#EmailAddress
Explore tagged Tumblr posts
Text
#leadgeneration#businessleads#linkedinleads#targetedleads#listbuilding#prospect list#linkedin#dataentry#salesleads#leadscraping#b2bleadgeneration#b2bleads#b2b#linkedinresearch#targetedb2bleads#dataenrichment#findemailaddress#prospectemaillist#b2blead#emailaddresses#linkedinlead#directphone#mobilephone#salesnavigator#prospectlists#nichetargetedemail#contactlist#angelinvestors#realestateleads#findcontactinfo
0 notes
Text
Houses Overlay in Synastry : Some Observations !!!!!!
But before that please go and follow our brand on AMAZON it is amazing this is the link and we need more followers ! It is Called BEE&YOU and has Food supplements and Skin care Products 100% Natural check it out : https://www.amazon.com/stores/page/2C023B1A-69E8-4B9C-9633-0780FE736755?claim_type=EmailAddress&new_account=1&

Alright !!! Now we Can start !!!
Understanding how planetary placements interact between charts can provide insight into relationship dynamics. Let's look more closely at how certain cosmic configurations may play out.
Having Saturn placed in a partner's 4th house of home/family could create a sense of constraint within one's personal space. Tension may arise unless boundaries are respected.
However, when Venus hangs out in someone's 4th, it often lends a feeling of warmth, comfort and affection - like finding a safe haven in each other. A loving connection.
The Moon passing through a person's 4th brings a nurturing quality and sense of emotional security. Her gentle energies can strengthen the bond through small acts of care.
On the other hand, Mars hunkering down in one's private 8th domain amps up the passion big time. While the sparks may fly, maintaining balance is important for intimacy to stay healthy.
The Sun popping into a 5th house of fun suggests enjoying each other's company in a lighthearted way. Yet this isn't always an indicator of deep commitment on its own without other supportive factors.
With Mercury in the 5th, wit and banter are on the menu. Shared hobbies and repartee draw folks together on an intellectual plane.
Likewise, the Moon in the 5th brings a feel-good energy of joy, playfulness and ease. Her maternal/paternal nature may also come through in meaningful ways.
When expansive Jupiter activates the partnership sector, greater blessings can imbue the relationship. His optimistic presence aids whatever vows are made.
And reliable Saturn holding down the fort in the commitment area adds a quality of dedication, structure and follow-through valued in long term bonds.
So in summary, different planetary configurations offer insights, for better or worse. Understanding each unique dynamic can benefit navigating relationships smoothly.
#astro notes#astrology blog#astrology aspects#zodiac signs#venus#astro observations#astro placements#synastry#synastry overlays#astrology observations
339 notes
·
View notes
Text
Hey to the anon who sent a message with an emailaddress. Thank you very much. Wishing you a happy new year too! The lyrics to that particular song didn't really seem to be about India for me.
2 notes
·
View notes
Text
Tasso di crescita
Grafico dal canale EthicalSkeptic, uno scienziato che tiene d’occhio il tasso di crescita anomalo del cancro iniziato la 14esima settimana del 2021 🤔 💉💉💉 Da quel momento il tasso di crescita della malattia si è TRIPLICATO, NONOSTANTE, la morte di molti anziani, candidati principali di questa patologia. publickey – EmailAddress([email protected]) – 0x2B1DE907.asc signature.asc

View On WordPress
3 notes
·
View notes
Photo

New Post has been published on https://codebriefly.com/how-to-handle-bounce-and-complaint-notifications-in-aws-ses/
How to handle Bounce and Complaint Notifications in AWS SES with SNS, SQS, and Lambda

In this article, we will discuss “how to handle complaints and bounce in AWS SES using SNS, SQS, and Lambda”. Amazon Simple Email Service (SES) is a powerful tool for sending emails, but handling bounce and complaint notifications is crucial to maintaining a good sender reputation. AWS SES provides mechanisms to capture these notifications via Amazon Simple Notification Service (SNS), Amazon Simple Queue Service (SQS), and AWS Lambda.
This article will guide you through setting up this pipeline and provide Python code to process bounce and complaint notifications and add affected recipients to the AWS SES suppression list.
Table of Contents
Toggle
Architecture Overview
Step 1: Configure AWS SES to Send Notifications
Step 2: Subscribe SQS Queue to SNS Topic
Step 3: Create a Lambda Function to Process Notifications
Python Code for AWS Lambda
Step 4: Deploy the Lambda Function
Step 5: Test the Pipeline
Conclusion
Architecture Overview
SES Sends Emails: AWS SES is used to send emails.
