#Distributed Computing Server Assignment Help | Distributed Computing Server Online Help | Distributed Computing Server Homework Help | Distr
Explore tagged Tumblr posts
Text
10 Web Hosting Terms You Should Know Before Building a Website

If you're planning to create a website, understanding web hosting is essential. If you're looking for a website hosting company in Gurgaon, knowing these terms will help you choose the right provider. Web hosting provides the server space and technology needed to make your website accessible on the internet. However, the world of web hosting can be full of technical jargon that might seem confusing at first. To make informed decisions, here are 10 key web hosting terms you should know:
Control Panel A control panel is a user-friendly interface that allows you to manage your server settings without needing extensive technical skills. It simplifies the process of managing your website, offering tools to configure domains, emails, databases, and security settings. Popular control panels include cPanel and Plesk, which let you handle server tasks through a graphical interface rather than typing complex commands.
Bandwidth Limit Bandwidth refers to the amount of data your website can transfer to and from the server each month. Hosting providers, like a Web hosting company in Gurgaon, set a bandwidth limit to ensure resources are distributed fairly among customers. If your site reaches this limit, your hosting provider might slow down access (throttle it) or even temporarily suspend your site until the next billing cycle. Knowing your bandwidth needs can help you choose the right hosting plan.
Managed Hosting Managed hosting is a type of service where the hosting provider handles essential maintenance tasks for you, such as software updates, security monitoring, and backups. This can save time and effort, especially for those who are less experienced with server management. Managed hosting is an excellent option for businesses that want to concentrate on their main activities while entrusting technical tasks to professionals.
IP Address An IP address is a unique set of numbers assigned to each device connected to the internet, including your hosting server. It acts as an identifier, allowing computers to locate and communicate with each other. When you purchase a hosting plan, your server will be assigned an IP address, which you can use to access your website files, manage the server, and set up remote connections.
Uptime Uptime is a measure of the reliability of your hosting service. It represents the percentage of time that the server is online and accessible. Most reliable providers aim for an uptime of 99.9% or higher. A high uptime rate is crucial because frequent downtime can result in lost traffic and frustrated visitors. Some hosts offer an uptime guarantee, promising compensation if their service falls below the agreed uptime rate.
Shared Hosting
It is an affordable hosting option where multiple websites utilize the same server. Since the cost of running the server is divided among all users, shared hosting are generally inexpensive. However, because resources are shared, high traffic on one website can affect the performance of others on the same server. This makes shared hosting ideal for small websites or those just starting.
VPS (Virtual Private Server) A VPS, or Virtual Private Server, provides a more dedicated portion of server resources compared to shared hosting. Although multiple users still share the physical server, each VPS operates independently, with allocated CPU, RAM, and storage. VPS hosting is a good middle-ground option for websites that need more power and customization than shared hosting can provide, but without the higher cost of a dedicated server.
Dedicated Hosting With dedicated hosting, you have an entire server reserved solely for your website. This means you have full control over all resources, including CPU, memory, and storage, without any competition from other users. Dedicated hosting is the most powerful but also the most expensive option. It’s often used by large businesses or websites with high traffic that require top performance and customization.
Disk Spaced
Disk space, or storage space, refers to the amount of space on a server available for storing your website's files, databases, and other content. The two main types of storage drives are HDDs (Hard Disk Drives) and SSDs (Solid State Drives), with SSDs offering faster performance. When choosing a hosting plan, consider the storage needs of your website, especially if you plan to host high-resolution images, videos, or large files.
11. SSL (Secure Sockets Layer) SSL is a security protocol that encrypts data transferred between your website and its visitors, keeping information secure. To activate SSL, you'll need an SSL certificate, which enables HTTPS for your website, signifying a secure connection. This is particularly crucial for websites that manage sensitive data, like login credentials or payment information. Many web hosting providers in Gurgaon now offer SSL certificates as part of their hosting packages
Conclusion Understanding these web hosting terms will help you make better decisions when setting up your website. Choosing the right hosting plan and knowing the features available can save you time, money, and frustration in the long run. Whether you’re just starting with a small website or launching a large-scale project, familiarity with these terms will make the process smoother and more manageable.
If you want to know more about our services, please feel free to contact us at:
Mobile: 08826196688 or 9910248322
Email: [email protected]
Website: www.deltait.co.in
#website hosting company in Gurgaon#Web hosting company in Gurgaon#web hosting providers in Gurgaon#delta web services
2 notes
·
View notes
Text
Understanding Cloud VPS: How It Differs from Traditional VPS Hosting
As online presence has become important, determining which hosting service to choose has become one of the essential business decisions. There are two well-known options: Cloud VPS and Traditional VPS, and each has distinct characteristics and benefits. Understanding their differences can help you choose the hosting solution that has all the features you want for your website. Let us explore the distinction between Cloud VPS and Traditional VPS hosting.

VPS Hosting: The Building Block
Practically, VPS hosting is a reality of virtualization technology, and it includes the segmentation of a physical server into several virtual areas. Each VPS works as stand-alone units, providing users with distinct and reserved assets, greater governance, as well as enhanced security as compared to sharing resources with others (like in shared hosting). This type of unit is perfect for those who want more than shared hosting, but do not wish to have a dedicated server.
Traditional VPS Hosting: What to Expect
An underlying issue with Traditional VPS hosting is that a physical server hosts several distinct virtual servers which are partitions of the single physical server. Individual computational units, such as CPU and memory resource denominating units, are assigned to every partition (virtual server instance) separately.
Benefits of Traditional VPS:
Allocated Resources: Each Virtual Private Server has been allocated dedicated assets alone and hence given room for performance stability.
Steady Environment: All available resources for the servers or applications are set, hence high reliability in performance.
Increased Security: Geo-segmentation of virtual servers result in the captivity of data to determined borders hence more security.
Disadvantages of Traditional VPS:
Potential Growth is Lower: Moving to a new server is often required because scaling specially target resources at taking out the entire current server.
Singe Instance of Trouble: At the incident of some hardware fault on the server all VPS (virtual private servers) instances that were hosted there are affected.
Static Division of Resources: Adjustment on the availability of certain resources at any one time is difficult hence, may cause frustrations in the management of traffic surges.
Cloud VPS Hosting: The Adaptable Approach
Cloud VPS hosting employs a cloud based virtualization technology that allows connection of several servers over a network cloud. Such a structure cultivates flexibility, quick growth and more strength since resources are sourced from several servers rather than one.
Cloud VPS benefits:
Scalable with ease: Resources are completely adjustable and scaling does not involve any upgrades.
Reduced Downtime: The chances of a server going down are drastically reduced because the workload is handled by multiple servers.
Improved Performance Levels: Traffic across servers is balanced to achieve efficiency and a rush is experienced even when the level of activity is busy.
Pay Per Use: The per minute charge system means that costs only increase when the resources increase.
Cloud VPS disadvantages:
Unstable Prices: Servers that bill based on resources consumed means the expense for that month can be somewhat erratic.
Location Issues: This can be a contentious issue due to the fact that all data is kept distributed over many servers in some heavily regulated industries.
Network Dependency: Understandably, the performance of Cloud based VPS is determined by the Internet connection quality; slower networks tend to hamper the speed at which the resources are accessed.
4. Which VPS Option is Right for You?
Choose Traditional VPS if:
You are looking to operate in a more stable and consistent environment.
Your website experiences traffic that is steady and within reasonable limits.
You would like to pay a fixed monthly fee without any variations.
Choose Cloud VPS if:
You are looking for more flexibility and expansion options.
Your site receives fluctuating and irregular visits, or seasonal peaks.
It is essential for your organization to experience high availability and low downtime.
5. Final Thoughts
There are benefits as well as different uses associated with Cloud VPS and Traditional VPS. For example, Cloud VPS offers agility, growth potential, and dependability and is therefore suitable for businesses that are poised for expansion and need to cope with abrupt increases in demand for the products marketed online. On the other hand, Traditional VPS is a great and affordable option for people seeking a certain fixed resource and where variability is not a major factor.
Remember that it is crucial to choose the right type of VPS when starting a website. The difference in performance, online presence, and cost can be widely affected by the host one chooses, making it imperative to adapt the virtual private servers to the needs of the business.
4 notes
·
View notes
Text
Best Ways to Repurpose Your Old Laptops for New Uses

If you have an old laptops collecting dust, you may be wondering what to do with it. Rather than throwing it away, there are numerous creative and practical ways to repurpose old laptops and give them a second life. With the growing popularity of renewed laptops and refurbished laptops, it’s easier than ever to extend the life of aging devices in ways that benefit both you and the environment. Whether it’s turning your device into a media server or donating it for a worthy cause, let’s explore the best ways to repurpose your old laptops for new uses.
1. Turn Your Old Laptop into a Home Media Server
Making a home media server out of an old laptop is one of its most useful conversions. If you have a vast collection of movies, music, or photos, you can store them all on your laptop and stream the content to other devices in your home, such as smart TVs or tablets. By installing software like Plex, your old laptop can serve as a central hub for all your digital entertainment.
2. Use It as a Learning Tool
Old laptops can be perfect for children or students who need a device for basic tasks like writing assignments, conducting research, or attending online classes. While it may no longer handle intensive applications, an old laptop can still perform everyday tasks, making it ideal for educational purposes. You can also install learning programs and educational apps to help enhance learning experiences. Used laptops in India are in high demand for this purpose, especially for students with tight budgets.
3. Create a Backup Device
If your old laptop is still functional, why not turn it into a reliable backup device? Having an extra computer on hand can be helpful in case your main device breaks down. You can install lightweight operating systems such as Linux to give your old laptop a fresh start and use it for emergency tasks like sending emails or completing urgent projects. This is a great way to utilize second-hand laptops that may no longer be your primary machine but still have some life left in them.
4. Refurbish Your Old Laptop for Resale
Before considering disposing of your old laptop, you may want to consider refurbishing it for resale. Many companies and websites like Retechie specialize in selling refurbished laptops inIndia, and it’s a win-win solution for those looking to make a little extra cash. With some minor upgrades such as adding more RAM, replacing a failing hard drive, or cleaning up the system, you can breathe new life into your device and sell it as a renewed laptop to someone else.
5. Donate Your Old Laptop
If you don’t need your old laptop anymore, consider donating it to someone in need. Many charitable organizations accept donations of second-hand laptops and distribute them to students, low-income families, or non-profit organizations. By donating your laptop, you’re not only helping someone gain access to technology but also reducing electronic waste. Websites like Retechie offer a range of refurbished laptops to buyers who are seeking affordable options, and your donation could have a similar impact.
