Nadcab Lab, Leading Blockchain Developers Blockchain development has gained immense popularity over the past decade, transcending its initial association with cryptocurrencies.
Don't wanna be here? Send us removal request.
Text
The Benefits of NFT Wallet Development for Your Company ?

NFT is a name given to the digital representation of assets stored on the blockchain, a distributed and secure ledger system. Every NFT is unique and thus irreplaceable, unlike fungible tokens like cryptocurrencies (like bitcoin).
The way we interact with digital assets—from unique digital content and collectibles to in-game content and event tickets—is being completely transformed by NFTs. That’s why NFT Wallet Development is useful in this situation.
Boost Your Business with NFT Wallet Development
NFT Wallet Development Services can be the way to go if you're a developer, an established business, or an entrepreneur looking to make an identity for yourself in the blockchain world. Here's how:
Opening up new revenue sources: You might benefit from the growing NFT market by building a trustworthy and safe NFT wallet. Aside from safe networking and storage, users will also need to spend on possible interfaces such as an NFT toolset or a wallet-based marketplace. This gives your company a reliable revenue stream.
Enhanced Brand Recognition: Creating an excellent NFT wallet makes you stand out in the blockchain industry. This makes your brand more recognizable to consumers and presents you as the market leader in the rapidly changing field of digital assets. By funding NFT wallet development, those who started using it could benefit greatly in terms of user trust and brand reputation.
Build Customer Loyalty: An attractive NFT wallet promotes user loyalty in addition to attracting new users. You provide a platform that people can trust with their important NFTs by providing an outstanding user experience together with strong security features. This committed user base acts as a starting point for other NFT ecosystem activities.
Diverse User Base: There are no restrictions on the NFT market's target audience. Creating an NFT wallet that is customized will allow you to serve a variety of users. Features like supporting several currencies, connectivity to other NFT marketplaces, and the capacity to handle different NFT kinds (such as music, art, and in-game objects) can all be part of this.
Integrate with Current Products: If you already have a business, adding NFT features can enhance your existing products. For example, an online store can use an NFT wallet for limited-edition items or loyalty programs, boosting customer engagement.
Why Choose Nadcab Labs for NFT Wallet Development?
Security & Experience: Their team is a group of experienced blockchain professionals that specialize in creating safe, accessible NFT Wallets.
Tailored Solutions: Their in-depth understanding of NFTs enables them to create wallets that are specifically tailored to your demands in the NFT industry.
Concentrate on Growth: Flexible solutions guarantee that your NFT wallet is able to meet the needs of an increasing user base.
Working Together: Throughout the development process, you are kept informed through open and honest communication.
Collaboration for Success: Nadcab Labs is dedicated to your success and will work with you to promote your company's growth via your NFT wallet.
In short, using Nadcab Labs for the development of your NFT wallet guarantees that you will work with a group of people who are knowledgeable about the technical aspects of blockchain technology and who can also provide creative, scalable, and safe solutions that will help you expand your company's presence in the digital asset market.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
1 note
·
View note
Text
ERC-7007 for the Future of NFTs

The NFT (non-fungible Token) landscape is rapidly evolving. The original concept of a unique verifiable digital asset will be preserved, but the standards governing the operation of these assets will be expanded. In this case, the most effective standard is scalable, ERC-7007 appears as a strong competitor, an innovative solution for niche markets and a growing segment of the NFT market: AI-Generated Content (AIGC).
Understanding the Need for NFTs
In the digital age, repeatability is king. Photos, videos, and even documents can be endlessly copied and shared. This presents a challenge for creators who want to own their digital work and scale it down. NFTs fix this by using blockchain technology to create unique identifiers associated with digital assets. These marks act as certificates of authenticity that allow producers to prove their ownership and provide collectors with unique items that can be authenticated.
Will ERC-707 Rule the NFT World?
While ERC-7007 is a strong contender, it will be important to see how the NFT fares in standards competitions. Here is a balanced overview of its power potential:
Early Stage: ERC-7007 is still in development and its actual deployment is not yet known. Its ultimate success will be determined by widespread adoption by developers, manufacturers and markets.
AIGC-Specific: While ERC-7007 offers significant benefits to AIGC NFTs, its focus on this particular niche market may limit its widespread use in the NFT market.
Innovation Catalyst: Although ERC-7007 is not a de facto standard, its innovations may inspire future standards that meet the needs of NFT applications.
Features of ERC-7007 Token Standard
ERC-7007 stands out in the NFT standards race by offering features specifically tailored for AI-Generated Content (AIGC) NFTs. Let’s understand with the help of these key features:
Certification of AIGC origin: This is arguably the most important feature of ERC-7007. Standard NFT formats lack the ability to verify AI-generated content. ERC-7007 addresses this challenge by adding non-knowledge machine learning (zkML) and optimistic machine learning (opML) capabilities.
Enhanced minting and management: ERC-7007 is based on the established ERC-721 implementation, which is the basis for most non-fungible tokens. This ensures a smooth minting process for AIGC NFTs, and allows developers to quickly tokenize their work.
Metadata Extensions: Although ERC-721 lays the foundation for token creation, it provides limited options for metadata. ERC-7007 defines additional metadata fields specific to AIGC. This expanded metadata may also include information about the AI model used, the process, and the standards for AIGC products in the future.
Interoperable Interfaces: ERC-7007 defines a set of standardized interfaces for basic functions of AIGC NFTs such as minting, verification, and calculation. This ensures seamless communication between platforms and applications that choose to use the standard.
Use Cases of ERC-7007
The ERC-7007’s capabilities extend beyond looking at the provenance of AI-generated art. These new standards open up exciting applications that could transform the way we create, own and interact with digital content:
1. AI-Generated Art and Collectibles:
The most important use case is created for art, music and design. AI Artists can use ERC-7007 to NFT to print their creations, ensuring verifiable and real ownership. This allows collectors to confidently invest in unique AI-powered pieces.
2. AI-Powered Content Creation Platforms:
Platforms that use AI for creative content will greatly benefit from ERC-7007. The standard provides a framework for AI-assisted consumer product ownership and financing. Imagine a platform where users can access and trade AI-generated poetry, music loops or artwork.
3. Decentralized AI Model Marketplaces:
ERC-7007 itself can facilitate the creation of a market specifically for commercial AI models. These templates can be anything from music generation to graphic design. Standard control functions provide customers with an authentic and high-quality model.
4. Fractional Ownership of AI Art:
ERC-7007 compatibility with ERC-721 opens the door to a fraction of valuable AI-produced art. This allows collectors to purchase smaller shares and share in the ownership of valuable AIGC NFTs.
5. Dynamic and Evolving NFTs:
Some works of AI may evolve over time. Thanks to ERC-7007’s dynamic metadata, these changes are reflected in the NFT itself. This creates a more interactive ownership experience where the NFT becomes a living, breathing work of art.
The Future of NFTs
The release of ERC-7007 is an important milestone in the continuous development of NFT standards. As creators and collectors seek new ways to express and authenticate digital assets, these standards are constantly being adapted. Although it is premature to declare ERC-7007 the ultimate leader, its strong control mechanisms and expected performance place it prominently in the competitive landscape of NFT valuation. Our dedicated team at Nadcab Labs is well versed in ERC-7007 and other state-of-the-art NFT standards, ensuring that we provide expert guidance for NFT token development and implementation.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Cryptography in Blockchain: Build Trust in Decentralized Systems

Cryptography is the backbone of blockchain technology, providing tools to protect data, authenticate participants and ensure transaction integrity. The essence of cryptography is to store and decrypt data while protecting against unauthorized access. Blockchain networks use two main encryption techniques- hash functions and public key encryption.
Cryptography ensures that only authorized users can initiate transactions. Blockchain stores transaction data in chunks that are chained over time. Cryptography without hashing. Hashing is the process of converting any data into a unique code, such as a digital fingerprint. Encryption ensures that only authorized users can initiate transactions. Blockchain stores transaction data in chunks that are chained over time. Cryptography without hashing. Hashing is the process of converting any data into a unique code, such as a digital fingerprint.
Importance of Cryptography in Blockchain
Cryptography is the backbone of Blockchain Security, offering several critical functionalities:
Confidentiality: Although the blockchain itself is public, encryption can hide the exact information of transactions and ensure privacy.
Data Integrity: Cryptographic hashing ensures that blockchain records remain unaltered. Any attempt to manipulate the block would be instantly recognizable due to this hash change.
Non-Repudiation: Digital signatures ensure that a transaction originates from specific users and cannot be repudiated later.
Enhancing Trust and Transparency:By removing the need for a central authority, encryption creates a trusted environment where participants can verify information themselves.
Features of Competent Cryptography in Blockchain
Strong Encryption: Strong encryption uses strong encryption algorithms that are resistant to attacks. Commonly used algorithms are SHA-256 for compression and ECDSA (Elliptic Curve Digital Signature Algorithm) for public key encryption.
Decentralization: Blockchain's cryptographic mechanisms are decentralized, meaning that there is no single entity on the network. This decentralization is necessary to maintain the security and integrity of the blockchain.
Consensus Mechanisms: Cryptography supports consensus mechanisms such as Proof-of-Work (PoW) and Proof-of-State (PoS) needed to authenticate transactions and add new blocks to the blockchain.
Anonymity and Privacy: Although the blockchain is transparent, cryptographic techniques ensure that the identities of users remain anonymous. Only the public keys are visible, not the involved parties.
Application of Cryptography to Ensure Blockchain Security
Cryptography plays a multifaceted role in securing blockchain networks:
Securing Transactions: The sender digitally signs the communication with their private key, which ensures authenticity and prevents unauthorized changes.
Block Validation: Miners or authenticators use a cryptographic hash to verify the integrity of each block before adding it to the blockchain.
Consensus Mechanisms: Many consent mechanisms, such as proof of work, rely on cryptography to secure access and prevent unauthorized influence by malicious parties.
Smart Contract Security: Cryptography protects the rules of Smart Contracts, verifying their authenticity and functionality, and preventing vulnerabilities that could lead to hackers.
Challenges Relating to Cryptography
While cryptography offers immense security benefits, it also faces some challenges:
The rise of quantum computers could break some widely used cryptographic algorithms. To solve this problem, post-quantum cryptography is being studied.
Improper use of key functions such as weak passwords or poor storage can compromise the entire system. Accidentally exposing private keys or cryptographic application vulnerabilities can still leave a system open to attack.
How does Nadcab Labs use cryptography to keep blockchain networks secure and trustworthy?
As a Blockchain Development Company, Nadcab Labs uses cryptography to build trust and security at the very foundation of the blockchain network. This is done by combining cryptography principles and technologies. This technology encrypts data and transactions, ensuring confidentiality and immutability on the blockchain.
Furthermore, cryptography is based on consensus protocols that authenticate transactions and authenticate the network as a whole. By using robust cryptography tools and adhering to secure coding practices, Nadcab Labs empowers businesses to confidently participate in the decentralized world of blockchain.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
The Role of Blockchain in Metaverse

