modify or replace the boot code. When a user attempts to restart the desktop, the virus loads and runs as part of the master Boot Record.
What Are Email Viruses?
Email viruses are viruses that use the email system to spread their virus. Although virus-infected files can be sent to email as attachments, email viruses know how the email system works. They usually target a particular type of email system (Microsoft Outlook being the most popular), and can harvest email addresses from multiple sources.
How Can I Prevent Computer Network Viruses?
If you are a business owner, organization or business department manager, the best method for removing and preventing harmful computer viruses is to hire a professional Cybersecurity company, like InfoTech Services Group Inc. We have 30+ years of experience, skills, and the right software to prevent damage to your computer system. Call us at (877)724-8781 so we can get started as your Computer Network Security company.
More References Sources
You can find out more about Network Security and Computer Viruses at the InfoTech Services Cybersecurity and Network Security page.
InfoTech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
(877)724-8781
The post Computer Network Security Info Tech Services Group first appeared on .
Originally published here: https://techismything.com/computer-network-security/?utm_source=rss&utm_medium=rss&utm_campaign=computer-network-security
0 notes
Text
Cybersecurity Virus Removal & Prevention Los Angeles
What Is Cybersecurity?
Virus Removal And Prevention
Cybersecurity is the protection of networks and devices, data, as well as information, from criminal or unauthorized use. Cybersecurity also covers the protection of data and networks from criminal or unauthorized use. Computers and the Internet are now essential for businesses. Virus removal is just one of the activities of a Cybersecurity program. Communication (e.g. email, smartphones, tablets), entertainment, transportation (e.g. Navigation systems, shopping online (e.g. Credit cards, medicine, equipment and medical records are just some of the many examples. Los Angeles businesses need cybersecurity to protect their data and ensure security on computer networks.
Businesses, organizations, and government agencies all use computers to store information. This means that your computer network contains data about humans that is stored on your computers and it is your responsibility to protect this data. When you have questions about your Cybersecurity, call InfoTech Services Group Inc. at 1(877)724-8781. We can test your computer network system, analyze the data, recommend a Cybersecurity services Los Angeles CA program to protect your valuable data.
Computers are used to store information by businesses, government agencies, and organizations. Your computer network may contain data about people. It is your responsibility for protecting this data. InfoTech Services Group Inc. can help you with Cybersecurity and computer virus removal. Call us with your questions at 1-877-724-8781. We can analyze your network and recommend a Cybersecurity program to protect your data. InfoTech Services Group specializes in cybersecurity services including computer virus removal for all businesses, organizations, or government agencies in Venice Los Angeles and Los Angeles County.
More About Cybersecurity in This Video
youtube
What Is A Computer Virus?
Computer viruses are a type malware that attaches itself to another program (like a file), and can spread once it is installed on a computer. You might receive an email with malicious attachments, then open the file without knowing it, and the virus will run on your computer. Viruses can cause data loss, slow down systems resources, and log keystrokes.
How can I stop computer viruses?
Computer viruses can be stopped by investing in cybersecurity software. InfoTech Services Group conducts research and analyses on anti-virus software. We are experts in identifying the best cybersecurity software and installing it. Our management team can stop viruses from infecting your computer network.
Computer viruses behave somewhat like viruses that infect humans. These are three main facts about Computer virus.
A host program is required for a computer virus.
Some type of action, like opening a file, will cause the computer virus to spread.
Computer viruses attach bits of their malicious code to files, or replace files with duplicates of themselves.
virus removal software maintenance Los Angeles CA, virus prevention services Los Angeles CA, virus prevention software install Los Angeles CA, virus prevention software service Los Angeles CA, virus prevention software support Los Angeles CA, virus prevention software maintenance Los Angeles CA, virus prevention software management Los Angeles CA, virus prevention software maintenance Los Angeles CA, virus protection services Los Angeles CA, virus protection software install Los Angeles CA, virus protection software installation Los Angeles CA, virus prevention software installation Los Angeles CA, virus protection software service Los Angeles CA, virus protection software support Los Angeles CA, cybersecurity InfoTech Services Group Inc, computer security InfoTech Services Group Inc, cybersecurity Los Angeles InfoTech Services Group Inc, Los Angeles cybersecurity InfoTech Services Group Inc, virus removal services Los Angeles CA, virus removal software management Los Angeles CA, virus protection software maintenance Los Angeles CA, virus protection software management Los Angeles CA, virus protection software maintenance Los Angeles CA, virus removal software install Los Angeles CA, virus removal software installation Los Angeles CA, virus removal software service Los Angeles CA, virus removal software support Los Angeles CA, virus removal software maintenance Los Angeles CA
InfoTech Services Group Inc.
36 Sunset Avenue
Venice, CA 90292
1(877)724-8781
The post Cybersecurity Virus Removal & Prevention Los Angeles first appeared on .
Originally published here: https://techismything.com/cybersecurity-virus-removal/?utm_source=rss&utm_medium=rss&utm_campaign=cybersecurity-virus-removal
0 notes
Text
Information About InfoTech Services Group Inc.
InfoTech Services Group Inc Brand Information
InfoTech Services Group Inc Located In Venice Los Angeles CA
Brand Information
InfoTech Services Group Inc. specializes in Information Technology, computer services, and consulting for individuals, businesses, schools, as well as government agencies. We are a team of computer consultants specializing in helping companies develop their IT infrastructure. Our services include E-mail Spam Management, Paperless Office, Remote Access, and Anti-Virus/Worm/Spyware software solutions.
