#AntiSpyWare for Computer
Explore tagged Tumblr posts
Text
please also use "Shut up Win10+11" to customize a huge list of settings that can turn off all sorts of fishy bullshit windows likes to spring on you. you'll have to re-run it after system updates, but you can save and export/import your SUW10 settings so it won't be that bad.
LINK
A boy can dream, can't he?
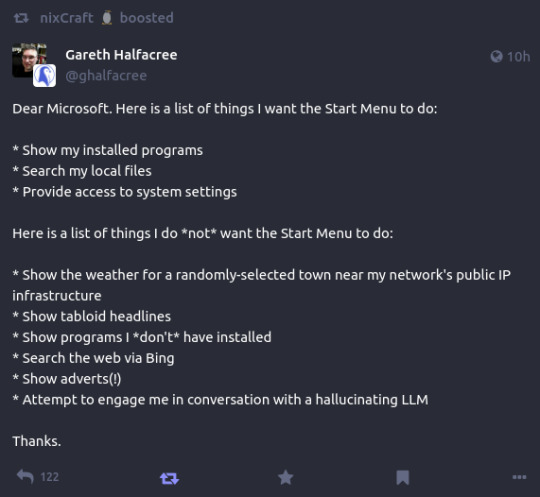
175K notes
·
View notes
Link
[ad_1] The top 10 spyware list describes the most common spyware threats behind famous spyware attacks and is frequently identified by leading antispyware tools from vendors like Webroot, Norton and Malwarebytes. What is spyware? Spyware refers to malicious software purposely designed to access a computer and record its activity. Spyware can track and record a user's browsing habits, login credentials, passwords and more. The spyware author uses the information obtained in this data breach to engage in fraudulent activity or might sell it to a third party. [embed]https://www.youtube.com/watch?v=ZgXw3WCNXc8[/embed] Spyware often spreads through phishing emails, malicious downloads, fake apps or compromised websites. Once installed, it can run in the background logging keystrokes, capturing screenshots or transmitting sensitive data. Adware, keyword loggers, Trojans and mobile spyware are common forms of spyware. Visit our spyware feature page to learn more about this problem and how to beat it. The top 10 spyware threats Some of the top spyware threats organizations face today, according to security experts, include the following: 1. Advanced Keylogger Advanced Keylogger, a keystroke logger, monitors keystrokes and takes screenshots. 2. CoolWebSearch (CWS) CoolWebSearch (CWS) is a software suite originally used to exploit vulnerabilities in Internet Explorer (IE), which Microsoft officially retired in 2022. Though now considered outdated, CWS remains historically significant as one of the earliest, most aggressive examples of browser hijackers. It could rewrite search engine results, redirect DNS lookups and change browser settings to push users toward ad-laden pages. 3. FinSpy (aka FinFisher) FinSpy, or FinFisher, is an advanced suite of surveillance tools sold to law enforcement and intelligence agencies. FinSpy works on Windows, macOS, Linux, Android and iOS operating systems. Its capabilities vary depending on the platform. Law enforcement, intelligence agencies and threat actors often use FinSpy to secretly turn on microphones to record conversations, switch on cameras, record and transmit images, transmit key logs in real time, modify files and more. 4. Gator (GAIN) Gator is a type of adware that can display banner advertisements based on a user's web surfing habits. Gator is often bundled with numerous free software programs and pirated applications. Gator monitors online user behavior and targets them with personalized ads. 5. GO Keyboard GO Keyboard was a virtual Android keyboard app that masqueraded as a legitimate mobile application. It was found to transmit personal information to its remote servers without explicit user consent, violating Google Play policies. The app was eventually removed from the Google Play Store, but it serves as a cautionary example of the risks posed by third-party keyboard apps. Information shared by GO Keyboard spyware included the following: Android OS version. Device model and screen size. Google account email address. International Mobile Subscriber Identity (IMSI). Location. Network type. Preferred language. Social media interactions. GO Keyboard executes code from a remote server to breach Google Play privacy policies. 6. HawkEye HawkEye, a keylogger virus, was dormant for years but resurfaced during the COVID-19 pandemic. It infects machines to track key logs and other inputs, sharing that information with a remote server. New versions are increasingly difficult to detect due to enhanced anti-detection features. One campaign impersonated the World Health Organization in a social engineering attack designed to trick users into downloading a malicious attachment. 7. HuntBar HuntBar is a Trojan application that hijacks web browser settings and downloads and installs adware without the user's knowledge. Also known as Adware, Websearch or WinTools, HuntBar tracks browsing behavior, redirects web traffic to affiliate websites, forcefully displays advertisements and installs more spyware programs and toolbars on IE. 8. Look2Me Look2Me is spyware that tracks user behavior, website logs and social media interactions and shares this information with a remote server. The information is then used to show intrusive advertisements. Look2Me spyware also downloads and installs various add-ons, extensions, toolbars and other unwanted programs on a user's computer. This makes the spyware threat more dangerous than traditional adware. Removing Look2Me is difficult because of its rootkit-type functionality. 9. Pegasus NSO Group's Pegasus spyware is one of the latest spyware threats making headlines. Although Pegasus was initially developed to fight terrorism, evidence suggests that many clients use Pegasus to spy on journalists, political activists, political opponents and almost anyone the client desires. The governments in France, Hungary, India, Saudi Arabia, United Arab Emirates, the United Kingdom and the United States are known to have used Pegasus spyware. 10. PhoneSpy PhoneSpy is an example of a spyware virus that pretends to be a mobile application to gain access to and infect Android mobile devices. This approach allows threat actors to remotely control mobile devices and steal data. Mobile applications with PhoneSpy aren't available on Google Play Store, so it's believed to spread through social engineering attacks and third-party platforms. Emerging mobile spyware threats As mobile device usage continues to rise, threat actors have increasingly turned to smartphones as high-value targets. Here are a few of the most concerning mobile spyware threats discovered in recent years: Hermit Hermit is a powerful mobile spyware tool designed to infect both Android and iOS devices. Typically delivered via fake mobile carrier apps or malicious links in SMS messages, Hermit can record audio, track location, intercept texts and access contact lists. It has been linked to state-sponsored surveillance campaigns targeting journalists and political figures. SpyNote SpyNote is a remote access trojan (RAT) that targets Android users. Once installed, it allows attackers to record audio, access text messages and call logs, and even activate the device's camera without user consent. SpyNote is often disguised as a legitimate app and distributed through unofficial app stores or phishing links. Anatsa (also known as TeaBot) Anatsa is a banking Trojan with spyware-like capabilities. It has been known to steal login credentials by capturing keystrokes and recording screen activity on Android devices. Anatsa spreads through fake app downloads posing as QR code readers, PDF viewers or security apps. How to protect yourself from spyware Spyware can be difficult to detect until it's already compromised your device. Here are simple best practices to help reduce the risk of infection: Use reputable antivirus and antispyware software and keep it up to date. Avoid downloading apps or files from untrusted sources, especially third-party websites. Enable automatic software updates on your devices to patch known vulnerabilities. Use strong, unique passwords and turn on two-factor authentication (2FA) for sensitive accounts. Be cautious of phishing emails and attachments, especially those with urgent or alarming messages. Review app permissions before installing, particularly for mobile apps