Don't wanna be here? Send us removal request.
Text
Something Awesome - reflecting
And its done! It took me a lot longer than I expected to get the basic format working, but it finally does. You can now enter a message and an image file and get yourself an image with a hidden message wooo!
Here were some of the problems I faced over the last couple weeks:
My setPixel was not being saved. When I would inspect the steg image it had returned to its original format Fix: Didn’t realise the need for ImageIO.write
Unable to set/clear the correct bits. Originally, I tried to make a new integer for the RGB value, and after some fiddling realised it was easier and actually more efficient with the layout of each colour in a bit corresponding to 1 bit of the message, to make new individual RGB values and then create a new colour using those
Alpha bit would not clear. I had been setting the LSB of RGB and Alpha originally. This was a convenient format given a char is 8 bits it would always be a factor of 4 so I didn’t need to pad the string so that it would work nicely in the for-loop. Not sure why the transparency always returned to 1111 1111, if it was my error or something to do with the image type but I ended up just adding a padding function and splitting the string into 3-bit sets and not altering the transparency value
My bitwise functions were a little rusty – had to play around with setting/clearing bits a little bit
Initially I had no check in place for message length which caused all sorts of problems since the image I primarily tested on was only 8 pixels large and could only store a small message.
Mostly, it was a lot of playing around, testing how images worked and being able to visualise the data. I did some testing on changing different bits to see when a change in the image was noticeable, but it was really dependent on how many pixels the image contained and what the surrounding colours were.
I wanted to look into translating a small program into binary and storing it within the image, but I didn’t have time to implement it. I read some information on gcc compilers and how they convert c files, but was unsure how to apply this in a java program.
Here’s a look at the final code:



0 notes
Text
Case Study 6: Cyberwarfare
Cyberwarfare is suuuch a terrifying thought. It’s scary how rapidly warfare has advanced over the past century and crazy to think now people can attack us from the comfort of their bed, a million miles away, undetected. And these attacks don’t even necessarily have to come from a country. It could be a group of really smart, really bad people, who have the ability to target entire nations.
As we integrate computer systems into more and more aspects of our life, we become increasingly dependent on them. Our food supply, water supply, medical systems, transportation increasingly rely on systems which all contain vulnerabilities (we know this since all systems inherently have vulnerabilities). Cyberwarfare would involve disrupting these systems.
During our tutorial discussion today, I was most surprised by the idea of social engineering and propaganda as a part of cyberwarfare. I hadn’t really considered how these could be used to spread chaos. My mentality of “warfare” still involves guns and trenches and bombs. Using social engineering to rig an election and move the wrong kinds of people into power would have massive implications for a nation ( and it has ). But it still just doesn’t seem like “warfare” to me. I guess it’s an evolving definition. It was also very eye-opening to consider how the exploitation of “small” things, like blacking out traffic lights, could lead to more disorder than one might expect.
Here is a few interesting articles I read on cyberwarfare:
https://www.zdnet.com/article/cyberwar-a-guide-to-the-frightening-future-of-online-conflict/
https://www.technologyreview.com/s/612713/five-emerging-cyber-threats-2019/ - the section on the deepfakes is so creepy
https://www.forbes.com/sites/kateoflahertyuk/2018/05/03/cyber-warfare-the-threat-from-nation-states/#743107221c78
0 notes
Text
Another Interesting Event
Got this message from JB Hi-Fi today:

Scarily I was in JB Hi-Fi during June, but I’m not a big survey person, so I googled the scam and found a JB Hi-Fi article on them:
https://www.jbhifi.com.au/General/Corporate/Consumer-Matters/data-security-scams/
I’m guessing what fools people most is that it comes from “JBHiFi” - the built in name gives it a sense of legitimacy. As for whether they knew I was in JB Hi-Fi during this period or not – that’s a much scarier thought.
