Don't wanna be here? Send us removal request.
Text
Group Think
Richard gave an example of a time he caught himself out in a group think scenario. Whilst he was still fairly junior, he attended a dinner with some senior colleagues and found himself not being able to voice his opinions when he wanted to disagree, and when he would laugh along at jokes even if they weren’t funny.
Group think refers to a situation when you value group membership and harmony, over getting things done right. You don’t want to be the one everyone dislikes and talks about behind your back. This is extremely applicable in the real world, and I am certain everyone has found themselves in at least one group think scenario throughout their lives.
In small contexts it may seem harmless, but this basic human condition can lead to large (often ethical) consequences when left unchecked. The Bay of Pigs incident is often cited as a prime example of group think. The invasion plan was "uncritically accepted” and when others attempted objection, the Kennedy team essentially ignored these objections, continuing to believe in the morality of their plan. Eventually those who objected minimised their own doubts, performing “self-censorship”. “The Kennedy team failed to question the CIA about its false assumptions, including the ineffectiveness of Castro's air force, the weakness of Castro's army, and the inability of Castro to quell internal uprisings”.
Here, group think occurred due to Kennedy’s position of power, with those below him not questioning his authority. As well as himself abusing his power, knowing those below him would be affected by group think and obey his command. It would’ve worked out if perhaps Kennedy’s plan was a good one, yet his lack of revision of the plan resulted in a massive tragedy. As a political leader, Kennedy would’ve evaluated his alternatives in regard for the possible political consequences, especially with the desire to avoid damage to reputation. With the US being a strong capitalist country, and communist Cuba lying so close, it was a direct threat to the country. As such, with self-interest at heart, it’s not surprising the plan went ahead unchecked, with Kennedy going as far as trying to hide US involvement.
Following the invasion, it was believed Kennedy would eventually allow the American military to intervene in Cuba on their behalf, however it was evident he had reservations about explicitly involving the US from the start.
Whether or not he really did only had his own intentions at heart I can’t say for sure, but knowing that there was a lack of revision in the plan, dismissal of outside opinion, and his attitude after the fact, leads me to believe there wasn’t enough effort placed in for him to have truly cared about the cause.
Preventing Group Think
As a leader, avoid stating own preferences when assigning tasks
Allow for others to come up with their own ideas first
Encourage group members to remain critical.
Don't discourage dissent or challenges to the prevailing opinion
Assign at least one individual to take the role of the "devil's advocate"
Discuss the group's ideas with a 3rd party to get impartial opinions
0 notes
Text
SA Reflection
Overall I really enjoyed researching this project! At first I found it extremely daunting, just because I had never done anything like it before and communicating with the system was always just taken as given, I was always told not to worry about function implementations.
I found the learning curve to be harder than I expected, but once I got into it, and did my research, it did become easier as I went on. Originally I had planned to develop a full on rootkit (even though my tutor had warned me this seemed implausible), but what I ended up with was a good grasp of the basics of rootkit related concepts such as hooking and loadable kernel modules, and even a small program that would capture user input as well as hide itself from the system’s ls command. Although I deviated a lot away from my original plan, it was because once I began and had a better idea of what the project really involved, it was easier to make a more realistic estimate of how much I would be able to get done with the remaining time and skill level I had. I also thought it would be more beneficial to put what I’d learnt into practice and create something practical, rather than continue carrying out research because it would show that I actually understood the concepts I had studied.
Something I wasn’t expecting to gain was a newfound appreciation for open source code. Using FreeBSD for this project, hunting down function implementations and learning to exploit them was made a lot simpler and became sort of like navigating a maze within Github (low key fun but high key frustrating).
Following this, there’s still a lot more I want to learn and I will be continuing to do so during the term break. I will also be making a start on playing CTFs because all the Something Awesome projects I’ve seen involving them seem extremely interesting and would be relevant to this by helping learn more about the command line.
0 notes
Text
SA Wk6: More Hiding
Unfortunately it definitely seems I won’t be able to implement a way to hide my program from kldstat. However, I did read up on it to see how I would potentially implement this.
