Text
Facebook information download
For this week’s module, we picked one of the companies, download your data and analyse what you've found. Share the types of data you found, and point out one thing that surprised you.

I downloaded my information from facebook and google. I was an actice facebook user till last year, but I started using instagram, so I deleted most of my photos, posts, and etc so I thoought there would be not much stuff that I can have a look. However, facebook was also storing my comment histories as well, which was pretty interesting to me. When i clicked on it, it went to the posts that I commented in, and showed the comments and replies on the comments as well.
0 notes
Text
[Lecture Analysis] Chernobyl
The Chernobyl disaster was a nuclear accident that occured on 26 April 1986 at Chernobyl Nuclear Power Plant. It is considered the worst nuclear disaster the world has ever seen.
Even after many years of scientific research and investigation, there are still many unanswered questions about the accident, especially regarding the long-tern health impacts that the massive radiation leak would have on those people who were exposed.
The Chernobyl plant used four Soviet-designed RBMK-1000 nuclear reactors, a design that's now universally recognized as inherently flawed. In addition, unlike most of nuclear reactors which uses water as a coolant and to moderate the reactivity of the nuclear core by removing the excess heat and steam, RBMK-1000 used graphite to moderate the core's reactivity and to keep a continuous nuclear reaction occurring in the core. As the nuclear core heated and produced more steam bubbles, the core became more reactive, not less, creating a positive-feedback loop that engineers refer to as a "positive-void coefficient."
What caused the disaster?
The disaster occurred on April 25–26, 1986, when technicians at reactor Unit 4 attempted a poorly designed experiment. Workers shut down the reactor’s power-regulating system and its emergency safety systems, and they withdrew most of the control rods from its core while allowing the reactor to continue running at 7 percent power. These mistakes were compounded by others, and at 1:23 AM on April 26 the chain reaction in the core went out of control.
While there is still some disagreement over the actual cause of the explosion, it is generally believed that the first was caused by an excess of steam and the second was influenced by hydrogen. The excess steam was created by the reduction of the cooling water which caused steam to build up in the cooling pipes — the positive-void coefficient — which caused an enormous power surge that the operators could not shut down.

source:
https://en.wikipedia.org/wiki/Chernobyl_disaster
https://www.livescience.com/39961-chernobyl.html
https://www.britannica.com/event/Chernobyl-disaster
0 notes
Text
crackme reflection
valgrind error
When I first tried to run the exercise, I was on my mac, so I just used gcc to create executable and run it with binary ninja. However, when I reached level 0x05, gcc was printing out bunch of errors, and not creating executables. So I asked jazz about this problem.
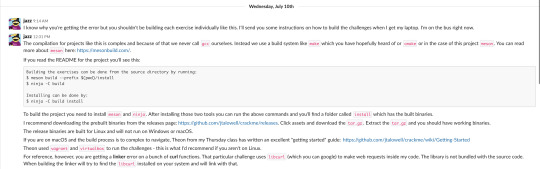
Basically, we were not allowed to use gcc to create executables for the challenge exercises. Also, the released binaries were built for Linux, so it won’t be working on Windows or OS X. Instead, I had to use vagrant and virtualbox to run the challenges. To run vagrant and virtualbox, jazz recommended to read through wiki page written by one of he’s student doing the challenges as well.
assembly
Looking through the code with binary ninja required knowledge on assembly languages. I never learned assembly before, but luckily, I also took COMP1521 this course, which went through assembly codes. Therefore, I was able to understand some lines of codes in assembly ninja.
0 notes
Text
crackme 0x07
The binary requires authentication with an access code.
There are two tasks:
i) exploit a bug that results in the program printing “Access granted!”
ii) modify the binary such that any input results is “Access granted!”

We can see fget() in the first block. Suppose fgets() succeds, we then see strlen(). And the result of this value is compared to 0x07. This tells us that the user password must be 7 characters long. But to submit a password, we have to press enter, which also submits a newline character at the end, so the actual password should be 6 characters long.