6. Convert Your Laptop into a Security Camera System
Your old laptop can easily be converted into a security camera system for your home or office. With simple, free software like iSpy or Yawcam, your laptop can be used to monitor your property, providing an affordable and convenient way to enhance security. This is an ideal solution for repurposing old laptops that may not have the processing power for heavy-duty tasks but are still capable of running background security programs.
7. Use It as a Personal Cloud Storage System
Using an outdated laptop as a personal cloud storage system is an excellent second use for it. With tools like Nextcloud or ownCloud, you can set up your own private server for storing and accessing files from anywhere in the world. This is particularly useful for businesses or individuals looking for secure, cost-effective cloud storage solutions without relying on third-party providers.
8. Recycle It Responsibly
If your old laptop is beyond repair and can't be repurposed, the best option is to recycle it responsibly. Electronics contain valuable components that can be reused, but they also contain hazardous materials that should not end up in landfills. Many recycling centers and electronic stores offer programs to ensure your laptop is properly disposed of. By recycling, you’re helping reduce the environmental impact of e-waste.
9. Convert your outdated laptop into an electronic picture frame.
An innovative and fun way to repurpose your old laptop is by converting it into a digital photo frame. You can use slideshow software to display your favorite memories and set it up in a prominent spot in your home. This is a great DIY project that gives new life to a device you might have otherwise discarded.
10. Convert Your Laptop into a Retro Video Game Console
Old laptops can be perfect for running classic games or emulators. If you’re a fan of retro gaming, you can install emulators for old gaming systems like NES, SNES, or Sega on your laptop and turn it into a dedicated retro gaming machine. While your old laptop may not handle modern AAA games, it’s more than capable of running older classics.
Conclusion
Repurposing your old laptops is a smart and environmentally friendly way to extend their lifespan. Whether you're transforming it into a media server, refurbishing it for resale, or donating it to someone in need, there are plenty of ways to give your device a new purpose. For those interested in buying refurbished laptops or renewed laptops, platforms like Retechie provide a range of options for those looking for affordable yet reliable technology. So before you consider throwing away your old laptop, think about how you can repurpose it for a new use! Visit Retechie to explore refurbished laptops in India and find out more about how to extend the life of your devices.
#Renewed Laptop#Old Laptop#Old Laptops#Used laptops in India#refurbished laptop#refurbished laptops#renewed laptops#refurbished laptops in India#Second hand laptops#Second hand laptop#Retechie
0 notes
Text
does express vpn program hide ip addresses when downloading torrents
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does express vpn program hide ip addresses when downloading torrents
IP address protection
Internet Protocol (IP) address protection is a critical aspect of online security and privacy. An IP address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves as an identifier for a specific device on a network, enabling data to be transmitted to the correct destination.
Protecting your IP address is essential to safeguard your online activities and personal information. One of the primary reasons for protecting your IP address is to prevent cybercriminals and hackers from accessing your device and stealing sensitive data such as passwords, financial information, and personal details.
There are several methods you can use to protect your IP address. One common approach is using a Virtual Private Network (VPN). A VPN encrypts your internet connection and routes it through a remote server, masking your IP address and making it difficult for third parties to track your online activities.
Another way to protect your IP address is by using a proxy server. A proxy server acts as an intermediary between your device and the internet, hiding your IP address from websites and online services you visit.
It's also important to keep your devices and software up to date with the latest security patches and updates to prevent vulnerabilities that could be exploited by cyber threats.
In conclusion, safeguarding your IP address is essential for maintaining online privacy and security. By using tools like VPNs, proxy servers, and practicing good cybersecurity habits, you can protect your IP address and reduce the risk of falling victim to online threats.
Torrent downloads
Torrent downloads are a popular way to share and download files online. Torrents are small files that contain metadata about the files and folders to be shared and the network locations of trackers. These trackers help coordinate communication between users sharing and downloading the files.
When you download a torrent file and open it in a torrent client, the client connects to the tracker and other users to start downloading the files in small pieces. This peer-to-peer file sharing method allows for faster downloads and more efficient distribution of large files.
One of the main advantages of torrent downloads is the ability to download large files quickly, as the file is broken down into smaller parts that can be downloaded from multiple sources simultaneously. This not only speeds up the download process but also reduces the strain on individual servers as the file is being downloaded from multiple users.
However, it is essential to note that not all torrent downloads are legal. Some files are copyrighted material, and downloading them without permission is illegal in many countries. It is crucial to ensure that you have the right to download and share the files through torrenting.
In conclusion, torrent downloads are a useful and efficient way to share and download files online. By understanding how torrenting works and being mindful of the legality of the files being downloaded, users can make the most of this file-sharing method while staying within the bounds of the law.
Online anonymity
Online anonymity refers to the ability of individuals to conceal their identity when engaging in activities on the internet. It offers users the freedom to express themselves without fear of repercussions or judgment based on their real-life identity. This concept has become increasingly important in today's digital age, where privacy concerns are at the forefront of discussions about online safety and freedom of speech.
One of the primary benefits of online anonymity is the protection it provides against surveillance and tracking. With the proliferation of data collection by governments, corporations, and other entities, many individuals are wary of sharing personal information online. By remaining anonymous, users can mitigate the risk of their data being exploited or misused.
Moreover, online anonymity enables individuals to explore sensitive or controversial topics without fear of retaliation. This is particularly crucial in regions where freedom of speech is restricted, allowing dissenting voices to be heard without facing censorship or persecution.
However, online anonymity also has its drawbacks. It can facilitate cyberbullying, harassment, and other forms of malicious behavior by providing perpetrators with a shield to hide behind. Additionally, the anonymity afforded by the internet can sometimes lead to a lack of accountability, fostering a culture of distrust and incivility.
Despite these challenges, online anonymity remains a fundamental aspect of internet culture, providing users with the autonomy to navigate the digital landscape on their own terms. As technology continues to evolve, finding a balance between privacy and accountability will be essential in ensuring a safe and inclusive online environment for all.
Virtual Private Network (VPN)
Title: Navigating the Digital Realm: Understanding Virtual Private Networks (VPN)
In an era where digital privacy is paramount, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. A VPN creates a secure, encrypted connection between your device and the internet, effectively shielding your data from prying eyes and potential threats.
One of the primary functions of a VPN is to encrypt your internet traffic, ensuring that your online activities remain private and protected from eavesdroppers, hackers, and even government surveillance. By masking your IP address and routing your connection through servers located in different geographic locations, VPNs enable users to browse the web anonymously, free from the constraints of geo-blocking and censorship.
Moreover, VPNs are instrumental in securing sensitive information, such as passwords, financial transactions, and personal communications, particularly when accessing public Wi-Fi networks. Without a VPN, these networks are vulnerable to interception and exploitation by malicious actors, putting users at risk of identity theft and financial loss.
Furthermore, VPNs offer additional benefits beyond privacy and security. They allow users to bypass geographic restrictions and access region-locked content, such as streaming services, websites, and social media platforms. Additionally, businesses often utilize VPNs to provide secure remote access to corporate networks for employees working from home or traveling abroad.
However, it's crucial to choose a reputable VPN provider that prioritizes user privacy and employs robust encryption protocols. While there are numerous VPN services available, not all are created equal, and some may compromise user privacy by logging and selling personal data.
In conclusion, Virtual Private Networks (VPNs) play a vital role in protecting online privacy, security, and freedom. By encrypting internet traffic and masking IP addresses, VPNs empower users to navigate the digital realm with confidence, ensuring that their online activities remain private and secure.
ExpressVPN features
ExpressVPN is renowned for its robust features that prioritize user privacy, security, and seamless browsing experiences. Here's a breakdown of some key features:
Military-grade Encryption: ExpressVPN employs AES-256 encryption, the industry standard trusted by security experts and government agencies worldwide. This ensures that all data transmitted through the VPN is virtually impenetrable to hackers and snoopers.
No-Logs Policy: Users can browse with peace of mind knowing that ExpressVPN adheres to a strict no-logs policy. This means that the VPN does not store any activity or connection logs, preserving user anonymity and privacy.
Global Server Network: With servers in over 160 locations across 94 countries, ExpressVPN offers unparalleled access to content from around the globe. Whether you're streaming geo-blocked content or accessing restricted websites, ExpressVPN ensures a fast and reliable connection wherever you are.
High-Speed Connections: ExpressVPN's optimized network infrastructure delivers lightning-fast connection speeds, making it ideal for streaming, gaming, and torrenting without buffering or lag.
Kill Switch and Split Tunneling: The kill switch feature automatically disconnects the internet if the VPN connection drops, preventing data leaks. Split tunneling allows users to route specific traffic through the VPN while accessing other services directly, providing flexibility and control over their internet usage.
Cross-Platform Compatibility: ExpressVPN is compatible with a wide range of devices and operating systems, including Windows, Mac, iOS, Android, Linux, routers, and more. Users can protect all their devices with just one subscription.
24/7 Customer Support: ExpressVPN offers round-the-clock customer support via live chat and email, ensuring that users receive assistance whenever they need it.
Overall, ExpressVPN's comprehensive suite of features makes it a top choice for users seeking privacy, security, and unrestricted access to the internet.
0 notes
Text
why is my vpn showing wrong location
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why is my vpn showing wrong location
VPN geo-location mismatch
A VPN geo-location mismatch occurs when the location displayed by a user's IP address does not match the actual physical location of the user. This discrepancy can lead to various issues, including online tracking, restricted access to geo-blocked content, and potential security risks.
One common reason for a VPN geo-location mismatch is when the VPN server's IP address is registered in a different location from where the user is physically located. This can happen if the VPN service provider does not update or properly manage their server locations, resulting in inaccurate geo-location data. As a result, websites and online services may incorrectly identify the user's location based on the VPN server's IP address, leading to geo-blocking or targeted advertisements based on the wrong location.
Another factor that can contribute to a VPN geo-location mismatch is IP address leakage. Sometimes, certain websites or applications may bypass the VPN tunnel and directly access the user's original IP address, revealing the true location instead of the masked one provided by the VPN. This can compromise the user's privacy and anonymity, as well as undermine the purpose of using a VPN for location obfuscation.
To avoid VPN geo-location mismatches, users should choose reputable VPN providers with a wide range of server locations and robust privacy policies. Additionally, regularly checking for IP leaks and ensuring that all internet traffic is routed through the VPN connection can help mitigate the risks associated with geo-location discrepancies. By staying vigilant and informed, users can better protect their online privacy and security while benefiting from the advantages of using a VPN service.
