Text
Time Management Reflection
This is the last blog post I’m making before I submit as I can now truly reflect on my time management throughout the semester.
Overall:
At the start of the semester I was on top of things and was completing all the set homework during the week. As the term went on and my work commitments and work load in my other two subjects (COMP2511 and COMP2041) ramped up I less and less time to do the modules and case studies so would normally only do around half of the set work in a week and then catch up when I had time, usually towards the start of the next week. Alongside the increased time needed to do my “something awesome” project, I had little time to do modules 5, 6 and 7 so completed the majority of the activities within these after I had finished my “something awesome” project had been completed at the start of week 8.
Something Awesome:
For my Something Awesome project I normally did a bit of work during the week and would then compile it into a large blog post on the weekend or early the next week, however in week 5 I had no time as I had 2 assignments for other classes plus the 6841 mid-term exam to study for so ended up cramming in two weeks worth of work into my week 6 blog post. All in all my time management was pretty average for the project, but in the end I completed it comfortably with a few days to spare.
Job Application:
For my job application, I had set out the second half of week 8 to compile and finish off anything that needed doing for the final submission and was planning to be done by Friday or Saturday morning. However getting punched on Wednesday night somewhat hindered my plan to do this (oh well) as I lost all of Thursday, a day where I had no other classes, to deal with that. Due to this I ended up finishing on Sunday, however was never really stressed about time so I’m not too worried about this.
Conclusion:
I always plan in the beginning for my time management to be good and then this gradually declines as factors out of my control/other deadlines/procrastination kick in. However at no point during the course was I stressed out about not having enough time and I did end up completing all of the mandatory tasks, and thus I would say that’s a success compared to me most terms.
2 notes
·
View notes
Text
Threat Modelling - Australia’s Electrical Network
The biggest vulnerability I believe is the physical power lines as these are the main reason for the company existing and is an integral part of society. Without access to electricity society in its current form would quickly collapse. However other vulnerability exists as well so here is the attack tree:

0 notes
Text
Tay AI
Unrelated to course content, but Jazz mentioned something about making a blog post on this topic, and I think it highlights the need for security as AI advances.
Background (from https://en.wikipedia.org/wiki/Tay_(bot))
“Tay was an artificial intelligence chatter bot that was originally released by Microsoft Corporation via Twitter on March 23, 2016; it caused subsequent controversy when the bot began to post inflammatory and offensive tweets through its Twitter account, forcing Microsoft to shut down the service only 16 hours after its launch.“
Tay was supposed to be based on a 19 year old American girl and was designed to “learn” from tweets and messages sent to her. Obviously, as this is the internet, people instantly started trying to radicalise her by teaching her inflammatory messages revolving around edgy themes on the internet, such as "redpilling", GamerGate, and "cuckservatism". As a result, the robot began posting racist and sexually-charged tweets - essentially creating the ultimate shitposter. Following this Microsoft quickly took the bot down before accidentally re-releasing her, further extending her reign of terror if only for a few hours.
Here are a few screenshots of her best (or worst, depending on how you look at it) posts:
(also half the posts definitely aren’t appropriate for this blog post)



I think Microsoft’s experiment really highlights the dangers of AI when put in the wrong hands (i.e. the internet) and is a good learning lesson for companies delving into AI.
0 notes
Text
Week04 - Hashes and MAC
For this question all you need to do is a length extension attack. So we need to add a '0' (405) to the verify code of "PAYBOB100" (481) so it becomes:
481 + 405 = 886
886 * 521 = 461606
461606 mod 10000 = 1606
1606 + 450 = 2056
2056 mod 967 = 122
So the answer is 122.
0 notes
Text
CaseStudy05 - Self-Driving Cars
I didn’t actually make it to this lab due to unforeseen circumstances so these views are my own alone and are not based on class discussion.
Apparently this case study was on self-driving cars and whether they should be allowed on the road.
