UNSW's COMP6841 Extended Security Engineering and Cyber Security - blog, notes and more.
Don't wanna be here? Send us removal request.
Text
Week 10 Notes
PRIVACY LECTURE BY ADAM SMALLHORN
Studying Ethics is quite important!
Data is the new oil - Oil is a huge source of danger! Oil Spills! Massive reputation damage. This is similar danger of “CoLLECTING ALL THE DATA”
Issues around data collection
Data Linking - Linking data and uniquely identified by the combination of their gender, DOB. etc. E.g. two phone numbers are the same, link the datasets together.
De-anonymisation - It’s anonymised! It’s fine! Risk of being reversed. Sharp distinction between personal info and de-identified data. Can’t be 100% confident.
Massive Scale - Data being collected at imaginable pace. E.g. two phones, multiple PCs etc.
Massive Data Breach - Data being disclosed
Phishing Expeditions - Large and persistent datasets provide temptation for phishing expeditions in the future.
There is just so much data! Linking MAC addresses everywhere I walk.
What if I could map out all the ways I’m being tracked? - Tech companies, dating sites, UNSW, employer, banks, government, etc.
Could infer friend groups, political learnings, sexual attraction, communication history, criminal records etc.
Google had 6GB of data, 1500 calendar events, and 200,000 location samples. Browsing history, calendar etc.
These tools weren’t built for users - Google makes these features for government etc. Private companies want to comply with the law. They all have portals.
iPhone data- App data, call history
Text Messages - Lots of data! (Heightened periods)
Chat Info, Ad Topics, IP Addresses
Facebook does analysis and infers things on related friends. LOTS OF HIDDEN DATA by Facebook.
How can we use this data? A day in the life of Adam
Web History - How to make a strong password, Trello board, some websites, cute dogs
Calendar - 2pm Cyber Bootcamp.
Opal Card - Eastwood and Town Hall
Photos - Dogs, meeting photos, shop photos
GPS and XIF data - Google keeping track.
Dropbox files - Check when files sync.
What we know - Visited the city after 1pm, attended cyber event, evidence of presentation, visited QVB stores and home at 7pm.
Metadata reveals some information.
Incognito mode - just hides browser history on your local PC. Doesn’t store history, cookies.
Browser fingerprinting - Screen Res, browser plugins, particular data from your browser. Track you with your browser identity!
Do companies like FB legally have to give me my info? - Under Au legislation, they need to do that. Good PR and they offer those tools. The thing they don’t have to give is the data they have inferred about you - e.g. race, political etc.
Bank - they have ID data (e.g. drivers licence), spending data, AU legislation API
After a Bank Account is Cancelled - ?
It’s a Big Problem - Private Industry, Government, intelligency Community
Flickr - Readily find people from GPS coordinates in photos.
Private Companies - Going crazy for data.
Data Lakes - Hoover, access, patch? Encrypt? Streams of data all coming into a lake, run analytic data, infer things. COLLECT ALL THE DATA, GET IT INTO ONE SPOT.... then realise no access restrictions. The mentality is to collect, collect, collect. Don’t fall into sense of security.
Companies struggling to keep computers up to date. Impossibly hard.
Target Pregnancy Email thing - Very powerful and creepy.
Quantium does data mining on Woolworths data. My de-identified data was probably there, then Quantium matched it up with your Facebook data.
Qantas frequent flyer is the most profitable part of Qantas.
Workplace Surveillance - everything on a work laptop is monitored. Find one infraction as the cause to fire someone.
UNSW Wifi data - You track people using WiFi.
DNS Requests Are In The Plain.
False Sense of Security - E2E Encryption, Its algorithms not people, It only does x under y conditions, It’s locked down, We have through auditing in place, It’s secure, its anonymised.
Anonymising Strategies
Redacted - Delete a column in excel
Encrypted/hashed
Pseudonyms - (name1, name2)
Statistical noise / ‘binning’ - Bins (buckets) instead of exact values
Aggregation - “There were 300 people in this lecture theatre”
Match amazon rating data with Netflix moving watching.
Just 4 data points from cell towers can uniquely identify you from the whole population 95%.
Take-Aways
Anonymmisation is not a certainty
Most data compromises had identifier betweenr ecords - allowing researchers to following a apttern.
The apptern becomes the fingerprint, not the data.
To adequately anonymise data might render the data useless.
Government
Centrelink and ATO data glued together.
My Health Record - no one really asks for this service. Will be incredibly useful for the government.
Opal
Australia Card killed, but come back in form of myGov.
Collection laws will emerge and re-emerge in different forms until passed.
The collection is always going to increase in scope.
Terms of usage always start narrow, but quickly broaden.
The last bad thing is no change in the status quo; the most bad thing is quite bad.
Access is almost relaxed or automated.
Mandatory metadata retention
Incoming and outgoing calls
Location of device
Unique id for pphotos
Emaila ddress of an email
Time, data of recipents
Size of attachements
Aussie face recognition system
Access and Assistance bill - Backdoors. Is it justified? - Is it reasonable for government not have access? 50 years ago you just get a warrant.
How To Fix Privacy
Start With Engineers
Advocacy
Design
Story Telling - Black Mirror
0 notes
Text
Week 9 Notes
Just Culture
Done well it works. Instead of blaming the individual who was the approximate cause of the problem - look at the overall system.
A just culture helps create an environment where individuals feel free to report errors and help the organization to learn from mistakes. This is in contrast to a “blame culture” where individual persons are fired, fined, or otherwise punished for making mistakes, but where the root causes leading to the error are not investigated and corrected. In a blame culture mistakes may be not reported but rather hidden, leading ultimately to diminished organizational outcomes.
https://en.wikipedia.org/wiki/Just_Culture
WHAT DO WE THINK NOW?
Time - Ability to observe failures and learn.
Engineers - Learning from the past. Methodologies to follow. Notion of best practice and standards. CHECKLISTS ARE REALLY GOOD! (Like aeroplane pilot).
Engineers need to have processes about being creative. Profession needs to have people who think outside of the box but if they get stuck needs to be some procedure in place.
What makes science is that you are following the procedure to prove yourself wrong - Falsifying. We can constantly prove something is wrong and then gain confidence as time goes by. Engineering is trying to always break it wrong, we always test in our mind and lab trying to break things. Engineering has a culture of excellence.
Agile Software Development is not good for security. Ship! Ship! Ship!
You have a duty - “not comfortable doing that”. Say that to your boss.
Plan and deal with conflicts of interest.