that request access to contacts, location or cameras. Two-factor authentication is a good form of spyware protection. Staying alert and maintaining good digital hygiene can significantly lower your risk of falling victim to spyware. FAQs about spyware threats Can spyware infect mobile devices?Yes. Spyware is increasingly targeting mobile devices through fake apps, malicious links and phishing messages. Android devices are especially vulnerable when apps are downloaded from third-party sources. What is the most dangerous spyware in 2025?Pegasus remains one of the most sophisticated spyware tools in use. However, newer threats like Hermit and Anatsa are also highly capable and dangerous, especially on mobile platforms. How do I know if my device has spyware?Common signs include unexpected battery drain, overheating, slow performance, unknown apps appearing, and unusual network activity. If you suspect spyware, run a trusted mobile security scan and review app permissions. Is Pegasus spyware still active?Yes. While originally marketed for counterterrorism, Pegasus has been used by various governments and entities for broader surveillance. It remains a high-profile threat and continues to evolve. Learn more on how to prevent spyware through best practices, including using a layered defense or content filtering. See how to protect against malware as a service. Also, protecting your endpoints is critical for maintaining security. Learn why endpoint detection and response technologies are essential for endpoint protection. Explore how to protect, detect and remove malware from mobile devices. [ad_2] Source link
0 notes
Text
Laptops are portable and convenient, and you can do much with them. They allow you to surf the internet, write documents, listen to your favorite music, watch movies, or even play games. Unfortunately, regardless of how gently you try to handle your laptop, it’s bound to get some problems in the long run. But the good news is that most common laptop issues can be easily solved through DIY laptop repairs. Here are some of the most common problems related to laptops and their simple solutions. Blue Screen Errors The blue screen error, also known as the blue screen death, is among the most frustrating issues on windows laptops. The error can be caused by several things, which may be related to either hardware or software. You might be able to restart the computer sometimes, but in some cases, you may not. If your laptop can start back into windows, perform a quick scan for viruses using Microsoft AntiSpyware (commonly known as Windows Defender) or any other antivirus software installed on your computer. Ensure the antivirus is up to date before you run the scan. When that doesn’t solve the problem, check for faulty drivers and update them. To do this, go into the device manager. If you notice any yellow exclamation beside any hardware components, update the driver by just right-clicking on it and selecting ‘update driver software.’ The Laptop Battery Doesn't Last for Long One of the best features of a laptop is that it can be run by a battery. However, after a lifetime and regular use, the lithium-ion batteries may lose the ability to hold a charge, while some will only last for a fraction of the rated time. In such a case, battery replacement might be the best solution. Most brands charge a lot for new batteries, so you may need to look for computer repair experts since they will offer you a new battery at a lower price. If you are a Lenovo user, search for Lenovo laptop repair near me to find a quick repair or replacement for your laptop battery. Broken screen or no display One of the most common laptop issues is a broken screen or no display. A cracked screen may be caused by physical damage after dropping the laptop or dropping something on it. Other problems that can cause a laptop computer screen to malfunction or appear broken include: Malfunctioning backlight Screen burn Problems with cables or connectors Outdated driver Stuck pixels If your laptop displays a black screen or no picture when you turn it on, it’s always best to try some fixes before paying for a costly repair. The screen appearing not to work might be caused by an operating system problem or some other conflicts which can be removed by simply restarting your laptop. Restarting is straightforward, so it should be the first thing to try. If you are skilled with disassembling computers, you can remove the faceplate around the screen, flip covers, or any other case component to uncover the screen, backlight wire, and connectors. Check your screen and backlight connections and ensure everything is properly secured and the cables are not broken or crimped. If none of these fixes works, your screen probably needs to be replaced. Laptop screens with large or colored lines, black holes, or colors that seem to shake are usually beyond repair. A Laptop Not Turning On Another common laptop issue is a complete failure of the device to turn on, which can leave you without access to your crucial programs and files. If your laptop looks dead and doesn’t light up or make any sound, there are a few possible causes and fixes. First, ensure your laptop is fully charged. However, if you believe it has been charged, your AC adapter may have failed. Use a voltmeter to test your AC adapter or test a new adapter. If your AC adapter is working, the DC jack might have failed, preventing power from reaching your computer, or the issue is with your motherboard. Overheating Overheating is another common problem for nearly any kind of laptop, especially the ones older than five years.
The problem can cause a decline in your laptop’s performance, leading to system crashes or freezes. Every computer typically generates a considerable amount of heat while working, but laptops are especially bound to overheat because of their small sizes and lack of ventilation. Overheating may also be caused by excessive dust that clogs the air vent, blocking your system from getting cold air to cool down. The best way to alleviate the overheating problem is to use the laptop on hard, cool surfaces. Never use your laptop on the bed or your lap since this can block the fan and cause the system to overheat. In addition, you can spring clean your laptop to make it run faster and live longer. Bad Keyboard Keyboards tend to stop working due to prolonged use or when you spill water or hot coffee. As a result, keys can usually get dislodged or worn out. Fortunately, most laptop manufacturers offer simple online guides for keyboard replacements on their client support or help pages. You can search for “keyboard replacement” through the search bar to get some guides for a keyboard replacement. No Internet Laptops are infamous for losing internet connection, causing frequent time-outs while browsing, which can be a great hassle. Before assuming some equipment failures are causing the problem, try out some basic steps. Most laptops have an actual wireless button or switch to activate the internet connection. Find the button and ensure it is in the ON position. After that, reboot your router by disconnecting it, allowing the juice to drain out for 10 to 20 seconds, and then re-plug it. If the problem continues, use the control panel or networking troubleshooting tools to diagnose and troubleshoot your network. Finally, re-create your network once again to ensure all your connections are set up correctly. Endnote Several simple steps can often help you fix some of the most common laptop problems. However, there are some significant issues that you may not be able to solve by yourself. If you try any DIY fixes and still experience the same problem, it’s time to look for a laptop repair professional.