A future where digital and physical realities collide is promised by the approaching metaverse. But how will this virtual environment operate? Presenting blockchain technology, a transparent and safe ledger system poised to serve as the metaverse’s structural backbone.
In this blog, we’ll find out the crucial role blockchain plays in shaping the metaverse, exploring:
Metaverse is a virtual environment that combines digital and physical reality. Virtual reality (VR), augmented reality (AR), and other interactive 3D settings are among the many digital environments it includes. By interacting with one another and the surroundings, users can build a shared and ongoing virtual world. Instead of being a single platform, the Metaverse is a network of linked virtual places that each provide different experiences and chances for amusement, socializing, and purchasing.
Blockchain technology is a distributed ledger system that operates on several computers and is decentralized. Blockchain reduces the possibility of a single point of failure by operating on a peer-to-peer network, in contrast to conventional centralized databases. Because every transaction is kept on file in a publicly accessible ledger, dependability and accountability are raised.
The Importance of Blockchain in the Metaverse
The metaverse is an ever-expanding persistent virtual universe of infinite possibilities. But it needs a solid and reliable base in order to really thrive. Here’s where blockchain technology comes into play, helping to shape the metaverse’s future in a big way. Here’s how the special qualities of blockchain are critical for this new digital frontier:
Ownership and Value: True digital ownership is established by blockchain thanks to its fundamental idea of NFTs (Non-Fungible Tokens). Envision purchasing an exclusive digital asset or a virtual plot of land. By ensuring that these assets are distinct and verifiable, NFTs foster a flourishing digital economy in which users can access, exchange, and profit from their contributions.
Security and trust: The benefits of blockchain’s decentralized structure. Transactions are secure and unchangeable since they are publicly available and preserved in the public library. This stops fraud and gives users the confidence to interact with one other in the Metaverse.
Breaking the Wall: Individual platforms do not have to contain the Metaverse. Blockchain’s interoperability makes it possible for users to transfer their assets and digital identities with ease. Just think of being able to move your valuable virtual sword from one Metaverse game to another!
Empowering Creators: Blockchain gives creators more control in the metaverse. Tokenizing their digital works as NFT allows artists to confirm their legitimacy and maybe take part in future sales. As a result, a dynamic and long-lasting manufacturing economy is created, one that values the contributions of artists.
A Fair and Open Metaverse: Blockchain promotes a decentralized metaverse, free from control by a single entity. This fosters a more open and equitable environment where users have greater control over their data and experiences.
Examples of Blockchain Usage in the Metaverse
Several projects and platforms illustrate the integration of blockchain technology into the metaverse:
1. Decentraland: An online community where Ethereum blockchain technology is used to allow members to construct, purchase, and exchange virtual land. Every plot has a non-fungible token (NFT) representation.
2. The Sandbox: With this platform, individuals can design, possess, and profit from virtual experiences. To ensure genuine ownership and uniqueness, it represents geography, items, and avatars using NFTs.
3. Axie Infinity: In the blockchain-based game Axie Infinity, users breed, fight, and trade virtual animals known as Axies. The game’s native cryptocurrency, AXS, provides funding.
4. CryptoVoxels: Users can purchase CryptoVoxels, an Ethereum blockchain-based virtual world that allows them to build a distributed landscape and engage in unique experiences.
What is the Future of the Metaverse?
The future of the metaverse holds exciting possibilities as it continues to evolve and expand. With advancements in technology and increasing interest from both individuals and businesses, the metaverse is poised to become a central part of our digital lives. Here’s a look at what we can expect:
Enhanced Virtual Experiences
Because of the advancements in augmented reality (AR) and virtual reality (VR), the Metaverse will provide experiences that are more realistic and immersive. Users are able to explore environments that resemble the actual world quite a bit.
Expanded Economic Opportunities
Virtual real estate, digital commodities, and services are among the new financial opportunities that the metaverse is generating. Virtual assets can be purchased, sold, and traded by users, fostering a thriving digital economy. Businesses are likewise searching for fresh approaches to connect and interact with customers.
Interconnected Platforms
Virtual worlds and platforms will interact more in the future within the Metaverse. Users can move between virtual worlds with ease, bringing their identities and digital belongings with them. Metaverse Consulting Company are essential for assisting businesses in navigating this networked environment.
How Nadcab Labs Enhance Interoperability and Security in the Metaverse with Blockchain Technology
Interoperability: Making Things Work Together
Nadcab Labs can create digital items (like avatars, land, or items) that follow common standards. This means these items can be used across different metaverse platforms.
By using blockchain, they ensure that digital assets and currencies can move between different platforms smoothly. This would let users carry their virtual belongings from one game or virtual world to another without any trouble.
Security: Keeping Everything Safe
Blockchain records who owns what in a decentralized way, meaning there’s no single point of control. This makes it harder for hackers to steal or alter ownership of digital assets.
These are self-executing contracts with rules and conditions written in code. They can automate transactions and agreements, ensuring they are carried out exactly as agreed without needing a middleman. This reduces the risk of fraud.
Nadcab Labs can create a more interconnected and secure metaverse, offering users a seamless and trustworthy virtual experience.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
A Deep Dive into Smart Contracts

Within the dynamic realm of Blockchain Technology, smart contracts have become a revolutionary development. The way we communicate and do business online is being completely transformed by these digital contracts, which are written in code and kept on a blockchain.
Digital contracts known as "Smart Contracts" are designed to automatically carry out and enforce the conditions of an agreement. They are kept on a blockchain, which when specific criteria are satisfied, automatically carries out the terms of an agreement. By doing this, the intermediary is removed and the requirement for confidence between anonymous individuals is removed. Consider it an automated, safe method of carrying out agreements and transactions.
How Smart Contracts Differ from Traditional Contracts ?
Here's how Smart Contracts differ from traditional contracts:
Execution: Traditional contracts are executed manually, frequently requiring an attorney or mediator to interpret and carry out the terms of the agreement. Self-executing code, or smart contracts, carry out the agreement automatically when pre-programmed conditions are satisfied.
Intermediaries: A dependable third party, such as a bank or attorney, is frequently involved in traditional contracts. This requirement is removed by smart contracts, which lowers expenses and expedites transactions.
Immutability: A Smart Contract cannot be altered after it has been deployed. This makes the agreement tamper-proof on a blockchain, as opposed to traditional contracts that could be altered or faked.
Transparency: All interactions with a smart contract are all public on the blockchain, giving all parties involved a transparent audit trail. Conventional contracts may lack clarity, allowing for misunderstandings.
In short, smart contracts offer greater automation, security, and transparency compared to traditional contracts, but require technical expertise to create and may not be suitable for all situations.
Smart Contract Platforms and Languages
Smart Contracts are self-executing programs that run on blockchains. They automate agreements and processes in a secure and transparent way. To create these smart contracts, developers need two things:
Here's a breakdown of both:
Platforms for Smart Contracts:
Ethereum: The most well-known and innovative platform. It has its own language, Solidity, and runs on the Ethereum Virtual Machine (EVM).
Solana: Renowned for its cheap rates and quick transaction times. Rust is used in the building of smart contracts.
Cardano: Prioritizes scalability and security. It makes use of Plutus, a special language derived from Haskell.
additional Platforms: There are a plethora of additional platforms, each with unique advantages and disadvantages. Tezos, Polkadot, Avalanche, and Binance Smart Chain (BSC) are a few well-known examples.
Smart Contract Languages:
Solidity: The most widely used programming language for Ethereum-specific smart contracts is called Solidity.
Rust: A general-purpose language that is becoming popular for smart contracts because of its emphasis on performance and security. (Applied by Solana)
Plutus: A functional language with an emphasis on formal verification created specifically for Cardano.
Michelson: Tezos's stack-based language. Additional Languages: For the development of smart contracts, a number of additional languages are utilized, such as Java, Kotlin (for Hyperledger Fabric), and JavaScript (for Stellar).
Use Cases of Smart Contracts
Smart contracts development has a wide range of potential applications across many industries. Here are some of the most promising use cases:
Financial Services:
Smart contracts can manage capitalization tables, distribute dividends, and carry out stock splits in the securities industry. Businesses save time and money as a result of the decrease in errors and paperwork.
Smart contracts can automate the loan and mortgage approval process, reducing the need for human intervention and speeding up loan servicing. Smart contracts have the potential to expedite the processing of insurance claims by automatically determining the legitimacy of a claim and initiating payouts promptly.
Supply Chain Management:
They track products from point of origin to point of delivery, guaranteeing genuineness and lowering counterfeiting. When certain criteria are satisfied, such as a successful delivery, automated payments to suppliers are made, which reduces paperwork and delays, enhances cash flow, and streamlines the supply chain.
How does Nadcab Labs make sure the smart contracts they develop are secure for their clients?
Nadcab Labs protects the security of smart contract manufacturing using a multi-layered, proactive strategy. To guarantee the security of smart contract manufacturing, they employ a proactive, multi-layered strategy. Every smart contract is subjected to stringent regulatory inspection and comprehensive testing in order to detect and mitigate any potential flaws. Because they adhere to best practices and industry standards, their smart contracts are dependable and stable. They frequently emphasize the integrity and security of their smart contracts by collaborating with outside security auditors to carry out impartial reviews and offer further assurance.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Web 3 Revolution: Key Insights for Future-Focused Developers

The rapid evolution of technology is continuously changing the digital landscape. As we stand on the new era, Web 3.0 is poised to revolutionize the way we interact with the internet.
Web 3, also known as the decentralized web, is a paradigm shift in how we interact with the internet. It emphasizes decentralization, user ownership of data, and a more democratic online experience. Also, It leverages blockchain technology to create a more transparent, secure, and user-centric online experience. Unlike Web 2.0, where data is controlled by a few major entities, Key technologies powering Web 3 include blockchain, cryptocurrencies, and decentralized applications (dApps).
Why is Web 3 Important?
Web 3.0 has the potential to address some of the biggest challenges of the current web, including:
Data Privacy: Web 3.0 allows users to control their data and decide who has access to it.
Security: Decentralized networks are inherently enduring to hacking and censorship.
Net Neutrality: An open and decentralized network ensures equal access to information.
Challenges and Considerations
Web 3.0 applications can also be too complex for non-technical users, requiring user-friendly interfaces and learning materials to bridge the gap.
To efficiently process large transactions, a blockchain network must overcome scalability issues. This ensures that seamless communication between blockchain networks and traditional systems is critical. The blockchain and cryptocurrency regulatory landscape continues to evolve, and companies need to stay informed and compliant. Making web 3.0 applications usable and accessible to a wider audience is essential to increasing their adoption.
For Web 3.0 to succeed, these challenges must be addressed to ensure a secure, scalable, and convenient future for the Internet.
The Future of Web 3.0 Development
Web 3.0 development is still in its early stages, but there are several exciting trends to watch:
Maturity of DeFi (Decentralized Finance): Many new financial products and services based on blockchain technology are expected.
Integration of AI and Machine Learning: AI plays a role in customizing user experiences and securing Web 3.0 applications.
Rise of the Metaverse: Web 3.0 can be the foundation of a truly immersive and connected virtual world.
Web 3.0 development is still in its infancy, but there are many interesting things to watch.
How Does Nadcab Labs Make Web 3.0 Easy for Everyone?
They use advanced techniques such as layer 2 scaling and sharding to ensure that their solutions can handle multiple tasks efficiently and effectively. They create solutions that can connect to different blockchain networks and traditional systems, making it easy for users to switch platforms and work seamlessly..
They follow the latest regulations and ensure that their solutions comply with all necessary laws, making them safe and legal for users and businesses. They focus on designing intuitive and user-friendly interfaces. They implement strong security measures, including encryption and rigorous testing, to protect against hackers and data breaches.
Nadcab Labs helps create Web 3.0 solutions that are not only efficient and secure, but also easy to use. This approach makes the wider adoption of Web 3.0 technologies more likely, bringing the benefits of decentralization to a wider audience.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Cryptocurrency Exchanges Explained: Functions, Types, and More-

