Text
Cryptograms Week 3 (2)
These are getting increasingly harder, and while that might be good for my problem solving for harder ciphers, may not be good preparation for the exam. Thinking Richard will release an easy-medium level one so it won’t take too much time to solve and will be crack-able for everyone.
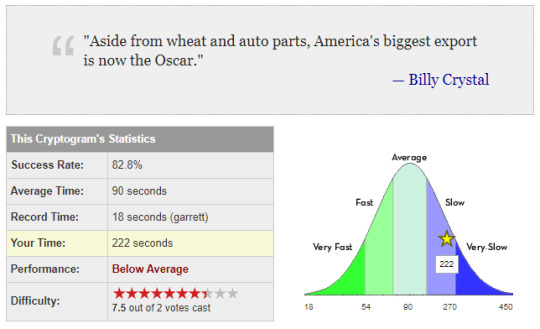
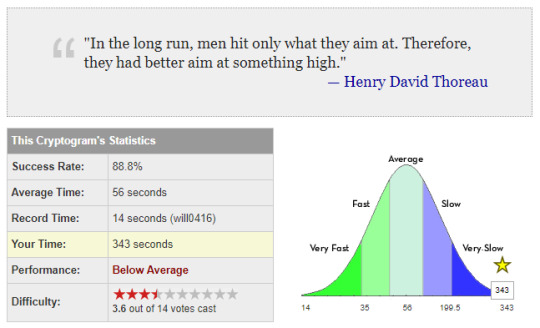
This one wasn’t too hard at all despite the rating. I guess since only two people voted, that’s why the rating is so high.
0 notes
Text
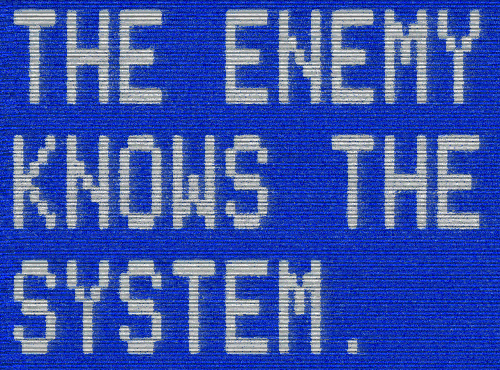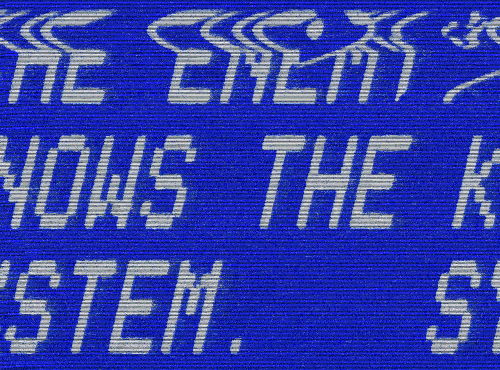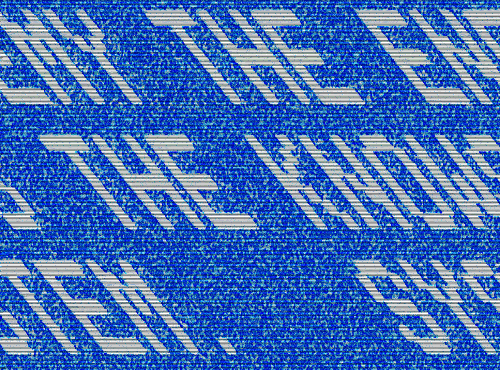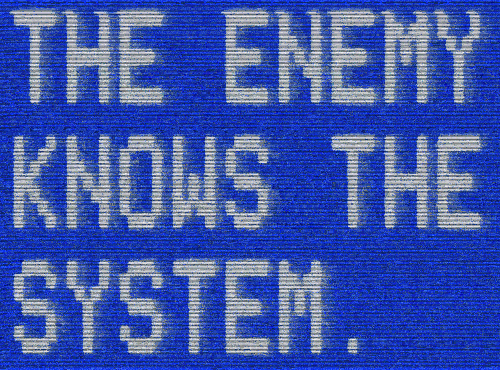
Cryptograms Week 3 (1)
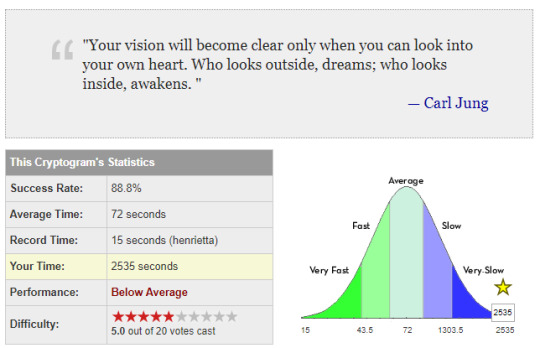
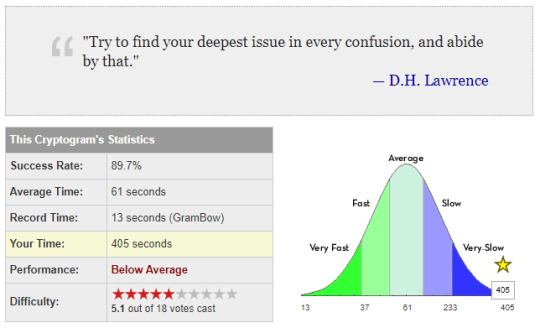
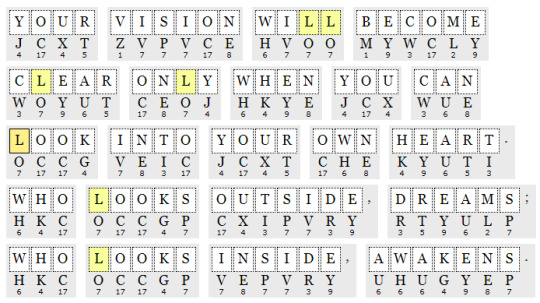
Straight up this one was so confusing I fell asleep whilst doing it. The critical word was LOOK and since there were so many instances of O, it’s frequency was insanely high compared to the rest. Once I woke up and figured out that word, the rest sort of just fell into place. I feel like it’s that with most puzzles, they’re dependent on a certain clue or step that will boost your progress.
1 note
·
View note
Text
Cryptograms Week 2 (7)