When a module is loaded, both itself and its relevant linker files are stored in two lists, modules and linker_files, respectively.
Both of these are doubly linked lists holding relevant structs, hence we should traverse them, search for the modules/linker files, and remove them.
Relevant struct declarations are defined in /sys/kern/kern_linker.c and /sys/kern/kern_module.c
0 notes
Text
Wk 8: Schedule
Once again I have another dentist’s appointment on Tuesday so I’ve needed to move going over the lecture content to later in the week.
The first 2 days of the week will mainly be focused on making my Something Awesome video. I’m aiming to get it done by Monday but have left time for it on Tuesday if I need it.
The rest of the week will be a little prepping for the Something Awesome presentation on Friday as well as bringing together my job application. I am worried about underestimating how much time I’ll need for this but at the same time I don’t want to fall behind in the course by placing too much priority on it.

0 notes
Text
Wk 7: Public Privacy
This case study involved debating whether or not citizens have a right to their privacy and would have us split into 2 groups, the government side against and the citizens side for. I was in the government side.
Reasons For
If people know they are being surveillanced, they will be less likely to carry out criminal activities
It become easier to locate existing criminals if everyone’s data is accessible
Bomb threats easier to trace and stop
Terrorist attack prevention
Tax avoidance can be ended
Reduction of spam online
Bot social media accounts detected and deleted
Cyber clean
Emergency medical access
Identification of deceased bodies if everyone’s faces are registered
Public access to medical records important in emergencies to identify allergies, diseases, etc.
People who lie about having contagious diseases can be avoided by citizens
Save money on other services
Due to reduced criminal activity, less funds need to be allocated to eg. police departments, physical forensic departments, and can be allocated to other public services such as health, education instead
Sell citizens’ data for revenue
Sounds ridiculous but this is a very possible scenario
Reasons Against
Overall the main reason against is just the fact that holding data creates the vulnerability for leaking that data. Although the government is holding the data for good intentions, not matter how secure they think their system is, the potential for a data breach is there. And as long as it’s there, people with malicious intents are going to try to make it happen. This argument is extremely simple, but it’s a damn good reason as to why citizens should have a right to privacy.
Often people don’t care about whether data should be publicly available because they don’t have anything to hide. But even then, can you really feel comfortable with everyone knowing each and every detail of your life? The routes you take to work, who your friends are, where you live? Having this kind of data on someone makes targeting them a piece of cake. Attackers no longer have to do the research and follow you around every day because Google has done it for them.
Further Thoughts This case study has been the most enjoyable one so far. At first I was not keen to also have to craft arguments for the government side, but it was actually interesting to try and understand their point of view and where they may be coming from. Some of the reasons for collecting data are very valid and could be useful (the idea of a ‘cyber clean’ and eliminating all spam social media accounts sounds extremely enticing), but the trade off for the potential data breach just doesn’t seem to be worth it to me. But then again who knows, if one day lack of public data somehow meant the end of the world then maybe yes I would consider publicising data, but even then, what would the consequences of that be?
0 notes
Text
Off The Grid
With all this talk of privacy and the Internet being evil, I wanted to see what would happen if I just decided to drop off the grid for half a day (whilst I wasn’t at home). No mobile, no Internet. Would my life really become that difficult?
Morning I’d asked my aunt the night before to lend me her physical train timetable (yes they still make those), so I knew which train I’d need to catch to make it to uni on time. To catch a bus to reach the station, I had to read the physical timetable at the bus stop to figure out which bus to catch. This wasn’t terribly inconvenient, the only catch was without my Tripview app, I was not able to check for real-time data so I wouldn’t know if public transport was delayed, and had to hope everything would be running smoothly today. The bus was not exactly on time as scheduled, running 5 minutes late, but I had allowed extra time for this so I was still able to make my train on time, which was also running on time.