A Cryptocurrency Exchange is a digital platform that allows users to buy, sell and trade different cryptocurrencies. These exchanges act as intermediaries between buyers and sellers, facilitating transactions and providing a secure environment for exchanging digital assets Users can trade cryptocurrencies for alternative digital currencies or traditional fiat currencies, and exchanges often provide a range of tools and resources to help monitor and analyze trading.
How Does a CryptoCurrency Exchange Functions? Cryptocurrency exchanges work like traditional stock exchanges, but involve digital assets. Here is a step-by-step process.
Register and become verified: The exchange requires you to register for an account, much like other websites. For security purposes, further authentication could be needed for some exchanges.
Fund your account: You can transfer current cryptocurrency to your exchange account or make regular deposits of cash (fiat currency).
Putting in an order: Exchanges offer user interfaces where you can peruse various cryptocurrencies and select the quantity you wish to purchase or dispose of.
Order matching: The mechanism of the exchange compares your order with that of another user in reverse order. The transaction is finished when a match is discovered.
Crypto storage: It's critical to keep your cryptocurrency securely stored after purchasing it. Although some exchanges come with built-in wallets, for more control many users would rather keep their cryptocurrency in their own wallets.
Pros and Cons Cryptocurrency exchanges have made it much easier to buy and sell digital currencies, but they come with advantages and disadvantages: Pros: • Convenience: Exchanges for cryptocurrencies offer a simple way to purchase, sell, and trade cryptocurrencies, just like stock trading. • Buying crypto without crypto: Buying cryptocurrency with fiat currency, like USD, is possible on several CEXs, which eliminates the need to purchase cryptocurrency elsewhere. • Variety of options: The exchange provides a large selection of cryptocurrencies to meet various investment objectives. • Other features: Beyond simple trading, many exchanges provide services like margin trading (for seasoned users), gambling (to receive payment in a currency), and crypto lending (to increase your cash flow profit).
Cons: • Security risk: Your cryptocurrency is stored on centralized exchanges (CEXs), which makes them vulnerable to hacking. • Charges: Your overall profitability may be impacted by the vast variations in transaction charges across exchanges. • Restricted control: The only way you can directly manage your cryptocurrency at CEXs is to move it to a wallet of your own. • Regulations: Since the bitcoin sector is still developing, local laws differ. Certain exchanges could be forbidden in your region.
Types Of CryptoCurrency Exchanges Centralized exchanges, or CEXs, serve as middlemen between bitcoin buyers and sellers. CEXs are typically: • Simple to use: You can typically purchase cryptocurrency with fiat currency through their user-friendly interfaces. • Safe (but not infallible): CEXs often have robust security protocols in place, but there's always a chance that they could be discovered holding your cryptocurrency. • Costlier: Compared to DEXs, CEXs are able to impose larger fees.
Decentralized Exchanges (DEXs): In this, there is no middleman and you trade directly with other users. Every DEX is: • Greater control: Since you keep your cryptocurrency in your wallet, you have greater authority over it. • Not very user-friendly: DEX can be challenging to use, particularly for new users. • Reduced price: DEXs typically have lower fees than CEXs.
How Does It Differs from a Cryptocurrency Wallet ? Exchanges for cryptocurrencies • Marketplace: A Crypto Exchange is comparable to a sizable internet marketplace where individuals congregate to purchase, sell, and exchange different cryptocurrencies. • Focus: Trade and Exchange: Provides functions like buyer-seller matching, trade management, and procurement. • Security: Since exchanges typically store transaction data in their wallets, a hack could jeopardize the exchange's security. • Convenience: CEXs usually allow ordinary currency to be used to purchase cryptocurrency and offer user-friendly transaction processes.
CryptoWallet: • Safe Vault: A crypto wallet is a way to store your cryptocurrency holdings digitally. It acts as a safe haven for your cryptocurrency. • Main Point: Safe Storage: Preserves the secret key that opens your cryptocurrency's blockchain. • Security: Because you own a private key with your wallet, you have more control over your cryptocurrency. • Limited functionality: Trades and orders are two things that wallets often don't give. To trade, you will have to move your cryptocurrency to an exchange.
Why should you consider Nadcab Labs, when choosing a cryptocurrency exchange for your trading needs? Nadcab Labs is a cryptocurrency exchange market startup that provides a number of strong arguments for you to think about using its platform for your trading requirements. • Creative solutions: They create a seamless shopping experience with features you won't find anywhere else by utilizing the newest technologies. • Security at Fort Knox: They take the security of your cryptocurrency seriously and put in place robust security measures to protect your money. • Easy Business: Their easy-to-use platform makes going to market simple, and there's always excellent support available. • Competitive fees: Knowing that fees can stack up, they offer you competitive pricing to help maximize your crypto profitability.
Author Profile: Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
0 notes
Text
How to set up a crypto wallet?

A Cryptocurrency Wallet is used to communicate with the Blockchain network. The three main types of crypto wallets are hardware wallets, software wallets and paper wallets. Based on their performance, they can be further classified as cold or hot wallets. Software-based wallets are more accessible and convenient, while hardware-based wallets are the most secure. Paper wallets are printed on paper and are now unreliable and outdated. In fact, cryptocurrency wallets do not store currency, but act as a means of communication with the Blockchain, i.e. create the necessary information to receive and send money through Blockchain transactions.
The data contains private and public key pairs. Based on those keys, an alphanumeric identifier called an address is created. Basically, it defines the address to which coins can be sent on the blockchain. The address can be shared for money, but the private keys must never be revealed. The private key can be used in any wallet to access cryptocurrency. As long as the private key is known, the money is available on any device. Also, coins are simply transferred from one address to another and never leave the Blockchain.
Why do we need wallets in cryptocurrency?
Crypto wallets are digital tools that keep your digital money safe and give you control over it. They store your private keys, which are like secret codes to securely access your cryptocurrencies. Wallets are important for security because you can send and receive money directly without a bank. They also make transactions quick and easy and at a lower cost than traditional banking services. Whether you use a computer, phone or physical device, wallets ensure your financial independence and privacy in the digital world.
Cryptocurrency Wallet Types
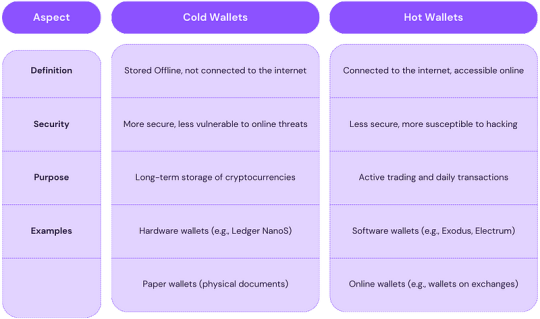
Hardware wallets
Hardware wallets are USB-like devices designed for secure offline cryptocurrency storage. They connect to computers via USB. These wallets offer high security by keeping private keys offline, reducing hacking risks. Popular models include Ledger Nano S and Trezor. While not as user-friendly as web or desktop wallets, they are more accessible than paper wallets. Despite some usability challenges for beginners, hardware wallets are a top choice for robust cryptocurrency protection.
Paper Wallets
A paper wallet is a physical document with a QR code for your cryptocurrency address and private key. They can be created offline, making them safe from hackers. However, they have significant flaws: you can’t send partial funds and the wallet can’t be reused safely. Paper wallets were popular for cold storage but have been largely replaced by more secure hardware wallets. With strict security measures, paper wallets can still be used effectively.
Desktop Wallets
Desktop wallets are apps on your computer for safely storing cryptocurrencies. They’re more secure now but need antivirus protection since they’re online. They’re safer than exchanges for storage.They’re the third safest way to keep crypto and are great for storing on a clean computer. Easy to use, they keep transactions private without involving third parties. Regular computer backups are crucial. Popular choices include Exodus, Bitcoin Core, and Electrum.
Mobile Wallets
Mobile wallets are like desktop wallets but designed for smartphones. They’re convenient for daily transactions using QR codes. But they can be vulnerable to malware, so encryption is crucial to protecting your assets.Mobile wallets are practical and ideal for on-the-go use, but they’re susceptible to viruses. Examples include Coinomi and Mycelium.
Web Wallets
Web wallets, accessed through internet browsers, store private keys online. They can face security risks like DDOS attacks. Hosted versions manage your keys, while non-hosted versions give you full control over your funds, but they’re less secure.Different from hot wallets, web wallets are suitable for small investments and quick transactions. Examples include MetaMask and Coinbase.
Custodial Wallets and Non-Custodial Wallets

Which Should You Choose?
Beginners: Custodial wallets are easier and provide support if you lose access.
Experienced Users: Non-custodial wallets give you more control and security.
How Does Crypto Wallets Work?
Cryptocurrency wallets are digital tools that handle your access to digital money using keys — think of them like passwords. Here’s how they work: When you create a wallet, it gives you a pair of keys. Your public key acts like an address where others can send you cryptocurrencies, while your private key is your secret code to manage and authorize transactions securely. The wallet doesn’t store your actual coins but these keys, which interact with the blockchain to access and control your funds. Wallets come in different types — software ones for computers or phones, hardware devices for extra security, and paper copies for offline safekeeping. Security is key, with wallets using encryption to protect your keys, and backup options like seed phrases to recover your wallet if needed. Understanding how wallets manage keys and connect with blockchain technology is crucial for safely using and managing your digital money.
Why do you need to protect your crypto wallet?
Security of Funds- Your wallet contains private keys that control access to your cryptocurrencies.
Prevention of Theft- Protecting your wallet prevents unauthorized access and potential theft of your digital assets.
Preserving Privacy- Securing your wallet maintains your financial privacy and prevents tracking of your transactions.
Avoiding Loss- Proper security measures and backups prevent the risk of losing access to your funds.
Compliance- Protecting your wallet helps you comply with legal and regulatory requirements.
Peace of Mind- Securing your wallet ensures you have control over your assets and can manage them confidently.
Crypto Wallet Security
Strong Passwords- Use complex passwords that are hard to guess.
Two-Factor Authentication (2FA)-Add an extra layer of security with 2FA for access.
Backup Safely- Keep backups of your wallet’s private keys or seed phrases offline.
Stay Updated- Keep your wallet software updated to get the latest security features.
Secure Networks- Avoid using public Wi-Fi for transactions; use secure, private networks.
Beware of Scams- Be cautious of phishing attempts and avoid clicking on suspicious links.
Consider Hardware Wallets- For extra security, use hardware wallets that store keys offline.
Monitor Activity: Regularly check your wallet for any unusual transactions.
What types of wallets does Nadcab Labs offer, and what services do they provide?
Nadcab Labs offers services for creating cryptocurrency wallets. They are a reputable company specializing in blockchain technology and provide comprehensive solutions for developing secure and user-friendly cryptocurrency wallets.
Services and Wallets Offered by Nadcab Labs -
Custom Wallet Development- Nadcab Labs designs and develops tailor-made wallet solutions to meet your specific requirements. Whether you need a simple wallet for a single cryptocurrency or a complex one that supports multiple currencies, they can create it for you.
Multi-Currency Wallets- They develop wallets that can support a wide range of cryptocurrencies, allowing you to manage different digital assets in one place. This is particularly useful for users who invest in or use multiple types of cryptocurrencies.
Security Features- Security is a top priority for Nadcab Labs. They implement advanced security measures to protect your digital assets. These features can include multi-signature support, biometric authentication (like fingerprint or facial recognition), two-factor authentication (2FA), and encryption techniques to ensure your wallet is safe from unauthorized access and hacking attempts.
Mobile & Web Wallets- Nadcab Labs creates user-friendly mobile applications for both iOS and Android platforms, making it easy to manage your cryptocurrencies on the go. They also develop web-based wallets that can be accessed through any web browser, providing flexibility and convenience for users.
Integration Services- They offer services to integrate the cryptocurrency wallet with your existing systems, whether it’s an e-commerce platform, payment gateway, or any other application. This seamless integration helps in managing transactions efficiently and enhances the user experience.
UI/UX Design- Nadcab Labs focuses on creating an intuitive and attractive user interface and user experience, ensuring that even users who are new to cryptocurrencies can easily navigate and use the wallet.
Backup and Recovery Solutions-They provide robust backup and recovery options to ensure you can restore your wallet in case of data loss or device failure. This often includes features like mnemonic seed phrases and encrypted backups.
Ongoing Support and Maintenance-After the wallet is developed, Nadcab Labs offers ongoing support and maintenance services to ensure the wallet remains updated with the latest security patches and feature enhancements.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
What is post-Quantum Cryptography? How does it work?

