Don't wanna be here? Send us removal request.
Text
Google is ending support for the Explorer Edition of Glass

Google is rolling out one more update for the Explorer Edition of Glass before cutting off support for its old wearable. The tech giant introduced Project Glass back in 2012, opening it up for preorders for $1,500 each. Despite people raising privacy concerns about its ability to record videos, the company quickly released an upgraded version of the device. It soon decided to change its approach and target businesses, though, releasing an Enterprise Edition of the device in 2017. The company will continue supporting the enterprise version, suggesting that it's doing better than its older sibling. In a support page detailing the final update, Google says users will need to manually download, unzip and install the file. Doing so will allow them to pair Glass with their phone -- MyGlass will no longer work, but Bluetooth pairing will stay -- as well as take photos and videos, as usual. Those who don't update the device can continue using it, but mirror apps like Gmail, YouTube and Hangouts will no longer work. After February 25th, 2020, though, they need install the update or they'll no longer be able to use Glass if they're not logged in or get logged out. They can wait until they get kicked out of the system to install the file, but they'll have to keep in mind that the update will only be available until February 25th, 2022. Read the full article
0 notes
Text
Apple now owns Intel's mobile modem business

Intel completed its sale of the "majority" of the company's smartphone modem business to Apple today. The deal -- which was announced in July -- is valued at $1 billion, though Intel claims it is still taking a "multi-billion dollar loss," according to Reuters. By owning Intel's modem technology, Apple will be able to source more components for its connected devices in-house rather than turning to vendors like Qualcomm -- a company with which Apple has a bitter relationship. The sale only includes Intel's smartphone modem business; the chipmaker will still be creating modems for PCs, IoT gadgets and autonomous vehicles. Intel claims that Qualcomm's anti-competitive patenting tactics forced the sale of its smartphone modem business to Apple. The company's executives have been testifying about the claim in court as part of the FTC's ongoing antitrust case against Qualcomm. A judge ruled against the company, but Qualcomm appealed the decision, bringing the case to the 9th U.S. Circuit Court of Appeals. With the deal completed, Apple will own more of its technology stack and supply chain, and will be less dependent on third-party vendors when it comes to designing and manufacturing some of the most crucial components of its mobile devices. The company has been transitioning away from third-party chips since the iPhone was first released -- the first three models used Samsung CPUs before Apple unveiled its A-series chips -- to gain more control over its devices and enable better performance. Apple is even rumored to be phasing out Intel CPUs in some of its computers, replacing them with the company's own ARM-based processors. Read the full article
0 notes
Text
MacBook Pro 16-inch review: The ultimate Apple laptop

Pros Powerful Intel CPU and AMD GPU Excellent new keyboard Gorgeous 16-inch Retina Display Best-in-class speakers and mic Relatively low starting price Cons Still only four USB-C ports No SD card reader Upgrades can get expensive quickly Summary Apple’s 16-inch MacBook Pro is basically every creative’s dream machine, with a ton of power and a vastly improved keyboard. The larger screen makes it more useful than the 15-inch model it replaces, and it even has decent battery life for a workstation. The 16-inch MacBook Pro is the closest Apple has come to recreating the glory of that machine. It's incredibly powerful, and the company finally listened to complaints about its shallow butterfly keyboards and equipped this model with more traditional scissor switch keys. While it doesn't address every pro-user issue -- you're still limited to four USB-C ports and there are no card slots -- it's hands down the best MacBook Pro available today for creatives.
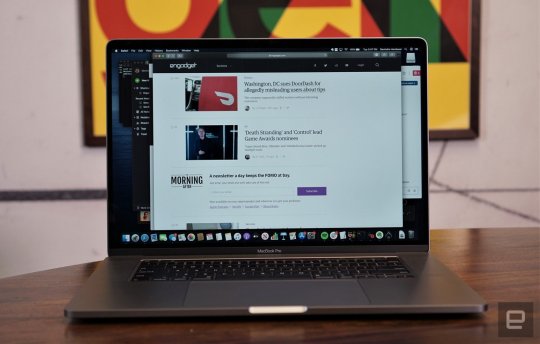
Let's get the obvious differences out of the way first: its 16 inch screen is noticeably larger. Like many PC makers, Apple managed to fit a larger display into a similarly sized case by shaving down the bezels around the side and top. The result is a gloriously immersive, 500-nit Retina Display that can finally compete with Dell's Infinity Edge screens. It's a legitimate step up from the previous model, and a reminder of the glory days of Apple's 17-inch notebooks. And then there's the new Magic Keyboard -- which feels more like a miracle keyboard. Mac users have been complaining about the flat Butterfly keyboards ever since they debuted. And, while Apple eventually fixed some sound and reliability issues, they never felt great to type on. It always felt like pretend typing on a pane of glass -- it's not satisfying, and barely functional. The Magic Keyboard fixes that issue by going back to the scissor mechanism Apple has been using in its desktop keyboards for years. There's a millimeter of key travel now, and they aren't wobbly like they used to be on older MacBook Pros. In comparison, the Butterfly keyboards had a mere half-millimeter of travel, and Dell's XPS 15 offer a slightly deeper 1.3 millimeters.