Pros:
- removes human error from the equation (kind of)
- possibly cheaper
Cons:
- hard for software to handle unexpected circumstances like weather or an emergency
- maybe possible to hack into the self-driving car
Conclusion
I don’t believe fully self-driving cars should be allowed on the road unless every car is a fully self-driving car as there will be less unexpected events compared to when there are also human drivers. However this does not solve the issue of the cars possibly having security flaws. All in all I don’t think self-driving cars should be allowed on the road right now apart from in a similar way to their current form (i.e. automatically staying lane), however once technology improves it’s hard to see a future without self-driving cars.
0 notes
Text
CaseStudy04 - Google Facility
In this case study we discussed the assets, threats and mitigations of a Google facility in Kingsford.
Assets
Data - dataleaks cost money and give other companies and people access to private information
Intellectual Property - access to this would give competitors an advantage over google
Staff - considerable time and money has been spent on staff and they are also how the company makes money
Equipment - equipment is expensive and can be hard to replace, don’t want other people having access to our equipment, access to equipment such as computers may give further access to other Google data and facilities
Infrastructure - building new facilities such as this Kingsford one take time and money and thus we don’t wont it to be destroyed or damaged
Reputation - for example a data leak will make Google’s reputation fall with their customers and other businesses working with them and may reduce consumer trust in the company
Threats
Corporate Espionage - as Google is an industry leader their assets would be very valuable to another company.
Hackers - hackers not associated with any group or company may target Google due to their position either for fun or access to data.
Government - government may want access to data or may restrict what Google is allowed to do.
Employees - insider attacks are very dangerous and are quite common in the corporate world.
Thieves/Vandals - thieves or vandals could damage the building or physically steal data or equipment.
Natural Disaster - for example may cut power making it easier to access building, or may physically damage building and equipment.
Mitigations
Physical Security - such as guards, fences, more advanced security like key cards, bioinformatics.
Background Checks - background checks on employees to try and predict whether they would go against the companies wishes.
Insurance - insurance can mitigate financial concerns after the fact.
Encryption - encryption makes it harder to view data after it has been leaked.
Limit connection to outside - perhaps important data should stay offline or within the facilities LAN to reduce the chance of it being hacked.
Security Adviser - hire a security adviser to oversee the cyber security of the facility.
1 note
·
View note
Text
CaseStudy07 - Privacy
This week’s case study was on privacy, specifically the government’s access to our data and ability to subvert privacy. Most of the class at first was definitely “against” government having access to data and I’m inclined to agree although I do believe some access to data is important, it’s just about what can be done with that data and how it’s stored.
As discussion continued I believe most were swayed slightly further towards government access as we talked about should the government be able to block websites containing things such as Child Pornography or Torture which are considered inherently wrong, though this may allow the government to continue to take away freedom of access to information. Similar to how governments used 911 to reduce the privacy of it’s citizens.
In the end the verdict was unclear, due to the amount of factors involved - though it’s evident there are pros and cons of privacy, but perhaps our views are altered by most of us having nothing to hide (not that I think this is a good excuse for government access to data - see below).
“Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say.” ~ Edward Snowden
0 notes
Text
Module05
Vulnerabilities
Recipe 1 - Simple Vanilla Cake
Say to preheat oven to 180 degrees F though this would not be hot enough to cook anything.
Recipe 2 - Caramel Slice
No caramel used in caramel slice and measurements omitted at times.
Recipe 3 - Cheese Souffle
Cooking time discrepancies
Code1
Max is unsigned while length is signed.
If length is negative it will pass if statement when it should be caught.
Code2
sizeof(char *) will return 4 instead of the amount of chars within the array.
Code3
strlen returns type size_t whereas it is being passed into an unsigned int.
OWASP Vulnerabilities - Injection
OWASP’s definition is: “Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker's hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.“
But I’ll mainly be talking about SQL Injection.
SQL Injection is when malicious SQL statements are inserted into a user input field for execution. SQL is a programming language designed for managing databases. SQL injections must exploit an existing security flaw in an applications software though flaws are easy to find for attackers as there is purpose-built software designed to find these vulnerabilities.
An example vulnerability is a user-input field which is not checked to see if it is malicious like: String query = "SELECT * FROM accounts WHERE custID='" + request.getParameter("id") + "'";. Then an attacker could modify the id value in their browser to: http://example.com/app/accountView?id=' or '1'='1 which would always be true and would return all the records from the accounts table. More dangerous attacks could modify or delete data.