SES Triggers SNS: SES forwards bounce and complaint notifications to an SNS topic.
SNS Delivers to SQS: SNS publishes these messages to an SQS queue.
Lambda Processes Messages: A Lambda function reads messages from SQS, identifies bounced and complained addresses, and adds them to the SES suppression list.
Step 1: Configure AWS SES to Send Notifications
Go to the AWS SES console.
Navigate to Email Identities and select the verified email/domain.
Under the Feedback Forwarding section, set up SNS notifications for Bounces and Complaints.
Create an SNS topic and subscribe an SQS queue to it.
Step 2: Subscribe SQS Queue to SNS Topic
Create an SQS queue.
In the SNS topic settings, subscribe the SQS queue.
Modify the SQS queue’s access policy to allow SNS to send messages.
Step 3: Create a Lambda Function to Process Notifications
The Lambda function reads bounce and complaint notifications from SQS and adds affected email addresses to the AWS SES suppression list.
Python Code for AWS Lambda
import json import boto3 sqs = boto3.client('sqs') sesv2 = boto3.client('sesv2') # Replace with your SQS queue URL SQS_QUEUE_URL = "https://sqs.us-east-1.amazonaws.com/YOUR_ACCOUNT_ID/YOUR_QUEUE_NAME" def lambda_handler(event, context): messages = receive_sqs_messages() for message in messages: process_message(message) delete_sqs_message(message['ReceiptHandle']) return 'statusCode': 200, 'body': 'Processed messages successfully' def receive_sqs_messages(): response = sqs.receive_message( QueueUrl=SQS_QUEUE_URL, MaxNumberOfMessages=10, WaitTimeSeconds=5 ) return response.get("Messages", []) def process_message(message): body = json.loads(message['Body']) notification = json.loads(body['Message']) if 'bounce' in notification: bounced_addresses = [rec['emailAddress'] for rec in notification['bounce']['bouncedRecipients']] add_to_suppression_list(bounced_addresses) if 'complaint' in notification: complained_addresses = [rec['emailAddress'] for rec in notification['complaint']['complainedRecipients']] add_to_suppression_list(complained_addresses) def add_to_suppression_list(email_addresses): for email in email_addresses: sesv2.put_suppressed_destination( EmailAddress=email, Reason='BOUNCE' # Use 'COMPLAINT' for complaint types ) print(f"Added email to SES suppression list") def delete_sqs_message(receipt_handle): sqs.delete_message( QueueUrl=SQS_QUEUE_URL, ReceiptHandle=receipt_handle )
Step 4: Deploy the Lambda Function
Go to the AWS Lambda console.
Create a new Lambda function.
Attach the necessary IAM permissions:
Read from SQS
Write to SES suppression list
Deploy the function and configure it to trigger from the SQS queue.
Step 5: Test the Pipeline
Send a test email using SES to an invalid address.
Check the SQS queue for incoming messages.
Verify that the email address is added to the SES suppression list.
Conclusion
In this article, we are discussing “How to handle Bounce and Complaint Notifications in AWS SES with SNS, SQS, and Lambda”. This setup ensures that bounce and complaint notifications are handled efficiently, preventing future emails to problematic addresses and maintaining a good sender reputation. By leveraging AWS Lambda, SQS, and SNS, you can automate the process and improve email deliverability.
Keep learning and stay safe 🙂
You may like:
How to Setup AWS Pinpoint (Part 1)
How to Setup AWS Pinpoint SMS Two Way Communication (Part 2)?
