Don't wanna be here? Send us removal request.
Text
Hack the USV: 2017 (CTF Challenge)
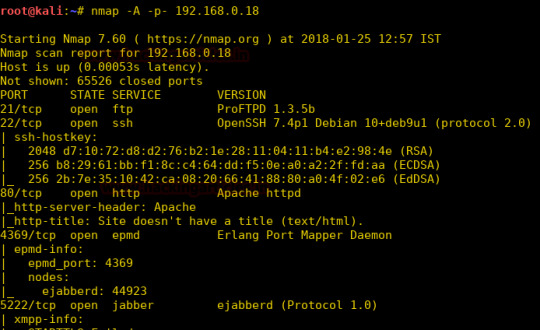
Hello friends! Today we are going to take another CTF challenge known as USV: 2017. The credit for making this vm machine goes to “Suceava University” and it is another capture the flag challenge in which our goal is to find 5 flags to complete the challenge. You can download this VM here. Let’s Breach!!! Let us start form getting to know the IP of VM (Here, I have it at 192.168.0.18 but you will…
View On WordPress
0 notes
Text
Forensic Imaging through Encase
Scenerio: Mr X is suspected to be involved in selling his company’s confidential data to the competitors, but without any evidence no action could be taken against him. To get into reality and proof Mr X guilty, company has requested the forensic services and have come to know all the relevant data is present inside the desktop provided to him.
This article is about getting the forensic image of…
View On WordPress
0 notes
Text
Burpsuite Encoder & Decoder Tutorial
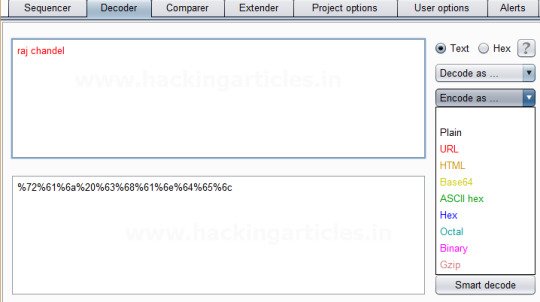
Burpsuite Decoder can be said as a tool which is used for transforming encoded data into its real form, or for transforming raw data into various encoded and hashed forms. This tool is capable of recognizing several encoding formats using defined techniques. Encoding is the process of putting a sequence of character’s (letters, numbers, punctuation, and symbols) into a specialized format which is…
View On WordPress
0 notes
Text
Beginners Guide to Burpsuite Payloads (Part 1)
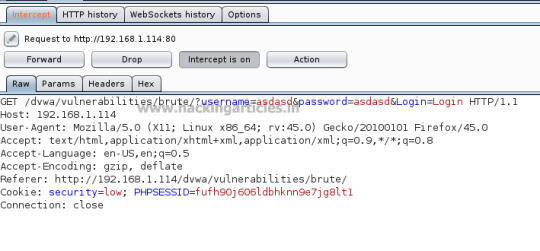
Hello friends!! Today we are discussing about the “Types of Payload in Burp Suite”. Burp Suite is an application which is used for testing Web application security. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. This tool is written…
View On WordPress
0 notes
Text
Hack the VM Cyberry: 1(Boot2root Challenge)

Hello friends! Today we are going to take another CTF challenge known as Cyberry: 1. the credit for making this vm machine goes to “Cyberry” and it is another boot2root challenge where we have to root the server to complete the challenge. You can download this VM here.
Let’s Breach!!!
Let us start form getting to know the IP of VM (Here, I have it at 192.168.0.18 but you will have to find your…
View On WordPress
0 notes
Text
Memory Forensics Investigation using Volatility (Part 1)
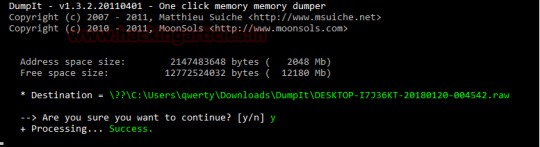
Our focus today is on the Volatility framework, on its capability of analyzing process activity.