After checking the length of the password, the programs calls strtol(). As we seen this in the previous exercise, it converts the passowrd from a stirng to a long int. So we can assume that the passaword is an integer.

We can see that hex value 0x1 is being loaded into another local variable. We can also see that this value is to be incremented in a loop. Here, we can make an assumption that this local variable may be a counter.
In the next block, the value of counter is compared with password. If the value of password is greater than the counter hen the program branches to a block with lots of operations. If not, it jumps to another block towards the bottom of the program.

At the start of this block, the program loads a local variable into a register, XORs the local variable with 0x1, goes through test to check if the value is equal to 0 and branches to the failure section if this comparison succeeds. To fail this comparison, we need the value of the variable to be 1 after the XOR operation. When we look up to the beginning of the program, this local variable is the one which was initialised as 0. We want the value of the variable to be 1 after the XOR, so we want it to stay as 0 by the time it reaches this check. The execution of the program must pass through this block in order to print Access granted.
Now, we can see that this variable is responsible for checking whether access is granted to the program. With the fact that the local variable is of 1 byte length, we now know that the variable is a boolean which determines whether access is provided to the user. We can rename the variable to check_access for clear understanding.
In conclusion, if the comparison between counter and password fails (if the password is less than the loop counter) then the program jumps to the block which checks the value of check_access. If it finds check_access to be 0, then it XORs it to become 1, the test fails and we branch to the ‘success’ section. But check_access starts with the value 0, so all we need to do is ensure that when we branch to this block that check_accessnever changes its value. The way to do this is to provide a password that will always be less than counter. Since the counter starts with the value 1, we can choose any password which has a value less than 1 (any negative number will work!).
0 notes
Text
crackme 0x06
This binary requires authentication with an authentication code.
There are two taks:
1) Find input that results in the program printing “Access granted!”.
2) Modify the binary such that any input results in the program printing “Access denied!”.

First, we can notice that this program reads arguments in the command line. If no arguments are given, it immediately jumps to failure part. We then can see strtol(), which converts the initial part of the string in str to a long int value according to the given base. Therefore, we can assume that the passowrd should be an integer. Because there are no initial value for srand, we can assume that the argument value from the command line will be the seed for srand(). The rand() is then compared to the decimal value 1857631170.
In conclusion, to find a correct password, we have to find a seed that produces the value 1857631170. However, we know that random number generation is not actually random since it will always produce same number when given a particular seed. So I tried to brute force the password for this problem.
Eventually, the valid seed was 22. So this was the password for this task.
Part 2: For this level, to modify the program to deny every attempts, we can set the seed value to any value other than 22 so that the ran() function never returns 1857631170.
0 notes
Text
Module7: Trump phishing
Security Alert!We have detected unusual login on your gmail account. If this is not you, please click the link below to change your password immediately.Login from new devicelocation: New South WalesDevice: Macbook Pro [link]
0 notes
Text
Security Everywhere: FaceApp's viral success proves we will never take our digital privacy seriously
https://edition.cnn.com/2019/07/17/tech/faceapp-privacy-concerns/index.html
This week, I’ve seen a lot of my friends posting their selfies taken by using FaceApp which shows how they look like when they get much older. And it is currently the top free app in App store. However, privacy concerns have grown about the app. One of the headline said “Russians now own all your own photos.”
This incident shows that after more than a year of privacy leaks, consumers still don’t inspect thoroughly on the services before handing over their sensitive personal data. To add, it also shows how little people understand how companies collect out information and what rights they have on it.
According to security researchers, the FaceApp is gathering people’s entire smartphone camera roll. However, the company claimed that most iages are deleted from their servers within 48 hours.