What I quickly realised, was how much time I really spend on social media during times like these whilst I’m in transit. I was craving my feed so much so I decided the reasonable course of action would be to take a nap. Normally when I did this, I would set a silent alarm on my phone to wake me up right before I reached my stop but of course I could not. I silently debated whether or not I should ask the person sitting next to me to wake me up at my stop. I decided I was too awkward for this and just risked it, the announcements were usually loud enough to wake me up anyway.
It turned out fine and I did not miss my stop.
Afternoon I didn’t have any classes today, and only needed to attend for a session at business school so the majority of the day wasn’t too bad. I did have a small panic because I’d thought I’d forgotten which classroom I was allocated but I anticipated this and wrote it down on some paper the night before. Coming home, it was basically the same as the morning, needing to check physical timetables. I also thought about how I would do this if I didn’t have a watch and needed to use public services to check the time. The train stations have clocks all over, as well as on notice boards. On the bus if you’re sitting at the front, the time is shown on the bus driver’s screen in the top right corner, so you can peer over his shoulder to see. The uni could invest in some outdoor clocks though. Another strategy was relying on time stamps on receipts I received from food purchases, etc, if clocks weren’t around.
On the bus ride back I actually decided to strike up a conversation with a random person next to me (just out of boredom), and had an interesting conversation about what it’d be like living as a hermit.
Further Thoughts All in all, this was a good experiment and it felt good to get away from the screen for a while. The main thing I learned is that if you are determined, there’s no reason you can’t live without the Internet.
Although some people did miss me...


0 notes
Text
Defending vs Protecting
Throughout the case studies this term, I’ve always found it much easier to think of ways to attack, rather than to defend. I think a concept from this week is going to help.
Rather than considering how best to defend against attacks, we should consider how to protect our largest assets.
Previously, when thinking of defending, I was thinking of ways the enemy could attack us and how we’re going to prevent those attacks. But not once did I ever think about what we are actually protecting here. It’s important to understand that we cannot defend against every attack, and there will always be the potential to be breached, but if we can place our efforts into protecting what is most valuable to us, then we can say we put in our best efforts and did all we could. It would be embarrassing to land in a scenario wherein we’ve put multiple defences in place broadly across our entire system, only to be attacked at a point we had seemingly forgotten about and one of our greatest assets came loose as a result of something that could’ve been prevented if we had targeted our defences.
Consider if we were protecting files on a computer system. We could set up a really strong encryption system such that breaking into the system is difficult, protecting all our files at once, even the trash can files. Or, we can assess which files are most important to us, create physical copies (either on paper, on a removable device, or even not at all), and erase them from the system. Of course, we should not do this for all the files, only our most important ones, as leaving the attacker with nothing after breaking into our system (yes I’ve assumed they were able to bypass our really strong encryption system), would draw suspicion.
Note that specialising defences does not necessarily mean we are going to increase defence by stationing 100 men outside a room or encrypting a file 100 times - this would actually just raise more suspicion. The only foolproof way to protect an asset, is to destroy it. Protecting cash? Spend it. Protecting data? Erase it. Although most of the time this is unplausible, and of course there are many other strategies out there for protecting your asset. The main idea though, is that we know what our assets are.
How to assess our assets;
1. Regularly survey the values of the people involved in what we are protecting 2. Develop a sensible plan 3. Periodically revise the current list of assets
Specialised defence is always stronger than general defence. It even sounds better. And if attacks can be targeted, why can’t defences?
0 notes
Text
SA Wk5: Hiding
From the terminal, ls works through the getdirentries syscall. Hence, hooking this syscall will allow us to hide our malicious files from the user. Its implementation is found in /sys/kern/vfs_syscalls.c .
If sys_getdirentries is successful, it returns the number of bytes successfully read from the directory entries into td->td_retval. The directory entries are stored in the args struct in char *buf as dirent structs. Lucky for me, in COMP1521 I had just completed a lab exercise on file systems so I wouldn’t need to learn about dirent structs from scratch.
To hook the module, I will need to traverse buf after calling sys_getdirentries and remove the entry corresponding to the file I am trying to hide. For simplicity I will just hardcode the name of this file in.
