Text
Can we really trust the people who collect our data, even there is a legit policy?

While I was scrolling through my Facebook feed, there was a post about the penalty of $5 billion fine that Facebook has to pay. I was so shocked about the amount of money because the website reports that this is the highest amount of fine with a private company in history.
After I read through the report and thought about it for a couple of minutes. This made me feel kind of worry about our privacy and security of our personal data, even there is a law or legal commitment that person who collects this data would not use it in a risky way. So I would elaborate my thought and mention about my opinion on this issue.
In 2017, there were several rumors saying that Donald Trump had used the data of 50 millions accounts of the Facebook user in his election campaign. The biggest question was ‘How could he has access to all those enormous amounts of data?’. Several months later, the truth was revealed about how could all of those data had been used without asking for permission of the owners.
Briefly speaking, there was an academic professor creating a mobile application named ‘thisisyourdigitallife’. This application became very popular among people in the USA and requires a Facebook account to sign-in into the application.

This means that this professor can have access to all the information of the user using his application through the Facebook account. Additionally, Facebook API regulation about the permission to access user information at that time allow an application developer to access all information of account in that user’s friend-list as well. Imagine you are using this application and have 500 friends on friend-list, all of their data can be accessed.

The problem of this issue has started from here, he sold all of the data to a British data-driven company, Cambridge Analytica (CA). Facebook instantly contacted this company after they knew what happen and told CA to delete all of them. Although there was a legal contract about this action, CA still did not delete it. Finally, Donal Trump hired CA to analyze data and perform microtargeting for Trump’s election campaign. After 2 years of investigating this case, these consequences ended with $5 billion fine on the Facebook side.

My opinion
The point I would like to make here is about the security of what happens here.
Firstly, even there is a regulation that the professor could not use this data for personal profit, he still broke the rules.
Secondly, even Facebook told Cambridge Analytica to delete all the data, they decided not to do it.
These 2 situations above were done legally, but the problem still happened. So how could we trust any services that have access to our personal information? maybe not at all. As Richard said, security can’t rely on trust. Even there is an obvious law or legal contract, people still be able to break it anyway.
4 notes
·
View notes
Text
[W5] Activity: Vulnerabilities
Recipe
Recipe 1 - Simple Vanilla Cake
No measurement of any ingredient at all
170 degrees Fahrenheit is 82.22 degrees Celcius, can this temperature really bake a cake? it is not even able to boil water.
Recipe 2 - Caramel Slice
2 x 395 sweetened condensed milk? Hey grandma, what unit is this?
where is caramel in this recipe? You have no caramel in caramel slice???
Recipe 3 - Cheese Souffle
the ratio of each ingredient is not so reasonable.
It is mentioned that cooking time takes half an hour. However, a whole process would take around 10-15 mins in the recipe
I C Your Probleme There
Code 1

the first conditional statement (length > max) is not cover all the cases because the length can be a negative value.
Code 2

In the fourth conditional statement, sizeof(buffer) will fail to find the size of the allocated memory. It will return a size of 4 (32-bit system) or 8 (64-bit system).
Code 3

It is not a good idea to compare the size of different variable types, which are short and long in this code
3 notes
·
View notes
Text
[w4] Activity: Bits of Penguin

I have illustrated a problem into a picture above. It indicates the possible colors of the ring for a single penguin. The white circle indicates having no ring.
So there are 2 and 3 possibilities from left and right wings, 6 and 7 on the left and the right foot. So the combination of all possibilities is 2 x 3 x 6 x 7 = 252.
However, the real value in this question is 251 because there is a condition saying that every penguin needs to have a ring. In order to convert to bits of security, 256 is the closest number in the root of 2 which is 2 to the power of 8. Hence this penguin case has 8 bits of security.
2 notes
·
View notes
Text
[w8] tutorial: Ghost
For the tutorial class this time, I did not really understand what the question exactly is. I thought it is the same as Houdini case but Hayden mentioned at the end of the class that they are completely different and If any student thinks they are similar, so it means they do not understand the point of this case study.
So there are invisible man, major, and alien. Additionally, the condition of the protocol is like the figure below

Basically, X - I - A are major - invisible man - alien respectively. So there is only an invisible man that could not send a message to major. Apart from that, the rest can send a message and everyone and receive the sent message.
So we were separated into a new group. Everyone in my group was kind of blank, maybe because we were all not 100% sure about the concept of the case study really is, however, this is what we came up with.
Firstly, we would like to know that Alien is reliable and trustworthy or not and we realized that the communication in the sender side can be performed in a clockwise direction starting from Major through the invisible man. So that means if we assume that invisible man always on the major side and not going to lie to us, we can check that Alien says the truth or not.