0 notes
Text
Week 6
++ the stack grows up ++
Don’t mix data and control – v v bad idea, then you have access to everything
AES – advanced encryption standard
The process of selecting a new algorithm was open to the public to allow full analysis and scrutiny. The algorithms were judged based on their ability to
resist attack (most importantly )
their cost – efficient both in terms of computation and memory
their implementation – flexibility, sustainability in hardware and software, simplicity
Rjindael Cipher was chosen
A block cipher used to protect classified information – encryption of electronic data
There are 3 block ciphers each of 128 bits, but with different key lengths – 128, 192, 256 bits
It is a symmetric-key algorithm i.e. the same key is used for encryption and decryption
All of the key lengths are sufficient to protect information up to the “Secret” level (see wk 2 Bell LaPadula) but “Top-Secret” level documents require 192 or 256 bit keys.
Data is storied in an array before being put through a series of rounds consisting of substitution, transposition, mixing of plain text and transformation into cipher text. The number of rounds differs depending the key size.
Substitution table -> shift data rows -> mix columns -> …. -> XOR operation on each column using a different part of the key …
Based on substitution-permutation network

Buffer Overflow Vulns
A buffer overflow is when more data is put into a fixed length buffer than the buffer can handle. The additional data overflows into adjacent memory, overwriting the data stored there. In a buffer overflow attack, the data is intentionally made to overflow into areas where important executable code is stored, where it can be overwritten with malicious code, or altered to change a program’s behaviour.
In C, there is no built-in protection against accessing data outside of certain boundaries, so it is essential to implement boundary checking when dealing with arrays.
Canary -> space deliberately left between buffers which look for actions written into them
DON’T USE gets()
Block Cipher – to secure a msg (encrypt / decrypt)
An algorithm which takes a fixed-length of bits called a block and applies a symmetric key and cryptographic algorithm (rather than applying it to one bit at a time – stream cipher). The previous block is added to the next block so that identical blocks are not encrypted the same. (I think this is not true of all block ciphers but good ones do this - ECB doesn’t that’s why it sucks) An initialisation vector also help prevent identical ciphertexts – they are a randomly generated set of bits, added to the first block and key.
Block Modes – for authentication
An algo that uses a block cipher to provide confidentiality / authenticity. It describes how to repeatedly apply a single-block op to securely transform data greater than the size of a block. They usually require an IV which must be non-repeating. Data greater than a single block is padded to make it a full block size – some modes don’t pad they act more like stream cipher.
ECB – Electronic Codebook: The simplest. Do not use for cryptographic protocol
Each message divided into blocks and encrypted separately -> this means identical plaintext becomes identical ciphertext leaving it vulnerable to pattern searching attacks. It is also susceptible to replay attacks as each block is decrypted the same way

CBC – Cipher Block Chaining
In cipher block chaining each message is XOR-d with the previous block (kind of like Merkle-Damgard ?) This makes it more secure than ECP mode as you cannot decrypt individual blocks – they are all dependent on the previous block. The initialisation vector is unique for every message, it does not have to be secret but keeping it secret probably adds a bit of extra security

CTR (Counter Mode)
CTR mode changes a block cipher into a stream cipher (i.e every bit is encrypted rather than every block). Kestream blocks are generated by encrypting a nonce with a counter ( I think - come back to this )

Moore’s law
Processor speeds will double every 2 years – i.e. the number of transistors on an affordable CPU double. This was a prediction made in 1965 and despite many others predicting this rate would slow, so far it has been pretty accurate
Cold Boot Attacks
A side channel attack used to gain access to the encryption keys of an OS. The attacker needs physical access to the computer to perform a cold reboot to restart the machine. After a computer is switched off there is a small window where the RAM holds onto data. In a cold boot attack, the contents of the RAM can be copied to an external drive in this time.
Attackers can also lower the temperature, giving them more time before the RAM fades due to lack of electricity. The computer must be forcibly turned off so that the processor does not dismount important data. Most modern systems wipe memory early in a boot process to help prevent these attacks. Of course this attack can be stopped entirely by remaining with your computer for a few minutes after it’s switched off, ensuring no one has access to your machine.