Cryptography keeps our digital world safe by ensuring our online activities, like banking and emailing, stay private and secure. It works like a lock and key system, where we can send messages without sharing the key beforehand.
But with the arrival of quantum computers, our digital locks might not hold up anymore. These super powerful computers could easily break the locks on our private emails, making it possible for others to read them. They could also make it easier for fraudsters to steal money through online banking, and even put our country's secrets at risk.
In simple terms, Quantum Computing could break the security we rely on every day online, so we need to find new ways to keep our digital world safe in the future.
What is post-quantum cryptography?
In the quantum computing era, Post-Quantum Cryptography (PQC) is essential for securing digital communication and data. PQC involves developing cryptographic algorithms that are secure against both quantum and classical computers, and can be easily integrated into current systems.
Research in PQC has led to the development of several promising mathematical schemes, including lattice-based, multivariate polynomial, code-based, hash-based, and isogeny-based cryptography. To standardize these quantum-safe algorithms, the U.S.National Institute of Standards and Technology (NIST) started a program in 2016.
The following algorithms selected by NIST address general encryption and digital signatures that are crucial for Securing Data Exchanges and identity authentication:
Quantum Threat to Current Cryptography
Current cryptographic algorithms like RSA and ECC are based on mathematical problems that are difficult for classical computers to solve. However, quantum computers, using algorithms like Shor's algorithm, can solve these problems much more quickly, potentially breaking the security of these cryptosystems.
Imagine your digital secrets as treasures locked away in a safe. This safe is like the one you might have at home, protecting your valuables from intruders. Now, think of a new kind of master thief - the quantum computer. It's not like any thief you've ever seen before; it's super smart and can crack your safe in the blink of an eye, without breaking a sweat.
That's the threat hanging over our current way of keeping digital secrets safe. The locks we use, based on complex math puzzles, are like the locks on your safe. They're strong, but quantum computers have powers that can easily break through them. This means our private messages, online purchases, and even government secrets could all be at risk.
And it's not just a future story. Quantum computers are getting smarter and more efficient every day. It's like watching a storm gather on the horizon, knowing it could hit at any moment. That's why experts are scrambling to find new ways to protect our digital secrets before it's too late.
Why Post-Quantum Cryptography is Important?
Ensuring Long-Term Security- Term Security-Implementing PQC demonstrates your commitment to long-term data security and reassures customers that their data is safe.
Securing a Competitive Lead- Being an early adopter of PQC can set your company apart from others. This positions you as a progressive cybersecurity leader and attracts customers who put security first.
Preparing for Regulatory Compliance- Standards bodies like NIST are working on defining PQC standards. Early adoption can help you stay compliant with future regulations and best practices, avoiding potential legal and financial repercussions.
Future-Proofing Your Systems- Transitioning to PQC now ensures that your systems are protected against future threats, avoiding the need for urgent and costly upgrades later.
Implementing Post-Quantum Cryptography
Step 1- Assessing Current Systems
Evaluate your current cryptographic systems and identify which components are vulnerable to quantum attacks. Develop a roadmap for transitioning to PQC, balancing immediate needs with long-term goals.
Step 2: Educating and Training Your Team
Ensure your development team understands PQC, including how the new algorithms work and how to integrate them. Training is crucial for a smooth transition.
Step 3: Selecting Appropriate Algorithms
Choose the right PQC algorithms for your use cases. NIST’s ongoing standardization process is a valuable resource for finding vetted algorithms that meet your needs.
Step 4: Implementing and Testing New Algorithms
Carefully implement the chosen PQC algorithms and rigorously test them to ensure they meet security and performance requirements. Thorough testing is essential to identify and fix potential issues.
Step 5: Communicating with Clients
Inform your clients about the importance of PQC and the steps you’re taking to protect their data. Transparency builds trust and reassures clients that you are proactive about security.
Projecting into the future
Post-Quantum Cryptography is now a reality rather than just a theoretical idea. PQC has been used in a number of ways. OpenSSL has completely supported PQC for digital signatures and fundamental establishment procedures in its most recent version. Being the first to use PQC for main key generation, Signal Protocol, a crucial component of Signal, Google RCS, and WhatsApp communications, also revealed support for the PQXDH protocol. For iMessage, Apple has launched a new PQ3 encryption protocol that provides enhanced post-quantum security features.
PQC is expanding quickly in the fields of cryptography, quantum safe digital signatures, and basic exchange mechanisms. Given the growing hazards associated with quantum supremacy, its broad implementation is inevitable.Because standardized algorithms have not been tested in the real world, they may contain exploitable errors that force them to change or create entirely new algorithms.
Post-Quantum Cryptography has been an important part of cyber security plans for many years. In addition, safety regulations should require or recommend Post-Quantum Cryptography.
Post-Quantum Cryptography is now an integral part of an organization's security, protecting the integrity and confidentiality of sensitive data and preventing quantum attacks.
Businesses need to start preparing for the post-quantum transition from secure lock to impenetrable vault! Service providers are essential to helping businesses succeed at all levels.
How is Nadcab Labs incorporating post-quantum cryptography into its development strategies?
Nadcab Labs is focusing on advancing Post-Quantum Cryptography in its development initiatives. They are playing a supportive role in the development of new cryptographic algorithms that are resistant to quantum computer attacks. Additionally, they are participating in standardization initiatives with prominent organizations like NIST and ETSI, aiming to develop and promote post-quantum cryptographic standards.
Nadcab Labs is preparing to integrate post-quantum cryptography into their products to enhance data security for their customers. Their main goal is to be prepared well in advance of future quantum computing advancements and to strengthen data security by incorporating post-quantum cryptography into their offerings.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
0 notes
Text
Decentralized Storage Network In Web3

In 2006, British mathematician Clive Humby famously said, "data is the new oil." This idea is even more relevant today, as our personal data is closely linked to our online experiences.
Our digital identities are currently typically kept in centralized systems. These systems are simple to use, but because users do not have complete control over their data, it is more dangerous for loss, privacy violations, and cyberattacks.
However, the emergence of Web3 is altering how we communicate online, and blockchain technology is a major factor in this change. Applications powered by Blockchain function independently of others, eliminating the need for dependable third parties and promoting a decentralized Internet where users have greater control over their personal information and online activities. Furthermore, rather than depending on a single centralized server, users can store and retrieve their data throughout a distributed network with Decentralized storage alternatives.
Understanding Decentralized Storage Networks
Decentralized storage networks distribute data across multiple nodes, often spread globally, rather than storing it in a single, centralized location. These networks use blockchain technology and P2P (peer-to-peer) protocols to ensure data integrity, security and accessibility.. Each node in the network contributes storage space, and in return, earns rewards, typically in the form of cryptocurrency.
How Does Decentralized Storage Work?
Decentralized storage works by spreading data across many different computers or nodes in a peer-to-peer (P2P) network, such as BitTorrent or the InterPlanetary File System (IPFS).
When you upload data to a decentralized storage system, it’s broken down into small pieces and distributed across multiple nodes in the network. When you need to retrieve your data, the network gathers these pieces from the various nodes and puts them back together for you to download.
Moreover, the data stored in a decentralized system is secure because it’s automatically encrypted using cryptographic hashing. This means the nodes storing the data can’t see or change it. Only users with the right private keys can access their data, ensuring that unauthorized people can’t get to it.
Types of DSN
1. Peer-to-Peer Networks-
Directly share files or make calls without central servers, like BitTorrent for downloads and Skype for calls.
2. Blockchain and Cryptocurrencies-
Public Blockchains- Open to everyone, like Bitcoin and Ethereum.
Private Blockchains- Restricted access for specific groups, like Hyperledger Fabric.
3. Decentralized Finance (DeFi)-
Exchanges- Trade cryptocurrencies directly with others, like Uniswap.
Lending/Borrowing- Borrow or lend without banks, using platforms like Aave.
4. Decentralized Autonomous Organizations (DAOs)-
Organizations run by code, where members vote on decisions, like MakerDAO.
5. Decentralized Apps and Identity-
dApps- Apps running on a blockchain, like the game CryptoKitties.
Decentralized Identity- Control your own digital ID, with projects like Sovrin.
6. Decentralized Storage and Marketplaces-
File Storage- Spread files across many computers for security, like IPFS.
Marketplaces- Buy and sell directly without middlemen, using platforms like OpenBazaar.
Centralized Vs Decentralized Storage
Centralized Storage-
Centralized storage refers to storing data in a single, central location, often managed by a single organization or entity. This is the traditional model used by most businesses and cloud storage providers.
Decentralized Storage-
Decentralized storage distributes data across multiple nodes or locations, often leveraging peer-to-peer networks and blockchain technology. Examples include IPFS (InterPlanetary File System) and blockchain-based storage solutions like Filecoin and Stor.

Challenges In Decentralized Storage Network
Security-
Ensuring strong encryption to protect data.
Trusting nodes not to tamper with or steal data.
Reliability-
Maintaining network uptime and data availability.
Ensuring sufficient data replication to prevent loss.
Performance-
Speeding up data retrieval, which can be slower than centralized systems.
Reducing network latency.
Economic Incentives-
Creating fair compensation models for storage providers.
Managing the volatility of cryptocurrency-based payments.
Legal Issues-
Complying with varying data storage laws across countries.
Determining responsibility for illegal content.
Usability-
Making the network user-friendly and easy to integrate.
Building trust and awareness among users.
Technical Problems-
Ensuring interoperability with other systems.
Developing secure and efficient consensus mechanisms.
Maintenance-
Coordinating decentralized upgrades and improvements.
Rapidly addressing security vulnerabilities and bugs.
Future Developments and Innovations
Smarter Consensus Mechanisms-
Researchers are creating new ways for systems to agree on data integrity that are more efficient and environmentally friendly, such as Proof of Stake (PoS) and Proof of Burn (PoB). These innovations aim to secure data without wasting resources.
AI Integration-
Artificial intelligence is being woven into decentralized storage networks, making data storage and retrieval smarter and faster.They improve security and privacy by giving consumers more control over their personal information.
Ongoing Blockchain Innovations-
New blockchain technologies with improved scalability, quicker transaction speeds, and more security are always being created. The usage of distributed storage is now more solidly supported by these developments.
Rise of Decentralized Identity-
As privacy concerns increase, more individuals and organizations are looking to Decentralized Identifiers (DIDs) and other decentralized identification solutions. They improve security and privacy by giving consumers more control over their personal information.
How does Nadcab Labs use decentralized storage networks to boost client profitability?
Nadcab Labs uses decentralized storage networks to improve its blockchain services. By distributing data across multiple nodes, they make it difficult for hackers to secure information. This arrangement also allows businesses to grow without expensive infrastructure upgrades. It also reduces costs by reducing the need for central data centers. Overall, this approach helps Nadcab Labs customers become more efficient and profitable by providing a combination of security, scalability and savings that benefit multiple industries.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
0 notes
Text
The Rise of the Data Availability Layer

