Don't wanna be here? Send us removal request.
Text
Autonomous Cars Discussion
This week’s case study was the study of the assets and risks involved in a company creating autonomous cars.
For the assets of the company making autonomous cars, my group and I decided that they should be the software, the company’s reputation which it needs to be positive to remain profitable, and any financial assets they had resting in this venture.
For the risks of this project, an obvious one was identified as that of there being accidents involving the cars themselves due to unpredicted behaviour, as well as the systems of the cars being compromised by those wishing to do harm to users and the company.
As a solution to these risks, we proposed that to reduce any negative impact on the company’s reputation, such as through letting down expectations of the final product, realistic expectations and development goals should be set, instead of flashy, unnecessary promises to make sure that consumers know definitively what they are buying and reduce the chance of letting them down. For protecting the software and the system of the car, strict security procedures should implemented. Also, as this will be a new type of technology, interacting with the consumers so that they are able to have confidence in the product, and by extension the company, should be conducted. This can be through free lessons on how to operate their autonomous car, or what do to in an emergency.
0 notes
Text
Protecting Assets Case Study
For protecting Google’s assets, me and my partner identified that no matter what, employees came first, as no life is worth any amount of data of money, and then it was the data, since data is a vital core component of Google’s business model, and finally the infrastructure, which Google needs to store all their data and do all their work on.
For the three key security design features that we needed in our system, we decided that it would need to keep hostile entities out, but also allow individuals out quickly in the case of an emergency, such as a fire, and protecting the infrastructure and data.
To keep unwanted individuals out but also evacuate quickly should there be a need, we came up with the idea that there should be access cards for every verified employee with photo ID and unique ID number for use in entering certain buidings and that there should be a large number of easily accessible evacuation routes; also, security training for all employees so that techniques such as tailgating by strangers are prevented; Google should also implement layered defence by installing a number of checkpoints with guards from the entrance to the site (i.e. boomgates, fences) where ID can be verified; constant surveillance; background checks on employees to mitigate insider attacks; and evacuation facilities that can contain a large number of people at a time
To protect data, important data operations should require multiple employees to operate in order to be committed (i.e. copying data into different servers).
To protect infrastructure, use the above mentioned security techniques to keep unauthorised persons out of data centers
0 notes
Text
Cryptography Terms
Confusion: each bit of encrypted data should depend on multiple parts of the key
Diffusion/Avalanche effect: a small change in the plaintext should result in a large change in the encrypted data
Substitution-Permutation Network: encryption using a series of XORs, substitutions and permutations, where tokens are swapped around
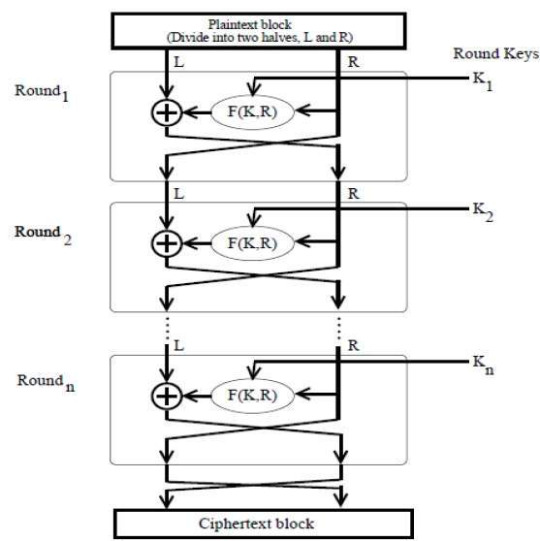
Feistel Network: a type of block cipher that consists of multiple stages where input is divided into two halves, the left half is XORed with the result of a function between the key and right half, then swaps positions with the right half as input for the next layer
Stream cipher: symmetric key cipher, every bit is encoded with a corresponding key bit
0 notes
Text
Buffer Overflows and Format String Exploits
