The inner machinations of my mind are an enigma. - Patrick
Don't wanna be here? Send us removal request.
Text
I’ve said this before and I’ll say it again but it is absolutely an example of civilizational inadequacy that only deaf people know ASL
“oh we shouldn’t teach children this language, it will only come in handy if they [checks notes] ever have to talk in a situation where it’s noisy or they need to be quiet”
355K notes
·
View notes
Text
Where Do I Go From Here?
One of the questions I’m asked most often is what I want to do in Computer Science. I don’t completely have an answer yet, but there are a few things that are interesting to me. I know that I enjoy cryptography and cyber security and figuring out how those things work. I also enjoy video games and the development that goes into them (common answer I know). Of course my dream job would to be the next Jeff Bezos or Steve Wozniak, but those aspirations are somewhat unrealistic. However, it is fun to dream.
I suppose my dream job would be working for a video game developer (large or indie, both are good). I really like the creative aspects (My mom is an art teacher, so I grew up painting and drawing) as well as the programming side of it as well. I got a Game Developer Barbie last year, which is fun to look at. When I was a kid, the only Barbies you could buy were veterinarians, teachers, nurses, and things like that. I probably didn’t know what a game developer was, or even what a computer programmer was. It’s cool how Mattel is introducing STEM careers to younger girls.

As for areas that I wish that the Intro to Computer Science Class covered more deeply, there are many (however I understand it is an introductory class). Mostly, I wish we did more coding (because coding in Scratch isn’t really coding, but I guess it’s good for learning). I think it would be cool if we went over each of the main languages (C++, Java, Python, PHP, and so on) and then practiced coding a little bit in each different language. That way we could know the differences and similarities between them. That was the thing that bothered me the most about this class. I did more programming in Intro to Computer Engineering than I did in Intro to Computer Science (and they told me I wouldn’t have to code in Intro to Computer Engineering). I also would like to learn more about Cryptography, the section of it we learned in class really interested me. The Enigma Machine was fun to learn about but I really wanted to know more in depth things about it.

My favorite book for this class was 9 Algorithms That Changed the Future by John MacCormick. It was easier to understand and he explained the concepts in simple ways that made them seem less complex. I found myself not forcing myself to read this like I had to for the Pattern on the Stone by W. Daniel Hillis. That book was really dry and also very boring. It was kind of outdated in terms of Computer Science I thought too. I remember he said that he was writing the book on some “top of the line” laptop that now is pitiful compared to today’s hardware. Tubes by Andrew Blum was my second favorite textbook for this class. It was written from more of a journalist /investigator view than a “I’m a techie” point of view. The internet is very complex and it was interesting to learn where it “came from” (kind of).
Finally, here are some classes that I look forward to taking. CIS 520 Operating Systems I really piques my interests for some reason. It would be cool to learn how to design and make an operating system. The other class is CIS 200 Fundamentals of Software Design and Implementation, which so far I’ve heard everyone complain about. I’m curious to see how difficult it is and what kind of stuff we learn in there (OOP? Arrays? Uhhhh?)
Anyways, that’s about all I have time for today.
- Samantha
References:
Enigma Machine
Barbie Picture
9 Algorithms That Changed the Future by John MacCormick
The Pattern on the Stone by W. Daniel Hillis
Tubes by Andrew Blum
0 notes
Text
Computing Science & Mathematics
Today’s blog will be about how Computing Science and Mathematics are related, as one might infer from the title.
Some areas in the theoretical section of Computer Science that interest me are Quantum Computing, Cryptography, and Information Theory.
My favorite part is probably Quantum Computing. However, most people don’t even know what a Quantum Computer is or why they are so cool. It’s kind of similar to a traditional computer, but it uses the laws of quantum mechanics to process information. Also its using qubits (quantum bits) instead of the usual bits (1′s and 0′s). The qubit has two distinguishable states, like a regular bit, but it can also behave quantumly, so we can also use “superposition” and “entanglement” to calculate things even faster. The book The Pattern on the Stone by Hillis has a section on this from pages 71-76.