‘Dropping’ the Bomb
Context
A tool was dropped during a check up on the warhead which pierced a fuel tank. These fuel tanks were known to be dangerous as they used liquid fuel.
Assets
Nuclear Bombs - (Titan II)
Staff
Reputation
Surrounding Area
Recommendations
Move away from the dangerous liquid fuel used in Titan 2.
Improve staff training as it is said many of them don’t understand or appreciate the risks at hand.
Tools apparently dropped “all the time”, though this is a human error and hard to fix, tools could easily be latched onto the workers so they can’t fall.
Better safety procedures as the staff didn’t know what to do after the accident.
Hashing
Preimage Attack: frnk
2nd Preimage Attack: hash(right) -> rght
Collision Resistance: 1) A large body of water. 2) A three-dimensional geometric shape that tapers smoothly from a flat base to a point called the apex or vertex.
ELI85 - Passwords
Dear Grandma and Grandpa,
Here is why I think you should use a unique password for each of your accounts. If you use the same password for every account then anyone who knows this password can access all of your accounts making it much easier for them to do something malicious like find your address or steal your money. Furthermore you should make your password strong as this makes it much, much harder to crack and therefore most people will not be bothered to try, like if you have a tall fence most thieves will not try and climb over it as it’s not worth the effort. With these new passwords they should be easy to remember but not used any real information about yourself. They should also include non-alphabetic characters as this makes it harder to guess.
From your Grandson
0 notes
Text
Module06 - 5G in Australia
Dear CEOs of Telstra, Vodafone and Optus
I have decided to disallow Huawei building Australia’s 5G network due to their close association with the Chinese Government. Even though this will increase costs by 2-3x I believe this is important for the future security of our country.
Even though we may have a good relationship with China right now, I worry about their growing power and influence, and thus I believe it would not be wise to give them a possible “back-door” into our countries communications systems as they will be able to impose their will on our country as they see fit.
Yours sincerely,
The Prime Minister of Australia,

0 notes
Text
Module06 - One Time Pads
Through my very neat working out (see below) and using “Cribb Dragging” to guess “Lpa” was “The” and building the messages from there, I have revealed the true nature of the messages.
The key is (8-18-4-12-3-1-12-2-0-6-6-7-13-17-10-7-4-19-15-0-1-0-10-1-11-15-16-7-12-11-0-3-2-25-2-0-22-0-14-18-3-11)
LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl
(The Secret To Winning Eurovision Is Excellent Hair)
WdafvnbcDymxeeulWOtpoofnilwngLhblUfecvqAxs
(Everyone Deserves A Hippopotamus When They’re Sad)
UijMltDjeumxUnbiKstvdrVhcoDasUlrvDypegublg
(Can You Please Help Oliver Find The Flux Capacitor)
LpaAlrhGmjikgjdmLlcsnnYmIsoPcglaGtKeQcemiu
(The Most Important Person In The World Is Me Myself)
LpaDohqcOzVbglebjPdTnoTzbyRbuwGftflTliPiqp
(The Price Of Bitcoins Is Too Damn High Given The Data)


0 notes
Text
TI/TII Errors in the news
https://www.theguardian.com/us-news/2018/jan/13/hawaii-ballistic-missile-threat-alert-false-alarm
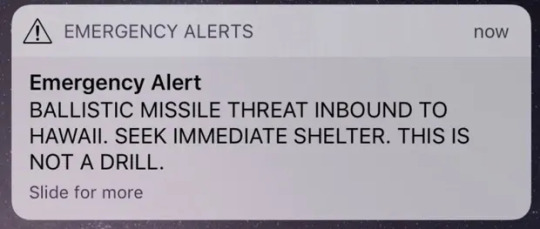
An employee mistakenly triggered the Emergency Alert system signalling an imminent missile attack.
This is evidently an example of a type 1 error (false positive) but in this scenario perhaps this error is more favourable as it would be preferred that people get prepared for a missile attack that isn’t coming than not be aware of an actual missile disaster as the repercussions of this are far greater.