0 notes
Text
An interesting event
In the first tutorial of this course, Kris mentioned we might come out of it loving security engineering or we might come out of it cynical of everything. Never before this course had I had any issues with my own security and I continued on lightly with my repeated passwords, uncovered camera on my laptop, unconsciously sharing all of my data with the world.
Every day I did get a little bit more overwhelmed with just how many ways someone can virtually screw you over. And then one day I woke up to an email from an angry German guy about why I hadn’t sent him his lawnmower. And this was the first day I got hacked.

I had gotten a couple of emails in German from eBay, but being pretty vague I honestly just ignored them and didn’t think anything of it. So when I received a message from this German guy, I was quite surprised he seemed to genuinely believe I owed him a lawnmower.
So I called eBay, told them I was not in fact selling a lawnmower and was just wondering how this could have happened. Worryingly, they didn’t seem very worried. Sent me an email to reset my password, told me not to contact the buyer and that was pretty much it.

Should I be worried? Thanks to this course, I already was 😊
0 notes
Text
Case Study 5: Self-Driving Cars
During the tutorial this week we were split into groups and not allowed to share our case study with the other groups. As it turned out we all had the same topic – should we be looking towards self-driving cars, but we were given the topic from different viewpoints. Our group was playing a government representative.
Our tasks were:
Consider the assets of the country which would be affected:
the citizens of the country
infrastructure (roads in particular)
industry (taxis, uber, petrol companies, etc)
government reputation
What risks need to be acknowledged?
the safety of people both inside and outside the cars
the cars themselves
a shift in the economy
other normal drivers on the roads
malfunctions, hardware and software attacks
Who should acknowledge these risks?
As a government representative, we put forward that an independent advisory should be put together to test the cars and return an evaluation. The test group should include engineers, economists, security engineers
Would you advise in favour of self-driving cars?
The overwhelming response from all industries was yes. Our group did consider though that measures would need to be put in place to help the transition for industries most affected eg/ taxis, normal car making companies, insurance companies, public transport etc
Personally, I’m all for self-driving cars. It seems like the next logical step in our world of rapid technological advancement. I think the hesitation from most people comes from a fear of change. But I also think that the general population’s lack of understanding of how computer systems work plays a roll. When I help my parents sort out a problem with their computer, they can never comprehend that the computer isn’t working because they aren’t telling it the right thing. They think oh the computers wrong, its broken. But its not. As we know, computers have a massively lower error rate than humans do – they just do what they’re told. That’s what makes them do many things better than humans. Most people just can’t see how a machine could be a better driver than them – but we’re constantly distracted, even if we’re staring straight ahead there’s always other things on our mind. But for a computer it’s just completing a task. And if it’s told how to do that task effectively, it will do it better than a human. As they are phased in, people will trust autonomous cars more and more and like all the other technologies we’ve introduced, they won’t remember how they did life without them.
0 notes
Text
Passwords
This week’s advanced lecture was very enlightening. Passwords are such an essential part of our life but people seem to be soooo lazy and casual about them, myself included. To be honest I’ve re-used one of my passwords about 400 times for all the crap I sign up for. After watching this lecture I went and got myself a password manager and reset like 1000 passwords.

Here was my takeaway on passwords:
They suck -> we’re looking to a future without them
Don’t reuse them -> somewhere, someone’s got access to a password you used once. As soon as you reuse it, you’re vulnerable all over again
Get yourself a password manager (done 😊 )
When constructing a password it should:
Be long
Use a combination of symbols
Avoid patterns ( pretty much impossible for humans but try )
Avoid including personal data
Try not use English words -> full of patterns
NIST policies:
Lots of limitations on passwords narrows the scope and makes it easier to crack.
Allow long passwords
Don’t provide security questions (cough cough myGov- its not like the info myGov has on people could be important )
Don’t provide hints
Allow pre-fill password fields
0 notes
Text
Something Awesome - an update
After trying to make this work in Bash, I’ve resigned myself to the fact that it’s just not going to happen. Switching to Java to see how it goes. I’m not super confident with my Java skills but there are a lot of online resources particularly relating to image processing which should come in handy.