0 notes
Text
systems face the exposure to a number of threats that can cause serious damages leading to huge financial losses. Information security damages can lead to significant information system destruction. Various threats could attack an information system, including virus threats that alter the way a computer operates without the consent of the user Straub. In addition, there is the spyware threat, a program that monitors an individual’s online activity or installs programs without their knowledge, to access the user’s personal information (Straub, 2008). Moreover, there are hackers who victimize other people for their own benefit of breaking into computer systems to destroy or steal information in the form of cyber-terrorism. Lastly, there is the spyware, adware, and Trojans, usually installed with other programs without the users consent. They monitor an individual’s behavior on the internet, display targeted advertisements, and even download other malicious software onto a computer. It is the every responsibility of individuals to protect their own information. I play my role in ensuring information security through keeping it safe in backup devices. I secure the information from the system by the use of safe browsing practices. This occurs through an evaluation of the browser’s security settings before making any online transactions. In addition, I am keen when using email attachments, using safely the instant messaging and chat rooms. To improve information security I will install antivirus and antispyware software program and make sure they are up to date for the protection against any attacks. Furthermore, I will disable non-essential software’s from the computer as they increase the opportunities for attack. In conclusion, I will ensure the use of strong passwords to prevent unauthorized access to information. ReferenceStraub, D. (2008). Information security policy, processes, and practices. Armonk, N.Y.: M.E. Sharpe. Read the full article
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description ESET NOD32 Antivirus I Essential antivirus protection ESET I PROGRESS. PROTECTED When technology enables progress, ESET is here to protect it We are a global digital security company, protecting millions of customers and thousands of companies worldwide. Privately owned, ESET is still run by the same engineers who started the company three decades ago. Maintaining our independence allows us to focus on our primary goal - protecting customers and businesses towards a better future. As we are a cybersecurity company, our values come naturally: integrity, reliability, passion and courage. One of the world’s best antivirus Made in Europe. Protects more than 110+ million users worldwide secure their computers and devices Support across 200+ countries and territories worldwide Over 30+ years of innovation, build and run by security specialists Trusted by some of the biggest companies in the world. Highly regarded by partners and independent analysts. ESET makes the only product ever to win 100 VB100s. ESET NOD32 Antivirus I Essential antivirus protection Antivirus and Antispyware Provides proactive protection against all types of online and offline threats and prevents malware spreading to other users. Anti-Phishing Protects your privacy and assets against attempts by fraudulent websites to acquire sensitive information such as usernames, passwords or banking details, or feed you fake news from seemingly reputable sources. Gamer Mode Automatically switches to silent mode if any program is run in full-screen. System updates and notifications are postponed to save resources for gaming, video, photos or presentations. Ransomware Shield Blocks malware that tries to lock you out of your personal data in order to demand a ‘ransom’ payment. Advanced Machine Learning It is specifically designed to detect advanced, never-before-seen malware, while having a low impact on performance. Cloud-Powered Scanning Speeds up scans by whitelisting safe files based on the ESET LiveGrid file reputation database Device Control Allows you to prevent unauthorized copying of your private data to an external device. Allows you to block storage media – CDs, DVDs, USB sticks, and disk storage devices. Lets you block devices connecting via Bluetooth, FireWire and serial/parallel ports. Advanced Memory Scanner Enables improved detection of persistent malware that employs multiple layers of encryption to conceal its activity. Exploit Blocker Blocks attacks specifically designed to evade antivirus detection, and eliminates lock screens and ransomware. Protects against attacks on web browsers, PDF readers and other applications, including Java-based software. UEFI Scanner Protects from threats that attack your computer on a deeper level, even before Windows starts - on systems with the UEFI system interface. Small System Footprint Maintains high performance and extends the lifetime of hardware. Fits any type of system environment. Saves internet bandwidth with extremely small update packages.
Secure your data and money against digital fraud Protect your privacy and assets against attempts by fraudulent websites to acquire sensitive information, such as usernames, passwords or banking details. Enjoy the full power of your computer without interruptions Play, work and browse the internet without affecting your computer’s performance. Stay unplugged and online longer with battery- saving mode. Explore the digital world, safe from all types of malware threats Detects and neutralises all digital threats, including viruses, ransomware, rootkits, worms and spyware, as well as techniques that seek to evade detection. ESET NOD32 Antivirus Built for everyday users, with the legendary ESET NOD32 engine at its core, ESET NOD32 Antivirus provides essential defense against malware. Along with ESET’s award-winning antivirus and antispyware, it offers Gamer Mode that saves resources for uninterrupted gaming and videos, and includes a personal monthly Security Report. Its Exploit Blocker feature is designed to detect and defeat ransomware and lock screen attacks. Like all ESET products, ESET NOD32 Antivirus protects your device with our UEFI Scanner and Advanced Machine Learning, while the ESET HOME portal and app provide comprehensive oversight of your ESET products, licenses and services. Powerful technology... sophisticated behavior 1 billion+ protected internet users 13 global Research & Development centers 600+ R&D experts behind our technology 30+ years of tech know-how Speed - Built to keep you running fast, with no interruptions. Detection - Blocks and eliminates even the most advanced threats. Usability - Provides set and forget protection you can install in minutes. Technical Details OS Windows 8.1, Windows 8, Windows 7, Windows 10 Architecture 32/64 Bit System requirements Microsoft Windows 10, 8.1, 8, 7 with SP1 and latest KB updates installed Manufacturer Amity Infosoft Pvt Ltd Country of Origin India Imported By Amity Infosoft Pvt Ltd Code will be mailed to the Amazon registered email ID within 2 hours of ordering or check 'Buyer/Seller messages' under Message Center at "amazon.in/msg" Antivirus; Antispyware; Anti-Phishing, License manager; Security Report Advance Machine Learning; Device Control, Ransomeware shield; Script-Based Attack Protection, Exploit Blocker; UEFI Scanner Within 2 hours of ordering, registration link and configuration instructions will be available in 'Buyer/Seller messages' under Message Center at "amazon.in/msg" and your Amazon regd. email ID Software activation code along with download instructions will be delivered in an e-mail. If your account does not have an email ID on amazon, Please register the same before purchasing This software works on devices with India IP addresses only [ad_2]
0 notes
Text
does a vpn secure against keyloggers
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
does a vpn secure against keyloggers
Funktionsweise eines VPN
Ein VPN, oder Virtual Private Network, ist ein Dienst, der Ihre Internetverbindung verschlüsselt und Ihren Datenverkehr über speziell konfigurierte Server umleitet. Dies bietet mehrere Vorteile, einschließlich erhöhter Privatsphäre, Sicherheit und Anonymität beim Surfen im Internet.
Die Funktionsweise eines VPN ist relativ einfach. Wenn Sie eine Verbindung zu einem VPN-Server herstellen, wird eine sichere und verschlüsselte Verbindung zwischen Ihrem Gerät und dem Server hergestellt. Dadurch wird verhindert, dass Dritte Ihren Datenverkehr ausspionieren oder auf Ihre persönlichen Informationen zugreifen können.
Ein weiterer wichtiger Aspekt der Funktionsweise eines VPN ist die Möglichkeit, Ihre virtuelle Position zu ändern. Indem Sie sich mit einem Server in einem anderen Land verbinden, können Sie auf geografisch eingeschränkte Inhalte zugreifen, als wären Sie physisch in diesem Land.