Data Availability Layer (DAL), your data's best friend in the digital world. It functions similarly to a personal assistant, ensuring that information is prepared and organized for you whenever you need it. Consider it the unsung hero that worked away in the background to make sure your data is dependable, safe, and accessible. In this introduction, we look at how DAL makes your data journey easier so you can make better decisions and find your way around the data landscape's complicated terrain with ease.
What are Data Availability Layers?
Data Availability Layers ensure that your data is always ready when you need it, much like a support system. The Replication and Distribution Layer makes sure backups are ready, the Storage Layer safeguards your data, the Access Layer makes it easier to find, the Caching Layer keeps frequently used data accessible quickly, and The synchronization process Layer keeps everything in sync. They work together to guarantee that you can always access your data.
What is the significance of Data Availability Layers?
Abstraction of Data Sources-With only a single button, you may access all the data you require, regardless of its format or location, akin to a universal remote control for data.
Data Consistency-Consider data consistency as your friendly neighborhood library ensures that all book borrowers receive the most recent edition, even when multiple individuals request it at the same time.
Scalability- Imagine that your favorite restaurant suddenly becomes very popular. The data availability layer helps it scale smoothly and accommodate more customers without losing its charm.
Fault tolerance- It's like a backup generator for your data - even if the power goes out, you'll still have uninterrupted access to everything you need.
Performance optimization- Think of it as a personal assistant that knows exactly where to find it and makes sure you get what you want quickly and efficiently.
Security and Access Control- Think of it as a trusted guardian for your data, letting only the people you want in while keeping intruders out.
Interoperability- Imagine being able to seamlessly switch between different devices or apps without getting stuck. The data availability layer helps achieve this by making sure everything flows smoothly, like a well-choreographed dance.
What are the essential components of Data Availability Layers, and how do they enhance data accessibility and reliability?
Data storage-
It acts as a safe place for all your important documents.
Data Replication-
Consider making copies and storing them in a safe place with data backup and document backup.
Data Integration-
Integrating data is like putting neat folders on a messy desktop.
Data Access Layer-
Display a helpful assistant who knows all the locations of a large library.
Data Security and Governance-
Security and data management can be compared to locking your windows and doors to keep your house safe.
Data Quality Management-
Think of data quality management as spring cleaning your data to ensure all data is correct and reliable.
What steps are involved in the implementation of Data Availability Layers?
Gather Requirements- Talk to everyone who will use the data to understand what they need.To keep everyone on the same page, put your goals in writing.
Plan Data Structure- Decide how you’ll organize and store the data. Choose the best format (database, blockchain, etc.) for your needs.
Select Technologies- Pick the software and tools that will support your data storage and management, ensuring they can scale with your needs.
Backup Strategy- Plan how to create and store backups of your data to prevent loss, considering local and cloud options.
Set Up Distribution- Implement a system to distribute data efficiently across your network, ensuring speed and reliability.
Implement Consensus- Use methods to keep all copies of your data in sync across different locations, ensuring consistency.
Check Data Integrity- Implement checks to ensure your data is available and hasn’t been tampered with, using techniques like cryptographic proofs.
Implement Security- Encrypt your data and set up strong access controls. Conduct regular security audits to find and fix vulnerabilities.
Ongoing Monitoring- Use tools to continuously monitor data performance and availability. Schedule regular updates and maintenance.
Launch and Train- Deploy your system with a clear plan for data migration and minimal downtime. To guarantee a smooth transition, give users support and training.
What challenges do Data Availability Layers face?
Scalability
Data Volume-Properly handling and storing huge amounts of data.
Throughput-The ability to process data requests quickly and continuously without stuttering.
Security
Data Integrity-Making certain that data is not altered.
Security-Securing confidential data, similar to setting up exclusive, protected spaces for priceless documents.
Latency
Data Acquisition- Ensuring that you can obtain the necessary info quickly.
Transmission- Ensuring that data modifications are immediately reflected
everywhere, similar to updating all catalogs as soon as a new book is received.
Redundancy and Replication
Cost-It is costly to store extra copies.
Consistency-the same way it's important to make sure every library branch has the most recent edition of a book, all copies must be current
Fault Tolerance
Resilience-Preserving system functionality in the face of technological difficulties.
Recovery-Recovering from errors fast to prevent data loss, similar to recovering a library's collection following a natural disaster.
Network Bandwidth
Capacity-Ensuring that every data transaction has adequate bandwidth.
Congestion-Managing network traffic to prevent lags.
Economic Incentives
Incentive Structures-Putting in place just and inspiring incentive programs for individuals who contribute to keeping data accessible.
Regulatory Compliance
Auditability-Transparent record-keeping to demonstrate data processing procedures, akin to keeping an exhaustive record of all books checked out.
Data Sovereignty-Following regulations regarding the storage and transit of data
Interoperability
Standards-Ensuring the seamless integration of various systems.
Integration-Likened to the addition of a new wing to an ancient library, blending in seamlessly with the current infrastructure.
User Adoption
Ease of Use-To make the data easy to obtain and utilize, the system is user-friendly.
Education-Informing users about the advantages and constraints of DALs, akin to orientation programs at libraries.
What is the future of Data Availability Layers in blockchain and beyond?
There are exciting new layers of data availability (DA) in blockchain that we can expect. They improve scalability through pooling and sharing, improve cross-chain communication and standardize protocols to ensure seamless interoperability.
DA layers are integrated into distributed storage solutions to enhance data security and integrity. Financial incentives encourage participation, which can lead to a decentralized market for data services.
DA layers also integrate with traditional IT systems and attract businesses by connecting blockchain to existing infrastructure. Improved privacy through zero-data truth and better user interfaces make DA layers more accessible, encouraging wider adoption and innovation.
How do Data Availability Layers contribute to the scalability of blockchain networks?
Data Availability Layers (DAL) greatly improve the scalability of blockchain networks by separating data storage and consensus mechanisms, separating these functions into consensus nodes that can confirm and agree transactions without large amounts of data. This is the main advantage of the distributed architecture of distributed algorithms. They achieve efficient transmission of data using techniques such as sharding and distributed storage protocol, distributing data across several nodes or sections to reduce the bandwidth and storage requirements of individual nodes.
In addition, DAL enables parallel processing of transactions, which increases network performance by allowing simultaneous processing on different patches or partitions. Some DALs even include dynamic tuning mechanisms that adapt data to network conditions and maintain optimal performance under varying workloads. In addition, DALs improve fault tolerance by replicating data across multiple nodes, ensuring network resiliency in the event of a failure. These strategies enable DAL networks to play an important role in enabling blockchain networks to scale efficiently to meet increasing transaction volumes and user needs while maintaining decentralization and security.
What role does Nadcab Labs play in developing data availability layers for blockchain networks?
Nadcab Labs is essential in making Blockchain networks more reliable and efficient by developing smart ways to ensure data is always available. They create custom solutions that keep data safe and accessible, even in decentralized systems. By integrating these solutions into existing platforms, they enhance performance and security. Nadcab Labs also makes sure data is backed up to protect against failures and attacks. They offer advice and support to help clients implement these data availability layers effectively. With ongoing research and dedicated assistance, Nadcab Labs helps blockchain projects run smoothly and securely, ensuring data is always at your fingertips.
Author Profile: Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Role of Verifiable Random Functions in Cryptographic Systems

5 Key Takeaways in Simple Terms:
Consistent Results: Same input, same secret key, same output every time.
Easy to Verify: Anyone can check the result is correct without knowing the secret key.
Secure: Hard to find two different inputs that give the same output.
Blockchain Essential: Used in blockchains for fair and secure processes like choosing leaders.
Privacy Boost: Helps keep things private and secure in various digital protocols.
Introduction
Verifiable Random Functions (VRFs) are the eyes and ears of contemporary encryption, combining integrity checking with selection. VRFs generate outputs that approximate random numbers, compared to conventional techniques, but they have one unique advantage: they can demonstrate the accuracy of their results without disclosing their exclusive technology. Particularly in critical cryptographic activities like verifying digital signatures are authentic, ensuring consistency on Blockchain changes, and safeguarding confidential data when numerous parties are involved, this unique capability fosters trust and transparency. VRFs are crucial for maintaining the security of our digital world because they are like the superheroes of security, perfectly fusing proof and randomness. In this blog, We will explore how VRF systems impact our society.
What is the fundamental principle behind the functioning of VRF?
Verifiable Random Function (VRF) like a special machine you have. You put in a secret key and a number, and out pops a seemingly random result. The best thing is that you don't need to reveal your secret key to anyone else in order to demonstrate to them that the outcome originated from your computer.
Imagine you have this magical device that takes in a special key and a number, and out comes what looks like a random output. The tricky part is that you can demonstrate to others that this output is genuine without disclosing your trade secret. The magic of VRFs is that! They give you random-looking results that you can prove came from you, without revealing your secret key to anyone else. It's like having your own personal random number generator, but with built-in proof of authenticity!
What methods were used before VRFs for generating and verifying randomness, and how do they compare in efficiency and verifiability?
Before Verifiable Random Functions (VRFs) became a widely adopted method for generating and verifying randomness, several other methods were commonly used. These methods are:
True Random Number Generators (TRNGs):Electronic noise and radioactive decay are two examples of unpredictable physical processes that are used by True Random Number Generators (TRNGs) to generate random values. Their actual randomness stems from this, but because they rely on these physical processes, they may be slower. Although TRNGs can be tested for randomness, independent confirmation is difficult because there is no method to ensure that their output hasn't been altered.
Pseudo-Random Number Generators (PRNGs):Pseudo-Random Number Generators (PPseudo-Random Number Generators (PRNGs) generate reportedly random numbers using algorithms. Examples include the Linear Congruential Generator (LCG) and the Mersenne Twister. Starting from a single seed value, these algorithms can quickly produce large amounts of random-like data. However, since PRNGs are deterministic, anyone who knows the seed can predict the output. For applications that require great security and unpredictability, this renders them less appropriate. Moreover, PRNGs don’t have built-in ways to verify their randomness.
Cryptographic Random Number Generators (CSPRNGs):CSPRNGs, or cryptographic random number generators, are a unique kind of PRNG developed for use in cryptography. To ensure that their outputs are unpredictable, they employ secure algorithms such as Fortuna or those based on AES or SHA. Because of the intricate cryptographic effort required, CSPRNGs are typically slower than standard PRNGs, although being more safe. Even with security, it is still impossible to objectively confirm that CSPRNGs' randomness hasn't been manipulated.
Commitment Schemes:Picture a commitment scheme as sealing a surprise gift in a box before sending it. You keep the contents hidden until it's opened, along with proof it's what you sealed. It's like putting the finishing touch on the surprise to make sure it stays flawless until it's revealed!
Comparison with VRFs(Verifiable Random Functions)-:
VRFs like your secret recipe for baking the perfect chocolate chip cookies. They whip up random values and prove they're the real deal without giving away your special ingredients. It's like baking a batch of cookies that everyone can trust without seeing your secret recipe card!
And the best part? They are safe and speedy, similar to making cookies quickly without sacrificing flavor. So whether you're whipping up treats for your friends or securing data in a blockchain, VRFs are the trusty tool in your kitchen (or code) drawer. They are the best combination for openness and confidence in the age of digital technology.
How do VRFs benefit applications and what are some key scenarios where their algorithmic implementation proves valuable?
Cryptographic primitives known as Verifiable Random Functions (VRFs) generate an output that is pseudo-random and verifiable by anybody. VRFs are quite useful for many applications because of this special feature, especially where both randomness and reliability are required.
Benefits of VRFs
Randomness with Proof of Authenticity:Ensures authenticity and guards against manipulation by generating random outputs with proofs.
Deterministic and Consistent:Predictable verification is ensured because the same input and key consistently yield the same output.
Privacy:conceals the private key to protect the identity of the source of the randomness.
Non-interactive Verification:makes it possible for anybody to confirm outputs without contacting the generator.
Key Scenarios for VRFs
1. Blockchain and Cryptocurrencies:-
Consensus Algorithms: These algorithms, such as Algorand, are used in Proof-of-Stake (PoS) to safely and arbitrarily choose validators.
Lottery systems: Provide impartial and sustainable means of selecting winners in decentralized lotteries.
2. Multi-party secure computation (SMPC):-
Generates random values that are accepted and confirmed by several people without disclosing personal information.
3. DNS Protection:-
Offers verified non-existence proofs and authenticated denial of existence, blocking DNS zone enumeration.
4. Haphazard beacons
Generates random numbers that may be independently verified by the public for uses in election auditing and lotteries.
5. Verification and Permission:
Increases security by creating one-time passwords or tokens that may be independently validated.
6. Digital Certificates and Signatures:
Ensures tamper-proof procedures by adding randomness and verifiability to the issue of digital certificates.
7. Unpredictability in Protocols:
Gives safe and verifiable randomness for cryptographic protocol operations like challenge creation and key generation.
What security risks do Verifiable Random Functions (VRFs) pose, and how can they be managed for safe cryptographic operations?
Key Security: Use safe key management procedures to keep the private key secret.
Algorithmic Vulnerabilities: Select VRF structures that rely on proven cryptographic primitives and thoroughly examine them.
Implementation Vulnerabilities: To prevent implementation errors, adhere to safe software development best practices.
Cryptological Premises: Update cryptographic primitives frequently in light of new findings to reduce risks associated with innovations.
Misuse or Misapplication: To prevent security vulnerabilities, employ VRFs in accordance with recognized recommendations and best practices.
It's critical to stick to established cryptographic standards, use carefully considered and applied algorithms, use secure key management procedures, keep up to date on the most recent advancements in cryptography, and update cryptographic software and libraries on a regular basis in order to mitigate these risks and guarantee safe cryptographic operations with VRFs. In-depth security audits and assessments of VRF implementations can also be helpful in locating and addressing such issues.
What ways could future improvements in VRF technology better protect people's online security and privacy?
Separate Party Zones: Through VRF, the internet is divided into distinct "party rooms," preventing any one group from bothering the others if they become too rowdy.
Sharp Security Checks: VRF's filters, akin to watchful bouncers, spot troublemakers attempting to enter the party covertly, ensuring everyone has a safe and enjoyable time.
Instant Space Adjustment: VRF provides more space without compromising security by expanding like magic walls when more visitors come.
Automatic Backup: VRF leaps in anytime there's an issue, taking care of problems before you even realize. They act as unseen workers.
Secret Messages: Virtual Rewrite Framework (VRF) lets you keep online chats secret by limiting who can read them to the intended recipient. It works similarly to a locked note.
Exclusive Access: To help you unwind without worrying about outsiders, VRF puts up VIP zones online that are only accessible to trusted pals.
How does Nadcab Labs leverage Verifiable Random Functions to operate effectively?
Verifiable Random Functions (VRFs) are a sophisticated cryptographic mechanism that Nadcab Labs uses to add a little bit of unpredictability to our operations while maintaining transparency and fairness. Consider it our method of rolling the dice in a safe online setting! VRFs are essential for choosing validators in blockchain networks, selecting winners in lotteries and auctions, and even allocating workloads equitably in decentralized apps. They guarantee that, similar to tossing a coin but with an extra layer of cryptographic magic, all parties involved can have faith in the randomness of the result. By incorporating VRFs into our operations, we're not merely introducing randomness.
Conclusion
Verifiable Random Functions (VRFs) guarantee that unpredictability in digital processes is genuine and verifiable, much like the reliable magic of a fair game. VRFs are the virtual dice roll that makes things entertaining but fair here at Nadcab Labs. By using VRFs in our operations, we're doing more than just mixing in some randomness—we're laying the groundwork for openness and trust. VRFs enable us to traverse the digital world with integrity and dependability, ensuring that all parties involved feel confident and valued in their interactions with us. These applications range from Blockchain networks to auctions and decentralized apps.
Author Profile:
Nadcab Labs — A Leading Blockchain developer with over 8+ years of experience in, Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation, and Many More Services.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Interconnecting Ledger Systems - The Power of Cross-Chain Bridges