I’m starting small, hiding a message in a file – hopefully it won’t take me too long and I can hide better things than strings!
0 notes
Text
Week 5
Don’t roll your own: you think you can make a better crypto function, but you can’t.
WEP – Wired Equivalent Privacy
A standard network protocol intended to add security to Wi-Fi to give it the same level of privacy as a wired network. WEP uses a data encryption based on user and system generated key values. Originally it supported 64 bit encryption keys – 24 bits being an initialisation vector – which was eventually extended to 128, 152 and 256 bit variations to increase protection. WEP encrypts data when it’s sent via WiFi, using the keys to make it no longer readable to humans but so it can be processed by the receiving device.
A stream of bits is XOR-d with a “random” stream of bits generated by an algorithm. The only way we can get the original stream is to re-XOR the encrypted product with the same stream of bits.
WEP is super flawed. Everything you read about it pretty much says never use it.
Firstly the initialisation vector was susceptible to a related key attack since at only 24 bits it was not long enough to ensure it was not repeatedly used
The packet transmitted contained both the data and the control data – data and control should never mix
In 2005 a WEP protected network was cracked in 3 minutes by manipulating the RC4 keystream used for confidentiality
In 2007 this attack was extended where upon capturing 40,000 packets it was possible to recover a 104-bit key with a 50% probability. This increased to 95% with 85,00 data packets. 40,000 packets could be captured in less than 1 minute thanks to deauth (not sure what this is though)
The Payment Card Industry banned the use of WEP as part of any credit-card processing.
Hash History
++ compression functions can’t handle arbitrary sized inputs, they require padding ++
MD5 – Message Digest Algorithm - produces a 128 bit hash value. Fails sooo bad with collisions – can be found in seconds on a basic computer. Cryptographically broken but can still be useful to verify data integrity
SHA-1 – Secure Hash Algorithm - 160 bit hash value ( message digest ) represented as a 40 digit hex number. Now outdated – Google performed collision attack. Here’s an interesting article on how it actually works https://brilliant.org/wiki/secure-hashing-algorithms/
SHA-2 – the current standard. There are 6 hash function with values of 224, 256, 384 or 512 bits. They are computed with 32 and 64 bit words
SHA-3 – for the future. Not vulnerable to length-extension attacks
Merkle Damgard Construction – collision resistance
A method of building collision-resistant functions – used in MD5, SHA-1, SHA-2.
Messages are padded to make them an appropriate length (512, 1024) -> m || p
The result is broken into blocks which are each hashed individually. (This is a compression function hash which can only handle inputs of fixed size)
Each block is combined with the previous before it is hashed again

Length Extension Attack
Using Hash( m1 ) and length( m1 ), attacker can determine Hash( m1 || m2 ) where m2 is controlled by the attacker. The content of m1 doesn’t need to be known, only the length. Algorithms based on Merkle-Damgard are susceptible -> sending H( secret || message ) to someone, gives them both the hash and the message length -> they can take the hash, pass it into f again with a new message, extending the original. This is why we use HMAC
Here’s a good explanation:
https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks - reminds me a lot of my steg project
Digital Signatures – authenticity, integrity
Used to verify the authenticity of digital messages or documents and gives integrity to the communication. It is a value calculated with the data and a key known only by the signer. In RSA we have a public and private key -> private used as the signature key and public as the verification key. DON’T SIGN TIL THE END
Key Stretching
Techniques used to make a key more secure against a brute-force attack by increasing the time and/or space it takes to test each possible key. Basically making a password longer and more random -> more entropy = harder to crack.
Salting
Adding random data to (usually) a password as an extra layer of security. Salting a password makes it more likely to be unique as well as making it longer thus making it more difficult to crack. They protect commonly used passwords and users with repeated passwords as adding a different salt to the same password produces a different hash. The salt must be different for each password regardless of what characters make up the password. It must also be of suitable length, otherwise it remains susceptible to a rainbow table attack.