I've almost forgotten what it was like to enjoy typing on a MacBook Pro, but this new keyboard brought me right back to my early days of writing on a second-gen MacBook Air. There's a responsiveness that makes the keyboard feel inviting, like it's a world-class instrument waiting to be played. That millimeter of feedback practically makes the notebook feel like an extension of my body, instead of a tool that annoys me every time I touch it. Even butterfly keyboard defenders will have a hard time denying that the Magic Keyboard simply feels better, and it can't reach other MacBooks soon enough. Apple even compromised a bit with the Touch Bar: the physical Escape key is back! And there's a separate TouchID and power button, which makes it easier to find without looking. I'm still not completely sold on the Touch Bar's usefulness, but at least it feels like less of a hindrance to my workflow.

The 16-inch MacBook Pro is a bit taller and wider than the 15-inch model by a few millimeters, and it's marginally thicker at .64-inches, instead of 0.61. It's heftier too at 4.3 pounds, instead of around 4. It definitely weighed down my backpack more, and it's slightly larger dimensions make it a bit of a chore to fit on cramped coffee shop tables. But I think the trade offs are worth it for the sheer power Apple managed to stuff into this machine. It would have been nice to see more of a design refresh, but Apple's unibody aluminum case looks as sleek as ever, so I can't really complain much. Under the hood, you've got Intel's latest six and eight core i7 and i9 processors, the latter of which can reach boost speeds up to 5GHz. You can also choose between AMD's Radeon Pro 5300M and 5500M GPUs with 4GB of VRAM. That more powerful GPU can even be configured with 8GB of VRAM for heavy-duty 3D rendering work. Apple claims the 5300M graphics are 2.1 times faster than the 15-inch MacBook Pro, and that makes sense since it's powered by AMD's new rDNA architecture.

Apple is breaking new ground for memory and storage in the MacBook Pro as well, with support for up to 64GB of DDR4 RAM and 8 terabytes of fast SSD storage. Notably, Apple says this is the largest SSD ever in a notebook, and we haven't found any evidence out there to prove otherwise. These are fantastic high-end specs for programmers and artists alike. It used to be that you had to settle with a small SSD in a modern laptop and carry around a portable drive for larger files. The 16-inch MacBook Pro gives you the sort of storage flexibility you'd expect from a desktop workstation. Of course, you'll pay dearly for maxing out those specs. Bumping up to 64GB of RAM is an additional $800, while the 8TB of storage is an eye-watering $2,200 extra. These aren't really upgrades meant for average users, but I'd bet huge VFX firms wouldn't think twice about spending $5,899 for a decked out MacBook Pro to speed up their workflows.

Our review unit, which featured an eight-core i9 CPU and AMD Radeon Pro 5500M graphics, tore through whatever I put in front of it. It's clearly more than I needed for my typical workflow, which mostly involves juggling a ton of browsers, light image editing, Evernote, Slack and Spotify. When I gave it a serious job, like transcoding a 4K movie clip, it leaped into action. Handbrake handled a two minute clip in just 52 seconds, whereas it took the new 15-inch Surface Laptop 3 a full minute longer. In the Geekbench 4 Compute benchmark, the new Radeon Pro GPU also scored twice as much as the last-gen AMD hardware. Simply put, this thing screams. As I was benchmarking the 16 inch MacBook Pro, it never felt hot to the touch, and while the fans were noticeable when they spun it, they weren't annoyingly loud. As part of the notebook's revamped cooling setup, the fans can now push out 28 percent more air than before, and the heatsink covers 35 percent more internal space. All of those improvements, and the slightly larger case, means the new MacBook Pro should be able to withstand heat better than any of Apple's previous notebooks. Apple also made a slew of other compelling upgrades to the 16-inch MacBook Pro. A new six speaker setup makes music and movies sound great. It's no replacement for dedicated speakers, but it's impressive for something coming out of a very thin laptop. There's also a 3-microphone array that Apple is putting against standalone mics like the Blue Yeti. That's definitely going a bit too far, but recordings I've made sound good... for a laptop mic at least. And there's very little background hiss. It's more useful for video chats and shouting at Siri, since pro users tend to be pretty religious about their preferred mics.