Superposition is where a particle can be in more than one place at once (electrons, protons, neutrons and so on all behave like this). They can be “up” at the same time they are also “down.” And also left and right, you might guess. Here, there, anywhere. Particles can also be entangled. This is where particles behave in unison, matching each other exactly or “dancing”, if you want to call it that. This can connection can happen at great distances (on opposite sides of the universe!), which makes it really amazing. Einstein described Entanglement as “spooky action at a distance.”
With superposition and entanglement on its side, a quantum computer can perform a lot of computations simultaneously because the qubits can have 1′s and 0′s, but also superpositions of them. Traditional computers can multiply very large numbers easily, but there is one thing they struggle with - factoring very large numbers (500 digits or more.) This is where quantum computing comes to the rescue. In 1994, Peter Shor (a mathematician at MIT) unveiled one of the most impressive algorithms ever. Shor’s algorithm describes how if a good quantum computer is available that it can factor large numbers easily.
Now, you may ask, why do we care about factoring large numbers? This part may interest you - factoring large numbers is involved in RSA encryption, a common way online retailers store and protect your credit card information. The retailer has a “public” key (really big number) which is available to anyone. It is the product of two large prime numbers that only the retailer knows. If an attacker could figure out those two prime numbers, they could easily access your credit card information (which if they had a quantum computer they could). For more on this, see Chapter Nine and Chapter Four of 9 Algorithms the Changed the Future by MacCormick.
Before you freak out, realize that if we develop powerful quantum computers we will also have a new (really powerful) method of encryption for sensitive data. This combines the one-time pad method and a quirk of quantum mechanics. It’s a little hard to explain, but KhanAcademy has a good video on what the one-time pad is. The quantum part of it relies on photons and the fact that they can be polarized at random. Let’s say two people (Gabby and Alex) are trying to communicate with each other. They use a laser that generates “entangled” (they move in tandem essentially) photons on the top of Alex’s house. Alex receives one half of the polarized photons and Gabby gets the other. They look at the polarization of each photon and either write down a “one” or a “zero.” So if Gabby writes down a key of 10110110, Alex should have 10110110 as well. However, if I spy on their communications, the polarization of the photons will change and Alex and Gabby will notice their keys don’t match and they’ll know someone is spying. Anyways, Alex and Gabby will keep going until they have a long string of numbers that they can use as a key to encrypt their data.
youtube
In recent news, Berkeley Laboratory in California suceeded at using their supercomputer Cori (the fifth fastest supercomputer in the world) to simulation of a 45-qubit circuit. That is the largest simulation of a quantum computer that has ever been achieved. Just a few more qubits and experts think the quantum computer will equal the power of most supercomputers. At 50 qubits, they believe they will achieve “quantum supremacy,” which is where the quantum computer becomes more powerful than the classic computer architecture.

Sources:
Berkeley Supercomputer
Quantum Computing 101
9 Algorithms That Changed the Future by John MacCormick
The Pattern on the Stone by W. Daniel Hillis
0 notes
Text
Making Meaning: Tubes
For this week, I will be writing a small report and book review on Tubes: A Journey to the Center of the Internet by Andrew Blum.
First, the book starts off with the author describing how one day, his internet broke. Well, not the entire internet obviously, Apparently a squirrel may have chewed the cable. So just his internet was out. I can kind of relate to this situation because at my house in Cheney, we can only get satellite internet. It often breaks if there’s a windy day or a big thunderstorm. The top speed is 5 mb/s. Pretty sad, I know. It would be nice if we could get broadband, however there is a river between our house and the town...and they won’t run a cable across it. Now, after reading Tubes, I find this hilarious considering there are cables running across both the entire Atlantic and Pacific Ocean. I presume there are some business reasons behind it, perhaps there aren’t enough customers to justify the cost of it. But I digress.
The author begins to wonder “Where exactly does the Internet come from? Where is the center?” I kind of scoffed at this question, because the Internet is a bunch of devices connected together...how could there be a true center? It also bothers me that people always talk about the Internet like it’s magic...like there’s some sort of alien spaceship the comes down and transmits some waves and signals...and bam. That’s it. That’s how we get the internet. When in reality, it is a physical, true thing that takes up space on Earth. This talk of finding the center of the Internet reminded me of a SciShow video on How to Break the Internet. It goes a little into about the cables involved and that sort of stuff.