Zusammenfassend lässt sich sagen, dass ein VPN Ihre Daten schützt, Ihre Privatsphäre wahrt und Ihnen ermöglicht, frei und sicher im Internet zu surfen. Es ist besonders nützlich für diejenigen, die viel unterwegs sind und öffentliche WLAN-Netzwerke nutzen, da es Ihnen eine zusätzliche Sicherheitsschicht bietet.
Schutz vor Keyloggern
Keylogger sind gefährliche Schadprogramme, die insgeheim auf einem Computer installiert werden und alle Tastatureingaben des Nutzers aufzeichnen. Dies kann dazu führen, dass sensible Informationen wie Passwörter, Kreditkartendaten oder andere persönliche Daten gestohlen werden. Der Schutz vor Keyloggern ist daher von großer Bedeutung, um die Privatsphäre und Sicherheit der Nutzer zu gewährleisten.
Es gibt verschiedene Maßnahmen, die ergriffen werden können, um sich vor Keyloggern zu schützen. Eine effektive Methode ist die Verwendung von Antiviren- und Antispyware-Programmen, die regelmäßig auf den neuesten Stand gebracht werden sollten. Diese Programme können helfen, Keylogger zu erkennen und zu entfernen, bevor sie Schaden anrichten können.
Zusätzlich ist es ratsam, sich bewusst zu sein, welche Websites besucht und welche Programme heruntergeladen werden. Vorsicht ist geboten bei verdächtigen Links oder Anhängen in E-Mails, die möglicherweise Keylogger enthalten könnten. Es ist wichtig, nur aus vertrauenswürdigen Quellen zu downloaden und auf sichere Passwort-Praktiken zu achten.
Eine weitere Möglichkeit, sich vor Keyloggern zu schützen, ist die Verwendung von virtuellen Tastaturen. Diese virtuellen Tastaturen zeigen das Tastaturlayout auf dem Bildschirm an und ermöglichen es dem Nutzer, durch Klicken mit der Maus oder das Tippen mit dem Touchscreen Eingaben zu machen, anstatt die physische Tastatur zu benutzen.
Durch die Umsetzung dieser Schutzmaßnahmen können Nutzer Ihre Daten besser sichern und das Risiko von Keyloggern minimieren. Es ist wichtig, sich bewusst zu sein, dass diese Bedrohung existiert und entsprechende Vorkehrungen zu treffen, um sich davor zu schützen.
Virtuelles privates Netzwerk
Ein virtuelles privates Netzwerk, auch bekannt als VPN, ist ein äußerst nützliches Tool, um Ihre Online-Privatsphäre und Sicherheit zu schützen. Ein VPN ermöglicht es Ihnen, über das Internet eine sichere Verbindung zu einem entfernten Server herzustellen. Dadurch wird Ihre IP-Adresse verborgen und Ihre Online-Aktivitäten werden verschlüsselt. Dies bedeutet, dass Dritte nicht in der Lage sind, Ihre Daten abzufangen oder Ihre Internetnutzung zu verfolgen.
Es gibt viele Gründe, warum Menschen ein VPN nutzen. Zum einen kann ein VPN dabei helfen, geografische Beschränkungen zu umgehen, indem es Ihnen erlaubt, auf regional gesperrte Inhalte zuzugreifen. Darüber hinaus schützt ein VPN Ihre sensiblen Daten, wie zum Beispiel Passwörter, Kreditkarteninformationen und persönliche Chats, vor Hackern und anderen Cyberbedrohungen.
Ein weiterer Vorteil eines VPNs ist die Möglichkeit, öffentliche WLAN-Netzwerke sicher zu nutzen. Da diese Netzwerke oft ungesichert sind, sind sie anfällig für Hackerangriffe. Mit einem VPN können Sie jedoch sicher im Internet surfen, auch wenn Sie mit einem öffentlichen WLAN verbunden sind.
Es ist wichtig, ein vertrauenswürdiges VPN auszuwählen, da einige Anbieter möglicherweise Ihre Daten sammeln und weiterverkaufen. Achten Sie darauf, dass das VPN Ihrer Wahl über eine starke Verschlüsselung, eine strikte Datenschutzrichtlinie und eine Vielzahl von Serverstandorten verfügt.
Zusammenfassend ist ein virtuelles privates Netzwerk ein unverzichtbares Werkzeug, um Ihre Online-Privatsphäre zu schützen und Ihre Sicherheit im Internet zu gewährleisten. Wenn Sie Ihre Daten und Identität schützen möchten, sollten Sie in Betracht ziehen, ein VPN zu nutzen.
Datensicherheit
Datensicherheit ist ein äußerst wichtiger Aspekt in der heutigen digitalen Welt. Unternehmen und Einzelpersonen müssen sicherstellen, dass ihre sensiblen Daten vor unbefugtem Zugriff geschützt sind. Datensicherheit bezieht sich auf die Praktiken und Technologien, die eingesetzt werden, um die Vertraulichkeit, Integrität und Verfügbarkeit von Daten zu gewährleisten.
Eine der grundlegenden Maßnahmen zur Datensicherheit ist die Verschlüsselung. Durch die Verschlüsselung werden Daten in einen nicht lesbaren Code umgewandelt, der nur mit einem speziellen Schlüssel entschlüsselt werden kann. Dadurch wird sichergestellt, dass selbst wenn Daten abgefangen werden, sie nicht ohne Autorisierung gelesen werden können.
Ein weiteres wichtiges Konzept in der Datensicherheit ist die Zugriffskontrolle. Unternehmen müssen sicherstellen, dass nur autorisierte Personen auf bestimmte Daten zugreifen können. Dies wird durch die Vergabe von Berechtigungen und die Implementierung von Zugriffskontrollrichtlinien erreicht.
Zusätzlich zur Verschlüsselung und Zugriffskontrolle ist es wichtig, regelmäßige Backups durchzuführen. Auf diese Weise können Daten im Falle eines Hacks oder eines Datenverlusts wiederhergestellt werden.
Insgesamt ist Datensicherheit entscheidend, um das Vertrauen von Kunden und Partnern zu wahren und rechtliche Anforderungen zum Schutz von Daten einzuhalten. Unternehmen sollten daher in angemessene Sicherheitsmaßnahmen investieren und regelmäßig ihre Sicherheitsrichtlinien überprüfen und aktualisieren.
Abwehr von Cyberbedrohungen
Die Abwehr von Cyberbedrohungen ist heutzutage von entscheidender Bedeutung, da die digitale Welt immer komplexer wird und Cyberkriminelle immer raffinierter vorgehen. Unternehmen und Organisationen müssen sich aktiv gegen diese Bedrohungen wappnen, um ihre sensiblen Daten zu schützen und mögliche finanzielle Schäden zu vermeiden.