0 notes
Text
Social Engineering
This weeks advanced lecture was on social engineering. At first I thought the scenario they gave was maybe a bit far-fetched, but then when I considered it more closely, I thought that because I knew the actions they were taking were part of an attack. If someone asked me for a line extension, my first thought wouldn’t be that they are planning on doing something bad. Again, if I found someone in the wrong place I’d probably just give them the benefit of the doubt if they told me they didn’t know they weren’t supposed to be there. Little things go unnoticed and it’s when all these small vulnerabilities come together that we are exploited. I guess we need to have our security mindset on 24/7.
95% of all attacks involve security engineering - this was my biggest takeaway
I remember Andrew’s anecdote on the guy asked to pentest the fabulous security of a company. I was surprised how much of it relied on human interaction rather than an advanced piece of software. In a world where so many people use computers that they are completely uneducated about, it’s easy to take advantage of people’s ignorance. I guess that’s why so many people are scammed easily online. A combination of trust and ignorance.
0 notes
Text
Random Number Generation
Generating truly random information is crucial in cryptography, particularly in initialisation vectors. But how random is it? There are two categories of random numbers - true random numbers and pseudorandom numbers.
In true random number generation, a physical phenomenon is measured to generate entropy. There are a multitude of events which can be measured, some producing “truer” randomness than others. For example, measuring the radioactive decay of an atom is less predictable than generating numbers based off key-events of a computer user, given some letters are much more commonly used than others. This data is converted to an electrical signal which is then converted into a digital number.
Pseudorandom numbers basically pretend to be random. A seed value, or a starting point in a sequence, is used alongside an algorithm which produces a set of numbers with a very large period. The scale of the period is such that the numbers appear random, but in fact, using the same seed value would generate the same sequence of “random” numbers. Not so random after all.
0 notes
Text
FOI Requests
Part of this evening’s lecture was from Matt O’Sullivan on how to lodge an FOI request. I still struggle to comprehend the scope of what can be asked and with no pressing matters on my mind I probably won’t lodge one but here are some of the tips he gave:
don’t be too broad – asking something vague, something that expands too great a period of time or crosses too many areas is likely to be rejected. You don’t need to be specific to the point of asking a single question, but know the kind of information you’re looking too gain from the request
know the type of documents you want – it can be hard to sift through hundreds of pages of information you may receive relating to your request – ask for briefing documents if you need an overview of information
sometimes persistence is required if you really want to get your answer. Being polite doesn’t go too far astray either
An interesting article I read after learning about FOIs was a case in Britain where WhatsApp messages from a government group were released after the group’s existence was revealed. The names of those in the group were not released but their correspondence was. I found this interesting for a few reasons:
This FOI request was not processed by members of the group so how did they gain access to the chat? Surely WhatsApp would not release encrypted messages? Does the government retain information of these chats? Are they obligated to reveal the chat upon request?
None of the messages are particularly interesting, but I wonder if the people involved knew there was a possibility their communication could legally be released to the public? I know email communications within companies are recorded and monitored but something about a WhatsApp chat just seems so much creepier and the fact that the whole world could read them is a bit scary
Here’s the link to the story and a few others on interesting information obtained via FOI requests.
https://www.rte.ie/news/2017/0115/845061-government-whatsapp/
https://www.gizmodo.co.uk/2017/02/heres-what-tfl-learned-from-tracking-your-phone-on-the-tube/
https://time.com/3131512/weird-foia-uk/ - this one is funny, I wonder what the actual responses were
https://www.bbc.com/news/magazine-30645383
Melissa Segura, BuzzFeed News: “I’m happy to report that my FOIA experiences have been marked almost exclusively by monotony, bureaucracy and tedium–you know, like they’re set up to be.”
Thought this was funny, exactly how I expect anything I request to be received haha, a painfully beaurocratic process
0 notes
Text
Something Awesome - some research
Idea: Write a program that can hide a given message in a given image.
