Don't wanna be here? Send us removal request.
Text

hacker clown
4 notes
·
View notes
Text


GIF of an ASCII hacker in different sized fonts
#ascii#hacker#hacking#cybersecurity#infosec#ascii art#trippy#hackerman#hackers#programmer#programming
3 notes
·
View notes
Text




Top 5 Reasons I like The Flying Wingman
He has nice colors
His bright orange and purple colors make him stand out in the sky. It's also easy to spot if he gets lost, as his colors are so recognizable.
He has a great design. The shape of the wings is aerodynamic and efficient, making it easier for him to fly quickly. He also looks stylish while flying through the air.
He is super loyal. He will always come when called to help his friends out of a pinch, no matter how far away he is. He is also very protective of his flock and will stay by their side until the danger has passed. He’s got lots of friends. The Flying Wingman makes friends quickly,
He is a simple design
His design is simple and streamlined, making it easy to build and maintain. He doesn't need many complicated parts or tools to assemble him, so anyone can do it.
He has a great personality. The Flying Wingman seems like he'll be friendly and always up for a chat. Someone who loves telling stories about his adventures with his flock, and he's always willing to lend an ear if someone needs an understanding friend. Sure seems like a great listener!
These are just a few of the many reasons why I like The Flying Wingman. His bright colors, stylish design, loyal nature and easy assembly make him the perfect companion for any flying adventure. Plus, his friendly personality never fails to put a smile on my face! With The Flying Wingman by my side, I'm sure to have many exciting adventures ahead.
I sure could use a Wingman for SaaS security!
I love The Flying Wingman's abilities when it comes to SaaS security. He is vigilant and always on the lookout for any malicious user activity that could put my cloud data at risk. Thanks to his superior surveillance skills, we can trust that our data will be safe in the sky.
The Flying Wingman is the perfect companion for any cloud-based journey. He's got a great look, a loyal nature, and he even helps keep our data safe from hackers. What more could you want in a flying friend? The Flying Wingman is by far one of my favorite companions to have on any adventure!
I'm sure that anyone who meets The Flying Wingman will quickly understand why I love him so much. From his bright colors to his loyal nature, he really is the perfect companion for any journey! Whether you need a friend or a guardian in the sky, The Flying Wingman is always there to lend a helping wing. So what are you waiting for? Get yourself a Flying Wingman and share your adventures with the world! You won't regret it.
Gentle GIFs like these are a lost art
I'm so glad you appreciate The Flying Wingman's gentle, flowing GIFs! I think they are a great way to relax and enjoy a few moments of peace in this hectic world. Plus, it's always nice to have some cheerful company when things seem overwhelming. That's why I love The Flying Wingman's GIFs
1 note
·
View note
Text
Top 10 clichés in Cybersecurity Explained

