Text
2024's Top Ethical Hacking Course
In the current digital era, ethical hacking is an essential ability for safeguarding data and systems against online attacks. But how can you pick the right course for you when there are so many to select from? Let's take things simple for now.
What is hacking with an ethical bent?
By employing hacking techniques to identify and address security flaws in computer systems, ethical hacking contributes to the prevention of malevolent assaults. It's similar to being a skilled hacker who keeps businesses safe.

Why Take an Ethical Hacking Course?
1. Career boost: ethical hacking skills are in high demand. Completing a course can lead to exciting job opportunities. 2. Skill Development: Learn practical skills to identify and fix security flaws. 3. Certification: Many courses offer certifications that validate your skills and knowledge.
Top Ethical Hacking Courses in 2024
Here are some of the best ethical hacking courses available right now, each catering to different needs and skill levels:
1. Certified Ethical Hacker (CEH) by EC-Council
Overview: One of the most recognized certifications in the field, the CEH course covers various hacking techniques and tools. Pros: Comprehensive and widely accepted. Ideal for those aiming for a career in ethical hacking. Cons: Can be expensive and might require a basic understanding of networking and security concepts.
2. CompTIA PenTest
Overview: This certification focuses on penetration testing and vulnerability assessment. Pros: Great for beginners and those looking to deepen their knowledge in penetration testing. Cons: Less focus on advanced hacking techniques compared to CEH.
3. eLearnSecurity’s eJPT (eLearnSecurity Junior Penetration Tester)
Overview: A hands-on course that emphasizes practical penetration testing skills. Pros: Affordable and offers a practical approach to learning. Cons: Might not be as well-known as CEH but still highly respected in the industry.
4. “The Complete Ethical Hacking Course: Beginner to Advanced”
Overview: A popular online course on Udemy that covers various ethical hacking topics from basics to advanced. Pros: Affordable and accessible with lifetime access to course materials. Cons: May not offer official certification, but great for learning and practice.
5. Coursera’s “Introduction to Cyber Security Specialization”
Overview: Provides a solid foundation in cybersecurity with some focus on ethical hacking. Pros: Offers a broad understanding of cybersecurity with a focus on ethical hacking. Cons: Less specialized compared to other dedicated ethical hacking courses.

How to Choose the Right Course
Assess Your Skill Level: Beginners might start with more foundational courses, while experienced individuals can opt for advanced certifications. Check Your Budget: Courses vary in cost, so choose one that fits your budget and offers value for money. Consider Your Career Goals: If you're aiming for a specific job role, select a course that aligns with those requirements.
0 notes
Text
Understanding Ethical Hacking: What You Need to Know
The term "ethical hacking" is getting more and more popular in today's digital environment. What does it actually mean, though? Is it risky, and how is it carried out? Let us put it in layman's words.

What is hacking with an ethical bent?
Penetration testing, white-hat hacking, and ethical hacking are terms used to describe the process of testing a computer system, network, or online application to identify security flaws before malevolent hackers, or black-hat hackers, may take advantage of them. The tools and methods used by cybercriminals are also used by ethical hackers, but they do so with consent and for legitimate purposes.
Consider it a cordial security examination. Similar to how you could undergo a physical examination to identify any abnormalities early, ethical hacking assists companies in identifying and resolving possible security risks.
How is cybercrime carried out?
1. Obtaining authorization: Ethical hackers need to obtain express authorization from the organization they are testing before they can start any testing. This guarantees that their actions are permitted and lawful.
2. Attack Planning: Before anything else, ethical hackers lay out their strategy. They collect data on the system they intend to test, examining elements such as security protocols and network architecture.
3. Testing the System: Ethical hackers try to take advantage of holes in the system by using a variety of instruments and methods. They might attempt to log in without authorization, look for software flaws, or stage a hack.
4. Reporting Findings: Following their testing, ethical hackers produce a thorough report outlining their findings. Information about vulnerabilities and solutions is provided in this report. Assisting the company in enhancing its security is the aim.
5. Resolving Issues: The organization addresses and resolves the vulnerabilities found in the report. An ethical hacker may also run additional tests to make sure everything is safe.

Is it harmful to hack ethically?
When done correctly, ethics hacking is safe. The key is to identify security flaws and address them in a controlled and compliant manner. Generally speaking, ethical hacking is safe for the following reasons:
Permission-Based: Since ethical hackers never operate without authorization, they are never in violation of the law.
Controlled Environment: To avoid unintentional disturbances, testing is conducted in a controlled environment.
Improvement-focused: Improving security is the main objective; causing harm is not.
But in order to minimize dangers, it must be done correctly, just like any other security measure. Inadequate ethical hacking practices have the potential to unintentionally interfere with operations or reveal private data. Because of this, it's critical that ethical hackers have expertise and adhere to best practices.
To sum up, ethical hacking is essential to preserving strong cybersecurity. Ethical hackers are crucial to maintaining the security of our digital environment because they find and address flaws before malevolent hackers may take advantage of them.
0 notes
Text
The Fundamentals of Ethical Hacking: How It Safeguards Your Online Life
In a world where cyber threats are a constant worry, ethical hacking has become a key player in safeguarding our digital lives. But what exactly is ethical hacking, and how does it work? Let’s break it down in simple terms.

