Don't wanna be here? Send us removal request.
Text
Infographic
Today I made an infographic using the information from a web analytic blog called Occam's Razor by Avinash Kaushik with Piktochart. This is the blog post that was used to create this infographic:
https://www.kaushik.net/avinash/data-visualization-inspiration-analysis-insights-action-faster/#treemap
I briefly overviewed the different types of data visualization that Kaushik explained in his blog post. The screenshots that was used in infographic was taken from his article as well. I also provided different resources for others to make their own data visualization based on the sites Kaushik recommends. This exercise was fun and challenging for me as appropriate information needed to be chosen and displayed for others to understand the topic. It was a little difficult trying to fit all the information and choosing the displays, fonts, and colors. However, I hope you all are able to understand and learn something new from my infographic.

2 notes
·
View notes
Text
Coding
Programming is a very good skill to have, no matter what you are interested in. It comes handy in many ways especially during these times where technology is everything. Hence, codeacademy.com was a very fun learning experience for me. I got to learn a lot about python and there were many other courses that I could choose. If anyone is looking to get started in programming, I suggest for them to use codeacademy. Bellow are the list of achievement from the lessons and the example of the coding that was used


Don’t keep calm and code on
0 notes
Text
Cyberbullying
Nowadays everyone uses internet in their daily lives. But there are many benefits and risks that comes with the use of internet. I have covered a topic on such risk to educate others about cyberbullying. Please watch the video and be safe.
https://youtu.be/Bh58iB5mgqc
1 note
·
View note
Text
App to help you choose books
Books are important part of my life. So I decided to build an app to help you choose the right book for you. Open the app and read the reviews to choose the right book for you.
https://snappy.appypie.com/html5/books-for-you-98fd8b5fafe2
0 notes
Text
Personal Branding Statement
When developing my personal brand statement, I really had to think about who I am as a person and the information about myself that I want to convey to others. It was mostly about how I wanted to be perceived by others. Stefano Principato’s Personal Branding says that the first question to reflect on for personal branding is “Who am I?” To answer this question, I looked at my personality, passion and abilities that can be used to describe me. I would answer this question using my traits. I am a positive, energetic, cheerful, and resilient person. My abilities are being a fast learner, efficient problem solving and ability to collaborate with others. My passions are reading, writing, photography, sports, and travelling. In terms of what I do, I am a biology student with some volunteering experiences at a hospital and lab. My mission in life is to be a decent person who is respected by family, friends, loved ones and my chosen communities. I am here to make a positive difference despite being imperfect. My work reflects my values and enables me to travel widely and enhance the lives of others and remain a happy person. People will remember me for being there to lend a hand, keeping an open mind, and for getting involved in issues that matter most to me. My vision is to earn another degree related to biology, learn how to network better and attend networking events, be an expert in my field of study, and be the most productive employee of a company. The more I analyzed the main factors of developing a personal brand, the more I realized that my personal branding statement will continue to change with time as I come to understand myself deeper and the more experiences and changes I will go through. But for the moment in time, my personal branding statement is:
As a biology student with volunteering lab experience, I am someone who is always looking to learn and be inspired by the world and who strives for happiness and peace. I am someone who likes to make others comfortable, be productive by myself or in a group, and can maintain an optimistic outlook on the end result of any situation, no matter how disheartening it is.
0 notes
Text
Cybercrime and Cyber security
Cyber crimes are crimes that involve the use of computers and internet. Some examples are: cyber extortion, crypto jacking, identity theft, and credit card fraud.Usually these crimes are committed to target an individual or corporation’s data. Cyber extortion is when there is an attack or threat of an attack along with a ransom demand to stop the attack. Crypto jacking is using scripts to mine cryptocurrencies without their consent by loading cryptocurrency mining software to the victim’s system. Identity theft is when the cybercriminal steals the user’s personal information such as bank access information or SIN through the access to their computer. Credit card fraud occurs when cyber criminals gain banking information of victims by hacking the retailer’s system or by installing credit card skimmers.
There are many common ways that cyber criminals carry out their attacks such as DDos, phishing, credential attacks or hijacking a website. Distributed DoS attacks, DDoS, are often used to shut down systems or networks by overwhelming the network’s ability to respond to connection requests. Infecting systems and network with malware to damage or shut down a system until a ransom is paid. Phishing is when a cybercriminal sends fraudulent email and spreads malware to their system or to the company’s network through their system. Credentials attack is when the cybercriminal aims to steal user’s ID and password by installing software or hardware that exposes the victim’s information.
Although cyber crime cannot be completely eradicated, there can be measures that can be taken to increase cybersecurity and defend one selves. Some of the simple steps that can be taken are changing passwords regularly, using additional security such as multi factor authentication, backing up information and data regularly to reduce information loss, and not risking your personal information by not opening or responding to suspicious messages. Updating your system regularly, and downloading antivirus and antispyware software will also prevent many of these attacks.
0 notes
Text
Does Online Privacy Matter?
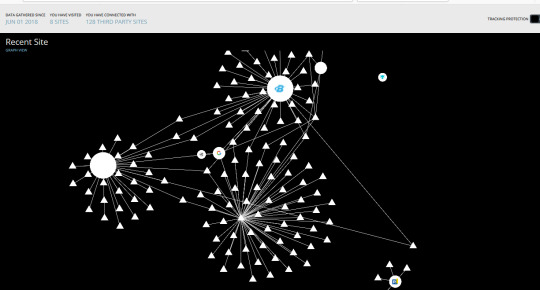
Have you all ever wondered how much privacy we have online and how much of our information is secure. I installed an add on called lightbeam from firefox to to show both the first and third party sites I interact with on the Web. Lightbeam basically shows the visualization of all the third parties that are active on the page you visited. It displays the relationship between the third party sites and the sites you visited. I was genuinely shocked when I saw the graph. I had only used only 8 sites but had unknowingly connected with 128 third parties sites. We all use internet everyday but we are still unaware of many thing related to it. Nothing in all the world is more dangerous than sincere ignorance and conscientious stupidity. As a concerned netizen, I ask others to try to learn more and use the lightbeam add on themselves to see how many third parties sites they interact with. I will add the picture of my GraphView down below. Always remember the quote by Richard Cecil: “The first step towards knowledge is to know that we are ignorant." Always be on the pursuit of knowledge and insight.
0 notes
Text
Module 3 - CEID100
Here is a little review on the topic that we have chosen for an assignment to teach high school students a little something from our course. Click on the post below and follow the Prezi.
https://prezi.com/m/bsphhcenkz7o/ceid100-final-project-proposal-cloud-computing/
0 notes
Text
How to Google: Hacks