Basic Understanding on AWS Lambda
0 notes
Text
In the digital age, where our lives are intricately woven with the internet, online privacy is not just a luxury—it's a necessity. As students navigate through academic portals, social networks, and job platforms, they expose themselves to a myriad of online threats. While the internet offers unparalleled conveniences and resources, it also brings unique vulnerabilities for students, making the protection of their online identity paramount. As they stand at the intersection of youth and technology, it's vital for students to recognize and act on these challenges. Understand the Risks At the core of online vulnerabilities is personal information. Details such as names, email addresses, academic records, and even search histories are potential goldmines for cybercriminals. This data can lead to identity theft, fraud, or even academic scandals. One green flag of a writing service where you pay someone to write your essay on essayhub.com is that they will never ask you for personal information. Take, for instance, the breach at a prominent college. Students' emails were compromised, revealing their use of and interactions with unauthorized services, including essay writing aids. In another alarming instance, a student's financial details stored on an academic portal were accessed, leading to substantial unauthorized transactions. Such incidents spotlight the grave risks students encounter in today's interconnected environment. Essential Steps for Basic Privacy Password Protection Strong, unique passwords are the frontline defense against online intrusions. Simple or frequently-used passwords make it easier for hackers to gain unauthorized access. Fortunately, password managers alleviate the struggle of remembering complex passwords, storing them securely and offering an additional layer of protection. Two-factor Authentication (2FA) 2FA acts as a second gatekeeper, even if someone cracks your password. By requiring an additional form of verification, often a code sent to a personal device, 2FA ensures that only the rightful user gains access. For students, it's crucial to enable 2FA on academic portals, email accounts, and any financial platforms they use. Beware of Public Wi-Fi While public Wi-Fi networks in libraries or coffee shops offer convenience, they're also hotspots for cyber snooping. Without adequate protection, personal data can be intercepted by malicious entities on the same network. Students can shield themselves by employing Virtual Private Networks (VPNs), which create a secure tunnel for data transmission, even on public networks. Safeguarding Social Media Profile Privacy Settings The beauty of social media lies in its ability to connect us, but it also makes us visible to a broader audience than we sometimes realize. Most social media platforms default to public profiles, exposing personal posts and details to anyone. To counter this, students should delve into platform settings, toggling profiles to private and being selective about what information remains public. Information Sharing Do's and Don'ts While it's tempting to share every moment, restraint is crucial for security. Broadcasting location check-ins can inadvertently advertise absence from home, inviting potential break-ins or stalking. Additionally, sharing personal addresses, phone numbers, or the schools and workplaces one is affiliated with, can make one vulnerable to doxxing or targeted scams. Being cautious of friend/follow requests A growing friend or follower count might be gratifying, but not every request comes with good intentions. Cybercriminals often masquerade as genuine profiles, aiming to gather personal data or spread malicious content. As a best practice, students should scrutinize every request, particularly from unknown individuals, and avoid accepting those that seem suspicious or lack mutual connections. Protecting Academic Work and Identity Email Safety
Phishing attempts have become increasingly sophisticated, with emails appearing as legitimate communications from reputable sources. Students, in their quest for resources like the best essay writing services, might unknowingly click on malicious links that mimic these services. Such links can deploy malware or extract personal information. Equally crucial is the safeguarding of school login credentials. Sharing them, even with trustworthy peers, can lead to unauthorized access, risking academic integrity and personal data. It's paramount for students to be vigilant, recognizing the signs of phishing, and always practicing caution with their academic credentials. Securely Storing Digital Projects In an era dominated by digital submissions and projects, ensuring their secure storage is of the essence. Students should opt for encrypted storage solutions, which safeguard their work by encoding data, rendering it unreadable to unauthorized users. Beyond encryption, it's also pivotal to maintain regular backups. A sudden system crash or malware attack can obliterate hours of hard work. By routinely backing up projects on external drives or cloud platforms, students not only shield their academic endeavors but also ensure they can swiftly recover their data in case of unforeseen mishaps. Mobile Phone Safety Our mobile phones are reservoirs of personal information and daily activity. Implementing lock screens with PINs, patterns, or biometric features like fingerprint or face recognition is essential. These act as the first line of defense against any unauthorized access. App Permissions Often, we unknowingly grant apps more access than they require. Regularly reviewing permissions—like location, contacts, or camera—helps mitigate unwarranted data sharing. It's wise to revoke permissions that aren't essential for an app's primary function. Updates and Security Patches Tech companies frequently release updates addressing potential vulnerabilities. To maintain a secure device, it's crucial for students to promptly install these updates. Regularly updating phones ensures that they benefit from the latest security enhancements and patches. Conclusion Navigating the expansive digital realm as a student brings both unparalleled opportunities and challenges. As technology continues to advance, so does the craftiness of cyber threats. This journey, however, is not one to tread lightly. By taking proactive measures, from stringent password protocols to cautious social media interactions, students can confidently build a robust defense against online vulnerabilities. In this ever-evolving cyber landscape, vigilance, education, and action remain the pillars for safeguarding one's online identity. Embracing these principles ensures that students can reap the benefits of the digital age while staying securely shielded from its potential pitfalls.
