Don't wanna be here? Send us removal request.
Text
Something Awesome Project #5 Developing a simple malware
This is the malware I wrote which can be used to track people. Also, it is hard to turn off if you don’t know how to kill services running in the background. I demontrated the malware in the video below. Check it out and enjoy :)
https://www.youtube.com/watch?v=7IW6qaY-MIQ&feature=youtu.be
0 notes
Text
Something Awesome Project #4: Analysing the code of the malware (java)
Finally, we got the chance to see what is happening inside the malware's code with gd-gui. First of all, let's have a look of the main class:
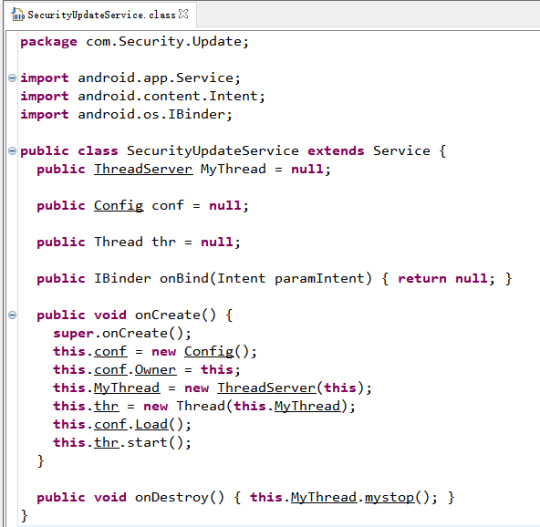
We can see the class is called SecurityUpdateService which means the malware is pretending to be a security improvement app (good move). Also, the main class is a service, which performs long-running operations in the background, and it doesn't provide a user interface. Now, inside the onCreate method, which will be executed when the service is created, the malware initialise instances of Config class and ThreadServer class respectively. Let’s move onto these two classes:

Inside Config.class, it imports a lot of I/O classes along with hashing and crypto classes. Some data sending and receiving must be happening in the app. Furthermore,
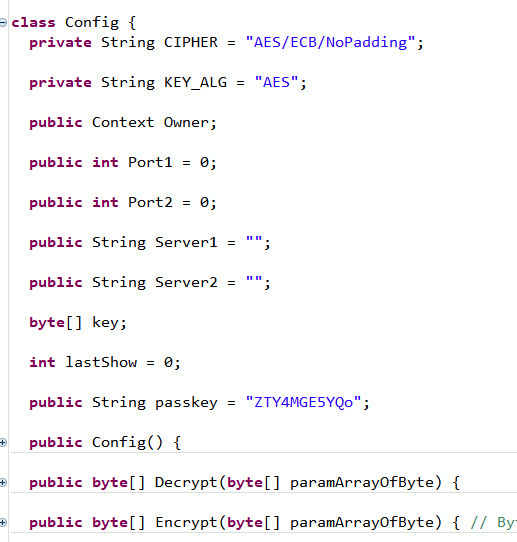
The class initialises some variables called port and server. Things are getting clearer that this app must have been doing some communications. Let’s go to the ThreadServer.class:
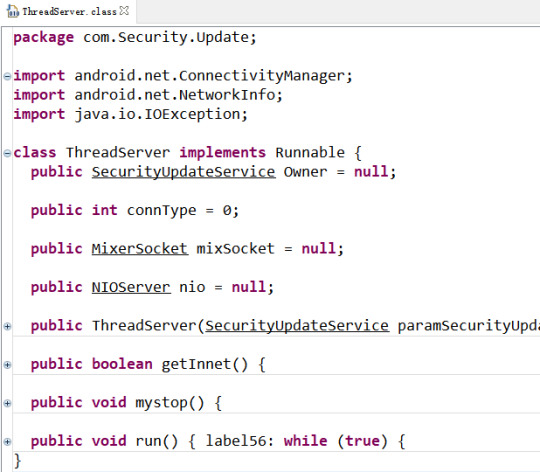
Here, we can see the server thread constantly monitors the Internet connection and executes some code in the method called run().
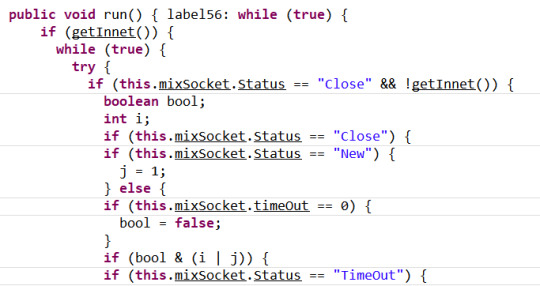
This is what the thread keeps doing all the time. It seems trying to maintain a socket to be open. Now, things are much easier and we can finally get to know what this malware does with another two classes:

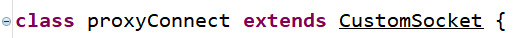
As you might have guessed, this malware turns your android phone into a proxy server, potentially used to gain illicit access to private networks. It can help the attacker go around the security controls of the internal network and make your device act like a spy.
At this point, I have finished analysing the code of this malware in a rough way. Next time I will demostrate the simple malware designed by me directly.
0 notes
Text
Something Awesome Project #3: Disassembling and Decompiling an Android malware
After installing all the tools we need to reverse Android apks, it is time to gain some hands-on experience. I downloaded an Android malware through GitHub named NotCompatible.A.apk. First of all, we can recognise the type of this file with the command line file
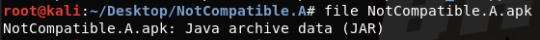
It is shown that apk files are just some JAR files, so we can simply unzip it. However, before that, I’d like to use apktool to decompose the apk file to see some other content
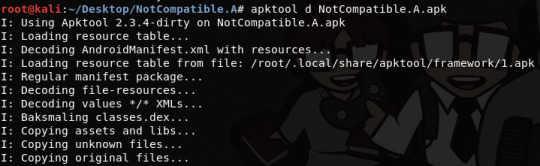
This is the directory created by apktool
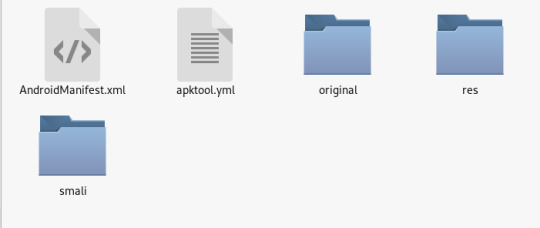
Now, we are able to see some interesting stuff here, such as Manifest.xml which describes essential information about the malware and a smali directory which is a human readible assembler/disassembler for the dex format. The former one is more intersting here

We can see the malware is asking for some permissions like Internet access, network state access and system booting notification. The malware seems needed to be booted when the device is on. From this point, let’s dig deeper by unzipping the file

These are all the file we got. We already know classes.dex is the source code from previous blogs, so it is our next target
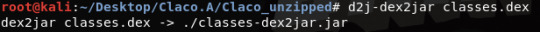
Dex2jar decompiles the byte code and we can read the java code with jd-gui