Quantity - Measure everything you can and check it. Engineers don’t say that looks thick enough. They smash bricks and things. The danger of quantifying is not everything is worth measuring. E.g. 6% secure website? Wtp does that mean.
You are a thoughtful analytical person and when you are in a crisis you are thoughtful.
Assurance - ways of being confident in what you say. Justification of saying the bridge is saying. Not challenger “1 in a million chance”
Closing the loop - So many systems are Feed Forward. Closing the loop - Feed Back. 10 years time come back and you didn’t get a job. Closing the loop is checking something is right. The art of engineering is closing the loop. We want wise thinking not wishful thinking.
350 alarms - Something went wrong on a oil ship and 350 alarms went off. Of those 350 alarms, only 8 were important. 350 alarms how do you need to know what is wrong? Metaphor for Cyber Security - You can hear 350 alarms, but you need to listen to the ones you need to be listening too.
System Properties - Need to think of systems. QANTAS Engineers sweating in non airconditioned plane. Frame of mind. Submarine incident - sweating, swearing while nuclear war might be happening on surface. Submarines can launch nuclear missiles. However commander didn’t launch - credit to him saving the world. Leaving a spanner in a thing.
Coherence - Need a system to have coherence and not be very complex and not be tightly coupled. Three things that lead to error. Coherence - everything in a unit has to be doing the same thing e.g. one function() does half a thing. Second of all, components shouldn’t be tightly coupled - changes in one affect changes in the other.
Wargames - Why are there humans in the loop? Humans are a real problem - you get a whole pile of crap. Can you replace humans with Automatic Safety devices? Difficult to cover every scenario. If everything occurs as intended, then it is okay. However if it is a different problem then what happens with the ASDs? Attackers exploit the fact that the system is not perfectly designed. An attacker wants to know what happens when the system is out of spec. The human designers don’t design systems properly. The system will operate outside of the spec - can’t use ASDs for everything. Can’t solve Apollo 13 with ASDs. ASDs put a bottom line - if all you have is ASDs you are in trouble. Needs humans in the loop (CHINA SYNDROME) .
Voting System - Not entirely tested. Not commercial grade software. If something fails during your election, you get the wrong government.
End 2 End - Security is an end to end property. People attack the ends. E.g. keylogger. Attack the weakest point.
Work to undermine limits - Anyone in power works actively to increase their power. Checks and balances stopping POTUS from having too much power. People will always try to overcome controls and things.
Ruler of the galaxy - Single trusted party. One person at top controls everything - single point of failure. Criteria - you don’t want to be ruler of the galaxy.
Assange - You want free speech except that is critical/inconvenient of you.
Cars and Trolley Cars - Uber/google etc. No one asked the question is this safe or danger of hacking? Absolutely - Top People working on it. Distraction 1 - probably the cars will kill people, but so many people die anyway today. We expect the accident rate to reduce. Then he said about the ethical decisions - avoid hitting would have to kill a young person - don’t know the answer to the question. Distracted from the hacking problem! Attacker could take over every car in the city and drive them into people, when you can’t patch your phones, browsers etc. How can you assure this?
No Trusted third parties - At some part you might need a trusted third party. Every attack is an attack on trust. Who can you trust. If you have the idea of insiders/outsiders - convenient theory e.g. Trump build a wall. However insides and moles are the real person. If you can’t trust anyone what can you do? Computer systems trust each other - function1() don’t need to check function2(). You might have to put checks everywhere - trust makes stuff work. Without trust the system is very inefficient. A trust no one will et access to the harddrive physically - then someone does and gg dead. Trusted third parties keep failing. However don’t roll your own security either! Difficult balance.
A remarkable number of missiles did not hit British ships. The missiles were rigged! Can’t trust third parties.
Secret to communication - It is not about me, it is about you. All the matters is what you hear. Ultimately it is all about the listener. 2 Firearms book - one sucks, one good.
Canary in a Coal mine - Canary in the coal mine dies very quickly. As soon as it died it stops singing - useful for mine.
Opal - Credit card and same discount - logging your identity and tracking everything and keeping it.
Face ID - Suckiing your face and sending to server
Data needs to be free - It was data about me and you. We could use this data to do greatt hings! World will get better - Your data. Setting other people’s data free. Can’t be put back. Danger of data - Patterns of data - the more you have compound effect. 3 pools = 1 lake. Worth more than 3 pools separate.
Read article - Secret agents could travel around and do things without people working out who they were. Pervasive tracking and databases and data matching allows them to be detected. They Are Canarys. A world where the secret agents can’t do their stuff is a world like 1984.
We would have lost all the privacy before we realise.
Cyborg - augmented human. We have become cyborgs with our phones. Offload our cognitive functions to our phone.
personal identity leaking out into the world. Governments collected data pretty bad.
REVERSE ENGINEERING
What is Reverse Engineering?
Taking an executable program and analysing its insides to figuring out how it works
Machine binary -> Assembly -> Code
Why reverse engineer
Challenge, Profit - Bounties, Malware analysis, Interoperability - extend the function of software you own
How to Reverse Engineer
Static - Read the decompiled code to determine purpose
Dynamic - Step through in real time to understand it
Static - Disseamble program by decompiling it
x86 - Generally just understand registers, system calls are a black box, function calls, branching - if statements, just read mneomic and guess, use reference manual, Google
Simple exam - Move value to register, call is system call
Tools for dynamic analysis - Basically any version of GDB, walk through the program during runtime.
Tips from demo - Look at the big picture - don’t get caught in the assembly. Look at strings. Many tools allow you to rename things and make commands. Run the program beforehand. Focus on areas of interest only. Work your way up.
CRACKING - It is illegal.
Patching - Change the program to always go to password correct. Skip everything! Jump and skip authentication. Crackmes.
Further Concepts - Stack - short term variable storage for programs (comp1521 stuff). We push a stackframe on the stack when we call a function. Save previous function’s registers on the stack.
Anti Reverse Engineering - Don’t release debug build. Remove symbols from the binary, dump symbols, disable asserts. Tomb Raider reverse to the original C code.
Anti RE: Tricking the Disassembler - Common techniques - Excessive jumps, dummy instructions, overlapping instructions. Self modifying code - COmmon in malware, non in commercial software - needs RWX text segment.
Overlapping Instructions - Embed instructions inside other instructions
Movfuscators - Turns every single instruction into MOV instructions
0 notes
Text
Week 8 Nuclear Energy, Chernobyl and Fukushima Daiichi
Richard said to research either Chernobyl, Challenger or Bhopal. I already researched Challenger and wanted to extend my knowledge a bit more. I find it interesting thinking about nuclear accidents as nuclear energy seems so scary and mysterious, and there are many complex things involved in the system.