Incorrect IP address display
When dealing with networking and internet connectivity, encountering issues with incorrect IP address display can be frustrating and potentially disruptive. An IP (Internet Protocol) address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. Inaccurate IP address display can lead to problems such as difficulty accessing websites, disrupted network connections, and security concerns.
One common cause of incorrect IP address display is misconfiguration or malfunction of network hardware, such as routers or modems. These devices are responsible for assigning IP addresses to connected devices through a process known as DHCP (Dynamic Host Configuration Protocol). If the DHCP settings are not properly configured or if the hardware is faulty, it can result in the distribution of incorrect IP addresses.
Another possible cause is IP address conflicts, where two or more devices on the same network are assigned the same IP address. This can occur if IP addresses are manually assigned and not managed properly, or if there is a glitch in the DHCP server's allocation process.
Additionally, outdated or corrupt network drivers on individual devices can sometimes cause incorrect IP address display. Ensuring that network drivers are up to date and functioning properly can help mitigate this issue.
To troubleshoot and resolve incorrect IP address display, several steps can be taken. These include power cycling network hardware, releasing and renewing IP addresses, checking for IP conflicts, updating network drivers, and resetting network settings to default.
In conclusion, incorrect IP address display can stem from various sources, including misconfigured network hardware, IP conflicts, and faulty network drivers. By identifying the root cause of the issue and implementing appropriate troubleshooting steps, users can restore proper network connectivity and address any associated disruptions effectively.
Geolocation detection errors
Geolocation detection errors can be frustrating for both users and website owners. Geolocation is the process of determining the physical location of a device or person using various technologies such as GPS, Wi-Fi, or IP address. While geolocation can provide valuable information for services like targeted advertising, weather forecasts, or location-based apps, errors in detection can lead to inaccurate results.
One common source of geolocation errors is the use of VPNs or proxy servers, which can mask a user's true location and provide a different IP address to websites. This can result in websites showing the wrong content or location-based services being rendered useless. Similarly, using public Wi-Fi networks can also lead to inaccuracies in geolocation detection due to the shared nature of these networks.
Moreover, browser settings and privacy preferences can also interfere with accurate geolocation detection. For example, if a user disables location tracking in their browser or device settings, websites may not be able to accurately determine their location. Additionally, outdated browser software or issues with GPS signal reception can also contribute to geolocation errors.
To address geolocation detection errors, website owners can implement alternative methods of location tracking, such as HTML5 geolocation APIs or user input forms. By providing users with the option to manually enter their location, websites can minimize the impact of geolocation errors and ensure a more accurate user experience.
Overall, understanding the common causes of geolocation detection errors and implementing effective solutions can help improve the accuracy and reliability of location-based services and enhance the overall user experience.
VPN server location discrepancies
Title: Navigating VPN Server Location Discrepancies: What You Need to Know
In the realm of virtual private networks (VPNs), the concept of server location is paramount. Users often rely on VPNs to mask their online activities, enhance security, and access geo-restricted content. However, recent discussions have brought attention to discrepancies in server locations offered by VPN providers, sparking concerns among users about the reliability and effectiveness of these services.
One of the primary reasons for these discrepancies is the dynamic nature of VPN infrastructures. VPN providers operate numerous servers worldwide to accommodate user demand and optimize performance. However, the actual physical location of these servers may not always align with their advertised locations. Factors such as server load, maintenance, and network optimizations can lead to temporary or permanent shifts in server locations without prior notice to users.
Another factor contributing to server location discrepancies is the practice of virtual server locations. In this setup, a physical server located in one country can appear to be operating from another country through the use of virtualization technology. While this approach can help VPN providers expand their global reach, it can also result in misleading representations of server locations to users.
The implications of VPN server location discrepancies extend beyond mere inconvenience. Users relying on VPNs to access region-locked content or bypass censorship may find their intended destinations inaccessible if the VPN server's actual location does not match the desired region. Moreover, concerns about data privacy and security arise when users are uncertain about the true whereabouts of the servers handling their internet traffic.
To navigate these discrepancies effectively, users should prioritize VPN providers with transparent policies regarding server locations and regularly updated infrastructure information. Additionally, verifying server locations through independent testing tools can provide valuable insights into the actual performance and reliability of VPN services. By staying informed and vigilant, users can make informed decisions to ensure their online privacy and security remain uncompromised in an increasingly complex digital landscape.
IP address location inaccuracies
Title: Unraveling the Mysteries Behind IP Address Location Inaccuracies
In the digital realm, IP addresses serve as virtual fingerprints, identifying devices connected to the internet. However, despite their seemingly precise nature, IP address locations often harbor inaccuracies, leading to confusion and misinterpretation.
One primary reason for these inaccuracies is the method used to determine location. Geolocation databases rely on various sources of information, including Internet Service Providers (ISPs), GPS data, and user-provided information. Unfortunately, these sources aren't always up-to-date or reliable. Consequently, IP addresses can be erroneously associated with incorrect locations.
Moreover, the proliferation of Virtual Private Networks (VPNs) and proxy servers further complicates location tracking. These tools allow users to mask their true IP addresses, making it appear as though they are accessing the internet from a different geographical location altogether. Consequently, attempts to pinpoint a user's actual location based solely on their IP address may yield inaccurate results.
Another factor contributing to IP address location inaccuracies is the dynamic nature of IP assignments. ISPs frequently reassign IP addresses to different geographical regions, especially in densely populated areas with high internet usage. As a result, geolocation databases may struggle to keep pace with these rapid changes, leading to outdated location information.
Additionally, the inherent limitations of IP-based geolocation technology contribute to inaccuracies. Factors such as network latency, routing anomalies, and mobile device roaming can all affect the perceived location of an IP address.
Despite these challenges, geolocation technology continues to evolve, with efforts underway to improve accuracy through advanced algorithms and data validation techniques. However, it's essential to approach IP address location data with a degree of skepticism and recognize its inherent limitations, particularly in scenarios where precise location information is critical. By understanding the complexities behind IP address location inaccuracies, we can navigate the digital landscape more effectively and responsibly.
0 notes
Text
does a docker image use the same vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a docker image use the same vpn
Docker Image Network Isolation
Docker Image Network Isolation
In the world of containerization, Docker has emerged as one of the most prominent platforms for creating and managing lightweight, portable containers. One key aspect of Docker's functionality is network isolation, which plays a crucial role in ensuring the security and stability of containerized applications.
Network isolation in Docker refers to the ability to restrict network access for individual containers, thereby minimizing the risk of unauthorized access and potential security breaches. By default, Docker containers are isolated from the host machine and from other containers, but it is important to further enhance this isolation by configuring network settings appropriately.
There are several ways to achieve network isolation in Docker. One common approach is to use Docker's built-in networking capabilities, such as creating custom networks and assigning containers to specific networks. This allows for greater control over how containers communicate with each other and with external networks.
Another important aspect of network isolation in Docker is the use of network namespaces. Each Docker container runs in its own network namespace, which provides a separate network stack and set of network interfaces. This means that containers are completely isolated in terms of network communication, helping to prevent interference and conflicts.
Implementing network isolation in Docker is essential for maintaining a secure and well-organized container environment. By following best practices and leveraging Docker's networking features, developers and system administrators can ensure that their containerized applications remain isolated, resilient, and protected from potential threats.
VPN Utilization within Docker Containers
Title: Maximizing Security and Privacy: VPN Utilization within Docker Containers
In the realm of cybersecurity, safeguarding data and ensuring privacy have become paramount concerns, especially in the era of cloud computing and remote work. Docker containers have emerged as a popular solution for packaging and deploying applications across diverse computing environments. However, maintaining robust security measures within Docker containers remains a challenge. One effective approach to enhance security and privacy within Docker environments is through the utilization of Virtual Private Networks (VPNs).
VPNs establish encrypted connections between the user's device and a remote server, thereby shielding data from potential eavesdropping and cyber threats. Integrating VPNs with Docker containers adds an extra layer of protection, particularly when transmitting sensitive information over public networks.
One of the primary advantages of using VPNs within Docker containers is the ability to encrypt network traffic at the container level. By encapsulating containerized applications within a VPN tunnel, organizations can mitigate the risk of unauthorized access and data breaches. This approach is particularly beneficial for enterprises dealing with regulatory compliance requirements such as GDPR or HIPAA.
Furthermore, VPNs enable Dockerized applications to bypass geo-restrictions and access region-locked content securely. This capability is invaluable for businesses operating in global markets, as it ensures seamless connectivity and unrestricted access to online resources.
Implementing VPNs within Docker containers also facilitates secure communication between distributed microservices. By encrypting inter-container traffic, organizations can prevent man-in-the-middle attacks and ensure data integrity across complex application architectures.
In conclusion, the integration of VPNs within Docker containers offers a potent solution for enhancing security and privacy in modern computing environments. By encrypting network traffic, bypassing geo-restrictions, and securing inter-container communication, VPNs empower organizations to fortify their cyber defenses and safeguard sensitive data effectively. As cyber threats continue to evolve, leveraging VPNs within Docker containers will remain instrumental in preserving the confidentiality and integrity of digital assets.
Network Configuration in Docker Images
Network configuration in Docker images plays a crucial role in ensuring seamless communication between containers and the external network. Docker provides several options for configuring network settings within images, allowing developers to tailor their networking setup to suit their specific needs.
One of the primary methods for network configuration is through the use of Docker's built-in networking drivers. These drivers enable containers to communicate with each other and with external networks. Docker supports various network drivers, including bridge, host, overlay, and macvlan, each offering different features and functionality.
The bridge network driver is the default choice for most Docker installations. It creates a virtual bridge that allows containers to communicate with each other and with the host system. This driver provides isolation for containers while still enabling them to access external networks.
Alternatively, the host network driver allows containers to bypass Docker's networking stack and use the host system's network directly. This can offer improved performance in some cases but may sacrifice some of the isolation provided by Docker's default networking setup.
For more complex networking requirements, Docker also supports overlay and macvlan network drivers. The overlay driver facilitates communication between containers running on different Docker hosts, making it ideal for multi-host deployments. On the other hand, the macvlan driver assigns a unique MAC address to each container, allowing them to appear as separate devices on the network.
In addition to choosing the appropriate network driver, developers can further customize network settings within Docker images using configuration options such as IP addressing, port mapping, and network aliases. These settings enable fine-grained control over how containers communicate with each other and with external systems.