Unfortunately, you're still stuck with 4 Thunderbolt 3 USB-C ports for connectivity. It'd be nice to see Apple bring back an SD card reader, but unlike the keyboard, that's one area where the company is refusing to back down. At least USB-C dongles and accessories are cheaper and better these days, but I've talked to plenty of pro Apple users who still pine for the flexibility of that 2015 MacBook pro. The new 100 watt per hour battery also lived up to Apple's marketing hype. The company claims it'll last up to 11 hours -- during our battery test it survived for 11 hours and 20 minutes. Of course, we were just looping an HD video, you can certainly expect it to drain faster under heavy duty workloads. Apple includes a new 96-watt USB-C power adapter in the box -- the beefiest we've ever seen on a MacBook Pro. It's only a bit larger than the 15-inch notebook's adapter.

Surprisingly, Apple is keeping the 16-inch MacBook Pro at the same $2,399 starting price. That's a pretty great deal for all the upgrades you get. Shell out $2,799 and you can step up to the Core i9 model with the best Radeon Pro graphics. That's not too pricey for this category, though you can get that same processor and decent NVIDIA graphics on the XPS 15 for $2,350. It's no surprise that a Windows PC is cheaper -- what's important is that Apple once again has a compelling high-end notebook to keep frustrated Mac users from jumping over to Windows. The 16-inch MacBook Pro is the closest Apple has come to crafting the ultimate notebook. It's exactly the upgrade Mac fans have been waiting for, even though it might not have all the ports they want. It's so fast, I don't think the Mac faithful will mind carrying around an SD card reader. Read the full article
0 notes
Text
Tesla's electric ATV matches well with the Cybertruck

Besides the electric Cybertruck, Elon Musk also showed off an apparently Tesla-designed electric ATV. It's not available as part of the pre-orders currently live on Tesla's store, but in the presentation it was used to show off how the Cybertruck's adaptive suspension tilts for easy loading. It can apparently charge directly from Tesla's truck while sitting in the bed, but with production not scheduled to begin until late-2021, there's plenty of time for the company to work out this toy vehicle. Gallery: Tesla Cybertruck







Read the full article
0 notes
Text
Now Twitter users can enable two-factor without linking a phone number

Twitter has finally made a change users have been waiting a long time to see. No, it's not editable tweets, but as of today everyone can enable two-factor authentication on their account without linking a phone number. While SMS-based two-factor can be a fallback for people who lose access to code-generating devices or don't have security keys, it's very vulnerable to SIM-swapping attacks. Twitter added code generator support a while ago, but still asked users to add a phone number if they wanted the extra verification and you couldn't remove the fallback. That's upsetting for those concerned about their privacy, they may not want to link a phone number to their account at all, and Twitter has already admitted that it used phone-numbers to target ads even for users who declined that. Attackers used SIM-swapping to send tweets from Twitter CEO Jack Dorsey's account earlier this year, and while the exploit didn't use two-factor codes, it showed how vulnerable the SMS-based system can be. If you already have a phone number linked in your profile, then you can go ahead and remove it now. However, a security engineer noted that you can't remove the number and rely simply on a security key for access since that's only supported on the website.

Kayvon Beykpour ✔@kayvz Another

update today: you can now use Two Factor Authentication without linking a phone number. If you already have your phone number linked along with App-based 2FA, you can unlink your

it in the "Account" section of your settings while still keeping 2FA on. https://twitter.com/TwitterSafety/status/1197621020229804054 … Twitter Safety ✔@TwitterSafety We're also making it easier to secure your account with Two-Factor Authentication. Starting today, you can enroll in 2FA without a phone number. https://twitter.com/TwitterSafety/status/1134174785137782789 … 172 10:09 PM - Nov 21, 2019 Twitter Ads info and privacy Read the full article
0 notes
Text
Here's How Scammers Tried to Dupe Trend Micro Customers