A basic type of exploit, buffer overflows involve exploiting memory structure in C. Given the stack-like structure of memory in C, local variables are stored before the return address for a function. Since C functions such as gets that receives input from the user don’t check that the number of characters entered is more than the size specified for the variable, entering more characters will overwrite the memory after area allocated for the buffer. With this ability, both local variables and return addresses for functions can be overwritten such that important variables can be changed to a desired value, or the function will return to run another piece of code.
One method to protect against buffer overflows is to store a value called a canary before any local variables are allocated, so that any buffer overflows will overwrite the canary, and the program will check the canary is the required value afterwards, and if it isn’t, will terminate the program.
However, the value of the canary can still be checked using format string exploit, where giving a printf function a format string without any corresponding arguments will print out the values in subsequent memory addresses. The %n format code also stores the number of characters that comes before it to a specified variable, or the next memory addresses if no variables are given.
0 notes
Text
Week 6 Lectures
In this week, I learnt how initialisation vectors were used in cryptography to help the encryption of data. In the Cipher Block Chaining process, IVs are strings of random characters that are the same length of the plaintext and are XORed with the plaintext before it is encrypted with a key, and the resulting encrypted text is XORed with the next block of data to be encrypted. Compared with just encrypting blocks of data with the same key known as Electronic Codebook Mode, this method, with the introduction of a random element provides diffusion for the encrypted data that hides any patterns within the data. However, CBC can also be cracked if IVs and keys are reused, as is what happened with WEP, as it only used a 24-bit IV.
In disk encryption, a random key is used to encrypt data on the disk, but is then itself encrypted with a password and stored somewhere other than the disk itself.
I also learnt about threat models and how they help in breaking down the possible ways a system can be attack into, so that individual components can be analysed. This makes it easier to know which areas of security attention should be focused on based their likelihood.
0 notes
Text
Threat Modelling an Electricity Transmission Network
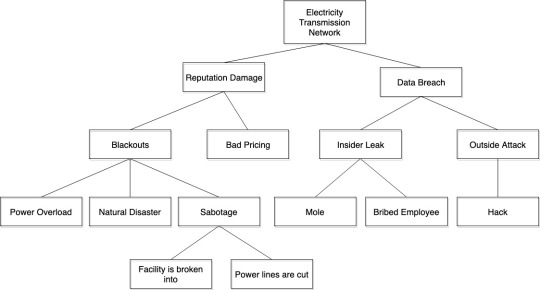
As can be seen from my tree, I believe there are both physical and data vulnerabilities to be faced by a power company, as this type of company relies mostly on its infrastructure for its business, as well the large amounts of data it has on its customers to make informed business decisions. For both power overload and natural disasters, better infrastructure can mitigate these risks. However, for sabotage, facilities can be better protected with increased security, while power lines can be placed in areas that re hard to access without specialised equipment. For protecting against insider leaks, a strict logging system that records which employees have access to what data can help to both discourage leaks as well as help quickly track down any potential suspects in the event of a leak. Protection against hacking can be improved through having an in-house unit specialising in protection against cyber attacks.
0 notes
Text
CTF Challenge 12: cmd2
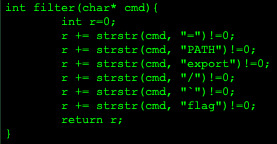
I found this challenge to be a little similar to cmd1, however it had a stricter filter function that rejected any ‘/’ in the arguments:
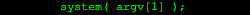
Due to this, I instead decided to turn my attention to the system() function that usually runs cat command:
On its man page, I found out that it actually uses the execl() function to run a binary of sh to run the command:

Checking the man page for sh, I found that the sh program has a builtin command called ‘command’, and has an option -p, that will run any command that can be found in the PATH environment variable. Knowing this, I ran the command:
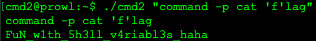
to bypass the filter and obtain the flag.
2 notes
·
View notes
Text
Week 5 Lectures
This week, I learnt about different types of vulnerabilities as well as more on hashing. One vulnerability that I learned about involved Wired Equivalent Privacy, and consisted in intercepting a data packet and changing its destination address to that of a device owned by an attacker. This packet would then be resent to an access point, which would decode it and send it to the specified location. This is an example of exploiting existing systems to work in unintended ways, showing that sometimes, the hard work doesn’t always need to be done by the attacker.
For hashes, I learnt that to protect against length extension attacks, the hash h(key|h(key|message)) should be used as the extra layers of hashing prevent attackers from simply adding on extra data at end of a hash. Also, salting a password by adding random data before it and then hashing the result is also an effective method at negating the impact of rainbow tables, which contain pre-calculated hashes of common phrases, and whose effectiveness relies on its reusability.
0 notes
Text
CTF Challenge 11: lotto
In this challenge, the code involved entering 6 characters into a program:

I noticed that all the characters in lotto would be transformed into ones within the range of 1-45, and the only printable characters within that range were space, and !"#$%&'()*+,- The nested for loops also showed that there only had to be 6 identical characters for an input to possibly trigger the . Thus, I had to rely on chance for my input, which could be any of the characters mentioned above:
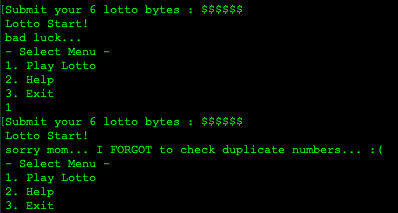
0 notes
Text
CTF Challenge 10: cmd1
The code for this challenge was quite straight forward:

From experiences from past challenges, I knew I had to get the string “/bin/cat flag” into the last system function call. However, I identified that the filter function would cause the program to quit if the string ‘flag’ was detected.
However, I had an idea to use echo of a separated string for flag, which worked:

0 notes
Text
CTF Challenge 9: bof
In this challenge, a simple buffer overflow was needed to obtain the flag, where an address in memory should be overwritten by user input to change the natural program flow. The code:

shows that a gets is used to allow the overflow, and it can be seen that key, which should have the value of 0xDEADBEEF, is checked to be equal to 0xCAFEBABE. From this it can be assumed that the address holding key or 0xCAFEBABE should be overwritten.
Using GDB, I disassembled func:
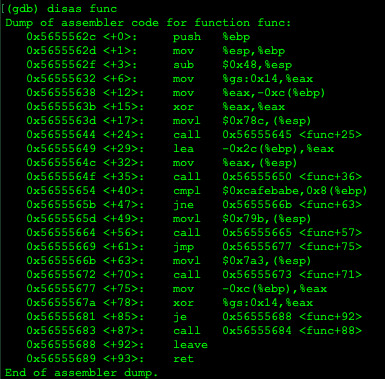
and noticed that the address for comparing 0xCAFEBABE and key is at 0x56555654, so I set a breakpoint there.
After running the code and inputting some xs, I inspected the memory pointed to by the stack pointer:

I noticed that that the xs I inputted were 13 32-bit words in front of the address containing the key variable that currently holds 0xDEADBEEF. This means that to change the value in key to 0xCAFEBABE, there needs to be 52 padding characters entered before the hex values of BE, BA, FE, and CA in that order due to little endian.
Knowing this, I piped in some Python output into the CTF server to obtain the flag.
0 notes
Text
OWASP A5-2017: Broken Access Control
Access control dictates what resources and systems a user can access, depending on their account level. When access control is broken, the attacker is given access to areas where they should not be allowed and can result in adverse effects, such as data breaches.
Normally, access control is implemented by giving roles to each user, which determine how they may interact with files and systems, each of which have their own rules on what roles may read, write and execute them.
A common to break access controls in web apps would be to enter the appropriate URL in a browser’s address bar that requests data for a high level role account through the use of parameters (i.e. www.website.com/admin_info). For systems, elevating roles and privileges can be done through techniques such as SQL injection.
Access control can be improved with multi-layered login, and ensuring privileged access to certain webpages, as well as logging all activity access control failures.
0 notes
Text
Week 4 Lectures
In this weeks lectures, I learnt about bits of security and hashing.
Bits of security is a measure of how much work or how secure a method of security is. This is typically measured by taking the total number of unique possible combinations and turning it into an exponent of 2. For every increase in a bit of security, the possible number of combinations doubles. 10 bits of security is approximately 1000 (2^10 = 1024).
Hashing is when data of variable length is transformed into data of fixed length. Hashing is mainly used to ensure integrity of the data, that is, the data hasn’t been changed during transmission, and to provide authentication, where the identity of the sender is verified. Unlike encryption, hashing is not intended to be reversible. To provide integrity, a hash of a message can be first created by the sender and sent in one channel, and both the message and hash of the message are sent to receiver, and provided they know the hashing method, can check whether hashing the received message matches the one given in the first channel. For authentication, and for cases where an attacker may know the hashing method and thus be able to change the message, hashing-based message authentication codes (hMAC) are used, where a shared secret is hashed along with the message. Even if an attacker knows the hashing method, they might not be able to create a valid message as long as they don’t know the secret. However, if the secret is added before the message and then hashed, an attacker can commit a length extension attack where by they gather as many transmissions as possible and brute force the hash of the secret by checking if a value that hashes with messages matches their corresponding hashes. Knowing the hash of the secret will then allow the attacker to create a valid hash for their own message.
0 notes
Text
CTF Challenge 8: leg
This challenge involved analysing both C source code and assembly code.