What Is Ethical Hacking?
Ethical hacking is like having a friendly neighborhood watchdog who helps you secure your home. Instead of just keeping watch, they actually test your security measures to make sure they're strong. In the same way, ethical hackers test the security of computer systems to find vulnerabilities before the bad guys can exploit them.
Why Is It Important?
Think of your computer system like a house. If you leave doors and windows unlocked, burglars can get in easily. Ethical hackers help you find and fix those weak spots before the burglars do. This process is crucial for businesses and individuals alike to protect sensitive information from cybercriminals.
How Does Ethical Hacking Work?
Here’s a simple rundown of the ethical hacking process:
1. Planning and Scoping Goal Setting: The ethical hacker and the organization agree on what systems will be tested and what methods will be used. Permission: Unlike malicious hackers, ethical hackers always get permission before testing any system. This is usually done through a legal agreement.
2. Reconnaissance Gathering Information: The ethical hacker collects as much information as possible about the target system. This can include details about network architecture, software in use, and user practices.
3. Scanning Identifying Vulnerabilities: Tools are used to scan the system for known vulnerabilities. This is like checking the locks and windows of a house to see if they’re easy to bypass.
4. Exploitation Testing weak spots: ethical hackers try to exploit the identified vulnerabilities, but only in a controlled and safe manner. This step is crucial for understanding how serious the vulnerabilities are.
5. Reporting Documenting Findings: After testing, the ethical hacker creates a detailed report outlining the vulnerabilities discovered, how they were exploited, and recommendations for fixing them. Fixing Issues: The organization then uses this report to address the security issues.
6. Re-testing Verification: Once fixes are applied, ethical hackers may be asked to test the system again to ensure that the vulnerabilities have been properly addressed and no new issues have been introduced.

The Role of Ethical Hackers
Ethical hackers are often called "white hats" in contrast to "black hats," who are the malicious hackers. White hats use their skills to improve security and protect information, while black hats exploit vulnerabilities for illegal gain.
Why You Should Care
In today’s digital age, cybersecurity is more important than ever. Whether you’re running a business or just managing personal accounts, ethical hacking helps ensure that your information remains safe from those who might want to misuse it.
By understanding and utilizing ethical hacking, you’re not just protecting your data; you’re helping to build a safer digital environment for everyone. It’s like having a trustworthy friend who keeps a vigilant eye on your security, ensuring that you can go about your online activities with peace of mind.
So, the next time you hear about ethical hacking, remember—it’s all about making sure that the digital world stays secure, one test at a time!
0 notes
Text
Unlocking the Secrets of Ethical Hacking: A Beginner’s Guide
Hi there, nerds that love technology! Have you ever wondered about the work and education of ethical hackers? Think of ethical hackers as the cyberworld's superheroes, utilizing their abilities to defend us against the bad guys. Let's investigate ethical hacking and what you may expect to learn if you choose to pursue this fascinating profession.

Ethical hacking: What is it? Penetration testing and white-hat hacking are other names for ethical hacking, which simulates assaults on computer systems in order to find and address security flaws. Instead of using these flaws to further their own agendas, malevolent hackers employ their expertise to assist enterprises in fortifying their defenses and safeguarding confidential data.
What Is Learned by Ethical Hackers?
1. Recognizing the Fundamentals of Cybersecurity
An understanding of cybersecurity is essential for ethical hackers before they can dive into hacking techniques. This entails being aware of the typical risks and weaknesses that could impact networks, systems, and applications as well as how they operate.
2. Acquiring Knowledge of Various Hacker Types
Malicious hackers employ a variety of hacking techniques, thus ethical hackers must be aware of these as well. They can effectively defend against possible threats by using this knowledge to predict them.
3. Learning the Trade's Tools
A variety of specialized tools are used by ethics hackers to test and examine systems. Software for network scanning, online application testing, and vulnerability sniffing is among them. You may come across popular tools such as Nmap, Metasploit, and Wireshark.
4. Making evaluations of vulnerabilities Finding holes in systems is one of the main responsibilities. This include looking for security holes, examining possible attack vectors, and figuring out how to take advantage of these flaws.
5. Acquiring Knowledge of the Ethical and Legal Limits
Ethical hackers have to follow the law and moral principles. This entails protecting privacy and confidentiality and acquiring the required authorization prior to testing systems. It's critical to understand the rules and legislation pertaining to cybersecurity.
6. Carrying Out Penetration Exams
Penetration testing, sometimes known as "pen testing," is the process of modeling cyberattacks in order to assess a system's security. These tests are carried out by ethical hackers in order to find vulnerabilities before the bad guys do. This procedure entails organizing, carrying out, and recording the tests. The results are then reported to assist in enhancing security protocols.
7. Examining and Documenting Ethical hackers are required to evaluate test results and produce reports that are easy to understand and implement. These papers include suggestions for strengthening an organization's security posture in addition to assisting them in understanding the dangers they face.
8. Keeping abreast of trends
Since the hacking industry is constantly changing, ethical hackers must keep up with the newest methods, resources, and trends. They can remain ahead of emerging dangers and make sure they're employing the best tactics thanks to this constant learning.

What makes ethical hacking crucial?
Because ethical hackers find and address flaws before malevolent hackers can, they are essential to cybersecurity. By doing this, it contributes to the preservation of confidence, the protection of sensitive data, and the security of online activity.
0 notes
Text
Understanding Ethical Hacking: Securing the Digital World
In the linked world of today, cybersecurity is more important than ever. In this sector, "ethical hacking" is a fundamental idea. What precisely is ethical hacking, though? Allow me to explain it simply.
What is hacking with an ethical bent?
Penetration testing, ethical hacking, or white-hat hacking is the deliberate probing and testing of computer systems, networks, and applications to identify and address security flaws before malevolent hackers may take advantage of them. In contrast to malevolent hackers who utilize vulnerabilities for their own benefit, ethical hackers operate under the authorization of the system proprietor and strive to enhance security.