Some research:
Steganography is when data is hidden inside an image, document, audio file, video, etc. At first glance the file appears to be a normal file but with some techniques the data can be extracted. Steganography is not an encryption technique, but data is more secure when the two are combined. It has some advantages over pure encryption in that steganography files do not raise suspicion to outsiders. A plain encrypted message will always arouse some interest as there is clearly something being hidden, but in steganography it is not obvious that information is being concealed. The goal of steganography is to hide the data being sent and to hide the fact that there is data being sent.
Steganography is not only used to protect data, it can also be used in a malicious way. Steganographic attacks are common in scams and virus distribution.
Some different techniques I could use:
Lowest Bit -> data is hidden in the least significant bits of sound or image files
Encrypting a message and hiding it within a random encrypted text. The message overwrites a small part of the random encrypted block
Chaffing and Winnowing -> ?
Mimic functions -> changes file A so that it has the statistical properties of file B
Pictures embedded in video
Pictures embedded in audio files
Echo steganography -> modifying the echo of a sound file
IDN attack -> using homographs
White text in emails, word documents, etc
Least Significant Bit - start with this
An image contains pixels - each pixel is 4 bytes: 1 Red value, 1 Green value, 1 Blue value and a transparency value

Changing the lowest bit doesn’t really affect the image so we can use this to store the bit of our choice - like a but of a message
International Domain Name Homograph Attack (script spoofing)
Exploiting homographic characters i.e. characters that appear the same but are actually different. Different alphabets have letters which appear the same - Latin, Cyrillic, Greek, etc Can exploit this to misdirect eg/ google.com where the o is not a Latin o, but a Cyrillic o, redirecting to an unexpected sight.
Not sure if this is too specific to steganography, but its really interesting so maybe I can work it into this project somehow.. we’ll see
0 notes
Text
Week 4
++ if something is “broken” a property can be violated faster than brute force ++
Bits of Security and brute force
Bits of work represents how much security a particular system has / how much protection it has against a brute force attack / how hard it is to brute force. An attacker would have to perform operations to break it
1 bit = 2 options
2^10 ~ 1,000 2^20 ~ 1 million 2^30 ~ 1 billion
Eg/ if we have a 10 digit password – a-z, A-Z, 0-9 only then
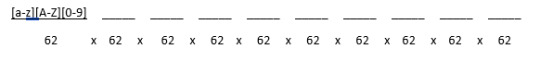
62 options for each digit = 62^10 options
2^6 ~ 64, so we have (2^6)^10 = 2^60 -> 60 bits of work to brute force this password
But the average time it would take to brute force, is half the total time i.e. so 59 bits of work
Brute forcing is really slow, definitely not an efficient way to crack something. With 256 bits of work is probably enough to not be cracked. We can be smarter about how we decrypt things, especially when we know they’re in English. See index of coincidence post for more on English letter frequency distribution.
Since most English-speaking people use English words in their passwords, and communicate in English, we can greatly reduce the amount of work it takes to crack an encrypted message/password thanks to the lack of entropy within the English language.
There are 2^25 possible combinations of English letters in a 5 letter word
There are only 2^13 valid words
Each letter added to a password adds ~ 2.5 bits of work
Patterns and entropy + English language + Claude Shannon
Redundancy in English language -> rules like i before e except after c, q must be followed by u
Grammar, parts of speech, we can’t just make up words and make sense. All these things contribute to English language being redundant. Thanks to redundancy, we can better understand English when everything is not clear. For example
msot poelpe can raed a sneatnce if the frsit and lsat lterets are the smae,
despite other letters being jumbled. Similarly when there is a lot of background noise we can often still discern what is being said, despite not hearing the annunciation of every letter.
An N-gram is used to calculate the entropy of English. We can statistically calculate the randomness of the next letter when we know the previous N-1 letters. As N increases, the entropy approaches H (i.e. we get closer to knowing the true entropy value of English ? )
Calculating the statistics of Fn has a difficulty of O(26^N)
F0 = 4.7 -> this is the maximum entropy value for English letters, where each letter has equal probability.