The method of iteration I plan to use is similar to that of a linked list, however instead of using curr = curr->next, I will need to explicitly specify how many bytes to traverse forward, which is made easy using the d_reclen attribute from struct dirent that specifies the number of bytes of the name of the current directory entry.
Pseudocode for the hook function:
Call sys_direntries Save the total number of bytes read Copy in the buf from the syscall Initialise a curr pointer Initialise offset value While we have not read all the directory entries, If the entry is the one we want, Copy the rest of buf into the current position, overwriting the entry Update the total number of bytes read Copy out the new buf Increment curr Increment offset
This sounded easy enough but I ended up having the kernel panic SO many times that I started feeling bad for purposely giving it anxiety. This was due to page faults, ie. accessing memory I wasn’t supposed to. To debug the code I treated this as I would a seg fault, and looked for areas where I was potentially accessing NULL pointers, out of array bounds, etc. Some of the errors I encountered;
Incorrectly calculating the correct byte offset to overwrite the file
Missing type casts in some places
Initialising with NULL instead of mallocing
Not having a condition for empty directories
Interesting: The implementation of malloc is a macro because of a clang 6 bug: “an inline function variant ended up being compiled to a mere malloc call regardless of argument”.
After panicking the kernel another 10 times or so, I finally got the module working! I combined it with the keylogging module and thank god that worked too (but only after it panicked on unload and I realised I accidentally loaded the read syscall into the getdirentries offset).
At this point I’m uncertain whether or not I’ll have enough time to also figure out how to hide the module from kldstat, especially since the video submission will be now due on Tuesday and the Job Application also due next week. If I’m not able to do this by the presentation, I still want to try afterwards to implement it before submitting my Job Application.
0 notes
Text
Wk 7: Schedule
Ive had to move things around quite a bit this week. I have a dentist’s appointment on Tuesday during the time I would normally spend going over this week’s lecture content so I’ve had to move that to Sunday. Ideally I would’ve moved it to Saturday but I’ll be volunteering at the Society of Medical Innovation’s Hackathon during then.
This week the Something Awesome is the priority since the video is due next Tuesday. I was a bit shaken when Richard decided to announce the video would be due on Tuesday rather than simply just before your tutorial. I hadn’t really accounted for this and now I’m worried I won’t complete everything I set out to do.
Two of the buffer overflow exercises from last week were difficult and I’ll be having another go at them this week.

0 notes
Text
Buffer Overflow
Running processes store information in the stack, including variable declarations, functions, and return addreses. Consider if an array of fixed length is stored in the stack by a process. At runtime, if input is read into this array and copied in without checking whether or not it would actually fit into the array, the array is essentially ‘overflown’, and may write into memory stored directly above the array, normally resulting in a segmentation fault. Now consider if the memory that had been overflowed overflowed into a section of the stack holding the return address of a function, overwriting it. The function would then jump to a nonsense address rather than the one it was supposed to.
This forms the basis of a buffer overflow attack.
Buffer overflow attacks occur when an attacker is able to write to invalid memory (eg. beyond the end of a buffer), leaking into return address and overwriting with jumps to their own malicious code some other place in memory, rather than the actual return addresses intended by a process. This vulnerability can commonly occur with functions such as gets(), strcpy(), strcat(), etc as they do not check bounds when called, meaning if the program does not explicitly do so, the potential for a buffer overflow attack arises.
This video from Computerphile was very useful in explaining the concept: https://www.youtube.com/watch?v=1S0aBV-Waeo
This is a good demo showing buffer overflows in practice a bit more in-depth: https://www.youtube.com/watch?v=hJ8IwyhqzD4
I decided to have a go at caff’s buffer overflow challenges.
Basic
This first one seemed pretty straightforward. Two variables are declared; char team = ‘A’ and char name[32]. On inspecting the code, if team = ‘B’, we would reach the win() function, which was the goal. Since team was declared first, overflowing name could potentially write into team. I first tried inputting 33 Bs to see where we’d get, and surprisingly there was no seg fault. I assumed this is because there just happened to be some free space in this memory space. It actually took exactly 48 Bs to the reach the flag.