What makes ethical hacking crucial?
Hackers are continuously searching for new vulnerabilities to attack, and cyber threats are always changing. Finding these flaws and guaranteeing the security of an organization's data and systems are major tasks for ethical hackers. They assist in averting data breaches, monetary losses, and harm to one's reputation by identifying and resolving security vulnerabilities. Businesses can preserve consumer trust and adhere to legal obligations by using ethical hacking techniques.
How Do Cybercriminals Act Ethically?
Ethical hackers find vulnerabilities using a range of instruments and methods. Usually, their procedure consists of:
1.reconnaissance.
Obtaining knowledge about the target system, including its IP address, domain names, and network architecture, is known as reconnaissance.
2. Scanning: This process involves using tools to find open ports, services, and possible security holes in the system.
3. Obtaining Access: Trying to get into the system by taking advantage of vulnerabilities that have been found.
4. Maintaining Access: determining the maximum amount of time they can enter the system undetected.
5. Clearing Tracks: Eliminating any traces of their actions to make sure their testing doesn't interfere with the system's regular operation.
6. Reporting: Recording results and offering suggestions to strengthen security.

The morality of hacking
Hackers that are ethical adhere to a rigid code of behavior. Before testing any technology, they must get express authorization, and they must stay inside the owner's bounds. They must also responsibly disclose vulnerabilities and refrain from using them for their own gain. They contribute to the creation of a safer online environment for all users by upholding these moral standards.
ethical hacking is a crucial practice in the fight against cybercrime. It bridges the gap between security vulnerabilities and robust defenses, making the digital world a safer place for all of us. Whether you're a business owner or an IT professional, understanding and supporting ethical hacking can significantly enhance your cybersecurity posture.
0 notes
Text
The Value of Ethical Hacking: A Worthwhile Pursuit
The rise in sophistication of cyber threats and the expansion of the digital realm have led to an increase in the popularity of ethical hacking. It entails hacking into computers and other devices lawfully in order to assess an organization's security. Here, we'll examine the significance, professional prospects, and personal fulfillment of ethical hacking as why it's a worthwhile and fulfilling career path.

The Value of Hacking Ethics Protecting sensitive data and preserving the integrity of digital infrastructures depend heavily on ethical hacking. In a world when cyberattacks and data breaches are common, ethical hackers are essential in spotting vulnerabilities and fixing them before malevolent hackers can take advantage of them. They support organizations by:
Prevent Data Breaches: Ethical hackers assist in preventing unwanted access to sensitive data, protecting financial and personal information, by identifying and resolving security flaws. Verify Adherence: Strict laws mandating regular security evaluations apply to many businesses. By ensuring that companies follow these guidelines, ethical hacking helps them avoid paying large fines and suffering reputational harm. Preserve Your Image: The reputation of a business might be damaged by a security breach. By guaranteeing that strong security measures are in place, ethical hackers contribute to the preservation of confidence.

Opportunities for a Career in Ethical Hacking There are many different job options and strong demand for ethical hackers in many different industries. To safeguard their assets, enterprises of all sizes—from startups to multinational conglomerates—need knowledgeable ethical hackers. Among the career paths are:
Conduct fictitious cyberattacks as a penetration tester to find and fix security flaws. Assist companies in improving their security posture by providing best practices and techniques as a security consultant. Respond to security breaches, minimize damage, and create plans to stop similar attacks in the future as an incident responder. Moreover, there are plenty of prospects for advancement and specialization for ethical hackers in a variety of sectors, including technology, healthcare, government, and finance. Credibility and employment prospects can be further enhanced by certifications such as the Offensive Security Certified Professional (OSCP) and Certified Ethical Hacker (CEH).
Ethical Considerations and Personal Satisfaction In addition to being a profitable career, ethical hacking provides personal fulfillment. Experts in this domain take pleasure in:
Hard Work: To outwit cybercriminals, ethical hacking demands ingenuity and problem-solving abilities. It is an intellectually interesting field of work. Sense of Purpose: It can be very satisfying to know that the job you do shields people and organizations from harm. Constant Learning: The cybersecurity industry is always changing, which makes for chances for ongoing education and keeps work interesting.
Additionally, ethical hackers follow a strict code of ethics to make sure their abilities are applied for the benefit of society. Their dedication to moral values sets them apart from malevolent cybercriminals and ensures the authenticity of their job.
0 notes
Text
India's Growing Need for Ethical Hacking
Cybersecurity is becoming a major worry for everyone in the modern digital age—individuals, companies, and governments alike. The need for ethical hackers is growing in India due to the surge in cyberthreats and attacks. In order to stop harmful assaults, ethical hacking—also referred to as white-hat hacking—involves locating and repairing security holes in computer systems. The field of ethical hacking is growing quickly in India, providing several opportunities for specialists in the field.

