Text
NOC Services
NOC is an acronym for the network operations centre. In the industry of managed services, it is the
monitoring and remediation of various network aspects for businesses. This is where administrators
perform the supervision, monitoring, and maintaining of a telecommunications network. Companies
with large networks typically have a NOC, which is a room that has network visualizations or monitoring
of the networks. The remediation and monitoring services are performed for companies by NOC services
providers to reduce the overhead and free up IT departments for other important aspects of the
businesses.
Core NOC Services
Data Management with a NOC
The process of remotely managing data allows staff to be freed up for other tasks. This includes the
creation of reports and monitoring the occurrence level of incidents and resolutions. The in-house IT
team can then focus on maintaining, improving, and upgrading existing features instead of mundane,
repetitive tasks such as scheduling, virus scanning, and email analysis.
Network Infrastructure Installation
Focusing on the business is essential to the development and making it as strong as it can be, so the
network is crucial to the daily operations. Reliable support is needed for the installation and
implementation of the wireless network. This means the system is set up to reduce downtime by the NOC
management provider such as ExterNetworks.
Minimize Downtime with Remote System Backups
Remotely backing up the system means that the network operations centre can restore the system
remotely if it goes down. This will save both time and money since the restoration is done without the
need for calling in someone else or using the IT team. Less downtime and fewer internal resources being
used means considerable savings for any business.
Managing Operations Remotely – Handling Issues and Solving Problems
Incident management is the solution for effectively monitoring incidents based on the events that caused
them. The network monitoring team at ExterNetworks assigns the issues to appropriate teams for
resolving them quickly. Dedicated teams will work on handling incidents even while your team is at
home outside of working hours.
Monitoring and Troubleshooting Networks
A wide range of proactive monitoring and troubleshooting allows for various levels of service to be
provided consistently improving the quality while costs are reduced allowing companies to respond to
changes promptly. Remote monitoring is done twenty-four hours a day seven days a week to ensure
networks are safe and properly functioning.
Around the Clock Support
Knowing that you can get assistance all day every day offers you peace of mind. Help Desk services being
available always are vital to IT operations being efficient, reliable, and affordable. The remote service
teams are always learning to ensure the latest technical knowledge is always available to you while
allowing for experienced professionals to aid in dealing with issues.
Issues are Documented and Reported by NOC Providers
All issues are tracked and documented to create reports that are used as references for the IT team. This
is to ensure members are trained in all aspects of the network. The daily reports are compiled into
monthly reports which are used to recreate incidents and use them to prevent the same problems from
arising in the future.
Monitoring Capability of NOC Services
The main benefit of outsourcing the activities of a network operations centre is the ability to have the
majority of operations remotely monitored.
Monitoring the Infrastructure of the Network
ExterNetworks can monitor both virtual and physical network infrastructures proactively to pinpoint
issues before they turn into network outages.
Server Monitoring
Company’s servers are monitored remotely to ensure that the system is running smoothly and prevent
downtime.
Applications Development
Developing applications can be expensive and complicated to meet the needs of businesses.
ExterNetworks has a proven record of expertise to achieve a consistent result.
URL Functionality
Checking for the website’s HTTP 200 return, logging in, transactions on the website, and the results of
transactions are validated.
Troubleshooting Through Simulated Transactions
Monitoring that simulates actual user’s actions is automated to run at scheduled intervals eliminates the
changes of input errors by users.
Message Logging
Existing rules are already in place, and engineers customize alerts for these to meet client specifications.
Events in Windows
Windows operating systems will forward logs of events to the SIEM or are viewable in a snare console.
SNMP Traps
These are supported by any device that is monitored. Processing of inbound telemetry is done in real
time, and an engine that is rules-based flexible is used to separate noise from important events.
Improving Server Performance with NOC Services
Monitoring and Reporting on the Network, Around the Clock Service Desk
The service desk being open 24×7 means that someone is always available to assist businesses in locating
issues. Diagnosis of issues in the network can be done through various methods of monitoring.
ExterNetworks NOC monitoring allows for alerts around the clock as remote technicians fix the issues.
The costs are lower for off-site support than on-site support which saves companies money.
Infrastructure Monitoring:
The IT infrastructure is monitored to identify events that cause problems and find ways to resolve
them effectively. ExterNetworks allows companies to stay ahead of the issues and prevent
significant matters.
Application and Server Monitoring:
Applications and servers are monitored at all hours of the day and night by highly qualified
engineers.
Management of Incidents and Problems
ExterNetworks provides a single contact point for every incident as outlined in the Service Level
Agreement. The cause of events is found because incidents are automatically raised, and the monitoring
team assigns them to the correct team, so they are resolved quickly.
Monitoring Creates Web-based Reports
Reports based on the monitoring of servers, websites and customer interaction are generated daily and
compiled into monthly reports. This remote monitoring allows automatic generation which ensures the
performance level of the network is always known. The most significant advantage to web-based reports
is that they allow for actual user transactions to be duplicated to pinpoint what caused a problem and its
origin so that it can be handled effectively. Incidents that have been dealt with are summarized and
given to clients to keep the communication consistent.
Firewalls
Computer firewalls are the defence systems of computing devices or networks. They are the software
used for security on private networks to prevent unauthorized access or software from getting access
through the Internet connection. Firewalls are useful for filtering traffic when the system is exposed to
the global internet.
VPN Tunnels
The link between another network and a device that is encrypted is the VPN tunnel or Virtual Private
Network. Users are given access to the network’s protected information through a public network that is
used to connect to the private network.
Wireless Access Points
An access point or wireless access points are a hardware device that gives Wi-Fi devices the ability to
connect to the wired network. A router is usually connected to through the access point, or the router
itself can serve as the wireless access point. A NOC can monitor the access points remotely to help ensure
that the network is not being accessed without permission to prevent unauthorized access to
information.
LANs/WANs/MANs
LAN is the local area network or group of network devices and computers typically in a single location
that is connected. WAN is a wide area network meaning it is not restricted to a single location but is in
the same state or country. MANs are metropolitan area networks which are more significant than the
LAN but limited to a specific geographical area.
Services provided include optional services and reports.
Power and Facility Systems
Network Operation Centres provide redundant power sources that are powered with uninterruptible
supplies. Widespread system failures because of power outages are prevented with the assistance of
these backup generators. The facilities for outsourced NOC have cooling, system security and the
network considered in the design. It is essential that the machines be kept cold to keep them operating
correctly.
NOC Services Maximize the Performance of the Network (servers) with Minimal Cost
Users are not aware a NOC is present when the business’s network is operating at maximum efficiency
with the managed IT service partner. Cost is minimal because the company does not have to deal with
housing the IT department or if the current IT staff is dealing with issues of lesser importance. The
services are outlined, and costs specified in the agreement between the NOC provider and the
businesses.
NOC Captures and Classifies Network Events, Notifies of Network Events, and Minimizes Downtime by
the Escalation of the Resolution.
Network events are captured through the around the clock monitoring of the network to ensure that
incidents are detected and identified immediately. Performance indicators can be collected from
components, the detected events are correlated, and steps are taken to correct them. Incidents are
confirmed and electronic notifications are sent of the incidents. Management of incidents is done with
the goal to reduce the disruptions to business so that the highest levels of satisfaction and availability is
achieved.
IT Resources are More Efficient, and the Expenses Associated with Staffing and Software are Reduced
while the Performance of the Server is Maximized.
IT resources are free from sending emails about incidents and tracking them so the focus can be placed
on other things. The cost associated with staffing and software is reduced by outsourcing to remote
network operations centres. The current software can be kept up to date which increases server
performance.
Network Operation Centres Protect Against and Fix Network Outages
Network operations centres are there to prevent and fix outages in the network. Monitoring tools allow
the NOC to be prepared to handle outages at various levels with teams of technicians at every skill level.
For example, Tier 1 remediation services include but are not limited to, network infrastructure resetting,
server rebooting and the restarting of applications that have crashed. Issues are quickly resolved through
the triage of the system being instituted remotely.
Understanding SLA Driven NOC
NOC services are rising in use because of business competition, enhanced services, and technical tools.
Companies want the time spent on maintenance of IT departments so they outsource the support to a
provider who can monitor all the tools and the network remotely. The SLA driven NOC gives both
ExterNetworks and its clients an advantage because both know exactly what to expect when it comes to
services.
Reduction in Operational Costs
Service providers and clients have protection with the agreement for service level which outlines the
conditions and terms of service to be provided. Service level agreements or SLAs reduce the costs of
operations and define what level of service is provided by outlining what companies can and cannot
expect from the provider.
Service Level Agreement Customization
The SLA or Service Level Agreement can be altered to reflect that a company is only using certain services
instead of an entire package of services so that only services provided are paid for instead of paying a set
cost for a package and not receiving all the services.
Advanced Expertise Services
ExterNetworks offers an analysis of the gap between how things are and any changes that are being
considered. Software development includes training, extended management of projects and service
customization to optimize the environment of users. Productivity is increased through outsourcing
because the IT department is free to take care of other issues of more importance.
NOC Monitoring Tools and Software
NOC management has five essential elements known as tools which are a vital element toward
improvement. You need to know which tools will give you the best return on the investment into
outsourcing to companies such as ExterNetworks. There are many ways that these tools can help you to
give your team more control over tasks while putting the Network Operations Centre (NOC) in a position
to be an exclusive resource for the IT department.
The Five Essential Tools of Network Operation Centre Services:
Incident Tracking through a Ticketing System
The use of a ticketing system will enable all issues to be kept track of by the urgency, severity and who is
assigned to handle a specific task. Issues that arise tickets are created to describe the issue so that it can
be processed and assigned to the correct person or department. When the person or department
assigned to a task cannot complete it, the ticket will move to the next level for correction. The best
service can be provided to customers and the tasks of each shift prioritized by making all pending issues
known.
Centralization of Knowledge
A centralized place for all documentation and knowledge that is readily accessible to every team
member is known as the knowledge base. It should be a fluid source of information that is always up to
date with lessons from incidents so they can be used to prevent the same thing from happening in the
future. The experiences should be referenceable to the entire company and used in making future
improvements to the organization.
Daily and Monthly Reports for Measuring Incident Severity and Improvement Progress
Reports should be created on both a daily and monthly basis. The last 24 hours should be included in the
daily report with every major incident included. All incidents that were resolved should have the root
cause listed. The reports help the NOC managers, shift leaders, and the entire IT department knew about
the activities of the NOC services and significant incidents. The progress of the team can be measured
when the monthly report is made from the daily reports. Trends in performance will be seen more
efficiently, and areas that can use improvement will be identified speeding up the process.
Monitoring – NOC has Two Monitoring Process Types That are Relevant to It:
Infrastructure Monitoring – Environment of the data center, network, or servers make up the monitoring
of the infrastructure. This allows for the entire system to be protected from threats by detecting them
early.
User Experience Monitoring – problems are replicated to find practical solutions by simulating the
activities and behavior of users to see the resulting actions associated with them. Actual issues that users
run into can be duplicated to find ways to fix them and to prevent them in the future making the
experience more pleasing to everyone.
Automation of the IT Process
Time is freed up for more strategic projects through the automation of repetitive daily tasks. Level 1
teams can deal with restart services, clean-up of disk space and resetting of passwords. MTTR is also
reduced in critical incidents during IT Process Automation. Essential events of the system can be handled
during off hours through the triggering of specific workflows.
The benefits of having all these services outsourced and automated assists with expediting the process of
problem-solving. Staff is freed up to do other things when the issues with the network and that arise for
customers is handled remotely. User experiences are made smoother through the improvements that
monitoring creates.
NOC Services Functionalities
The focal point of organizations to control and monitor networks is the NOC. This is where the network
operations are kept up to par through all the stages, ways, and channels of communication available to
the staff that is overseeing them. The ability to outsource these services and have them performed
twenty-four hours a day allows companies to detect and fix issues immediately preventing downtime
and loss profits. The benefits are increased when an experienced MSP such as ExterNetworks takes over
the basic functions.
NOC Major Functions
The technical team of the NOC keeps an eye on the endpoints by managing and monitoring to resolve
issues as they come up and prevent issues from occurring by taking preventative measures. Engineers,
technicians, and other staff is free to perform other tasks.
Network Monitoring
Available around the clock with ExterNetworks, remote network monitoring allows applications and
machines to be checked remotely. Custom watches designed to keep an eye on clients, equipment and
products are done by specialist ensuring that everything is always working correctly. Monitoring of the
network can also be used to identify threats and other issues in the network which increases the
efficiency of the network.
Incident Response
NOC outsourcing through ExterNetworks gives faster incident response times allowing them to be taken
care of as they occur no matter what time it is. Incidents are responded to and resolved more quickly
with the benefit of 24 hours 7 day a week monitoring to identify them as they occur. The improved
response times means that incidents are dealt with faster and can be prevented more easily in the
future.
Establishment, Investigating and Refreshing of Application software.
Picking the correct application software for a business can improve the functioning and efficiency and
the proper software will ensure that your business is saving time and resources. The application software
is a program for performing specific functions such as resource coordination, figure calculations, and
information management. Visuals can be constructed, and data manipulated through the use of
application software.
The outsourced NOC services can include finding the new application software and checking it for issues
that can cause problems with the network. The software can also be updated to perform tasks more
efficiently, and this will increase the overall efficiency of the company.
Patch Management
Patches are part of the network security. The management of patches assists in the acquiring,
installation and testing of multiple patches or code changes on software tools and applications that are
already present on computers. Systems remain up to date with existing patches and the appropriateness
of patches is determined. The types of patches implemented in a network depends on the types of
threats that are present.
Network Capacity and Backup
Network Operations Centre can remotely backup the data on the company’s network. The capacity refers
to the available storage space for the backing up of files and other data on the server. This reduces or
even eliminates the need for in-house backup systems. The storage capacity needed for regular backups
on in-house systems is also reduced when backups are done remotely from an off-site location. There can
be an increase in storage capacity to ensure that the network does not fail as a result of an inability to
restore it from a backup.
IPS Administration and Firewall Checking
An IPS (intrusion prevention system) monitors networks for activities that are malicious including
violations of policy and threats to security. The primary purpose is to identify suspicious events, log the
information and attempt blocking of the activity. Finally, any suspicious activities are reported. Through
the identification and logging of the suspicious activity it is possible to identify it faster in the future and
come up with a solution to prevent it from occurring again.
The firewall is the system of network security that controls and monitors traffic on the network using a
set of safety rules that have been predetermined. A barrier is created between trusted and untrusted
networks. Traffic is filtered between at least two networks and run off the network hardware by network
firewalls. Host computers run host firewalls which control the traffic pattern on the machine.
Analysis of Threats
The network operation centre design allows for threats to the system to be analysed remotely freeing up
company resources from being down while scans are run, and systems are troubleshooted. Whenever
something comes in it is scanned to see if there is anything that could potentially be damaging. This
means that time is saved by the IT department because they don’t have to spend time determining
threats or the severity of threats to the system. Threat severity is determined by trained engineers and
technicians at a remote location to ensure that the system continues to run smoothly. The in-house IT
team can focus less on threat identification and prevention and more on other infrastructure building
tasks.
Filtering and Remediation with Antivirus Software
Frequent checks for viruses are done on emails with the valid server license for supported software to
ensure that malicious emails do not make it through and infect the entire system. Antivirus remediation
is the method used to attempt to remove viruses found on the system, hopefully before they can damage
the system. The filtering for viruses regularly reduces the overall risk of system downtime a great deal.
Management Based on Policies
The administrative approach aimed at simplifying the management of endeavours when it comes to the
establishment of policies designed to deal with potential situations that could arise is known as policy-
based management. Operating rules are needed for order to be kept. It is essential to achieve
consistency and maintain security while achieving a goal. Staff members should be educated on the
policies that are in place for the way that things should be handled throughout the company.
There are various forms of around the clock NOC monitoring that organizations make available including
the checking of the physical machine and applications. The software, hardware, and network itself are
kept up and running to prevent downtime which prevents companies from losing revenue. The ability to
have threats identified and dealt with off-site means that it is possible users never realize there was a
danger to the system since it is less likely to experience downtime as a result of a threat to the system.
NOC Trends
The latest trends in technology are being provided support by Network Operations Centre to ensure that
the current systems are kept up and running with minimal downtime when corporations are not ready to
replace the entire system. Outdated systems might not be upgradeable or can crash often reducing the
productivity of the whole company. Outsourcing to a third party can save costs by allowing these
systems to be given the ability to keep up with the demands of traffic, sales, and general tasks.
NOC Services Assist Companies Switch or Upgrade Networks
There are several ways that Network Operations Centres such as ExterNetworks aid companies that wish
to switch or upgrade current networks without too much expense or complications. The use of various
techniques to upgrade software, have technology at multiple locations connected, transitions of wireless
networks and keeping the infrastructure secure. ExterNetworks NOC services will give you peace of mind
by taking these tasks out of your hands and freeing up staff.
Outsourced NOC Services Follow Several Trends:
Hybrid Technology for Upgrading Outdated Software
There are several places still using software and hardware that has been around for over a decade which
can slow business down. It still works, but you might not be able to update to the newest software which
leads to the term hybrid in the security space. A hybrid technology device is something that can support
several different technology types when you plug it into your system to maximize its capabilities. This
allows for platforms to be upgraded to take advantage of the newest features giving the organization
the ability to scale the physical security of the infrastructure slowly and over time. Increased security
means the system is not as vulnerable to attack.
Understanding High-End Infrastructure
The category of infrastructure referring to specialized facilities that bridge the existing gap is known as
high-end infrastructure. It is required for the demonstration of reproducibility and innovation products
scaling. Mitigating risks, maturing technology, and assisting in securing various funding makes having a
high-end infrastructure crucial. When technology is considered mature, it means that it has been around
long enough for the reduction or removal of initial faults and problems that were persistent in having
occurred or one that is just coming into daily use on a large scale.
Supporting the Transition from 4G to 5G Wireless Networks
The next few years will see the transition for companies to go from 4G to 5G wireless technology which
will be at least ten times faster and will be immensely more powerful. This gives businesses the
opportunity for improved IoT ecosystem support, increases in efficiency and reliability of communications
specific to industries through the encouragement of increasing the efficiency of activity. The networks
are currently being tested to find the issues with them before the full roll out.
Technology at Multiple Locations
This technology gives you the design and what it looks like from the perspective of technology making it
as important as the back end. You need a plan for when the technology is up and running. The execution
of a strategy for multi-site technology requires methods that are consistent with making the locations as
alike as possible. Customers are not satisfied, and money is lost when locations are unable to process
transactions meaning that all locations should function the same.
The monitoring of technology, remote troubleshooting and other services offered by network operations
centres help to ensure that companies are not losing money but instead are seeing a higher return on
investments. Technology monitoring allows issues to be detected and prevents some of the problems
that could cause the system to crash and prevent transactions from being processed. The ability to
update existing technology without replacing the entire system saves money and allows businesses to
upgrade the network as it becomes more cost efficient for them.
Benefits of utilising NOC Services:
24x7 Monitoring and remediation of servers, networks, applications, databases, and
workstations
Increased capabilities without the need to increase head count or internal resources.
Eliminates the hassle of dealing with every alert and to minimize the number of false-positive
tickets
Gives you and your engineers more time for higher-margin and strategic projects
For IT managed services Mumbai india visit below link
Link : https://orientindia.in/
0 notes
Text
Managed IT services company Mumbai | DaaS provides a fully managed model combining hardware, services, and software into a single configurable solution for a predictable, affordable periodic fee. Orient Technologies Mumbai
0 notes
Text
Optimizing the PC Lifecycle
Helping You Embrace the Modern IT Workspace!
Device As a Service (DaaS)
DaaS provides a fully managed model combining hardware, services, and software into a single configurable solution for a predictable, affordable periodic fee.
What can be included in a DaaS solution?
Hardware: Any Hardware offers PCSD hardware options, MBG, and DCG products. Devices from other OEMs can be considered on a case-by-case basis.
Services: All Services in our portfolio, from warranty upgrades to full system deployment. Availability of services varies across goes so be sure to check with your local services organization to confirm availability.
Software: All Software, as well as select third-party software such as Absolute, Microsoft Office, and WinMagic, to name a few.
Target Customers
The following challenges are good indicators that a customer might be ready to transition to a DaaS Solution:
CIOs looking for an easy, ongoing refresh model that reduces costs and allows them to stay current with the latest device technologies and software to maximize workforce productivity and retain top talent.
IT Managers who want to engage with one vendor and have one contract for all their IT-related needs. If they face service challenges, they have “one throat to choke”.
Finance Managers need to better manage their cash flow through a predictable monthly fee model.
Business Owners looking to strategically outsource costly individual IT requirements or completely rid themselves of the entire device support lifecycle.
Meet the New DaaS Solutions
Ease
Choice of the latest flagship devices, premier support, Standard Reports, Asset Disposition, and flexible financial services financing.
Benefits:
Designed especially for small and medium-sized businesses, simplify gives customers the opportunity to leverage the very latest technology backed by premier support. It features easy, predictable monthly payments and no upfront investment in an easy-to-understand, simple-to-buy solution.
Intensify
Everything from the Simplify Solution, imaging/enterprise-ready preload, asset tag, Custom BIOS settings, Microsoft Autopilot registration, and flexible financial services.
Benefits:
For medium-sized businesses and enterprises, accelerate enhances the speed and ease of IT delivery by utilizing the efficiency of our configuration services and streamlined deployment. These services provide a premium end-to-end user experience across the customer’s organization.
Enhance
Everything from Simplify and Accelerate solutions and adding in the flexibility to build a custom DaaS solution combining any options from our full services catalog, including transformative services such as Encryption, Cloud Deploy/recovery, Unified Endpoint Management, Accidental Damage Protection, Keep Your Drive, as well as a Custom Ordering Portal, Service Delivery Manager, and flexible Financial Services.
Benefits
For enterprise and global customers, Transform will change the way a customer’s organization experiences Modern IT, delivering premium devices, expert support, smooth and simple deployment, plus advanced IT automation and intelligence services. IT resources to stay focused on what they do best, users are empowered to stay productive, and finance is satisfied with a simple, affordable, and predictable cost structure.
DaaS Solutions – Make Modern IT Easier
DaaS allows businesses to simplify and enhance their organizational IT assets, services, and support resources—yet it can be difficult to know where to begin in pivoting towards a modern workplace. Our new solutions allow organizations to transform into Modern IT through a selection of DaaS constructs, giving a clear entry point from which, they can build the complete DaaS solution that best meets their business needs.
Customize for your Perfect Fit
The solutions are designed to be customized, so every customer can access the right mix of DaaS features to power efficiency and increase productivity across their organization. Rely on us to keep your organization’s environment running safely, securely, and at optimal efficiency with ThinkShield built-in protection. At the end of the term, we will manage secure asset disposition that is compliant with local governance and environmental regulations, while customers experience uninterrupted workflow with a convenient device refresh. Depend on the expertise to deliver smart lifecycle services and bring the modern workplace to your organization with the most flexible and cost-effective DaaS solutions.
Key Features of DaaS
Configuration
Custom image, configure BIOS, and load management tools.
Hardware & Software Monitoring
Hardware and software asset reports, remote management and remediation tools, multi-vendor patches and on-site options.
Hardware & Software Add-ons
Web monitoring, email monitoring, managed anti-virus, and Office 365.
Deploy on-site
Install new machine, migrate data, and remove old machine.
Asset Recovery
Lease management reports, call history/loss control reports, and removal of old assets with a certified data delete.
Premier Support
Single end-user phone line, Technical Account Manager, multi-vendor, and on-site fix.
Flexibility to Scale
Ability to adjust PC volume to meet changing usage over the contract term.
Data & Device Security
Manage endpoint security with continuous monitoring. Includes suspicious event alerts, security posture reports, at-risk data discovery, security application health monitoring, and remote remediation of potential security incidents
0 notes
Text
Connecting Networks with Overlapping IP Ranges
Connecting Networks with Overlapping IP Ranges
A common situation we see in customer networks is when there are resources with overlapping IP address ranges that must communicate with each other. Frequently this occurs when companies are acquired and have used the same private (RFC1918) address ranges. However, it can also occur when a service provider with a unique IP range must provide access to two different customers that each have the same IP range.
Network overlaps can also occur unintentionally. Make sure that you check the documentation of services and applications when building your VPCs to avoid conflicts with predefined IP addresses.
This post discusses some ways in which you can overcome this obstacle for IPv4-based networks. Customers that are using IPv6 aren’t expected to experience this problem given the size of the address space.
Note that the solution you choose will depend on how your applications communicate with each other. You may require full two-way connectivity between applications (that is, network sessions can be established by either side). In other situations, you may only need “outbound” connectivity – where sessions are established from one network to the other and not the other way around. These patterns will influence how you design your network to deal with overlapping IP ranges.
Option 1: Renumber IP networks
This is always the first suggestion we make to customers. It won’t work in the service provider scenario above. However, if there’s an opportunity to renumber the networks, then it’s the best option. Although changing a network configuration isn’t easy, it avoids long-term pains such as:
Increased network management costs: Most of the other solutions presented below require appliances or services which will have a charge attached to them. Renumbering a network isn’t free (after all, time and people cost money, too). But in the long term, it removes the ongoing cost of running the components required to connect overlapping networks together.
Increased complexity: Generally, connecting two or more networks that overlap together is difficult! In the long term, it may prove to be increasingly complex as the application landscape grows and changes or as additional networks are added.
Complex troubleshooting: When things go wrong, trying to figure out what’s happening; where it’s happening; and what to do about it, is complex enough without having to deal with overlapping IP addresses. This can all be confusing and mean that troubleshooting takes much longer than it otherwise could.
Compatibility issues: All the following solutions utilize Network Address Translation (NAT) in some way. Some applications won’t work with NAT, and others will have limitations in how they can be used. You may not have applications today that don’t work with NAT, but they could be deployed in your environment in the future. Renumbering completely avoids this problem.
Utilizing NAT also means additional management overhead: Because applications use overlapping IP addresses, firewall rules will be complex as you keep track of and update the original and NAT IP addresses that the application use.
In general, we strongly recommend renumbering overlapping networks where possible as it is cheaper and easier in the long term.
Option 2: AWS PrivateLink
In 2017 AWS launched PrivateLink. This is a Hyperplane-based service that makes it easy to publish an API or application endpoint between VPCs, including those that have overlapping IP address ranges. It’s also ideal for service providers who must deliver connectivity to multiple customers, and thus have no control over the remote IP address range. Furthermore, it provides the same benefit to customers with complex networks where IP addresses overlap. This is by far the simplest option presented here, as it requires no change to the underlying network address scheme.
In the following diagram, you can see an application that resides in the “Provider” VPC. It has a Network Load Balancer (NLB) attached to it, and by using PrivateLink we can share the NLB with multiple “Consumer” VPCs. Here, the consumer VPCs overlap with each other and with the provider – the worst-case scenario.
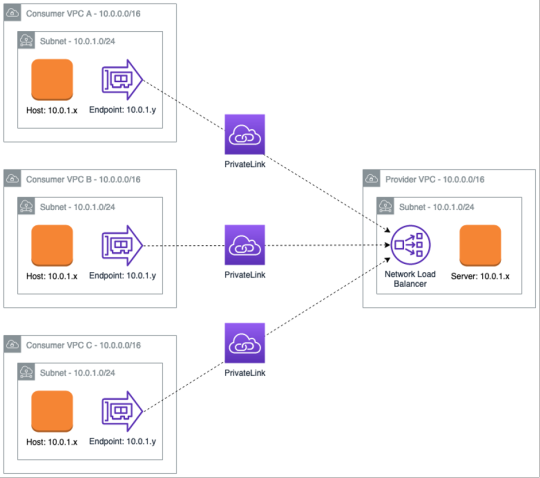
In each consumer VPC, the PrivateLink endpoint appears as an Elastic Network Interface with a local IP address. In the provider, VPC, connections from the consumer VPC appear to come from a local IP address within the producer VPC. The underlying Hyperplane service is performing a double-sided NAT operation to make PrivateLink work.
There are added security benefits:
When establishing the PrivateLink connection the provider must send the owner of the consumer VPC a request. Then, the owner must approve it – the same way that VPC peering works. There’s no way for a provider to create a consumer-facing PrivateLink without approval.
Only configured TCP ports are allowed between the consumer and provider. This makes sure that the consumer only has access to specific resources in the provider VPC and nothing else.
There’s no way for the application in the provider VPC to establish a connection to the consumer VPC.
Finally, there is a scalability benefit – an application can be published by a provider to hundreds of consumers’ VPCs.
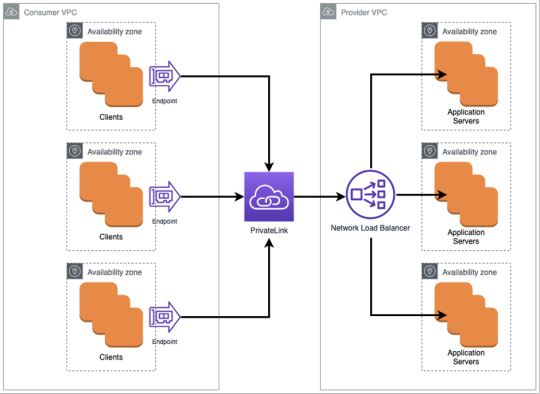
Redundancy comes built into PrivateLink in the form of the NLB. This delivers traffic to the back-end servers and consumer VPC configuration. Moreover, you choose which subnets to place endpoints in. The following diagram shows a multi-subnet environment that would be set up across multiple availability zones.
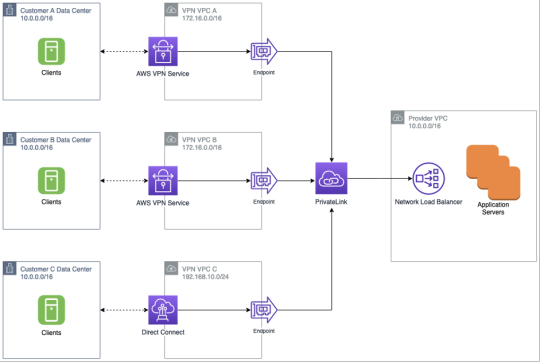
One common question from customers is how to achieve this connectivity with on-premises networks. In the following example, we have a provider VPC that’s connected to multiple independent consumers, who are in turn connected to AWS via VPN. Note that the consumers all have overlapping IP addresses, even with the provider VPC. The only challenge is to find an IP range that will be allocated to the VPC where the VPN service is attached that doesn’t overlap with the on-premises range. In this example, the on-premises clients will connect to an IP address allocated to the PrivateLink endpoint in the VPN VPC.
This solution also works with AWS Direct Connect as seen for Customer C in the diagram. Customer C also has a different IP range in the VPN VPC – perhaps because 172.16.0.0/16 was already in use in their network so the intermediate network must be different for them. This isn’t an issue, as the IP address range in that VPC only needs to not conflict with anything in the networks that Customer C uses. Therefore, there’s a huge range of flexibility in what can be chosen.
Setting up this option is straightforward, as it has no additional maintenance, is highly redundant, and also highly scalable. Furthermore, it provides separation between the customer networks. If you’re creating applications in a service provider environment, then consider architecting your solution so that PrivateLink can deliver this level of network flexibility for you.
Note that there’s a cost for PrivateLinkas per Aws. Some applications may not work with this solution as applications must present as a single TCP port. If you have an application that uses UDP or has multiple TCP ports and the clients must maintain back-end server affinity then PrivateLink isn’t appropriate for you.
Option 3: Use multiple IP address ranges in VPCs
You may have an application that’s broken into different tiers – a front-end that responds to users or other application requests; and then one or more “back-end” tiers comprising middleware, databases, caches, and so on. In this environment, you can choose to have a set of front-end subnets that have non-overlapping IP addresses while the back-end subnets do overlap with other applications.
The following diagram shows three application VPCs connected to Transit Gateway. Note that the VPCs have overlapping IP address ranges but different front-end subnets are advertised to Transit Gateway so that they can each be reached by end users. This requires that automatic route propagation to Transit Gateway be disabled as not all of the subnets in each VPC should be advertised.
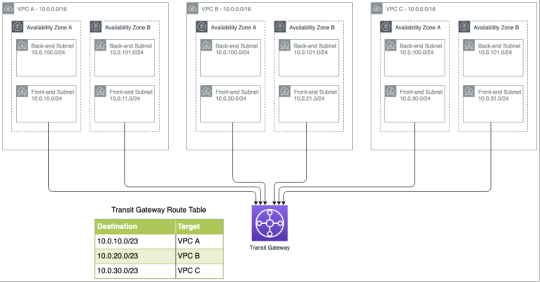
Until recently, the biggest drawback to this architecture was that the applications couldn’t communicate with each other, as there was no way to create a more specific route in each VPC to allow connectivity to the front-end subnet in another VPC. For example, in VPC A you couldn’t create a route for 10.0.20.0/23 because it’s more specific than the VPC address range.
The launch of more specific routing in VPCs has resolved this problem. In each front-end subnet, you can modify the VPC route table so that other 10.0.x.x networks (in this example, 10.0.20.0/23 and 10.0.30.23) are routed to Transit Gateway.
This doesn’t solve the challenge of how to administer servers that reside in the back-end subnets. One way of doing this is to place a bastion host in the front-end subnet of each VPC. This will let administrators reach the back-end subnets by using SSH or RDP to that intermediary host.
You will still want the back-end servers to download code from repositories, update from appropriate servers, send application logs, and provide performance metrics. For this, you might use a combination of private endpoints for AWS services (such as Amazon CloudWatch and Amazon Simple Storage Service (Amazon S3)). If your servers need outbound access to non-AWS endpoints, then a NAT or proxy service hosted in the front-end subnets will be required.
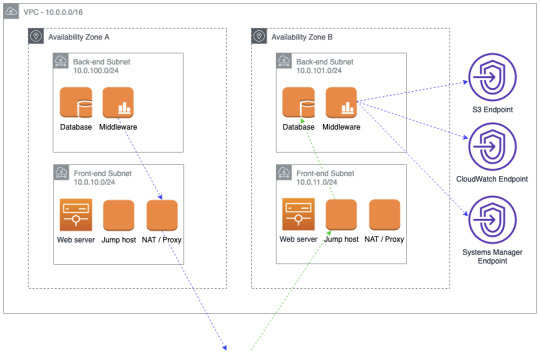
This option means that if you had to renumber just some of the overlapping networks, then you can do less work (by only changing the front-end subnets) while mitigating most of the risk (by not having to run complex NAT solutions to have applications and users communicate). However, there are additional costs – bastion hosts, NAT or proxy instances, and private endpoints for AWS services. We also strongly encourage that this infrastructure is deployed and managed using automation to keep administration costs as low as possible.
Although this diagram shows the web server (or any other front-end component of the application) in the front-end subnet, you could easily deploy load balancers to that subnet and keep the Amazon Elastic Compute Cloud (Amazon EC2) components in another subnet using a non-reachable IP address range.
This option lets you to deploy back-end workload subnets that have thousands of IP addresses without worrying about whether those overlap with other applications. Furthermore, you can only use the minimum number of IP addresses for front-end subnets to make sure that the application is reachable from external (to the VPC) networks.
Option 4: Hide subnets using Private NAT Gateway
We recently (in 2021 as of when this was written) launched Private NAT Gateway. In the same way that NAT Gateway lets you “hide” an entire VPC network range from the Internet (making it appear to come from a single Elastic IP address), Private NAT Gateway lets you do that when connecting from a VPC to other private networks. Instead of using an Elastic IP address and an Internet Gateway, Private NAT Gateway uses the private IP address that it’s allocated from within your VPC as the address that the VPC is “hidden” behind.
This is useful in an environment where you want to connect from a VPC to your on-premises networks or other VPCs, but don’t want to connect directly to resources in the VPC. This is very similar to Option 2 presented above except that you don’t have to run a NAT or proxy instance to provide outbound connectivity from the VPC.
The following diagram illustrates how Private NAT Gateways work:
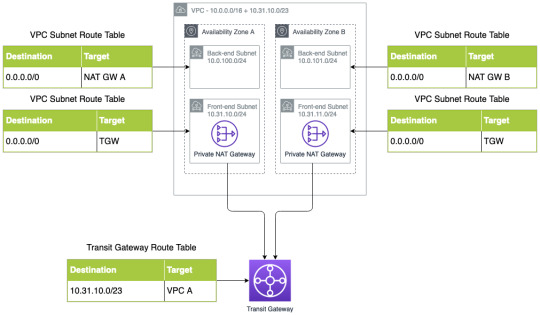
Note that the VPC IP address range is 10.0.0.0/16 but two extra subnets have been added (10.31.10.0/24 and 10.31.11.0/24) which are outside of the original VPC IP address range. A Private NAT Gateway has been added in each availability zone (note that as with Internet-facing NAT Gateways only one is required but two are recommended for redundancy) to the each of the subnets with the secondary IP address ranges. The NAT Gateways will use an IP address from that subnet to translate IP addresses of the workloads from the back-end subnets.
In Transit Gateway, a route to the front-end subnets has been added so that return traffic can be sent back to the Private NAT Gateways. Within the VPCs, traffic from the back-end subnets will be routed to the Private NAT Gateways in much the same way that Internet-facing NAT Gateway route tables operate.
In this case, managing instances in the back-end subnets would need to be done using SSM or bastion hosts in the front-end subnets. If application deployment was automated then there would be no need for human management of those hosts. This is a far more desirable outcome.
As with the previous option this is a great way to conserve IP addresses while making sure that relevant and critical parts of the workload are still routable and thus available. You can find a detailed walkthrough on how to create this type of environment in a recent post.
Note that there’s a charge for using Private NAT Gateway as shown on the pricing page.
Conclusion
In this post we’ve shown several ways of dealing with overlapping IP networks. The following table shows a comparison between the options:
Option
Service Cost
Redundancy
Full Network Reachability
Solution Complexity
Maintenance Complexity
Ideal For
1: Renumber
Low
N/A
Yes
Low
Low
Everyone – recommended
2: Private Link
Medium
Yes
No
Low
Low
Service providers
3: Use multiple IP ranges
Medium
Yes
No
Medium
Medium
Container/large workloads
4: Private NAT Gateway
Medium
Possible
No
Medium
Medium
Container/large workloads
Remember that renumbering the networks that conflict is by far the best option (in terms of cost, complexity, and visibility) in the long-term. For service or application providers that have no control over the networks to which they connect, PrivateLink is designed specifically to deal with that problem.
0 notes
Text
AWS SYSTEM MANAGER
What is AWS System Manager?
AWS Systems Manager is a set of features that help you manage your applications and infrastructure running in the AWS Cloud. Systems Manager simplifies application and resource management, reduces the time to identify and resolve operational issues, and helps you manage your AWS resources securely and at scale.
Application Management
Application Manager helps DevOps engineers investigate and troubleshoot issues with AWS resources in the context of applications and clusters. In Application Manager, an application is a logical grouping of AWS resources that you operate as a unit. This logical grouping can represent different versions of an application, an operator-owned line, or a developer environment, to name a few. Application Manager support for container clusters includes both Amazon Elastic Kubernetes Service (Amazon EKS) and Amazon Elastic Container Service (Amazon ECS) clusters. Application Manager aggregates operational information from multiple AWS services and Systems Manager functions into a single AWS management console.
Change Management
Change Manager is an enterprise change management framework for requesting, approving, implementing, and reporting operational changes to application configuration and infrastructure. AWS Organizations allows you to manage changes across multiple AWS accounts in multiple AWS Regions from a single delegated administrator account. Alternatively, you can use local accounts to manage changes for a single AWS account. Use Change Manager to manage changes to both AWS and on-premises resources.
Node Management
A managed node is any machine configured for Systems Manager. Systems Manager supports Amazon Elastic Compute Cloud (Amazon EC2) instances, edge devices, on-premises servers, or virtual machines (VMs), including VMs in other cloud environments.
Compliance
Use Compliance to scan your fleet of managed nodes for patch compliance and configuration discrepancies. You can collect and aggregate data from multiple AWS accounts and AWS Regions and drill down to specific non-compliant resources. By default, Compliance displays compliance data for the Patch Manager patch and State Manager associations. You can also customize the service and create compliance types based on your IT or business needs.
Fleet Manager
Fleet Manager is a unified user interface (UI) that allows you to remotely manage your nodes. Fleet Manager allows you to view the health and performance status of your entire fleet from one console. You can also collect data from individual devices and instances and perform common troubleshooting and management tasks from the console. This includes viewing the contents of directories and files, managing the Windows registry, managing operating system users, and more.
Inventory
Inventory automates the process of collecting software inventory from managed nodes. Inventory can be used to collect metadata about applications, files, components, patches, and more.
Session Manager
Use Session Manager to manage your edge devices and Amazon Elastic Compute Cloud (Amazon EC2) instances through an interactive browser-based one-click shell or the AWS CLI. Session Manager provides secure and auditable management of edge devices and instances without the need to open inbound ports, maintain bastion hosts, or manage SSH keys. Session Manager also helps you comply with corporate policies that require controlled access to edge devices and instances, strict security practices, and fully auditable logs that detail access to edge devices and instances. but it is cross-platform and easy to access with one click for the end user. Access to edge devices and EC2 instances. Advanced instance level must be enabled to use Session Manager. For more information, see Enabling Extended Instance Tiers.
Run Command
Use Run Command to manage managed node configurations remotely and securely at scale. Use Run Command to perform on-demand changes such as updating applications or running Linux shell scripts and Windows PowerShell commands on a target set of tens or hundreds of managed nodes.
State Manager
Use State Manager to automate the process of keeping managed nodes in defined states. State Manager can be used to ensure that managed nodes start with specific software on startup, join a Windows domain (Windows Server nodes only), or be patched with specific software updates. I can do it.
Patch Manager
Use Patch Manager to automate the process of applying security and other types of updates to managed nodes. You can use Patch Manager to patch operating systems and applications. (On Windows Server, application support is limited to application updates released by Microsoft.)
This feature scans managed nodes for missing patches and updates that Can be applied individually or too large groups of managed nodes using tags. Patch Manager uses patch baselines. This includes rules for automatically approving patches within days of their release, and a list of approved and rejected patches. By scheduling patching to run as a Systems Manager maintenance window task, you can install security patches on a regular basis or patch managed nodes at any time as needed.
For Linux operating systems, you can define a repository to use for patch operations as part of a patch baseline. This allows you to ensure that updates are installed only from trusted repositories, regardless of which repositories are configured on the managed node. For Linux, you can also update any package on managed nodes, not just those classified as OS security updates. You can also generate a patch report that will be sent to an S3 bucket of your choice. For a single managed node, the report contains details of all patches on the machine. For the All-Managed Nodes report, only a summary of missing patches is provided
Distributor
Use the dispatcher to create packages and deploy them to managed nodes. Distributor allows you to package software or find AWS-provided agent software packages, such as AmazonCloudWatchAgent, to install on nodes managed by the Systems Manager. After installing a package for the first time, you can use the distributor to uninstall and reinstall newer package versions, or to perform in-place updates that add new or changed files. Distributors publish resources such as B. Software packages on nodes managed by the Systems Manager.
Hybrid Activations
To set up your servers and VMs as managed instances in a hybrid environment, create a managed instance activation. Once activated, you will receive an activation code and ID. This code/ID combination works like an Amazon Elastic Compute Cloud (Amazon EC2) access ID and secret key to provide secure access to the Systems Manager service from your managed instances.
Operations Management
Incident Manager
Incident Manager is an incident management console that helps users mitigate and resolve incidents affecting their AWS-hosted applications.
Incident Manager improves incident resolution by notifying responders of impact, highlighting relevant troubleshooting data, and providing collaboration tools to get service back up and running. Incident Manager also automates response planning and enables response team escalation.
Explorer
Explorer is a customizable operational dashboard that reports information about your AWS resources. Explorer presents an aggregated view of operational data (OpsData) across AWS accounts and AWS Regions. In Explorer, OpsData contains metadata about Amazon EC2 instances, patch compliance details, and operational work items (OpsItems). Explorer provides context on how OpsItems are distributed across business units or applications, how they evolve over time, and how they change by category. You can group and filter information in the explorer to focus on items that are relevant to you and require action. If you identify high-priority issues, you can use OpsCenter, a feature of Systems Manager, to run automation runbooks and troubleshoot those issues.
OpsCenter
OpsCenter provides a central location for operations engineers and IT professionals to view, investigate, and resolve operational work items (OpsItems) related to AWS resources. OpsCenter is designed to reduce mean time to resolution for issues affecting your AWS resources. This Systems Manager feature aggregates and standardizes his OpsItems across services and provides contextual investigation data about each OpsItem, his related OpsItems, and related resources. OpsCenter also provides Systems Manager Automation Runbooks that you can use to troubleshoot issues. You can specify custom data that can be searched for each OpsItem. You can also view auto-generated summary reports on OpsItems by status and source.
CloudWatch Dashboards
Amazon CloudWatch dashboards are customizable pages in the CloudWatch console that allow you to monitor your resources in a single view, even if they are spread across different regions. You can use CloudWatch dashboards to create custom views of your AWS resources' metrics and alarms.
0 notes
Text
5 Tips for Effective Data Center Network Management
Consistently, a huge number of server farm supervisors deal with a few issues, for example, diminished execution proficiency and surpassed limit while attempting to oversee server farm networks successfully. To effectively regulate a server farm organization, IT groups need to concentrate on geography, perhaps look for a way to improve on the most recent principles and gauge the effect of impending innovations like SDN.
As per the Server farm Innovation, it is assessed that in excess of 40,000 individuals at any one time had to sit in virtual sitting areas in the wake of hurrying to a site publicizing medical care benefits.
Such cases feature the way that server farm chiefs need to guarantee their organization the executives is exceptional for their methodology to remain in front of hierarchical requirements.
The following are five ways to guarantee powerful server farm network the board which will assist with setting up a nimble, adaptable and versatile organization for your business.
Augment Capacity Limit
Scope organization has forever been a fundamental part of server farm network the executives. Yet, presently, in the virtual period and distributed computing, scope quantification has become much more basic. It is beyond difficult to utilize customary strategies for putting away information. Organizations need to update them by utilizing the most recent innovative progressions.
This implies having the option to store countless data of interest, data sources and measurements and have the option to dissect them to anticipate future necessities and changes in future.
Legrand Server farm Arrangements (LDCS) upholds the rising requirement for organizations to store and develop their current framework.
By providing a variety of items including server racks, organized cabling, rack sensors and fiber optics, associations can constantly stay in their prime.
Consequently, supervisors are encouraged to go for stockpiling and limit devices that will assist them with examining the information such that they can disregard every single imaginable result and diminish cost and hazard also.
Update Server farm Engineering
Conventional innovation had information streaming in a north to south organize, which would frequently make bottlenecks as information would pass; subsequently upsetting your stream.
New advances, as hyper-met framework, assist in guaranteeing information with moving from east to west. One such design is Leaf-Spine engineering that can help multi-directional information stream. This type of design likewise helps in lessening the quantity of links and switches.
Leaf-spine is likewise advantageous for intelligent systems administration of server farms as data is shared all the more straightforwardly and productively between gadgets.
While refreshing your organization geography, make a point to incorporate leaf-spine design to assist you with utilizing Programming Characterized Organizations (SDN).
Oil Your Server farm Foundation The executives Programming
A very much oiled server farm is the way to productive organization the board. It assists in lessening with gambling, expanding the uptime, and quicker conveyance of administrations and applications at a negligible expense.
Server farm Foundation The board (DCIM) likewise helps in working on information by and large. It assists the administrator with running effective server farm tasks and further develop framework arranging and plan.
Boost Uptime
Assuming you're taking a gander at expanding your effectiveness and boosting your efficiency, foundation the board is fundamental. It helps in gathering patterns, provides details regarding information and furthermore screens any infringement. This will alarm you, and you can follow up on any deviations ahead of time.
Increment Efficiency
An oiled framework will likewise assist you with expanding efficiency by saving, moving, adding, and making changes to make computerized work process the executives.
Drive Proficiency
Foundation the executives programming helps in building feeds, IT and non-IT loads for guaranteed computation for your server farms to guarantee productivity.
Asses Fiber Optic Links
Assuming you need fast associations, fiber-optic links can be your deliverer. Unions and IT patterns will quite often pressure the copper links out.
On the off chance that you at any point expected to link a connection north of 330 feet, you ought to be know about fiber optic links as copper links can arrive at 330 feet. Then again, fiber optic links can uphold up to 700 feet.
Fiber optic links have a SX based optic which is normal in little structure factor pluggable (SFP). It is a standard model for 1 GbE, SFP+ modules and consider 10 GbE in a similar structure factor.
Advanced Symptomatic Observing (DDM) is assisting fiber optic links with developing. As data will go through the wire, IT groups can investigate connections and switch issues with DDM. It is fundamental for make changes in accordance with fiber optic links as more transfer speed will be expected in future.
Gather Supplemental Information
Frequently server farm supervisors face issues and get cautions when there is an issue on the organization, however don't have the important data to examine it.
For circumstances like these, actually take a look at the logs on the gadgets and servers. Ensure they have sufficient room to store information and occasions over a lengthy period. Reinforcement your information for making it more effective.
You ought to likewise catch the organization traffic that goes in and out from gadgets on your significant foundation list. Attempt to find who is interfacing with your framework and what information is being gotten to.
In a perfect world, you ought to have a log of use explicit data. What documents are being gotten to, information base questions, and furthermore the pages that are being visited on your site.
0 notes
Text
Microsoft Authorised Reseller for Corporate Sales in Mumbai | Productivity is so critical for business. Having the choice to make, group up and communicate | Orient Technologies Mumbai
0 notes
Text
The 7 Key Benefits of Using Office 365 for Business
Productivity is so significant for business. Having the option to make, team up and convey consistently makes any association more compelling. Approaching efficiency apparatuses that empower individuals to take care of their responsibilities all the more effectively - and from anyplace - makes associations dexterous and allows them to contend in their area.
Office 365 is Microsoft's efficiency suite with instruments like Word, Trade, Succeed, SharePoint, Groups and the sky is the limit from there. Since Office 365 is cloud-based, the unlimited experience can be gotten to from anyplace, on any gadget, for however long they're on the web.
The devices in Office 365 complete one another and cooperate consistently, so it's an unquestionable necessity for any business.
The following are seven critical advantages of Office 365.
Access Files Anyplace
Office 365 permits your association to store every one of the files in the cloud. This implies they can be gotten to on any gadget, from any area with a web association. For associations where portable working is fundamental, having the option to get to all the applications and files you want when out of the office is significant.
Secure Cloud Storage
Office 365 is a thoroughly safe climate with strong safety efforts set up, similar to two-factor verification, which guarantees unapproved individuals can't get to your files in the event that they end up getting on your gadget. Danger location and against malware implies security dangers are recognized and halted right away, which is especially significant for associations that arrangement with classified information or data. Utilizing Office 365 methods your business is allowed to work with no worries for security.
Further developed Correspondence
Office 365 gives clients instruments to keep correspondence unified and clear across Skype and Standpoint. Skype for Business allows you to hold phone calls and gatherings with staff and outer organizations anyplace on the planet, so you can continuously team up and convey paying little mind to distance or time contrast. Groups gives a texting capability where remarks can be added and files transferred simultaneously, which is helpful for cross-office joint effort and while co-writing archives. You can likewise 'at' individuals in Groups so they get a warning that a remark is pointed straightforwardly at them. This large number of elements mean you can be in consistent and quick contact with groups and people any place they are found and whenever. Yammer is one more element of Office 365 which goes about as a sort of informal community for your association. By posting on your organization 'news channel' you can quickly message the whole labor force, and staff get an email warning when there is another post so messages aren't missed. Anybody can remark on a post, and you can make different 'diverts' in Yammer for various purposes, so you don't necessarily in all cases need to post to the whole organization.
Unsurprising spend
Office 365 is paid for on a for each client, each month premise, similar to a membership. The expense of your licenses relies upon the degree of usefulness you decide for your business. Different endeavor levels incorporate various applications and items, which directs the expense of each permit. Paying per client, each month gives you an anticipated active and assists you with planning your IT spend for the year ahead. Overhauls are remembered for the expense of your licenses, so there are no unforeseen or extra expenses. Assuming that you purchase your licenses through Center, you can likewise change the quantity of permit you have whenever, on the off chance that you recruit or individuals leave, for instance. Like that, you are rarely over-authorized and there is no waste.
Business Progression
With files put away in the cloud and routinely supported up, your association keep on working as would be expected on account of a debacle at the office. Regardless of what befalls your actual gadgets, your email, files and information are securely put away in the cloud. Trade likewise has recuperation highlights which mean individual messages or even whole inboxes can be reestablished if necessary. Regardless of the circumstance, it very well may be the same old thing on the off chance that you're utilizing Office 365.
Programmed overhauls
All the fundamental applications like Word, Succeed and Viewpoint are incorporated and work online without the need to introduce any product. Overhauls are performed naturally at foreordained spans, so you don't need to stress over being on the most recent form; that will happen consequently. The cost of purchasing new programming is additionally destroyed as updates are remembered for the membership for your Office 365 licenses.
Incorporated Cooperation
Office 365 allows you to share post boxes, schedules, contacts and alter archives progressively through cooperative devices. Sharing schedules in Return implies you can see who in your association is accessible when, so you can plan gatherings that work for everybody, first time round. Shared letter drops mean various individuals can get to a similar post box, so messages can be sifted to land in the common post box and will not be missed. SharePoint is one more necessary apparatus for empowering joint effort. Records that are saved here can be gotten to and dealt with by any staff part, and shared as a connection in email. Various clients are likewise ready to alter records put away in SharePoint progressively, which makes co-writing simple. You can see who is in the record whenever and even where they're working thanks to minimal hued banners which recognize every client.
Office 365 offers online adaptations of the most famous instruments like Microsoft Word, PowerPoint, Succeed, and OneNote. For any business, the scope of highlights given by Office 365 are unrivaled. The month to month membership model presented for Office 365 makes it more straightforward for organizations to purchase an arrangement that is reasonable for their size and number of clients, and keep on working to the surprise of no one.
0 notes
Text
Apple Authorised Reseller in Mumbai India | Searching for a new laptop, but you are not sure about switching from Windows to macOS | Orient Technologies Mumbai
0 notes
Text
Top Benefits Of Using Apple Macbook
Searching for a new laptop, but you are not sure about switching from Windows to macOS? Or are you intrigued about why MacBook models are so notable, regardless of the excessive cost?
Here are the Top 5 Benefits Of Using Apple MacBook That You Should Know
1. MacBook is easy to understand
Apple is notable for the ease of use of its products. MacOS works naturally and all options and programs are not difficult to track down. Particularly when you're utilized to the Mac ecosystem since you as of now have an iPhone or iPad, for example. All products by Apple function admirably together. For example, you can begin composing an email on your iPhone and finish it on your MacBook. What's more, what about involving your iPad as a second screen for your MacBook? The choices are endless.
2. MacBook is trustworthy
MacOS is the operating system by Apple itself and is specially built for Mac PCs. Thanks to this, software and hardware function admirably together. This makes the MacBook truly steady. Also, you're less susceptible to viruses with macOS, because there basically aren't as many viruses for macOS. Yet in addition because your MacBook has more underlying security. Apple updates macOS consistently, which keeps the system secure and trustworthy. Like that, you can get started with an inner serenity.
3. MacBook is durable
A laptop is truly an investment or truly a venture. That's the reason you need it to keep going as far as might be feasible. The casing of a MacBook is made of aluminum. This is a strong and durable material that stays nice for long. It's not shocking that the MacBook generally scores well in terms of durability. A MacBook likewise has a high exchange esteem.
4. MacBook has a decent battery
Despite tests for durability, there are likewise tests that focus on the normal battery life. The MacBook generally scores well on these tests as well. It effectively lasts a whole working day on a fully-charged battery. So don't worry if you forget to bring your charger in the morning. Apple MacBook models with an Apple M1 chip last as long as 20 hours on a single charge. How quick the battery runs empty depends on how extensively you utilize your MacBook.
5. MacBook looks perfect
What's more, not immaterial the design. Because let's be honest, looks do matter. The moderate design and the smooth lines with adjusted edges. Apple keeps it straightforward, and it works. The MacBook feels strong and trustworthy, despite the thin design. Another is the light weight. Because of this, you can easily take it anywhere with you without hauling a weighty sack around all day.
Now, Let's Understand That How You Can Choose The Right Mac For You in 2022?
Apple’s Mac product line has changed a lot recently, and if you’re searching for a new Mac, you have different options to consider. For specific people, it’s a fundamental choice, but for others, the choice can be more complex.
You could require a desktop Mac, and as of now you have four options for that type of PC. If you want a laptop, you have couple of options in models, components, and screen sizes. But you might want to use a laptop on your desk as well, growing the amount of possibilities. Now we are going to discuss how you can choose the right mac for you according to your use case.
Apple’s M1 & M2 processors
The best change in recent years regarding the decision of new Macs is the release of Macs running Apple’s M1 processors, which started in late 2020. In mid-2022, Apple had changed all of their Macs but one to these in-house chips. Apple’s initial demonstration of these new computers was stunning to the point that Mac users couldn’t believe what they were seeing. The speed and power consumption promised was astounding, and this was borne out in benchmarks and genuine usage.
The first M1 models included a processor with eight cores; consider of a core as a mini-processor. A significant part of the work we do utilizes just a single core, but demanding tasks use multiple cores working all the while.
The second round of M1 Macs – utilizing what Mac is calling the M1 Pro and M1 Max processors – focused on the MacBook Pro. With two models, 14″ and 16″, these are genuine pro laptops. They come with 8 or 10 cores, In addition to extra realistic centers, and allow you to add more memory than the first M1 Macs.
And in March, 2022, Apple brought out the M1 Ultra, in its then-new Mac Studio. This processor is comprised of two M1 Max processors, utilizing a die-to-die interconnect, giving equal processing.
In June 2022, Apple declared the first Macs with the next-generation M2 processor. While this new processor doesn’t show immense jumps in that frame of mind to the M1, it is an improvement, notably in its ability to offer up to 24 GB RAM. The 13″ M2 MacBook Pro holds all the features of the past model, with a speed bump, and Apple claims that it is 1.4x faster than the M1 model.
The M2 MacBook Air is an absolutely new interpretation on Apple’s lightest laptop. Gone is the aerodynamic wedge shape, and it currently seems to be two iPad Pros stacked together. Still fanless, the M2 MacBook Air adds a Fluid Retina display, MagSafe charging, and brags as long as 18 hours of battery duration.
With just about all of Apple’s product offering right now updated to the association's own processors, you don’t have to worry about getting a Mac with a backward-looking Intel processor (aside from on the off chance that you need one). You have options no matter what, and in basically all possible form factors. The first wave of M1 Macs, conveyed in late 2020, included the MacBook Air, the 13″ MacBook Pro, and the Mac mini. The 24″ iMac was released in May 2021, and in October 2021, Apple added two MacBook Pro models, a 14″ and a 16″. Then came the new Mac Studio, in March 2022, a moderate-sized computer between the Mac mini and Mac Pro; this last option is the only Mac to not yet have Apple silicon. Finally, the initial 13″ M2 MacBook Pro and MacBook Air show great promise toward the future of Apple’s processors.
Do you want to enjoy the user-friendliness of Apple, but do you have a proper work area? Your safest bet is probably a Mac desktop. This Apple product gives you all the benefits of macOS and won't look out of place on your desk either. At Orient Technologies, We are the best Apple Authorised Reseller in Mumbai India. If you are also in search to buy an Apple product, do contact us for detail information.
0 notes
Text
AWS Cloud Service Provider in Mumbai | Amazon Web Organizations (AWS), the cloud platform introduced by Amazon.com Inc (AMZN), has transformed into a giant component | Orient Technologies Mumbai
0 notes
Text
Amazon Web Services & Why Is It So Productive?
Amazon Web Organizations (AWS), the cloud platform introduced by Amazon.com Inc (AMZN), has transformed into a giant component of the e-commerce business portfolio. In the second quarter of 2021, AWS got a record $14.8 billion in net sales, addressing just over 13% of Amazon's total net sales. Having filled steadily in the 30% area the past several quarters, AWS is a pioneer to other cloud computing platforms like competitor Microsoft Azure.
So What Is AWS Exactly?
AWS is contained of different cloud computing products and services. The significantly profitable division of Amazon gives servers, storage, networking, remote handling, email, flexible development, and security. AWS can be broken into three crucial things: EC2, Amazon's virtual machine service, Glacier, a minimal cloud storage service, and S3, Amazon's storing system.
AWS is so gigantic and present in the computing world that it's far overwhelmed its competitors. An independent analyst reports that AWS has more than third of the market at 32.4%, with Azure following behind at 20%, and Google Cloud at 9%.
AWS has 81 accessibility zones in which its servers are found. These serviced regions are isolated to allow users to define geographical boundaries on their services (if they so choose), yet also to give security by expanding the physical regions wherein data is held. All things considered, AWS crosses 245 countries and areas.
Cost Savings
Jeff Bezos has compared Amazon Web Services to the service associations of the mid 1900s. Surprisingly long time back, a factory requiring power would build its own power plant when the factories were able to buy power from a public utility, the need for costly private electric plants subsided. AWS is endeavoring to move associations away from physical computing technology and onto the cloud.
Generally, associations looking for a great amount of storage would need to genuinely build a storage space and keep up with it. Storing on a cloud could mean denoting a large amount of storage space that the association would be capable "develop into". Building or buying too little storage could be disastrous that the business took off and exorbitant if it didn't.
Similar applies to computing power. Associations that experience flood traffic would generally end up buying stacks of capacity to help their business during active times. On off-peak times - tax accountants for example - enrolling impact lays unused, yet costing the firm money.
With AWS, associations pay for what they use (pay-as-you-go). There's no upfront cost to develop a storage system and no need to estimate usage. AWS users use what they need and their costs are scaled normally and suitably.
Flexible and Adaptable
Since AWS's cost is changed considering the customers usage, startups and small associations can see the prominent benefits of including Amazon for their computing needs. Indeed, AWS is ideally suited for building a business from the bottom as it gives all the tools vital to associations to start up with the cloud. For existing associations, Amazon gives low-cost migration benefits with the objective that your ongoing establishment can be seamlessly moved over to AWS.
As an association grows, AWS gives resources for assist with expansion. As the business model allows for adaptable use, customers will not at any point need to contribute energy considering whether they need to reconsider their computing use. Believe it or not, aside from budgetary reasons, associations could realistically "set and neglect" all their computing needs.
Security and Reliability
Apparently, Amazon Web Services is essentially safer than an association working with its own website or storage. AWS at this point has numerous data centers across the globe that are continuosly monitored and strictly maintained. The upgrade of the data centers ensures that a disaster striking one region doesn't cause permanent data loss worldwide. Imagine in the event that Netflix some way or another figured out how to have its staff reports, content, and backed-up data centralized on-site on the eve of a typhoon. Disorder would result.
Actually, confining data in an easily identifiable region and where numerous people can sensibly get access is hasty. AWS has endeavored to keep its data centers as hidden as posible, tracking down them in distant regions and allowing access simply on an essential basis.
The data centers and all of the data contained in that are shielded from interferences, and, with Amazon's contribution in cloud services, power outages and potential attacks can be promptly identified and easily relieved, 24 hours a day. The same can't be said for a small association whose handling is managed by a singular IT specialist working out of a colossal office.
Analysis of AWS
While the success of AWS is unquestionable, critics of the service say Amazon is abusing its control of the market slice by participating in anti-competitive behavior. This investigation has come from open-source data base makers who ensure Amazon is copying and consolidating software that was at first made by other tech associations.
One such association, Flexible, recorded a case against Amazon for allegedly violating trademark laws. A declaration conveyed by the association ensures "Amazon's behavior is clashing with the guidelines and values that are especially critical in the open-source eco-system."
The Conclusion
Amazon Web Services is a cash cow for Amazon. The services are working up the computing world in the same way that Amazon is changing America's retail space. By assessing its cloud products extremely cheaply, Amazon can offer affordable and flexible services to everyone from the latest start-up to a Fortune 500 association across the globe.
To drive business esteem from the cloud, you need to re-evaluate your drive, and accomplish something beyond cloud projects. You need a comprehensive way to deal with your cloud change. At Orient Technologies with our skills and experience, you can utilize the speed, scale and financial matters of the Amazon Web Services while keeping away from normal traps.
0 notes
Text
List of Companies Providing Microsoft Azure Cloud Services Mumbai | Since associations have changed to work from home and hybrid working conditions, measurements for Microsoft 365 | Orient Technologies Mumbai
0 notes
Text
Cloud Computing Services Mumbai | At the point when we think about insider threats, our brain commonly goes to disappointed employees that have specific goals | Orient Technologies Mumbai
0 notes
Text
5 Helpful Tips To Protect Your Microsoft 365 Data
Since associations have changed to work from home and hybrid working conditions, measurements for Microsoft 365 information breaks have expanded at a stunning speed. The numbers show that paying little mind to industry and size of the organization, M365 breaks might be surprisingly normal.
Is Your Association's Data Secure?
As much as Microsoft 365 has been the trusted "go-to" stage for relationship all over the planet, it could similarly be a not-really stowed away security commitment for those that have chosen to neglect the shortcomings. The legitimization for looking the substitute way appears to increase with additional unassuming associations. The tendency that they are pretty much nothing or don't house a satisfactory number of data seems to shield the decision to dismiss even the most fundamental wellbeing safety efforts.
"43% of ongoing digital goes after straight forwardly designated Small Businesses."
The fact of the matter is cyber criminals additionally realize that independent companies maintain this viewpoint. With refined attack plans, high level devices, and unmonitored induction to open associations, the current cyber criminals are devouring private companies.
What should truly be possible?
Microsoft 365 has made a gigantic weak side for associations accepting that Microsoft itself is totally managing security with updates and fixes, in any case, this isn't correct. Developers, Ransomware, unplanned/harmful eradication are a couple of examples of things that aren't covered by M365's local security organizations.
“Over the recent a year, 85% of Microsoft clients have experienced an email data break.”
With new dangers continually arising, there won't ever be where an association can say that they are completely secured. What we can do is make layers and continually update the security includes that we really use to assist with safeguarding our delicate data.
Here we have few tips to help you with keeping your Microsoft 365 Data Protect:
5 Helpful Tips To Protect Your Microsoft 365 Data & Why It's Important
1. Limit Administrative Accounts
Most IT specialists would teach against the creation with respect to administrator accounts basically for the way that when an administrator account is compromised the results can be outrageous. An open administrator record can permit induction to an association's entire structure. If unapproved access is disguised an aggressor can uninhibitedly confirm and include respects however they see fit.
2. Configure Your Security Settings and Find your Microsoft Secure Score
Microsoft 365 has a couple of security settings that occupants can empower to support their M365 data protection. Inside the better than ever Microsoft 365 security place, associations can acquire bits of knowledge on their ongoing level of assurance by survey their Microsoft Secure Score.
The Microsoft Secure Score measure's an associations security position to assist with recognizing which regions need to carry out greater improvement activities to all the more promptly adjust to Microsoft's best security practices. By breaking down your standard development and your ongoing security settings, proposals will be given steps on the most capable method to work on your score and lay out better security act. Microsoft Secure Scores will give a full investigation on the most capable strategy to diminish the general risks and the weaknesses right now present inside your association.
Activities are coordinated into a few gatherings:
* Identity (Azure Active Directory records & roles)
* Gadget (Microsoft Defender for Endpoint protection)
* Apps (Email and Cloud apps, including Office 365 and Microsoft Cloud App Security)
Your lead account with administrative distinctions will actually need to see the score and arrange your security settings appropriately. Using this assistance not just prescribes which security settings to turn on, however it might likewise show you settings that you might not have even known about.
3. Update Your Data Loss Prevention Policy (DLP)
Disregarding the way that Microsoft 365 executes its own security and offers different devices and organizations to address various things we notice, huge quantities of the local safeguards are not enough generous to offer unique confirmation against the consistently changing threats that associations are by and by standing up to. Consider how remote workers are relying upon email and virtual particular procedures more now than any time in ongoing memory. This suggests most associations are going up against more noticeable external data bets:
* Inadvertent data transparency
* Wiping out/Data mishap
* Unapproved access
* Threatening risks.
Uniting these risks with break uncovering guidelines, necessities for insurance qualifiers and reputational costs being referred to, compares to fundamentally more strain for associations to think about consistence and detailing and record sharing policies set up.
"In general, only 5% of associations' envelopes are properly protected."
4. Raise The Level of Employee Awareness Training
This one is indeed a continuation of refreshing your DLP. While utilizing rules and setting up associations to assist with deterring messages that could accidently share fragile data from going out, employee care planning will be crucial to help remote, and in-house, delegates remain fixed on solid areas for a first culture. Microsoft occupants need to have understanding that diligent tutoring is vital. Regardless of what the extra layers of associations security, procedures and updates from Microsoft, things can regardless get away from everybody's notification and finally a human either taps on something they shouldn't have or includes fragile materials in a risky manner.
The goal of Employee Awareness Training is to transform your most vulnerable association into your most grounded security asset.
"95% of online insurance breaks are a result of human slip-up."
5. Bolster Your Security Layers
Depending upon business grade antivirus alone isn't definitively seen as a strong way to deal with keeping Microsoft 365 information out of the hands of digital lawbreakers. However, when you add layers of protection, it can start to grow your association wellbeing posture and make limits to assist with supporting your securities.
Basic yet strong choices can be added with devices and associations, for instance:
* Turning on Multi-Factor Authentication (MFA) to give two-step actually take a look at processes.
* Using Virtual Private Networks (VPN) while communicating distant gadgets.
* Uilizing Password Vaults to ensure complex passwords are secured and not reused across stages.
"40% of private endeavors experienced no less than eight hours of individual time because of a computerized break costing a typical of $1.56 million in disasters."
Data breaks are expanding at an upsetting rate since computerized criminals grasp where the low-lying organic product is as they keep on focusing on M365 as a fundamental wellspring of unguarded data among free endeavors. Overall, M365 is still, certainly, an extraordinarily helpful and important instrument for associations. Nevertheless, associations need to fill in safety efforts to guarantee their data is securely gotten to, made due, and noticed, especially while giving remote and cross breed working circumstances.
Take your Microsoft 365 Protection Further with Live Monitoring the entire day/365
Complex security risks and current work spaces are persistently undermining the security of our progressive associations. Therefore our business grade organizations blow away local security plans.
Composed Managed Detection and Response (MDR) helps you with taking care of:
* The entire day/365 live observing.
* Added security.
* Danger Response.
* Maintain Stronger Security Policies.
* Detailing and Compliance designed for your association.
Find out how we at Orient Technologies can help with protecting your Microsoft Data. Designed to assist you with skillfully managing and secure your M365 account, our powerful Microsoft 365 Security Software and Security Analysts actively monitor for risks, research alerts, discard false positives, and provide guided response and remediation to your association.
0 notes
Text
Best Practices to Secure Your Business From Insider Threats
At the point when we think about insider threats, our brain commonly goes to disappointed employees that have specific goals to play out a malicious demonstration. What we don't consider are the employees representing a threat because of absence of information and carelessness.
An insider threat is a security risk that starts from inside the association. These threats could be the current or previous team, business partners, or contractors who approach basic and delicate data inside the association's network, and PC frameworks.
What are the Types of Insider Threats?
Understanding such insider risks will help you with better shielding your data from the risk associated with it. There are different sorts of insider threats that are organized depending upon the motivation behind the person being referred to.
1. Reckless
These insiders or pawns don't have the assumption to seriously put the association at risk, but by acting in problematic ways, they could do so non-maliciously. For example, passing on devices unattended or capitulating to a scam. Representatives who don't have authentic data and care may incidentally tap on an inconsistent association that can infect the work environment structure with malware.
2. Malicious
Also suggested as "turncloaks". An insider who certainly plans to take malicious data for money related or individual increments. Overall, an employee or contractor who has real licenses yet is misusing their entry for benefit. For example, it will in general be a disappointed employee whose goal is to sabotage the association by taking and selling safeguarded development.
3. Third - Party
These insiders can be employees for recruit or merchants that an association has given an induction to its association or some likeness thereof. These insiders compromise an association's security through misuse or dangerous usage of business assets.
Signs of an Insider Threat
There are few markers that would propose an insider risk, it might be at an association level or a specialist's change in behavior. Here are few signs of insider risk:
* Tries to sidestep security.
* Being in the working environment during after work hours.
* Showing disappointed lead toward partners.
* Violation of corporate policies.
* Downloading gigantic amounts of data.
* Getting to fragile data that are not related with their work.
* Use of unauthorized storage devices.
* Data collecting and replicating records from fragile coordinators.
Tips and Best Practices to Prevent Insider Threats
a. Monitor User Behavior and Manage Accounts
Noticing client behavior logically to expect abnormal client behavior associated with potential data theft, anticipated harm, or misuse. Another strategy for restricting the insider threats is to monitor and manage your employee accounts. It limits how much data open to employees who has the assumption to finish a threatening attack against the business.
This similarly means that attackers or cybercriminals who have gotten to a employee's record will have confined approval to get to all edges of the's association's network.
b. Maintain Security Policies
Your association should also carry out a security procedure that will safeguard your business against insider risks. The security procedure will include methods and cycles that will prevent and perceive any harmful activities.
The methodology should similarly include bits of knowledge concerning access to individual data about employees and demonstrate who can access to what data, under what conditions, and who might they anytime at some point share the information with.
Besides, employees are as of now bringing their own devices and can access the association network through their devices. Shaky devices can permit your business data and assets exposed. Promising you have endpoint security installed can direct the risks.
c. Give Security Awareness Training
Despite what kind of security plans your association places assets into, you can't easily predict a human error and restrict risk. Clients are at this point considered as a frail association with network security thus the meaning of planning and real guidance.
Get employees to properly look out the differentiation among strong and weak passwords, motivate them to learn and be aware of stunts, phishing mails, and the use of individual devices inside the office.
Everyone in the association should be realize about your security approaches and frameworks and record them to prevent insider risks.
d. Conduct Proactive Network Monitoring
Each district, division, and corner of your business should be noticed including the on-premises, and cloud environment. the entire day, consistently noticing will allow you to quickly recognize events that will require a brief response.
Furthermore, it will increase consideration regarding your employee's exercises, for example: attempts to records past working hours or downloading an unnecessary application.
Insider risks are harder to identify compared to external risks, they come undetected by firewalls and interference area systems. Malicious insiders, specifically, who are have a lot of familiarity with your association's security measures can without a doubt avoid detection.
Any business, gigantic or little can encounter the evil impacts of an insider risk. Orient Technologies as an IT service provider, we are centered around getting your data and defending your business from any kind of association threat. If you want to protect your business from insider threats, Reach out to us today!
0 notes