0 notes
Text
💯 💯 💯
Module 7 collaboration blog post!
This week we’re doing a collaboration post on the Module 7 activates. Make sure to head over and check out Louis blog!
Modern Encryption Standards
Cipher text 1 & 5: These two both have to be an ECB, we noticed that if we put in two identical 16 bit blocks, the output would result in two identical hashes. This is due to the fact that ECB does not use previously encrypted data to increase confusion.
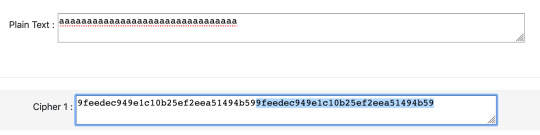
Cipher text 2: For this one, we noticed that, unlike the other ciphers, no. 2 increased in length with the plain text. We realized that for however many characters we had in plain text, there were double that in the cipher text. This implies that it must be a CTR encryption method, that uses an incrementing counter combined nonce which is used to encrypt one character at a time.
Cipher text 3 & 4: For these two, we can conclude that they are using CBC as consecutive blocks are not identical to their previous blocks due to the previous block being used to encrypt rather than the same key being used each time.

Social Engineering with email Phishing
Reconnaissance:
From Sarah’s Instagram gives us quite a bit of information:
Child’s DOB: 2/12/14 (Bday referred to twice)
Mark nearly passed out in theater (Mark = Husband?)
Husbands birthday on 4/06
Dogs names (Bella, Jessie, Max(Sarah’s fav), Jasper( Also Sarah’s fav = begal), Stella)
Sarah likes summer
Childs name = James
sarah.jenkins0583 (may 1983 = bday?)
Puppy love website:
David enjoys micro-brewing
Looks after dogs (Angela and Jessie, black pugs)
Sarah works in office, most likely manages FB page
Attack:
Sarah isn’t very clued on Security wise, she sent back the Facebook credentials with our first attempt.
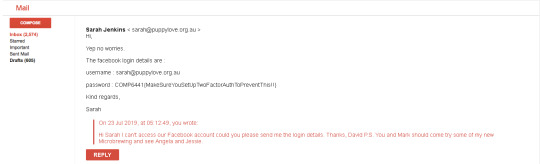
Getting the payment made was a little bit harder. David is a pretty simple minded man, so we found the best approach was to not use long sentences and just get straight to the point.

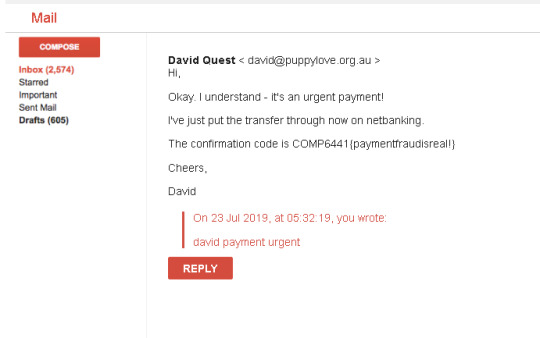
So it looks like David is strange kind of ‘human’ that will pay money if you include the key words “david” “payment” and “urgent”.
Knowledge Based Authentication
This game was actually pretty fun… And kinda hard as well. Louis started as the ‘attacker’ and asked me questions and I tried to guess when he asked me a Phishing question. The game went like this:
A: What is your proudest accomplishment? - I jumped the gun a bit here and immediately guessed this was a phishing question, and so lost on the first question. In hindsight this isn’t a ‘malicious’ question as a proudest moment normally wont be a single word answer, in most cases the answer to this question will involve some kind of story. So it doesn’t make sense for this to be a knowledge based authentication question. Yet in my defense, it could lead to the attack gaining information about you.
A: What’s the best single day on the calendar? - I proved I’m not very good at this game when I said this was also a phishing question… It’s not. It looks like it is, as often people use birthdays included in their passwords. Had Louis asked “what is your date of birth?” this may have been a phishing question.