Heat in nuclear reactors are created by the fission and the radioactive decay from the atoms. Uranium-235 is a special isotope of Uranium where if you hit it with a Neutron, it will split in half, create energy and create more neutrons! And if those neutrons hit other neutrons, that will cause a nuclear chain reaction, which is how nuclear energy is created.
In nuclear reactors you want to control the speed of the chain reaction by controlling neutrons. Moderators in nuclear reactors use moderators to slow down neutrons. Typically moderators are things like heavy water.
The accident occurred at Reactor 4 when the operators of the plant took action in violation of the plant’s procedures - they ran it at very low power, without safety precautions and without properly coordinating the procedure with safety personnel.
The moderator in the plant was a unique combination of graphite and water, and the control rod design made the reactors highly unstable at low power.
This led to an uncontrollable power surge that caused an increase in heat, rupturing pressure tubes. The hot fuel particles reacted with water and caused a steam explosion, causing massive damage and exposing the reactor core to the environment.
Chernobyl did not have a fortified containment structure common to most nuclear power plants around the world. Without this protection, radioactive material escaped into the environment.
Lessons Learned
Ever since the accident, the design of the reactors around the world have been changed making them much more stable at lower power. Automatic shut down procedures also respond faster. Apparently, it is now impossible to repeat the Chernobyl accident in today’s age due to these design changes.
The operator error was probably due to the lack of knowledge of nuclear reactor physics and engineering, as well as a lack of experience and training, according to Wikipedia. The first report that came out placed the blame solely on the plant operators. Later on, more reports came out saying that these were the contributing factors leading to the failure of the system:
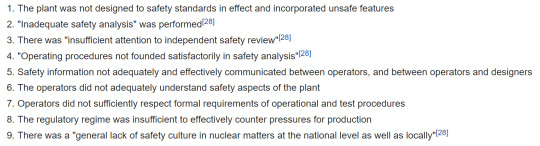
Analysis
I think the above picture is a good summary of what Week 8 is about. Week 8 in this course is all about learning about Errors and especially Errors in systems. There is not a specific person that can be blamed but several factors leading to the accident. It is interesting to see that half the dot points have the word ‘safety’ in them. It was both a combination of fragile engineering, along with bad safety procedures, which accelerated the accident and made the situation much worse. Hopefully we have learnt from our mistakes and nothing of a similar nature happens again.

Still to this day Chernobyl is a problem, as we are now building a new dome for the reactor in the abandoned city.
Fukushima Daiichi Power Plant
In 2011, another pretty bad nuclear accident occurred in Japan, where an extremely powerful earthquake hit the coast of Japan. An hour after the earthquake, a massive tsunami hit the coast, causing massive damage.
The wave hit the power plant and breached the sea wall. Reactor 1 was isolated from its heat exchanger while in the middle of a procedure. As a result, the operator was unable to activate the head exchanger, once the wave hit. Similar problems occurred in Reactor 2 and 3. After a while, a meltdown occurred as the cooling system was not cooling anymore.
Due to physics reasons, Hydrogen was generated and reacted with oxygen, caused a massive explosion in the top part of the reactor building. In the 4 days, 3 reactors exploded.
An investigation report concluded that the disaster occurred not because a large tsunami was unanticipated, but because they were reluctant to invest time, effort and money in protecting against a natural disaster considered unlikely. "The utility and regulatory bodies were overly confident that events beyond the scope of their assumptions would not occur . . . and were not aware that measures to avoid the worst situation were actually full of holes," the government panel said in its final report. (Low Risk High Impact!)
0 notes
Photo

100 posts!
1 note
·
View note
Text
Week 8 Ghost
Unfortunately we didn’t do the case study in the tutorial but I did my best to do it at home.
Stargate Ghost Problem - Suppose that you are the friendly Major M who sends a man X to another dimension. X becomes friends with Alien A and Alien A asks whether he can come to Earth with X. X agrees, but upon coming back X disintegrates and dies and becomes a Ghost. Now Alien A can communicate with Major M and the Ghost X but no one can communicate with X.
Q: What would you M do to get from X his report on the Alien's (A's) planet?
This is an interesting problem because you don’t know if Alien A can be trusted. The alien acts as a man-in-the-middle sending messages between X and M.
The first thing that came to my mind was to use Diffie-Hellman. The problem is that Diffie-Hellman doesn’t provide any mechanism for Authentication. Perhaps Alien A will intercept the process and create two symmetric keys between M and A and A and X. So if M sends a message, A decrypts it and modifies it, and then sends to X, and vice versa.
We could solve this problem by perhaps signing the data beforehand so that the other party will know it has been intercepted before attempting to do Diffie-Hellman. This presents a problem as both M and X must know each others public key beforehand - similar to how Certificate Authorities are hardcoded in your web browser.
Hence the solution is as always, some sort of shared secret. Maybe each one could remember a codeword like ‘sausage’ and send the message along with a HMAC, so they would know the message is not being tampered. Unfortunately if A doesn’t want to cooperate and send no messages there is nothing that can be done, but if he does allow messages to be sent then it can be easily proved that the man in the middle is not tampering the message.
My Something Awesome also involved man-in-the-middle attacks, where you can image X is the server and M is the client, with there being possibly several As which can listen to your connection.
So to conclude, it seems that the Stargate Ghost problem is a man-in-the-middle problem in disguise, and all solutions to this typically involve some sort of shared secret, something both parties know beforehand or a secret code word. This idea is key in Security Engineering (no pun intended).
0 notes
Text
Week 8 Human Weakness
HONESTY (or the lack thereof)

I hate these type of dictionary definitions! Seems so lazy by whoever wrote the dictionary.
Anyway one of the weaknesses Richard mentioned was Honesty and gave an example of how one uni has an honour code and emphasises it a lot and another one doesn’t, but both had the same probability for cheating on a test! Clearly you can’t just tell someone to “be honest” and this makes this a human weakness.
Imagine that you had the choice of lying versus getting 100% in a course. Obviously the normal person would lie, especially if the chance of getting caught is low. Low risk high reward! However if everyone is dishonest then what becomes of our world? Can we trust each other anymore, or is it just a game of trying to gain people’s trust and tricking them?
But imagine we didn’t live in a world of dishonesty! Then we could trust each other and feel more comfortable with others. But then someone can easily become dishonest for their own gain, since everyone is being honest. It is like the prisoners dilemma from Game Theory - no one will be honest if they didn’t care about ethics, as it provides no competitive advantage. It is only because of our morality that we wish to be honest, but if we can get away with being dishonest then clearly it is the optimal, logical choice.