We all use Google. Googling has become like second nature to us. If there are any questions, we type them in the search bar and all the available answers show up. But did you know that there are more ways to find exactly what you want? There are many google hacks to make your life better and easier. Use the following hacks to spend less time searching, so you can find more time for your assignments, YouTube, or Facebook.
1.) To search an exact word or phrase in google, write quotation marks around it. For example, search “need school help” or "word" and the results will only show the sites that have exactly the same phrase in the same order.
2.) To search something on a specific site, there are two ways to perform this specific action:
a. I believe everyone knows this step. Go to the specific site, use the search bar of the site by pressing ctrl +F, and type up the text you want to find and the words will be highlighted.
b. A slightly easier approach to lazy people like you and me is - in google search bar, type of the word site with a colon (site: ), the specific site that you want the results from, and the word you are looking for. For example, if you want to find constitution in Wikipedia, simply type site: wikipedia.com constitution. Voila! Google becomes magic.
3.) To find the definition of a word, use word “define” with or without a colon and type up the word that you want to be defined. (e.g. Define: education or define education)
4.) To find the product within a price range, type the name of the product and write the minimum amount followed by “…” and then the maximum amount. (e.g. beats headphones $100...$200)
5.) To look for a specific filetype, type the topic that you are interested in followed by filetype: and the type of file you are looking for. For example, Philosophy filetype:doc
6.) To include words in the search, simply add the word “AND” between the two words. (e.g. philosophy AND society)
To exclude words, simply add “-“ to each word. (e.g. If you want topics about science without including physics and chemistry then search science -physics-chemistry)
7.) To find sites or pages similar to the existing one, type the word "related:" followed the existing website or pages (e.g. Related:Wikipedia.com)
8.) To find the exact form of a quote, even if you were missing some of the words, add asterisk in place of the missing word. For example, search she wore * in her * and carried magic * in her eyes.
9.) To search for pages containing two connected words, you can use the word “or” between the words/ phrase or place “~” in front of each word. For example, if you are looking for the relationship between philosophy and society, search "philosophy or society" or "~philosophy ~society".
10.) To search for hashtags, simply type site followed by colon (site: ), followed by the type of social media you want the hashtag from, then the actual hashtag you are looking for. (e.g. site:twitter.com #CEID100)
Read these hacks, memorize them and become the king or queen of googling for that essay, assignment, or research. Hope these hacks change your life. Hope you enjoy this blog. Till next time.
0 notes
Text
NETIQUETTE : The Steps to be a Good Netizen
Netiquette is defined as the set of etiquette that is applied for acceptable online behavior while browsing internet or during online communication. Everything that is posted online can be traced and can never actually be deleted completely. Your “online footprint” can always come back to haunt you. So, use the netiquette to ensure that your online footprint reflects well on you.
Remember to apply the same standards and values online as we would apply in real life. Online world is just an extension of our real world. So the values placed in our society such as hate speech, copyright violation and other forms of exploitation still applies in online world. Always treat others with courtesy, kindness, openness and the respect you would like to receive. Always accept the law that is placed to protect the rights of other netizens. Acknowledge the cultural differences; accept that social norms of some netizens might not be the same for all the netizens.
To make communication more efficient, always say things with care. First step is to proofread your messages. A good netizen should always use appropriate language. Intelligence and education is judged by the use of language, spelling, grammar and message clarity. Do not use all caps in a sentence. It can be interpreted as a person shouting. Do not spam or contribute to worthless information or rumors.
Last but not least, always respect others people’s privacy. The rule of thumb is if you wouldn’t do it in real life, don’t do it online. Be a good netizen, use netiquette to increase online presence by maintaining good online relationship with others and building a positive reputation.

Source: www.keepcalmandposters.com
0 notes