The picture above explains how our protocol works. Firstly, major have to specify a way to send a signal that can indicate that the alien is lying or saying the truth. It can be anything, for example, if it is trustworthy, send a message at midnight; else, send it in the morning.
After major has finished setting up a signal, he will tell the invisible man to pass some message. it can be anything because there is only himself who know what it is. This message will be passed clockwise through the alien, the major, and back to the invisible man, which can know at this point about the alien behavior. According to the picture, message A is sent from i to A, then A^ is sent to X from alien. Once A^ has been passed to i, i can check if A^ and A are the same or not, which will let i know if alien is lying.
The signal specified by major at the beginning is used here. The invisible man will perform that signal to let major know the truth about alien and major can decide what is the next thing to do from this signal. Additionally, we realized about another assumption that we have to make, in order to make this protocol works. We have to assume that Alien will instantly pass the message once he has received and there is no delaying message at all.
If the alien is not on our side, kill him!!!!!
0 notes
Text
[w8] Lecture reflection
Imbalance of power
- In 991 scenario,
Digital Forenciss
- 3 stages of investigation [Acquising/Imaging, Analysing, Reporting]
Type of Forenciss
- Computer forencis
memory, data
mobile device
phone
Network
Router, switches, packet captures
Database forensics
Video/Audio
movie files, audio recorded
Tooling
Encase
Autopsy/The sleuth Kit
KTL imager
File
Strings
Xxd
Foremost, Binwalk, mmls
Drives and Partitioning (FAT32)
Allocates memory in clusters
The FAT records stores the status of each cluster (bad region, allocated, unallocated)
2FAT records for backup
Kahoot!!

Richard Section
3 Mile Island
Nuclear reactor: It basically has a mechanism to put the rod into the water to prevent reaction that can cause problems (failure of the systems).
0 notes
Text
Captain America Civil War: inspired from Team America: World Police
Richard mentioned about Team America World Police in the class. It is about police fighting with a terrorist. Even they have defeated all the terrorist they have also almost destroyed a whole city as well.

This really reminds me about one of my favorite movies, 3 years ago, “Captain America: Civil War”. The story of this is set up after an avenger team has been fighting bad guys for so long which results in causing countless damage to innocent people, for example, Sokovia falls (Avengers: Age of Ultron). Even avengers succeed to save the world from Ultron attack, the whole city till falling into pieces and pointing to the city below, which causes thousands of loss.

There are so many scenarios in the movie that illustrate how the consequence of protecting or saving something could cause a loss and sometimes it is not worth at all. So to highlight Richard’s word again, as we are a security engineer, we have to consider the trade-off of everything.
0 notes
Text
Risk of One-time password in transaction verification
I saw a new talking about Germany has decided to stop using OTP message authentication system. This made me start to search up about it in more detail. The reason why I did this is that it makes my international transaction (my Thai bank account) become very complicated. I have never seen any benefit of it since I reached the age of 15 and be able to open my own bank account in Thailand when I was in high school. Here are the things I found, and also my opinion about why this system should not be used anymore.

OTP (One-time password) is basically a system to authenticate a person, usually used in the transaction or financial areas. It was developed since the 1980s (Seriously? How could you still use authentication approach from the last 30 years in this age!?).
To make it more clear, for example, once I do some online transaction by using my debit card. A message will be sent to my phone number, usually a sequence of 4-6 numbers. This password has to be used to authenticate the real bank account owner.
Apart from the security side which will be mention in the next section, the convenient side is not so effective. To clarify, suppose I would like to pay my tuition fees with my Thai bank account but I have no SIM card for my Thail phone number to receive OTP message, therefore I could not do it at all. That’s why I do personally hate it. It is not possible to reinsert sim card every single time I need to do the transaction. Other than that, many electronic-mail service providers still use it as well. Imagine how hard it is in signing in on a new laptop like a university machine and it requires authentication code from my Thai-phone number. Life is way more difficult because of this.