Professional Development and Prospects The field of ethical hacking offers a wide range of professional opportunities. A wide range of industries, including IT enterprises, financial institutions, governmental organizations, and cybersecurity companies, employ ethical hackers. To make sure that digital assets are protected, they are engaged to perform security audits, penetration tests, and vulnerability assessments. As cybersecurity awareness grows, a lot of businesses are spending a lot of money to hire ethical hackers with advanced skills to safeguard their networks.
Those who want to work in ethical hacking can pursue a variety of training courses and certifications in India. In the business, credentials like the Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Offensive Security Certified Professional (OSCP) are highly valued. Possibilities for employment and income growth can be greatly increased with these certifications.
Prospects and Difficulties for the Future Even with the bright prospects, ethical hacking in India is not without its difficulties. The lack of qualified specialists is one of the main issues. Proficiency in many programming languages, networking, and cybersecurity principles are essential for this job. To succeed in this field, one must always be learning new things and keeping up with the newest innovations in technology.
An additional obstacle is the regulatory environment. Although ethical hacking is acceptable and even recommended for security reasons, it is crucial to carefully consider the legal bounds. To prevent legal issues, ethical hackers must follow ethical standards and acquire the necessary license before performing any tests.

With rising cybersecurity spending and a focus on digital transformation, ethical hacking in India appears to have a bright future. Strong security measures are going to be more and more necessary as more firms go online and utilize cutting-edge technologies. Maintaining a secure cyberspace and protecting digital infrastructure will be greatly aided by ethical hackers.
In India, a lucrative and promising professional path is provided by ethical hacking. The need for cybersecurity specialists is growing, which means there are lots of prospects for development. Aspiring ethical hackers can significantly improve the safety of digital environments and protect digital assets by earning the required training and certifications. The job of ethical hackers will grow more and more important as the digital landscape changes, making it an exciting and dynamic field to pursue.
0 notes
Text
The Field of Ethical Hacking: An Extensive Synopsis
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. Protecting sensitive data and guaranteeing the strength of cybersecurity defenses require this technique. Now let's explore the realm of ethical hacking from four main angles: vulnerability identification, data and privacy protection, legal compliance, and proactive defensive strategy development.

Recognizing Weaknesses One of an ethical hacker's main responsibilities is to identify and take advantage of system flaws before malevolent hackers can. In order to find vulnerabilities, this procedure entails a careful analysis of the network, systems, and applications within a business. Ethical hackers can ascertain which security issues require quick correction and how readily a system can be compromised by simulating cyberattacks.
safeguarding information and privacy Data breaches and privacy violations are serious concerns for both individuals and corporations in the modern digital age. Since ethical hackers may spot possible access points for cybercriminals, they are essential to the protection of sensitive data. To prevent unwanted access, they make sure that security policies are in place, access restrictions are strong, and data is encrypted.
Observance of Laws and Mandates Strict laws pertaining to cybersecurity and data protection apply to many businesses. Ethical hacking makes sure that security procedures are up to par, which helps firms comply with these regulatory obligations. Compliance with frameworks such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) generally requires regular penetration testing.
Preventive Defense Techniques In addition to locating and fixing vulnerabilities already in place, ethical hackers aid in the creation of preventative defensive plans. They assist firms in anticipating and preparing for potential attacks by staying up to date on the latest cyber risks and trends. By comprehending the mindset and methods of attackers, ethical hackers are able to provide guidance on optimal network architecture and software

The field of ethical hacking is broad and diverse, covering proactive defense, data protection, compliance, and vulnerability detection. In the constant fight against cyberthreats, ethical hackers play a critical role in assisting enterprises with system security, sensitive data protection, and regulatory compliance. The significance of ethical hacking will only increase as cyber threats continue to change, making it an essential part of contemporary cybersecurity tactics.
0 notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Text
Exploring a Career in Ethical Hacking
Cybersecurity has become a critical issue in today's digital world, as everything from banking to shopping is done online. The field of ethical hacking, sometimes referred to as penetration testing or white-hat hacking, is essential to safeguarding private data and preserving network integrity. Here is a brief introduction to ethical hacking that should help you decide if it's the right career path for you if you're thinking about pursuing it.

What is hacking with an ethical bent?
Cybersecurity professionals with permission to breach computer systems, networks, and software in order to find weaknesses are known as ethical hackers. The goal of ethical hackers, as opposed to malicious hackers (also known as black-hat hackers), is to identify and address security flaws before they may be used by fraudsters.
The Benefits of Choosing a Career in Ethical Hacking 1. High Demand: As cyberattacks grow in frequency, there is a growing need for knowledgeable ethical hackers. Cybersecurity experts are required by companies in a variety of sectors to safeguard their systems and data.
2. Competitive Salary: Given their skill, ethical hackers receive a competitive salary. Because the work is so specialized, qualified individuals can demand substantial compensation and first-rate benefits. 3. Diverse Opportunities: There are many different places where ethical hackers can find employment, including government organizations, commercial businesses, cybersecurity corporations, and as independent consultants. You have freedom to choose where and how you want to work thanks to this variety.
4. Continuous Learning: Since cybersecurity is an area that is always changing, ethical hackers must keep up with the newest threats and technologies. This never-ending learning process can be rewarding and intellectually interesting. 5. Making a Difference: Ethical hackers are essential to safeguarding private data and upholding users' and clients' confidence. It may be incredibly satisfying to have a sense of purpose and to contribute to the larger good.