Es gibt verschiedene Arten von Cyberbedrohungen, wie z.B. Malware, Phishing, DDoS-Angriffe und Ransomware. Um sich effektiv dagegen zu schützen, ist es wichtig, präventive Maßnahmen zu ergreifen. Dazu gehören beispielsweise die regelmäßige Aktualisierung von Software und Betriebssystemen, die Schulung von Mitarbeitern im Umgang mit verdächtigen E-Mails und Links sowie die Implementierung von Firewalls und Antivirus-Programmen.
Ein weiterer wichtiger Aspekt der Abwehr von Cyberbedrohungen ist das Monitoring und die Analyse des Datenverkehrs. Durch die Überwachung des Netzwerkverkehrs können verdächtige Aktivitäten frühzeitig erkannt und entsprechende Gegenmaßnahmen ergriffen werden, um einen möglichen Cyberangriff abzuwehren.
Zusätzlich ist es ratsam, ein Incident Response Team zu etablieren, das im Falle eines Cyberangriffs schnell und effektiv reagieren kann. Dieses Team sollte klare Zuständigkeiten und Handlungsabläufe festlegen, um die Auswirkungen eines Angriffs zu minimieren und den Betrieb möglichst reibungslos aufrechtzuerhalten.
Insgesamt ist die Abwehr von Cyberbedrohungen eine komplexe Herausforderung, die ein proaktives und ganzheitliches Sicherheitskonzept erfordert. Indem Unternehmen und Organisationen angemessene Sicherheitsmaßnahmen implementieren und kontinuierlich aktualisieren, können sie ihre IT-Infrastruktur effektiv schützen und Cyberangriffen erfolgreich entgegenwirken.
0 notes
Text
Embedded Security Market Outlook: Trends and Projections for 2028
The embedded security market size has been estimated to be valued at USD 7.4 Billion in 2023 and is projected to reach USD 9.8 Billion by 2028; growing at a CAGR of 5.7% from 2023 to 2028.
The key factors contributing to the growth of the embedded security market include the rising prevalence of interconnected devices, coupled with the escalating complexity of cyberattacks, underscores the urgency for heightened security measures. Additionally, the imperative to adhere to regulatory mandates is exerting a pivotal role in steering the market’s growth trajectory.
The key players in this market are Infineon (Germany), STMicroelectronics (Switzerland), NXP (Netherlands), Qualcomm (US), Thales Group (France), Microchip Technology (US), Samsung (South Korea), Texas Instruments (US), IDEMIA (France), and Renesas (Japan). The players in this market have adopted various strategies to expand their global presence and increase their market shares.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=63839062
Wearables are likely to witness the highest CAGR among all application segments between 2023 and 2028.
The wearables segment is expected to witness the highest growth rate during the forecast period. Wearables often contain sensitive health, financial, and personal information, necessitating advanced embedded security solutions to prevent unauthorized access and data breaches. This heightened concern for user privacy and data integrity has prompted manufacturers to prioritize security features, including biometric authentication, secure data transmission, and encryption, fostering greater consumer trust and adoption. Moreover, the increasing integration of wearables in healthcare, finance, and enterprise sectors further underscores the need for stringent security protocols, thus propelling their growth within the embedded security market.
Based on the offering, software segment likely to register a higher growth rate in the overall embedded security system market from 2023 to 2028
The software security market is expected to offer lucrative growth opportunities during the forecast period. Commonly used software security are firewall, antivirus, antispyware, and network security. A firewall stops unauthorized users from gaining access to a computer or network. Both hardware and software can be used to create a firewall. Antivirus software prevents dangerous malware from attacking a computer by detecting the attack before it starts. Antivirus software is beneficial because it tackles security concerns when attackers get past a firewall.
North America likely to account for the second-largest market share by 2028.
North America has a wealth of highly sensitive data, and with billions of devices connected to IoT, security is a major concern in the region. Security has been identified as the most severe economic and national security challenge by the government of this region. The growing concern for protecting critical infrastructure and sensitive data has increased government intervention in recent years. Specific budget allocations and mandated security policies are expected to make North America the most lucrative market for different categories of vendors. Other factors pushing the market growth in this region are the enormous usage of smart handheld devices, rapidly growing e-commerce, and friction among competing nations, which includes countries such as the US and Canada.
0 notes
Text
How to Protect Your Computer From Viruses and Malware
Computers are one of the most incredible technologies we use every day of our lives. But, unfortunately, they're prone to viruses and malware that could damage our files and steal our personal information, such as banking details and social security information. Secure your company's data with the assistance of Managed IT Security Los Angeles professionals.
This blog outlines five simple steps that you can use to help protect your computer from viruses and malware.
Following these steps can keep your computer safe from malicious attacks.

Install an Antivirus
One of the best ways to protect your computer is to install an antivirus program. Choose one that includes features like real-time protection and automatic updates. Use common sense when online. For example, don't open email attachments you don't know or trust, and be careful about what you share online.
Don't click on links within emails
It is always important to be cautious when it comes to email. Make sure you back up your computer regularly and never open attachments from unknown sources. Also, be careful of what you search for online, as internet viruses are rising these days.
Use a Strong Password
Viruses and malware are on the rise, and they can do damage to your computer. To protect yourself:
Make sure you use a strong password that is at least eight characters long and contains a mix of letters, numbers, and symbols.
Make sure you use different passwords for different accounts - you don't want to have to remember one password that services all your online activities.
Keep your password stored in a secure location like a locked cabinet or file cabinet.
With these simple steps, you can safeguard your computer from viruses and malware.
Backup Your Computer
It's essential to take precautions to protect your computer from viruses and malware. By following these five simple steps, you'll be one step closer to safeguarding your computer from harm.
1. Back up your computer every day to keep your data safe.
2. Make sure the backup is stored safely, like a fireproof cabinet or online storage service.
3. Keep your computer clean and free of viruses and malware by regularly cleaning it.
4. Install antivirus software to help fight off malicious attacks.
Use stronger authentication
One of the simplest ways to protect your computer is to use a solid authentication when uninstalling antivirus or antispyware programs. This will help ensure that malicious software isn't installed on your computer in the first place. In addition to strong authentication, it's also essential to use an authenticator app when logging into sensitive information such as email accounts or online banking profiles. By doing so, you'll be able to safeguard your data from being accessed by unauthorized individuals. Furthermore, make sure you keep your computer clean - removing spyware and viruses regularly will help guard against nasty malware infiltrations in the future.
Conclusion
As computer security has become an important issue, it is essential to learn how to protect your computer from viruses and malware. By following the five simple steps outlined in this blog, you will be well on your way to safeguarding your computer from potential harm. Make sure to install an antivirus and keep your software up to date, as these are the most effective ways of protecting your computer.
1 note
·
View note
Link
Following points make SUPERAntiSpyware is an excellent security application.