FaceApp terms of service:
"grant FaceApp a perpetual, irrevocable, nonexclusive, royalty-free, worldwide, fully-paid, transferable sub-licensable license to use, reproduce, modify, adapt, publish, translate, create derivative works from, distribute, publicly perform and display your User Content and any name, username or likeness provided in connection with your User Content in all media formats and channels now known or later developed, without compensation to you."
Translation: FaceApp can do whatever they want with your selfie.
Facebook terms of service:
"If you share a photo on Facebook, you give us permission to store, copy, and share it with others,"
But this is not the only tech privacy scandals that happened in the past few years. Data collected through a personality test on Facebook was provided to Cambridge Analytica, a popular period tracking app was sharing data with Facebook, and Amazon listens when you speak ti its Echo smart speakers.
Even though people think this is wrong and companies shouldn’t be donig this, at the moment we hear about a flashy new service that makes our selfies look better or makes our life convenient, we forget about the privacy concerns and use the service right away, without knowing for sure where it’s stored or what it may be used for.
The companies certainly deserve criticism, but so do we.
0 notes
Text
I found your data. It’s for sale.
https://www.washingtonpost.com/technology/2019/07/18/i-found-your-data-its-sale/?fbclid=IwAR1UUaFwYdjNZaI6S8xN6tTpfdoHYjbhZd4YxQJZiyFV05kajW-17Y4yfO4&noredirect=on&utm_term=.e50848ef2f91
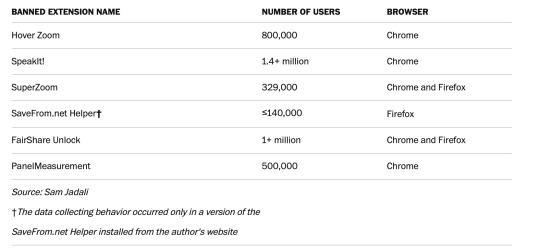
According to a research, as many as 4 million people have web browser extension on chrome and firefox that sell their every click. And this is just the tip of the iceberg.
When browsing, these plug-in makes our life much more convenient. i.e, it finds counpons or remember passwords. People download then assuming that any software from the store run by Chrome or Firefox has got to be legit which is NOT true.
Think about everything you do in your browser at work and home. It knows everything about you. What you think, what you do, what you want. Now, imagine those clicks harvested for hackers.
0 notes
Text
“How Do We Steal Cookies “ Workshop
session cookie
how do we steal cookies
~/Library/Application/Support/Google/Chrome/Default/Cookies (encrypted)
./cookie_crimes > cookies.txt
get a shell
get root
use root_shell to steal cookies
log into everything
does chrome have an API
headless chrome - doesn’t display scren
google-chrome ���headless https://mail.google.com —dump-dom
—>not logged in
chrome —headless —user-data-dir=“$HOME/Library/Application\Support/Google/Chrome/“gttps://gmail.com--dump-dom —logged in as the target! but no cookies
google-chrome —headless https://mail.google.com — remote-debugging-port=9222
use curl
0 notes
Text
Reverse Engineering Workshop Reflection [6/13]
What are computers (from the perspective of a programmer)
-tools we use to do things
-black box machines with defined instructions
-manufacturers provide documentation
What are programs
-series of instructions
-perform complex operations using primitives
Life cycle of computer programs
-CPU requires instructions in binary
-Binary can be represented as hexadecimal
-difficult to programing so instead we use assembly
-difficult to program in and not portable so instead we use C
The role of operating systems(from the perspective of a userland programmer)
-engineers provide documentation
-do trusted things
-provides system calls(instructions)
-abstraction over hardware
-resource management
Virtual memory
-abstraction modern operating systems provide
-we didn’t always have ps
-programs shared memory addresses
-no separation
-hard to know what addresses can be used
mistakes
-thinking that the code they write is the code that runs
-thinking that binary is impossible for a human to understand
understanding executables
-disassemblers take a binary and produce readable assembly
-decompilers take assembly and attempt to produce C
-debuggers let us follow program execution
-control flow graphs help us make sense of the program
breaking executables in the wild
-client-side “protections” are easily defeated
-understand the program
-modify the program to achieve desired behavior
0 notes
Text
Cryptogram : Much faster now!