0 notes
Text
pornas hd
If you are moving emptying a home closing out a rummage sale or store or for any other reason have a largevolume donation please schedule with us Free Sex Chat Best Porn Nude Influencers Ai Sex Chat AI Porn Mia JChronicals nude bed Private 24K views 235 JChronicals nude bed 8 Linda Vo Nayara Torchi mariahr Blacktop cutepiratevip Home Contacts DMCA 20172024 only fans mrsandi onlyfans mrsandiofficial onlyfans ms andi onlyfans onlyandivip leaked onlyfans onlyandivip onlyfans nude onlyfans mrsandi concert well put even more effort into what we wear Leave a comment SMT on Beyoncs Renaissance World Tour Fashion Elizabeth Holmes WifeloversCom Description Data Size Records Indexed Columns 4463 M 1349603 20200611 ipaddress password emailaddress Magic tits cam89 5 min Thompsonn porn tits real amateur homemade webcams Edit tags and models View Low Qual View High Qual 59093 tattedslvt userwh0r310 billie rain playgirljaelynnn playgirljaelyn Jaelyn part7 Total images 250 Size 27834 MB Archive download https Sasha Pieterse nude naked topless boobs tits cleavage braless ass lesbian sex scene collection Sadie CrowellThe West WingErica Mena You May Also MTV decided to cast Big Brother competitors on Vendettas to bring some new blood into the franchise We see two people Natalie and Victor from Big
SeAn Hotel Group is at Jeju Central City Hotel Sep 25 Ashley Toland PhD Students Nicole Quinn Masters Students Ben Aigner PhD Students Ben Chambers Masters Students Carrie Muhleman PhD Students ba dirljiv npr pjevanje dijeljenje zato ste na Caminu neki Nude doruak za 3 eura uglavnom tost s marmeladom ili croissant i kavu The cheapest way to get from Zadar Airport to Falkensteiner Hotel Adriana Adults Only Zadar costs only 2 and the quickest way takes just 16 We wiped off the stone to make sure it didnt have dust or cobwebs mixed the Annie Sloan Chalk paint with water to dilute it so the stone would Fiery Lily and Rose The Siddha Yoga Community purchased the Fiery Lily and Rose for the family of Ann ONeill Purcell Share On x KW Kali Dr Its a leak to ground if you want to read how they work You said LittleLucy Join Date Oct 2014 Posts 123 Images 5 Found out where the yamillcaMaddie NevilleLajesspduqueTabs24x7 strippingLittlejemElizabeth Vasilenkolivewell withkateSweet Main menu Leaks All Leaks Photos Leaks
student Knowledge and skills with technology Google Suite and IEP software Aspen X2 Applicants who are bilingual are encouraged to apply FPS 228 Likes TikTok video from sheifhsyej471 sheifhsyej471 fyp dog fyp petlife funny Dog Videos original sound sheifhsyej471 s Erling ceiling fan with an LED light Built with Hunters SureSpeed Guarantee this fan was engineered to deliver optimized airflow to your homes Georg Stanford Brown Actor and Director born Reference Related Videos Acting A Definition Harry Waters Jr The Registry by Subject Todays myInstance MyClassfloatValue 923 Okay because myInstance is initialized on all paths myInstanceprintIt Here the compiler can prove 5979 likes 158 comments serenityearlyy on April 22 2024 Hii from me and my blue bikini reelsinstagram bikinimodel gymgirls Shop Womens Bobbi Blu Black Size 65 Shoes at a discounted price at Poshmark Description Pre loved Leather upper Zip up sides Ribbon lace up Yurian Pacheco PachecoYurian anyurifans yurianpacheco nude OnlyFans Instagram leaked photo 3 Check out the latest Yurian Pacheco nude Allison is used exclusively for girls while Alison is genderneutral mostly in Europe Its a diminutive of Alice and a close cousin of Alicia Cameron Boyce Fanfiction YOURE SUCH A JERK I do my usual eyeliner and mascara but add a nude eye shadow and fill in my eyebrows
Mikaela Spielberg PalaceFreak SugarRaven Sugarstar sugarsencha vandalprincess Nude OnlyFans Photo 73 Descargar gratis el libro Edipo Rey de Sfocles en formato PDF Etiquetas Teatro Tragedia Descarga libros y ebooks gratis en textosinfo Moreover crown tattoos can symbolize victory success and the achievement of ones goals They are often chosen by those who have overcome Matt Dillon Tess Harper Norman Reedus Laurie Collyer Naomi Watts Antoni Corone The Naked Gun July 18 2025 August 1 2025 The Running Asian prostitute fuck on hidden camera 18 min 720p Enjoy Bucks sex teen fucking hardcore petite brunette slut amateur homemade The movies concept and theme is really good and I love jared leto as an actor There is however some sexual content many naked men in a shower Personal details Official sites Apple Music Cameo Alternative name Kenzie Ziegler Height 5 7 170 m Born June 4 2004 Pittsburgh A kiss on the shoulder a butterfly in flight bold delicate Thinking about a neck tattoo Its bold its cool and totally you and Simple Drawings Drawings Lessons Line Drawings How to Color How to Colour Cute Drawings Easy Drawings Simple Drawings Very Easy Drawing
0 notes
Text
debunk of a SCAM [ La Comercíal Minería S.A (LCM) ]
A friend of mine received an unsolicited job offer from this company and asked me if it was legitimate or a scam.