Unlucky Trend Micro customers ensnared in the insider hack at the antivirus company are being bombarded with fake tech support calls seeking access to their computers. "The first call seemed very legitimate to me," one customer named Rona told PCMag. "I almost fell for it." Rona, who requested her last name be withheld, was among the estimated 68,000 Trend Micro users who had their names, email addresses, phone numbers, and customer support ticket numbers exposed in the breach. Since August, Trend Micro has been investigating why customers were receiving fake tech support calls and sourced it back to a rogue employee who was selling customer information to an unknown third party.
How the Scam Works

Rona, who is based in Alberta, Canada, said she tried to warn Trend Micro about the potential hack in early October when she received a mysterious call on her cell phone from the scammers. The man, who had an "Indian or Pakistani accent," said he was contacting her on behalf of Trend Micro to report a problem with the company's antivirus software, which she's used for the past decade. The mysterious man knew Rona's name, as well as how she had recently called Trend Micro's help line to install the company's antivirus software on her mother's computer. He then asked Rona to open an email he had sent, which outlined the steps she needed to take to fix the problem. "I asked why they were not sending the fix through normal downloads. They said the servers were also infected and that is why they needed to do the fix via email, Rona said. "Since I was at work we decided that they would call me on Saturday, when I would be at my laptop." If Rona had been at her laptop when the scammer had called, she might have simply followed the man's instructions, assuming the request to be legit. But after the call, she thought the whole story of an infected Trend Micro server was suspicious. "So I phoned Trend Micro (the real company) and they told me it was scam," she said, which caused her to promptly delete the email the mysterious man had sent. According to Trend Micro, the company's technical support never makes unsolicited phone calls to customers. A call will only be made if it's been pre-scheduled. Nevertheless, many Trend Micro customers are probably unaware of the policy.
Red Flag No. 1: A Valid Support Ticket Number
In Rona's case, the calls from the scammers didn't stop. Mere days after the first call, she received another from a man who also had an Indian accent, but sounded different from the first. Knowing that the man was likely part of the same scheme, Rona attempted to tease out details from the caller. "Eventually, he realized that I knew that he was scammer," she said. The man then made an alarming proposal. "He said, 'You have a really nice voice. You can pay me money and I'll sleep with you. How much do you want to pay?' Maybe he was trying to get my bank account number. I don't know." Rona promptly hung up. But the scam calls continued. She remembers receiving a third call from a man who was able to quote a valid Trend Micro customer support ticket number she has received from the company. That's when she began to strongly suspect Trend Micro had a serious breach on its hands. "I phoned them (the real Trend Micro) and I'm like how did they get my valid ticket number? That's not something you guess. And they just said, 'I'm sorry for the inconvenience," she recounted. "It was pretty obvious to me that an employee was behind this, but I didn't think Trend Micro was treating ouit serisly." In the meantime, scammers tried another tactic: bombarding her phone number with robocalls—sometimes three times a day—claiming Trend Micro was going to charge or credit her bank account, and that she need to respond. In all cases, the calls came from different numbers, making them unblockable.
Why No Earlier Warning?

The story from Rona matches the experiences other Trend Micro customers have been reporting to the company. "I received four phone calls this morning from someone saying they were with TrendMicro and that my account has been auto-renewed for $299.99," wrote one user in Trend Micro's support forums a month ago. "They told me I needed to log in to my computer and they would walk me through it; they told me they could help me get my computer to run faster free of charge." One customer reports the scammers trying to trick him into visiting a fake login portal for Trend Micro after supplying a valid support ticket. "When it was obvious they were up to no good and would not explain what they were doing, I disconnected my Ethernet cable and hung up," the user wrote in a separate forum post. Another user reported the scammers wanting bank account numbers on the pretenses of supplying a refund. So far, Trend Micro has remained mum on what the scammers were after, and if they were trying to install malware on to victims' computers. Whether Trend Micro will cover the costs for victims who fell for the scammers' schemes is also unknown. For now, the company has said it's continuing to investigate the breach with the help of law enforcement. The unnamed employee accused of supplying the customer information has also been terminated. Earlier this week, Trend Micro sent out emails to affected consumers notifying them about the breach. However, Rona questions why the antivirus vendor didn't warn customers about the threat sooner. Although Trend Micro did issue an advisory about the scam on Sept. 20, it was confined to a post on the company's support site. "It was really hypocritical of them. They put announcements on their web page about different companies having security problems, but they don't talk about their own," she said. "It feels like they are trying to hide it. There are people like my mother who could have easily fallen for this." In response to her concerns, Trend Micro's CEO Eva Chen did send an email to Rona apologizing for the breach. "We are taking actions to trace the data flow and collect evidence in an effort to assist shutting down the scammer group," Chen says in the email. "I promise that we have learned from this event and have already begun taking steps to help prevent this type of incident frm happening again." Read the full article
0 notes
Text
How to Find a Lost Smartphone