The cloud with a lock is probably the most overused cliché in the Cybersecurity industry
Here's the top ten list of clichès in cybersecurity explained:
1. "There are two types of companies: those that have been hacked and those that don't know they have been hacked."
This cliché is often used to describe the current state of cybersecurity. While it's true that many companies have been breached and may not even know it, this phrase oversimplifies the problem. There are actually many different types of attacks, and each company's vulnerability depends on a variety of factors.
2. "The only way to be completely secure is to unplug from the internet."
This is simply not true. While disconnecting from the internet can reduce your attack surface, it's not a foolproof solution. Attacks can come from malicious insiders, portable devices, and other sources.
3. "Prevention is the best cure."
This cliché is often used to describe cybersecurity strategy, but it's not always accurate. In some cases, it's better to detect and respond to an attack than to try to prevent it.
4. "Security is a cat-and-mouse game."
This cliché is often used to describe the ongoing battle between attackers and defenders. While it's true that security is an ever-evolving arms race, this phrase oversimplifies the problem. Security is actually a multi-dimensional problem that involves people, process, and technology.
5. "There's no such thing as perfect security."
This cliché is often used to describe the impossibility of achieving perfect security. While it's true that perfection is impossible, this phrase oversimplifies the problem. There are actually many different levels of security, and it's important to strive for continuous improvement.
6. "Security is a trade-off between convenience and security."
This cliché is often used to describe the need to balance security with other factors such as usability or cost. While it's true that security is sometimes a trade-off, this phrase oversimplifies the problem. In many cases, it's possible to have both security and convenience.
7. "An ounce of prevention is worth a pound of cure."
This cliché is often used to describe the benefits of proactive security measures. While it's true that prevention is better than cure, this phrase oversimplifies the problem. In many cases, it's more effective to detect and respond to an attack than to try to prevent it.
8. "Security is a never-ending race."
This cliché is often used to describe the need for continuous improvement in security. While it's true that security is an ongoing process, this phrase oversimplifies the problem. In many cases, security is a multi-dimensional problem that involves people, process, and technology.
9. "The enemy of my enemy is my friend."
This cliché is often used to describe the need to cooperate with others in the fight against cybercrime. While it's true that cooperation is often necessary, this phrase oversimplifies the problem. In many cases, the enemy of your enemy is not your friend.
10. "There's no such thing as a silver bullet."
This cliché is often used to describe the impossibility of finding a perfect solution to a security problem. While it's true that there is no perfect solution, this phrase oversimplifies the problem. In many cases, there are multiple solutions to a security problem, and it's important to choose the best one for your particular situation.
And while these clichés are frequent and common, it is important to remember that they oversimplify the cybersecurity landscape. Cybersecurity is a multi-dimensional problem that involves people, process, and technology. And while there is no silver bullet, there are many different steps that can be taken to improve security. So don't fall prey to these common clichés - instead, educate yourself on the realities of cybersecurity and take proactive steps to protect your business.

#cybersecurity#saas secuirty#ascii#ascii art#ascii gif#clichè#clichê#cliche#cybersecuirty industry#saas
2 notes
·
View notes
Text
5 ways to tell that company employees are using shadow IT

1. They're using unsanctioned apps: If employees are using apps that haven't been approved by the company, it's a good sign they're engaging in shadow IT.
2. They're accessing forbidden websites: If employees are visiting websites that are blocked by the company's firewall, it's another sign they're trying to get around corporate restrictions.
3. They're storing data on personal devices: If employees are storing work-related data on their personal smartphones or laptops, it's a clear sign they're circumventing the company's IT policies.
4. They're using unsecured networks: If employees are connecting to public Wi-Fi networks or other unsecured networks, they're putting the company's data at risk.
5. They're engaging in risky behavior: If employees are engaging in any other activities that could potentially jeopardize the security of the company's data, they're likely engaged in shadow IT.
But remember, shadow IT isn't always a bad thing. Sometimes, employees turn to unsanctioned apps and services because the sanctioned ones don't meet their needs. So, it's important to strike a balance between giving employees the freedom to use the tools they need and keeping the company's data safe.
If you're concerned that your employees might be engaging in shadow IT, talk to them about it. You might be surprised to find that they're willing to conform to your IT policies if they understand the importance of keeping the company's data safe.
2 notes
·
View notes
Text
5 ways cybersecurity is a cat and mouse game, explained