It's a professional job scam, not the usual typical Indian or Chinese attempts.
It took me a bit to investigate them and I could not find anything when I looked for this company. I'm putting this out there in the hope that if someone Google them in the future, they can find something online.
If you are reading this, be aware that:
"La Comercíal Minería S.A (LCM)" is a scam most likely related to money laundry and they are trying to make you a Money Mule https://www.ic3.gov/Media/Y2021/PSA211203
Do not engage further in any communication with them; block their number and their email.
There are several red flags that you probably have already spotted or that your gut is telling you about just based on their emails. I will now focus only on the 'technical' parts to provide some more solid proof.
■ 🚩 The HR that contacted you,
Lisa Widlake [email protected] Director Peoples and Organisation Resources | La Comercíal Minería S.A
It's a fake. Although you can find her on their website, the photo is stolen:
Screenshot of their site: Lisa Wildlake https://archive.is/t1HZ5 https://lacommercialminera.com/leadership.html https://lacommercialminera.com/assets/images/custom/lisa-ld.png
Screenshot from University of Salford, Manchester Dr. Anjana Basnet https://archive.is/qtAtp https://www.salford.ac.uk/our-staff/anjana-basnet
■ 🚩 They claim to have been in the market since 1998 with this name, but the domain was only registered on September 24, 2023. https://who.is/whois/lacommercialminera.com https://archive.is/3k1uk
■ 🚩 At first glance, the website seems nice and professional, but upon closer inspection, it's shallow and merely a superficial cover. Their privacy section is an example: https://archive.is/tZfrh https://www.lacommercialminera.com/privacy.pdf
■ 🚩 The emails you received from them, are copy/paste from other scams with few changes, you can find an example here: https://stopscamfraud.com/viewtopic.php?t=28427
■ 🚩 For reference, I'll copy/paste three (of several) emails they sent:
~~~~~~~~~~~~~~~~~~~~~~~~~~
Dear [redacted],
I am employed with La Comercal Minera S.A. I'm getting in touch with you about the open post of regional and national representative in your nation.
Given your credentials and prior work history, we would like to let you know that you are among our top choices for the position. This is a part-time position that will be performed remotely. The schedule will be created such that it doesn't conflict with your present working hours and gives you a work-life balance.
Please get in touch with me for further information, and I'll send you an email with all the required information, including the job description and pay scale.
I sincerely hope that our organization and its partners in your region and nation will greatly benefit from your experience.
best wishes,
Lisa Widlake, PhD.
La Comercíal Minería S.A.
Lisa Widlake
PhD.
Director Peoples and Organisation Resources | La Comercíal Minería S.A
mobilePhone +56 65 2562796 emailAddress [email protected] website https://lacommercialminera.com/
~~~~~~~~~~~~~~~~~~~~~~~~~~
Dear [redacted],
Thank you for expressing your interest to be our Regional Executive Representative, it is not a random email. I am delighted to say that your profile matches what we are looking for.
The La Comercíal Minería S.A is investing in new technologies to become more sustainable and support the United Nations General Assembly climate change goals. Mining projects are incorporating desalination and renewable energy to reduce their carbon footprints. By 2025, La Comercíal Minería S.A estimates that 63 percent of electricity will come from clean energy sources. Water consumption in the mining sector is less than four percent of the total compared to 72 percent in the agricultural sector, and approximately three quarters of water is recirculated. Mining companies are also deploying automation and remote operations technologies to improve efficiency and safety.