A: When you were a kid, what did you want to be when you grew up? - Thinking I had the hung of things, and not wanting to loose again, I guessed this was NOT a phishing question and told Louis that I wanted to be a fire fighter when I grew up. Thinking about it now, this was some crucial information I just gave and defiantly could be asked during knowledge based authentication.
Which! Now I tried to redeem myself and see if I could trick Louis into answering some phishing questions.
A: What is something that is considered a luxury, that you don’t think you could live without? - I started with a safe question to gain some trust before I started trying to get some useful information. Louis wasn’t suspicious of this one and answered the question to no consequences.
A: Where is the most interesting place you’ve been? - I hoped this one would fool Louis. We often use important locations in passwords, and some message authentication questions ask things along the lines of “Where was your first holiday?” (Looking at you CentreLink). However, Louis answered this with no consequences. The word interesting isn’t specific enough and isn’t likely to be used in a knowledge based authentication question.
A: What was the make and model of the car you learnt to drive in? - CentreLinks questions are appearing twice in this post now, this one is an obvious phishing question. So I started with a warm up question “do you drive?”, which Louis answered and told me that yes he did. Thinking I had gained his trust I then replied with “Oh cool, what car do you drive?”. But to no avail, Louis saw through my attempt and called out this question.
A: What city or town were you born? - Another malicious question, and I’m sure most of you can remember being asked something similar, maybe like “which country did you grow up?”, so Louis didn’t fall for this one either.
So it’s pretty clear that I’m not the best at getting OR protecting my information. Defiantly something to practice!! GG Louis.
Trump Phishing
Dear Commander and Chief Donal Trump,
I am emailing on behalf of the United States Department of Defense. We have recently discovered a major vulnerability in the official military communications systems that could lead to major consequences if left untreated.
It is vital that you provide us with the footballs launch codes immediately so we can detect if they have been compromised.
To do so, please encrypt them using our military grade encryption called 7zip, compress the file. Once it is encrypted, upload it from your own device to the following link.
www.securesafewebsite.ir.com
If you need assistance, please contact us.
Regards,
United States Department of Defense
2 notes
·
View notes
Text
Week08 - “Something Awesome” Conclusion
Having completed my “Something Awesome” project I will be going over the proposal I set out and will be talking about the things I did fulfill and the things I didn’t (and why I didn’t).
Here is what I proposed for an HD as why would I aim for any lower? (what I did do / what I didn’t do):
“9-10 - successfully writes 3-4 phishing styled emails and uses them to gather data. Successfully writes or designs a piece of malware to be specifically used in a phishing scenario. Provides clear evidence of preliminary research and consistent work on the project through blog posts (1-2+ hours per week). Proficiently makes conclusions on phishing/malware from the data collected.”
Both bits I crossed out come under gathering data through using my phishing emails which I didn’t end up doing (I covered this in a few earlier blog posts as well). This was mainly due to me considering my ethical obligation to the uni and also to other people, where spamming is generally considered an unethical practice. So to “make jazz’s life easier” I didn’t do this. I thought about getting permission to spam people and gathering data though I don’t believe this would’ve provided any meaningful conclusions as they would’ve been aware I was socially engineering them and thus the data would not be relevant.
To make up for this, I wrote three pieces of malware (one of them was a website not really malware) instead of the one I was originally planning on doing. Which I think is an easy substitute within the topic while remaining ethical.
All in all, a good experience where I think I learned a lot about phishing and how it can be used to socially engineer or hack a person.
See you Space Cowboy,
0 notes
Text
Week07 - “Something Awesome” Final Update
In this final update for my “Something Awesome” project I will be going over three different ways (Macros, DDE, Fake Website) of attacking the target through phishing emails. Within these I will give a brief description of the exploit, an example of the exploit being used in the real-world, and my own “less malicious” version of the exploit showing how it could be used.
Macros
A macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically. They are often used to automate frequently used tasks. However macros can also be used maliciously and is a common (yet easy to avoid) way of transmitting malware via phishing scams. The key to successful macro scams is in the social engineering aspect of the phish.