How to Hack Something Ethical
1. Education and Training: Begin with a solid background in information technology, computer science, or a similar discipline. In addition, a lot of ethical hackers work toward certifications like CompTIA Security+, OSCP, and Certified Ethical Hacker (CEH).
2. Acquire Experience: Real-world knowledge is essential. To hone your skills, work on actual projects, take part in hackathons, and practice on websites like TryHackMe and Hack the Box. 3. Keep Up to Date: Since cybersecurity dangers are constantly evolving, it's critical to keep up with the newest developments in both technology and fashion. Participate in virtual groups, go to conferences, and always look for new ways to learn.
4. Ethics and Integrity: Keep in mind that the goal of ethical hacking is security and protection. A prosperous career in this industry requires upholding a solid ethical base and integrity. An fascinating profession in ethical hacking comes with great pay, great challenges, and the chance to change the world.
This can be the ideal career route for you if you have a strong sense of ethics and are passionate about technology. You may be at the vanguard of protecting the digital world by learning new things all the time and staying ahead of cyber dangers.I appreciate your precious time, and I hope you have an amazing day.
0 notes
Text
Starting Your Journey in Ethical Hacking
It's thrilling and difficult to set out on an ethical hacking adventure. Your objective as an ethical hacker is to find and address security flaws in systems before malevolent hackers may take advantage of them. Here's a short guide to help you get going.

1. Recognizing the Fundamentals
What is hacking with an ethical bent? Legally breaking into computers and other devices to test an organization's defenses is known as ethical hacking. The goal is to identify weaknesses before the adversaries do. Study the Principles Prior to learning how to hack, you should have a firm grasp of the fundamentals of computer science. This comprises: Networking: Recognize the protocols used, how data moves across networks, and how to troubleshoot problems with networks. System Operating Environments: Learn about several operating systems, with a focus on Linux since it's a popular choice in the security industry.
Crucial Certifications A systematic learning path can be provided by certifications, which are frequently needed by employers. Several well-liked certificates consist of:
A thorough education covering many facets of ethical hacking is required to become a Certified Ethical Hacker (CEH). A certification aimed for beginners that concentrates on broad security procedures is CompTIA Security+. The Offensive Security Certified Professional (OSCP) credential is recognized for its pragmatic methodology and necessitates conducting actual penetration tests. 2. Enhancing Your Capabilities Practical Application While theory is valuable, real-world experience is even more so. To practice, set up your own lab setting. Virtual Machines (VMs): To construct a virtual lab, use software such as VirtualBox. Challenges related to Capture the Flag (CTF): Take part in online CTF challenges to assess your abilities in a safe setting.
Bug Bounty Programs: You can locate and report flaws in actual organizations' systems on sites like HackerOne and Bugcrowd, frequently in exchange for compensation. Take advice from the locals. Participate in forums and communities where you can share knowledge and remain up to date on the newest methods and trends. Among the well-liked communities are:
Reddit: Excellent places to get resources and debates include subreddits like r/ethicalhacking and r/netsec. Stack Overflow: For assistance with scripting and coding. Security Conferences: To network and pick the brains of professionals, go to events like Black Hat and DEF CON. 3. Moral Issues and Maintaining Legal Status Knowing the law Laws and regulations must always be complied with in ethical hacking. Unauthorized system access may result in harsh legal repercussions. Before you test any systems, be sure you have express permission.
Guidelines for Behavior Observe the rules of professional behavior. Hackers with morality ought to:
Observe privacy: Prevent needless surveillance of personal information. Be open and honest: Make your findings plain to organizations and assist them in recognizing the hazards. Be a responsible person: Avoid taking advantage of weaknesses for your own benefit or to harm others. Ongoing Education Cybersecurity is a constantly changing field. Keep yourself informed about the most recent security risks, resources, and methods by:

Reading Security Blogs: Keep up with sites like The Hacker News, Dark Reading, and Krebs on Security. Enrolling in Advanced Courses: With advanced certificates and specialized courses, you may keep improving your skills. Professional Networking: Talk with peers and mentors in the field to share experiences and information.
1 note
·
View note
Text
Navigating the Path to Front-End Mastery: A Guide for HTML/CSS/JavaScript Enthusiasts
Are you someone who is eager to advance in your web development career and is already conversant with HTML, CSS, and JavaScript? Well done on making it this far! Let's now set a path to help you become a skilled front-end developer.
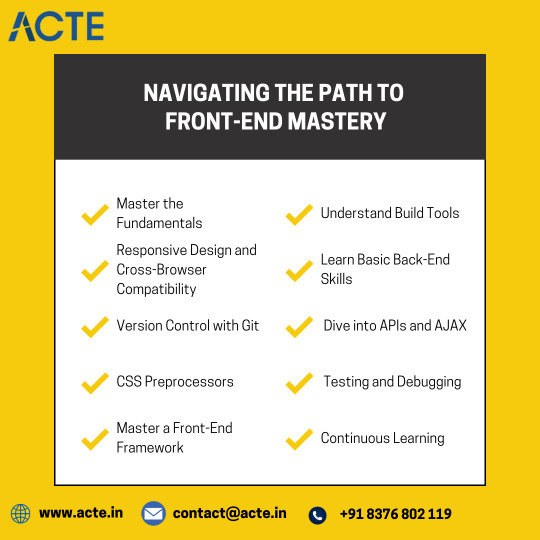
1. Master the Fundamentals
Make sure you have a strong foundation before tackling more complex ideas. Expand your knowledge of CSS layouts, JavaScript fundamentals, and HTML semantics. This guarantees a solid understanding of the resources available to you.
2. Responsive Design and Cross-Browser Compatibility
Discover how to create responsive designs. Make sure your webpages look great on all types of devices by learning how to use CSS media queries. Explore cross-browser compatibility as well to guarantee a consistent user experience across different browsers.
3. Using Git for Version Control
Git is a very useful tool for team development. Discover the fundamentals of version control to keep track of changes, collaborate easily, and protect your work. GitHub and GitLab are two platforms that can be great places to start.
4. CSS preprocessors, such as LESS and SASS
Investigate preprocessor languages like SASS or LESS to improve your CSS skills. They improve the efficiency and maintainability of your stylesheets by adding variables, functions, and mixins.
5. Master a Front-End Framework (e.g., React, Vue, Angular)
Nowadays, front-end frameworks form the foundation of online development. Select one and go in-depth with it. Angular, Vue, and React are well-liked options. It is crucial to comprehend how to create and manage a project using these frameworks. 6. Understand build tools (e.g., Webpack).
Effective building procedures are becoming more and more necessary as your projects expand. You can bundle your code, optimize assets, and improve performance with the aid of tools like Webpack. Learn how to use these tools effectively to optimize your development process.
7. Learn Basic Back-End Skills
Although it's not required, having a foundational understanding of back-end technologies (such as Node.js, Express, Django, etc.) might help you become a more versatile developer. You'll work with back-end engineers more productively and comprehend the entire stack.
8. Explore AJAX and APIs.
It's essential to know how to retrieve and work with data. Develop your understanding of APIs and AJAX (asynchronous JavaScript and XML) to build dynamic, interactive websites.
9. Testing and Debugging
Develop your ability to test your code. Examine JavaScript testing tools such as Jest. Plus, learn how to debug effectively to solve problems quickly.
10. Continuous Learning
The tech industry is changing quickly. Keep your mind open to picking up new skills, resources, and best practices. Read blogs related to the industry, take part in forums, and attend meetups or conferences to stay on top of the latest trends.
The path to becoming a front-end developer is never-ending. Take on new tasks, construct genuine initiatives, and never forget that it's acceptable to go one step at a time. Even if the path ahead may seem convoluted, if you have a strong will and a desire to study, you may become an accomplished front-end developer. Have fun with coding!
if you're interested in learning more about full-stack developers because it provides opportunities for certification and job placement. Skilled educators can improve your learning. These services are available both offline and online. Take it step by step, and if you're interested, think about signing up for a course.
Thank you for spending your valuable time, and have a great day.
0 notes
Text
Building Blocks of a Website: A Simple Guide to Website Development
Although starting a website may seem like a difficult undertaking, have no fear! In this blog article, we'll simplify and make it easier to grasp the website-building process. Let's examine the fundamentals of making your website work, regardless of your level of experience or whether you need a refresher.