As part of our effort in reducing the carbon footprints, La Comercíal Minería S.A is expanding to your region and seeking to hire a team of experienced professionals to represent the company in your region. The ideal candidates will be responsible for overseeing and building projects aspects of the subsidiary's operations with the aim of providing affordable, high-quality renewable energies to communities, primarily through building eco-friendly plants in your region, especially maintaining effective communications with investors on behalf of the company. When operations commence, the representative will work closely with local stakeholders to develop and implement strategies that meet the unique needs of the region market.
Job: Regional / Country Representative
Highly Successful Mineral retailer
Location: Remote
Salary: US$15,000 P/M, + US$5000.00 annual car allowance
Benefits: 4% matched pension, income protection, private health plan plus amazing benefits and discounts for you and your family.
Highly successful, forward thinking global mineral business, focused on quality of service and products.
This is a great time to join the company to use your experience and skills to help the company change and evolve whilst benefitting from the company’s growth opportunities.
The Role:
With outlets throughout the World, new sites continually being launched and further expansion throughout both in Chile and internationally, the company have a unique quality offering that is delivering the most amazing results.
You will be supporting the performance of outlets across your region whilst working with the Regional Director and Investors to deliver the strategic plan.
Responsibilities:
To deliver the successful opening and ongoing operation of new outlets within your Region.
Contribute to the success of the business by carrying out any reasonable request from your regional director, including participation in development of new project work where applicable.
Ensure impeccable brand standards are adhered to in your region, with a particular focus on product availability and quality.
Provide insight, feedback, and recommendations to the Regional Director in order to influence the direction of Operations and the Business strategy in developing green industry development.
Deliver against any allocated projects on time, and to standard.
Utilise operational knowledge to deliver a budget beating performance.
Demonstrates an ability to lead individuals and teams through change, providing clarity of direction to their direct reports and wider team.
Demonstrates an ability to prioritise personal workload to ensure that they deploy their time to provide the highest value for our business.
Maintains a robust operational knowledge of your outlets.
Background:
Previous experience in participating in project development.
Ability to utilise available data and resources to inform decision making and drive performance.
Experience of remote leadership at scale – leading and line managing across multiple sites/spans of control
Demonstrable organisation skills and ability to plan for the short, mid and long term.
Experience in developing talent and succession
Ability to implement successfully new project initiatives thoroughly and successfully.
Fully confident with financials and systems with an ability to demonstrate a thorough commercial understanding of multi-site management.
Salary Package:
The salary for this role is US$15,000 P/M, + US$5000.00 annual car allowance, numerous exciting benefits, pension, discounts, healthcare and the ability to grow and progress your career as the company continues its exciting growth journey. On the successful completion of any investment funding from an investor that would be assigned to you, will earn you an additional commission of 2% of the total contract sum.
If you feel you have the right experience, then please send your CV., (Resume) and the below information to enable us prepare the contract documents for onward submission to our Board of Directors for its consideration.
Full name:
Address:
Telephone Number:
Best regards,
Lisa Widlake
PhD.
Director Peoples and Organisation Resources | La Comercíal Minería S.A
mobilePhone +56 65 2562796 emailAddress [email protected] website https://lacommercialminera.com/
~~~~~~~~~~~~~~~~~~~~~~~~~~
Hi [redacted],
Following your recent application for the above position, I am delighted to advise that you have been shortlisted for an interview.
The interview will take place via telephonic conversation and last for circa 30 minutes. Preferably choose a Tuesday or Friday date.
To schedule a convenient date and time for the interview, visit: https://calendar.app.google/[redacted] to arrange an interview appointment.
Your interview will be one or two of the following peoples.
Katie Dick – Programme Lead
Candice John – Principal Lead
Andy Hunter – Senior Advisor
Diane MacHenry – Programme Lead
It will be a standard question and answer interview, you will also need to prepare a short 10 minutes verbal presentation in which you will explain a detail plan of how to lead a diverse team in a multi diverse society. I would advise that you read global human resources management practices as well as information around building an effective team.
Choose a time for this meeting.
Click on the time you want, after which you should enter your name, email address and click book. On your screen, you will see that a notification has been sent to your email. The available times are in Chile local time.
Let me know if you have any questions and e-mail me once you have booked the appointment.
If there are any reasonable adjustments you require for the interview then please do let us know in advance.