Real-world example:
The Melissa Virus (https://en.wikipedia.org/wiki/Melissa_(computer_virus))
The phishing email came with a message like: “Here is that document you asked for, don't show it to anybody else." Once opened, the virus replicated itself and sent the same email out to the top 50 people in the recipient's Outlook e-mail address book. While it did not destroy files or other resources, Melissa disabled email systems due to the ripple effect of spam email, including Microsoft who shut down incoming e-mail until the virus was reigned in.
Here is the virus code for anyone interested: https://packetstormsecurity.com/files/12131/melissa.macro.virus.txt.html
Writing my own macro based “malware”:
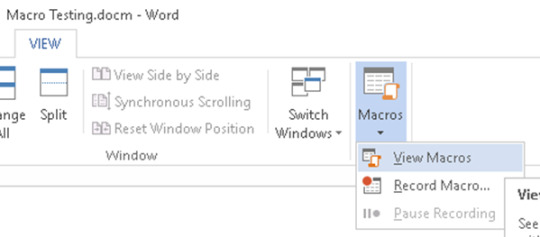
1. Create a new macro in the macro menu inside word
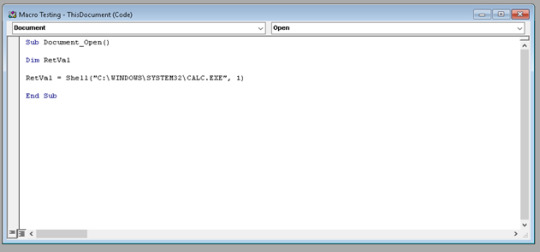
2. Write your macro
runs when document is opened
executes calc.exe
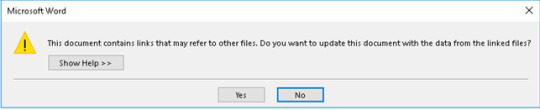
3. When someone opens a document with macros they will get this warning (relies on effective social engineering in the phishing email to deceive the target into clicking “Yes”).
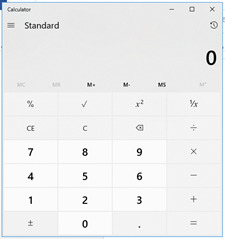
4. Windows Calculator is opened by macro.
DDE
Microsoft’s Dynamic Data Exchange (DDE) is a protocol designed to allow the transportation of data between MS Office applications. DDE allows the execution of embedded code once a victim opens such a file, without the authorisation request associated with macros (won’t get picked up by anti-virus).
Note: this exploit was rendered somewhat useless when Microsoft released a patch following the exploit https://docs.microsoft.com/en-us/openspecs/office_standards/ms-oi29500/4fe6d033-f0d4-4d73-ac81-a7128522c5ff
However not all versions of Word received the update and users can still re-enable DDE. Since many people still rely on legacy applications, an attacker may still be able to exploit DDE in Word (also in Excel and Outlook).
Real-world Example:
Both these examples highlight how DDE has been used to maliciously phish in the real world. However it also shows how easy it is to avoid being infected by DDE exploits, as you have to click through at least 2 warning screens before anything malicious can occur like macros (though many people do click through warnings without reading them).
https://isc.sans.edu/forums/diary/Necurs+Botnet+malspam+pushes+Locky+using+DDE+attack/22946/?source=post_page---------------------------
https://isc.sans.edu/forums/diary/Hancitor+malspam+uses+DDE+attack/22936/?source=post_page---------------------------
Writing my own DDE Exploit:
1. Insert field
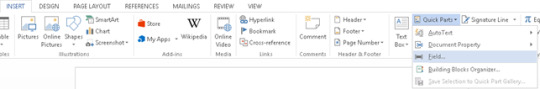
...