It is interesting to think that this human weakness is the core reason for Security Engineering in the first place. We need to authenticate people, so we have come up with things like passwords and Diffie-Hellman, so that we can remove honesty from the equation. If everyone is honest then we don’t need passwords! Just type in the email and go, promising that you are the owner of the email. Obviously this sounds ridiculous, but we wouldn’t need passwords if everyone was honest with who they are when logging in?
0 notes
Text
Week 8 Security Everywhere
Australia Post told to improve cyber security practices
Article - https://www.itnews.com.au/news/australia-post-told-to-improve-cyber-security-practices-527738
The national auditor found gaps in the security of two of Australia Post’s critical systems! Australia Post was called out for “not effectively managing cyber security risks” and not undertaking “detailed risk management assessment” on the systems for the past two years. This means that the ability for Australia post to withstand a cyber attack is pretty bad, as their evaluations would only be accurate 2 years ago. Any new developments in cyber security, such as a new attack, would make the Australia Post system vulnerable.
The audit found only half of the ten sampled controls were designed and implemented as specified in the framework, with others only partially implemented or not in place at all.
I find it interesting that a government controlled entity is audited by itself and found to be fully of security holes. Similar government entities such as the Reserve Back underwent a similar audit and they didn’t have such risks.
One of the things Australia Post didn’t do was application whitelisting for “blocking unauthorised applications from executing on its corporate desktop and server environments”. This makes it possible for a Stuxnet like situation to occur - an attacker could simply plug in their USB and infect the system. Especially if the malware is a worm which spreads it across the network, the system is susceptible to single point of failure.
The auditor says that “risk aren’t being managed effectively”. This links back to what Richard usually says. It is about the risk not the outcome. People like to see that if there is no bad outcome, then the security is good! Perhaps Australia Post saw that they have not been hacked for a while and became complacent. This leaves them open for future attacks. So the fact that Australia Post didn’t have proper procedures in place to manage risk is already a failure, even if nothing bad has happened.
The Australian Cyber Security Centre has listed strategies that businesses should follow to mitigate cyber security incidents. https://www.cyber.gov.au/publications/strategies-to-mitigate-cyber-security-incidents.
Here are some from the page that we can all follow!
Configure Microsoft Office macro settings to block macros from the Internet, and only allow vetted macros either in 'trusted locations' with limited write access or digitally signed with a trusted certificate.
Application whitelisting of approved/trusted programs to prevent execution of unapproved/malicious programs including .exe, DLL, scripts (e.g. Windows Script Host, PowerShell and HTA) and installers.
Patch applications e.g. Flash, web browsers, Microsoft Office, Java and PDF viewers. Patch/mitigate computers with 'extreme risk' vulnerabilities within 48 hours. Use the latest version of applications.
1 note
·
View note
Text
Week 8 Authentication
WHAT IS OAUTH?
OAuth is an open standard for access delegation, allowing people to login into websites without giving their personal information. OAuth provides to clients a “secure delegated access” to server resources on behalf of a resource owner.
OAuth allows tokens to be issued to third party clients by an authorisation server, with the approval of the resource owner. The third party then uses the access token to access the protected resources hosted by the resource server.
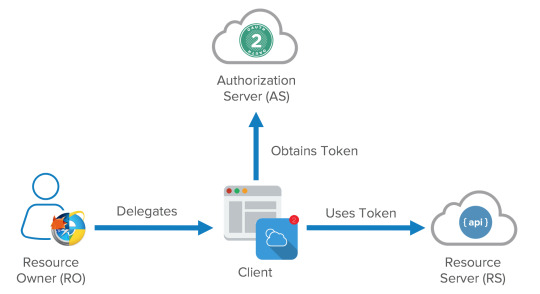
OAuth is an authorisation protocol, rather than an authentication protocol. The diagram below shows the difference between OpenID and OAuth, different protocols used online for logging in.
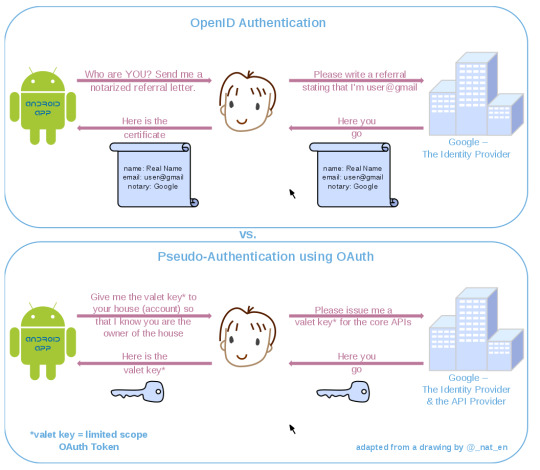
Because the identity provider typically (but not always) authenticates the user as part of the process of granting an OAuth access token, it's tempting to view a successful OAuth access token request as an authentication method itself. However, because OAuth was not designed with this use case in mind, making this assumption can lead to major security flaws
COME UP WITH ATTACKS AGAINST BARBARA USING THE TECHNOLOGIES ABOVE THAT WOULD COMPROMISE HER ACCOUNT
As the above says, OAuth is Pseudo-Authentication. It is possible to get the OAuth Access token using a service which doesn’t require authentication. OAuth is typically associated with authentication as it is built on top of OpenID. Access tokens do not represent the user or authentication. So depending on the service Barbara is using, she could use a service which assumes such a design, and then the security could be exploited.
The intended audience of a token is the protected resource. It is down for the prospected resource to validate the token. So if for some reason the token is sent to the client, they are violating the design of this system.
There is not much hope for a client application to receive access tokens and be sure that no one cut and paste that token from a different request.
0 notes
Text
Week 8 Spot The Fake
EXAMPLE OF SOMETHING THAT HAS BEEN FAKED OR SPOOFED
Something that has been faked and spoofed and will be done for the foreseeable future are skills and experience in job interviews. In job interviews, they may ask you a behavioural question like “tell me about a time when you had a conflict in a team?”. If you didn’t have a conflict in a team, or your conflict was pretty trivial, then what do you answer that question? Do you just say “I didn’t have conflict?”. If you do that, look forward to the rejection email. As a result, this is a question many candidates prepare for and perhaps come up with a fake response that makes it impressive to the interviewer. Since interviewers don’t perform a deep background check about every fact you say, they trust you and rely on their instincts. It makes it easy to fake any past experiences you had to gain a competitive advantage. In fact, I believe that without a bit of lying in a job interview you will always be at a competitive disadvantage, as many others will lie with much better examples for job interview questions.