An advanced security application that excludes malicious spyware which your anti-virus program may miss. Identifies and eliminates rogue antiviruses, malware, Trojans, rootkits, and helps protect your personal information from identity-stealing spyware. It’s designed to work collectively with existing anti-virus and/or anti-malware software to provide a layered approach to security for extra protection.
1 note
·
View note
Link
First Close All Open computer Program and application.
Go to the Windows Start Menu > Control Panel.
Choose the Open Programs / Uninstall a program Option.
In the list of All installed application Program find SUPERAntiSpyware.
Select the SUPERAntiSpyware and Top upper menu to choose the Uninstall Option. OR
Right Click on this Selected program and Click on uninstall.
0 notes
Text
With an increasing use of the internet for communication, business and pleasure throughout the world, an anti-virus software package has become an integral part of computer software in any electronic device used for online access. Although the concept of internet security was unknown during the 1980s, the status changed with the introduction of Morris Worm, the first known large-scale virus attack throughout the network. With a continuous increase in the online use, the attacks have become commonplace with the unleashing of malware just for fun or to steal personal, financial and confidential information of the users. Every household has many internet connected devices that make them vulnerable to all types of cyber security attacks. Information hackers and criminals are looking for any sensitive information on your device that can be compromised to their benefit. In some cases, it is also used to smash the military defense of the country. To increase the safety of the device and counter their attack, there are many organizations who offer various types of packages such as antivirus, firewalls, antispyware and various combination of this software. A common myth in Mac OS users is that "it does not require antivirus software", however, this has been proven wrong in recent past with dozens of free hacking tools and many successful hacking attacks on Mac users. Therefore a plethora of Mac OS antivirus software has evolved recently. Network Level Protection Software To Stop Virus Attacks These software needs to be installed at a network entry point to protect all devices that can get accessed via same network entry point. Port Blocking Software On Router Port blocking is a common defensive technique to disallow unused ports on your network entry points. Security experts suggest that you must block any traffic from ports that are not being used. This can be easily done via most modern router software. If this is not available already you can achieve this by installing a firewall too. Firewall Software The main focus of firewall software is to analyze the incoming as well as outgoing data packages against a set of pre-determined rules and make a decision whether they should be allowed through the firewall. Today, there are three types of firewalls; namely application layer firewalls, proxy servers, and packet layer filters. Network And Packet Layer Filters Also known as packet filters; these are the most simple firewall that only allows pre-determined format of information packets to cross through firewalls. There are two types of network and packet layer filters - stateful and stateless firewalls. Proxy Servers The main function of the proxy server as the firewall is to inspect and allow incoming packet only for specific applications and block every other request and act as gateway monitor. Application Layer Firewall The main function of this firewall is to inspect every packet for some specific protocols such as browser traffic and FTP. These types of application layer firewall are considered most effective in blocking the spread of Trojans and worms. Web application firewalls, commonly known as WAF are a popular choice in this layer of software. There are some powerful and free options available on this page. Many companies build their own application layer security software for corporate networks, however, this can be an overkill for a home based network. The second type of product in this category is antivirus software. Antivirus Software The main focus of any antivirus software is the identification, prevention, and removal of any malware such as worms, Trojan attacks and viruses from any computer device intended to harm the computer software and database. Malware can be described as malware such as worms, Trojans, spyware, keyloggers, hijackers, backdoors, rootkits, and adware, among others.
The modern anti-virus software programs use various methods for detection and removal of almost all type of malware. Signature-based Detection One of the main methods used for detection of malware includes signature-based detection. Every virus possesses a digital signature or a code that activates its designated function. When anti-virus software is activated, it scans every file on the computer against a virus signature database and cleans it after correct identification. Heuristics Since the anti-virus software cannot protect the computers from new and unknown viruses, the manufacturers have created heuristics algorithm that enables the antivirus software for detection and cleaning of the variants in a short time. Anti-rootkit The antivirus software is also programmed to detect rootkits, a nasty form of malware that has the ability to alter the working of the operating system as well as the antivirus software. To counter its attack, the antivirus software also includes a program to scan the files for this type of malware and clean them. Real-time Protection Almost all antivirus software also provides real-time protection with continuous updates to virus signature database. Antispyware Software There are two types of spyware; the first is an integral part of the software that has been installed by the user in an intentional manner and the other is stealthily installed when a user visits any infected website. Although they are not intrinsically dangerous, they take up a large space of computer processing power and network bandwidth. As a result, the speed of the computer slows down due to its cumulative effect. Not only that, as the spyware sends user’s information to various companies without the user’s consent, it violates their privacy. Like most anti-virus software, the anti-spyware software also provides real-time protection and relies mainly on the updates provided by the spyware company. There are many online only options also available for scanning without installing a heavy weight software. Combination Software Today, most of the leading companies in this field offer a comprehensive package of a firewall, anti-virus software, and anti-spyware package. Not only that, they provide continuous updates through the internet to combat the current crop of malware that is present online. Purchase of Software On The Web eBay It is very easy to purchase any anti-virus software on eBay, all a user needs to do is to visit this website and choose the software which meets the budget and requirement. All he or she has to do is to complete the required payment process and the customer can upload it on his or her computer device. Amazon Amazon is also a popular choice for any popular anti-virus purchase. You can choose from CD or online version of some leading antivirus software. Antivirus Rating System When a buyer needs to purchase anti-virus software, he or she needs to check antivirus rating system available online on various sites. I recommend you to refer at least two independent websites for this. Looking at the company website of software may not give you a clear picture of reviews. Conclusion An essential part of the modern computer and mobile devices, security and antivirus software can be divided into many categories such as firewalls, anti-spyware, root-kit software or anti-virus software. The main function of these security and antivirus software is the protection of computer software and its inherent database from intentional or unintentional malicious attack. Most of the manufacturers of these software packages offer a comprehensive package with a combination of different software that includes anti-virus software, firewall software, root kit software and antispyware software. Not only that, they offer continuous updates for a specific time-period to counter the attack of new virus and malware that abound the world wide web.