Uh oh. Where's your smartphone? If it's lost or stolen and you need to find it quickly, you have a few options. Apple owners can locate a device with the Find My app (known as Find My iPhone on pre-iOS 13 devices), ping an iPhone via an Apple Watch, or sign into iCloud to track down a phone. Google provides an app and website called Find My Device through which you can seek out your Android phone. If you believe your iPhone or Android phone may have been stolen or you don't want it falling into the wrong hands, you can remotely erase the information on it so no one else can access it. No matter what you own, here's how to locate your missing device.
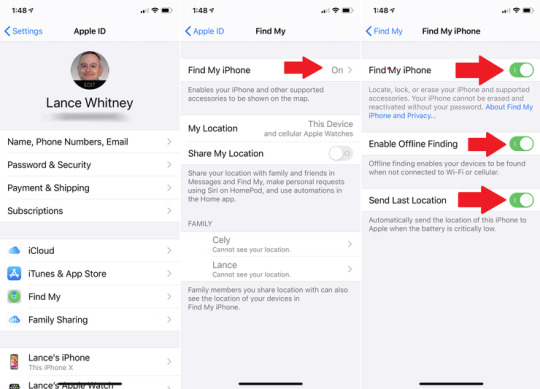
How to Find a Lost iPhone on iPad Before your device went missing, you should have set up the Find My (iPhone) feature. On iOS 13+, go to Settings > > Find My > Find My iPhone. On an earlier operating system, navigate to Settings > > iCloud > Find My iPhone. Either way, make sure that Find My iPhone and Send Last Location are both turned on. The new Find My app comes with the added bonus of tracking your device's location even if it's offline. If you want this capability, make sure to turn on the switch next to Enable Offline Finding.
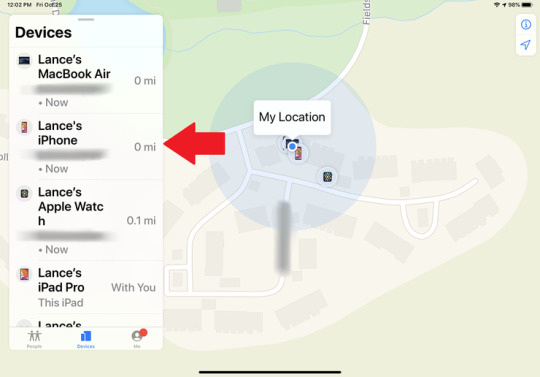
Find Your iPhone on the Map Now, let's say your phone is lost. The first trick is to simply call it from another phone, but if that doesn't work, it's time to enlist the aid of another device. If you own an iPad running iPadOS, fire up the Find My app. In the lower-left corner, tap Devices. The app displays a list and a map showing the locations of any of your Apple devices that are currently turned on. If your device is running an older operating system, the Find My iPhone app will automatically show any registered devices on the map and in the list.
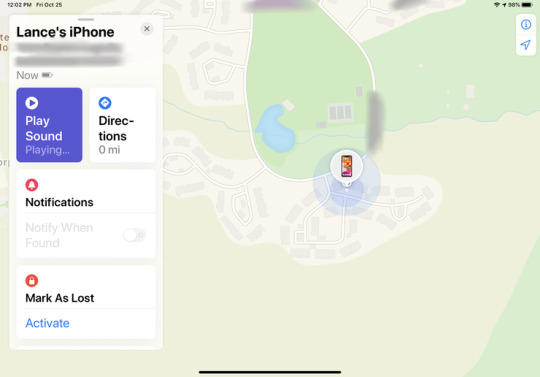
Select the iPhone Entry If your iPhone's location is visible, tap the icon on the map or the entry in the list. The app will then display a few options. Tap Play Sound and your iPhone will emit a pinging sonar noise to help you find it. Tap Directions within iPadOS and the app will give you directions to the lost device.