By carefully configuring network settings within Docker images, developers can ensure optimal performance, security, and scalability for their containerized applications. Whether deploying a simple web server or a complex microservices architecture, understanding and leveraging Docker's network configuration capabilities is essential for success in modern containerized environments.
VPN Compatibility with Docker Networks
With the increasing popularity of Docker for containerization in the IT industry, many users are curious about the compatibility of VPNs with Docker networks. Docker provides a way to package and deploy applications within containers, offering a consistent environment across different machines. However, when it comes to incorporating VPNs into Docker networks, there are certain considerations to keep in mind.
One key aspect to consider is ensuring that the VPN client is running at the host level rather than within the Docker container itself. By running the VPN client on the host machine, it ensures that all network traffic from the Docker containers will be routed through the VPN connection. This setup allows for secure communication and data transfer, especially when dealing with sensitive information.
Additionally, users should pay attention to the network configurations within Docker to avoid any conflicts with the VPN connection. It's important to configure the Docker network settings to work alongside the VPN settings to prevent any disruptions in network connectivity.
Furthermore, utilizing VPN services that offer support for dynamic IP addresses can also aid in ensuring seamless integration with Docker networks. By allowing for changes in IP addresses without affecting the VPN connection, users can maintain network security and privacy within their Docker environments.
In conclusion, while VPN compatibility with Docker networks is achievable, users must follow certain protocols to ensure a smooth and secure setup. By running the VPN client at the host level, configuring network settings appropriately, and selecting VPN services that support dynamic IP addresses, users can successfully incorporate VPNs into their Docker networks for enhanced security and privacy.
Securing Docker Image Connections
When it comes to securing Docker image connections, it is crucial to take necessary measures to protect your containers from potential security threats. Docker images are widely used in various applications and workloads, making them valuable targets for malicious actors. By following best practices and implementing proper security protocols, you can enhance the security of your Docker image connections.
One essential step in securing Docker image connections is to ensure that you are using official and trusted Docker images from reputable sources. Avoid downloading images from unverified repositories, as they may contain vulnerabilities or malicious code that can compromise your system. Always verify the integrity of the images and regularly update them to patch any known security issues.
Furthermore, consider implementing strong authentication mechanisms to control access to your Docker images. Utilize secure authentication methods such as multi-factor authentication to prevent unauthorized users from accessing sensitive containers. Additionally, configure secure network settings to restrict access to your Docker images and containers only to authorized users and services.
Encrypting Docker image connections using secure protocols such as HTTPS can also enhance the security of your containerized applications. By encrypting data in transit, you can prevent eavesdropping and protect sensitive information from interception by malicious entities.
In conclusion, securing Docker image connections is essential to safeguard your containers and data from security threats. By following best practices such as using trusted images, implementing strong authentication mechanisms, and encrypting connections, you can enhance the security posture of your Docker environment and minimize the risk of potential attacks.
0 notes
Text
can your network see what you do on a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can your network see what you do on a vpn
VPN privacy
Title: Understanding VPN Privacy: How Virtual Private Networks Safeguard Your Online Security
In an age where cybersecurity threats loom large, safeguarding your online privacy has become paramount. One potent tool in this digital arsenal is the Virtual Private Network (VPN), which offers a secure pathway for transmitting data over the internet. VPNs are particularly renowned for their ability to enhance privacy by encrypting your internet connection, thereby shielding your online activities from prying eyes.
The fundamental mechanism behind VPN privacy lies in encryption. When you connect to a VPN server, your data is encrypted before it travels across the internet. This encryption process renders your information indecipherable to anyone attempting to intercept it, be it hackers, government agencies, or internet service providers. As a result, VPNs serve as an effective barrier against surveillance and data interception, ensuring that your online communications remain confidential.
Moreover, VPNs provide anonymity by masking your IP address. By rerouting your internet traffic through a remote server, VPNs obscure your actual location and assign you a different IP address. This not only safeguards your identity but also allows you to bypass geographical restrictions and access content that may be blocked in your region.
However, while VPNs offer robust privacy protection, not all VPN providers are created equal. It's crucial to choose a reputable VPN service that prioritizes user privacy and employs stringent security measures. Factors to consider include the level of encryption offered, the jurisdiction of the VPN provider, and their logging policies.
In conclusion, VPNs are indispensable tools for preserving online privacy in an era of heightened digital surveillance. By encrypting your internet connection and masking your IP address, VPNs fortify your online security and enable you to browse the web with peace of mind. However, users should exercise caution and opt for trustworthy VPN services to maximize the efficacy of their privacy protection measures.
Network monitoring
Title: Enhancing Network Performance through Effective Network Monitoring
In today's digital age, where connectivity is paramount for businesses and individuals alike, the importance of network monitoring cannot be overstated. Network monitoring refers to the practice of overseeing computer networks for any potential issues or performance bottlenecks. It involves the continuous tracking of network components such as servers, routers, switches, and applications to ensure optimal functionality and performance.
One of the primary objectives of network monitoring is to detect and address any anomalies or irregularities in real-time. By leveraging specialized software tools, administrators can monitor network traffic, bandwidth utilization, and device statuses. This proactive approach enables them to identify potential issues before they escalate into major problems, thus minimizing downtime and ensuring uninterrupted connectivity.
Moreover, network monitoring plays a crucial role in ensuring network security. By monitoring for suspicious activities, unauthorized access attempts, and potential security breaches, administrators can promptly respond to threats and safeguard sensitive data and resources. Additionally, monitoring network traffic patterns can help identify and mitigate potential cyber attacks, such as Distributed Denial of Service (DDoS) attacks, which can cripple network infrastructure.
Furthermore, network monitoring facilitates capacity planning and optimization. By analyzing historical data and trends, administrators can anticipate future network requirements and allocate resources accordingly. This proactive approach helps prevent network congestion and ensures sufficient bandwidth to support growing demands.
In conclusion, network monitoring is indispensable for maintaining the performance, security, and reliability of modern computer networks. By continuously monitoring network infrastructure and proactively addressing issues, organizations can enhance productivity, minimize risks, and provide seamless connectivity to users. As technology continues to evolve, the importance of robust network monitoring solutions will only continue to grow.
Internet activity tracking
Internet activity tracking refers to the process of monitoring and recording an individual's online behavior. This practice is commonly used by companies, government agencies, and other entities to gather data on users' actions, preferences, and interests. While internet activity tracking can have legitimate purposes, such as improving user experience or enhancing cybersecurity measures, it also raises concerns about privacy and data security.
One of the most common forms of internet activity tracking is cookies, which are small pieces of data stored on a user's device by websites they visit. Cookies enable websites to remember user preferences and track their browsing habits. However, some cookies can be used for targeted advertising, where users are shown personalized ads based on their internet activity.
In addition to cookies, internet service providers (ISPs) and social media platforms also track users' online activities. ISPs can monitor users' browsing history, while social media platforms collect data on users' interactions and behaviors to personalize their feeds and targeted advertisements.
The widespread use of internet activity tracking has led to growing concerns about individual privacy and data protection. Many internet users are unaware of the extent to which their online activities are being tracked and monitored. There are also risks of personal data being exposed or misused, especially in cases of data breaches or unauthorized access.
To protect their privacy online, users can take steps such as regularly clearing their cookies, using virtual private networks (VPNs) to mask their IP addresses, and being cautious about the information they share online. Additionally, regulatory bodies and policymakers are increasingly focused on implementing measures to enhance data privacy and security in the digital space.
VPN encryption
VPN encryption plays a crucial role in safeguarding data privacy and security online. VPN, which stands for Virtual Private Network, uses encryption protocols to create a secure connection between the user's device and the internet. This encryption ensures that any data transmitted over the network remains secure and inaccessible to unauthorized third parties.
There are several encryption protocols used by VPN services to protect user data. One of the most widely used protocols is OpenVPN, known for its strong security features and reliability. OpenVPN uses a combination of symmetric-key encryption and public-key cryptography to secure data transmission effectively.
Another commonly used encryption protocol is IPSec (Internet Protocol Security), which works by encrypting data packets to ensure confidentiality and integrity. IPSec is often used in combination with other security protocols to enhance the overall security of the VPN connection.
TLS (Transport Layer Security) is another encryption protocol used by VPN services to secure data in transit. TLS encrypts data at the transport layer, adding an extra layer of security to prevent unauthorized access and data manipulation.
VPN encryption ensures that sensitive information such as passwords, credit card details, and personal communications remain secure and protected from potential cyber threats. By encrypting data traffic, VPN services provide users with peace of mind knowing that their online activities are private and secure.
In conclusion, VPN encryption is a cornerstone of online security, providing users with a safe and secure way to browse the internet while protecting their data from cyber threats. Choosing a VPN service with robust encryption protocols is essential for maintaining privacy and security in an increasingly connected world.
Online anonymity
Online anonymity refers to the ability of individuals to conceal their identities when engaging in activities on the internet. It offers users the freedom to browse, communicate, and interact without revealing personal information such as their name, location, or other identifying details. This anonymity can be achieved through various means, including using pseudonyms, virtual private networks (VPNs), anonymous browsing tools like Tor, and encrypted messaging services.
One of the primary reasons people seek online anonymity is to protect their privacy. In today's digital age, where personal data is constantly collected and monetized by companies, maintaining anonymity can help individuals safeguard their sensitive information from being exploited or misused. Moreover, anonymity enables individuals to express themselves freely without fear of retaliation or discrimination. It allows whistleblowers, activists, and marginalized communities to voice their opinions and share their experiences without facing repercussions.
However, online anonymity also has its drawbacks. It can provide a cloak for cybercriminals to engage in illegal activities such as hacking, fraud, or harassment. The anonymity afforded by the internet can make it difficult for law enforcement agencies to track down perpetrators and hold them accountable for their actions. Additionally, malicious actors may use anonymity to spread misinformation, incite violence, or manipulate public opinion without facing consequences.
Despite these challenges, online anonymity remains an essential aspect of internet freedom and digital rights. It empowers individuals to control their online presence and protect their privacy in an increasingly interconnected world. As technology continues to evolve, striking a balance between anonymity and accountability will be crucial in ensuring a safe and inclusive online environment for all users.
0 notes
Text
Piracy in India: Concept and Laws

This article on 'Piracy in India: Concept and Laws' was written by Tosani Lal, an intern at Legal Upanishad.