Command used: python -c "print 'B'*50" | ./basic

Where Am I
This one was a bit more difficult. Overflowing the array was simple enough, just with 64 As, however overwriting the function address needed me to do some goggling. I looked up the hexadecimal table and tried to see if I could just enter in letters/symbols to reach the correct but address but unfortunately not. I eventually found some threads on stack overflow detailing how to explicitly enter in a hexadecimal address, rather than having the system read the string byte by byte. As little endian is used to organise bytes, the address had to be entered from back to front.
Command used: python -c "print 'A'*64 + '\x06\x85\x04\x08'" | ./whereami

Return To Square One
This one was challenging at first as the C code wasn’t provided and I would need to work only with the binary file. I used gdb and initially made it much more complex than I thought, disassembling the file and setting breakpoints. I eventually found out about gdb's info function command on stack overflow, which lists you the defined functions along with their addresses. Bingo! I found a “PlzDontCallThisItsASecretFunction” at address 0x080484e7. What I needed to do now was overflow the buffer to figure out its size then overflow into the return address with the secret function’s address.
To find the size of the buffer, I just flooded the input with A’s, running through gdb with the command run << $(python -c "print('A'*500)"). 500 definitely overflowed the buffer and you can see the 41′s (hexadecimal for A) overwriting the return address below. I just kept guessing until I found the exact point where an over flow starts. I found the size of the buffer to be 268, hence the 269th byte is where it starts overflowing into the return address.
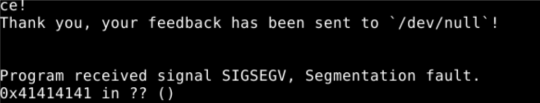
From here, we can carry on just as we did in the previous exercise, appending our own address in little endian format to the A’s.

Command used in gdb: run <<< $(python -c "print('A'*268 + '\xe7\x84\x04\x08')")
Blind I used the same approach as the previous challenge with gdb’s info functions command and found a win() function at 0x08048506. I piped in python commands again at the cmd line in the same way as before and found the overflow starts happening at 77 bytes. Once again throw in the address in little endian format, ‘\x06\x85\x04\x08′, and the flag pops out!
Command used: python -c "print 'A'*76 + '\x06\x85\x04\x08'" | ./blind

I found the concept of buffer overflows pretty interesting because they’re actually quite a massive vulnerability, and with enough practice I think they wouldn’t be too difficult to exploit.
This all ties back nicely to the lecture content and the danger of mixing data and control. With practical applications like this, it becomes clear that mixing the two results in access to data = access to control. Since users have access to the data, if they know this also gives them access to control, manipulation of the system can become trivial.
0 notes
Text
Wk6: Cyber War
For this case study we were asked to consider if we were thrust into war with a superpower, what cyber attacks we might suffer, and what are some strategies we can implement in these situations.
Attacks
Mass power outages
Satellites being taken down
Espionage
Intercepted telecommunications
Telecommunications taken down
Nuclear attacks
Leakage of funds from country
Mass propaganda
Massive data breaches
Redirecting air traffic control commands
Generally just sewing chaos in trusted public services
Strategies
Decentralised energy network, wider implementation of renewable energy
Multiple energy plants supplying power to different areas, all disjoint from each other; in emergencies plants can extend themselves to other areas
In the case central nuclear energy plants are taken down, buildings will have access to energy through renewable sources
Renewable energy generated and not used should be stored in batteries for emergency use
Strengthening relations with allies
If we become helpless due to just too many attacks, we can always ask our allies for assistance if we are on good terms
Eg. if we lose our satellites we can borrow theirs
Can be risky however as it opens the potential for our allies to also go under attack, increasing the scale of the war
Combining physical and cyber requirements to shut down important systems
Eg. Shutting down the power grid requires computer access as well as access to some physical controls
Increases difficulty of attack
May be difficult to implement as physical controls are often mapped to the computer; also increases difficulty when required in emergency shutdown conditions
Cyber task force
Team specifically dedicated to hunting cyber threats and taking them down before they reach our systems
Prevention is always better than a cure
Offensive strategies
The attacks listed above can always be reversed, where we play the same attacks on the enemy before they attack us, whilst we still hold the resources
Once again, with an exercise like this, it’s always easier to think of ways we can be attacked , over ways we can defend against an attack. I think this is because of the mindset humans have in that it is much easier, and more fun(?) to think of ways to destroy something. When you attack something, it is easy to see whether or not your attack was successful, however with defence, you will never know if your defence truly works, and can only wait until it is attacked to see it is flawed. When attacking, you have a target, so you learn everything you can about the target to circumnavigate its defences. When defending, you don’t know what you’re defending against, you may have an idea, but you will never know the exact nature of an attack until it happens, making defence so much more difficult than attack.