In order to obtain the flag, I had to figure what were the return values of the three key functions.



For key1(), the corresponding assembly code looked like this:

I noticed that the mov instruction was located in address 0x8cdc, but the program counter would then be 2 ahead of it, in 0x8ce4 (36068).
For key2():

The value in r3 is first copied from the program counter, and like before, is 2 ahead of the current position, so 0x8d08, but then it increased by 4 to 0x8d0c (36108).
For key3():

The value of r3 is obtained the lr (link register), which records where the program counter should return to after finishing the function.
From the disassembly of main():

it can be seen that this value is 0x8d80 (36224).
Thus the value that should be entered into the program is 36068 + 36108 + 36224 = 108400

0 notes
Text
CTF Challenge 7: blackjack
This challenge involved looking at the source code of someone’s blackjack game, which included a phase for betting money and hitting or staying hands. While the code itself was quite long, I identified two pieces code that seemed exploitable to me:


The first block shows the function that reads in an integer value for a bet amount, while second block shows that upon losing a hand, the total cash the player has is subtracted by the value of bet. I noticed that while the betting function checks whether the bet value is not larger than the money in hand, it doesn’t check if it is negative. If it were to accept negative values, then losing a hand would then result in the amount of money actually increasing rather than decreasing.
Testing this on the pwnable server, I found that this did in fact increase the amount of money the player has. Using the hint from the pwnable site, I increased my money to above $1,000,000 and received the key.


0 notes
Text
CTF Challenge 6: shellshock
In this challenge, there was mention of bash and shellshock. After searching online, I found that this referred to an exploit of and older version of Bash that allowed the execution of Bash commands through an exploit involving setting environment variables: https://en.wikipedia.org/wiki/Shellshock_(software_bug)#Initial_report_(CVE-2014-6271).
Checking the provided source code, shellshock.c

I could see that it called a custom version of Bash to run some code.

Using the code given in the website as an example, I executed the above code and received the flag.
0 notes
Text
CTF Challenge 5: mistake
In this challenge, the hint mentioned operator priority, which I understood to be the order in which operations, such as assignment and arithmetic operations.
I noticed in the provided source code that there seemed to be a misplaced operation:

where fd is supposed to be assigned the return value of the proceeding open function and checked for being less than 0. However, due to order of operations in C, it is actually assigned the Boolean result of the operation of checking if the return value of open() is less than 0, which if not successful, is 0. Assuming the file is always successfully opened, the value of fd will always be 0.
The following code:
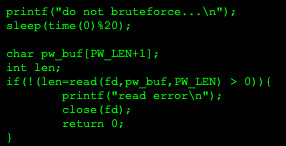
shows taking in input from the file pointed to by fd and copying it into the string pw_buf. Since fd will always by 0, this means it will take input from stdin, but due to the sleep call before it, 19 seconds must be waited until submitting any input.
The remaining code:

shows that a second string of 10 characters is taken in fro stdin, has a function xor performed on it, and compared to pw_buf.
The xor function:

goes through each character of a given string and XORs it with the value 1, thus incrementing even values and decrementing odd values.
The following gave me the flag:

since k has an ASCII value of 107, I used js, which would be incremented by the xor function.
0 notes