1. Define Your Purpose and Audience:
It's important to decide who your target audience is and what your website's goal is before getting too technical. Are you making a portfolio, a blog, or an online store? Making decisions on design and development will be guided by your goals.
2. Choose a domain name and hosting:
The first step in creating a website is choosing a hosting company and a domain name, or web address. To make sure that people can reach your website, pick a domain name that accurately describes your brand or content and a reputable hosting provider.
3. Plan Your Website Structure:
Consider your website to be a book. Make a plan for the primary sections (pages) and their arrangement. Home, About Us, Services and Products, and Contact are examples of common pages. This planning stage helps in creating a user-friendly navigation structure.
4. Website Design:
Let's now work on creating a visually pleasing website. Either use website builders and templates, or engage a designer. Look for fonts, color schemes, and imagery that complement your brand and draw in customers.
5. Front-end coding (JavaScript, HTML, CSS):
What users view and work with is known as the front end. Your material is structured using HTML (Hypertext Markup Language), styled using CSS (Cascading Style Sheets), and interactive with JavaScript. Frameworks such as React or Vue. JS are widely used in current websites to simplify front-end development.
6. Create the server, database, and server-side language on the back end:
Your website's functionality is powered by the backend. This entails configuring a server, selecting a database (such as MySQL or MongoDB), and handling data and background tasks with server-side languages (such as Node.js, Python, or PHP).
7. Integrate Functionality (APIs, Plugins):
Use APIs (application programming interfaces) or plugins if your website requires additional functionality, such as payment gateways or social network integration. These tools make it possible for your website to easily communicate with outside services.
8. Test Your Website:
Test your website thoroughly before launching to identify any faults or difficulties. Verify that all of the features function as expected by checking how responsive it is across a range of browsers and devices. Your website's functionality is powered by the backend. This entails configuring a server, selecting a database (such as MySQL or MongoDB), and handling data and background tasks with server-side languages (such as Node.js, Python, or PHP).
9. Search Engine Optimization (SEO):
By making your website search engine-friendly, you may increase its visibility. This entails making sure your material is easily available to search engine crawlers, employing relevant keywords, and developing descriptive meta tags.
10. Go Live with Your Website:
Best wishes! You're prepared to take off! After you link your domain to your hosting, your website will go live and be available to everyone.

Planning, designing, coding, and testing are all steps in the methodical process of creating a website. With the correct strategy and a little imagination, you can make a website that looks amazing and accomplishes its goals well. Website building is an exciting process, whether your goals are to sell things, share your opinions with the world, or showcase your work.
The Full Stack Developer course in Hyderabad is a great place to start if you're interested in learning more about full-stack developers because it provides opportunities for certification and job placement. Skilled educators can improve your learning. These services are available both offline and online. Take it step by step, and if you're interested, think about signing up for a course.
Thank you for spending your valuable time, and have a great day.
0 notes
Text
Great Career Choice in 2024: Navigating the Tech Landscape
Selecting the best job path in the ever-changing field of technology can be difficult. But if you're thinking about a job that combines adaptability, solving problems, and a dash of creativity, becoming a full-stack developer is the best option. We'll discuss the advantages of being a full-stack developer in 2024 in this blog post. Choosing the best full-stack developer courses in Hyderabad is a crucial step in acquiring the necessary expertise for a successful career in the evolving landscape of full-stack developers.