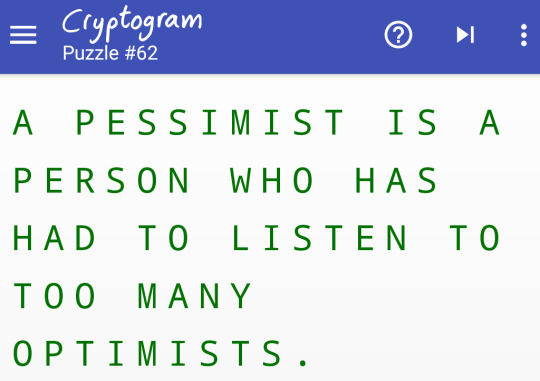
This one was quite challenging because of the unconventional appearance of “plodding”. It’s hard to anticipate when these rare words come up, but I think given the context it sort of helps? Anyway, I took 14 minutes on this so definitely terrible.

With a double letter at the end, and double again at position 3, the word is usually H A P P I N E S S.
Relatively easy - I think my solving is either fast or extremely slow depending on the difficulty and how obscure words are.



1 note
·
View note
Text
Coincidence Index
The basic idea is to mathematically determine the number of matching letters in a shifted text. This method can be used to help solve substitution ciphers more easily, by using the information of letter frequencies from the CI.

0 notes
Text
Something Awesome Proposal
Basic Proposal
Work through a hacking textbook, summarise the knowledge learnt in each chapter and apply it practically.