1. The arms race between attackers and defenders
2. The ever-changing nature of cyber threats
3. The need for constant vigilance
4. The importance of collaboration
5. The challenge of staying ahead of the curve
Cybersecurity is a constant battle between attackers and defenders, with each side trying to outwit the other. It's a cat-and-mouse game that requires both sides to be constantly on their toes, always adapting and evolving.
The arms race between attackers and defenders is one of the most important aspects of cybersecurity. As attackers develop new ways to exploit vulnerabilities, defenders must work to harden systems and close those gaps. This back-and-forth has led to major advances on both sides, with attackers becoming more sophisticated and defenders becoming more adept at detection and response.
The ever-changing nature of cyber threats is another key factor in this game. With new technologies and attack methods being developed all the time, it's hard for defenders to keep up. They must constantly be on the lookout for new threats and adapt their defenses accordingly.
The need for constant vigilance is perhaps the most important lesson of all. In cybersecurity, there is no such thing as being too prepared. Defenders must always be on the lookout for new threats and be ready to respond quickly and effectively if an attack does occur.
The importance of collaboration cannot be overstated. In today's interconnected world, no one can fight the battle against cybercrime alone. It takes a community of experts working together to share information and best practices to really make a difference.
Finally, the challenge of staying ahead of the curve is one that both sides must face. With the pace of change in the cybersecurity landscape, it can be difficult to keep up. But it's important to remember that the goal is not to be perfect, but to stay one step ahead of the attackers.
Cybersecurity is a complex and ever-changing field, but by understanding these key principles, we can all play a part in keeping our systems and data safe. Like we said. it's a cat and mouse game.

Further Reading
What is SaaS Security
What is Shadow IT?
5 Common Cybersecurity Vulnerabilities
3 notes
·
View notes
Text


Some ascii artwork and GIF for y'all.
Ascii cat by the fire - GIF
Ascii cat - PNG
Enjoy. We know lots of hackers have cats, so this seemed like a better graphical to use than dodgy hacker pics :)
#cat#cats#ascii gifs#ascii cats#ascii gif#ascii art gif#ascii#ascii art#meowbeauties#meowmeow#meow wow#saas security#infosec#art#ascii artwork#hackers#cybersecurity#saas security gifs
2 notes
·
View notes
Text




And looks like we are back!
Got banned and account terminated for a few months there, but we wrote to Tumblr support and got reinstated, SO WE ARE BACK!! Here is some of the latest ASCII art you guys have missed while all that was being all sorted out...
Great to be back and hoping to bring you more artwork soon.
These are just artworks from different projects, many of which got passed on as i work in marketing saas security and anytime I need an image of a hacker, everything we found online is offensively cheesy, so made these to be a little less offensively cheesy. Usually its used like in the background on part of the final marketing materials, notthe whole thing at once. If you have any stock photo type of hacker pics that are clearly not of real hackers, please share them with us!
#ascii gifs#ascii art gif#ascii gif#ascii art#ascii#hackers#hacker art#cybersecurity#ascii artwork#art#hacker#infosec#saas security#anonymous#gifs#gif#ascii faces#ascii media works#old web#hip#groovy#cool#new art#latestart#server room#cyber security#malware#data security#privacy#networking
27 notes
·
View notes
Text

Hacker VS HACKER
ASCII art GIF
#ascii art gif#ascii gifs#ascii gif#ascii#ascii art#ascii artwork#saas security gifs#saas security platform#saas security#trippy#cybersecurity#cyber art
2 notes
·
View notes
Text

Tripp GIF artwork of ASCII patterns depicting a hacker typing on his keyboard
3 notes
·
View notes
Text

#cybersecurity tips#cybersecurity#saas security#ascii art#ascii artwork#ascii#ascii drawing#so cool#hacker#hackers#hacker computer#trippy#artwork#computers#laptop
1 note
·
View note
Text