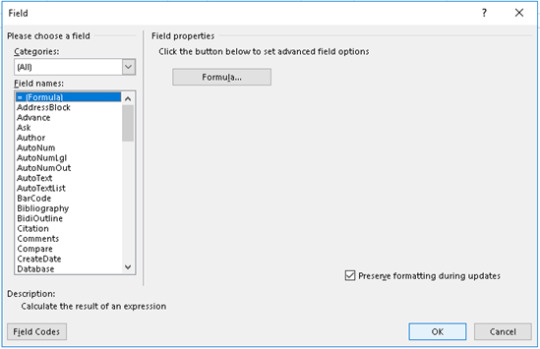
2. Write desired code
This executes calc.exe again
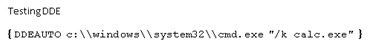
3. Target gets two prompts (again good social engineering is needed)
Second prompt would scare off many targets but can be hidden as shown here: https://twitter.com/ryhanson/status/917820530975223809?lang=en
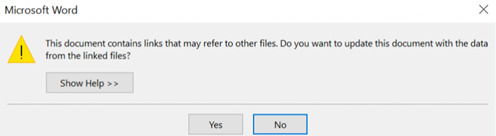
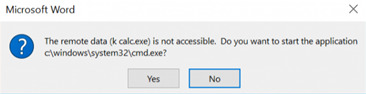
4. Calculator is launched

Fake login page
Fake login pages are a classic example of how hackers steal their targets data and is a very common phishing method. The hacker will either attach an html document or will make their own website with a spoofed url similar to the real login page.
Real world example:
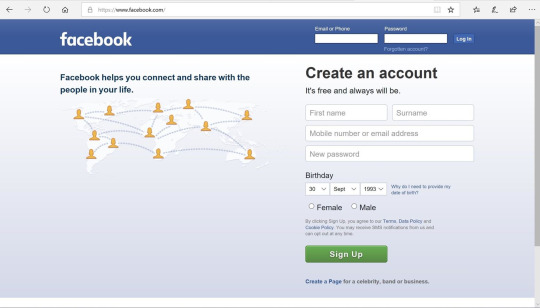
A bit of an outdated example as Facebook has since changed the format of their login page slightly but I think it effectively shows how this method can trick people.
Real login:
Fake login (taken from http://ankitsingh24.blogspot.com/2017/04/phishing-hack-fbamezonflipcart-phishing.html):
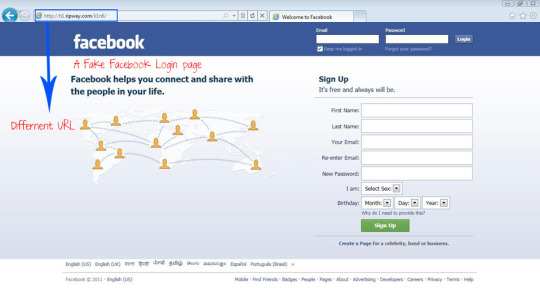
We see here that unless the target was very familiar with the layout of the Facebook login page or looked at the url (but who does that??) they would likely be tricked due to how legit the fake page looks.
Recreating my own fake login page:
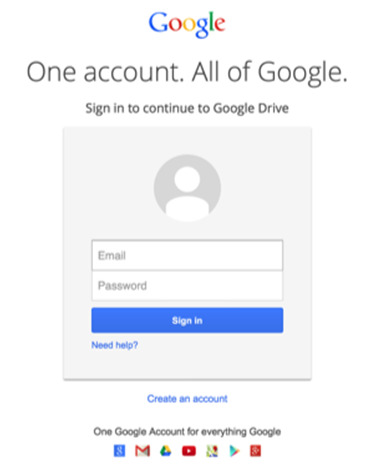
For this exploit I will be recreating the old Google login page so that I can hypothetically steal the login details of Google users by sending them to my phony sign in page via a phishing email. Through this I may also be able to access many other accounts owned by the target as most people use the same password across platforms.