SOMETHING IN EVERYDAY LIFE THAT COULD EASILY BE FAKED / SPOOFED.
Something in everyday life that could easily be faked is Coke. You could probably get a Coca Cola bottle, and modify the stick and put the Pepsi sticker on it instead. Most people probably wouldn’t realise the drink has changed. Perhaps you could put a Coke stick on a cheap brand, and sell it as a Coke bottle, and generate profits deceiving people!!
It is the fact that when we open a bottle that says Coke we don’t really think much about the taste, and a small variance of taste might be attributed to how dry our tongue is or how we are feeling, so you could easily spoof it. Of course if you try to replace a Coke bottle with orange juice then people will tell, so there is a degree of change people are willing to accept before things become suspicious.
0 notes
Text
Week 8 Google Yourself
Facebook
As the module suggested, I tried to download my Facebook information. There was so much information that It took quite a while to generate the files. I wonder what the backend services are doing generating the files. Is my private info distributed around the globe? Or perhaps generating the HTML files is a slow process. There were also so many categories of data they can keep track of. I only got Facebook around 2 years ago, and lots of information has been collected. I wonder how extensive the profile of those who have been using this service for 10 years are.
Once the archived processed, I saw some interesting things. Here is something I posted on a private page for the HSC.

One interesting piece of data was Face Recognition. It was just a piece of raw text. I wonder what it is about. Apparently the example count is “6″ which I assume is the number of training examples of my face they have used for their machine learning algorithm.
Beyond tracking my login and cookie info, there is nothing to ridiculous that Facebook has tracked. They don’t have any location info, since I have never used any of Facebook’s services requiring my location.
Google
Google had a similar issue, taking a long time to generate the info. I just decided to just download my Location History info instead.

That’s pretty scary - Google has tracked my whereabouts. The strange thing is how there is so much information concentrated in the city area. Maybe I visited lots of places in the city? Perhaps the Google service keeps track of all the unique places. This means it can count how many times you visit something and perhaps target ads!
I believe Google was able to track my info when I had an Android phone. I only had an Android phone for a short while. I don’t remember explicitly setting any location settings, so clearly the default is just to track everything.
Apple
I don’t have iTunes on my PC, but just my the suggestions Siri gives when I used my phone I know my phone usage habits and location is being tracked. iOS is smart enough to tell me that I should set my alarm clock at night time! Even third party apps like TripView tell me that I should check the bus timetable around the time I leave for uni in the morning! That’s quite convenient, but obviously my information is being tracked! I wonder if this info is being uploaded to iCloud.
0 notes
Text
Week 8 Notes and Reflection
REFLECTION
This was an interesting week, less focused on any technical things about security Engineering and more concerned with this idea of Errors - especially that you can’t pinpoint an error on one or two people but usually due to a bad system. Systems can be actual “systems” like nuclear power plants, or a system of behaviour in an organisation.
The lecture in the night time was incredibly weird. Richard literally read a book about the Three Mile Island accident. For the exam I will have to research a bit more about the accident - I like watching videos on YouTube, and it helps gain a different perspective. What I learnt was that the accident wasn’t caused by one entity - but by many entities involved - System Failure.
NOTES
Books on Errors
Human Error - James Reason
Normal Accidents - Charles Perror
Just Culture - Sidney Dekker
The Challenger Launch Decision - Diane Vaughan
Chernobyl: The History of a Nuclear Catastrophe - Serhii Plokhy
Command and Control: Nuclear Weapons, the Damascus Accident, and the Illusion of Safety - Eric Schlosser
When something goes wrong
What is the root cause? Root Cause Analysis. Do this analysis when something goes wrong. The point is that we can improve for the future. Reactive. You can do one more like an engineer.
Humans prefer to have a signal explanation. But in the rare case they say three things:
Human/user/operator error - You sack that person! Blame the person, problem solved. Looking for a hero/villain.
Every single cyberattack will because of human error. But it won’t be one human.
Story 1 - Aeroplane industry - “the last touch”. Root cause - the engineer who signed off on that last nose cone - the person would be the one at fault and fired. The last person who touched it and is at fault.
Story 2 - The second culprit is culture. We don’t have the right culture we have to change the culture! Culture is nice no need to blame anyone! Pay lots of money for consultants! Doesn’t really tell you how to fix the problem.
The above answers you won’t be able to solve the problem.
Fallback attack - when trying to hack someone, cause them to fall back to a less secure protocol. Only respond with less secure protocols.
Human Weaknesses
Honesty - commander in cheat. Humans not good at telling the truth. Some unis have an honour code - no cheat, no plagiarism. Psychologists what to work out to what extent honour codes alter people’s behaviour. Shredding exam paper - people got higher average score in test when the exam paper was shredded! Dishonest! Before you do it you would have to sign an honour code, saying you won’t cheat on the test. Different result when you sign at beginning vs end. Prinston you are shoved with the honour code. Stanford no honour code. Made no difference!
Misdirection and limited focus - Our attention is like a torch. Imagine it completely dark - you use the torch and focus on a few things. Some areas you never shine the light on - pay attention to only one or two of those factors. We don’t always pick the best factors to follow. Humans subject to misdirection - focus on something else rather than what you are supposed to focus on. Humans should focus on what’s logically important, but tend to focus on what it is psychologically salient. E.g. magician. Magicians make u make sure you can’t tell whats important to focus on. Sleight of hand and misdirection. Planned and executed in plain sight. If the situation is complex need to turn all the lights on. How do you deal with contradicting data? - Confirmation bias. Ignore stuff we don’t like that - confirm theory we are currently theory. The more often you do something, it will become routine. His obsession: "those factors which lead to and sustain wishful thinking rather than wise thinking"
satisficing and bounded rationality - Good enough is good enough, let’s move on.
People prefer positive statements
overriding tendency to verify generalizations rather than falsify them
Group-think syndrome - When you are in a group and the way you act in the group. What is value is group membership. Even if things are going off the rail they don’t want to be the annoying person no one likes.
developmental phases - goed and breaked 2
procedural
meta-procedural
conceptual
The system should be designed so if a human error occurs. it is not catastrophic.
Heuristics
Similarity matching - Have in your head schemes or situations from the past and try to match it. “Muscle memory”. This is how social engineers exploit you. The Brain is optimised to not think.
Frequency gambling - When you got a match - I’m going to recall the pattern and pick the pattern. When you pick the pattern how to pick the best matching one? Most likely pick the pattern that worked most often. Frequency gambling - picked the pattern from the past that worked the most. We are just trying to delegate to a pattern very quickly.