Article Updates Article Updated on August 2021. Some HTTP links are updated to HTTPS. Updated broken links with latest URLs. Some minor text updates done. Content validated and updated for relevance in 2021.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description ESET NOD32 Antivirus I Essential antivirus protection ESET I PROGRESS. PROTECTED When technology enables progress, ESET is here to protect it We are a global digital security company, protecting millions of customers and thousands of companies worldwide. Privately owned, ESET is still run by the same engineers who started the company three decades ago. Maintaining our independence allows us to focus on our primary goal - protecting customers and businesses towards a better future. As we are a cybersecurity company, our values come naturally: integrity, reliability, passion and courage.One of the world’s best antivirus Made in Europe.Protects more than 110+ million users worldwide secure their computers and devices Support across 200+ countries and territories worldwideOver 30+ years of innovation, build and run by security specialists Trusted by some of the biggest companies in the world.Highly regarded by partners and independent analysts.ESET makes the only product ever to win 100 VB100s. ESET NOD32 Antivirus I Essential antivirus protection Antivirus and Antispyware Provides proactive protection against all types of online and offline threats and prevents malware spreading to other users. Anti-Phishing Protects your privacy and assets against attempts by fraudulent websites to acquire sensitive information such as usernames, passwords or banking details, or feed you fake news from seemingly reputable sources. Gamer Mode Automatically switches to silent mode if any program is run in full-screen. System updates and notifications are postponed to save resources for gaming, video, photos or presentations. Ransomware Shield Blocks malware that tries to lock you out of your personal data in order to demand a ‘ransom’ payment. Advanced Machine Learning It is specifically designed to detect advanced, never-before-seen malware, while having a low impact on performance. Cloud-Powered Scanning Speeds up scans by whitelisting safe files based on the ESET LiveGrid file reputation database Device Control Allows you to prevent unauthorized copying of your private data to an external device. Allows you to block storage media – CDs, DVDs, USB sticks, and disk storage devices. Lets you block devices connecting via Bluetooth, FireWire and serial/parallel ports. Advanced Memory Scanner Enables improved detection of persistent malware that employs multiple layers of encryption to conceal its activity. Exploit Blocker Blocks attacks specifically designed to evade antivirus detection, and eliminates lock screens and ransomware. Protects against attacks on web browsers, PDF readers and other applications, including Java-based software.
UEFI Scanner Protects from threats that attack your computer on a deeper level, even before Windows starts - on systems with the UEFI system interface. Small System Footprint Maintains high performance and extends the lifetime of hardware. Fits any type of system environment. Saves internet bandwidth with extremely small update packages. Secure your data and money against digital fraud Protect your privacy and assets against attempts by fraudulent websites to acquire sensitive information, such as usernames, passwords or banking details. Enjoy the full power of your computer without interruptions Play, work and browse the internet without affecting your computer’s performance. Stay unplugged and online longer with battery- saving mode. Explore the digital world, safe from all types of malware threats Detects and neutralises all digital threats, including viruses, ransomware, rootkits, worms and spyware, as well as techniques that seek to evade detection. ESET NOD32 Antivirus Built for everyday users, with the legendary ESET NOD32 engine at its core, ESET NOD32 Antivirus provides essential defense against malware. Along with ESET’s award-winning antivirus and antispyware, it offers Gamer Mode that saves resources for uninterrupted gaming and videos, and includes a personal monthly Security Report. Its Exploit Blocker feature is designed to detect and defeat ransomware and lock screen attacks. Like all ESET products, ESET NOD32 Antivirus protects your device with our UEFI Scanner and Advanced Machine Learning, while the ESET HOME portal and app provide comprehensive oversight of your ESET products, licenses and services. Powerful technology... sophisticated behavior 1 billion+ protected internet users13 global Research & Development centers 600+ R&D experts behind our technology 30+ years of tech know-howSpeed - Built to keep you running fast, with no interruptions.Detection - Blocks and eliminates even the most advanced threats.Usability - Provides set and forget protection you can install in minutes. Technical Details OS Windows 8.1, Windows 8, Windows 7, Windows 10 Architecture 32/64 Bit System requirements Microsoft Windows 10, 8.1, 8, 7 with
SP1 and latest KB updates installed Manufacturer Amity Infosoft Pvt Ltd Country of Origin India Imported By Amity Infosoft Pvt Ltd Code will be mailed to the Amazon registered email ID within 2 hours of ordering or check 'Buyer/Seller messages' under Message Center at "amazon.in/msg" Antivirus; Antispyware; Anti-Phishing, License manager; Security Report Advance Machine Learning; Device Control, Ransomeware shield; Script-Based Attack Protection, Exploit Blocker; UEFI Scanner Within 2 hours of ordering, registration link and configuration instructions will be available in 'Buyer/Seller messages' under Message Center at "amazon.in/msg" and your Amazon regd. email ID Software activation code along with download instructions will be delivered in an e-mail. If your account does not have an email ID on amazon, Please register the same before purchasing This software works on devices with India IP addresses only [ad_2]
0 notes
Text
File Sharing & Virus Protection
If you have established any type of home business, you may let your computer do most of the heavy lifting for you. If you really value your business and file sharing (which you will do often as a VA), then you now need a complete computer security program. McAfee is synonymous with computer security. They have been around since we had the Internet, and there may be more. Your Managed VirusScan Plus AntiSpyware performs automatic and silent updates to all important files on your computer, and actively blocks any content that may harm your computer. This is the key first step in protecting yourself. If you want to further strengthen your computer's protection against worms, viruses and other malicious computer code hosts, please purchase a Linksys EtherFast Cable / DSL firewall router. It is very easy to set up and block Java, ActiveX, cookies, and anything else that might attack or take over your computer and its files. For complete security, it is always recommended to back up all files (and client files) after running an antivirus program. We do this at the end of each day. In this way, if your files are re-infected, you will not risk losing important information. We like our SanDisk Cruzer Micro 2GB flash drive. They contain a large number of files and download extremely fast. Who knew that such a small package could provide strong protection? In order to be completely protected from computer viruses, you need a backup plan. After all, when you inadvertently send the virus along with the bill to them, most customers just won't "receive it." Norton Ghost is a must-have program. It makes data backup and recovery a breeze by automatically performing all scans when you turn off your computer at night. Norton Ghost can also quickly and quietly protect you from system failures, which will greatly help build lasting and productive relationships with your customers. In addition, you will sleep better at night because you and your computer are safe and sound.
1 note
·
View note
Text
Computer Hackers Wanted For Organized Cyber Crime
Would you be able to envision an assistance needed advertisement like that in your neighborhood paper or pay-per-click promotion in your #1 web search tool? However, coordinated digital wrongdoing has gotten the most productive - generally safe - exceptional yield wrongdoing of our age. A huge number of hackers are unobtrusively utilizing the Internet, taking cover behind great many caught PCs, taking characters and cash from blameless individuals like you and me. Unfortunately, there is minimal possibility the hacker will at any point get captured. Coordinated digital wrongdoing has become a hotshot calling. Professional hackers make it their every day task to exploit current PC security drifts and convey dangers like Spam, phishing messages, Trojan ponies containing key lumberjacks, ruffians and that's just the beginning, all focused to take your character and eventually your cash. These digital hoodlums can work alone or in gatherings. In any case, their first objective is to catch PCs and transform them into zombies or bots. These are PCs that the hacker controls without the proprietors information. As an ever increasing number of PCs are caught, the hacker fosters an Army of PCs or botnet that can be utilized for quite a few crimes. The botnet may convey Spam messages, and Trojan ponies. A botnet can cause refusal of-administration assaults on sites coercing cash from the site proprietors. This entire time the hacker is taking cover behind a series of PCs under his influence. Following back to the hacker is almost unthinkable.