Anyway, so Blum begins tracing the wires from his house and thus begins his “Journey to the Center of the Internet.” It starts off kind of boring, with him just visiting big warehouses of large tall boxes with blinking lights...I swear he did that almost 50 times in this book. But towards the end, it started to get exciting and I began to enjoy reading this book.
One of my favorite parts was the chapter called “Cities of Light.” It talks about what exactly is going on inside the wires, which was pretty interesting to me. It’s fascinating to think about how we can send a message from the United States to Europe in like .2 seconds but it still takes half a day to travel there by plane. The speed of light seems almost instantaneous. It also was cool how Blum got to see them laying cable in the manholes to create these labyrinthine “fiber highways.”
He also visited a lot of buildings that used to be hubs for telephone and telegraph communications. At the time, these were thought to state of the art and very effective ways to communicate. However, we obviously don’t use these methods as much anymore. We use the Internet to talk to people halfway across the world. Clearly, it’s an easy and effective way...but could it be better? It’s fascinating to think “What’s next after the Internet? What will be the next ‘end-all’ communications technology?”
Probably my most favorite chapter was Where Data Sleeps, when Andrew Blum goes to one of Google’s data storage centers where it’s very top secret and high security. It was funny how he only made it to the lunch room. When he went to the Facebook data storage center, it was all very open and friendly (albeit only half finished) and he actually got to tour it. This makes sense though. Google is where people often ask very personal and private questions / searches so it seems logical that the center would be very high security. Facebook is where people go to share things with their friends and family that usually aren’t that private (ex: baby photos, dog photos, life updates).
He then goes on to say that we live on the Internet and that there isn’t really a true center to the Internet. Which is true, but kind of disappointing end I think. But I did like the epilogue though. All in all I though it was a good book and something that I liked enough to try and find similar books to it.
- Samantha
Sources:
Tubes (chapters 5 and 7) by Andrew Blum
How to Break the Internet by SciShow on YouTube
0 notes
Text
The Filter Bubble
This week’s blog is about the concept of the “Filter Bubble.” This happens when a search engine or social media algorithm personally adapts to what you have looked up in the past and makes an educated guess about what you would like to see in the future. In doing this, they gain a higher chance of getting your “click,” like, comment, or whatever it may be.
For my experiment, my guinea pig was my friend Chase (a fellow K-state student). I used his personal laptop for about fifteen minutes to see what it was like browsing the internet on it. I turned the Adblock off on his laptop and on mine as well (we figured out pretty quickly that was necessary.)
The websites I went to were Reddit, Facebook, Twitter, Tumblr, YouTube, Amazon, and Ebay. All of these websites are pretty popular and I visit them often on my own computer.
So first things first, Reddit. I noticed that his “front page of the internet” was quite different from mine because Chase wasn’t logged into his Reddit account. When I went there, I just got the default homepage with the most popular subreddits like r/funny, r/aww, r/pics, and r/todayilearned. On my laptop, I get pages like r/showerthoughts, r/mildlyinfuriating, r/politics, and r/FloridaMan (one of my favorite subreddits). All of these are subreddits I subscribe to on my Reddit account, which makes sense.
Next, I went to Facebook. Pretty normal other than Chase was friends with a bunch of people I didn’t know and they posted some weird stuff. Also there was some ads on the side for Bare Minerals (a natural makeup brand) which I asked Chase about. He said that he had been looking up some stuff about skincare so that is probably why. There was also some ads for games (Battlefield I think it was) and Chase is a “gamer” I guess so that is why he got those (I play games too but not really as much as he does.) On my Facebook, I get advertisements for music festivals like SXSW. This is because a couple of days ago I was looking up how much tickets to Coachella cost, most likely.