Mark Device as Lost If you can't find your phone, tap Mark as Lost in iPadOS (or Lost Mode in older versions). This mode lets you lock your phone so no one else can access it. If someone finds it, the device will display your contact information.

Erase iPhone If you can't locate your phone and are concerned about it being accessed by the wrong person, you can erase all the information remotely. Once the iPhone has been marked as lost, an option to erase the data becomes available. Tap Erase This Device (or Erase iPhone on older versions) to remove all personal information. The downside here is that an erased phone can no longer be tracked through this app, so only use this option if you have given up all hope of finding your device.
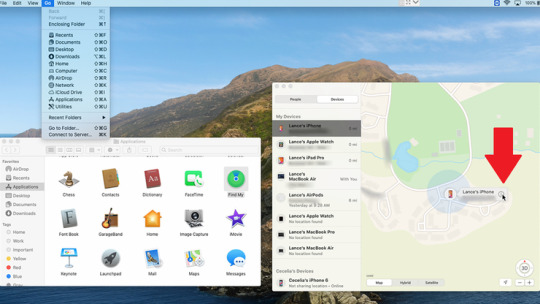
How to Find a Lost iPhone on Mac On a Mac with Catalina, you can use the Find My app to track down a missing iPhone. To get to the app, click Go > Applications > Find My in the top menu. In the Find My app, click the option for Devices. Click the entry for your iPhone from the list or select the icon on the map and click the Info button. From the Info menu, click the Play Sound button to play a pinging sound on your phone. Click the Directions button to view directions to your phone.

How to Find a Lost iPhone with iCloud If you don't have another Apple device handy, you can visit your iCloud website to find your phone. Launch your browser and go to iCloud.com. Sign in with your Apple ID and password. Click the icon for Find iPhone.

Select Your iPhone on the Map At the map, click the heading for All Devices and choose the entry for your iPhone. Click the green dot for your iPhone. From the pop-up menu, you can now play a sound on your device to help locate it, put it in Lost Mode so no one else can access it, or erase all the data.

How to Find a Lost iPhone with Apple Watch If you have an Apple Watch, you can use it to help find your phone. Swipe up from the watch face to display the Control Center. Then tap the icon that looks like a ringing phone. Your iPhone emits the pinging noise to help you locate it. The noise goes off just once, so you'll have to keep tapping the icon to keep the pinging alive.

How to Find an Android Device Google offers an app and web page where you can hunt down your phone. The app, which you can download from Google Play, is helpful if you have more than one Android device, while the web page comes into play if you have just one device. Now let's say your Android phone is missing, and the app is installed on your Android tablet. Fire up the app, and it should pinpoint the location of your lost phone. Select the lost device and ping it by selecting Play Sound.
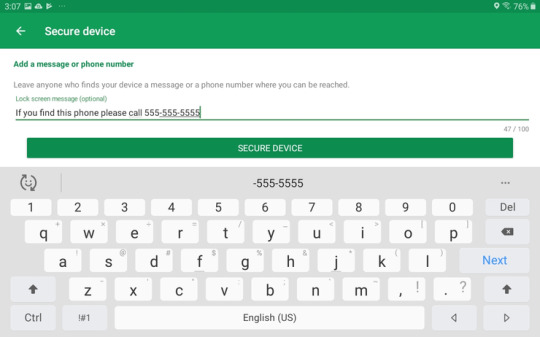
Secure Device You can lock the device and display a message for anyone who finds it. Tap Secure Device, then type a message to display on the lock screen. Tap Secure Device to finalize and lock the phone.
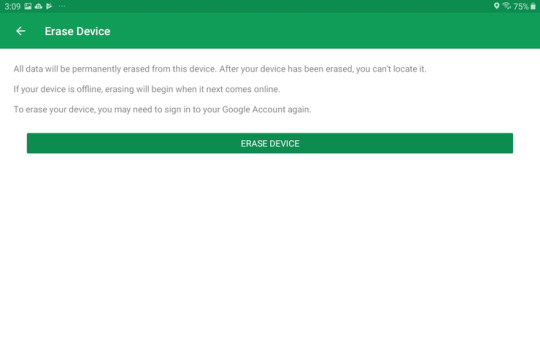
Erase Device Are you afraid the phone's been stolen or don't want someone to access the data on it? Tap Erase Device, then tap Erase Device again to finalize. Make sure you read the information on what will happen to your phone here because there’s no going back.