5 Key Takeaways in Simple Terms:
Linking Blockchains: Connects different digital worlds.
Easy Asset Swapping: Move your digital stuff between places effortlessly.
Blockchain Teamwork: Groups work together for shared goals.
Mixing Tech Skills: Combine talents for new ideas.
Friendly Tech Space: Make technology accessible and welcoming for everyone.
Lead
As Distributed Ledger technology has developed, so too has the significance of smooth interoperability across many platforms grown. Cross-Chain Bridges and Interoperability Protocols, which function as bridges between various systems, satisfy this need. With the help of interchain bridges, users can access a range of services and connect various systems by facilitating the easy transfer of tokens and information between blockchains. On the other hand, more complex decentralized apps (dApps) can be developed thanks to interoperability standards, which set the guidelines for dependable and secure interactions across multiple systems.
These innovations provide significant advantages to consumers, such as enhanced liquidity and increased adaptability. However, they also come with disadvantages, like vulnerabilities in security and the challenge of achieving uniformity across numerous Blockchain Platforms. Developing strong protocols for interoperability and bridges between different chains will be crucial as the blockchain sector expands. The forthcoming phase of expansion in the decentralized realm will be powered by these developments and fresh prospects.
What are cross-chain bridges and how do they connect blockchains?
Cross-chain bridges, which enable communication between several blockchain networks, are essential parts of the blockchain ecosystem. By acting as connectors between several blockchains, these bridges ease the flow of resources and data.Here’s how It operates:-
Token Locking: Consider the scenario where you wish to use tokens that are on Blockchain A on Blockchain B. These tokens are locked in a safe smart contract on Blockchain A to start the transfer.
Confirmation Process: The bridge verifies the transaction to avert any possible problems and makes sure your tokens are securely locked on Blockchain A.
Token Representation: On Blockchain B, an equal number of tokens are created following confirmation. You can now utilize these new tokens on Blockchain B, as they now represent the ones you locked on Blockchain A.
Bi-Directional Flow (Optional): Tokens can travel back and forth between the linked blockchains thanks to certain bridges, which gives consumers greater usage and flexibility.
Decentralized Verification: Cross-chain bridges frequently use decentralized verification techniques, such oracles, to verify transactions and provide transparency all along the way, all while preserving trust and security.
In order to facilitate the efficient and rapid flow of data and assets between decentralized ecosystems, cross-chain bridges guarantee interoperability between different blockchain networks.
How do interoperability protocols facilitate Distributed Ledger technology connectivity?
Protocols for interoperability are essential to creating a smooth connection between various blockchain networks. They act as the vital link that connects various networks, facilitating effective interaction and communication.
uniformity of data formats and communication protocols.
cross-chain transaction optimization.
Consensus strategies are put into practice for communication that lacks trust.
Using middleware or bridge entities to provide easy interoperability.
What security measures ensure the credibility of cross-chain transactions?
Hash Time-Locked Contracts (HTLCs) allow for direct peer-to-peer cryptocurrency transactions between multiple blockchains without the need for middlemen, guaranteeing that the transaction is completed by both parties or none at all.
Enable precise cross-chain state verification by enabling one blockchain to verify the state of another blockchain using complete relay nodes or Simplified Payment Verification (SPV) proofs.
Establish a sidechain that is linked to the primary blockchain in order to facilitate asset transfers that are protected by a two-way peg system that upholds a 1:1 asset backing.
Transferring assets between chains should be managed and secured by a group of reliable parties, and transactions should only be approved by numerous federation members’ signatures.
Strong consensus mechanisms enable standardized, safe communication between blockchains using frameworks like Polkadot’s relay chain model and Cosmos’s Inter-Blockchain Communication (IBC) protocol.
Smart contracts used in inter-chain transactions should undergo thorough audits by reputable companies to ensure the security and functionality of the code, identify any bugs, and correct them.
By combining data from several sources, decentralized oracles can be used to deliver accurate and impenetrable off-chain data to smart contracts, facilitating cross-chain transactions.
Since many private keys are required to approve a transaction, there is less chance of theft or fraud because no one individual can control the transaction.
Here are some examples of cross-chain bridge implementations?
Wrapped Bitcoin (WBTC)
What it does: By transforming Bitcoin into an Ethereum-compatible token, WBTC enables you to use Bitcoin within the Ethereum environment.
How it works: A custodian receives your Bitcoin and uses it to create an equivalent quantity of WBTC on Ethereum. It is comparable to exchanging cash for traveler’s checks that are accepted abroad.
2. Polygon Bridge
What it does: This bridge makes it easier to move assets between Ethereum and Polygon, enabling quicker and less expensive transactions.
How it works:On Ethereum, tokens are locked, while on Polygon, corresponding tokens are created. It is comparable to transferring money from a high-interest savings account to your primary bank account.
3. Binance Bridge
What it does:Asset transfers between Ethereum and Binance Smart Chain (BSC) are made possible via Binance Bridge.
How it works: You can use tokens on another blockchain since they are wrapped. Consider it as utilizing an adapter to enable your gadget to work with a different type of outlet.
4. Thorchain
What it does: Thorchain eliminates the requirement for wrapped tokens by enabling direct exchanges across various blockchains.
How it works:It functions similarly to a currency exchange counter at an airport, allowing you to exchange currencies right away.
5. RenVM
What it does: RenVM makes it easier to move assets like Zcash and Bitcoin to Ethereum.
How it works:Equivalent tokens are minted on Ethereum, while the original assets are secured in a vault. It’s similar to getting a certificate to trade and keeping your gold in a safe vault.
6. Polkadot Bridge
What it does: Polkadot and other Distributed Ledger technology, such as Ethereum and Bitcoin, are connected using Polkadot bridges.
How it works: secures the movement of data and tokens using a messaging system. It functions similarly to safely emailing crucial papers to a different network.
7. Cosmos IBC (Inter-Blockchain Communication)
What it does: Several blockchains can easily exchange tokens and connect with one another because to Cosmos IBC.
How it works: It’s similar to having many messaging apps that, independent of the app, can now communicate with one another.
8. Celer cBridge
What it does: The quick and affordable method of transferring tokens between different blockchains is provided by Celer cBridge.
How it works: Utilizes the use of a fast network to provide efficient and timely token transfers. It’s similar to traveling to your destination by bullet train as opposed to standard train.
How do interoperability protocols address scalability issues in blockchain networks?
Eliminating scalability problems in blockchain networks requires interoperability protocols. They make it possible for many blockchains to interact and exchange data, which helps to divide up the labor, increase throughput, and boost these systems’ general effectiveness. Interoperability protocols ease the scalability issues that frequently strike single blockchain networks by enabling blockchains to cooperate, exchange resources, and utilize network capacity more effectively.
Key ways:-
One way to balance the load and lessen stress on any one network is to shift transactions from busy blockchains to less crowded ones.
The transaction throughput of these protocols is increased by using state channels and sidechains, which execute transactions off-chain before settling them on the main chain.
Transactions between separate blockchains can be completed by users, which diversifies the burden and improves resource efficiency.
Resource Sharing: By pooling resources such as computing power and storage, linked blockchains are able to handle a greater volume of data and transactions.
Task distribution made possible by smart contracts working across different blockchains can expedite processing and eliminate bottlenecks.
What are the main risks associated with cross-chain bridges and interoperability protocols?
Security Exposure: Risks of bugs or weaknesses that could be exploited for theft or disruption.
Smart Contract Risks: Sensitivity in smart contracts used for transfers.
Centralization: Potential central points of failure undermining decentralization.
Liquidity Risks: Issues if there’s low demand for asset transfers.
Protocol Risks: Weaknesses in the interoperability protocols themselves.
Regulatory Risks: Compliance challenges across different jurisdictions.
Chain Reorganization: Potential impact of blockchain forks or reorganizations.
User Error: Mistakes in usage leading to fund loss.
How might cross-chain bridges and interoperability protocols evolve in the future?
Improve defenses against cyberattacks by strengthening defenses, carrying out frequent audits, and putting revolutionary encryption methods in place to protect assets and transactions.
Enhance non-technical users’ navigation and utilization of cross-chain bridges and interoperability protocols by streamlining interface designs, giving clear instructions, and adding intuitive features.
Preserve the decentralized character of blockchain technology by reducing dependence on central hubs or points of control, guaranteeing that governance frameworks and decision-making procedures continue to be shared among network users.
In order to handle the growing demand for cross-chain transactions, address scalability issues by improving network efficiency, optimizing transaction throughput, and investigating creative scaling methods like sharding, sidechains, or layer 2 protocols.
Enable the transfer of a wide range of digital assets outside of cryptocurrencies, such as non-fungible tokens (NFTs), digital securities, real assets, and even data, to increase the use and adaptability of cross-chain bridges and interoperability protocols.
Establish connections between blockchain and traditional systems to provide better technology synergy and integration. Interoperability with legacy banking infrastructure, supply chain networks, identity management systems, and other industries will be made possible by this.
Incorporate technologies that enhance privacy, such as secure multi-party computation or zero-knowledge proofs, to maintain confidentiality and boost confidence in cross-chain transactions. Put user privacy and data protection first while making sure all applicable laws and regulatory frameworks are followed.
How does Nadcab Labs utilize Inter-chain Bridges and Interoperability Protocols to connect blockchains?
Nadcab Labs creates effortless interactions between different blockchains by utilizing interoperability standards and Cross-Chain Bridges. They facilitate the seamless exchange of assets and data between various blockchain networks by utilizing these mechanisms. Nadcab Labs prioritizes risk mitigation strategies to guarantee the security and dependability of these connections, whether through in-house development of solutions or integration of pre-existing ones. Their dedication to interoperability creates a world of opportunities for their blockchain applications, encouraging creativity and increasing the use of Blockchain Technology in a variety of ecosystems.
Conclusion
Cross-chain bridges and interoperability protocols serve as bridges between various blockchains in the framework of decentralized networks. They function as freeways for value and information between various chains, much like digital highways. By making this smooth connection possible, they create countless chances for invention and cooperation, advancing the possibility of a time when Distributed Ledger technology functions as a single, cohesive system.
Author Profile:
Nadcab Labs — A Leading Blockchain developer with over 8+ years of experience in, Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation, and Many More Services.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
#blockchain technology#Cross-Chain Bridges#Interoperability Protocoals#nadcablabs#nadcab labs services#blockchain
0 notes
Text
Innovate, Adapt, Transform - Modular Blockchains and the Ever Evolving Tech Trends