INTRODUCTION
An individual original work with respect to the creation of cinema, which is also referred to as intellectual property, if it is stolen and misappropriated by another person as their own and leaked on their or any other website, shall be considered piracy. It shall be pertinent to note that the act of piracy might have varying understanding and punishment for different nations, but the common factor in all is that such an act is considered unlawful. In this article, we will try to understand the meaning of privacy in an Indian context and examine what legal measures the government has taken to protect individual work in the field of moviemaking.
DEFINITION
In the early days, piracy referred to acts amounting to maraud or illegal raiding, which usually occurred on a ship. The main object of such actions is to illegally obtain valuables and other significant belongings of other persons. In present times, this kind of act is defined as robbery, theft, or dacoity in Indian law. In terms of defining piracy, it now refers to the theft or misappropriation of one’s intellectual property, specifically with respect to copyrights. In other words, piracy is defined as infringement of copyrights for wrongful gain and causing damage to their intellectual property. Piracy has become more common in the digital age. A person illegally secures and distributes digital documents and movies for the purpose of wrongful gain. With respect to movies, when a person illegally obtains the digital print of the movies and distributes or leaks them on the internet for free access, such acts result in monetary loss to the creator and owner, as well as severe financial damage to the film fraternity.
KINDS OF PIRACY
Piracy can be categorised into five different types. Counterfeiting : In the case of counterfeiting, there is the acquisition, replication, and sale of any copyright material through an illegal method. Internet Piracy: The act of illegally downloading any documents from an internet platform. Piracy on the internet was performed by sending invites for free software downloads and documents containing any important digital print. Peer-to-Peer, also known as P2P, is a file sharing system that aids in transfer programmes. End-User Piracy: In this category of privacy, there is reproduction of the software through illegal methods. In other words, the user is not authorised to perform the act of reproducing such software. Client-Server Overuse: The situation where the clients of a certain server licence prescribed is exceeded, then the required in a computer network platform is referred to as overuse piracy or client-server overuse. Hard-Disk Loading: In this situation, a computer sold by a certain company also contains illegal sales software that is loaded into the hard disc with the object of making the sale and purchase of such devices more inviting.
Contact Us and avail the best assignment help for students available online!
LAWS ON PIRACY IN INDIA
In order to protect the rights of the owner of the intellectual property, especially the copyrights of individuals, the government has prescribed some legal measures and introduced laws with respect to the protection and punishment of piracy in India. One of the most significant laws of piracy in Indian legislation is the Copyright (Amendment) Act, 2012, which incorporates two main sections to protect the copyright owner and punishes for the act of illegally accessing important information through the internet. These are Section 65A and Section 65B of the Copyright (Amendment) Act, 2012. Section 65(A): This provision safeguards Technological Protection Measures (TPM) employed by copyright owners. It imposes penalties on individuals attempting to circumvent technological measures established to safeguard rights outlined in the Act, intending to infringe upon those rights. Offenders may be subject to a maximum of two years of imprisonment along with a fine. Section 65(B): Focused on Information Rights Management (IRM), this section protects sensitive information from unauthorized access. It penalizes individuals who knowingly remove or alter rights management information without proper authority or distribute copyrighted works with the awareness that such information has been tampered with or removed without permission. Violators could face imprisonment for up to two years, coupled with fines. Additionally, to the Copyright (Amendment) Act, 2012, the Information Technology Act, 2000 was introduced with the object of regulating laws on issues concerning the illegal sale of content that is subject to copyright. Section 66 of the Information Technology Act, 2000 deals with breach of a computer-related offence and shall be penalised for three years of imprisonment and levied with a fine that can be extended to five lakh rupees. Furthermore, on July 20, 2023, the Cinematography (Amendment) Bill, 2023, was brought up in the Rajya Sabha with the object of certifying films for exhibition. These legislative measures collectively aim to curb digital piracy and reinforce the legal framework surrounding intellectual property rights in the digital realm.
CONCLUSION
After reviewing the meaning and legal provisions of the piracy laws in the Indian context, it can be concluded that although the government has established these laws, in order for them to be effective and protect the owner's work from piracy, there should be some preventive measures that should be taken into consideration to protect them against piracy in the digital age. Such as regulating the price for offering access to cinema and providing some kind of incentive given the consumer the idea that their movie experience will be worth their while. Second, the government can create a policy that should effectively restrict the entry of illegal sites that distribute copies of such digital prints as movies and other sensitive documents. Therefore, in conclusion, it can be understood that, with the evolution of digital India, the male practice of piracy is also increasing at a higher rate. This causes a significant loss to the creator of the product. The legislation for the protection and prevention of acts of piracy needs to be more effective so as to at least reduce the losses suffered and discourage their violations.
List of References:
- The Copyright Act, 1957 (Act 14 of 1957) - Manish Jindal, Piracy Protection in India: A Closer Look, Bytes Care Blog, 4 December 2023, available at: https://bytescare.com/blog/piracy-protection-in-india - A Note on Anti-Piracy Laws in India, Brands & Bonds, available at: https://www.brandsnbonds.com/updates/intellectual-property-right/a-note-on-anti-piracy-laws-in-india/ Read the full article
0 notes
Text
Benefits Of Using Google Docs
In the event that you state computers have changed just how we build and store data, Bing Documents can definitely be called the following revolution. The principal aim of Google would be to remove redundancy. Let us imagine a business teacher Linda with thirty students in her Retail Administration class. She requires them to publish event studies on various retail chains. Automagically all 30 pupils will deliver her their case study drafts. Jane will explain regions of improvements and corrections in the files and deliver it back once again to them. This way four various copies of the same draft can get developed - two with Anne and one other two with the student. Multiply that with 30 i.e. amount of Jane's pupils and you can imagine the mess. The editing treatment may that one or more more round. Thus, Anne find yourself having at the very least 120 (30x4) various copies resulting in plenty of distress and waste of time and energy. These on the web papers saves time, power and space. It offers a program wherever documents can be downloaded and edited in real time. Linda can produce 30 various documents for each of her students. They could distribute their work in these documents. After, they have done that Jane can study them and make improvements on ab muscles files they worked on. This way all the job is going to be done on a single record provided between Anne and each student. The thirty situation reports will no longer lead to the formation of over 120 various files - as a result of Google Docs. Different safety choices given by Bing Docs will allow Jane allow or prohibit the access of these papers by people different her documents. When the assignment's timeline occurs, she can make the documents obvious and then himself or if she wants to a bigger audience as well. Once we say'documents'it may sound like we mean Microsoft Word files only, Number, Google Docs helps a number of record formats.How To Alphabetize In Google Docs This enables several types of users including academicians, analysts, students, business companions, writers and others to produce different kinds of files and produce a varied use out of the facility. Some of the types that Bing Documents supports are stated below. If you're used to discussing your official function documents such as spreadsheets or goods for presentations, the existing format only allows you to send each file, one at any given time to Google Docs. The procedure could be both boring and time consuming. As an example, you might want to attach added files to an existing batch. It'd thus require that you manually build new versions where you are able to store your papers at the cloud database. This approach requires a lot of time and less efficient. You can find small cut features which allow you to move and drop your folders directly from your workplace top to Bing Documents cloud server. The feature can be performed if you are using Windows or Traveler in your PC. For instance, if applying Windows, Click'my computer'then go to'My papers'and choose the file you'd want to transfer to Bing Docs. Click and drag the folder to the Cloud Hero get on your individual computer. Launch your directory onto the Cloud Hero space. The file or folder could quickly be published to the Google Files cloud database. You are able to undertake all that without having to log on to Google Docs. The benefits in using this approach is that everything is automatic and you need maybe not conduct some other function because every different function is automated. Because the procedure resembles the usual method of using Windows you'd discover it is easy to complete it. There is no additional pc software or plan to be learnt. Cloud Hero is definitely a good time-saving feature which enables you to function more efficiently. It suffices to notice that with Google Documents, you're only worried about transfer of documents in the exact same way as you do with MS Office, Excel, PDF, or PowerPoint. If, like you're a top Google apps person, it is possible to use drag and decline function within the Cloud Hero plan through the "any record form" function to keep your documents in the Bing Docs. How To Alphabetize A List In Google Docs This enables you to send and store different types of file types such as for instance video and audio. Versions that you simply use together with AutoCAD, Quicken or QuickBooks may also be saved there. You realize that the docs on the cloud gets control of the functions of any copy program even though that it's slightly located in the electronic cloud. This produces a great saving in comparison to different copy options. What makes Cloud Hero great is the fact that it accommodates any changes plus adjustments built to files in your workplace top. Any improvements made to a file on your desk prime could quickly be up-to-date at Bing Docs. The automated updating of documents takes place when you are linked online.
1 note
·
View note
Text
Picking The Best VPN System For You

more vpns With web security treats going left and perfect, choosing the best VPN assistance is important in making sure your business and your important data are not hacked or even maliciously distributed online. But with a variety of options to choose from, tips on how to select the best VPN service? What for anyone who is looking for when searching a brand for the VPN services that it gives?
In the succeeding sentences, we will shorten this geek-sounding mission into something that the majority of Joe can observe. The goal is planned to be able to teach any kind of internet-literate individual while using basics of VPN selection in order to just remember to are protected out of all sorts of malicious disorders on the internet. more vpns 1 . Start with looking at the server selections being offered. A good VPN service is often a secure connection this shields your mobile phone network from hacks. It is doing this by re-routing all your information for the VPN server at which it gets tested for integrity in addition to security before appearing transmitted to your personal pc. You are essentially insulation yourself by restricting all the connections with VPN service provider.
Just what exactly this does entail in layman's terms and conditions? Well, it means you must have access to servers inside locations where you need to watch a satisfy from. Consider this essential example: suppose you might be an expat upon assignment in European union and you want to proceed watching Netflix video lessons through a secure steady stream; you will need a YOU AND ME VPN server we are able to secure access to Netflix servers located in north america. If you are using a USA server, there could be no way for you to viewpoint Netflix streams. Exactly the same concept applies for other websites that you just wish to view -- you will need a VPN service provider which has a significant other server in the international locations where your vacation destination websites are organised from.
If you find every one of these considerations to be monotonous and confusing, you can actually alternatively pick a particular NL VPN system to allow you to browse the online world anonymously. It is a modest less secure however , with fewer complications, you wouldn't be required to think about too many issues regarding your service.
2 . not A big determinant within the price that you finally end up paying for the VPN service is bandwidth. For example , if you want some sort of iPad 2 VPN purely for surfing around purposes, you can purchase a service with a lessen bandwidth offer as opposed to if you wanted to steady flow Netflix movies. Designed for everyday use, 2GB bandwidth should be enough.