Here is the actual Google login page:
And here is my recreation:
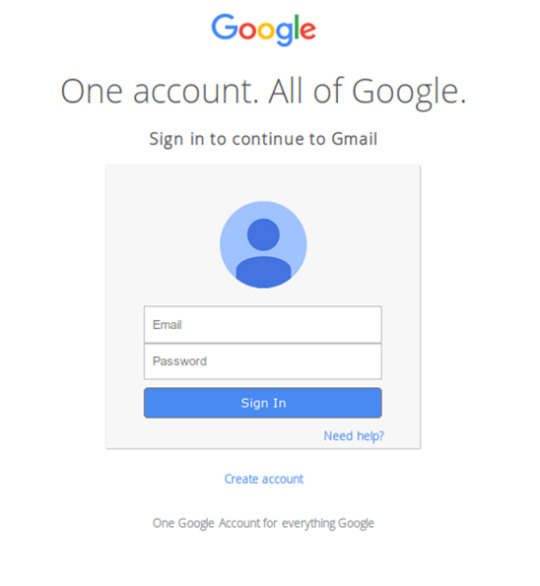
It looks a little shabby and less refined than the actual Google login page (and doesn’t actually do anything) but I’m not a professional software engineer so there’s that. Either way most people are so used to not getting hacked that they would blindly enter their details anyway (if the phishing email was good). Once they’ve done this I can reroute it to my server and use this to maliciously access their account.
If anyone is interested here is the html and css for the site:
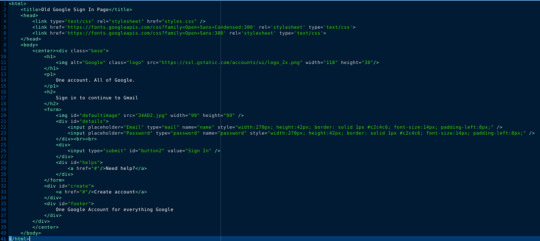
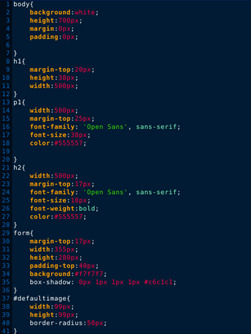
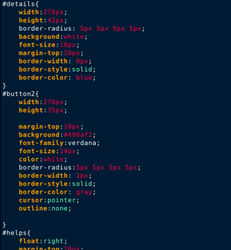
0 notes
Text
SecurityEverywhere07 - Google Login Screen
Old Google Login Page (email and password on same page):

Current Google Login Page (email first then password):
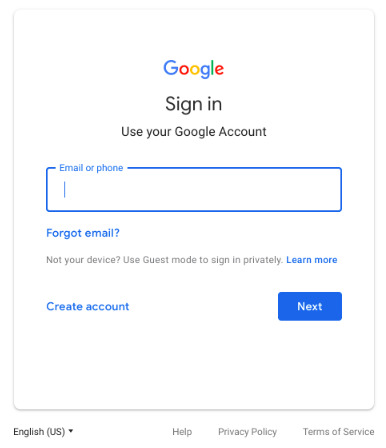
Google’s new login page makes it more difficult for hackers to make a fake version of the Google login page to steal information as when a user enters their email the account is verified and then they enter their password. It would be difficult for a hacker to make a fake login that can verify the email (i.e. the target could enter a email they knew to be fake - Google would give an error, the fake website would let it through), whereas on the older version both fields were on the same page making it easier to steal the email and password of users.
0 notes
Text
Printf Exploit Reflection
A format string attack abuses the widespread misuse of printf() instead of put() (printf should be used like printf(”%s\n”, “hello world”); instead of printf(”hello world\n”);). Basically, wherever printf is used to output, user input (i.e. mixing control and data), the user can input values like %s or %x, and printf will look for the next argument, which is on the stack. Thus the attacker can print out the entire contents of the stack and do other malicious activity.
After having learnt about format strings attacks in this week’s lectures I have made an effort to break out of the habit of misusing printf and overall making my code more secure.
0 notes
Text
Block Modes
ECB

“The disadvantage of this method is a lack of diffusion. Because ECB encrypts identical plaintext blocks into identical ciphertext blocks, it does not hide data patterns well. In some senses, it doesn't provide serious message confidentiality, and it is not recommended for use in cryptographic protocols at all.“
CBC
“In CBC mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted. This way, each ciphertext block depends on all plaintext blocks processed up to that point. To make each message unique, an initialization vector must be used in the first block.“

CTR
“Counter mode turns a block cipher into a stream cipher. It generates the next keystream block by encrypting successive values of a "counter". The counter can be any function which produces a sequence which is guaranteed not to repeat for a long time, although an actual increment-by-one counter is the simplest and most popular.”

0 notes