At first it was frustrating, but now I’m actually glad that most of these case studies place a larger focus on how we can defend against something rather than attack it because it really gets us to think in a way be normally wouldn’t. The answer is never clear cut, and hearing others’ ideas opens you up so many different ways of thinking. And at the same time, if you become a great defender, you immediately become a great attacker, because now you know all their secret tricks. But then again I guess this could also go the other way around.
0 notes
Text
SA Wk4: Keylogging
I started off just by writing a module that hooks the read syscall, and dumps the output to the console. At first I was testing the module just by loading it, logging out of the system, and then logging back in to see if my keystrokes had been logged. This wasn’t too difficult and was similar to the mkdir hook I wrote last week. However, dumping simply to the console seemed too trivial and I wanted to make it so that the output would be written to a file instead.
To be able to test the module more efficiently, I wrote a simple program that used sys_read to ask the user for a password and checked it against a hardcoded password. To make it a bit less simple, I wanted to make it similar to the system’s log in function so that when the password was typed, the keystrokes would not be shown on the console, meaning the only way an attacker could potentially intercept the keystrokes is from within the system (unless you could see the user tapping their keyboard from the outside but this is out of my control).
Apparently the getch() function from the conio.h header would achieve this for me automatically however it turns out this header is specific only to Windows systems. So I decided to implement my own version of getch() that would do the same thing. This mainly involved just setting the terminal attributes.
My thought process was that in the read_hook function, I should open a file, write to it with the input that was captured, and close it afterwards. However it seems I largely underestimated the difficulty of writing to a file from kernel space.
Here was my original attempt: https://github.com/sherryliu38/comp6841/blob/master/read_hook.c
I also tried variations of this using the kern_openat, sys_writev, kern_writev functions. This involved learning to use the struct iovec and struct uio data types. After spending way too much time on this, reading way too many forum posts, and giving myself anxiety from having 50+ tabs open at once, I came to the conclusion that writing to a file from kernel space may be out of the scope I am capable of. I think that to be able to properly implement this, I would need to have a lot more background knowledge and stronger understanding of how system calls are implemented. I did find some code on the FreeBSD mailing list where someone had attempted writing to a file from kernel space but I just found the method too complicated for me to understand with the level I’m at right now.
The general consensus I found in online forums was everyone being extremely against writing to files from the kernel space and so it was difficult to find more help in where to go next.
I ended up just printing the input into the system log instead because I really want to move on to hiding files from ls and modules from kldstat.
Some notes:
sys_open
sys/kern/vfs_syscalls.c
sys_write
sys/kern/sys_generic.c
sys_close
sys/kern/kern_descrip.c
0 notes
Text
Wk 6: Schedule
This week is pretty tame. The only thing I need to be wary of is underestimating how long it will take me to do the buffer overflow exercises.
The switching of work between Tuesday and Thursday I made 2 weeks ago seems to be working out better so I will be leaving it that way.

0 notes
Text
Wk 5: Giggle Cars
Assets
Customer safety
Reputation
Related technology
Satellites, source code etc.