GIF that was used for an Anti-thought leadership piece on Medium
0 notes
Text
#saas secuirty#saas security platform#saas#cyber security#ascii art#ascii#ascii gif#saas security gifs#yfrimer#text gif#cyber tech#infosec#information security
1 note
·
View note
Text
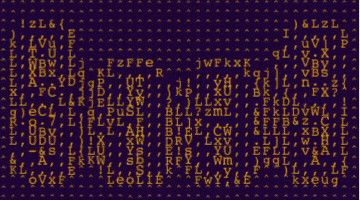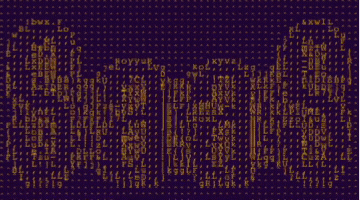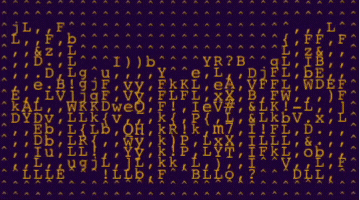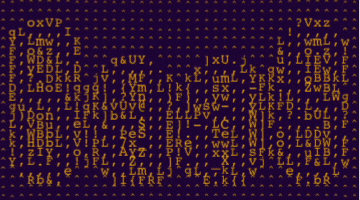
ASCII art of the letters S a a S
SaaS stands for Software-as-a-Service
1 note
·
View note
Text
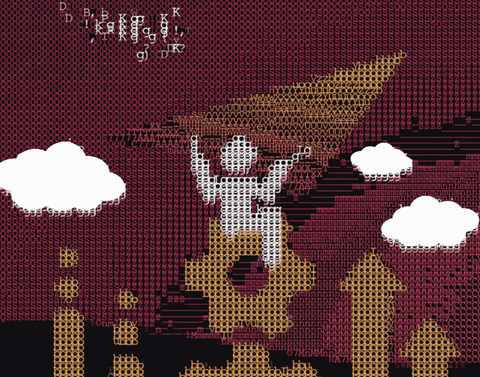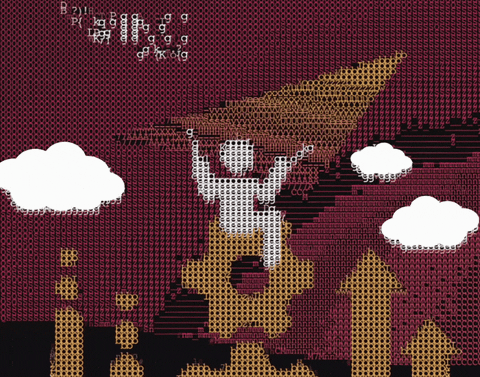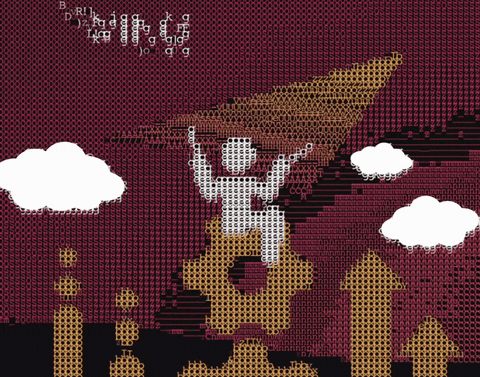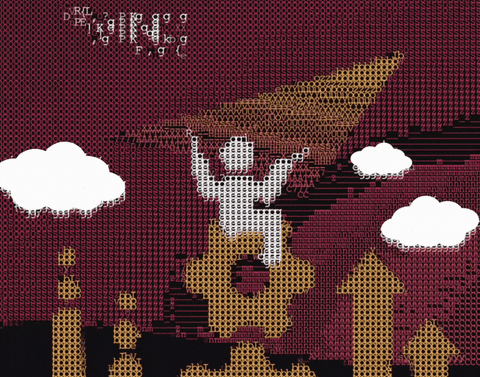
Artwork I created for an article about SaaS security but the final version here was rejected because it didn't meet the criteria the art director was looking for.
#ascii art#ascii artwork#saas secuirty#wing security#cyber security#infosec#wingman#paper airplane#gif#gifs#cyber gifs
2 notes
·
View notes
Text


GIF and Still-art of ASCII hacker at his laptop, hacking away. Created for use in a cybersecurity product, and they preferred a not "obviously fake" photo of a hacker
1 note
·
View note
Text

cloud security ASCII GIF
1 note
·
View note