On the Web Alternatively, you can use the Find My Device webpage. Log into the site with your Google account. The page should display the location of your phone as long as it's turned on. Like with the app, you can ping the device, secure it, or erase all the data on it. This Google webpage can also assist you if you need to find, lock, or erase your Android phone. Read the full article
0 notes
Text
Facebook sues Israeli firm over WhatsApp call exploit attacks

Facebook has filed a lawsuit against the NSO Group, accusing the Israeli cybersurveillance firm of using WhatsApp to spread spyware to 1,400 mobile devices in 20 countries from April through May. While the tech giant didn't say who it believes NSO's client was, the attacks focused on devices located in Mexico, Bahrain and the UAE. WhatsApp did reveal, however, that the victims included 100 journalists, some prominent female leaders, human rights activists and political dissidents. In a statement sent to Engadget, the NSO Group has strongly denied that it had a hand in the attacks. It also claimed that its surveillance technology called Pegasus, which it sells to governments around the world, is being used to save lives: "In the strongest possible terms, we dispute today's allegations and will vigorously fight them. The sole purpose of NSO is to provide technology to licensed government intelligence and law enforcement agencies to help them fight terrorism and serious crime. Our technology is not designed or licensed for use against human rights activists and journalists. It has helped to save thousands of lives over recent years. The truth is that strongly encrypted platforms are often used by pedophile rings, drug kingpins and terrorists to shield their criminal activity. Without sophisticated technologies, the law enforcement agencies meant to keep us all safe face insurmountable hurdles. NSO's technologies provide proportionate, lawful solutions to this issue. We consider any other use of our products than to prevent serious crime and terrorism a misuse, which is contractually prohibited. We take action if we detect any misuse. This technology is rooted in the protection of human rights -- including the right to life, security and bodily integrity -- and that's why we have sought alignment with the U.N. Guiding Principles on Business and Human Rights, to make sure our products are respecting all fundamental human rights." The WhatsApp attackers inserted Pegasus into victims' phones by calling them -- the victims didn't even have to pick up the phone to be infected. Facebook's lawsuit says that while the spyware isn't capable of breaking WhatsApp's encryption, it can access the messages after they've been decrypted on the receiver's device. The NSO Group previously confirmed that Pegasus was used to target the phone of a British lawyer, who contacted Citizen Lab and kickstarted the investigation that led to this lawsuit. That lawyer had represented plaintiffs who accused NSO of providing the tools to hack the phones of a Saudi Arabian dissident, as well as of Mexican journalists, among others. The company, however, denied that it uses its own technology to "target any person or organization." Pegasus, it said, is solely operated by "intelligence and law enforcement agencies," or its clients, in other words. WhatsApp head Will Cathcart, however, explained that the company is confident NSO was behind the attacks in a piece published by The Washington Post. "e learned that the attackers used servers and Internet-hosting services that were previously associated with NSO," he wrote. "In addition, as our complaint notes, we have tied certain WhatsApp accounts used during the attacks back to NSO. While their attack was highly sophisticated, their attempts to cover their tracks were not entirely successful." He also wrote: "NSO has previously denied any involvement in the attack, stating that 'under no circumstances would NSO be involved in the operating... of its technology.' But our investigation found otherwise. Now, we are seeking to hold NSO accountable under U.S. state and federal laws, including the U.S. Computer Fraud and Abuse Act... ...NSO said in September that 'human rights protections are embedded throughout all aspects of our work.' Yet it maintains that it has no insight into the targets of its spyware. Both cannot be true. At a minimum, leaders of tech firms should join U.N. Special Rapporteur David Kaye's call for an immediate moratorium on the sale, transfer and use of dangerous spyware." Read the full article
0 notes
Text
Huawei wants to license its 5G tech to US telecoms

Huawei is banned from selling its 5G technology in the US, but that isn't stopping it from trying an end run around that hurdle. Senior VP Vincent Pang told Reuters that Huawei is in early discussions to license its 5G tech to American companies. The talks are a couple of weeks old, but the unnamed firms have "shown interest" in both long-term deals and one-time transfers. Pang wouldn't predict if Huawei would land a deal, although he noted that any single-shot transfer would be expensive to maintain and develop. Company founder Ren Zhengei floated the possibility of these deals in September, but it wasn't clear at the time whether anyone would be receptive. However, that's not really the core problem. Huawei still sits on the US Commerce Department's Entity List, preventing it from doing business with US companies without explicit permission. A license or transfer deal could easily be considered a similar violation, even if no physical goods change hands. Politicians have been suspicious of Huawei and the possibility that it might slip Chinese government surveillance software into equipment, and it might not matter whose equipment that is. It's not hard to see why companies might warm up to the idea of a license. Current 5G networks are, outside of Huawei, dominated by Ericsson and Nokia. This would let American companies leap into 5G and offer more competition, even if they're technically 'borrowing' from Huawei. Read the full article
0 notes
Text
Instagram test helps you choose people to unfollow

Use Instagram for long enough and you'll probably rack up a few contacts that you don't really care about -- someone you followed on impulse and quickly forgot, perhaps. You might have a way to prune those unnecessary connections before long. App sleuther Jane Manchung Wong has discovered that Instagram is testing a way to group followers into categories, making them "easier to manage. Read the full article
0 notes
Text
Amazon cuts off three delivery companies publicly linked to deaths

Amazon has cut ties with three delivery contractors that were recently implicated in multiple deaths by a joint BuzzFeed News and ProPublica investigation. According to state documents obtained by the two publications, those companies now plan to lay off more than 2,000 employees, and in two of three cases, stop delivering packages for the e-commerce giant. #Amazon Read the full article
0 notes
Text
4 Features You Don't Want to Overlook About MX Player [2019 Facts]

Most of us are Android Users. And if you are searching what media player is best to use, well, it's hard to resist recommending MX Player! MX Player's ability to play the majority of video formats made it more exciting to use Android Devices. Read the full article
0 notes
Text
SEC puts a stop to Telegram's cryptocurrency plans in the US

Telegram's plans for its cryptocurrency and blockchain network may be in jeopardy. The US Securities and Exchange Commission has filed an emergency action and obtained a temporary restraining order against the company, which prevents it from Read the full article
0 notes
Text
Tesla may open 'Centers' to get around pro-dealership laws

Tesla may be planning an end-run around state laws that bar direct car sales and protect dealerships. Electrek sources claim the automaker is planning to open "Tesla Centers" in major urban areas that would theoretically avoid legal trouble by Read the full article
0 notes
Text
Nike’s Adapt Huarache are self-lacing sneakers you’ll actually want to wear

This probably isn't shocking to anyone who knows me, but I love sneakers perhaps too much for my own good. So when Nike introduced the Adapt BB with power laces earlier this year, I was pretty intrigued: It brought two of my favorite worlds together, sneakers and technology. #Nike #satelitebox Read the full article
0 notes
Text
iOS 13.1 review: A necessary update after a rough start

Major iOS updates tend to come like clockwork, but this year — well, this year has been a little weird. Earlier this month, Apple officially released iOS 13 for iPhones, iPod touches and the like, and all of its new iPhones came with the software already installed. Less than a week later, though, the company released iOS 13.1 and iPadOS, updates that bucked another trend by being shipped a few days ahead of schedule. #iOS #iPadOS #iPhone11 Read the full article
0 notes
Text
Central banks to question Facebook over Libra cryptocurrency

Facebook is about to undergo further scrutiny of its Libra cryptocurrency, and it may have to answer some difficult questions. Officials speaking to the Financial Times said that Libra representatives are meeting with officials from 26 central banks (including the Bank of England and the US Federal Reserve) in Basel, Switzerland on September 16th. The European Central Bank's Benoît Coeuré is expected to chair the gathering, which will question Facebook over the digital money's "scope and design." In response, Libra reiterated its earlier stance that it "welcome this engagement" with politicians and regulators, and that it "deliberately" set out a long launch schedule to discuss issues and modify its plans based on feedback. The conversation might not go the way Facebook and the Libra team hope. Coeuré in particular has warned that Libra has to clear a "very high" bar, and EU finance ministers in particular have worried that cryptocurrencies like Libra could destabilize finance and undercut the authority of government banks. France and Germany have both argued that Libra should be blocked in the EU as it would challenge the "monetary sovereignty" of governments. Facebook has pitched Libra as a way to democratize money, providing banking to many first-timers and creating a format that's independent of any one country. However, it's that last part that has officials and critics worried. While Libra is a "stablecoin" that should be pegged to the value of conventional currency, it could give Facebook and the Libra Association a tremendous amount of clout if it takes off. It may not have much choice but to make concessions if it wants the currency to be widely available, and even that isn't guaranteed. Read the full article
0 notes