Stakeholders
Manufacturing facilities
Risks
System is hacked
System self malfunction
GPS signal drops
Self modification by consumers
Industry competition
Lack of market demand
Public backlash
Strategies Addressing Risks
Clearly stated Terms & Conditions
Good software development
Thorough testing
Manual override ability
Procedure With Project
From the perspective of Giggle, despite the risks, it would be beneficial to proceed with the project. In a society where all cars are automated, human error is removed from the equation to greatly decrease the chance of accidents happening. However, this would only be the case if really all the cars were automated, as it would allow vehicles to effectively and instantly communicate with each other whilst on the road, which is an ability real drivers do not possess, hence why road accidents are precisely that, unexpected ‘accidents’. As a result, it seems reasonable that if each car were able to know the exact movements of nearby cars, the probability of these accidents would drastically decrease.
The only other factor we should be aware of, is the chance of technological malfunction leading to accidents. In this case, from the company perspective it is very important to clearly define where the blame lies in this kind of situation, ie. is the accident the fault of the passenger or the company? Similarly, ethical decisions by the vehicles during transport come into question. Consider a case where a vehicle may swerve to avoid another vehicle who has malfunctioned, however this swerve would cause the vehicle to hit an incoming pedestrian. Should the vehicle swerve to save the passenger but hit the pedestrian? It is not until these kind of situations are properly addressed that the project should proceed.
1 note
·
View note
Text
SA Wk 3: Hooking
Before I start this new chapter, there was a section on device modules I didn’t have enough time to cover last week. I’m going to cover it this week before starting Hooking. Hopefully shouldn’t take up too much time as I think I’ve gotten past the first learning curve.
Manipulating User Space Data From Kernel Space New functions:
int copyin(const void *uaddr, void *kaddr, size_t len); /*Copies len bytes of data from uaddr to kaddr */
int copyinstr(const void *uaddr, void *kaddr, size_t len, size_t *done); /* Copies len bytes string, successful number of bytes copied stored in done /
int copyout(const void *kaddr, void *uaddr, size_t len); /*As above but copies from kaddr to uaddr */
int copystr(const void *kfaddr, void *kdaddr, size_t len, size_t *done); /*As above */
Character Device Modules Kernel modules to install/create a character device (interfaces for accessing a specific device within kernel).
A character device is defined by its entries in struct defined in <sys/conf.h>;
struct cdevsw { ... } /*Too many attributes to list, see man */
Not every entry needs to be filled out, those left blank are NULL. The only 2 that must be filled are .d_version and .d_name.
Every entry point defined in struct cdevsw must have a corresponding function implemented. The prototypes for each entry are defined in <sys/conf.h>.
The device registration routine creates or installs the character device on /dev and registers it with the device file system. We do this by calling the make_dev function in the event handler.
sdev = make_dev(&cd_example_cdevsw, 0, UID_ROOT, GID_WHEEL, 0600, "cd_example"); /*Where sdev is of type struct cdevsw; called when loading module*/
destroy_dev(sdev) /*Called when unloading */
Useful Commands
kldstat displays files linked to kernel
kldstat –v for more verbose output
System Call Hooking Hooking modifies program control flow such that when attempting to call one function, the hooking function is called instead. In this context, hooking aims at altering the results of the system’s APIs.
Implementing a system call hook follows basically the structure of implementing a kernel module.
In the event handler function, during load/unload, simply replace the relevant syscall’s function in the sysent[ ] array with your own hook function.
I’m going to attempt writing a module that hooks the system’s mkdir function and prints an output message.
To write this kernel module there were a few pieces of info about the mkdir kernel module I needed to find;
Offset value for sysent
Located under <sys/syscall.h> header #defined as SYS_mkdir
Function prototype/implementation
Located at sys/kern/vfs_syscalls.c
sys_mkdir(struct thread *td, struct mkdir_args *uap)
Args struct definition
Located in same place as function definition above
struct mkdir_args {char *path; int mode; };
Keylogging
A basic rootkit functionality is keylogging. Seeing as I most likely will not be able to implement a full fledged rootkit, I think that being able to write something that keylogs user input and dumps it into a hidden file (maybe a removable usb?) would be a good exercise for the remainder of this project. I will start by writing a kernel module that hooks the read syscall and dumps user input to the console.