Moving on to the security side, this approach is very easy to be attacked. Since technological development these days, the attacker can easily intercept the authentication codes via a mobile network, or even they failed to get the first one, there is an option to re-send a new OTP password again on most of the online transaction services.
Additionally, from the change in human behavior this day, people tend to change their SIM card more often compared to the past, for instance buying a new smartphone that requires a customer to register a new phone number and have a fixed contract in using a specific package from the service provider. What if a user has forgotten to update the personal information with their bank. Even the user already cancel the phone number, this number still has a chance to be re-use in the system as well. Accordingly, their OTP message can be randomly sent to someone they do not know.
In nutshell, I do agree that this system should be taken out of the world already. This method has been disrupted from the development of high-speed internet long ago, as same as no one pays for a very expensive price for making a phone call across the country since the internet call has released. Hope my home country could cancel it soon so that I can make my transaction easier.
reference: German banks are moving away from SMS one-time passcodes
1 note
·
View note
Text
3rd party company stalking user’s conversations
I saw a report about this issue a few weeks ago and decided to find some more research about this. Firstly, we all have to admit that we are in the period in which data-flow rates are significantly high compared to the past. It changes the way we live and also influences our behavior as well. Additionally, smart devices have become more popular in the past few years. It makes our daily-life way easier than it was. However, there is a trade-off in losing privacy.

The news reported that Google admitted that they use a smart home speaker to collect user conversation. They claimed that all the smart speakers have to listen to the keyword of the user to trigger smart assistant function to perform an action such as “Okay Google”. But what if they collected more than that? It is still possible, right?
After I spent some hour searching up about other cases this issue, I found some interesting experiment. They tried texting with specific keys, for example, asking a friend to order some food with a very obvious keyword such as “KFC” or “fried chicken wings”. It turned out not enough evidence that can indicate Facebook is listening to the user. However, there is still a case that you can feel like being stalked when advertising provided by Facebook is directly related to the word you just have said or an action you just have done.
In my opinion, even we could not really say that there is a user data collecting process or have no obvious evidence. It does not mean that they don’t anyway. To be safe and live with privacy, users are the person who has to protect themselves and be aware of using those 3rd-party platforms.
reference: facebook listening experiment
reference: Google admitted about smart device collecting data
0 notes
Text
[w7] Tutorial: Should Government Have More Access In Collecting People Data?
I said that self-driving is my favorite case study last 2 weeks. It has changed right now because this week case study is soooo muchhhh funnnnnnn.
As the name of this blog, the problem of case study today is that “Should government have more access in collecting citizen data?”. Of course, Richard had provided us some pre-reading resources. I had gone through most of them a day before the class and realized that the content is pretty much close to my awesome project which is facial recognition.
Hayden told students to choose the side because we were all going to have a debate. I decided to go for the side that agrees if the government would like to have more permission in collecting citizen data. There were Franklin, Zhen, Hyeonji, Rob, and Sunny. Actually, there were 2 more but I couldn’t remember their name. The discussion turned out pretty satisfied even most of the member did not really prefer the government to have more, but not less than the current one. So here are some interesting points.
Even the government have no access to collect data legally, other 3rd-party companies still secretly do it anyway. Isn’t it better to have an official law in controlling the use of all these data?
Since the last 2 weeks, Google had an apology about using Google home mini in collecting user’s conversations.
It also makes the city be more secure. Imagine when there is a criminal and some CCTV can capture his face. Police can instantly know who he is and rush to charge him.
Once the debate was going to start, Hayden just swapped the topic and my side has to disagree with what we all had done. It was surprisingly unexpected, but I felt kind of enjoy it at the same time. It was like everything can go wrong, all the plans got ruined and we all had to solve an immediate problem.
Honestly, I do really appreciate most of the student. Even their topic had changed, they mostly performed so well and came up with various ideas. Moreover, I was sitting at almost the end of the table and had to debate very early. I did not come up with a nice idea and felt a bit regret myself.
1 note
·
View note
Text
[w7] Lecture reflection
The first point for this lecture class is about Diffie Hellman Key exchange algorithm. I could say that I was very confident with this point since I had done research about it since Week3 (This topic is in w3 online module). So I would write only the core idea of just to remind myself.
Diffie Hellman
Diffie Hellman is the way to have a shared key between 2 persons without having to concern about secret leaked to the public.
Krak Des Chevaliers
In the Crusade era, Full of templar knights, Castle had an outer and inner ring. Eventually, it fell from the attack of Ottoman’s kingdom. However, the castle has never fallen from the weak defense but the surrender.
Cyber Literacy - Vulnerability
Vulnerability is a weakness of something. it can be very various.
hardware problems
software bugs/errors
Exploits - attack directly to the vulnerabilities of the system, which can be various way
Memory corrupt is one of the techniques
OWASP - Open Web Application Security Project
A non-profit organization founded in the USA in 2004 aiming for making web development around the world to have a reasonable security standard. They usually make a security conference to educate IT organizations in security knowledge.
They made a list of top 10 vulnerabilities in web development