Fword = 2.62 -> the average word contains 4.5 letters
Since we can read sentences without spaces almost always, spaces become redundant. We exclude this to get a more accurate representation of entropy.
Maximum redundancy is when all letters have the same likelihood
Man in the Middle Attack
2 people think they are communicating privately with each other, when in fact there is an attacker in the middle relaying ( and maybe altering ) messages between the two. The attacker is able to intercept all messages between the two people as well as interject new ones. Attackers may also target information inside devices
These attacks can be done when the two are communicating via unencrypted Wi-Fi and the attacker is within range of the same access point. This is known as Wi-Fi Eavesdropping. The attacker may set up a Wi-Fi connection that appears legitimate (evil twin?) and wait for someone to connect, instantly gaining access to their device. They may also create a fake node to steal the data of anyone who connects
Session hijacking is another form of a MITM attack. Attackers will access the session created between your device and a website when you enter where they can steal your cookies – containing information such as passwords, pre-fill forms (i.e. bank details, addresses, phone numbers, company details – basically all your personal info) and access other accounts with these details.
Email interception -> monitoring communication between parties, gathering important data including transaction details, bank account information, personal details before impersonating an organisation and targeting individuals for example changing the receiving bank details to their own.
Man in the middle attacks highlight the importance of the Integrity and Authentication principles. It is essential that information is tamper-evident so that the receiving party can verify the authenticity of a message / communications.
Replay Attack
Kind of like a MITM attack, an attacker may intercept communications and then delays or resends it fraudulently deceiving the receiver.
Hash Functions
A regular hash function is any function used to convert data of any size down to data of fixed size. The same text will always result in the same hash – i.e. they are deterministic. A hash is quick to compute and very hard to reverse.
A cryptographic hash function is used to secure messages in transmission. It is unlikely that any two messages will have the same hash. In order for a cryptographic hash function to be secure it must fulfil 6 properties:
1. deterministic
2. quick computation
3. pre-image resistant -> infeasible to determine the message before hashing
4. avalanche effect -> small changes to message = big changes to hash
5. collision resistant -> unique inputs should produce unique hashes
6. puzzle friendly -> H(k|x) = Y – it must be infeasible to find x such that concatenating a random point with x produces the hash equal to Y
Collisions
A hash collision is when two distinct sets of data generate the same hash value. They are unavoidable when a very large set of data is mapped to a short string. This is unfortunate as collisions can be exploited by programs that compare hash values, for example password authentication.
Collision Resistance -> Find any 2 messages, m1 and m2 such that H(m1) = H(m2)
Second Pre-Image Attack -> given, H(m1) and m1, find m2 such that H(m1) = H(m2) (m1 != m2)
Pre-Image Attack -> given only H(m1) find m2 such that H(m1) = H(m2)
Message Authentication Codes (MACs)
A MAC is a way of authenticating and providing integrity to a message via a crypto hash – i.e. if you want to ensure the recipient knows that it has come from you, unaltered. It consists of 3 efficient algorithms
- G: key generation algorithm – a key is selected from the key space at random
Both the sender and receiver must share this symmetric key, K
- S: a signing algorithm – returns a tag given the key and the message
- V: verifying algorithm – returns accepted after verifying the authenticity of the message
For an MAC to be secure it should be computationally infeasible to compute a tag of the message without knowledge of the key

Take a message – combine with key – hash the result – send message w MAC – reperform MAC to verify w shared secret.
These are all bad:
MAC = hash ( key | message ) - vulnerable to a length extension attack
MAC = hash ( message | key ) – can still forge messages with collision
MAC = hash ( key | message | key )
We want HMAC:
HMAC = hash ( key | hash ( key | msg ) )
MACs do not provide non-repudiation – i.e. if there is a dispute over the origins of a message it cannot prove the message was sent by the sender.
0 notes
Text
More on Self-Interest and Separation of Powers
It’s a cynical view, but as discussed in last week’s WOtW self-interest is really the core of all humans. At the end of the day it’s a self-preservation instinct to put yourself first. This doesn’t mean we can’t recognise the importance of empathy and caring for others, just that when it comes down to it, we’re going to do what benefits us.