5 Key Takeaways in Simple Terms:
Better Performance and Flexibility: Modular blockchains split the system into parts that can be easily upgraded and optimized, making them faster and more adaptable.
Transparent Supply Chains: They help track products in real-time, ensuring accurate, tamper-proof records and improving trust and compliance in supply chains.
Solving Old Problems: Modular blockchains fix issues found in older, monolithic blockchains, like slow speeds and difficulty in making updates.
Impact on Industries: Various sectors, such as finance, healthcare, and retail, are benefiting from modular blockchains by gaining better security, efficiency, and transparency.
Enhanced Security: Nadcab Labs uses modular blockchains to boost security, ensuring data stays safe, private, and protected from cyber threats.
Prefaces
Modular blockchain technology is an advancement in distributed systems. Scalability, flexibility and efficiency are greatly increased by this novel technique, which disassembles the conventional monolithic design into discrete, interchangeable modules. Specific customisation is possible with modular blockchains, as individual optimization and upgrades are possible for components like execution layers, consensus, and data availability. This paradigm change not only solves the shortcomings of current blockchain systems but also opens the door for more resilient, flexible and long-lasting decentralized applications. Modularity is expected to play a major role in propelling future developments and broad acceptance of blockchain technology as it continues to change.
Modular Blockchain - An Introduction?
A revolutionary development in distributed systems, modular blockchain technology presents a novel approach to blockchain design. This innovative architecture greatly improves scalability, flexibility, and efficiency by segmenting the blockchain into discrete, swappable modules.Specialized customization and enhanced performance are possible due to the independent optimization and upgrading of each module, including the execution layer, data availability, and consensus mechanism.
This modularity addresses many of the limitations inherent in traditional blockchains, such as scalability issues and upgrade difficulties, by enabling targeted enhancements without disrupting the entire system. As a result, modular blockchains pave the way for more robust, adaptable, and sustainable decentralized applications. This evolution not only fosters innovation and development within the blockchain ecosystem but also positions modularity as a key driver for future advancements and widespread adoption, ultimately leading to more versatile and efficient distributed system.
How Does Modular Blockchain Make Supply Chains More Transparent?
Modular Blockchain Technology offers a decentralized, immutable database for tracking all transactions and movements of commodities, greatly improving supply chain transparency. Real-time tracking and verification are made possible by this technology, guaranteeing that all stakeholders have access to current and correct information. Modular blockchains provide flexibility and scalability by combining multiple, specially designed modules, enhancing dependability and efficiency across the supply chain. Stakeholder trust is boosted as a result, fraud is decreased, and regulatory norms are better followed.
Real-Time Tracking: Modular blockchain allows for the continuous and real-time monitoring of goods at every stage, ensuring accurate and timely updates for all stakeholders.
Immutable Records: Each transaction and movement is recorded on an unchangeable ledger, preventing tampering and ensuring the authenticity and integrity of the data.
Enhanced Integration: Companies can customize and integrate different blockchain modules to address specific needs, improving overall supply chain management and efficiency.
Increased Trust and Compliance: Transparent and verifiable records help build trust among stakeholders and ensure adherence to regulatory requirements, reducing the risk of fraud and errors.
What is a Monolithic Blockchain and What are its Drawbacks?
Monolithic blockchains existed before the advent of modular blockchains.Blockchain architectures that combine consensus, data availability, execution, networking, and other features into a single, cohesive framework are known as monolithic blockchains. Because of the conventional architecture, each network node handles every function, resulting in a rigid but well-functioning system.
Drawbacks of Monolithic Blockchains:
Scalability Issues:
As the blockchain grows, the workload for each node increases, leading to slower transaction processing and higher latency.
Limited capacity to handle a large number of transactions simultaneously.
Resource Intensive:
Nodes need significant computational power and storage to process and store all transactions and blockchain data.
Higher costs for maintaining and running nodes.
Upgrade Complexity:
Implementing changes or upgrades is challenging because modifications affect the entire system.
Risks of network forks if not all nodes adopt the upgrade simultaneously.
Limited Flexibility:
Monolithic design lacks the flexibility to optimize individual components, such as consensus or execution layers, independently.
Difficult to adapt to new requirements or integrate new technologies.
Single Point of Bottleneck:
Performance is limited by the capabilities of the most resource-constrained nodes, creating bottlenecks.
Network speed and efficiency depend on the slowest nodes.
Security Concerns:
A single unified structure means vulnerabilities in one component can compromise the entire system.
Greater risk if a significant portion of the network is controlled by malicious actors.
Inefficient Resource Utilization:
All nodes must perform every task, leading to redundant efforts and inefficient use of resources.
No specialization or division of labor among nodes, which could otherwise enhance efficiency.
Comparing Modular and monolithic in Blockchain?
Pros and Cons of Modular Blockchain Technology ?
Pros-
Each component may expand on its own, the system can handle rising demand without becoming overloaded.
It is possible to upgrade or change individual components without affecting the network as a whole, providing flexibility in response to evolving needs.
Specialized modules improve overall performance by streamlining procedures and maximizing resource utilization.
Isolating vulnerabilities, segmented architecture reduces the effect of possible breaches and increases the resilience of the system.
Each module has independent updates and maintenance, which makes management easier and minimizes downtime and operational interruptions.
Cons-
Interconnected modules may be dependent on one another, careful supervision is required to ensure smooth operation.
Interoperability problems and compatibility concerns might arise when integrating several modules from various sources.
Compared to monolithic architectures, designing and implementing modular systems requires more time, money, and experience.
Adoption and deployment may be delayed if users and developers need more time to become acquainted with the nuances of modular blockchain systems.
Managing multiple modules adds complexity, requiring meticulous coordination and oversight.
How Modular Blockchain Technology is Shaping Global Industries?
Modular Blockchain technology is not just transforming industries; it's changing the way we interact with the world around us. Imagine knowing exactly where your favorite shirt was made, how it got to the store, and whether it's genuine—all with a simple scan of a tag. That's the power of modular blockchains in Supply Chain Management, bringing transparency and trust to every step of the process. And it's not just about buying clothes; it's about feeling confident that the medicine you take is safe, your energy comes from sustainable sources, and your vote is counted accurately.
Industries are:-
Finance and Banking:
Enhancing transaction security, reducing fraud, and enabling faster cross-border payments.
Supply Chain and Logistics:
Improving transparency, tracking goods in real-time, and ensuring authenticity and quality control.
Healthcare:
Securing patient data, streamlining medical record management, and enhancing drug traceability.
Real Estate:
Facilitating smart contracts for property transactions and improving transparency in property records.
Energy:
Enabling peer-to-peer energy trading and enhancing the efficiency of energy distribution networks.
Telecommunications:
Securing data transmissions and improving the efficiency of billing and identity verification processes.
Retail and E-commerce:
Ensuring product authenticity, streamlining supply chains, and enhancing customer loyalty programs.
Entertainment and Media:
Protecting intellectual property rights and enabling transparent royalty distribution.
Government and Public Services:
Securing voting systems, improving identity management, and enhancing transparency in public records.
Insurance:
Automating claims processing and improving risk assessment and fraud detection.
Agriculture:
Enhancing traceability of food products and improving supply chain efficiency.
Education:
Securing academic records and enabling the verification of credentials and certifications.
How Does Nadcab Labs Enhance Security with Modular Blockchain Technology?
Modular blockchain technology is used by Nadcab Labs to strengthen security protocols in a variety of domains. Nadcab Labs protects data integrity, confidentiality, and resilience against cyber attacks by utilizing immutable ledgers, decentralization, encryption, and smart contracts. Frequent penetration tests and audits reinforce security protocols even further, and total defense measures are strengthened by interoperability with the current infrastructure.
Immutable ledgers safeguard data integrity, providing a tamper-proof audit trail of transactions.
Decentralization reduces the risk of single points of failure, enhancing resilience against malicious attacks.
Encryption, smart contracts, and access controls enforce stringent security measures, ensuring only authorized access to sensitive data and functionalities.
Summary
As the scalability equivalent of superheroes, modular blockchains achieve the ideal balance between security and expansion. Think of them as the designers of a futuristic metropolis, where each structure is customized to satisfy the specific requirements of its people. Starting new projects using modular blockchains is as simple as creating a masterpiece, with every brushstroke well planned. This degree of adaptability is a monument to human creativity and inventiveness rather than merely a convenience. As we move forward, let's embrace modular blockchains as partners in our pursuit of advancement rather than merely as tools, opening doors to a world where the possibilities are genuinely endless and the imagination has no boundaries.
Author Profile:
Nadcab Labs — A Leading Blockchain developer with over 8+ years of experience in, Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation, and Many More Services.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
#blockchain#nadcablabs#nadcab labs services#blockchain technology#Modular Blockchain#Modular Blockchain Technology
0 notes
Text
zk-Rollups - How They are Changing Layer 2 Solutions