If you do not want to be not allowed in your usage you have fixed bandwidth, seek out VPN services that are fitted with unlimited bandwidth. This may cost you more nevertheless it really would eliminate the have to worry about whether that you are about to exceed a VPN plan restricts or not.
3. Compatibility with your elected device is also essential. Again, if you want to use iPad 3 VPN services, remember to explicitly ask for a service. Most people find the cheapest service accessible only to realize later on that the VPN schedule they just picked up can only supply on their old, clunky desktops. It is always far better to ask if a offer is compatible using your preferred device therefore you are sure of what you may are getting.
4. More. These correspond to additional features in the give that may or will possibly not need. As such, you must ask. For example , you may decide your selection designed for best VPN service to allow P2P application. You wouldn't plan to find yourself in a situation where you stand safe from detrimental internet attacks however you can't do the things which you want to do on the internet simply because your VPN system is blocking those sites that you want to visit. Generally speaking, ask the specialist when you are in uncertainty.
From these tips, you need to be able to narrow lower your selection to a couple brands. A list of 3 to 4 potential VPN carrier's networks is ideal.
The past thing you need to do is usually to put these criteria together. The best way to accomplish this is to read assessments regarding your shortlisted organisations. Remember that there is no tactic to plan for everything on the subject of VPN so looking at about other people's goes through will help you find tips such as service durability, promotions, and reliability straight from the outlook of the user. Such intangibles are not consistently visible in the provide brochure.
Your best VPN should have the back up of many other clients, not just a select couple who have very lessened specifications and standards. It also isn't at all times the most expensive, usually not the fastest, or simply the most sophisticated. Customize your chosen services for the exact needs to help you to maximize what you have become from the company with no paying too much.
To start, make sure to run through an index of your basic targets before narrowing a person's list further a couple brands. From generally there, you can then begin the more often detailed task from comparing offers along with prices and criteria until you come up with the top VPN service of which suits your needs good.
VPN service providers are helping people protect their information online, while also giving them the ability to browse the internet in private. The world of VPN service providers is growing all the time. Discover which VPNs are the most trusted and which you should be using when it comes to protecting your personal information and computer files and browsing history.
1 note
·
View note
Text
What is AWS? Amazon Cloud Services Tutorial
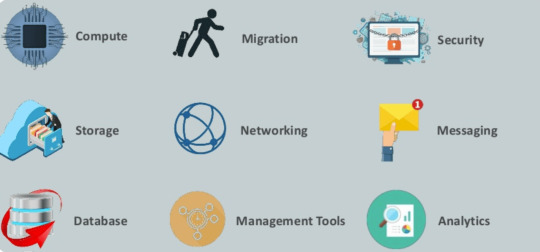
Cloud computing is a term referred to storing and gaining access to statistics over the internet. It does no longer preserve any data on the hard disk of your personal computer. In cloud computing, you can get right of entry to records from a much flung server.
What is AWS? Amazon net service is a platform that offers flexible, dependable, scalable, smooth-to-use and rate-effective cloud computing answers.
AWS is a entire, easy to use computing platform presented Amazon. The platform is superior with a combination of infrastructure as a provider (IaaS), platform as a provider (PaaS) and packaged software program as a company (SaaS) services.
In this tutorial, you may examine,
History of AWS 2002- AWS offerings released
2006- Launched its cloud merchandise
2012- Holds first purchaser occasion
2015- Reveals income completed of $4.6 billion
2016- Surpassed $10 billon income target
2016- Release snowball and snowmobile
2019- Offers nearly 100 cloud services
Important AWS Services
Amazon Web Services gives a extensive variety of various business company cause international cloud-primarily based totally merchandise. The products encompass garage, databases, analytics, networking, mobile, development system, agency applications, with a pay-as-you-bypass pricing model.
Here, are crucial AWS offerings.
AWS Compute Services Here, are Cloud Compute Services presented with the resource of Amazon:
EC2(Elastic Compute Cloud) - EC2 is a digital system in the cloud on which you have OS degree manipulate. You can run this cloud server each time you want. LightSail -This cloud computing tool robotically deploys and manages the pc, storage, and networking talents required to run your applications. Elastic Beanstalk — The device offers automatic deployment and provisioning of resources like a mainly scalable production website. EKS (Elastic Container Service for Kubernetes) — The device allows you to Kubernetes on Amazon cloud environment with out set up. AWS Lambda — This AWS carrier allows you to run capabilities within the cloud. The tool is a large price saver for you as you to pay handiest while your features execute.
Migration Migration services used to switch statistics physical between your datacenter and AWS. DMS (Database Migration Service) -DMS carrier may be used emigrate on-internet site databases to AWS. It helps you to migrate from one type of database to some different — for example, Oracle to MySQL. SMS (Server Migration Service) - SMS migration services lets in you emigrate on-internet website servers to AWS with out problems and short. Snowball — Snowball is a small software program which allows you to exchange terabytes of information inside and outside of AWS surroundings.
Storage Amazon Glacier- It is a really low-value garage issuer. It offers relaxed and rapid storage for facts archiving and backup. Amazon Elastic Block Store (EBS)- It presents block-level storage to use with Amazon EC2 instances. Amazon Elastic Block Store volumes are network-connected and stay unbiased from the existence of an instance. AWS Storage Gateway- This AWS carrier is connecting on-premises software application programs with cloud-based totally storage. It offers comfortable integration between the corporation’s on-premises and AWS’s storage infrastructure. Security Services IAM (Identity and Access Management) — IAM is a comfy cloud safety service which helps you to manage users, assign rules, shape businesses to control more than one clients.
Inspector — It is an agent that you may set up for your digital machines, which reports any safety vulnerabilities. Certificate Manager — The provider offers free SSL certificate in your domains which might be managed through Route53. WAF (Web Application Firewall) — WAF security service gives software-degree protection and allows you to block SQL injection and helps you to block flow-internet website online scripting attacks. Cloud Directory — This issuer lets in you to create bendy, cloud-native directories for coping with hierarchies of data alongside multiple dimensions. KMS (Key Management Service) — It is a controlled provider. This protection provider helps you to create and control the encryption keys which lets in you to encrypt your records. Organizations — You can create corporations of AWS bills the use of this service to manages protection and automation settings. Shield — Shield is controlled DDoS (Distributed Denial of Service protection provider). It offers safeguards against internet programs taking walks on AWS. Macie — It offers a records visibility protection carrier which lets in classify and defend your touchy essential content material. GuardDuty —It offers danger detection to shield your AWS money owed and workloads.
Database Services Amazon RDS- This Database AWS service is simple to installation, perform, and scale a relational database in the cloud. Amazon DynamoDB- It is a short, truly controlled NoSQL database provider. It is a smooth carrier which permit charge-effective storage and retrieval of statistics. It moreover permits you to serve any degree of request visitors. Amazon ElastiCache- It is an internet issuer which makes it easy to installation, carry out, and scale an in-memory cache within the cloud. Neptune- It is a quick, reliable and scalable graph database provider. Amazon RedShift - It is Amazon’s data warehousing answer which you can use to perform complex OLAP queries. Analytics Athena — This analytics company permits perm SQL queries to your S3 bucket to find out documents. CloudSearch — You have to use this AWS provider to create a completely controlled searching for engine for your net website online. ElasticSearch — It is similar to CloudSearch. However, it offers more functions like software monitoring. Kinesis — This AWS analytics carrier helps you to motion and studying actual-time statistics at big scale. QuickSight —It is a enterprise analytics tool. It lets you create visualizations in a dashboard for facts in Amazon Web Services. For example, S3, DynamoDB, and so forth. EMR (Elastic Map Reduce) —This AWS analytics service specifically used for big statistics processing like Spark, Splunk, Hadoop, and so on. Data Pipeline — Allows you to move records from one location to each different. For example from DynamoDB to S3. Management Services CloudWatch — Cloud watch lets you monitor AWS environments like EC2, RDS times, and CPU utilization. It also triggers alarms relies upon on diverse metrics. CloudFormation — It is a manner of turning infrastructure into the cloud. You can use templates for providing a whole production surroundings in minutes. CloudTrail — It offers an clean method of auditing AWS resources. It helps you to log all changes. OpsWorks — The service permits you to computerized Chef/Puppet deployments on AWS surroundings. Config — This AWS service video display units your environment. The device sends indicators approximately modifications when you harm certain described configurations. Service Catalog — This provider permits large institutions to authorize which services customer can be used and which gained’t. AWS Auto Scaling — The provider allows you to mechanically scale your assets up and down primarily based on given CloudWatch metrics. Systems Manager — This AWS carrier allows you to agency your assets. It permits you to understand problems and act on them. Managed Services—It offers management of your AWS infrastructure which permits you to consciousness to your packages. Internet of Things IoT Core— It is a controlled cloud AWS provider. The carrier allows connected gadgets like cars, mild bulbs, sensor grids, to securely interact with cloud programs and distinctive gadgets. IoT Device Management — It allows you to manipulate your IoT gadgets at any scale. IoT Analytics — This AWS IOT carrier is beneficial to carry out analysis on facts accumulated by using manner of your IoT gadgets. Amazon FreeRTOS — This real-time working system for microcontrollers helps you to be part of IoT gadgets inside the local server or into the cloud. Application Services Step Functions — It is a manner of visualizing what’s going internal your software and what wonderful microservices it’s some distance the use of. SWF (Simple Workflow Service) — The service helps you to coordinate both automated responsibilities and human-led responsibilities. SNS (Simple Notification Service) — You can use this carrier to ship you notifications within the form of electronic mail and SMS primarily based on given AWS offerings. SQS (Simple Queue Service) — Use this AWS carrier to decouple your applications. It is a pull-based totally definitely carrier. Elastic Transcoder — This AWS carrier tool lets you changes a video’s layout and determination to manual diverse gadgets like capsules, smartphones, and laptops of various resolutions. Deployment and Management AWS CloudTrail: The services facts AWS API calls and ship backlog documents to you. Amazon CloudWatch: The gear display AWS assets like Amazon EC2 and Amazon RDS DB Instances. It also allows you to display custom metrics created via customer’s applications and offerings. AWS CloudHSM: This AWS carrier allows you meet organization, regulatory, and contractual, compliance requirements for preserving information safety with the resource of the use of the Hardware Security Module(HSM) domestic device within the AWS environment. Developer Tools CodeStar — Codestar is a cloud-based issuer for growing, dealing with, and running with severa software development initiatives on AWS. CodeCommit — It is AWS’s version manipulate carrier which lets in you to keep your code and other property privately inside the cloud. CodeBuild — This Amazon developer service let you automates the device of constructing and compiling your code. CodeDeploy — It is a way of deploying your code in EC2 times mechanically. CodePipeline — It allows you create a deployment pipeline like testing, constructing, checking out, authentication, deployment on development and manufacturing