Assets in security engineering
Security is basically made to protect our assets, there are several basic idea about strategies in assets protections
Multiple pairs of eyes - ask many people
Standards and protocols tend to miss more than they catch
Do not think that everything has been done (it is impossible!)
Regularly surveying the values of people involved in what you are protecting
People who have to live with that asset would know about it more than security engineers
Make a sensible plan
Constantly re-evaluate current list of assets.
0 notes
Text
"Smurf Attack”, a clever way of DDOS attack
From the previous blog that I talked about how to reset a wifi router by using only a simple shell script (which can be considered as an attack), it made me feel want to know more about attacking network connection (especially router). So I did some more research and found that the most basic way is DOS attack.
DOS attack is basically an attack that trying to shut down the server of the target or making it inaccessible to its intended users. It is done by making a huge amount of traffic to that network. Once the traffic reaches a maximum level that the target network can manage, the system is shut down. This means that the attacker needs to have so many machines to make this attack.
Ping to Death
The most basic approach is “Ping to death”. As its name, an attacker sends a ping (target need to send a response of the request of the attacker) until the system is down. The most simple way of doing this is telling your friends (maybe hundreds or thousands of people) to keep refreshing (spamming F5) the target website.

So this approach requires a huge load on the attacker side, I wonder is there any other way to attack the system without a large amount of attacker? so I searched more for other approaches.
There is another interesting method that I personally feel that it is very clever and would like to share into my blog. Its name is “Smurf attack”.
Smurf Attack
Imagine when an attacker sends a ping to a server and makes it broadcast to all the machines connecting to that network. The result is that all those machines will send a response back to the sender by using a source address in the header of the request packet.

This means that 1 request could be amplified to a number of machines connecting to the network responses (Amplified by 3 in the example above).
So what if attacker force modify source address in the packet header? For example change to the target server address.

All the amplified response will be navigated to target address instead of the sender. If the network that receives a ping from the attacker have 1000 machines inside. this means 1000 times amplified responses will be sent to the target!. It is produced by only 1 ping request. So imagine the attacker consistently send requests at very high frequency, the target system will be destroyed easily. What a clever approach.
P.S. I drew all the picture myself! how do you feel? Is it cool, right?
0 notes
Text
Reboot router (RISK)

This person is Arm. He is Thai Ph.D. student who inspired me to study in computer engineering degree. He has a video streaming every Saturday night and the topic this time is about how to use Raspberry Pi to reset an internet router at home. Because my awesome project is about Raspberry Pi as well, so I was quite interested in this talk.
The idea of it basically just connects the Raspberry Pi to the network and periodically run a given shell script, resulting in having router being reset. It sounds so easy.
After his streaming, I searched up about how to do it myself because I would do it after my awesome project has finished. I think it would solve many problems in my WLAN router (Yeah, “reboot malfunctioned devices always solve the problem!”, my dad always says that LOL). Then I found something that is very interesting and would like to share to you guys especially person who is doing this course. It directly straight forward to the content.