Now, all the source code is here. Next time, I am going to analyse it to see what the malware is trying to do on Android devices.
0 notes
Text
Reflection on Social Engineering Study: Hacking Puppy Love
After playing with the social engineering simulator, I found it quit interesting to study people's weaknesses and try to exploit them (not in a bad way), which makes me curious about what make people susceptible to phishing emails. I will approach this topic in two steps: firstly, talk about my methods to phish the Puppy Love owners in reality. Then, analyse other students' ideas to get a wider understanding.
In the case of hacking Puppy Love, the first doable hacking method that comes into my mind is spear phishing exploiting the administrators' special feelings or empathy towards dogs since they are extreme dog lovers. Sending them a link, which contains malware or a fake log-in web page, inside a message talking about some puppies who need to be rescued or helped to lure them to click has good chance to obtain the information we want. That is why spear phishing is way more powerful than widely sent phishing emails because it is "customised". Moreover, the administrators exposed a lot of personal information on the website, such as their relationship, their son's name and dogs' names, which is extremely unsafe. Attackers can potentially crack the password of the facebook account using the names or send some emails using the information about their son who they even care more about.
Some students came up with some good and simple ideas in the comment, such as pretending to be the partner of the admin and asking for password through emails or pushing them to make a payment by telling it is urgent. Although those strategies worked with the simulator, I think these approaches are likely to make people feel skeptical since receiving an email from your partner is a little bit weird (maybe I am wrong and couples normally communicate through emails), and getting pushed by a stranger to make a payment easily alarms people. However, I know simulators are just simulators, and the simulator in this case only depends on keywords to make reply.
In conclusion, although we can implement some techniques like two-factor authentication in this case to prevent being hacked. However, as we all know, people are always the weakest link in the security chain. In many research, even psychological approaches, such as deterrence, compulsoriness, etc. have been implemented to complement technical methods. Therefore, In the way of combating phishing attacks, we are still facing many challenges.
0 notes
Text
Pen Testing Seminar wrap-up
Preparation stage
We started preparing the presentation three weeks before the seminar date. Five people participated in from the beginning to the end. We set up a Slack group discussing online and conducted two face-to-face meetings learning and preparing the slides for the presentation with our tutor.
Presentation process
•I introduced the definition of pen testing and the importance of conducting a penetration test •Harshil talked about some practical uses, steps and certificates of pen testing •Sophia introduced some pen testing tools such as Kali, NMAP, Metasploit, etc. •Nabil and Bailey did a demo of some real hack the box skills
Learning outcomes
Pen testing is a very interesting and practical topic, and pen testers are in high demand since security issues are becoming more and more critical. We only learned a little about penetration test as it has a range of tools and pen testing is an art of methodologies instead of following certain steps. However, this seminar is an extremely good starting point for me to build up interests and make me consider to get an OSCP certificate in the future.
0 notes
Text
Something Awesome Project #2: Tools for Reverse Engineering Android APKs
Last time I discussed the forward process of building APK file. In this blog, I am going to analyse the reverse process of each step and the corresponding tools used in each phase (depicted in Fig. 1.). After understanding how APK files are made, things become much clearer and easier.
Fig. 1. Reverse process and tools

1) Unpacking APK files: APK files are saved in a compressed .ZIP format and can be opened by any Zip decompression tool.
2) Decompiling APK file: In this stage, I will be using ApkTool to disassemble the Android app, ApkTool is a set of utilities and has the features: -Disassembling resources to nearly original form (including resources.arsc, classes.dex, 9.png. and XMLs) -Rebuilding decoded resources back to binary APK/JAR -Organizing and handling APKs that depend on framework resources -Smali Debugging
3) Converting .dex files to .jar files: In this phase, I will use Dex2Jar to convert the source code from .dex file into java code.
4) Analysing java code: From here,we can use JDGui to parse the java code. JD-GUI is a decompiler for Jar files. We can use it to obtain a readable representation of what may have been the original code. We can also use JD-GUI to export the decompiled .class files to Java files keeping the application hierarchy of packages. This is useful to then re-create the application on an IDE (e.g. Android Studio, Eclipse).
Next time, I will install the tools in a Linux environment and learn how to use them.
0 notes
Text
Something Awesome Project #1: Understanding the Build Process of Android Application Package (APK)
In order to reverse apk files, it is necessary to understand the forward process of developing android apps. Java compilation and packaging processes after coding are:
Step 1: android java code files compiles to .class files via javac command. .class files is also known as Java byte-code.
Step 2: Java byte-code further get converted to dalvik byte-codes, which is the format that android os understands. Here all .class files and any .jar library files compiles to single classes .dex. DEX is called as Dalvik executable files.
Step 3: Packaging (.apk file) is done using android apkbuilder tool(APPT). It generate an apk file (zip file) from a DEX file + non-Java libraries + zipped resources + signatures + other files (depicted in Fig. 2.). The classes.dex file, resource files are compressed by aapt (Android Asset Packaging Tool).
Fig. 1. The Build Process:
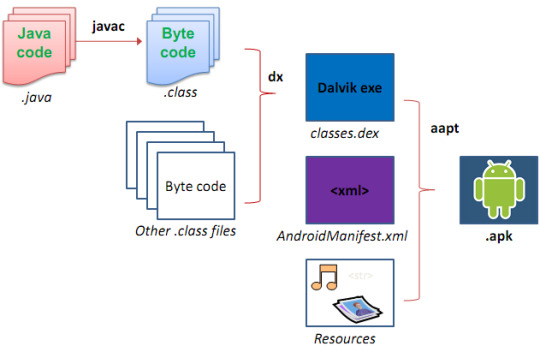
Fig. 2. APK Structure

Next time I am going to install the tools for apk reverse engineering and discuss the functionality.
0 notes
Text
Project Proposal Update: Reverse Engineering Android APKs / Mobile Malware Analysis
criteria pass - Understand how Android apps are built (forward engineering) - Learn how to use Android Reverse Engineering tools (e.g. ApkTool, dex2jar, jd-gui, etc.)
credit - Disassembling and Decompiling an Android malware - Read the malware's code - Analyse the malware's functionality and describe how it works
distinction - Modify the functionality of an existing malware
high distinction - Develope a simple Android malware based on the knowledge learned from previous steps and attack my own android device
1 note
·
View note
Text
high-impact, low-probability (HILP) events
The Fukushima Daiichi nuclear disaster was an energy accident at the Fukushima Daiichi Nuclear Power Plant in Japan, started primarily by the tsunami following the earthquake on 11 March 2011. Immediately after the earthquake, the active reactors automatically shut down their sustained fission reactions. However, the ensuing tsunami flooded the emergency generators that were providing power to the pumps that cooled the reactors. The coolant loss led to three nuclear meltdowns, hydrogen-air explosions, and the release of radioactive material in Units 1, 2 and 3 between 12 and 15 March.
The company used two different designs for safeguarding its 10 reactors in Fukushima. When the devastating quake struck on March 11, the five reactors with the newer design withstood the resulting 45-foot tsunami without their vital cooling systems failing. Those reactors shut down safely.
But the cooling systems failed at four reactors with the older design. Backup diesel generators and electrical-switching equipment were swamped by seawater. As a result, fuel melted down at three reactors and there were explosions at several reactor buildings, culminating in the largest release of radiation since Chernobyl.
The tsunami exposed an Achilles heel in the design of some of the plants: the questionable placement of a single kitchen-table-size electric-switching station. At newer plants, the station was in a robust building that also housed the reactor. In others, it stood in a poorly protected outbuilding—a relic of the original design. When the tsunami hit, those switches were knocked out, rendering operating generators useless.
The fateful design decisions were made in the 1970s. Some engineers say the company, known as Tepco, had opportunities over the decades to retrofit the old designs. The reason why the company did not eliminate the threat is probably because the low probability of the incidence. Unfortunately, the impact of this low-probability event is disastrous and far-reaching.
0 notes
Text
Type I /II errors
Have you experienced that you are waiting for a verification email but not receiving anything, and it turned out the email you were waiting for ended up on the spam email list. This is a type 1 error, also called a “false positive”, made by the spam detection system.
On the other hand, when you receive a real spam email in you mail box, and the spam detection system did nothing. A type 2 error, also known as a “false negative”, has just happened.
In Machine Learning field, “false positive” and “false negative” are very import indices to judge how good or bad a classification model is. If you give a picture of dog to your ML model and ask if this is a cat, type 1 error would be when your model says yes. Type 2 is when you give it a picture of cat and it says no.
0 notes
Text
Project Proposal: Compromising Organizational Cybersecurity by Exploiting Human Errors
Introduction
The information security environment has changed vastly over the years. Now, in spite of having infrastructure security elements such as firewalls, IDS/IPS, proxies, and honey pots deployed inside every organization, we hear news about how hackers compromise secured facilities of the government or of private organizations because of the human element involved in each activity.
The security of the entire organization can be at stake if an employee visits a malicious website, installs a malware on mobile phones, or clicks on the malicious link that he/she received in their personal or company e-mail ID. Therefore, I am going to perform these attacks in my project.
Checkpoints
- Spear phishing attack
- E-mail phishing attack
- Hacking android devices
- Other attacks found through the project
Other goals
All the above attacks are more or less based on social engineering techniques. Accordingly, social engineering is a key element for performing those attacks. Another purpose of this project is to learn how to use Kali Linux and Metasploit framework, which are very important tools for pen testers. Furthermore, instead of focusing on technical aspects only, I am going to study and analyse how these attacks can be prevented by building a human firewall.
1 note
·
View note
Text
Cracking a cipher
This little piece of cipher took me an hour to crack which proofs I can never become a cryptanalyst. I only know one-letter and two-letter words are the starting point, and rely on my luck for the rest. However, this also tells us substitution cipher really is a bad encryption method since even someone like me can decrypt it...

1 note
·
View note
Text
Hey people, this is the first post of my blog. Hope your guys like it...
1 note
·
View note