In-depth
Each week, go through a chapter in a hacking textbook
At the end of the week, summarise the different concepts and blog about my progress on my Something Awesome
At the same time, I intend to try and apply the concepts I learn in a practical manner by either hacking a set-up (safe or with permission) or developing an attack of some sort
The aim is to get a true sense of what hacking actually is, and the different ideas behind it
At the end of this project, I should be able to understand the core security concepts behind attacking and be able to apply this thinking in my day-to-day
Contingency
If I am unable to finish, or deliver a chapter by the end of the week, I will intend to wrap it onto the next week and cover both of them.
Assuming I start on Week 3 and work until the deadline of Something Awesome (Week 8?), I should have 6 chapters worth of content.
If the chapters are not too in-depth, I will extend it depending on the difficulty. For example, if chapter one is basic theoretical security, then I will cover both chapters 1 and 2 that week.
If this idea is too simple, I will focus my attention on more practical applications and look into how I can develop something testable at the end of the project
Extension
In the event that I am able to speed through the textbook (unlikely given I have University, work and society commitments) and successfully finish a decent amount of content, then I will direct my project towards polishing off a practical hack, test it out and report my findings.
Outcomes
A strong foundation and understanding on hacking
The capability to develop dangerous attacks and deploy it in security challenges, competitions and safe scenarios
An enhanced ability to “think like an attacker”
A public wealth of summarised information on hacking
A strong understanding of these concepts, enough to be able to teach them to others
Criteria
HD
DN
CR
PS
FL
Format stolen from: unit0-unsw and morethankradio
0 notes
Text
CIA
CIA is an acronym that describes different fundamental principles of security. Each have their own meaning and foundation in certain constructs and protocols used in security.
Confidentiality: prevents the disclosure of information to those who are unwanted/unauthorised
Integrity: ensures information will not be tampered with or modified unwillingly
Authorisation: verification of identity so that the person is who they say they are

0 notes
Text
Bell-LaPadula Security Model
Source: https://sites.google.com/site/cacsolin/bell-lapadula
The security model focuses on the C in CIA, that is Confidentiality. This is the idea that information is hidden from those you do not trust, and kept 'confidential'. It enforces this by restricting user access to only that on its own level or lower based on security clearance.

For example: A user with "Classified" access, cannot read files marked "Top Secret"! Furthermore, the model introduces the idea of both mandatory and discretionary access control (like Windows OS) where:
Mandatory: A trusted user (Admin or the System) creates and enforces the rules for access control
Discretionary: Owners of the file can manipulate the control permissions of that file at their own discretion
For Bell-Lapadula, the security model has no separation between protection and security. It's all baked in the 'secret' access within each level. The model is completely reliant on the access security, and nothing else. Therefore, if someone were to break in, there is no fail-safe or protection against it. Once they gain access to a level, there is nothing blocking them from accessing the levels below that one. Hence, if they were to take control of the whole system, they simply need to focus their attacks on the top level, which is able to access all the levels. Thereby, this system is flawed with a single point of failure at the top.
In fact, there previously was no protection against the information at each level. And there's nothing to stop someone from a higher level accessing the information at a lower level, copying that into a file and labelling that into a lower level. Thus the model had no protection against taking information from a higher level and assigning it to a lower level.
Thereby to combat this, they implemented a rule that higher levels could not write to lower level objects. This then tends information to drift upwards, so that only users of the same level or above would be able to access it. However, that further reinforces the fragility of the simple, which is most vulnerable at the top.
1 note
·
View note
Text
Coincidence Index Activity
The Coincidence Index helps you to solve substitution ciphers by taking the cipher text and shifting a copy beside it. By running through these two simultaneously, a coincidence index is calculated by taking the pairs of matching letters in both texts which is based on the alignment of your texts.
For each shift, a different coincidence index can be calculated, because there will be a different matching of pairs. However, there is a correct shift which reveals the KEY used to encode the plain-text into cipher-text. Once found, comparing this to the language yields a similar coincidence index, and therefore reveals what language it is in.
In the activity, we are given:
Cipher-text from Italian
Cipher-text encoded by the Enigma Machine
By following this method of determining the coincidence index, we are able to differentiate which is which. Since Italian has a CI of 1.94, we offset both texts until one with a similar value was found.
1 note
·
View note
Text
Week 2 NotMyTutorial

Joined the tutorial that runs on Thursday 5-7pm, run by the one and only Adam Smallhorn.
It’s a completely different experience to my tutorial which Trashpanda takes, in that Adam tries to create a familial community within the group. He encourages this by firstly:
Having a special name for the team (Adam’s Agile Angles)
Making everyone sit along the tables arranged in a U-shape
This way no one feels left out of the conversation while Adam does his thing at the front. Everyone is able to see each other and interact freely.
In comparison to my tute, it’s a lot more structured I like how Adam has a document with all the points he wants to cover in the tutorial.
Got exposed, my blog was featured and I had some empty posts I was planning on filling out in due time. Can’t help it - I put them there so I can remind myself to fill them in when I get the time.