Hacker Tools For Sale
Anybody can exploit the PC security drifts and become a piece of the coordinated digital wrongdoing world. The secrets to success are all over. You can discover sites that advance the utilization of these devices. What do you need? Here's a halfway rundown of things you can discover on the Internet.
· Remote Access Tools - known as RATs. These devices permit distant admittance to a PC. They were initially produced for white cap hackers to distantly fix PCs. Presently, this is a significant device in a digital criminal's tool stash.
· Key lumberjack Tools - Corporations and even guardians discover these instruments important to keep everybody in line on the Internet. Sadly, hackers have figured out how to utilize these devices to take your private data.
· Video And Audio Systems - Hackers have devices that will enter your PC frameworks and keep a close eye on you through the camera mounted on your PC or mouthpiece that accompanied your PC.
· Voip And Broadband Phone Services - you can undoubtedly discover devices, for example, web dialer worms to break into PCs and tune in to discussions or even dial and utilize the telephone administration. How hard is it for a criminal to put medicate buys or lead fear monger exercises with your PC?
· Computer Memory Storage - hackers can gain devices to partition your PC and store anything they need like kid erotic entertainment, criminal records and that's only the tip of the iceberg.
· Spamming Tools - need to send email out of another person's PC? Simply buy this simple to utilize programming and you can get that going. Hackers send a huge number of Spam messages each day making up more than 90% of all email conveyed around the world.
· Create Your Own Virus - Yes, it's actual. There are many sites offering to transform a current infection to your necessities. Of late, infection assaults have been more focused on. That is the reason you haven't found out about huge infection assaults of late.
· Drive By Spyware - There are some sites that advance that they will pay you to permit them to put a device on your site that puts spyware on each PC that visits the site. The more PCs contaminated the more cash you make.
· Computer Scrambling Devices - you can buy devices that will scramble all or a portion of the data on a PC. Just attack a PC, scramble significant data, leave a message advising the casualty to pay two or three hundred dollars payoff to an abroad record and they will send the code to unscramble the data.
This rundown could continue forever. Coordinated digital wrongdoing utilizes each instrument they can discover or devise to exploit the current PC patterns and improve their dangers.
The feature peruses: Computer Hackers Wanted For Organized Cyber Crime! The sub feature should say, "The overall population is impassive and isn't doing a lot to ensure themselves. The Timing couldn't be better."
Coordinated digital wrongdoing has moved, generally, from focusing on enormous organizations to people and independent company. Hoodlums realize that this focused on bunch has little information on PC security and a modest quantity of cash to put resources into their insurance. They see this gathering as simple prey. Up until this point, they are perfect.
The dismal truth is that the vast majority either don't appear to mind or don't have the foggiest idea what to do. A large portion of those that don't have the foggiest idea what to do don't do anything about it, all things considered. That is the current PC security pattern. Accordingly, coordinated digital wrongdoing and PC security dangers keep on developing at a speeding up pace. More than $67 billion was taken a year ago. More than 8,000,000 characters have been taken each year for quite a long time back.
How Can We Deal with Fight Organized Cyber Crime And Turn These Computer Security Trends Around?
Generally, hoodlums are apathetic. They are searching for the low street - not the more responsible option. Making yourself a hard objective to assault is your first protection against coordinated digital wrongdoing and PC security dangers.
The familiar adage, "information is power," is generally significant. Ensure everybody in your home or business comprehends the dangers and is mindful so as not to permit these on a PC. Be that as it may, even with the best information there can be inadvertent breaks from opening Spam email, drive-by-hacking from a site, downloading tainted cds and then some.
Here are a few hints to ensure your home and business:
· Make sure you stay aware of the most recent generally modern Microsoft Windows patches
· Use a modern evaluation bi-directional firewall. Most over-the-counter and items offered by Internet administrations don't offer this quality innovation
· Make sure you have cutting-edge antivirus insurance
· Make sure you have best-of-breed antispyware security. Antispyware and antiviruses are distinctive PC security dangers and require diverse assurance advancements.
· Avoid sites that may have spyware including betting and sexual entertainment.
The best insurance is utilizing a similar PC security arrangements utilized by significant companies all throughout the planet. An answer that utilizations covering advancements to forestall antiviruses, spyware and other PC security dangers.
Visit us for more.
1 note
·
View note
Link
Windows Add/ Remove Programs allows users a way to uninstall the program and every Operating System has Add/ Remove Programs feature. First Click on Start menu and run Control Panel. Find SUPERAntiSpyware and click on Change/ Remove to uninstall the program. Simply follow the uninstall wizard up to finish uninstalling the program.
0 notes
Text
Antivirus For Computer
In today's technology based world, security of your computer from malicious threats has become a very difficult task. Intruders who have wrong intentions, can access your important information thus stealing your identity and causing harm to your system. It is a must for every computer user to install and update antivirus software with the aim of protecting your system against malicious programs like viruses, malware, spyware and Trojan.
In case antivirus is not up to date then your computer is more vulnerable to these infecting programs. Viruses and its other forms enter your system in many forms without your consent. The computer system gets infected by malicious programs when you browse websites using internet, download any infected software, when you open an infected e-mail message and so. Every time you are connected to internet, your computer is at the risk of being infected by viruses.
The only way to protect your system against the noxious programs is to install updated antivirus software. It offer complete protection to your computer any harmful things. The central role is to check all files to determine the presence of viruses.
Once it is installed on your system, it is very important to regularly update it. Newer is the software installed more it will be able to find the newly discovered viruses and other security threats. You must select a program keeping in mind usage of your computer and internet.
When you are working on internet, malicious objects affect the efficiency of your computer system and slow down its speed and compatibility.
There are certain things that you always need to keep in mind which include running scan at least twice a week. This will allow you to know the current status. Viruses can affect your computer in such a large extent that you might need to format your computer which can cost you a lot. You can lose your important and personal data, if you don't use the backup. All these problems lead to a slow speed of your system and decrease its overall performance.
One needs to be very sure and careful while choosing one so that it is compatible with the configuration of your pc. You can also take suggestions from experts who are available to provide online technical help. You can download some free antispyware like Malware bytes, Spybot, super anti spyware and Trojan remover. These are few security products that you can use to protect your PC.
With the increase of computers in daily life of people, the need of improvising security is also increasing. Software are not enough to protect your computer system as it is estimated that there is over 120,000 computer infections such as viruses, spyware, malware and Trojan. Approximately 90,000,000 Spam and emails are sent out each day by computer users.
You can also avail online support to provide computer protection against security threats. There are a number of companies that are providing antivirus support. These organizations have certified professionals who are capable of troubleshooting any errors that occur in the system because of the viruses. Their support is 24x7 available at e very reasonable cost. These companies provide a range of effective services to resolve virus related issues.
1 note
·
View note