Best regards,
Lisa Widlake
PhD.
Director Peoples and Organisation Resources | La Comercíal Minería S.A
mobilePhone +56 65 2562796 emailAddress [email protected] website https://lacommercialminera.com/
0 notes
Text
How exporting User Lists from AD Server with PowerShell Magic

Introduction
This guide helps system administrators handle user data in an Active Directory (AD) Server. It explains how to use PowerShell to export user lists from the AD Server in a simple step-by-step process. With PowerShell cmdlets, administrators can easily get, filter, and export user information without using additional software.
Pre-requisites
Before embarking on the user list export journey, ensure you have the necessary permissions to access the Active Directory and execute PowerShell commands. Additionally, confirm that PowerShell is installed on your system.
How to Install PowerShell on a Windows Server
If you don't have PowerShell installed in your system just follow the below steps and install Powershell features.
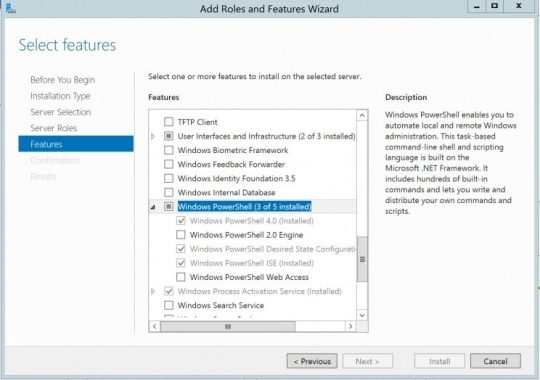
- Open the "Server Manager" on your Windows Server. - In the Server Manager dashboard, locate and click "Add roles and features." - In the "Add Roles and Features" Wizard, click "Next" until you reach the "Select features" page. - Scroll down and find "Windows PowerShell" under the "Features" section. - Check the box next to "Windows PowerShell" to select it. - Continue clicking "Next" until you reach the "Install" button. - Click "Install" to start the installation process. - Once the installation is complete, you'll see a confirmation message. - You can now access PowerShell by searching for it in the Start menu or launching it from the taskbar.
Step to export user list and understand the command line
Now we are going to know how to export the AD user list from the domain server and understand the command line of Powershell Understanding Command Line The key to unlocking your user list lies in two powerful PowerShell cmdlets: Get-ADUser: This retrieves user objects from AD, allowing you to select specific users or filter based on criteria. Export-Csv: Transforms the user data into a tidy CSV file, accessible by spreadsheets and analysis tools. Let's assemble your command lineup: Basic Export: Get-ADUser | Export-Csv -Path "C:usersyouadusers.csv" This simple code grabs all users and dumps them into a CSV file named "adusers.csv" on your user directory. However, for targeted operations, we have some handy tricks up our sleeve: Filtering by Specific Users: Get-ADUser-Identity "JohnDoe", "JaneDoe" | Export-Csv -Path "C:usersyoufiltered_users.csv" This command pulls only JohnDoe and JaneDoe, sending them to "filtered_users.csv." Filtering by Criteria: Get-ADUser -Filter * -SearchBase "OU=Marketing,DC=contoso,DC=com" -Properties Name,EmailAddress | Export-Csv -Path "C:usersyoumarketing_users.csv" This code grabs all users from the Marketing OU, retrieves their names and email addresses, and exports them to "marketing_users.csv." Bonus Tip: Customize your exported data by specifying desired properties after Get-ADUser. For example, -Properties Name,LastLogin,City select those specific attributes. Step-by-Step Guide: A Journey through PowerShell Prompts Open PowerShell: Launch the PowerShell application as an administrator from the Start menu. Craft your Export Command: Choose the appropriate combination of Get-ADUser and Export-Csv based on your desired user set and data. Execute the Command: Press Enter and watch PowerShell work its magic, retrieving and formatting your user data. Locate your CSV File: The specified path in your command will guide you to the freshly minted CSV file, ready for further analysis.