environments. Cloud9 —It is an Integrated Development Environment for writing, strolling, and debugging code within the cloud. Mobile Services Mobile Hub — Allows you to feature, configure and layout features for cellular apps. Cognito — Allows users to signup the use of his or her social identification. Device Farm — Device farm lets you improve the fine of apps with the aid of way of fast attempting out masses of cell devices. AWS AppSync —It is a fully controlled GraphQL company that gives actual-time records synchronization and offline programming competencies. Business Productivity Alexa for Business — It empowers your corporation with voice, the usage of Alexa. It will allow you to Allows you to build custom voice capabilities for your commercial enterprise enterprise. Chime — Can be used for online meeting and video conferencing. WorkDocs — Helps to save files inside the cloud WorkMail — Allows you to send and receive enterprise emails. Desktop & App Streaming WorkSpaces — Workspace is a VDI (Virtual Desktop Infrastructure). It permits you to use faraway computers in the cloud. AppStream — A manner of streaming laptop applications to your customers inside the internet browser. For example, using MS Word in Google Chrome. Artificial Intelligence Lex — Lex device helps you to build chatbots speedy. Polly — It is AWS’s textual content-to-speech company permits you to create audio versions of your notes. Rekognition — It is AWS’s face reputation issuer. This AWS carrier lets you recognize faces and item in pictures and movies. SageMaker — Sagemaker permits you to assemble, train, and set up device studying models at any scale. Transcribe — It is AWS’s speech-to-text carrier that gives excellent and cheap transcriptions. Translate — It is a very similar device to Google Translate which permits you to translate text in a single language to a few other. AR & VR (Augmented Reality & Virtual Reality) Sumerian — Sumerian is a hard and fast of device for providing notable digital truth (VR) experiences at the net. The issuer lets in you to create interactive 3-d scenes and publish it as a net site for customers to get entry to. Customer Engagement Amazon Connect — Amazon Connect permits you to create your client care center inside the cloud. Pinpoint — Pinpoint lets you recognize your customers and engage with them. SES (Simple Email Service) — Helps you to ship bulk emails for your customers at a in particular value-powerful price. Game Development GameLift- It is a carrier that’s managed by AWS. You can use this provider to host committed game servers. It allows you to scale seamlessly without taking your recreation offline. Applications of AWS services Amazon Web services are appreciably used for numerous computing features like: Web web site website hosting Application hosting/SaaS internet web hosting Media Sharing (Image/ Video) Mobile and Social Applications Content delivery and Media Distribution Storage, backup, and disaster restoration Development and test environments Academic Computing Search Engines Social Networking Companies the use of AWS Instagram Zoopla Smugmug Pinterest Netflix Dropbox Etsy Talkbox Playfish Ftopia
Advantages of AWS Following are the pros of using AWS offerings: AWS allows corporations to use the already familiar programming models, running structures, databases, and architectures. It is a value-powerful carrier that allows you to pay most effective for what you operate, with none up-the front or prolonged-time period commitments. You will now not require to put money into on foot and maintaining information centers. Offers fast deployments You can with out troubles upload or remove potential. You are allowed cloud get right of entry to speedy with limitless capability. Total Cost of Ownership is very low in evaluation to any non-public/dedicated servers. Offers Centralized Billing and management Offers Hybrid Capabilities Allows you to set up your software in a couple of regions round the world with just a few clicks
Disadvantages of AWS If you need more immediate or extensive help, you may must pick out paid assist packages. Amazon Web Services may moreover have some not unusual cloud computing problems at the same time as you circulate to a cloud. For instance, downtime, restricted manipulate, and backup protection. AWS units default limits on resources which range from region to area. These belongings encompass images, volumes, and snapshots. Hardware-level changes occur on your utility which gained’t offer the remarkable universal performance and utilization of your programs. Best practices of AWS You want to format for failure, but not anything will fail.It’s vital to decouple all of your additives before the use of AWS services.You want to preserve dynamic data inside the path of compute and static records closer to the man or woman.It’s essential to realise protection and performance tradeoffs.Pay for computing capacity via the hourly charge approach.Make a dependancy of a one-time fee for each instance you want to order and to obtain a large good buy on the hourly price. IEVISION Provides Aws Training in Pune with the right knowledge of AWS cloud for clearing AWS certification. You will get real time hands-on experience in working with cloud computing, Amazon Web Services, various components of cloud like Software as a Service,Course Details — Aws training in pune contact us — 9604641000 / 9604642000 Email Us — [email protected]
1 note
·
View note
Text
Architecture On The LAMP Environment AWS Existing Stack

The data layer of the solution consists of fully managed, scalable and highly available services such as DynamoDB and Amazon S3. DynamoDB provides a NoSQL datastore for storing structured data with low latency access. Amazon S3 offers an extremely robust and scalable archive of objects for storing photos, videos, binary data and other files that can be accessed directly via HTTP. Data stored in Amazon S3 can be stored in the Amazon Glacier service by applying a storage policy to the S3 bucket. Identity Management Amazon Cognito can simplify user authentication and authorization, and gives customers the ability to authenticate users with Amazon Cognito user pools, social identity providers, or their own identity management system. Amazon Cognito offers users access capabilities and integrates with Identity and Access Management AWS, adding additional security features to the mobile backend and simplifying the management of important security features for your app. Interface to access the user interface Log in with Facebook, Google and Twitter Add user access and access workflows to your applications for onboarding customers by supporting your apps with a fully managed multi-factor authentication service. You can also authenticate users through social identifiers such as Facebook, Twitter and Google+. This feature is provided by Amazon Cognito. Architecture Guided by Events AWS Lambda simplifies the implementation of event-based architectures that do not require permanent resources. Lambda hosts the backend logic for mobile apps. Lambda automatically runs the code in response to events and assigns resources to resolve requests as needed. In this way, you can provide the mobile application with a minimum logic to simplify scaling and updating. AWS Lambda automatically monitors lambda functions in your order and reports metrics via Amazon CloudWatch. To help troubleshoot problems, Lambda logs all feature requests and automatically logs logs through the Amazon CloudWatch logs. App Store Amazon Cognito Sync supports reading and writing in a local data store. This means that your app can work the same way, regardless of whether the device is online or offline. You can also save user data such as user preferences, logins and game status and then synchronize that data on the user's device for a consistent experience. Amazon DynamoDB offers a managed and highly available NoSQL database for storing and querying app data by eliminating unnecessary client and content mining downloads. Amazon DynamoDB includes granular access control to follow best practices of minimum privileges for lambda functions that query specific data Mobile Push Notifications Amazon Simple Notification Service (Amazon SNS) is a fast, flexible and managed push notification service that allows you to send push notifications to mobile users, email recipients or send messages to other simple and inexpensive distributed services. Mobile push notifications send messages directly to apps on mobile devices that can be viewed in the mobile app such as message notifications, badge updates, or even audible notification. Disaster recovery planning The underlying AWS services used by the solution provide built-in fault tolerance and high availability using multiple zones of availability in each area to protect against single computer or data center failures. For better understanding visit
Mobile App Developer in Austin
. Conclusion Serverless architectures with PaaS offers from the leading public cloud AWS offers the ability to deploy scalable and available applications without the need for capacity planning and server configuration. The ability to independently scale the web, logic, and data levels allows optimal performance of the overall solution.
3 notes
·
View notes
Text
Five types of hosting that are inexpensive for web design
Individuals can use web hosting services to publish their websites on the Internet. In order to help a website get a good spot on the internet, web hosting firms provide data centre and colocation services at reasonable prices. The websites are typically offered five distinct types of hosting. They consist of:
1. Shared Hosting
Shared hosting is the first of the accessible web hosting options. This is a well-liked hosting strategy because it is very cost-effective and offers the chance to share your server with other websites. The connectivity between thousands of different websites may fluctuate, creating a shared pool of server resources like CPU and RAM. Many services, like disc space, uptime, and bandwidth, are included with shared hosting. The shared website might later be hosted by a reseller, which is one of the advantages of shared hosting.
2. Dedicated Server
Another excellent and inexpensive san antonio web design hosting solution is dedicated server or dedicated hosting. For internet businesses that need a robust server, this hosting model is ideal. Although having a private server with this type of hosting comes with a lot of work, it allows you the flexibility.
A significant proportion of website traffic is also generated by the dedicated servers for your website. It's critical to realize that managed dedicated servers are focused on the on-site content and offer nothing in the way of technical support. You can choose unmanaged hosting on dedicated servers if you have technical know-how and are able to handle problems relating to your website.
3. Dedicated or virtual private servers
The web server resources can be split up into smaller virtual servers using this type of web hosting. Then, these resources are assigned in a way that prevents them from directly affecting the basic hardware. Given that it does away with the problems associated with dedicated servers, virtual private hosting has emerged as one of the most popular and reasonably priced web design hosting services.
In some circumstances, shared hosting can result in a closed environment, but with virtual hosting, you'll have a solution that's tailored to your website. When you need to distribute VPS containers among other servers, for example, virtual web hosting may be the ideal option. When it comes to web hosting, VPS becomes the most customized option because consumers have the choice to reach the host from a different virtual space.
4. Hosting the Cloud
Cloud hosting is one of the newest hosting platforms available among the low-cost web design hosting options. This type of hosting provides website owners with scalable, dependable, and powerful hosting that is built on a cluster of load-balancing servers and utility billing. This hosting solution is appropriate because it has eliminated single points of failure and only charges customers for the services they actually use. It also goes by the name "Cloud Computing."
5. Hosting Grid
The hosting company refers to server clusters as grids, hence the name. By creating several nodes, hosting is accomplished.
Odyssey Design Co start a full-service web design and IT company that offered high-end services for incredibly low pricing. Our skilled team of software engineers and designers will provide you with a wide range of services to fulfill your company's needs for a top-notch website. From completely new, personalized websites to the makeover of current ones, SEO, CMS, and much more, we can offer solutions.
Today, Odyssey Design Co is a rapidly expanding business with offices in San Antonio that provides services to clients. They are specialists in infrastructure management, online application development, and website design.
Visit the website Odyssey Design Co for more details.