What Services Does InfoTech Services Group Inc. Offer?
InfoTech Services Group Inc. offers many services to clients who require professional computer networking services. InfoTech can help you solve your computer networking issues. Our services include E-mail Spam Management and Remote Access. We also offer Cybersecurity Anti-Virus, Worm, and Spyware software. We offer services like a 24-Hour response guarantee, Microsoft Exchange Server implementation and Computer Hardware and Internet Security needs assessment. SQL Server & SQL Database Integration, Windows 10, Windows 11 Windows Server installation and configuration, as well as Offsite backups.
We also offer a variety of support services, including developing or updating systems; training staff on how to use these programs best; and providing individual attention when necessary. All with one goal: to make operations run smoothly so each employee can have what he/she needs whenever they need it.
InfoTech Services Group Inc. is the right company to call if you need IT-related assistance. InfoTech Services provides reliable and affordable support that is tailored to your company’s needs, eliminating any single point of failure. We have a team of experts that includes cloud architects, CIOs and tier 1 specialists to help you immediately. Our responsive and proactive IT support team can provide unlimited IT support for businesses in the Los Angeles region. No matter how or when you contact us, we are always available to help. Info Tech Services Group can help you with Information Technology services. Call us at 1 (877) 724-881.
What Cities Do You Serve?
We provide services to Venice CA, Los Angeles CA, and all cities in Los Angeles County, Orange County and Ventura County.
Here are Maps to give an indication of our Information Technology services area.
More About InfoTech Services Group Inc.
More information at IT Services From InfoTech Services Group Inc.
Info Tech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
1-877-724-8781
The post Information About InfoTech Services Group Inc. first appeared on .
Originally published here: https://techismything.com/information-about-infotech-services-group-inc/?utm_source=rss&utm_medium=rss&utm_campaign=information-about-infotech-services-group-inc
0 notes
Text
VMware Issues Warning For vSphere 7 Update
VMware Pulls vSphere 7.0 Update 3
Avoid Installing The vSphere 7.0 Update
VMware has discovered multiple issues with vSphere ESXi 7.0 Update 3, 3a, and 3b and vCenter 7.0 Update 3b. These versions are no longer available for download. If you downloaded any of these builds before VMWare pulled them, DO NOT install these updates.
InfoTech Services Group is an experienced VMware installationa and maintenance services company. Call (877)724-8781 information about our VMware services. See all our services on our hardware and software services web page.
The ESXi updates can cause the Purple Screen of Death (PSOD) and crash the host under certain circumstances. Here are links to known issues with these updates: https://kb.vmware.com/s/article/86287 and https://kb.vmware.com/s/article/86281. One client installed vSphere 7.0 Update 3, and it changed the iSCSI Qualified Name (IQN) on the host, which caused all of the shared SAN storage to go missing.
What Is VMware?
VMware, a vendor of cloud computing and virtualization software, is based in Palo Alto (California). VMware was founded in 1998 and is now a subsidiary Dell Technologies. VMware’s virtualization technology is based on its bare metal hypervisor ESX/ESXi in the x86 architecture. You can run bare-metal embedded hypervisors directly on your network server’s hardware, without the need for a primary operating systems. VMware server virtualization allows multiple virtual machines (VMs), to be run on the same physical machine by installing a hypervisor on that server.
Each VM can run its operating system independently, allowing multiple OSes on one physical server. All VMs sharing the same physical server share resources such as RAM and networking.
VMware products include virtualization and networking, security management tools, storage software, and software-defined data centers software. VMware vSphere allows you to manage large-scale virtualization infrastructures. VMware vSphere is also known as a cloud operating platform or a virtualized database platform. It allows IT departments to place workloads on the most efficient computer resource.
VMware has applications that can be used on desktops and servers. VMware’s desktop software can be used with Linux, Microsoft Windows, and Mac OS X. VMware Workstation, VMware Fusion, and VMware Player are some of the desktop products. VMware’s server software range includes VMware ESX Server, and VMware Server.
Benefits Of VMware For Your Business
As the name suggests, VMware (or Virtual Machine ware) creates a virtual machine on your computer network system. This allows businesses to better manage their resources and increase efficiency. Virtualization on a business server offers many benefits, including lower IT costs. Businesses can also make the most of their hardware and resource investments by virtualizing.
Virtualization allows them to use different constraints, scheduling and partitioning options to improve the computing environment’s flexibility. VMware allows companies to run multiple operating system and application workloads on one server, allowing for better resource management.
VMware allows virtual machines to behave exactly like a real computer. This allows each virtual machine to have its own window. This allows IT service providers to install the operating system and software they want on as many virtual machines as they wish, each one being stored on their hard drives. VMware has the advantage of allowing you to install and test software on your computer. You can also run software on a virtual computer that is not compatible with the operating system you have installed.
To run Windows programs on a virtual machine, you can use a Mac to install Windows. You can also use a VMware virtual computer to run an older version Windows program on a PC running a current version of Windows.
For businesses growing rapidly, VMware is a great choice. It’s safer, as you can delete a virtual machine and make a new one if it has a problem. Your physical computer will still be operational in all these cases.
Can You Help Me With My VMware?
Yes we can. InfoTech Services Group receives call regularly from business owners, and business and department managers, who have issues with installation and maintenance of their VMware software. If you need help with VMware call us at (877)724-8781. More information about our services on the hardware and software services page.
Contact InfoTech Services Group
Info Tech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
1-877-724-8781
VMware installation Venice California, IT software installation Venice CA, IT services Venice CA, VMware software services near me, Information Technology software Venice CA, VMware maintenance Venice California, virtual machine software, computer virtual machine installation Venice CA , computer virtual machine maintenance Venice CA
The post VMware Issues Warning For vSphere 7 Update first appeared on .
Originally published here: https://techismything.com/avoid-vsphere-update/?utm_source=rss&utm_medium=rss&utm_campaign=avoid-vsphere-update
0 notes
Text
CyberSecurity From InfoTech Services Group
What Is Cybersecurity?
Cybersecurity refers to the protection of networks, devices, data, and information from criminal or unauthorized use. It also includes the practice of ensuring confidentiality and integrity of information. Businesses now depend on computers and the Internet. Communication (e.g. email, smartphones, tablets), entertainment, transportation (e.g. navigation systems), shopping online (e.g. credit cards), medicine, equipment, and medical records are just a few examples. Much of our everyday life is dependent on technology.
Businesses, organizations, and government agencies all use computers to store information. This means that your computer network contains data about humans that is stored on your computers and it is your responsibility to protect this data. When you have questions about your Cybersecurity, call InfoTech Services Group Inc. at 1(877)724-8781. We can test your computer network system, analyze the data, recommend a Cybersecurity plan and implement that plan to remove malicious software, including viruses, ransomware, worms and spyware.
Cybersecurity Video From InfoTech Services Group Inc.
youtube
Types of Malicious Programs
What is Malware?
Malware, or “malicious software,” is an umbrella term that describes any malicious program or code that is harmful to systems. Hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and mobile devices, often by taking partial control over a device’s operations.
Although malware cannot damage the physical hardware of systems or network equipment (with one known exception: Google Android), it can steal, encrypt, or delete your data, alter or hijack core computer functions, and spy on your computer activity without your knowledge or permission.
There are several different varieties of Malware, including Virus, Ransomware, Worms, and Spyware. InfoTech Services Group provides Cybersecurity programs that will remove and prevent these malware programs from infecting your computer network.
What Is A Computer Virus?
A computer virus is a type of malware that attaches to another program (like a document), which can replicate and spread after a person first runs it on their system. For instance, you could receive an email with a malicious attachment, open the file unknowingly, and then the computer virus runs on your computer. Viruses are harmful and can destroy data, slow down system resources, and log keystrokes.
A computer virus behaves somewhat like a virus that infects humans. Here are 3 main facts about Computer viruses.
A computer virus requires a host program.
To transmit a computer virus from one system to another user action is required.
A computer virus attaches bits of its own malicious code to other files or replaces files outright with copies of itself.
How can I stop computer viruses?
Stopping computer viruses requires investing in good cybersecurity software. InfoTech Services Group does research and analysis on anti-virus software. We have experience and expertise in purchasing the right cybersecurity software, install, and management to stop viruses before they infect your computer network system.
How Do I Remove A Computer Virus?
Removing a computer virus requires a high quality software program that is designed specifically to remove computer viruses and prevention reoccurrence. We use a variety of cybersecurity antivirus programs including Symantec Antivirus Corporate Edition, Symantec Mail Security, PestPatrol, Spy Sweeper, and Spy Sweeper Enterprise. We can analyze your computer system and seek out security issues. Then we will recommend and install the antivirus system that will work best with your computer network.
Call InfoTech Services Group Inc. at 1(877)724-8781 to discuss your cybersecurity situation. Once we have your information we can test your system, then get started removing all computer viruses from your network and ensuring your system will not be infected with computer viruses in the future.
What is Ransomware?
Ransomware employs what is known as “asymmetric encryption.” This type of cryptography uses a pair or keys to encrypt or decrypt files. The attacker generates the public-private pair for the victim. The private key is used to decrypt files and make them usable. Although the attacker will only make the victim’s private key available after payment of the ransom, this is not always true, as we have seen with recent ransomware attacks. It is almost impossible to decrypt files being held hostage for ransom without the private key.
There are many types of ransomware. Ransomware and other malware are often distributed via email spam campaigns or targeted attacks. Malware requires an attack vector in order to establish its presence at an endpoint. Once malware is detected, it stays on the system until it is removed.
Ransomware then drops and executes a malicious program on the infected computer after a successful exploit. The ransomware then searches for and encrypts important files such as Microsoft Word documents, images and databases. Ransomware can also be spread through network and system vulnerabilities, potentially affecting entire companies.
What is a Computer Worm?
Computer worms are a type malware that self-replicates and infects other computers. However, they can also remain active on infected machines. Computer worms can replicate themselves to spread to other infected systems. This is often done by exploiting automatic parts of an operating systems that are invisible to the user. Worms are often only noticed when uncontrolled replication slows down or stops other tasks.
How Do Computer Worms Impact A Website?
Computer worms often depend on vulnerabilities and actions in networking protocols to spread their attacks. Once a computer worm has been installed on infected systems, it will usually follow its primary directive to stay active and spread the worm to other infected systems.
Once infected, one type computer worm malware starts a network search to find new victims. This is done by systems that respond SMBv1 requests. These clients allow the worm to continue spreading within a network. Worms can be disguised so that they appear to be a benign resource (e.g., a link or work file) which the user downloads or clicks on. However, it is later revealed to be a worm.
What is Spyware?
Spyware can be loosely described as malicious software that attempts to gain access to your computer, collect data about you and send it to third parties without your consent. Spyware could also be used to describe legitimate software that monitors data for advertising purposes. Malicious spyware, however, is used explicitly to profit from stolen data.
What Does Spyware Do?
Spyware’s surveillance activity, whether legitimate or fraudulent, can lead to data breaches and misuse. Spyware can also slow down network performance and device performance, affecting daily user activities. All spyware can see your data and track all of your computer activities, whether you have authorized it or not. Many trusted applications and computer services use spyware-like tracking tools. The spyware definition is mainly reserved for malicious programs.
Malicious spyware refers to malware that has been installed without your consent. Step-by-step spyware will perform the following actions on your mobile device or computer:
Infiltrate computers through an app installation package, malicious website or file attachment.
Monitor and capture data via keystrokes and screen captures and other tracking codes.
Email stolen data to the spyware author. Data can be used directly or sold.
What Can I Do To Stop Viruses And Malware?
Use Strong Passwords
Your day to day operations require software passwords, so make certain they are not a point of vulnerability. Do not use common words like “password”, or sequential numbers like 1234. Also avoid using your children’s’ or spouses’ names and birthdates. We recommend using a “complex” password with random letters, numbers and symbols that make up a password that is at least 8 characters long. Also vary your password from website to website or program to program. For larger organizations we recommend changing passwords every 30 to 60 days.
Use The Latest Version Of Your Software Applications
Make certain that all your computer software is up to date and you are using the latest versions for all devices including telephones, tablets, notebooks, cell phones, desktop computers and servers. When commercial software is updated, it is distributed with the most recent programming code necessary to prevent security issues. Major computer software companies, like Oracle and Microsoft are constantly updating their software to remove any program code error that could be used by hackers to break the program.
Any operating system software that has not been updated in more than three years will not have the built in capability to defend against newer malware programs or viruses that are recent programs.
Install Antivirus Software
Antivirus software is a computer program that protects against virtual viruses. Antivirus software can detect and eradicate the threat before you are even aware. At InfoTech Services Group Inc, we use several anti-malware programs including Symantec Antivirus Corporate Edition and other software programs to stop viruses.
Use a Firewall
A firewall is not automatically required if you use antivirus software. Both PC computers and Apple computer are delivered with pre-installed with firewall software. To provide additional protection against malware and viruses, make sure that it is enabled.
Install a Popup Blocker
While you go about your day online, many attacks occur through browsers. Hackers can access your computer by clicking on an innocent link or ad. To protect your computer’s data, an ad blocker or popup blocking program is necessary. It will stop unwanted pages opening automatically.
If you don’t know the source of an email or a file, never click on it, open it, or download it. This is particularly important for emails, which are a major source of malware.
Email Phishing Scams
32% of security breaches reported involve phishing scams. These emails appear as legitimate companies and are sent in an email form. This is an attempt to get you to enter personal information or click on infected links that allow access to your computer.
Every legitimate company should have its own domain for email. It’s a fraud if an email address claims it is from Netflix or PayPal, but ends in @gmail.com.
You should also be wary of suspicious attachments, buttons and links, as well as misspellings and poor grammar. Legitimate companies will not invite you to log in via email and provide billing or personal information. This is a great rule of thumb: if you are unsure, do not click on the link.
Educate Your Business Staff Members
Cyber-attacks are usually the result of an innocent act by an uninformed individual. This could be your child, a family member, or an employee not aware of smart Internet techniques. You can teach anyone using your computer the basics if you are unsure. You can review a few points in this post such as not opening email attachments or clicking on links coming from unknown sources. Cyberattack success and failure could be decided by a few minutes of education.
What Are The Signs of Malware Infection?
Computer viruses can still occur despite your best efforts. Are you able to recognize a virus on your computer’s hard drive? These are some things to look out for:
Multiple error messages
Computer suddenly slows down
It takes too long to restart or shut down the computer
Unexpected shutdowns
You haven’t installed new toolbars
Your home page changes
Rapidly draining battery for notebooks and cell phones
These signs can indicate that your computer has been infected. A virus is almost certain if you see more than one sign. Perform a scan to ensure that all software is the latest version. Search online for other user businesses with similar problems to see if they have any solutions.
Hire InfoTech Services Group Inc.
Most businesses need help with their cybersecurity, but are not in a position to hire full time staff for a Security Department. Use our Managed IT Services to ensure your computer network and servers are running properly and have all the anti-malware protection needed for optimum efficiency for your business.
Call InfoTech Services Group Inc at 1(877)724-8781 to discuss your company’s cybersecurity issues. We will develop and implement a customized IT Managed Services program for you that will include 24/7 cybersecurity for your business.
InfoTech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
1(877)724-8781
Los Angeles Services Area For InfoTech Services Group, Inc.
cybersecurity InfoTech Services Group Inc, computer security InfoTech Services Group Inc, cybersecurity Los Angeles InfoTech Services Group Inc, Los Angeles cybersecurity InfoTech Services Group Inc, virus removal services Los Angeles CA, virus removal software install Los Angeles CA, virus removal software installation Los Angeles CA, virus removal software service Los Angeles CA, virus removal software support Los Angeles CA, virus removal software maintenance Los Angeles CA, virus removal software management Los Angeles CA, virus removal software maintenance Los Angeles CA, virus prevention services Los Angeles CA, virus prevention software install Los Angeles CA, virus prevention software installation Los Angeles CA, virus prevention software service Los Angeles CA, virus prevention software support Los Angeles CA, virus prevention software maintenance Los Angeles CA, virus prevention software management Los Angeles CA, virus prevention software maintenance Los Angeles CA, virus protection services Los Angeles CA, virus protection software install Los Angeles CA, virus protection software installation Los Angeles CA, virus protection software service Los Angeles CA, virus protection software support Los Angeles CA, virus protection software maintenance Los Angeles CA, virus protection software management Los Angeles CA, virus protection software maintenance Los Angeles CA
The post CyberSecurity From InfoTech Services Group first appeared on .
Originally published here: https://techismything.com/cybersecurity/?utm_source=rss&utm_medium=rss&utm_campaign=cybersecurity
0 notes
Text
Remote Access IT Services Improve Business Efficiency
Remote Access Services At InfoTech Services Group
What Are Remote Access Services?
Remote access service (RAS), is any combination hardware and software that allows remote access to tools or information. These typically reside on a network IT devices.
RAS connects a client with a host computer, called a remote access server. Remote control of a computer using an internet connection or another network connection is the most common way to use this remote access services.
After installation, remote access computers can log in to the client’s computer. This allows us (the remote user), to view and manipulate data, execute commands and exchange files.
Who Uses Remote Access Services?
This service is used extensively by large computer manufacturers and businesses to solve technical problems for their customers. There are many professional remote desktop apps that can be used by professionals, whether they’re third-party, open-source, or freeware. Some of these are cross-platform and work with all versions of Windows, macOS, UNIX and Linux. Remote desktop programs may include LogMeIn or TeamViewer.
A RAS client program or any PPP client software is required to use RAS remotely. RAS is supported by most remote control software. Remote access is possible with PPP. It’s a standard set of authentication protocols and framing that industry professionals use.
A Short History Of Remote Access Services
Microsoft Remote Access Server is the predecessor of Microsoft Routing and Remote Access Server. RRAS, a Microsoft Windows Server feature, allows Microsoft Windows clients remote access to a Microsoft Windows server.
This term was first used by Microsoft to refer to the built-in Windows NT remote accessibility tools. RAS is a Windows NT service that allows access to most services available over a modem link.
RAS Compatibility
This service supports dialup and logon. It also provides the same network interface (albeit slightly slower) as normal network drivers. RAS is compatible with many major network protocols including IPX, TCP/IP and NBF. You don’t need to run Windows NT on your client. There are clients for other Windows operating system versions. RAS allows users to log in to an NT-based LAN via a modem or X.25 connection, or a WAN link.
Benefits Of Remote Access Services
Rapid And Accurate Troubleshooting
Secure remote access offers the advantage of being able to remotely troubleshoot issues from anywhere in the world or even across a desk. Remote desktop tools allow help desk technicians to quickly access a user’s device and answer users’ calls. Remote access saves everyone time and reduces travel costs. Remote access can make it possible to complete tasks that used to take a technician several days or more, such as travel.
This allows production to continue without interruption. It is important to resolve issues quickly and efficiently for an organization’s workflow, productivity, and may also be required by service-level agreements (SLAs). Organizations and vendors will benefit from a reliable and comprehensive remote access solution that allows them to keep their agreements and continue to partner with each other.
We specialize in Remote Access services for businesses, organizations, and government agencies. When you need a professional Remote Services company for your Venice CA business contact the skilled and experienced IT services team at InfoTech Services Group, Inc. Call 1(877)724-8781.
View video below to find out more about us.
youtube
Improve Employee Efficiency From Remote Locations
Working remotely is becoming more popular than ever, regardless of the size of your organization. With the COVID-19 epidemic, businesses are being forced to rethink how they work. Remote access allows employees to work safely from anywhere, on any platform or network, whether they are at home or abroad. Remote desktop allows them to access important files remotely and share their screen with others for meetings or troubleshooting.
Collaboration Is Improved
Remote access allows you to communicate securely and quickly with colleagues across the country or clients from the other side of town.
Remote collaboration includes chat functions, file sharing, shared word processing and video conferencing. All of these functions can be performed in an office but it is crucial to ensure that these capabilities can be safely used when working remotely. This can help make work from home days much more productive.
Security Is Enhanced With Log Records
You can log all activity in a network with remote access software. This is an important feature. These logs can be used to track everything, from video sessions to user authentication, including who has accessed your network and when. These logs are also useful for auditing, which is a common practice for organizations that must comply with regulations.
Large And Small Organizations Are Using Remote Access To Increase Efficiency
Remote work is a different concept in the global context. Imagine an organization with a server that runs a production line in Asia and another in Miami. A critical process on the server could suddenly fail, threatening to stop production at that location. Remote access is not possible so a technician in the area would need to resolve the problem. However, technicians may not always be available in every location because this is a global business. This can lead to expensive trips and decreased productivity while the problem is being resolved.
Remote Access Required For Mobile Devices
Remote access is becoming more difficult for organizations that use computers and laptops. Remote access solutions that can be used on different devices is essential for maintaining business operations, especially in retail settings. Technicians can log into secure remote networks to access their mobile devices and troubleshoot.
We specialize in Remote Access services for businesses, organizations, and government agencies. When you need a professional Remote Services company for your Venice CA business contact the skilled and experienced IT services team at InfoTech Services Group, Inc. Call 1(877)724-8781.
InfoTech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
1(877)724-8781
InfoTech Services Group, Inc. of Venice Map
remote computer network services Venice California, computer network service in Venice CA, computer network installation Venice CA, computer network management Venice CA, remote access, Remote Access Services from InfoTech Services Group of Los Angeles and Venice CA provide remote monitoring and management for your computer network. Our remote access services will Improve employee productivity, help your business acquire skilled workers, improve security for remote employees, reduce overhead costs, and assist in business planning.
The post Remote Access IT Services Improve Business Efficiency first appeared on .
Originally published here: https://techismything.com/remote-access-services/?utm_source=rss&utm_medium=rss&utm_campaign=remote-access-services
0 notes
Text
IT Support Los Angeles CA
Information Technology Support and Services
In Los Angeles
InfoTech Services Group, Inc. provide services for Operating Systems (Microsoft Windows), business software applications, and the industry specific software you need for your everyday business operations. We also manage and maintain your desktop or workstation computers, and keyboards, mouse, cables, computer servers, printers, and scanners.
We have 31+ years experience with IT Support, IT Services, Microsoft Exchange Server Solutions, Computer Networking, Internet Security, Email Spam Removal and Prevention, Paperless Office, Remote Access, and Anti Virus software. InfoTech Services Group, Inc. is Microsoft Certified Desktop Support Technician (MCDST), Microsoft Certified Systems Administrator (MCSA), and a Microsoft Certified Systems Engineer (MCSE) on Windows NT 4.0, Windows 2000, and Windows Server 2003 as well as newer versions, including Windows Server 2019. When you need IT support and IT services, contact InfoTech Services Group, Inc. at 1(877)724-8781.
We specialize in Microsoft networking technologies, firewalls, VPNs, and other security solutions in addition to designing and implementing messaging and business solutions for large and small organizations. Contact us today about your information technology requirements.
InfoTech Services Group, Inc. is the best Managed IT Services in Los Angeles and best IT Support in Los Angeles. Get IT Support and Managed IT Service from InfoTech Services Group in Los Angeles. We focus on the IT experience of our customers. We specialize in Cloud Managed Services, Cloud Migrations, IT Consulting, Computer and Server Support, Office re-location, IT processes and IT procedures. You can find us on the web using these terms:
IT Support Los Angeles
Los Angeles IT Support
IT Support
Computer Network Security
IT Services
Network Optimization
Network Support
Cloud Migration
Cloud Services
IT support Los Angeles, IT services Los Angeles, managed IT support Los Angeles, managed IT services Los Angeles, InfoTech Services Group, Inc.
What Are Managed IT Services?
Most small and medium sized businesses (SMBs) do not have the the budget or necessary resources to establish a complete Information Technology (IT) department. SMBs typically do not need a full time IT department. A company may employ one or two staff members who have some computer knowledge, but that is usually insufficient create and maintain the company’s IT infrastructure on a consistent operational level. For an SMB to maintain and expand their Information Technology they should contract with a professional IT support and services provider, like InfoTech Solutions Group, Inc.
This saves time and money for the company. Small businesses can quickly accrue expenses, especially if they don’t use technology very often. This means that the company doesn’t have to spend money on developing an in-house option. A dedicated Technician is paid with benefits much more than what it would cost to hire MSPs.
Some companies think they don’t need IT help. It is almost the last thing they think about – until their computers crash or stop working at all. This is a dangerous way to think. It makes you slower to market and less competitive than companies that allow technology to boost their operational speed.
We live in a technologically dependent world. Even if you don’t think technology is important to your business, IT services are essential. It is difficult to realize the extent of what you use until you are unable to use it. Other Information Technology considerations, such as backups and security, can be quite complex. In fact, IT support and IT services in general, are more complex than most office administrators or business owners realize. It is important to understand that you cannot ignore it and you will be waiting for an incident to occur, even though you may not know about it.
When you business needs Information Technology support and services, contact the premiere IT Support and IT services company in Los Angeles, InfoTech Services Group, Inc. Call 1(877)724-8781
InfoTech Services Group, Inc.
36 Sunset Avenue
Venice, California 90291
1(877)724-8781
Resources: IT Support Services Article
The post IT Support Los Angeles CA first appeared on .
Originally published here: https://techismything.com/it-support-los-angeles-ca/?utm_source=rss&utm_medium=rss&utm_campaign=it-support-los-angeles-ca
0 notes
Text
More Information About Our Premier IT Support
IT Support Web Pages
Here is more information about InfoTech Services Group on these interesting web pages. InfoTech Services Group Inc. specializes in computer service and consulting for individuals, businesses, schools, as well as government agencies. We are a team of computer consultants specializing in helping companies develop their IT infrastructure and provide IT Support services. Our services include E-mail Spam Management, Paperless Office, Remote Access, and Anti-Virus & Worm & Spyware software solutions.
Interesting IT Support Pages
IT support, IT services, Exchange Server, computer network installation
InfoTech Services Group, Inc.
More About IT Support At InfoTech Services Group, Inc.
Computer Installation
We install and service computers and computer networks for businesses and organizations in Los Angeles CA. We repair and replace broken and old computer servers that are no longer performing properly. We have 20+ years experience installing, repairing computers and installing computer networks.
IT Consulting Services
Our IT Consulting services are advisory services that help clients assess different technology strategies and align technology strategies with their business or process strategies. These services support our clients’ IT operations. Our IT Consulting will help your business computer operations.
Computer Networking
We provide Computer Networking systems for business. Computer networking refers to connected computing devices such as desktops, laptops, servers, smartphones, and tablets plus an increasing number of “smart” appliance applications. SonicWall Sales and Support: We install SonicWall services including Next Generation Firewall, Next-generation firewall for SMB, Enterprise, and Government Security Services with comprehensive security for your network, Network Security Manager for security management and Cloud Edge Secure Access, and Secure Mobile Access.
Cloud Phone Systems
We install cloud based phone systems for businesses. A cloud-based phone system is a business communications solution that is hosted and maintained in the provider’s data centers—not at your office—and is delivered through your internet connection.
Computer Repairs + Troubleshooting
We repair broken computers and have been performing repairs and troubleshooting services for 20+ years. Troubleshooting identifies and solves technical problems. Troubleshooting starts with general issues and gets more specific. We are an experienced computer repair and troubleshooting company.
Computer Hardware
InfoTech Services Group, Inc. is an information technology consulting firm, not an equipment reseller. We are often asked to recommend the best and most appropriate hardware and software for your specific requirements. We have extensive experience in working with all major computer manufacturers.
Secure Remote Access
We implement extremely secure remote access solutions that are designed to only allow authorized access to data while it protects your critical information from unscrupulous individuals. We achieve this goal by installing firewall and VPN (Virtual Private Network) hardware and software products.
Email Solutions
Our technical consultants are certified by Microsoft on Exchange Server 5.5, Exchange 2000 – Exchange Server 2019. We can show you how you can combine e-mail accounts from several sources and combine them all into one easy to use Inbox.
Spam Protection
We offer a sophisticated network of spam traps along with other ID layers typically block 98% of all inbound spam with zero false positives produced. Our software strips out @90% of our customers’ total in-bound email right off the top. The remaining 12% is clean and virus-free.
Online Data Backup
Backups of your data are vital. Online backups can be even more critical. When unfortunate events occur, online backups become invaluable. Data loss due to disasters can often not be recovered successfully from local on-site backup media. We have 20+ years experience providing Online Backup Service.
Microsoft Exchange Server Solutions
We provide Exchange Server installation and maintenance. Exchange Server is much more than simply an e-mail solution for your business. Exchange Server provides the foundation for worker collaboration by making available important groupware tools such as group calendaring and shared contacts lists.
Internet Security – Cyber Security
InfoTech Services Group, Inc is your Internet Security + Cyber Security expert. Computer security has come to the forefront as the number one concern for government, private industry, and individuals alike. With the popularity of the Internet as an inexpensive, yet very fast medium, we’ve seen a big increase in viruses and other noxious entities.
SQL Server Database Applications
For large data management we provide Microsoft SQL database solutions. Customer Relationship Management (CRM) systems typically require a SQL server to store their data. We can provide you with advice and a SQL Server programming solution for your company.
Our Los Angeles City Service Area Map
computer installation, computer maintenance, IT support, IT services, Information Technology support, Information Technology services from InfoTech Services Group, Inc.
Here is a link to our: IT Support Los Angeles Map.
The post More Information About Our Premier IT Support first appeared on .
Originally published here: https://techismything.com/it-support-information/?utm_source=rss&utm_medium=rss&utm_campaign=it-support-information
0 notes
Text
Data Backup and the 3 2 1 1 Backup Rule
Data Backup Is Important!
Why is a backup strategy important? According to the University of Texas 94% of companies that suffer a catastrophic data loss do not survive. 43% of businesses do not reopen and 51% are out of business within two years. What’s your company’s backup strategy? Make sure your company follows the best backup practices to protect your valuable data. InfoTech Services Group, Inc. specializes in business computer network backup services. We suggest following the core strategy of the 3 2 1 1 backup rule. What is the 3 2 1 1 backup rule?
The 3 2 1 1 Backup Rule
3 copies of your data.
2 copies on separate media.
1 copy off-site
1 copy off-line.
3 Copies Of Your Data
In addition to the copy of your data that runs on production storage you should have at least two additional backup copies. This gives you a much greater chance of successful data recovery with three copies of your data. If there’s a 1/1000 chance of errors on each copy of your data then the probability of each copy having errors simultaneously is
1/10001/10001/1000 = 1,000,000,000
That’s a one in a billion chance that all three copies of your data will be unreadable – a very small percentage.
2 Copies On Separate Media
It’s important to have at least two copies of your data on separate media like disk AND tape. If all of your backups reside on the same physical hardware and the hardware fails, you will not be able to restore from backup.
1 Copy Off-Site
You should keep one copy off-site to protect against disasters like fire, earthquakes and floods. This copy of your data should be stored far enough away to avoid the impact of any local disaster.
1 Copy Off-Line
It’s important to have at least one copy off-line. This off-line copy protects you against ransomware. Even if you have a copy off-site but still online, ransomware could encrypt all of your on-line backups and you will not be able to recover. Tape is still one of the most cost effective ways to keep your data off-line. An LTO8 tape can natively store 11 TB of data.
Auditing your Backup
It’s a good idea to regularly audit your backup environment before you have to perform a restore. Here are items to consider when auditing your backup.
Ensure All Necessary Data Backed Up
Verify that all production data is backed up. If a server exists it should be backed up. Be sure that any new servers are added to the backup rotation and any retired servers are taken out of the backup rotation.
What is the backup schedule? How often does the backup run? It should be run at least once a day or more often for critical servers. More about the data backup rule at Network World.
We recommend regular restores of your test environment to ensure your data is properly backed up. You don’t want to find out that your backups are corrupted when you need to perform a data restore. Veeam’s SureBackup Feature in their Enterprise and Enterprise Plus versions automatically verifies the integrity of the backup. It runs a malware scan on VM data, verifies it can start the VM in a protected environment and optionally runs a Cyclic Redundancy Check (CRC) on the data to ensure the backup data is valid.
Data Backup Summary
In our opinion you can never be too careful with backups. Having a robust backup strategy ensures you can recover from a data disaster. For more information on creating a customized backup strategy for your company please send an email to [email protected]. We provide IT Support and Network backup services for businesses, organizations and agencies in Los Angeles CA.
Our Los Angeles Service Area Map
Data backup services from InfoTech Service Group Inc, data backup in Los Angeles from InfoTech Services, Los Angeles IT backup service, IT backup services Los Angeles
The post Data Backup and the 3 2 1 1 Backup Rule first appeared on .
Originally published here: https://techismything.com/data-backup-rule/?utm_source=rss&utm_medium=rss&utm_campaign=data-backup-rule
0 notes
Text
Now You Can Avoid Email Scams Before They Damage Your Business
Don’t Let Scam Emails Disrupt Your Business
What Are Phishing Emails?
Phishing emails and phishing text messages often appear as though they’re from an organization or company you already know or trust. They may look like they’re from a credit card company, or a bank, an online payment website (like PayPal), a social networking site (like Facebook), an app, or an online store (Amazon is a favorite for phishing emails). If your are receiving scam and phishing emails, contact InfoTech Services Group, Inc. at 1(877)724-8781. We know how to remove and prevent Phishing Email and other scam emails.
Phishing emails and Phishing text messages frequently include a story trying to trick you so you with click a link or open an attached document. The phishing email might include the following:
Tell you that there has been some suspicious activity or log-in attempts
Inform you that there is a problem with your account or your payment information
Ask you to confirm some personal information
Send a fake invoice
Tell you to click on a link to make a payment
Let you know that you are eligible to register for a government refund
Say they are sending you a free offer
Common Phishing and Scam Emails
Some Phishing Emails are floating around that are particularly tricky. They are very common in the Payroll Protection Program (PPP) and Covid Vaccinations. If your are receiving scam and phishing emails, contact InfoTech Services Group, Inc. at 1(877)724-8781. We have the experience and the skill to rapidly remove phishing and scam emails. We provide service to all businesses and organizations in Los Angeles, Los Angeles County, Orange County, and Ventura County.
Payroll Protection Program (PPP) Phishing and Scam Emails
Quite a few companies have applied for a PPP loan and forgiveness of that loan. Many fake phishing emails attempt to trick you into clicking on a link, downloading an attachment, or entering confidential information. They are typically related to the Loan Forgiveness Process or other PPP related matter. As a general rule, DO NOT open these emails. Study them carefully, hover over any link to see where they will take you (usually over a cliff), review the sender, recipient, and any other clues that the message is fake. If it didn’t come from your bank or sba.gov, it’s probably fake. If you’re not sure, contact your bank or sba.gov directly to confirm that the message is legitimate.
Covid Vaccines Scam and Phishing Emails
We’ve seen numerous emails claiming you can get a vaccine early, pay to “jump” the line, or other methods and promises to get vaccinated early. Do NOT click on any of these emails. Instead, go to https://www.cdc.gov/vaccines/covid-19/index.html or other reputable web sites to get information about the availability of vaccinations in your area.
Hackers are aware that people are concerned, stressed, and may let their guard down during the pandemic. This is the perfect opportunity for these phishing campaigns to be more effective. Make sure to pause and review the email. If you have any doubts, delete the email and contact the resource directly. Stay safe, everyone!
Phishing Email Removal And Prevention
InfoTech Services Group, Inc. technician’s are highly skilled and very experienced at phishing email removal as well as setting up phishing email software on your computer network. We can prevent phishing email from re-occurring on your computers. Call us at 1(877)724-8781 to discuss your computer network and IT support requirements.
Resource for this web page: https://en.wikipedia.org/wiki/Phishing
InfoTech Services Group, Inc.
36 Sunset Avenue
Venice, CA 90291
Our Local IT Support Location Map
InfoTech Services Group can stop email scams block phishing email, block suspicious email, email services; email support company, IT email services, IT email support, prevent suspicious email, prevent virus email, remove suspicious email
The post Now You Can Avoid Email Scams Before They Damage Your Business first appeared on .
Originally published here: https://techismything.com/stop-scam-email/?utm_source=rss&utm_medium=rss&utm_campaign=stop-scam-email
1 note
·
View note