YouTube was up next. They have some of the best algorithms out there today I think because with the recommended videos I can spend up to two hours on there watching random stuff and “falling into the YouTube hole.” In my recommended videos, I get a lot of stuff related to comedy, music, the PC building community (I like those videos), and makeup (tutorials, reviews, etc.). It’s kind of a weird combination but somehow YouTube makes it work and manages to suck me in. The stupid Buzzfeed videos are the worst, I fall for the clickbait every time. Chase got recommended videos about music (usually popular artists like The Weeknd and Lorde) as well as gameplay videos (for Stalker, Fallout, and Battlefield). Also I’ve noticed that YouTube usually tailors the ads before videos based on the type of videos you’re watching (although I have adblock on 90% of the time because they annoy me). So if you’re on a gaming channel, like Markiplier or SSSniperwolf, you’ll probably get an ad for Tom Clancy Ghost Recon (I got that.) But for music videos, it will usually be more generic (car insurance, filing taxes) because almost everybody watches those and they get a lot of views.
Finally, I went to Amazon. It was pretty boring because Chase wasn’t signed in so he just got the default page. My Amazon page has recommended items like Nerd Ropes (don’t ask), craft supplies, computer monitors, and other random things that I’ve looked at on Amazon in the past few days.
As for further reading, I would recommend 9 Algorithms That Changed the Future by John MacCormick and Chapter 5 of The Pattern on the Stone by W. Daniel Hillis.
Anyways, that’s about it for the Filter Bubble.
Sincerely,
Samantha
0 notes
Text
Book Review
Today, I will be talking about my thoughts on the book, The Pattern on the Stone by W. Daniel Hillis. I thought it was pretty interesting, however it could be sometimes dry depending on the subject of the chapter. I am most used to reading exciting fiction books, so that could be part of the problem.
I did learn a lot while reading this book, and almost every chapter contained new information. My favorite part of the book was chapters 6, 7, 8, and 9. I did not care very much for the first part of the book, as it could be longwinded at times and was easy for me to get distracted while reading. However, I did enjoy when he was explaining that a computer could be made out of pretty much anything you want, and how he built a computer that could play Tic Tac Toe out of Tinkertoys.
I liked Chapter 6 (Memory: Information and Secret Codes) because of the descriptions of compression and the encryption discussion. Hillis used examples that were easy for me to understand and described how the book itself could be compressed. He also talked a little bit about encryption and encryption keys, which I also liked. The concepts were explained in a way that was comprehendible for me and it was also interesting to read about.
Chapter 7 (Speed: Parallel Computers) was enjoyable for me as well. I liked reading about parallel computers and how they worked. There were arguments and people were skeptical when the idea of these parallel computers was first introduced. However, as technology progressed and computers became more common and efficient, people began to realize just how powerful these machines could be. In fact, the fastest computers today are massively parallel and have lots of processors working together to be that way.
Probably my second favorite chapter of the book was Chapter 8 (Computers That Learn and Adapt). Software that can change and learn, or "get smarter" is very interesting to me. I also appreciated the idea of proportional control thermostat because sometimes the room just doesn't heat up or cool down fast enough for me! The AI program that Patrick Winston made was capable of being trained to recognize things like an arch was another part of the chapter that I liked. Hillis' explaining of artificial neural networks was pretty cool as well. It's hard to think that something as complicated and as mysterious as the human brain can be simulated using modern technology.
However, I saved the best for last. My favorite chapter of this book was number 9 (Beyond Engineering) it goes deeper on the topic of Artificial Intelligence and how exactly the brain works. I also enjoyed the story about the monk Roger Bacon and the creepy talking head he created. Kind of reminded me of some weird “Ex Machina” stuff. When he was talking about the brain, it was cool to learn that certain parts of the brain are specialized and devoted to names, or language and grammar. However, if part of the brain is damaged (like in a stroke, for example) the neurons in a different part of the brain will adjust and be recruited to "relearn" that function. Hillis' discussion on simulated evolution was interesting as well (although it was kind of hard to understand at times).