How is an accident different to an attack? - The intent - someone trying to make it go wrong. With an accident our adversary is Murphy. In an attack, you have someone who is adaptive and clever. The bad guy will make the cheese holes line up. Lego trains - interface trains through a serial port. At every Y intersection (switch) you could control it. The real problem was making sure the trains never collide - not the optimal solution. People distracted by the interesting things. Richard attacked them - he made Satin’s simulator. If you engage in an unsafe strategy, you’ve done the bad thing. This is how security is different to accidents.
SYSTEMS
50 trivial problems - old man driving, bus strike etc, full car park, all sounds lame! Primary cause of failing to get to job interview? Human error, mechanical failure, environment, system design, procedures you used. The best answer is all of them? None of the above - none of them caused the accident. it was a systemic accident.
Recognise that sometimes when things happen it is not due to the last person. It is about the system.
If you design a well designed system - resilient in accidents and attacks. If highly coupled and incoherent then that is pretty bad. Redundancy - Defence in Depth. However sometimes some failures cause other failures. COMMON MODE failure.
Cassandra and Apollo and hindsight and Chekhov and simplification - Wooed her about something. Cassandra Syndrome - knowing the truth but no one believes you. Chekhov gun - anything on-screen in a movie is there for a purpose. A gun is on the wall to be used. Hindsight - Looking back everything looks so clear, but at the actual event maybe not.
Belief that event has only one significant cause.
Plan for few contingencies than occur.
-ability to control outcomes - the illusion of control.
- hindsight bias - knowledge of outcome of previous event increases perceived likelihood of that outcome
2911 Things - complexity coherence coupling visibility - visibility - direct error (e.g. instant feedback - ship goes wrong way). Easy to detect. The real errors are latent errors and the consequence of the error stays hidden until the future. Latent errors with defence in depth systems. E.g. memory leak. Fail invisibly and think the system is safe.
operator deskilling due to Automatic safety devices - Ironic!
latent vs active failures
"Dead Battles like dead generals hold the military mind in their dead grip, and Germans, no less than other peoples prepare for the last war." - Barbara Tuchman - planning for future is planning for what happened before.
Exam question about one of these:
Chernobyl
Bhopal
Challenger
Three Mile Island -
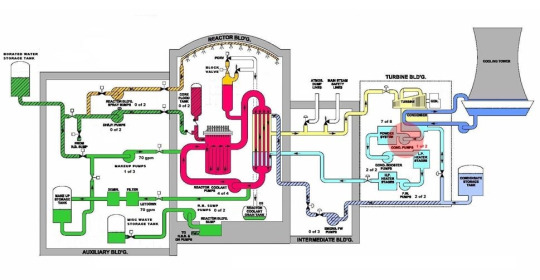
Chernobyl will be in the exam. The rods are in same liquid and pumped round and round circulating heat in the red area. Rods drop down to separate things, and absorb neutrons. For safety issues, the red stuff is inside a closed system and there is water cooling.
Nuclear plants plagued with startup problems. Imagine nuclear react is cloud services! The utility charged the builder, and the builder charged the utility in the accident. The water in the secondary system is pure. Resins might get in the water and must be removed. It leaked out and leaked into the pneumatic air system. The system drives some of the instruments. Interrupted the air pressure which went to two of the values for the water system. Emergency pump used but the pipes were blocked! Valves left in the closed position from a maintenance - invisible failure. Operator couldn’t tell the water is pumping through a closed pipe. Mystery how the valves were closed. Operators testified - not unusual to find some in the wrong position.
The decay heat builds up enormous temperature and pressure - normally there is lots of water to cool this. However the cooling system didn’t work. If the red part gets too hot, stainless steel around the red part might be brittle. There are ASD’s to handle the problem. The valve at the top of the yellow thing - relive pressure from the core. Reducing pressure becomes a gas, and explodes into steam. 1 in 50 times valve expected to fail. Presidents commission discovered that the valve fails often in other reactors. Unfortunately in this attack, the valve failed to close again after it opened. The radioactive water is gushing out! Absolute disaster. 32 thousand gallons stream out. The thing was simply uncaught. The indicator was recently added to the valve to indicate the valve had failed. However the indicator itself had failed too. Because the light was showing the valve had shut, they didn’t do any other tests. The valve only records whether a signal was sent to the valve to shut, not whether the thing was shut! The second shift determined the error and fixed it? When the mistake is a latent error - operator never notices. Can’t see that mistake again - new eyes come in and might solve the problem! Humans lead to failure and the failure to detect the failure. Operators couldn’t tell - only thing is “why is the core getting so hot?”. The system was tightly coupled - errors in one thing affect another.
The people were looking for one story to explain the failure - however it was multiple stories. Opaque system. Heat in the bottom tank - its “probably ok” even though it was burning hot. reason to believe the water could have come from anywhere. Went to different wrong tank which overflowed in the wrong building.
Everything will be weirdly connected - leave the tap on and all the password pour out of the tap. Tightly coupled system.
Theoretical thing when the core is uncovered and etc. Possible the reaction can lead to hydrogen gas - can lead to explosion. Theoretical reaction that oxygen and hydrogen - thought it was an oxygen explosion. The whole thing filled up with hydrogen gas. China syndrome, steam in air and Fukishima.
Investigations - Occurred. Reported that operators made terrible mistakes. THere were millions of things that went wrong, causing chain reaction. Can’t pick one person to blame. None of the people are actually the problem - they doing their best in a system designed to fail.
What we have to do is not focus on finding scapegoats, and pretending we have good systems - Design it so that if things go wrong, the impact is minimised.
UNSW how to improve cyber security - One real answer - work out the most important assets and JUST DEFEND THEM. Students? Safety? Staff? Money? Step 2- Assume you are going to be breached, and set it up so that is not a disaster. Have the vice chancellor read the press releases.
HR Department - Can we have a copy of your passport? “I don’t know how long we keep passports, and we built a huge passport database.” Don’t hold the data, and delete the passports. Get rid of the valuable data! Stop building it up. Don’t make a data lake.
PRIVACY EXTENDED LECTURE
When we use online services we forfeit our privacy for online services and fun.
Google Timeline - tracks your location when you left your GPS on.
The problem is when it is compromised - easy target and easy to stalk.
Signal Blocking - Phone in Aluminium foil. Today there was reports of people accessing metadata without warrants. Aluminium foil breaks bluetooth signal. Faraday bags only $6!!! Foil blocks Find my Android.
Methods of Prevention - Incognito mode, Privacy focused browsers, log out when you can, Don’t make accounts with other accounts (e.g. spotify with Facebook), LIE.