Because the midsem is this week, I want to put more focus into revising for that so I’m only going to write some pseudocode for now, and implement it fully next week.
0 notes
Text
Sila
Sila (real name protected for privacy purposes), a guest speaker, came in to speak today about bias in evidence, in context of the medical field. She noted the two main types of bias;
Observation bias
Relating to day-to-day experiences unconsciously influencing your decision-making
Eg. A doctor choosing not to prescribe a drug due to seeing his partner’s own reactions to that drug
Systemic bias
Influenced by entities who just want the outcome to go in one direction; Unconscious conscious decision making (if that makes sense)
Commercial entities will push their bias in order to make profits
Eg. A director of a pharmaceutical company offering to purchase lunch for a doctor to gain their favour in recommending their brand to patients
Studies have shown a $20 lunch has a measurable impact (approx. 5x increased likelihood) on a doctor prescribing that company’s drug over competitors’
Apparently, R&D costs < Marketing costs for drug companies
What was interesting to me, was how security concepts were very relevant and could be related back to this. Systemic bias proves this entire system is vulnerable to attack, wherein it is easier to target single points (individual doctors) rather than the entire system (the medical field itself).
This made me think about the times a doctor had prescribed me pharmaceuticals of a specific brand. I always assumed it was because it would just make it easier for me to find what I needed (rather than having to decide a brand for myself), or because it was the most effective, yet now I am beginning to question the veracity of this. This brings back the idea of never trusting anyone, and conducting your own research on a topic before coming to a conclusion. Next doctor’s trip I will definitely be questioning their integrity (but subtly of course, can’t have my doctor disliking me, especially when she’s jabbing me with a flu shot).
Truly no offence to Sila, I just feel I should question everything, but another point I came up with was after seeing Sila’s determination to be uninfluenced by systemic bias and towards her perspective. Who is to say Sila is not in fact biased herself on her viewpoint? Consider if there arose a scenario Sila were deemed not important enough to be a point of attack for these pharmaceutical companies, therein would lie a bias against them, and hence jealousy a motive to take them down - an inherent human weakness. Leading on from this, there is also the hard to get scenario, wherein Sila is actively, publicly against companies’ influences to increase their motivation to take her down, offering her larger bribes than a $20 lunch.
I always try to see the best in people and so I also question whether profits aside, some companies really do have their customers’ best interests at heart. If a company were finding their product to be more effective than competitors’ but were having issues gaining market power, this would be a legitimate reason to place bias within the system. However after witnessing so many companies do the same with only profits in mind, Sila has been put off the idea all together.
Once again, no discredit to Sila’s professionalism here, I do believe that she has the patients’ best interests at heart and is working hard to eliminate these biases within the workplace and I am grateful for it. It wouldn’t make any sense for her to act in the ways as described above as she would only discredit herself, I just thought it’d be good practice for the weekly case studies to try and consider an opposing perspective. I’m wishing her the best of luck in her fight against bias!
0 notes
Text
Wk 5: Schedule
At this point, I’ve decided it makes more sense if I move revising the lecture content to Tuesday whilst it’s still fresh. As a result, I’ve moved the case study readings to Thursday, which also makes more sense because then I can go into my tutorial on Friday with it still fresh in my mind. If this doesn’t work out I will need to rearrange again.
This week’s priority will definitely be revising for the midsem. This involves practicing bits of security questions, going over the lecture material, and playing around some more with the NSA app.
I most likely won’t be able to work as much on my Something Awesome as I’d like to this week seeing as I also need to move my tutorial reflection to the weekend to prioritise revision.
On top of this, I still need to make slides for our group presentation by Monday next week. Fingers crossed I come out of this alive.

0 notes