The Foundation of the Tech Ecosystem:
In the world of technology, full-stack developers are like Swiss Army knives. Both on the front end (what consumers see) and the back end (the magic that happens behind the scenes), they have a vast array of skills. Full-stack developers are invaluable because of their great worth in the tech industry due to their versatility.
Changing to Meet New Needs:
Businesses are continuously searching for people who can adapt to the ever-changing landscape of technology. Because of their expertise in a wide range of technologies and frameworks, full-stack engineers are well-suited to deal with the rapidly changing landscape of the tech industry. Their ability to adapt makes them highly sought-after assets for businesses trying to stay competitive.
Efficiency in Small Teams:
Efficiency is crucial in the fast-paced world of agile development and digital startups. In small, dynamic teams, full-stack developers thrive because they can work on both the front and back ends of a project. Because of its adaptability, the development process can be streamlined by minimizing the need for substantial collaboration between various professionals.
Meeting user expectations:
Every successful digital product has an excellent user experience as its primary focus. Because they can work on both server-side functionality and user interfaces, full-stack developers are essential to making sure that the user experience is smooth and interesting. This all-encompassing method of development is in line with the growing need for user-centric design by 2024.
Job Security and Demand:
It is anticipated that in 2024, there will still be a need for full-stack developers. Full-stack developers are a great asset in the competitive job market since companies respect experts who can contribute to numerous aspects of a project. This career path is even more tempting because it offers job security and prospects for career progress.

A full-stack developer's job will still be quite desirable in 2024 and relevant as well. Full-stack developers are well-positioned to prosper in the dynamic and ever-expanding world of technology because of their capacity to adjust to changing needs, support effective development processes, and fulfill user expectations. A full-stack developer may be the best option for you if you're thinking about a job that blends creativity, problem-solving, and ongoing education.
0 notes
Text
A Clear Guide to Ensuring Cross-Browser Compatibility in Front-End Development
Making sure your website or application functions properly across many browsers is a major responsibility when it comes to front-end development. Because people use different browsers to access the web, such as Chrome, Firefox, Safari, and Edge, it is important to achieve cross-browser compatibility. This blog article will discuss five useful strategies to guarantee a seamless and consistent user experience across various browsers.

1. Test Frequently and Early: When it comes to cross-browser compatibility, testing is your best friend. Early in the development phase, begin testing your code, and keep testing as you make changes. Check how your site appears and functions across a variety of browsers, rather than depending solely on your preferred one. It is easier to find and repair bugs when using tools that replicate diverse browser conditions, such as Sauce Labs or BrowserStack.
2. When using CSS, use vendor prefixes
Different browsers may respond differently to CSS attributes. Use vendor prefixes to ensure that your styles are correctly parsed in order to remedy this. Include prefixes like `-webkit-} for WebKit browsers (Chrome, Safari), `-moz-} for Firefox, and so on if you're using a border-radius property, for instance.
'''css .example { -webkit-border-radius: 5px; -moz-border-radius: 5px; border-radius: 5px;} '''
3. Implement feature detection:
Modernizr is a useful tool for this. It enables you to verify whether a given feature is supported by a specific browser before using it. By doing this, you can make sure that users have a more seamless experience across the board by gracefully downgrading your code for browsers that lack specific functionality.
4. Use JavaScript polyfills:
Not all browsers support all JavaScript capabilities equally. Now for the fun part: polyfills are little pieces of code that fill in the gaps in browsers that don't support specific functionalities. You can avoid potential compatibility issues by using services like Polyfill.io, which can automatically supply the necessary polyfills based on the user's browser.
5. Keep up-to-date and stay informed. As browsers change, so too should your approach to compatibility. Observe trends in browser market share and make necessary updates to your supported browser list. Check popular browsers often for updates, and make necessary adjustments to your codebase to bring it up to date. By taking this proactive approach, you can make sure that your application or website always reflects the preferences of your users.

Making sure that all browsers work together shouldn't be a difficult undertaking. No matter the browser a user chooses, you can reduce compatibility concerns and provide a flawless experience by implementing these five useful guidelines into your front-end development approach. Don't forget to thoroughly test, keep up with browser upgrades, and use any tools or tricks that will help streamline the process. Have fun with coding!
The Full Stack Developer course in Hyderabad is a great place to start if you're interested in learning more about full-stack developers because it provides opportunities for certification and job placement. Skilled educators can improve your learning. These services are available both offline and online. Take it step by step, and if you're interested, think about signing up for a course.
Thank you for spending your valuable time, and have a great day.
0 notes
Text
Unveiling the World of Front-End Development: A Beginner's Guide
Front-end and back-end development are two key areas in the broad field of web development that combine to build the websites we use on a daily basis. In this article, we'll examine the main duties associated with becoming a front-end developer and shed light on this exciting career.
Deconstructing Front-End Development: Also known as client-side development, front-end development is the process of building a website's interactive and visual elements that visitors may interact with directly. It entails making web designs come to life while making sure the user experience is smooth and intuitive. The work of front-end developers is essential to creating websites that are both aesthetically beautiful and useful because they are the designers of the user interface (UI).