The Volatility framework is an open source tool that is used to analyze volatile memory for a host of things. This framework comes with various plugins that can be used by the investigators to get an idea of what was going on in the machine when it was being used. Volatile memory is the primary…
View On WordPress
0 notes
Text
Forensic Investigation of Nmap Scan using Wireshark
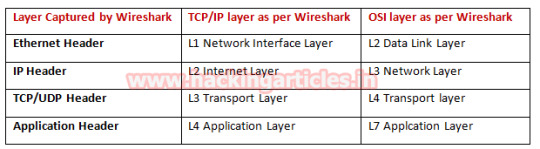
Hello friends!! Today we are discussing about how to read hexadecimal bytes from an IP Packet that help a network admin to identify various types of NMAP scanning. But before moving ahead please read our previous both articles “Network packet forensic” and “NMAP scanning with Wirehsark” it will help you in better understanding of this article.
Requirement
Attacking tool: Nmap
Analysis tool:…
View On WordPress
0 notes
Text
Post Exploitation in Windows using dir Command
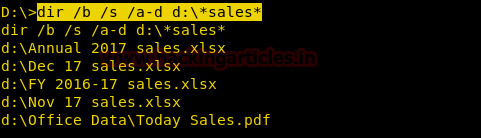
In this article you will learn how to use Windows Command Line Command “dir” and extract files, get information about Number of files of a particular extension and much more using Metasploit framework.
dir Command: It displays a list of a directory’s files and subdirectories.
Syntax
dir [<Drive>:] [<Path>] [<FileName>] [/p] [/q] [/a [[:] <Attributes>]] [/s] [/b]
[/p]:Displays one screen of the…
View On WordPress
0 notes
Text
Forensic Data Carving using Foremost
Foremost is a program that is used to carve data from disk image files, it is an extremely useful tool and very easy to use.
For the purpose of this article we have used an Ubuntu disk image file and the process has been repeated twice. The purpose of doing so was to see if Foremost can carve data out of incomplete disk images as well. We have used Kali Linux but if you want you can install…
View On WordPress
0 notes
Text
How to Configure Suricata IDS in Ubuntu
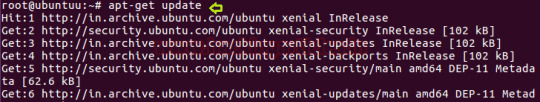
Suricata is developed by the Open Information Security Foundation. Suricata is a high performance Network IDS, IPS and Network Security Monitoring engine. Open Source and owned by a community run non-profit foundation, the Open Information Security Foundation (OISF). Suricata is developed by the OISF and its supporting vendors.
Features
IDS / IPS
Suricata implements a complete signature language…
View On WordPress
0 notes
Text
Detect SQL Injection Attack using Snort IDS
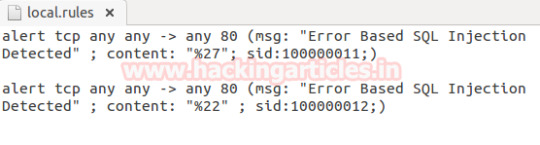
Hello friends!! Today we are going to discuss how to “Detect SQL injection attack” using Snort but before moving ahead kindly read our previous both articles related to Snort Installation (Manually or using apt-respiratory)and its rule configuration to enable it as IDS for your network.
Basically In this tutorial we are using snort to capture the network traffic which would analysis the SQL…
View On WordPress
0 notes
Text
Check Meltdown Vulnerability in CPU

Hello Friends!! You must be heard of the latest vulnerbility “Meltdown” which has been discovered almost in every CPU having intel processessor, from this link you can check list of vulnerable CPU discription. Today we are going to disccuss how to “Check Metltadown vulnerability in any CPU” by using a script.