Politics, being a human construct, is limited by our human flaws. Civilisations built on dictatorships -whether it’s a monarchy or a tyrant, have not been as successful (for the masses) as most democracies. This is largely due to the separation of powers and distribution of roles within government that exist within most democracies. Time and time again, we can see societies crumble as a ruler with too much power over too many sectors tightens controls and limits the population, whilst simultaneously building their own wealth / gains.
Greek born Polybius saw the importance of change, believing all things in existence were subject to decay. He believed in having a Cycle of Governments. Examining our own political system, we can clearly see the importance of this. Once altruistic politicians, set on bettering our nation and improving the lives of all, seem to become steadily more focused on their own position in government rather than their job as a representative of the people. I think all of the coups and leadership changes are a strong reflection of the self-interest of many politicians superseding their once noble intentions of bettering society.
A separation of key industries ensures balance - no one sector can become so powerful that they can control everything. It places limitations on the effects of self-interested people of power.
0 notes
Text
Case Study 3: Airplane Doors
This week our case study was on doors in airplanes, specifically the one separating the cockpit. The pre-readings were interesting, especially the GermanWings article as I remember that happening and being surprised there weren’t measures in place to allow ground control to take hold of a plane in the case it was hijacked.
Our task this week was to improve the safety of airplane doors.
Our group first divided possible scenarios that were a safety risk to a flight.
1. Both pilots are locked out of the cockpit
1a. There is no attacker ( but no one flying the plane )
2. Both pilots are locked inside the cockpit
2a. One of these pilots has gone rogue
2b. Both of these pilots have gone rogue
2c. There is a danger outside the cockpit
3. One pilot is locked out of the cockpit
3a. The pilot locked inside has gone rogue
3b. The pilot locked outside has gone rogue
When considering how to make the door as safe as possible we tried to consider all possibilities, but when it clashed we also placed a risk likelihood on the scenarios.
Considering most airline safety standards require at least one pilot inside the cockpit at all times, the likelihood of scenario 1 is low, if we assume human obedience to the rules (which we really shouldn’t).
In scenario 2, as read in the Germanwings case, 2a. is a higher possibility scenario. 2b. is less likely, however we will add guidelines to further decrease its likelihood shortly. 2c. is another more likely scenario and probably the most considered, given the general public’s fear of terrorism.
In scenario 3, 3a. is again a high likelihood and 3b. is slightly less.
We came up with a few suggestions:
There should be 2 people in the cockpit at all times – when 1 pilot leaves, they should be replaced by the head stewardess until the pilot returns. A small annoying alarm will activate if this requirement is not met. This is to encourage staff to comply with the rule. Should this fail, disciplinary can be taken thanks to a recording of an alarm being activated.
All members of crew should be subject to annual psychological testing
A key should be established to open the door from the cockpit. It involves multiple members of the crew (lets say 5?) to have their own personal key. When all 5 keys are used together, the door of the cockpit will open. When staff enter the plane, they sign in with a fingerprint which will allow the master key to be set as a combination of those key. The individual keys will be a sequence of numbers that the crew can pick when they begin working for the airline. This key is essential in mitigating risks in sections 2 and 3. Firstly if one pilot has gone rogue inside the cockpit, the staff can override his locking of the door and enter. This also works if both pilots have gone rogue or if the other pilot is trapped inside / injured. Secondly, if there is a danger outside of the cockpit, an attacker would require knowledge of which 5 members make up the key. Of course this is still a possible threat, since they may threaten violence, but we considered if an attacker is likely to kill members of staff who is unwilling to enter their key, they are probably trying to kill everyone. So, a staff member kind of loses either way, but they can save everyone else if they just don’t use their key :/
An emergency contact point should be available outside of the cockpit to contact air traffic control. By implementing this alongside the key idea, if all members of staff validated their key to confirm an on-board emergency, the plane could be controlled from the ground.
0 notes