The duties of a front-end developer include:
1. Converting Designs into Code: Converting static design files into dynamic, interactive web pages is one of the main duties of a front-end developer. To ensure that the website has the desired appearance and feel, they collaborate closely with web designers to execute the visual aspects.
2. Mastery of HTML, CSS, and JavaScript: Front-end developers are experts in all three languages. JavaScript brings interactivity, CSS takes care of styling, and HTML supplies the structure. These languages are the foundation of the front end, so knowing them well is essential for a developer.
3. Implementing flexible design: Front-end developers need to make sure websites are flexible because there is a growing range of devices that people use to access the internet. This entails developing designs that fluidly adjust to various screen sizes on PCs, laptops, tablets, and smartphones.
4. Cross-Browser Compatibility: When it comes to online browsers, internet users have different tastes. It is the responsibility of front-end developers to make sure that their websites work properly in different browsers, such as Chrome, Firefox, Safari, and Edge.
5. Improving the Performance of Websites: Front-end developers are essential to the improvement of website performance. This entails lowering page load times, improving picture quality, and putting best practices into action to raise a website's overall performance and speed.
6. Improving the User Experience (UX): The goal of a front-end developer's work is to provide a satisfying user experience, which goes beyond aesthetics. This entails creating a website with easy-to-use navigation, seamless interactions, and user-accomplishable goals.
7. Working together with front-end developers: The collaborative efforts of front-end and back-end developers guarantee a seamless and operational online application. Back-end developers oversee database interactions and server-side logic, while front-end developers work on the user interface. A smooth end-to-end development process requires cooperation between these two groups.

Basically, a front-end developer's main job is to create a visually appealing and usable interface by bridging the gap between design and functionality.
If you want to know more about full-stack developers, we highly recommend the full-stack developer course in Hyderabad, which offers certification and job opportunities. Experienced teachers will better support your learning. These services can be found both online and offline. Learn step by step, and consider enrolling in a course if you're interested. If not, feel free to mention it in the comments section. I think there is still a lot to learn.
0 notes
Text
Discovering the Enchantment of Complete Stack Development Services
In the vast technology landscape, full-stack development services have emerged as a magical solution for creating robust and dynamic web applications. But what exactly does "full stack" mean, and why does it seem so magical? Let's go on a journey to unravel the world of full-stack development in simple terms. Choosing the best full-stack developer course in Hyderabad is an important step in gaining the expertise needed for a successful career in the evolving full-stack developer landscape. About Stacks: In the world of web development, a "stack" refers to the combination of technologies and tools used to build web applications.

A stack typically consists of two main components: a front end and a back end. 1.Frontend:
Think of the frontend as the visible part of the iceberg, the tip with which users interact. This includes everything you see and experience on a website, such as the buttons you click, the images you see, and the forms you fill out. Technologies such as HTML, CSS, and JavaScript are the building blocks of the front end. 2.Backend:
Next, we dive below the surface of the iceberg. The backend is where the magic happens behind the scenes. Handles server-side logic, databases, and the overall functionality of the application. Common backend technologies include server-side scripting languages (such as Node.js, Python, and Ruby), databases (such as MySQL and MongoDB), and server environments (such as Express and Django). What is full-stack development? Simply put, a full-stack developer is someone who has the skills to work on both the front-end and back-end of a web application. Think of them as versatile architects who can design user interfaces, implement complex business logic, and seamlessly manage databases. The Magic Elements of Full-Stack Development:
1.Front-End Technology:
HTML: Building the Structure of a Web Page. CSS: styles to make these pages visually appealing. JavaScript:Add interactivity and dynamic features. 2: Back-end technology:
server-side language: Executes server-side logic to process user requests. Database: Efficient storage and retrieval of data. Server Environment:
Create a robust and secure environment to run your applications. 3.Version control systems:
Tools such as Git help developers track changes, collaborate, and effectively manage code bases. manages communication between the user's browser and the backend server. You can further accelerate your entry into this thriving industry by choosing the Full Stack Developer online course. Benefits of Full-Stack Development Services:
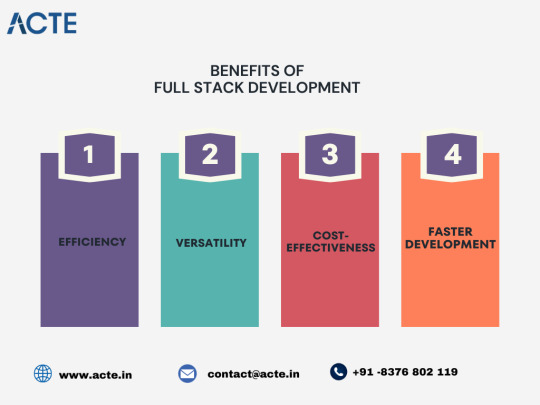
1.Efficiency
Full-stack developers can handle both ends of development, reducing communication gaps and streamlining the process. 2.Versatility:
It can be adapted to different project requirements, making it a valuable tool for different types of applications. 3.Cost-effectiveness:
In many cases, a single full-stack developer can replace the need for multiple specialized developers, saving companies money. 4.Accelerate development:
A comprehensive understanding of the entire application allows full-stack developers to accelerate development cycles. In the fascinating world of web development, full-stack development services serve as the benchmark for efficiency, versatility, and cost-effectiveness.
By mastering both the front-end and back-end, these developers add a magical touch to creating dynamic and seamless web applications. Whether you're working on a new project or extending an existing one, the magic of full-stack development can be just the magic you need for success. If you want to know more about full-stack developers, we highly recommend the full-stack developer course in Hyderabad, which offers certification and job opportunities. Experienced teachers will better support your learning. These services can be found both online and offline. Learn step by step, and consider enrolling in a course if you're interested. If not, feel free to mention it in the comments section. I think there is still a lot to learn.
0 notes