0 notes
Text
Cloud Computing: History, Advantages and Preparing
Cloud Computing
Distributed computing is the strategy for conveyance of registering administrations over the web. These processing administrations incorporate capacity, servers, data sets, programming, investigation and that's only the tip of the iceberg. Cloud Computing Training Service in USA is a data innovation worldview that empowers us to get to imparted registering sources to negligible administration exertion. By the assistance of Distributed computing, we can utilize figuring assets online over the web without putting cash in building and keeping up with processing framework. Along these lines, Distributed computing empowers associations to zero in on their center business as opposed to putting forth attempt in building significant level PC foundation. One more incredible advantage of Distributed computing is, it gives "pay-more only as costs arise" or "pay-per-use" model means you want to pay just for the assets you have utilized. It decreases your working costs.
History
The expression Distributed computing right off the bat showed up in 1996 (referenced in a Compaq inside report). Later on, the term was promoted in 2006 as amazon.com delivered its Flexible Distributed computing stage "Amazon web administrations". In mid 1993 the term cloud was utilized to allude to an organization of disseminated processing.
Benefits
The ascent of Distributed computing has offered associations and people various advantages including the capacity to get to any product or assets on any gadget without introducing it on your nearby gadget. Here are a portion of the top advantages.
Adaptability
One of the significant advantages is the versatility. On the off chance that your business needs increment, scaling your cloud assets from far off servers is simple. Thus, Distributed computing is great for organizations with developing requests for assets.
Cost
It diminishes the capital expense of building and keeping up with registering foundation. You can undoubtedly get to any asset through cloud without running nearby server farms and recruit TI specialists for dealing with this huge framework.
Efficiency
On location conventional processing foundation requires a great deal of equipment arrangement and tedious framework the board. It builds your efficiency by eliminating these tedious assignments and empowers associations to zero in on their center business.
Execution
A large portion of the cloud specialist organizations consistently update the administrations to the most recent age to help the presentation and give quick and effective registering administrations. This builds the efficiency of associations who share it's assets.
Pay-per-Use
Another extraordinary advantage is,the suppliers offer you "pay-more only as costs arise" based administrations implies you just need to pay for the administrations you use. This lessens the administration cost of associations.
Security
It gives you a superior security on the grounds that the information is put away in the cloud, you can get to your information and assets from anyplace regardless of whether you've lost your PC. And furthermore you can undoubtedly erase your own information from your lost machine with the goal that nobody can get to it.
Work from anyplace
In the event that you have a web association and a PC in your grasp, you can work from any area by getting to cloud assets over the web. Cloud administrations are additionally offering portable application with the goal that you can likewise get to assets on your cell phone.
Kind of administrations
For the most part, It administrations fall into three classifications for example IaaS (framework as a help), PaaS (stage as a help), and SaaS (Programming as an assistance). These three Distributed computing administrations are at times called the Distributed computing stack since they fabricate a stack as they sit on top of each other. Here is an outline of these three administrations.
Foundation as a Help (IaaS)
Framework as a help is one of the primary classes of administrations. It gives virtualized registering assets like virtual machines, stockpiling, organizations, and working frameworks to people or an association from a cloud supplier.
Stage as a Help (PaaS)
Stage as a help is a classification of administration that gives the stage to designers to construct applications and administrations over the web. PaaS gives the on-request improvement climate for creating, testing, and overseeing programming applications.
Programming as a Help (SaaS)
Programming as a help is a class of administrations gives on-request programming application over the web. Cloud suppliers have and oversee programming application and permit their clients to interface with the application and access the application over the web.
For more details, visit us :
Online Blockchain Training Course in USA
IT Training Classes Online in Delaware
Business Analysis Certification in Delaware
#Security Forensics Training#Cloud Computing Training Service in USA#Microsoft Training Course Delaware#Cyber Security Forensics Training USA
1 note
·
View note
Text
How to begin a tech career with Java
Volunteer to develop Java programs that are free Understanding the main APIs
In today's world, there are a lot of programming languages that will shape your future. Yet, when learning to code, you commence with the C language and proceed to C++ or many other programming languages. You all know that the most popular programming language is Java. The popularity of java online training can be attributed to its versatility, as it can be used to develop customized applications that are light and swift and suit different goals. Below listed are some techniques on how to begin a tech career with Java:
Keep up with the latest java updates:
The only constant in the programming language is evolution. To learn this field, you must expect transformations and keep up with new products. There will be a new framework on demand when you know one framework. The one you are good at may entirely fade from the market. Another possibility is that the most current Java development will repair the problems you see with the current release. You must adapt to the most recent Java developments to get your dream job.
Enhance your coding capabilities:
To attain embodiment, practice, practice, and more practice. Creating confidence is essential for the initial interview method. You must have practical Java experience to fill out Career in Java Development profiles. Codes can be daunting, but you must enhance your coding skills to land a career. Make a rule mandating day-to-day coding. Some information that can be useful includes Competitive coding, partaking or practising in the open-source project website, taking on authentic projects and reading the code of other developers.
Building soft skills:
So distant, you have established a concrete foundation, kept up with the most delinquent technologies, and enhanced your coding abilities, but this is insufficient. To perform as a Java developer, you must boost your soft skills. According to a survey, communication skills are vastly more critical to get your dream career than technical skills, which are only half a percentage as significant. You must enhance your communication knowledge to get your dream job as a fresher.
To construct their websites, many community platforms look for Java web developers. You must perfect your Career in Java Development proficiency before attempting your luck at applying for Java Developer positions. You can accumulate experience by proffering your services as a volunteer to help them build their website.
API is called an Application Programming Interface. A critical component of Java development is APIs. You must understand the language constructs and essential APIs, including Generics, Oddities, Threads, Supplies, and JDBC. In web development, you ought to be knowledgeable about JSPs. JSPs provide you with valuable experience in developing many sorts of applications.
Master Java EE:
Start learning Java Enterprise Edition's basics after completing the Core Java course. Understanding the factors of Java EE aids you perform on web development tasks, as Java EE requires additional attributes like web services and distributed computing. It includes technologies like Servlet, WebSocket, Java Server Faces, etc.
Make projects with JSP & Servlets:
Integrate Java with Front End technologies like HTML, CSS, and Javascript and try accomplishing mini projects in various areas to assist you in developing your skills. Make it a target to generate at least two assignments, one with JSP and the additional one with Servlet. Designing projects like these will aid you in assessing your skills in this programming language.
Learn Spring Frameworks and Hibernate:
The two frameworks are very prevalent among Java developers. They are,Utility of Spring framework: Several Java Development Companies operate Spring frameworks such as Spring Boot, Spring MVC, and Spring Cloud to design web applications.
Utility of Hibernate frameworks: Hibernate is the most sought-after framework for plotting an object-oriented field design to a relational database and the Hibernate Query Language. Learning these frameworks will give you an advantage over others when applying for Java Developer jobs.
Final thoughts:
Java Developer jobs are widespread and have reasonable options. You can achieve more wisdom by undertaking java training online or an internship program in Java. An in-depth understanding of Design Patterns, OOPs, and Polymorphism will be an incredible launch pad to kick-start your career in java development.
0 notes
Text
Chrome remote desktop chromebook

Chrome remote desktop chromebook install#
Chrome remote desktop chromebook full#
Chrome remote desktop chromebook android#
Chrome remote desktop chromebook pro#
This is like all other remote desktop applications where you have to pair two computers using a PIN and then initiate the sharing. And I’ve used it often to provide remote support.Google, following the footsteps of other tech giants, have released a utility named “ Chrome Remote Desktop”. I’ve had clients use it for remote access to desktop apps, as well as remote access to Windows servers. Your experience?Ĭhrome Remote Desktop can be a great way for people to securely access a desktop system.
Chrome remote desktop chromebook full#
If you are the person who intends to provide remote support, you’ll enter the 12-digit code in the “Give Support” section (on the lower portion of the /support page) then select “Connect.” You’ll need to use the full Chrome browser on a computer–not the mobile browser or mobile Chrome Remote Desktop apps–to provide remote support (as of August 2018). This creates a 12-digit code to share with the person you want to allow to access your system remotely. When you request support, you’ll then select the “Generate Code” button.
Chrome remote desktop chromebook install#
If you haven’t yet installed the Chrome Remote Desktop app, the steps in the setup process are similar to those above: Click the button to download the app, install it, allow it to run, accept the terms and install, then allow the download to open and to make changes. Remote Support: One-time sessionĪlternatively, you may configure Chrome Remote Desktop for single-use access, which works well for remote support. You can connect to a system configured for remote access from another desktop Chrome browser or from a Chrome Remote Desktop mobile app. The PIN needs to be at least 6 digits long.įinally, choose “Yes” to allow “Native messaging host for remoting host management.”Īfter you’ve completed the above steps, your system should appear with the name you assigned it, along with a status of “Online.” Even if your Google account user name and password somehow become known, an attacker also would need the PIN to connect. This adds an additional layer of security.
Chrome remote desktop chromebook pro#
SEE: Remote access policy (Tech Pro Research) If you have multiple computers configured for remote access, meaningful names can help differentiate systems. You’ll also need select “Yes” to allow Chrome Remote Desktop to open chromeremotedesktop.msi.Īfter that, enter a name for your computer, then choose “Next.” This is the name that will appear when you open your Chrome Remote Desktop app. For example, on a Windows system, select “Yes,” then wait a few more moments before clicking on the “Accept & Install” message that appears. Then you’ll need to allow the app to install. Next, click the blue button to download the Chrome Remote Desktop app. Then select either “Remote access” or “Remote support” to set up an always-available connection or a one-time connection, respectively. A system running any of those operating systems can serve as a host, from which you can share the screen. And you can install the Chrome Remote Desktop host software on most systems that run Windows 7 (or more recent), macOS 10.9 (or more current), or modern Linux distributions.
Chrome remote desktop chromebook android#
You can control a remote system either with an app (on Android or iOS), or from the Chrome browser (on Chrome OS, Windows, macOS, or Linux). This option gives you a great way to handle remote support or troubleshooting.Ĭonnections work across platforms. The second setup supports temporary remote access to a system with a one-time code. This configuration works well for systems you control that are often (or always) powered on, such as as a desktop (or server). The first configuration lets you connect to a system any time. Top TechRepublic Academy training courses and software offerings of 2022īest project management software and tools 2022Ĭhrome Remote Desktop supports two distinct setups: Always-allowed access or one-time access. Gartner identifies 25 emerging technologies in its 2022 hype cycle Once connected to a remote system, you can view the screen, type, move the mouse, or send a key combination, such as Ctrl-Alt-Del. Chrome Remote Desktop lets you connect computers for remote access.

0 notes