3 notes
·
View notes
Text
Week 2 Tutorial
Crytogram Activity
Once again, we went over the Cryptobaron together.
Type 1 and Type 2 Errors
Very very briefly covered Type 1 and Type 2 errors. Trashpanda was simply like, just remember like Richard said in the lecture. There are always two types. We don't need to distinguish between them, thankfully (False postive/negative). However, we should note that there are two, and they usually are opposing forces. Reduce one, and the other increases! If you want to reduce both, it will be very costly.
Case Study (Houdini)
This was an interesting case study in that it was extremely open. There wasn't any clear defined scope, nor were the details covered very well. Trashpanda didn't really explain anything and just let us roam free. In that sense it's both good and bad. Good in that we weren't limited and only constrained to the bounds of our imagination, bad in that we spent a lot of time confused together (at least my party) and stuck on how to get started.
I think definitely he should have defined what a protocol meant, what some examples were and what they entailed. That would have saved a lot of time. Also having perhaps a clearer scope between the communication method through Houdini would be a lot better. Not having a clear outline on who's dead, who's alive, how communication works, really caused a lot of confusion and we spent some time trying to figure that out.
0 notes
Text
Claude Shannon
Claude Shannon is a cryptographer often referred to as the father of Information Theory. As an American mathematician and electrical engineer, his theories were crucial for the development of electrical communication networks that are used today. His notable contributions were the proposal of Boolean Algebra to describe and design relay switching circuits, using binary bits to deliver information and early work on artificial intelligence.
In the early years of computing, Shannon wrote a master’s thesis proposing the use of a form of mathematical logic, deemed Boolean Algebra to design digital relay circuits; the foundation of circuit and chip design today
During the Second World War, Shannon worked on secret communications, which helped develop the system through which Roosevelt and Churchill communicated. His work on this matter revolutionised the nature of the field of cryptography.
In his work, Shannon saw the foundation of all digital communication, the digital binary bit of 0s and 1s. It was from his knowledge and understanding, that laid the groundwork for Computer Science and Information theory.
Later, Shannon published his most important paper, ‘A mathematical theory of communication’ in which Shannon showed that information could be delivered through imperfect channels, i.e. through phones and wireless connections.
Going on from that, Shannon also went on to experiment with electronic mice which could solve a maze, and developing chess playing engines which led to the field of artificial intelligence; the field in making machines think.

1 note
·
View note
Text
Modern Technology and Security
Technology has become so embedded in our society and culture at this point, that things that were unheard of a couple of years ago have become commonplace. It's at a point where people don't even blink twice when they get asked for their location, or prompted to scan their cards or follow directions to a place.
We've just learnt to live this way, and we've become numb to bad security. I think that's why for the general population, they lose any sensitivity towards the matter until they've been brought to light about it. That's also why I think it took some time for me to notice and wake up to the obvious flaws in our systems. Since you become used to it, and start to unconsciously block out and ignore these bad practices. However, given these circumstances, if anyone were to corrupt any of these systems, people wouldn't even notice if nothing on the surface went wrong! It's just gotten so bad that everywhere you go, things are vulnerable or already compromised.
Our attention spans have dropped significantly over the last few years. Less people are able to sit and concentrate on tasks or stay alert to issues. We're constantly bombarded with news of this and that, so people have either started to tune out, or just hop from one topic to the next. Therefore, it only takes an attacker a few seconds away from the attention of others to cause harm.
1 note
·
View note
Text
Cryptograms Week 2 (6)

Finding Patterns to Improve My Solving Speeds
A three letter word with all HIGH FREQUENCY generally can be either:
T H E
A R E
L E T

A matching first letter and second-last letter usually, results in the word ‘N O T H I N G’

Struggled with this a bit. I think you can count on a pattern with endings. Things that are common are like:
ING
ABLE
ION
Also, a matching FIRST letter and THIRD LAST letter usually is the word ALWAYS.

If the FIRST letter and the LAST TWO letters are the same then the word is probably SUCCESS.
0 notes
Text
Cryptograms Week 2 (5)
Decided to try out Richard’s previous student’s cryptogram project. They made a website that runs on Amazon’s AWS. I believe it was for their Something Awesome project most likely?
http://nsa-crypto.s3-website-ap-southeast-2.amazonaws.com/
Anyway, the functionality is quite limited, and I don’t think it’ll be updated at any point. It’s missing a timer and other jumping capabilities, so I much prefer other resources like Cryptobaron :)
However, since this is a security course, what are the chances that this is a huge experiment to get us to use it, and compromise our security???
Could be a thing hmmm.. if my blog goes down next week you know why.

1 note
·
View note