Key Takeaways
What are zk-Rollups?
zk-Rollups help blockchain handle more transactions by bundling them together off-chain and proving their validity with a special math trick called zero-knowledge proofs. This reduces costs and speeds up transactions.
Advantages and Challenges
Advantages: They make blockchain faster and cheaper by doing more work off the main chain.
Challenges: They're complex to set up and need good data handling to work well.
Comparison with Other Solutions
zk-Rollups are different from state channels and sidechains because they focus on proving many transactions at once, rather than keeping a channel open or running a separate chain.
Nadcab Labs' Role
Nadcab Labs helps improve zk-Rollups by researching, developing tools, and making them safer for everyone to use.
Future Impact
zk-Rollups could change how we use blockchain by making it faster and cheaper. This could lead to more apps and services using blockchain technology.
Lead-In
zk-Rollups are a key invention that could revolutionize Layer 2 scaling in the growing ecosystem of blockchain scalability solutions. By fusing the strength of roll-up technology with the efficiency of zero-knowledge proofs, zk-Rollups presents a viable solution to the current scalability trilemma that blockchain networks face, balancing throughput, security, and decentralization. This game-changing technology is essential to the development of future decentralized applications (dApps) since it not only lowers costs and increases transaction throughput while preserving the trustless nature of blockchain networks. An important turning point in the continuous development of blockchain technology is reached as we learn more about the nuances of zk-Rollups and how they affect the scalability of the blockchain.
What Exactly Are zk-Rollups and How Do They Work?
The zk-Rollups technique is a revolutionary way to execute more transactions on blockchain networks like Ethereum. Instead of processing each transaction individually on the blockchain, zk-Rollups combine multiple transactions off-chain and generate a cryptographic confirmation of their authenticity. Subsequently, this proof is posted on the blockchain, reducing the amount of data and processing power required on the main chain.
How Do They Work?
Transaction Aggregation: Multiple transactions are gathered and processed off-chain.
Proof Generation: A zero-knowledge proof (a type of cryptographic proof) is created to verify that these transactions are correct.
On-Chain Verification: This proof is submitted to the main blockchain (like Ethereum) and verified, ensuring the transactions are valid without processing them all on-chain.
What Are the Downsides and Challenges of Using zk-Rollups?
Technical Complexities
Complex Implementation: Requires advanced cryptographic knowledge.
Resource-Intensive: High computational costs for generating zero-knowledge proofs.
Data Availability Issues
Dependency on Off-Chain Data: Verification issues if off-chain data is unavailable.
Ongoing Solutions: Data availability proofs and committees still in development.
Maturity
Lack of Robustness: Still a relatively new and evolving technology.
Adoption Challenges: Slower adoption compared to more established Layer 2 solutions.
Interoperability
Compatibility Issues: Challenges in achieving seamless interaction with other Layer 2 solutions.
Standardization Needs: Efforts required to standardize protocols and interfaces.
User Trust
Building Confidence: Requires extensive testing, auditing, and transparency.
Steps for Trust: Regular audits, real-world testing, and open communication with the community.
How do zk-rollups help blockchain technology and make transactions faster by being a layer 2 solution?
As a layer 2 solution, zk-rollups improve blockchain technology's scalability by batching several transactions into one smaller transaction that is subsequently validated on the Ethereum mainnet. By drastically lowering transaction costs and expediting processing times, this method improves the effectiveness and economics of blockchain applications.
Transaction Offloading: Transactions are conducted off-chain and only summary data or proofs are posted back to the main chain.
Increased Throughput: By handling transactions off-chain, Layer 2 solutions significantly increase the transactions per second (TPS) capacity.
Cost Reduction: Off-chain transactions usually have lower fees compared to on-chain transactions.
Enhanced User Experience: Faster transaction times and lower fees improve the user experience.
Here are some examples of layer 2 solutions used to improve blockchain scalability?
Payment Channels:
These include off-chain user transactions that ease congestion on the main blockchain, as those made possible by the Raiden Network for Ethereum and the Lightning Network for Bitcoin.
Sidechains:
Sidechains are independent blockchains that run parallel to the main chain and are connected via a two-way peg. They allow assets to be transferred between the main chain and the sidechain, enabling offloading of transactions. Example - Plasma.
Rollups:
Rollups batch multiple transactions into a single transaction processed off-chain. The batched data is then submitted to the main chain, reducing data and computational load. Types of rollups include:zk-Rollups (Zero-Knowledge Rollups) & Optimistic Rollups.
State Channels:
such as those found in systems like Perun and Celer Network, which let several parties carry out transactions off-chain and only resolve the ultimate state on the main blockchain.
What Are the Challenges and Limitations of Layer 2 Solutions?
Complexity : Developing and maintaining Layer 2 solutions can be technically challenging.
Security : Ensuring the security of off-chain transactions and their connection to the main chain is crucial.
Interoperability : Achieving seamless interaction between different Layer 2 solutions and with the main chain can be difficult.
User Adoption : Educating users and developers about the benefits and usage of Layer 2 solutions is essential for widespread adoption.
How do zk-Rollups improve the efficiency of decentralized applications in blockchain ecosystems?
Blockchain's Layer 2 solutions are enhanced by zk-Rollups, which significantly increase scalability and lower transaction costs. They accomplish this by compiling off-chain transactions into a succinct proof (zk-Rollups), which is subsequently added to the main chain. This method increases the effectiveness and affordability of decentralized applications while preserving security through cryptographic proofs. zk-Rollups are also compatible with many blockchains, which increases their usefulness for a range of applications, including decentralized exchanges and gaming sites. All things considered, they successfully tackle the two main issues with blockchain technology: cost and scalability.
How does Nadcab Labs Contribute to the Advancement of zk-Rollups and Layer 2 Solutions?
One prominent player in blockchain technology, Nadcab Labs, has been actively working on developing and improving Layer 2 solutions, such as zk-Rollups. Their efforts are concentrated on maximizing security and scalability to guarantee safe and effective blockchain operations. Contributions from Nadcab Labs include:
Research & Development: Developing zk-Rollups technology to reduce costs and latency while improving transaction speed.
Implementation Support : Offering strong frameworks and instruments to incorporate zk-Rollups into different blockchain applications..
Security Enhancements : Improving the zk-Rollups' cryptographic methods to guarantee user confidence and data integrity.
Final Thoughts
zk-Rollups, blockchain scalability has advanced significantly and there's finally a workable answer to high fees and sluggish transaction speeds. Scalability, privacy, and security combined with zk-Rollups' potential to revolutionize Layer 2 solutions will allow the next generation of decentralized applications to flourish and create a more inclusive and productive decentralized future.
Author Profile:
Nadcab Labs - A Leading Blockchain Developers With over 8+ years of experience in Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation and Many More Services.
0 notes
Text
Exchange Market Making - Pillars of Liquidity and Price Discovery in Blockchain Technology

Introduction
Exchange market making is a process in which specific individuals, referred to as market makers, constantly quote the asking and bidding prices for financial instruments. These instruments, which are traded on multiple exchanges globally, can include anything from equities and bonds to derivatives and commodities. Market makers enable instantaneous trade execution by simultaneously quoting the buy (bid) and sell (ask) prices. This reduces the bid-ask spread and improves market liquidity.
Why is the Exchange Market crucial for the Functioning of Financial Markets?
Liquidity: Market makers guarantee that there is always a counterparty accessible for buyers and sellers by continuously providing bid and ask prices for financial products. By enabling investors to buy or sell assets fast without having a substantial impact on their prices, this improves liquidity.
Lower Transaction Costs: Market makers lower investor transaction costs by reducing the bid-ask spread. This reduces trading costs and promotes increased institutional and retail investor involvement in the market.
Preserving Market Stability: EMM companies smooth out supply and demand imbalances during times of market turbulence. By reducing price swings, this stabilizing influence promotes orderly market conditions.
Supporting Price Discovery: EMM firms play a critical role in price discovery by adjusting bid and ask prices in response to market dynamics. Their quotes reflect current supply and demand conditions, thereby aiding in establishing fair market prices.
Promoting Market Access: EMM services broaden market access by offering liquidity across a wide spectrum of financial instruments. This accessibility supports diverse investment strategies and facilitates the growth of capital markets.
How Do Market Makers Operate?
Market makers quote ask (sell) and bid (buy) prices for particular financial instruments simultaneously when providing Exchange Market Making Services. Their profit margin is determined by the bid-ask spread, which is modified based on factors such as asset volatility and supply and demand fluctuations. Ensuring liquidity, maintaining market stability, and promoting effective trading conditions are critical functions for centralized exchanges and the wider financial ecosystem.
What Strategies Do Market Makers Use?
Statistical Arbitrage: Using statistical models to identify mispricings and profit from price discrepancies.
Order Flow Management: Monitoring incoming orders to anticipate market trends and adjust quotes accordingly.
Algorithmic Trading: Leveraging automated trading algorithms to execute trades swiftly and capture opportunities in real-time.
What Challenges do Market Makers encounter in Exchange Market Making?
Market Volatility: Rapid and unpredictable price movements can pose significant risks for market makers, potentially leading to losses if not managed effectively.
Technological Risks: Reliance on high-frequency trading algorithms and electronic platforms exposes market makers to technological failures, such as connectivity issues or system outages.
Competition: Intense competition among market makers can compress profit margins and require sophisticated strategies to maintain profitability.
Counterparty Risk: Dependence on counterparties to honour trades and fulfil obligations can expose market makers to financial risks, particularly in unsettled or distressed market conditions.
Operational Risks: Operational failures, such as errors in pricing or execution, can lead to financial losses and reputational damage for market makers.
What role do Market Makers play in Providing Liquidity on Centralized Exchanges?
Continuous Quoting: Centralized Exchange Market Making involves market makers continually quoting bid and ask prices for various financial instruments listed on centralized exchanges.
Narrowing Bid-Ask Spreads: These market makers work to narrow the bid-ask spread, optimizing trading costs for investors by offering competitive prices for buying and selling.
Absorbing Imbalances: They play a pivotal role in absorbing temporary imbalances in supply and demand, ensuring stable market conditions during periods of volatility.
How does Nadcab Labs impact Exchange Market Making?
Market Integration: Bridging cryptocurrency markets with traditional finance could attract institutional investors, boosting liquidity and trading volumes.
Technological Advancements: Innovations in blockchain and web3 technologies may enhance trading efficiency and security on exchanges.
Regulatory Compliance: Focus on safe and legal integration of web3 technologies could help exchanges navigate regulatory challenges in cryptocurrency trading.
Global Presence: Operations in the UK, India, and globally bring diverse expertise to exchange market making practices.
Innovative Market Structures: Potential for new market structures or trading mechanisms inspired by Nadcab Labs innovations in cryptocurrency integration.
Conclusion
Exchange Market Making plays a crucial role in enhancing liquidity, efficiency, and stability in financial markets. By providing continuous bid and ask prices, market makers facilitate smooth transactions and contribute to the overall health of the market ecosystem. Understanding the role and strategies of market makers is essential for investors and market participants seeking to navigate and thrive in dynamic market environments.
Nadcab Labs - A Leading Blockchain Developers With over 8+ years of experience in Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation and Many More Services.
#nadcablabs#nadcab labs services#blockchain#blockchain technology#Exchange Market Making#Crypto Exchange
0 notes
Text
Exchange Listing Expert - Easily List Your Cryptocurrency with Blockchain Technology

Exchange lists are a complex task for many purposes. This is where the expertise of Exchange Listing Expert comes in, providing great guidance and support to make the publishing process a success. At the forefront of this space is Nadcab Labs, a leading provider of Exchange Listing Service dedicated to helping cryptocurrency projects achieve their most efficient and profitable listings.
What is an Exchange Listing Expert?
The Exchange Listing Expert is an expert who professionally guides companies in the process of quoting cryptocurrencies for a fee. They are well-versed in the requirements and processes involved in token registration, making them a valuable partner in your cryptocurrency journey.
Understanding the Role of an Exchange Listing Expert
An Exchange Listing Expert is an expert in managing the listing of cryptocurrencies on various exchanges. Your job is to navigate the complex processes and requirements established by the scholarship to ensure that the project meets the criteria required for inclusion. These experts are well-versed in cryptocurrency markets, exchanges, and regulatory environments, and can provide tailored strategies for a successful listing.
Why Choose Nadcab Labs for Your Exchange Listing Needs
Nadcab Labs is a trusted partner for Crypto Exchange Listing Services looking for expert leads in the directory. Nadcab Labs offers comprehensive transit inventory services tailored to meet the unique needs of each project, with a team of Exchange Listing Services who understand transit inventory trends. Nadcab Labs provides end-to-end support to streamline the listing process, from researching the right exchanges to preparing listing requests and managing communications with exchange platforms.
The Advantage of Cryptocurrency Exchange Listing
Securing a listing on a popular Cryptocurrency Exchange Listing provides many benefits to your project, including increased visibility, revenue and credibility in the cryptocurrency community. By leveraging a wider pool of investors and traders, listed projects can have better market and trading opportunities. In addition, listing on the exchange can serve as a sign of approval that indicates the correctness and quality of a project to investors and users.
Benefits of Using an Exchange Listing Service
Experience:
Exchange token experts have extensive knowledge of the cryptocurrency exchange environment, including the specific requirements and preferences of various exchanges. We can help you navigate the difficult process and increase your chances of a successful listing.
Save time:
Listing a cryptocurrency by price can be time-consuming, especially if you don't know the terms. A mailing list service can handle all the work for you, allowing you to focus your time on other areas of your business.
Increases Visibility:
Being listed on a popular exchange will greatly increase the visibility and credibility of your cryptocurrency. Our pricing experts will help you choose the right price for your brand and ensure it is visible to potential investors and users.
Compliance:
Exchanges are highly regulated when it comes to listing cryptocurrencies. An exchange rate quote specialist can help reduce the risk of delays or cancellations during the quote period by ensuring your listing meets the required compliance standards.
Leveraging Crypto Exchange Listing Services for Success
Navigating the competitive landscape of Crypto Exchange Listing Services requires a strategic approach and expert leadership. By using the services of an Exchange Listing Expert like Nadcab Labs, cryptocurrency projects can gain a competitive edge during the listing period. From choosing the right exchange to creating an attractive listing application, these experts play a key role in helping projects stand out in the crowded cryptocurrency market.
Conclusion
The role of Exchange Listing Expert is crucial in guiding cryptocurrency projects through the complexities of exchange listings. With Nadcab Labs at the forefront of interactive listing services, projects benefit from expert guidance, personalized strategies and intuitive support throughout the inventory process. Using the expertise of these experts, Cryptocurrency Exchange Listing can increase their visibility, credibility and success in the dynamic world of cryptocurrency exchanges.
Author Profile:
Nadcab Labs - A Leading Blockchain Developers With over 8+ years of experience in Custom Blockchain Development, Smart Contract Development, Crypto Exchange Development, Token Creation and Many More Services.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes