Text
Week 9 Analysis: Reagan
INCIDENT RESPONSE:
We don’t want to do things instinctively. We want to know more about the situation and figure out what to do.
Honeypots: Deceive attackers, watch what they are doing and then catch them.
CASE STUDY (protecting against gun violence):
Prevention
- Pre-crime / profiling
- Mental health services: solve issues with people’s mind, psychology.
- Rejection, social alienation, not being part of the tribe.
- Security Guard
- Metal Detector
- Design Buildings
- Information gathering
Mitigation (Incident Response)
- Drills, protocols, alarms
- Lockdown
- Access control (suspension)
- More exits
Format Strings
#include <stdio.h>
int main(void)
{
printf(”Hello, world!\n”);
return 0;
}
First argument to printf -> Format string
I have %d oranges\n. Pass 5 in there.
If you use %x, you can use it to read data in stack frame in hex.
Use %s to read contents of a string pointer (address)
use %n to write bytes written to stdout thus far to a memory location.
In simple words, format string vulnerability allows a user to pass a string which has format string identifiers inside and use this to gain unauthorised access like reading / writing data in any memory location. this can be done once the attacker knows where the printf frame is finishing and where the printf format parameters start.
0 notes
Text
Week 9 Lecture Notes
Morning Lecture:
Just Culture: Instead of blaming an individual, you look at the whole system.
Upsides of blaming people:
You become happy, one person take care of, easier.
You can sack them.
Downsides:
You don’t fix the actual problem.
“Shoot the messenger”: sack / kill the person the person who brings the bad news.
You can’t just keep firing people. It will never fix the problem
NOTE: Adopting this culture worked for Qantas. They put a very strong emphasis on Just Culture, and because of this they are such a reputable airline in Australia and the world. They have been topping the rankings of air safety for a long time in Australia due their highly effective company audits focussing on improving the system, not just one individual.
A just culture refers to a values-supportive model of shared accountability.
Else: Fault culture, which is full of toxic people.
SECURITY ENGG:
What is it about engineering culture that makes it so successful?
Time:
things being built over time
ability to observe failures and learn from them
high frequency errors, and medium frequency errors
Methodology & Standards:
Best practices
Not starting from scratch
Ex: Takoma bridge didn’t follow such practices and was built from scratch
It was wavy and unstable as a result. it got destroyed.
Using a checklist, which stops you from overlooking things.
Examples:
3-Mile island: 2 valves, no one noticed it. A new person came in he could see it. If there was a standard procedure in place, this could have been found out faster.
Cockpit recordings: For planes that crashed, you can hear what the pilots were doing prior to crashing: following a checklist of things to ensure plane survival.
Creativity / Dealing with uncertainty
Thinking outside the box
Dealing with issues and unpredictibilty
Testing
Science when done well
following procedure to prove it wrong
continuous improvement
more confidence in yourself and your work.
We want to find mistakes
keep evidence
Software Development:
Ship, ship, ship: Be agile
At the cost of shedding security
RICHARD’S LIST (Additional to the ones already mentioned)
Focus on process
Review at every level (even your own work)
Conflict of interest
Professionalism
Serve the profession, not just your boss.
Dealing with conflict of interest
You’re a son, a father, an employee.
You have make priority decisions some times.
Quantifying results:
Danger: Not everything worth measuring can be measured. Not everything that can be measured is worth measuring.
Assurance: Confidence on our beliefs and work quality
Closing the loop
Feed forward system, so many things
No feedback
Instead give feedback after on forward cycle is complete
You check the idea
Listening and improving
350 ALARMS WENT OFF
Something went wrong
Only 8 alarms were important
Focus on the right things
Security is state of mind
SYSTEM PROPERTIES:
Solving problem is noticing little things and fixing them?
No
You need to understand the entire system.
What is coherence?
We need the system to be:
Coherent
Every part of the system is working on achieving the same thing. No waste of work or effort. They are doing meaningful things to achieve something.
Not complex
Not coupled
Wargames Clip
Pull humans out of the loop
Automate things
systems are not perfectly designed
Preconditions behave as expected before postconditions
Attackers’ job: make preconditions be in an imperfect state.
Human creativity is needed to solve such problems.
ASDs are good, they can follow a checklist
But just ASDs are no good. We need humans to be able to think out of the box, which ASDs are not capable of.
China Syndrome: Consequences of having humans in the loop
Just knowing your technical stuff is not enough to be a capable engineer. We need to know sociology, psychology etc. in order to understand people. This is a highly important skill to have.
To be a security engineer, you need to think overall, removing mist and focussing on important things.
Society itself is a system
Society being hacked / spoilt
Nazi propaganda
Trump selection for president
Brexit
Security is end to end:
From start of voting
Chaining of votes (Russia kicks in here)
To collection
To announcing
Work to undermine limits.
Anyone in power, works in increasing their power, subverting control.
Ruler of Galaxy:
Multilateral Security: Each layer controls the layer beneath it
Person at the top controls everything. Single Point of failure.
One brain with many bodies.
Better to have multiple brains and people
You don’t get to know easily that you’re the ruler. You don’t want to be the ruler
Someone who wants power is excluded from having power.
Assange & Free speech:
You want free speech but not if it disagrees with your beliefs and situations.
Powerful people don’t like speech against them.
Self driving Cars and Trolley Cars:
Cars kill people
We never have a perfect system With computers controlling, we could reduce this. Pay the price.
Computers have to make ethical decisions
Kill a boy or an old lady?
This seems difficulty for them to decide
How can we ever be truly safe?
How does a car know speed-limit?
Central DB => GPS
If you hack it, then you can play with the limits and cause harm.
Or cars work it out from signage: Computer Vision
Third Parties’ Security
Trust: End to end security.
No trusted third parties
Building system, at some point you say use trusted third party.
Then no need to worry about security.
But who can you trust?
Moles / insiders
Good inside / bad outside
What can you do?
need walls everywhere
trusted third parties break trust?
Trusted third party vs roll your own security (not always possible)
Make choice
We set things up so they fail, but we ensure when they fail the impact is low.
Examples:
Buying missiles, have a backdoor built-in to the missile
To stop the builder from being attacked
YOUR FUTURE:
A new world forming
World needs Cyber Security Engineers.
EFFECTIVE COMMUNCATION:
Be brief
Explain simply
All about the listener not the speaker.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Evening Lecture (Reverse Engineering Seminar):
Most of the things in the seminar were pretty much self explanatory except Anti RE. So I am explaining only anti RE techniques:
It is used to ensure that your code / executable is not crackable. There are various ways you can do this:
Don’t release the debug build.
Gives attacker information of the inside of your executable
Trick the disassembler:
Excessive jump instructions or Dummy instructions
Movfuscator is a tool that does this. Makes the binary highly confusing to read.
Overlapping of instructions
Used to hide the actual program structure. Instead of seeing the function return, you make the disassembler continue, and it sees the return at the incorrect place. This is because it is never able to figure out that the actual return instruction was mixed in between another instruction
Like: add eax, 0xc3
A previous instruction jumps to the 0xc3, which is the return instruction in x86. Disassembler cannot figure this out.
CHINA SYNDROME MOVIE was the last part. It is assessible content, as situations from the movie could form case studies.
0 notes
Text
Security Everywhere - Sydney Light Rail testing
While coming back home from this week’s tute on Friday, I saw the Sydney Light Rail in test near Kensington. I was on my way towards Central station in the bus, when I saw this. They had put strong metal bars in place to keep all human activity out of the test area. I wanted to take a picture but I couldn’t in time, hence I am relying upon some of the web images.
What I am trying to link this to is physical security and also the risk it poses for people who are not careful near this. This is not related to cyber security but still poses physical threat to people, which is why I thought I should share this as security in general life. Also, as I work near George Street, there is another light rail in test there, which is even less protected, and hence people have to be really careful around this while walking between streets.


0 notes
Text
Week 8 Module Activity - Google Yourself
I downloaded information from Facebook to see what kind of data do they store about me. The findings were very interesting:
My payment history included the debit card I used with first 4 and last 5 digits exposed. This seemed a bit worrying to me as it is never too good to reveal so many digits in a credit card number.
0 notes
Text
Security Engineering skill development & Teamwork
Up till now, I have greatly enhanced my hacking and security engineering skills. I attribute a lot of this to overthewire challenges, participating and contributing in CTFs and doing extended activities each week. I got introduced to many different concepts and tools in SecSoc CTF held in UNSW and I am glad that I participated in it.
I ended up almost solving the reverse engineering challenge and contributed to each task that my team solved. I have been able to solve buffer overflow challenges as well in MIPS and solve some of the challenges released by Caff for exam preparation. I would consider this as strong demonstration of my security skills.
0 notes
Text
Time Management Week 8:
This week I was getting a little late for the tute, in which I had to present my Something Awesome project. I made my tutor aware of this beforehand, so that no issues arise and also confirm whether this will not result in me losing marks. I confirmed this and this was hence sorted quickly, over Slack.
0 notes
Text
Week 8 Activity: Spot the fake
I thought about common things that I have experienced in every day life regarding fakeness.
Two of the most notable things I can recall are:
Fake Social Networking Accounts: There have been many examples of people faking someone else’s facebook or twitter accounts to imitate them and bring their reputation down by posting awkward things.
For Prevention:
Don’t trust profiles which you don’t know in person.
Look for the sign “Verified” or something similar to indicate its authenticity.
Fake Online stores: There are fake online stores, vouching to offer certain goods at attractive prices, to just steal your money. They look like genuine online retailers and use names which sound authentic and in some cases even use stolen ABN numbers.
For Prevention:
In order to prevent against these, always do your research on the online store, and ask other people for their experiences. Online reviews can also help.
Always make payments using “https:” protocols to ensure your details remain safe.
0 notes
Text
Analysis Week 8 Case Study: The Stargate Problem
I found out more about this problem, through the content given on OpenLearning and through this blog a student made some years ago: https://www.openlearning.com/u/steffenjohansen/blog/Week7TutorialTheStartgateProblem/
I thought about this problem, and came with the answer of using some sort of mechanism that allows the ghost and his human friend to figure out if the message is authentic and maintains integrity.
To do this I thought of using MAC and Public and Private Key authentication mechanism. Using MACs they can find out if the alien intervened with the message at all or not. However they both will have to agree upon a way to produce a MAC from a message. This algorithm and key needs to be discussed beforehand via the alien which could cause loss of integrity, if the alien tells the wrong algorithm or key to one person on his will.
To counter this, and see whether the alien is trustworthy, we could use ciphers to communicate between the two. We would send a caesar cipher with a known shift key and then decrypt it at the other end. We should make sure we talk about such things in code words with the ghost, so that the alien does not have an idea on what is happening (that this is a shift key, and the message is caesar cipher encrypted). Like instead of saying “This is a key for a caesar cipher that we’ll use the communicate”, we could say “This is the key for talking”. Then later we could come with the ghost (only), write him down the choice of ciphers for ex: A. Caesar B. Vignere etc. Then we’ll erase the answers, and ask the ghost on what he chose and confirm. We’ll be able to know if alien is lying is he says something like ‘K’ which we never had as an option. With this initial communication channel setup, rest of the things become easier, we can then use MACs and public-private keys using this cipher communication.
0 notes
Text
Week 8 Lecture:
I missed the lecture in the morning, and so I made up for it by reading the official lecture notes and the video.
10am - 12 pm
Root Cause Analysis
Blame last person or group
Company Culture
The whole system / organisation
Human Weaknesses
Misdirection
We are bad at picking the right features for focus
We often look for a few things over a large landscape
For example, the 2 card swipe trick, we don’t focus on where the trick is happening, but on what the person wants us to see (misdirection)
Attackers try to get us to focus somewhere else
Honesty
Commander in Cheat - book about how Trump cheats at golf with his tiny hands
Humans lie often, but seem to appear truthful.
Group-think syndrome
People when put in groups start thinking and behaving differently than if they were alone / not in a group.
Confirmation bias
We seek evidence which agrees with what we believe, and tend to go against things that go against our beliefs, even though they might be true.
6pm - 8pm
SEMINAR TALKS:
Privacy:
Right to privacy is the right to be free from undue surveillance.
With advent of technology, we think we are safe and a lot of us think about the same, but unknowingly we release information without our knowledge. Attackers can harvest this information and use it against us. Therefore we need to be very careful with what we release on the internet.
This can be seen on various internet apps, like:
Facebook
Instagram
Snapchat
Countermeasures:
SIGNAL BLOCKING ON PHONES:
Using signal blocking with foil paper, we can block bluetooth signals which may otherwise cause eavesdropping.
Police can access your phone metadata without any warrant, so signal blocking may be a good idea for journalists and politicians.
BEST PRACTICES FOR ONLINE SECURITY:
Using incognito mode on Chrome:
Deletes cookies after use.
Use VPN
to hide your internet activity from the ISPs and routers. Also Hide your IP and identity which could leak your location.
Encrypts all your activity on top of HTTPS.
Onion Routing:
Multiple layers (skins) of encryption around an IP packet. Each node on the way takes one layer off to see where to send this packet to next.
Each node doesn’t know enough on its own to be able to tamper or manipulate your data.
Only the end end target server gets the unencrypted packet.
Disadvantages:
Timing attacks: Nodes can use timing of receiving and sending packets to identify which received packets correspond to the packets they sent. Using this cross-reference they can isolate communication messages.
Richard’s lecture
SECURE SYSTEMS: 3-Mile Island
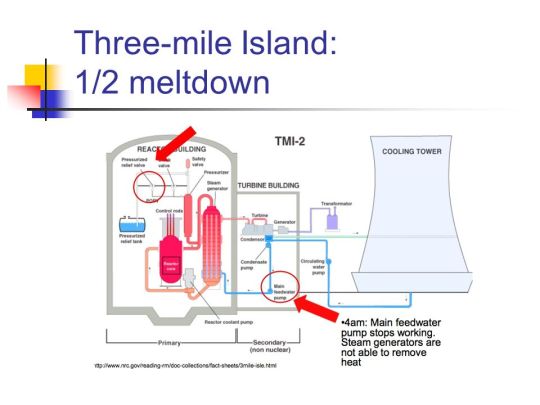
The red part is the nuclear reactor chamber, abstracted away from the rest of the systems.
It is very hot and submerged in water
The yellow / blue systems interface with the red one, heated by the hot liquid in the red, and are used by turbines to turn them
Some water leaked out of the water system to the pneumatic system (Reactor)
As more water started pouring in, the reactor could cause breakdown of water into Hydrogen (highly combustible) and Oxygen (spreads fire quick). A tiny spark could cause an explosion.
This caused the feedwater pumps, condensate booster pumps, and condensate pumps to turn off causing the steam generators to stop working. With steam generators off, the heat and pressure on reactor coolant system increased causing emergency reactor shutdown (SCRAM).
Note: I researched on the 3-mile island on Wikipedia: https://en.wikipedia.org/wiki/Three_Mile_Island_accident
0 notes
Text
Week 8: Something Awesome Submission
Submission requires a two minute demo and analysis afterwards by the tutor to have a better look at what we have done. We are marked on the criteria we proposed.
This is worth 8 marks, and the whole job application is worth 40 marks.
During the demo, everyone was keen to know what someone else has done. I ended up explaining to many students how a VPN works due the in-depth analysis I had done. I explained them this in an easy to understand way. I also explained a hard overthewire challenge to someone in a similar way.
0 notes
Text
Same Origin Policy - Something Awesome Project:
I conducted a more detailed analysis on SOP. Using this, I was able to find out how internet protects sites from keeping information confidential and not allowing one website to access data of another.
To explain, when you make a request to a website, your origin becomes equal to the hostname of the website you want to go to. Browser now understands the request is coming from a domain on the website, and can therefore render data without any problem.
If the same request were to come from a different origin, the request might succeed (GET, POST request) but it won’t return any data in the body as the browser will detect the difference in the origin between the two. An example of this is, if you you navigate to a website, which in turn runs a script to make a request on your behalf (the script will run on your browser). This script can run, but the origin will be different, and hence no data will be displayed by the browser. As a result, the script cannot read data or your cookies for that domain. This way, your data, cookies are protected from unauthorised access and also protecting data of one website from another.
The diagram below illustrates the above concept:
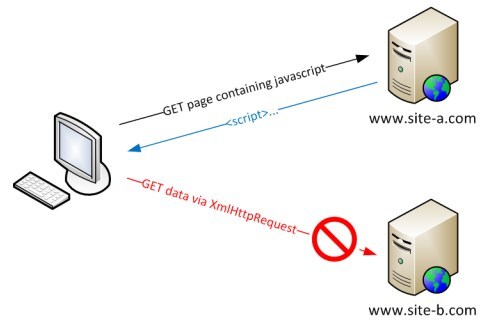
You navigate to www.site-a.com, which returns a script to you. This script tries to access data from another website www.site-b.com using a XHR, but this is not allowed as the origin is still set to www.site-a.com. This script hence can’t even access cookies of that domain.
0 notes
Text
Natas Challenges - Something Awesome Project
Level 0:
This could be found from the source code on web inspection:
Level 0:

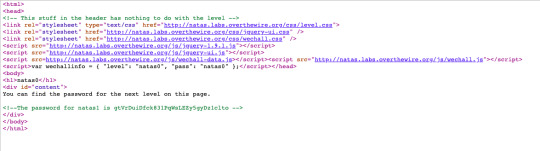
Level 1:
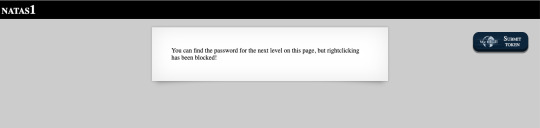
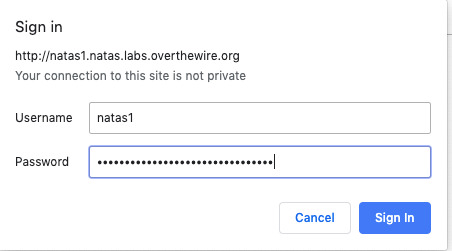
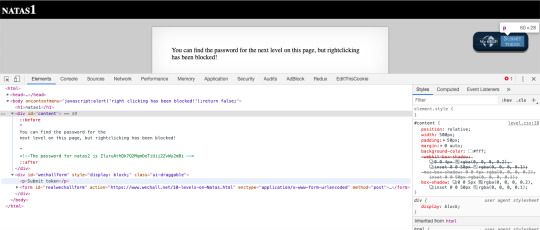
Level 2: Navigating to file system of the server, we can find a text file which contains the password.

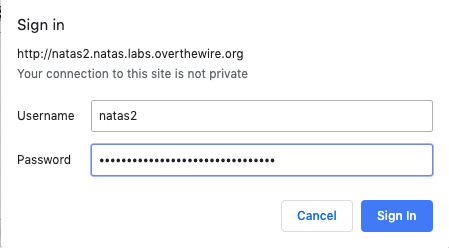

Level 3:
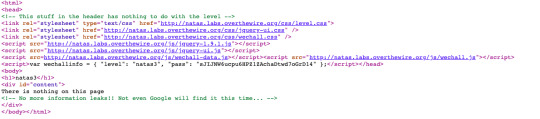
Not even google will find it (robots.txt file cannot be discovered by google)

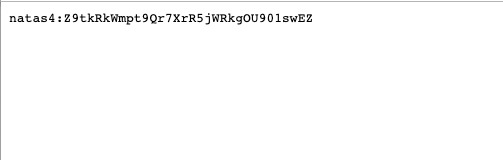
Level 4:
Setup a proxy connection so that each request can be intercepted by Burp Suite. Change referrer of that request and forward:
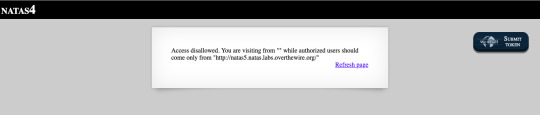

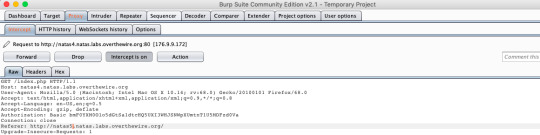
Level 5:
Update the cookie to have value 1 instead of 0. (True instead of False)
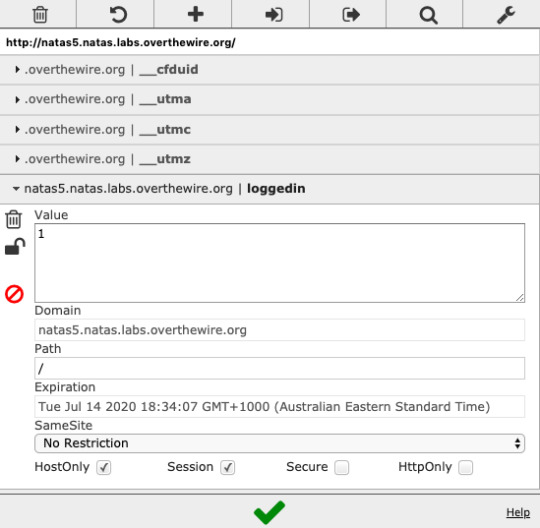
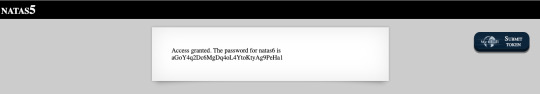
Level 6:
This needs a secret. From source code, we can find a hint that there is a secret.inc file. I try opening it and it has the secret. Using that secret the password can be found.
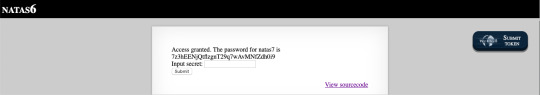


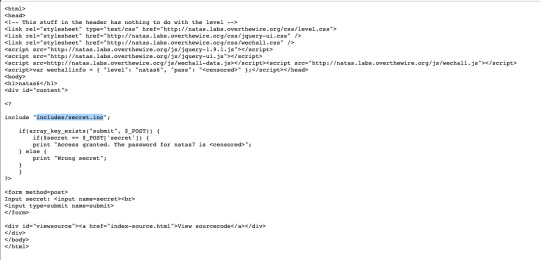
Level 7:
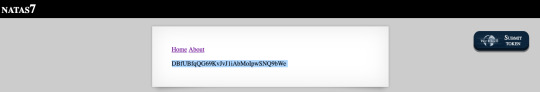
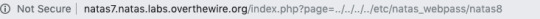
The source code says that password is in etc/natas_webpass/natas8. Putting that in the url, we get the password. This was discovered by navigating to home page and about page and finding out how the url changes.

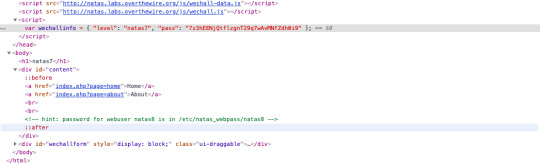
Level 8:
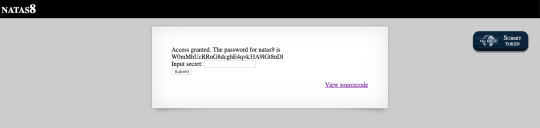
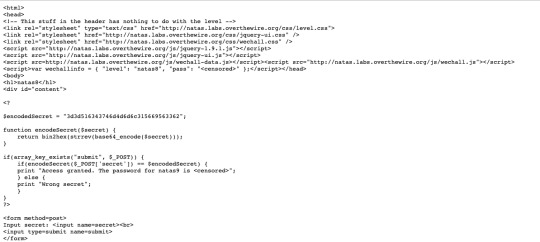
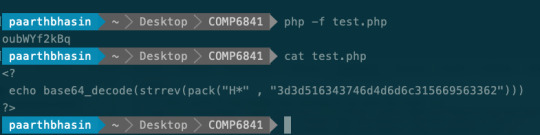
Decrypt the secret given using PHP methods and input into the secret below, to get the password for 9.
Level 9:
This is command injection:
Put the following command in search:
I found out the directory structure of the server using command injection with ls command.
> /dev/null ; cat /etc/natas_webpass/natas10
> /dev/null ; causes grep output to be sent to /dev/null, followed by showing natas10 password:
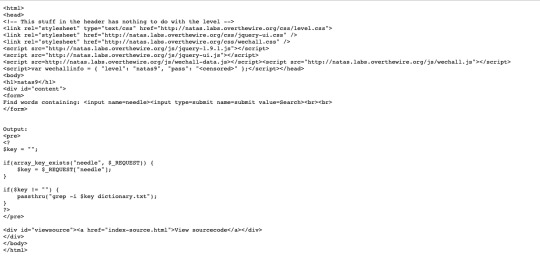
Level 10:
This time, they are escaping special characters, so command injection is still possible but restricted.