I’ve been playing cryptogram continuously since the beginning of the course. At first, I had no clue how to approach the text, and took a while to solve it. However, practice makes perfect! I’m now much faster on solving the text and in the mid term as well, it took less than 10 minutes so that I had more time to focus on other questions.






Also found this app on app store which is almost the same as NSA cryptogram.

0 notes
Text
0 notes
Text
Wk07 case study pre reading: Snoop
This week’s question:
Should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
On government’s side
- Face recognition
Why is using credit card on your electric devices allowalble but not face recognition?
To make our lives more convenient, we should get used to it.
Technology has developed enough to secure citizen’s informatoin.
“just walk out technology”
no more gate barriers
easier & faster
Digital identity verification will eventually be integrated with biometric recognition.
- Surveillance
to quickly identify a person of interest to help keep the community safe
This capability will only enable more targeted searching using still images taken from closed-circuit television or surveillance, for example, to quickly identify a person of interest to help keep the community safe.
1. 21st century war is different and requires new ways and methods of gathering information.
On citizen’s side
- Face recognition
the collected data will have enormous commercial value - not guaranteed to be kept secret.
People have a right to expect a certain level of privacy when navigating public spaces
must have trust that governments are taking appropriate action to protect that privacy
stop taking the framing from government that this is something that needs to happen
- Surveillance
if such surveillance continues to increase, people might reach a turning point and adopt some basic measures to “hide” themselves.
Is surveillance needed?
Do I trust the government? -- relatively low trust!
people are concerned about how their information is managed.
high error rate - posing a risk that innocent people are accused of criminality and wrongdoing.

0 notes
Text
Wk06 case study analysis: Safer
Suppose we are thrust into a war with a superpower such as Russia.
List what sorts of computer and internet related attacks might we suffer?
In today’s tutorial, we divided the students into two groups, one as a defense side and the other on the attacker’s side. These are the ideas that we came up and discussed during the class.
Attacker’s side:
Target financial institutions
paralyze the bank system = unable to withdraw money
DoS / DDoS
Defend our own military operations
Phycological warfare
propaganda, face news = targeting the people
differences in ethnicity
Cutoff internet
Holding cyber institutions ransom (i.e bank)
Satellites attack
Stuxnet
Screw with traffic
Emp
Target the allies
Blow an airport, for example, and pretend some other countries did it.
but this might not work because all the coding practices have own signatures of each countries.
Defenser’s side:
State sponored news government
Propaganda doesn’t work
social media = most of the young people gather infomation / see news from the social media.
Close network
Verify Australianity
0 notes
Text
Scam call!
This morning, i got a scam call saying that i had income tax violation so i might get arrested(!) I experienced scam calls in Korea several times, but it was my first time in Australia, so I was a bit frightened at first. However, googling a bit showed that it was a scam.