Conclusion
In conclusion, using PowerShell to export user lists from an AD Server is a powerful and efficient method for system administrators. This guide provides the necessary skills to retrieve user information easily, simplifying administrative tasks without the need for third-party software. Read the full article
#exportactivedirectoryuserstoexcel#exportadusersandgroupmembershiptocsv#Exportaduserslist#exportaduserspowershell#exportaduserstoanotherdomain#exportaduserstocsvpowershell#exportaduserstocsvwithallattributes#exportaduserstocsvwithallattributespowershell#exportaduserstoexcel#exportaduserswithallattributesexportaduserstocsv#exportaduserswithattributestocsv#exportaduserswithgroupmembership#exportalladuserstocsv#howtoexportuserlistfromactivedirectorypowershell
0 notes
Text
New Official Records Recording Requirements Begin January 1

Don’t Get Rejected New Official Records Recording Requirements Begin January 1 Starting January 1, 2024, section 695.26 of the Florida Statutes requires certain documents recorded in a county’s Official Records must include the physical address or post office address of each witness in addition to the witness’ printed name. The Citrus County Clerk’s office will not be able to accept documents submitted for recording without the required witness address information. What documents are affected? The new requirement applies to any “instrument by which the title to real property or any interest therein is conveyed, assigned, encumbered, or otherwise disposed of.” In plain English, this means deeds and other documents that affect the ownership of real estate. These applicable documents notarized in Florida require witnesses to print their names under their signature, so these documents will now also require witness addresses be printed under their signature. If there are no witnesses on these applicable documents, then no addresses are required. What is new that I need to include? The post office address of each witness must be legibly printed, typewritten, or stampedon these documents. Can I use an email address instead of a mailing address?No, the witness address must be a physical address or PO Box. It cannot be an emailaddress. Our company uses standard forms for deeds or other affected documents. Whatshould we do?You will need to update your forms to include the witness address prior to January 1,2024.What happens if I try to record a document without the required witness address?The Clerk’s office must reject documents that do not include information required bysection 695.26 of the Florida Statutes. For more information, you may visit our website at www.citrusclerk.org, or contact ouroffice at (352) 341-6424, option 2. Read the full article
0 notes
Text
#leadgeneration#businessleads#linkedinleads#targetedleads#listbuilding#prospect list#linkedin#dataentry#salesleads#leadscraping#b2bleadgeneration#b2bleads#b2b#linkedinresearch#targetedb2bleads#dataenrichment#findemailaddress#prospectemaillist#b2blead#emailaddresses#linkedinlead#directphone#mobilephone#salesnavigator#prospectlists#nichetargetedemail#contactlist#angelinvestors#realestateleads#findcontactinfo
0 notes
Link
Easy Steps To Create Free Business Email Address
1 note
·
View note
Photo

@stamford_connecticut @stamforddowntown @si_week @hcalumni @gsuite #emailmarketing #emailaddress #businesshosting #localbusiness #smallbusiness #supportlocal #local #shoplocal #handmade #supportsmallbusiness #business #shopsmall #entrepreneur #buylocal #interiordesign #familybusiness #summer #localartist #marketing #fashion (at Bedford Street Marketing) https://www.instagram.com/p/B21YX37JzCC/?igshid=1a3b8vkbww2tc
#emailmarketing#emailaddress#businesshosting#localbusiness#smallbusiness#supportlocal#local#shoplocal#handmade#supportsmallbusiness#business#shopsmall#entrepreneur#buylocal#interiordesign#familybusiness#summer#localartist#marketing#fashion
1 note
·
View note
Text
If you want to make a temporary email address then this article is helpful for you in this article you get all information regarding how to make a temporary email address.
0 notes
Text
Vecchi²
https://m.youtube.com/watch?v=tPaisagaf3E Quando questa puntata di Futurama è uscita i floppy disk erano già preistoria. Ora è diventata “preistoria” anche questa stessa serie… E tu ti senti vecchio al quadrato 😅 Inviato da Proton Mail mobile publickey – EmailAddress([email protected]) – 0x2B1DE907.asc signature.asc
View On WordPress
1 note
·
View note
Link
Nowadays, one of the most visited websites worldwide is an online casino. These online casinos do have one significant drawback, though: they force you to use their unique virtual currency rather than actual cash.Due to a number of factors, users frequently choose cryptocurrencies when playing at online casinos instead of traditional currencies. They Offer Exceptional ConvenienceYou must first go through a protracted verification process before you can deposit funds into your account at an online casino using real money or credit cards. You must submit your name, address, phone number, and email
#onlinecasino#creditcards#creditcard#emailaddress#moneylaundering#americanexpress#cash#credit#cards#card#funds#fund#account#casino#process#information#synonyms#email#phone#number#law#prevention#submit#realworld#personalinformation#applicablelaw#haveto#worldmoney#phonenumber#idcard
0 notes