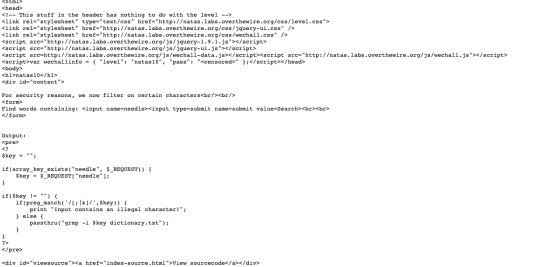
Do this search .* /etc/natas_webpass/natas11
Using this, grep searches for any character in the above file and dictionary.txt
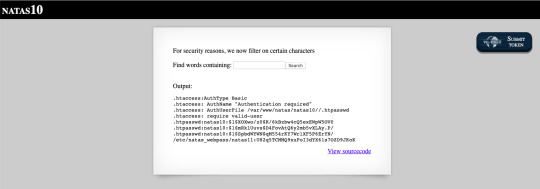
0 notes
Text
UNSW Login System - Something Awesome Project
Today I have been trying to figure out how major UNSW services like Moodle, myUNSW are doing authentication. It seems they are all using CAS (Central Authentication Service).
I captured the authentication loop using chrome extension “Web Sniffer”:

The POST Request above is sent to the CAS server at ssologin.unsw.edu.au with our user credentials. This gives a 302 redirect with a service ticket meaning sucessful authentication. This authentication is done using protocols like Kerberos, LDAP or Active Directory. These protocols allow you to find out if the a set of user credentials are valid or not, without you having to maintain a personal database of user credentials. This is done by these protocols. A simple explanation of LDAP using a diagram is shown below:
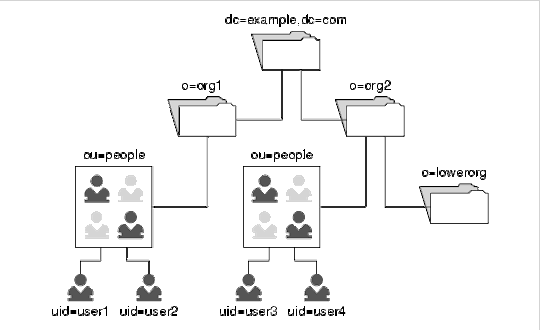
So using this, LDAP will be able to figure out which group are you a part of and if you are valid (configured in LDAP protocol via CAS)
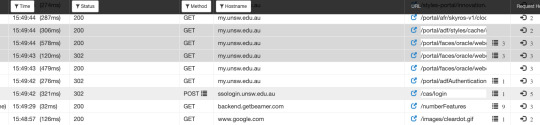
The POST request in the above screenshot is sent to CAS server of UNSW, which gives a 302 redirect. Upon redirection, it goes to my,unsw.edu.au/portal/adfAuthentication with a ticket cookie set by the previous redirect. This cookie is given by the CAS server upon successful authentication. Using this cookie you remain logged into various UNSW services without needing to login again, until the cookie expires.
0 notes
Text
Week 7 Analysis - Snoop
We discussed what information we would like the government to have and what we won’t. Most of this session was students presenting on a few lightning topics to gain bonus marks. Later on we went ahead with the tutorial.
The following ideas were discussed:
What would you want the government to have?
Address: Yes (It doesn’t pose a security threat with the government knowing our address)
Name: Yes (This is like a basic requirement, won’t cause any harm)
Family: Yes (similar to above)
Education: Yes, there is nothing wrong in this
Social Services:
Benefits: They can see whether we are cheating in our taxes, claims etc. or not
Disadvantages: They can discriminate against us in these matters.
Relationships: No (They have no rights to know about this)
Criminal Record: Yes (They should know our criminal records to be able to make sound judgement on our character)
Medical Records: I personally think having medical records of each citizen is going to be too much data and won’t be of any use to them either. This cause also lead to discrimination in voting and other civilian activities.
Passport: This is similar to sharing your address I feel. Passport is issued by the government, so they have the right to this information, I believe.
Finances: On this one, I feel we should only share limited information with the government, not each and every thing we do with our money. Like they shouldn’t know where we have invested money etc.
Race: This, similar to social services could cause discrimination in many things. A person shouldn’t be judged on their race.