From Wikipedia
Meltdown is a hardware vulnerability affecting Intel x86 microprocessors …
View On WordPress
0 notes
Text
Network Packet Forensic using Wireshark
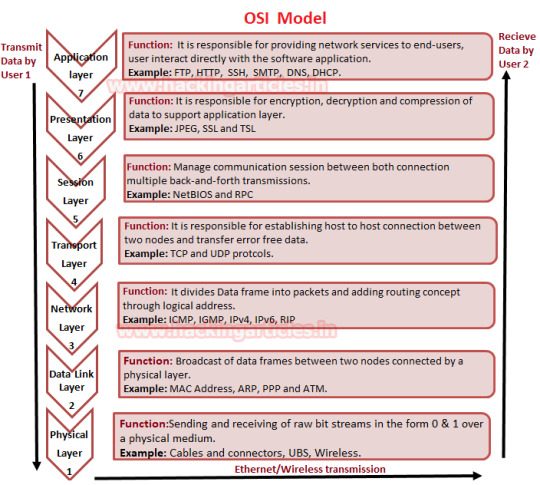
Today we are going to discuss “TCP Forensic” by covering some important track such as how Data is transferring between two nodes, what is “OSI 7 layer model” and Wireshark stores which layers information when capture the traffic between two networks.
As we know for transferring the data from one system to other we need a network connection which can be wired or wireless connection. But in…
View On WordPress
0 notes
Text
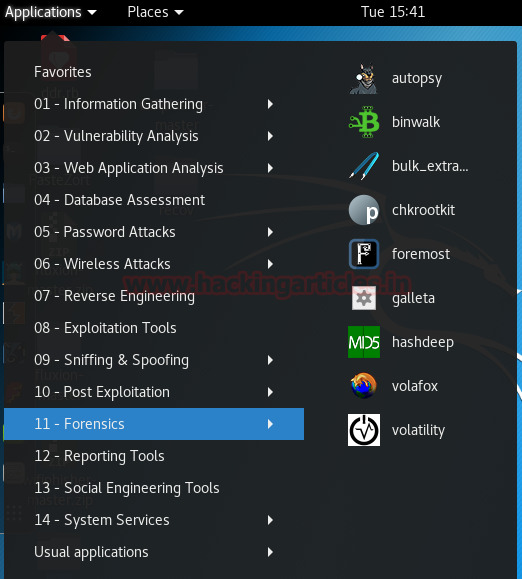
Forensics Tools in Kali
Kali linux is often thought of in many instances, it’s one of the most popular tools available to security professionals. It contains all the robust package of programs that can be used for conducting a host of security based operations. One of the many parts in its division of tools is the forensics tab, this tab holds a collection of tools that are made with the explicit purpose of performing…
View On WordPress
0 notes
Text
Hack the Basic Penetration VM (Boot2Root Challenge)
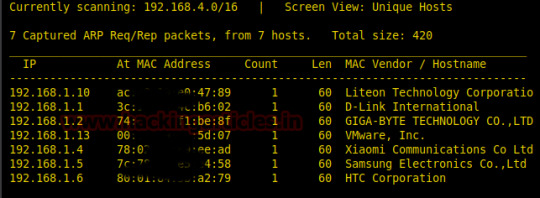
Hello friends! Today we are going to take another CTF challenge known as Basic Penetration. The credit for making this vm machine goes to “ Josiah Pierce” and it is another boot2root challenge where we have to root the server to complete the challenge. You can download this VM here.
Let’s Breach!!!
Let us start form getting to know the IP of VM (Here, I have it at 192.168.1.13 but you will have…
View On WordPress
0 notes
Text
ICMP Penetration Testing with Cat Karat
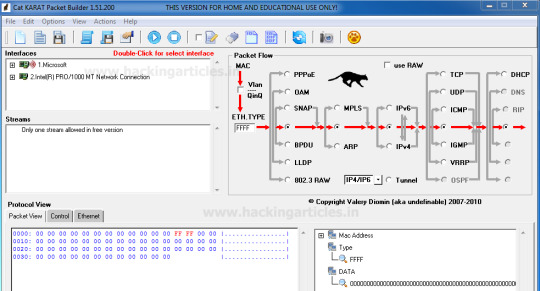
In our previous article we had discussed “ICMP protocol with Wireshark” where we had seen how an ICMP protocol work at layer 3 according to OSI model and study its result using wireshark. Today we are going discuss to ICMP penetration testing by crafting ICMP packet to test our IDS “Snort” against all ICMP message Types using Cat Karat tool, you can download it from http://packetbuilder.net link.
View On WordPress
0 notes