VPNS - Everything you connect through the internet is through the VPN, not your local address. Everytime you make a request the person making the request is the VPN. Trusting whoever makes the VPN.
Onion Routing - Diverting your request through intermediate nodes. Between each node is a symmetric key. 3 layers of encryption. Each node doesn’t know enough on its own that if it was compromised that it would give something valuable. Don’t know client or server. However attacker can perform timing attacks - see requests in and out.
A right to privacy - No different to free speech where you have nothing to say. You can get cheaper flight tickets through a VPN from another country.
Should I be concerned? - I have nothing to hide. I have nothing I can think of that I want to hide. If you are a good law abiding citizen then it is all good? Bruce Schenider = false assumptions of privacy and its value. Premise is that privacy is about hiding a wrong. The problem is the Power of The Government - Imbalance of Power. Left powerless as we don’t have a say on who can view our personal records. E.g. several airlines handed passenger records over to federal agencies after 9/11. Entirely different purpose of what the data was intended for. The policies become meaningless! Left us in a powerless position?
Privacy threatened by many small things, not one big thing.
DIGITAL FORENSICS EXTENDED LECTURE
Branch of forensics science
Recovery/investigation of material found on digital devices
Two types of personnel
3 Stages of Digital Forensics Investigation
Acquisition/Imaging - Capture an “image”
Analysis - keyword searches, recover deleted files, specialist tools
Reporting - evidence used to construct events/actions, layman report written.
Type of Forensics
Computer forensics - Memory and data
Mobile device - Phone
Network - Router switches, packet captures
Database Forensics
Video/Audio forensics - Movie, audio
Stenography - hidden files inside files.
Tooling - EnCase, Autopsy, FTK Imager, File, Strings, XXd, Foremost, Binwalk, mmls.
Drives and Partitioning (FAT32) - Allocates memory in clusters. FAT records the status of each cluster. Deleted files name is changed to 0xE5[file_name]. The first character of the file name is changed to show it is deleted. Forensics people check this FAT table and check for these deleted files.
Flag in IMage - https://imgur.com/a/X2mNAIZ
3 notes
·
View notes
Text
Week 7 Something Awesome Part 3
I’m slightly annoyed I have to redo the video again. Caff posted a message on the announcements saying the video has to be 2 mins long, but mine is 2min 45seconds. The original specification says the video can be 2-3min long....
Not sure how I will present the project, as it consists of two parts - the ARP spoofing attack and DNS spoofing attack. Swapping my settings between the two is not very seamless, and it might not work either. I’ll have to think about what I can do.
Overall, I really enjoyed the project. I spent way too much time on trying to perfect the OpenLearning pages. Not sure if it is worth the effort. I have learn a lot about internet technologies and WiFi, and I think it is pretty cool how I can just simply override people’s WiFi!
It was not an easy task, having to install and configure lots of networking things and figuring out ways around HTTPS and setting up the DNS server. By the end, I was able to crack most websites. Some websites may not be possible due to some very recently cached version of the page in the users browser. Some browsers are more vulnerable too. Basically, I feel like I have done the best possible without needing to crack RSA and HTTPS!
Now hopefully the presentation goes OK and the other parts of my job application are up to scratch.
WHAT COULD I HAVE DONE BETTER?
I feel like I could have managed by time slightly better in regard to writing the write ups. I wrote all the write ups in Week 7. Though at the same time I still feel like this is okay as I had no choice with trimesters - I had several exams in Week 5. I could only put my foot down once I finished them!
I also perhaps should have blogged a bit more. I spent lots of time solving the problem so I was relieved I solved it, but forgot to blug.
AREAS FOR FURTHER EXPLORATION
I want to see whether I can increase the success rate for more websites. Currently if the website is cached recently and they use Chrome then the hack doesn’t work. Though as soon as they visit a vulnerable website I can steal their information! Of course, I feel like I achieved my goals but with a bit more time maybe I could figure out how to sign a few certificates or get a better Rogue WiFi router and flash it with custom firmware such as DD-WRT for an even better attack.
0 notes
Text
Week 7 Something Awesome Part 2
PHP FORM BACKEND
I decided to make a really simple file which will be executed when the user presses submit on any form. This file would be placed in the root directory and would be common to all the fake login pages. I also decided that I won’t need to use Kali Linux to host the Apache server, I can just use the existing Apache server I’ve already configured on Windows, to save a bit of time. However the DNS server will be hosted on Kali Linux. An interesting this about this is that my Kali Linux and Windows machine will have different IP addresses, so basically it is like two different PCs on the network.
My PHP file looks like this:
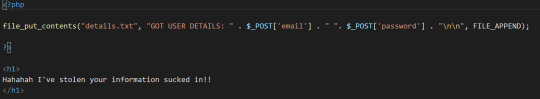
As you can see, I simply call a function print a string to a file. I also display a funny message to the user!
TESTING
Now I am truly done. Now I am truly done! Now I just have to test the overall functionality of my Something Awesome.
Setup for ARP Spoofing Attack:
First I had to connect the Rogue WiFi USB stick to my WiFi connection. This was slightly annoying, as the web interface for the stick is a bit clunky and failed to detect my router. After a while I connected and basically the stick became like a “bridge” into the real wifi network.
Restart my PC and initialise the Kali Linux VM I had installed.
Use ifconfig to get the IP address of the gateway.
Then go to the command line and run the MITMf attack, with ARP spoofing mode enabled. This is the command: sudo python mitmf.py -i eth0 --hsts --spoof --arp --dns --gateway 192.168.1.1 --jskeylogger.
Try to visit a few websites on any PC on the network. Most of the websites should be vulnerable. Invulnerable websites may fail to load, vulnerable websites may load.
Key strokes are shown in real time in the console. Any submitted form info is also shown in the console.
Done!
I made a video about this. This is not the video I used for my Something Awesome, it is slightly longer: https://www.youtube.com/embed/Ycyhx48zFns
Setup for Website Overriding DNS Attack:
Start DNSMASQ on the Kali Linux machine with the host file configured as before.
Start Wampserver on Windows, which is my Apache server
Modify the router settings so that the DNS server is the IP address of the Kali Linux machine.
Visit a few websites on any PCs on the network, most should redirect to ‘McDonalds Free WiFi’!.
Done!
I also made a video about this, slightly longer: https://www.youtube.com/embed/_uVM-Ucm5ac
I think I can conclude the technical aspects of the project are completed. Now time to write a few write ups and polish the presentation!
0 notes
Text
Week 7 Snoop Case Study
REFLECTION
This was quite an interesting tutorial, because it was just a debate! Ryan (tutor of the same name) changed the topic of the debate slightly to make it so that one side was arguing for the government collecting data, and the other side was arguing for private companies collecting data!
I was put on the side of private companies. I don’t really have an opinion on this. I think it is more scary for data to go in the hands of private people but at the same time the government seems like they have more dodgy systems. I was easily able to spoof my.gov.au in my Something Awesome, which proves there may be issues with their security!
Private companies usually collect data for their own gain, not in the interest of the customer. But perhaps you could argue that government is aiming for the interests of the people (if they are not corrupt). However a common argument was that the government is “incompetent��!
I liked the conclusion of the debate, where everything was at a standstill, and both sides agreed that both government and private sectors need to collect data. It is not simply a black and white decision that can be made.
THE DEBATE
Points made in my team before the debate
Private corporations are more efficient in their operations, as they are operating for a profit.
Government held accountable, and governments can change the law.
They just forced My Health Record - 70% of Australian’s didn’t know it existed.
If the government changes - policies and leadership also changes. We have had gazillions of prime ministers over the past 10 years.
The government has more power - enact harsher penalties on private companies that do not follow the rules.
Private sector more consumer focused - would cater more for the consumer.
Multiple private companies means there is more competition in the market - businesses would desire to be in the customer’s best interests.
Trust in the government changes really quickly. One stage they would love their president then riots in Egypt.
If one company gets hacked - it’s not everyone’s data. So there is no single point of failure.
The government oversees the private companies. Who overseas the government - no one!
You get the best programmers in the private sector.
Debate
Multiple private sector companies - no single point of failure.
Government provides convenience factor. Government is highly regulated. Transparent to the citizens. Most likely be more transparent. Convenience is ruined.
Private companies making money, might be more shady.
What if the government changes to authoritarian ?
Government different departments - not really centralised.
What if you are dying - if it is privatised can’t contact it as you are private company. Access data in emergency situations.
Government can give freedom to NOT collect the data. This one is the main differentiator!!!!
Data is split across 50 companies (though I don’t agree is a feasible model.
Having a baseline of data helps protects against terrorism. Wouldn’t matter you are being tracked if you are doing nothing wrong. Protected by the eyes of the government. So we are saying the government is like our buddy in this case.
0 notes
Text
Week 7 Teamwork Evidence
Just made this post to show some evidence I forgot to put up earlier.



.... ....
.... ....
.... ....
1 note
·
View note
Text
Week 7 Something Awesome Write Up - WiFi Signal Strength
WiFi Signal Strength

I want to figure out at what ranges and signal strengths will my PC connect to the Rogue WiFi vs connecting to the real one. I first step up both WiFi's to have the same SSID and security. As a result, in my networks list, they show up as one network, like intended.
My wireless access point is a Linksys WRT1900AC, while my Rogue WiFi is a Pendo mini 3-in-1 router and power bank.


My house has two levels, so I walked around the house recorded which wireless access point my PC connected to:
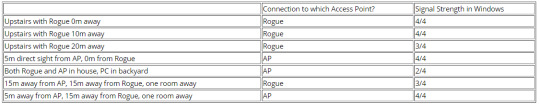
From the table above, I got fairly mixed results, indicating the signal strength from both devices was very similar. This is quite strange, as the Linksys router has 4 antennas on it, while the Pendo is just a pocket router. I think this is due to the placement of the Linksys router, as it is inside a TV cabinet close to many other electronic items.
It was good (and worrying) to see how easy it was to get my PC to connect to the Rogue WiFi. Basically, as long as I am closer to the PC compared to the Linksys router, the PC always connected to the Rogue. It seems that the algorithm for picking WiFi networks simply picks the one with greater signal strength. This is interesting, as my Linksys router uses Wireless AC 5ghz and 2.4ghz, while the pocket router uses Wireless N 2.4ghz only. It seems that 5ghz performance in my house is pretty bad, as the walls are double brick. The higher the frequency, the worse waves are at penetrating walls.
So to conclude, overriding WiFi is very easy. You just have to be closer.
0 notes
Text
Week 7 Something Awesome Write Up - DNS
Domain Name Servers (DNS)
There are a few types of DNS servers
Recursive name servers - Server that requests DNS information from the below three and caches results.
Root name servers - Contains mappings from .com -> TLD server.
TLD servers - Contains mappings from .com -> Authoritative name server
Authoritative name servers - The final name server, which actually contains the mappings IP -> Domain
Initially, I thought DNS was simple, but now I understand why the DNS server I initially downloaded (BIND) was so complicated. When a user goes on the internet to connect to a website, this is usually how the domain name is resolved:
Browser contacts recursive name server with the domain name
Recursive name server checks its cache to see if it has a mapping. If it doesn't, it checks with a root server for the given extension. For example, if you are looking for .org.au, then it will send a request to the .org.au root server. There are 13 root name servers worldwide.
The root server will respond the associated TLD server. The recursive name server sends a request to the TLD server to gain info about the authoritative name server which contains a mapping for the url, e.g. facebook.com.
The recursive name server contacts the authoritative name server for the IP, and caches it.
It returns the IP to the client.
DNSMASQ and Rogue WiFi
Dnsmasq is the DNS server I used for my project. Reading the specification, it is a DNS Forwarder, which is basically designed to forward DNS queries to recursive name servers. Dnsmasq is typically used for many things, such as performing validation on DNS server replies, and caching DNS queries. I have only used it for the functionality of local DNS, so that DNS queries are replied to from the forwarder with the attacker's PC.

The Rogue WiFi network works by setting the DNS field in the router to point to the IP address of the PC running dnsmasq. Hence, any DNS requests will go through dnsmasq first. Since dnsmasq is a forwarder, any sites I have not overridden will be resolved using the typical name servers, such as Google's 8.8.8.8 recursive name server.
DNS over HTTPS?
I was wondering why DNS requests are sent as plaintext. It turns out that if DNS requests were encrypted, ISPs and governments would not be able to track what website you are visiting! This article https://nakedsecurity.sophos.com/2019/04/24/dns-over-https-is-coming-whether-isps-and-governments-like-it-or-not/ provides a good overview on the technology.
Luckily, since DNS requests are sent as plain text, this has allowed the second part of the Rogue WiFi attack to be successfully executed.
Sources
How DNS works - https://cloudacademy.com/blog/how-dns-works/
DNS Server types - https://www.dynu.com/en-GB/Blog/Article?Article=DNS-Servers-Authoritative-Recursive-Root-TLD
0 notes