The steps in rebooting the router require only 2 things. Firstly, your machine has to connect to that network. Secondly, can do telnet scripting. The tutorial of how to do it is right there below.
reference: How to Automatically Reboot Your Router the Geeky Way
The point that I would like to make is that its requirements are just that 2 things and this can be done in a very expensive router that claims to have a good security system. Once you can connect to the someone internet network and there is no security in the software side implemented, you can shut down a whole network with 4 lines of telnet script. It is not secure at all and security engineer should concern about this as well.
1 note
·
View note
Text
[w6] Tutorial: Russia cyberwar
Honestly, this week case study was very very very difficult one! I do not really know what other people think about, but this is really what I feel. Moreover, this is a practice exam as well! Oh man, how can I survive in the final examination?
Since the question is that what should we do or is there any recommendation, as being a security consultant if there is a cyberwar and we have to prepare against Russia. To be honest, I did not really have many ideas about cyberwar attack. It was so hard to think of the proper way. Additionally, Hayden asked us to list 10 things while our group came up with only 3.
Firstly, the best solution in dealing with the problem is to not have a problem from the beginning. We all know that even you are is the winner of the war, it takes so much sacrifice and deadly loss. Being nice to them and try compromise when there is a problem.
Secondly, we need to educate people to at least understand the fundamental stuff about security in every range of age. Especially an older age (X and Baby Boomer generation) because they have less understanding in internet areas comparing to the younger one who is surrounded by technology. They tend to not aware of any risks from the internet such as scam email.
Lastly, we were pretty much running out of ideas at this time. One of our group members proposed something sounds silly but it made i whole class more entertain (it’s cool haha). He said we should outsource Indian to help us build a security army to and be prepared for the war.
In the discussion, most of the group came up with only 2-3 ideas. It was reasonable because none of us have in-depth knowledge about a cyber attack. So it is quite difficult to try to find a way to prevent them compare to the past case study where most of the problems based on a real-life situation. Moreover, I am not 100% know about Australia’s resources since I moved here just 2 years ago, or even I know, It still difficult anyway because Russia has lots of resources, technological power, and power in negotiation by themselves. By the way, this is a really good case study as well.
0 notes
Text
[Something awesome] iteration #6 [FINAL]
This is my last blog about my awesome project. There were so many problems happened along the way before I finished this blog. My Raspberry Pi got bricked 3 hours after I had finished integrating hardware and software components together. So I had no chance to record the video of it.
I spent fully 2 and days to reinstall the and set things up in my spare raspberry pi (As I mentioned in #5.5). However, it did not turn out as I had expected. Raspbian Buster, the latest version of the raspberry pi operating system, created for Raspberry Pi 4 which is the new model, is not 100% compatible with my model B+ and causes so many trouble while installing OpenCV module which takes 2-3 hours each time. It kept ending with error installation around 88-100% of the installation. I tried 5 different versions of this module (3.4, 3.4.1, 3.2.0, 4.0.0, 4.0.1) but all of them failed. I felt kind of regret that I did not take a video of my project before it got brick.
Fortunately, Last night at 3am, I decided to move on and looking for a way to make my software run in Arduino UNO in order to have some simulation to be shown in the presentation. Thanks to my Thai electrical engineering friend that guided me through this. So apart from how to do GPIO programming in python (for Raspberry Pi), I would write about how to control Arduino UNO through pyFirmata (module for python3) as another extension that was not mentioned in the proposal.
Redesigned Circuit

This is my new circuit connection. One more LED diode has been added and move the 5V DC source to NC side of the relay module. This would make the circuit to have 2 led color that can indicate door being locked or unlocked.
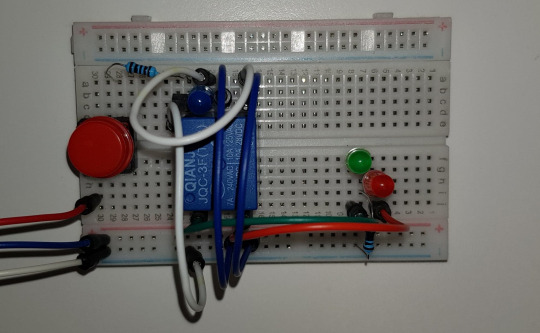
This is what it looks like in the real connection. It becomes way cleaner than the previous one having very messy wires and jumpers.