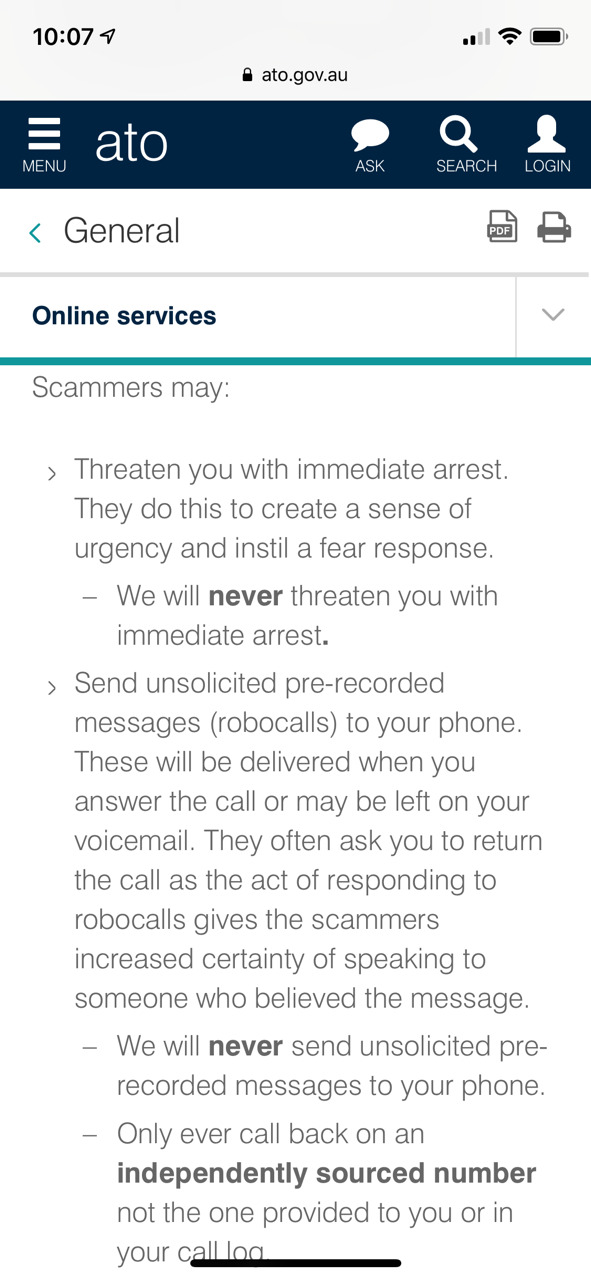
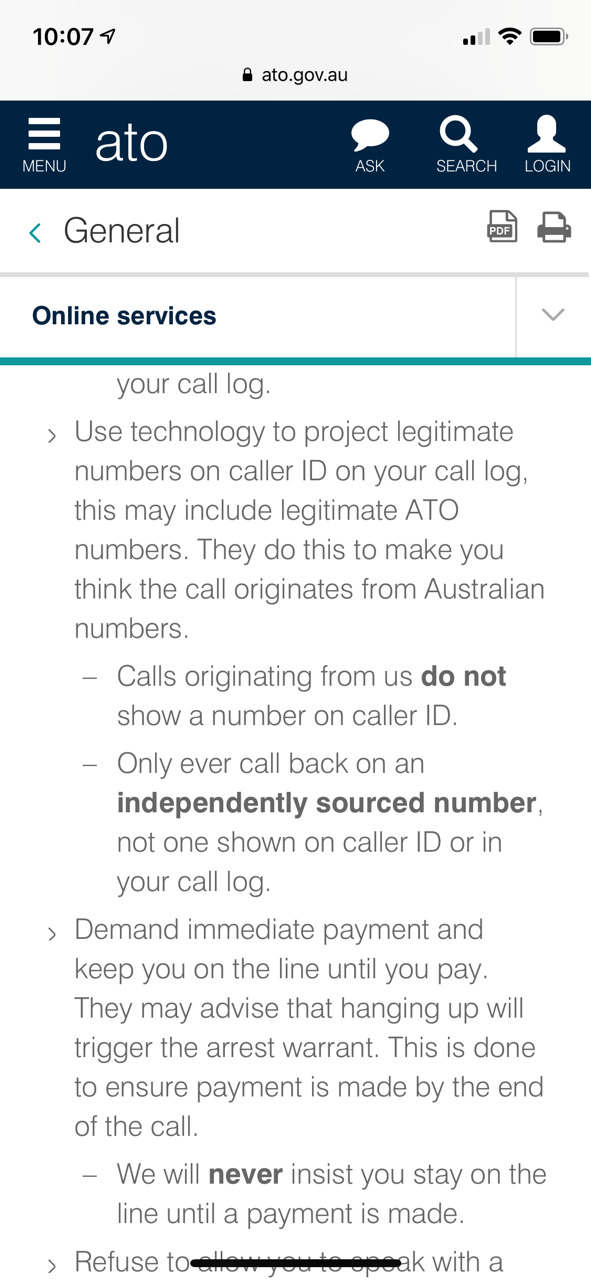
0 notes
Text
crackme0x05
The task for this level was to:
1) Find out how to disable the malware without modifying the binary. You are not required to actually disable it.