0 notes
Text
Something awesome - Caesar Cipher POC
I have implemented encryption and decryption of caesar cipher today. For decryption I have used brute force and have been working on frequency analysis. I have been looking into it but it doesn’t seem that its always correct. For this reason I may end up not using it.
Update (26 July 2019): I used the following python script to give a POC of cracking (decrypting) caesar cipher using brute force and frequency analysis. For now it only works with alphabets, so only try with alphabets not numbers or special characters. You can try input some text to get its encryption and then use it as input for decryption. Because of frequency analysis, the decryption has become has become more efficient.
alphabet = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z'] shift = 4 dictionary = {} import operator def createDict(shift, mode): for i in range(0, 26): letter = alphabet[i] if mode == 'E': dictionary[letter] = alphabet[(i + shift) % 26] elif mode == 'D': dictionary[letter] = alphabet[(i - shift) % 26] def decrypt(ciphertext): plaintext = '' for i in range(len(ciphertext)): if ciphertext[i].lower() in alphabet: plaintext += dictionary[ciphertext[i].lower()] else: plaintext += ' ' print(plaintext) def encrypt(plaintext): ciphertext = '' for i in range(len(plaintext)): if plaintext[i].lower() in alphabet: ciphertext += dictionary[plaintext[i].lower()] else: ciphertext += ' ' print(ciphertext) def brute_force(ciphertext, shif): createDict(shift=shif, mode='D') decrypt(ciphertext=ciphertext) def frequency_analysis(input): freq = {} for i in alphabet: freq[i] = 0 for k in input: if k.lower() in alphabet: freq[k.lower()] += 1 print(freq) maximum = max(freq, key=freq.get) print(freq[maximum]) return abs(ord('e') - ord(maximum)) # Compare shift with ‘e’ as it is most frequent letter. if __name__ == "__main__": print("Choose mode: Decrypt (D) or Encrypt (E): ") mode = input() if mode == 'E': print("Enter string to encrypt: ") createDict(shift=shift, mode='E') inputstring = input() inputstring = inputstring.lower() encrypt(inputstring) elif mode == 'D': print("Enter string to decrypt: ") inputstring = input() inputstring = inputstring.lower() frequency_shift = frequency_analysis(inputstring) print(frequency_shift) if frequency_shift > 0: for i in range(frequency_shift): brute_force(inputstring, shif=i) else: for i in range(26): brute_force(inputstring, shif=i)
The following example saves the decryption by running only 18 times, instead of 26:
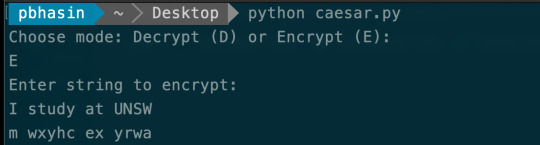
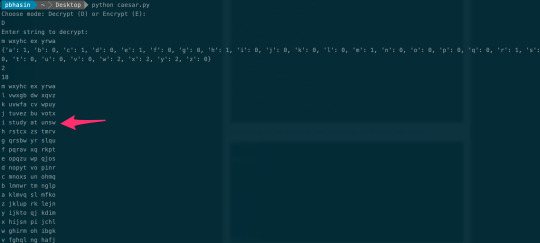
0 notes
Text
Week 7 Analysis - Trump Phishing
Hello Mr. Trump,
I am writing this email to inform you that the votes for the previous meeting held in the Whitehouse to determine what decision should we make regarding the Mexico border issue, has finished and the results are ready. You can view the results <here>.
Best Regards,
Office of Overseas Affairs
0 notes
Text
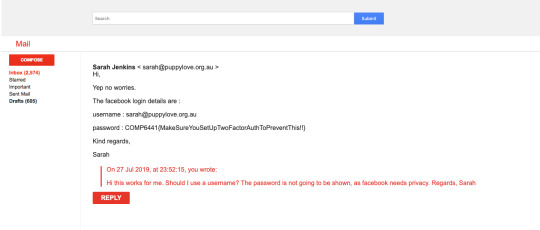
Week 7 Analysis - Email Phishing
This activity was to find out two flags (payment and facebook) by sending certain emails from the link given. I was able to find out the payment flag using the keywords: sarah, facebook and password
0 notes