The green light indicates that the door is unlocked, while red is the opposite way.
GPIO programming for Raspberry Pi
Example of GPIO programming on Raspberry Pi
After I have both software and hardware prepared good enough to be put together, the time that I have been waiting for so long is here!
Let’s put them together and create a really cool facial recognition doorknob system. What I have to do is just set the digitalWrite signal to enable the relay module once my face is detected.
Firstly, the GPIO module is needed if this software is going to run on Raspberry Pi. It basically allows you to access all the pin on the board.
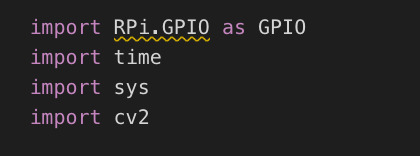
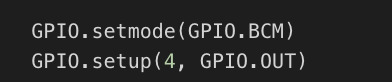
Next step is about to pick one pin as an output. The code below takes care of that.
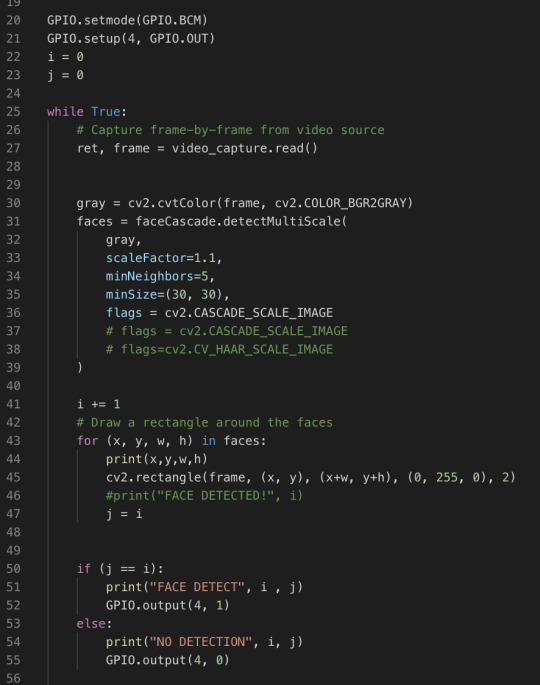
Then add a couple line of codes to make the pin to send digital output to the GPIO port in our circuit. A new code including line 22, 23, 41, and 50 to 55. It is very basic logic.
pyFirmata programming for Arduino UNO
This section is an additional one from having bricked Raspberry Pi. It is just to test that software and hardware can run together correctly because all of the computational parts are done by the laptop connected to Arduino. So the board is basically just a tool to send a digital signal to the circuit, no computation stuff at all.

So a module taking care of controlling the output pin in this time is pyFirmata. To do this you need to upload a standard program of Firmata into the Arduino board.

Arduino software provides you this program. You do not even have to learn how to code about this. PyFirmata is a program that changes your Arduino, that usually perform a software part, this burden is pushed to the high-level programming side (python in this time). So we can do everything, for example, reading and writing the pins.

The codes above have to be added into the main program of the recognition. It just specifies the port address connecting to the board, sets input and output pins.
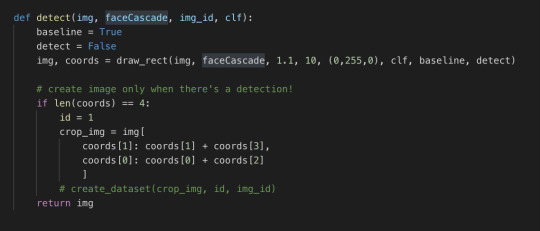
The first method is the detect. It is almost exactly the same as in iteration #5. The only difference is that I changed i and j into the boolean flags.
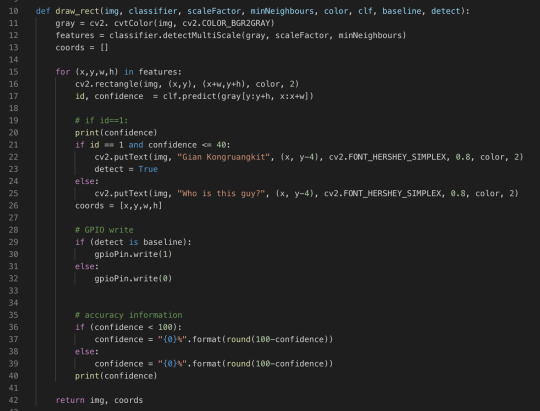
This is pretty much the same as last iteration’s code as well. Lines 28 to 32 are added. Just only 4 lines of code, we can have our system run on Arduino UNO! Isn’t it cool?
Running the program!
After all the time I spent on this project, this is the moment I have been waiting for. The facial recognition system that I created myself, got out of my comfort zone to build it from the scratch and researched heaps of self-learning. This video below could describe everything.
Video of the final result
Conclusion
This is a very long journey for me. I have learned a lot and my perspective of computer vision technology has been completely changed as well. I was really excited and proud of myself in the presentation today when I tested my program and shown it in the class. The reaction of everyone in the tutorial class made me feel like all the hard work paid off. Although my ways of explaining things are not that good, I hope you enjoy my blog and can gain at least some new knowledge from it. Cheers!
0 notes
Text
[w6] Lecture reflection
AES: Advanced Encryption Standard
It does not mean that it could not be broken, it can but not in the feasible time, for example, 100 years to brute force.
Based on the substitution-permutation network
Block Ciphers Modes
Allow cipher to work with large data streams without the risk of compromising the provided security
in order to ensure that the distinct ciphertexts are produced even the same plaintext is encrypted multiple times with the same keys. an initialization vector is needed.
ECB: Electronic Codebook Mode
Each plaintext block is encrypted separately.
Each ciphertext block is decrypted separately as well.
Can encrypt and decrypt by multi-threading approach.

CBC: Cipher-Block Chaining
Invented by IBM in 1976
XOR is added into each plaintext block to the ciphertext block that was previously produced.
the result is encrypted using general cipher algorithms.
every ciphertext block depends on the previous one.
XOR is added to a random initialization vector in the first block (no previous one).

CTR: Counter Mode
Block cipher can work in the same way as a stream cipher
Disk Encryption
a technology in protecting data by converting it into unreadable code.
This is very difficult to be decrypted by unauthorized people.
Richard talked about encryption keys are stored.
Random keys are generated to encrypt the disk
Encrypt the key and store it outside the disk
Windows Operating System
Check that disk can perform self-decryption
let the disk decrypt everything itself
Forensics
RAM is a memory that can maintain the data even the power is turned off.
0 notes
Text
[w5] Tutorial: Self-driving car case study
For the case study this week, I could say that it is my favorite one comparing to all the past weeks because Hayden gave each group different roles (Government side and car company side).
From the question, my group has to think about a list of assets of the country that has to be concerned if self-driving cars are allowed to be used in this country. Additionally, 3 risks that have to be concerned and how to deal with each one as well.
Here are the ideas I come up with myself.

In the discussion time, my group was sitting at the end of the table which was going to be the last group to propose our ideas. Once the first group (the one having Richie as a member) started to talk about what they had done, they talk about the reputation of the company, which really made our group have a question “why?” on our head. Why do the government have to concern about company reputation? shouldn’t we think only about the public or citizen sides?
They also proposed one idea which was quite the same mine which is having a testing phase by specifying some small city (should be countryside) and set that city to have 100% self-driving cars to measure the result.
There was another group that talked about the risk of low signal area for example inside the tunnel or underground that might cause AI to wrongly track GPS.
To conclude
I have really enjoyed this class since I thought that Ideas can’t be these various because I had not been able to think of many things and also felt a bit blank space in my head, but it turned out surprisingly different!
Then at the end of the class, Hayden just revealed the truth that half of a class had a role of government and the rest had company side. Hope there is kind of fixed different roles again in the rest of the tute!
0 notes
Text
[w5] Lecture reflection
This week, I did not attend the morning lecture since I had an appointment with a doctor for diagnosing my left arm. However, I tried to catch up the content by going through the course content on OpenLearning page module 5 and the note taken by other students.
Wired Equivalent Privacy
security protocol created with a good intention, however, it is not really secure enough. It provides several levels of security and privacy in WLAN.
Hashes
- There are various types of hash (such as MD5, SHA0, SHA2, ...).
- Some of them are broken, which means it can be violated faster than the time complexity of brute force (birthday attack is one of that).
Merkle Damgard Construction
This is the approach to create a collision-resistant cryptographic hash function. It basically breaks a message into a series of block and then gives the hash function starting with the first block. An output of it will be used in the hash function again combining with the next block. Repeat a whole process until all the blocks have been hashed, resulting in the final hash.

Digital Signature
From the idea of the public and the private keys in the past lectures. It can be used in another way to perform authentication.
By swapping the process, the sender encrypts a message with the private key and send it to the receiver. Once the receivers receive the encrypted message, they can use their public key to decrypt it.
This means that, if the messages are able to be decrypted, this can confirm the authentication of the sender.
Key Stretching
Online attacks: can be forced to log out of the account you signed in if you have failed attempts to many times.
Offline attacks: Hashed password files are stolen, it is used to decrypt the password locally.
0 notes