2) Modify the binary such that the malware is disabled.
First, I looked at the assembly code to understand what the program actually does. In particular, I looked for control flow, function calls, arguments, and return values.
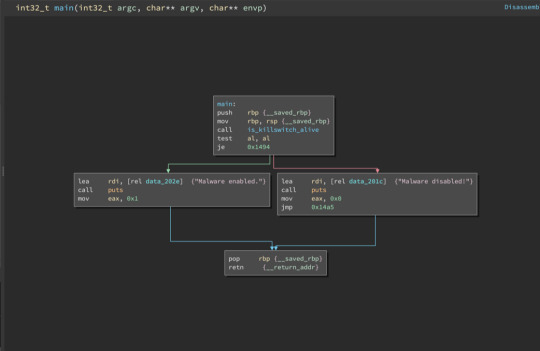
The control flow seemed pretty simple compared to the previous levels. The program calls a function called is_killswitch_alive(). It returns a value, and depending on the return value, the program branches to either a “Malware enabled” block or “Malware disabled” block. So we should have a look at is_killswitch_alive now.
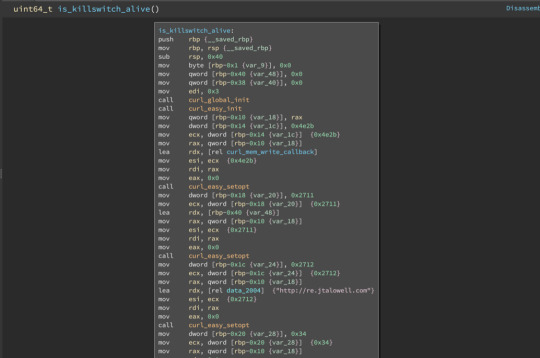
Here, I noticed several calls to curl functions: curl_global_init(), curl_easy_init(), curl_easy_setopt(). Curl is a software used for data transfer.
Since now I know that curl is used to make requests, I looked for a function argument which corresponds to the target of the request. And I could make a guess that this might be the target of the request.
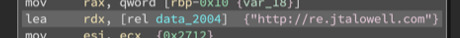
When I go to that link, I found another link, so when I visited it, it gave an error.

When I came back to the code, I saw a call made to another curl function curl_easy_perform(). I could assume that this function performs the curl request which was set up by the previous curl function calls. Before, I made a guess that the target of the requet is http://re.jtalowell.com, and the result of this request should be http://jnqi32uej8qiuenq398hr3jq.com/, which seems to be unregistered.
The program then compares and branch on the return value of the request, which should be checking whether request succeeded or not. If the request was unseccessful, it branches to exit. If it was successful, the programs makes another call to curl_easy_setopt() and curl_easy_perform(). Here, I assumed that the url to visit is the one fetched from the first curl request (http://jnqi32uej8qiuenq398hr3jq.com/).
The program then again compare and jump on the return value of this request. If the request succeded, then the program loads hex value 0x01. Therefore, we can know that this variable is a boolean as a return value for ths killswitch function. In conclusion, to make the program return true, we need to register the domain of the website so that the curl request succeeds. For this level, we don’t have to actually disable the mawalre, so this completes part one of this level.
To modify the program to disable the program, there are many options. (i.e do not branch, nop, etc). However, in this level, we can also disable malware by changing the boolean variable to true at the beginning.
0 notes