Overall, I enjoyed reading the book and probably would've never reached for it on my own, so I suppose it's a good thing I am taking this class. And I have one small complaint: he never put the accompaning diagrams on the page where he was discussing them... it was always the next page! That would confusing and annoying to have to flip pages, but maybe it's the publisher's fault I guess.
See you later, Samantha
References:
The Pattern on the Stone by W. Daniel Hillis
(Chapters 6, 7, 8, and 9)
“Ex Machina.” Directed by Alex Garland. 2015.
1 note
·
View note
Text
The Minimax Algorithm
Today, I am going to talk about the Minimax Algorithm, which is an algorithm used for finding the endings of a zero sum game.
First of all, you may wonder what exactly is a zero sum game? Some examples are Poker, Chess, Tic-Tac-Toe, and Checkers. The defining traits of a zero sum game are that there is a total payoff or “Utility” that can be divided among the players. This utility is always balanced because in order for one player to win the game, another player must lose by that same amount of utility. If there is a tie, the utility is not distributed, so it is still equal.
How does this algorithm work? Well, first a tree of possible moves is created and one player’s (let’s call them A) goal is to minimize the utility of the other player (i.e. make them lose). The other’s (player B) goal is to maximize the utility of player A (i.e. let them win). Hence, the name, Minimax.
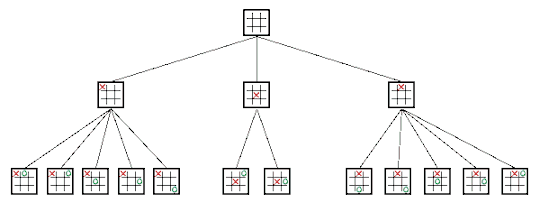
Here is a quick example of an outcome tree for the game of Tic-Tac-Toe.
Each of the possible moves that ends the game (terminal nodes) in the tree is given a value, and moves that have no effect (no winner or loser) are assigned a zero value. So the player who wins (maximizing player) is given 10 points and the losing player (minimizing player) is given -10 points, for example. If the game is played optimally neither player will win and the game will end in a tie (no points awarded). Depth (number of moves looked at that come next) may also be a factor in more complicated games like Checkers or Chess.
This video on YouTube goes pretty in depth and explains it in a good way, it’s where I got most of my information because the Wikipedia article didn’t make any sense.

Here is the pseudocode for a Minimax algorithm.
John von Neumann was a brilliant man who made several large contributions to many fields (mathematics, physics, economics, Von Neumann architecture...etc.). He was integral in the development of game theory and the digital computer. Von Neumann also worked on the Minimax. He first developed this algorithm in 1928 and did the first proof of it then. One of the things he said about it at the time was “As far as I can see, there could be no theory of games … without that theorem … I thought there was nothing worth publishing until the Minimax Theorem was proved.”
The Pattern on the Stone by W. Daniel Hillis goes more in depth on the more abstract and theoretical concepts of an algorithm in Chapter 5. Hillis mainly uses chess to describe how they work, but he does bring up Tic-Tac-Toe sometimes as well. He says that fast heuristics (which are not always super accurate, they are more like educated guesses) are better than algorithms (which usually exhaust all possibilities and come up with the best way to play but are very slow to calculate) when it comes to complicated games like chess. In the case of Tic-Tac-Toe, where it is easy to come up with all lines of play, an algorithm is okay to use.
The Minimax algorithm can be found in the real world in programs for games such as Tic-Tac-Toe, Chess, Checkers, and Go. The “maximin” aspect can even be applied in philosophy. In John Rawl’s book A Theory of Justice it is mentioned in the Difference Principle. The principle states that social and economic inequalities should be ordered in a way that they have the most benefit to those who have the least amount of advantages in a society.
The Turing Machines chapter in TPOTS also is a helpful reference in learning about algorithms and whether or not computers are capable of “thoughts” as complex as humans.
About all I can write on the topic. See you next time.
References:
Minimax Algorithm by breaktech: https://www.youtube.com/watch?v=ui3GPfSnT8E
The Pattern on the Stone by W. Daniel Hillis
Minimax Wikipedia article
A Theory of Justice by John Rawl
0 notes
Text

0 notes