#Ethical Hacking Training Course
Explore tagged Tumblr posts
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
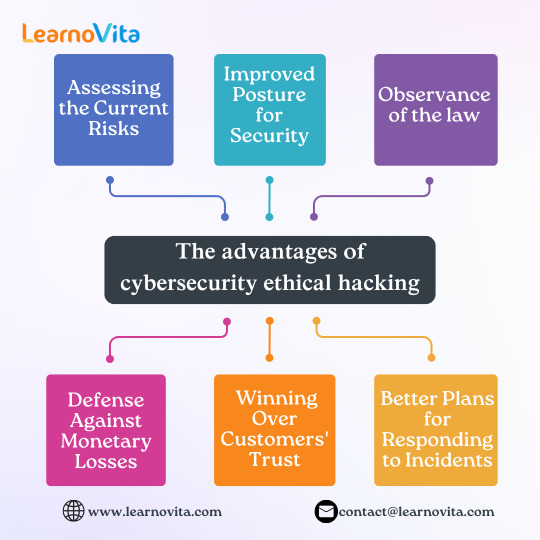
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text

Join Kochi’s trusted institute for a certified cybersecurity course. Learn from pros and get industry-ready.
1 note
·
View note
Text
Kickstart Your Tech Career with a Cyber Security Diploma in Mississauga

Looking to enter the world of cybersecurity? Enroll in a Cyber Security Diploma in Mississauga and gain hands-on training in ethical hacking, network security, and cyber risk management. This program equips you with the in-demand skills needed to protect digital systems and launch a rewarding tech career in Canada.
#Cyber Security Diploma#Mississauga Colleges#Tech Career Canada#Cybersecurity Training#IT Diploma Programs#Ethical Hacking Course
0 notes
Text

Six months of ethical hacking training in the areas of cybersecurity basics, vulnerabilities of network and systems, wireless and web security, and preparation for CEH exams using lab sessions and actual techniques.
#Ethical Hacking#Ethical Hacking Course#Learn Ethical Hacking#Ethical Hacking Training#Ethical Hacking Certification
1 note
·
View note
Text
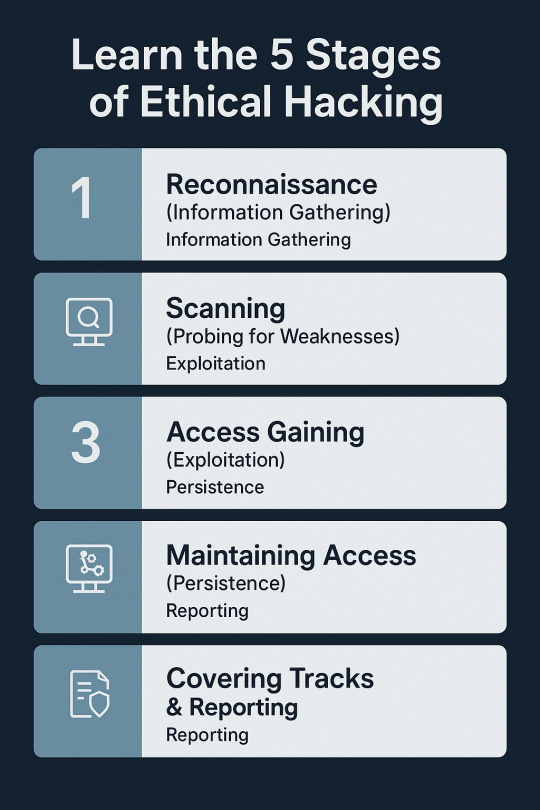
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Best Cyber Security Courses in UAE – Smartzett Academy
Upskill your career with Cyber Security Courses in UAE at Smartzett Academy. Our training by industry experts includes ethical hacking, network security, and risk management, imparting you with coveted skills. Obtain industry-recognized certifications and practical experience to lead the digital security industry. Join now!
#Cyber Security Courses in UAE#Ethical Hacking#Network Security#Cybersecurity Training#IT Security#Smartzett Academy#Online Security Courses#Cyber Threat Management
0 notes
Text
Basic Computer Course in Jalandhar | Learn Essential Skills

Join the Basic Computer Course in Jalandhar to learn MS Office, internet basics, typing, and more. Get hands-on training with expert guidance! 🚀
#aws training in jalandhar#digital marketing company in jalandhar#Content Writer / Copy Writer#45 Days Industrial training#Ethical Hacking Course
0 notes
Text
0 notes
Text
Indian Institute of Computer Science (IICS) is Delhi's leading IT training institute, offering a wide range of affordable programs and courses to empower learners with essential technology skills. With expert instructors and practical training in areas like AI, programming, web development, and more, we aim to prepare students for thriving careers in the tech industry. Join us to build your future in IT!best software engineer courses in Delhi
#Graphic Designer Course in Delhi#Best ethical hacking institute in Delhi#best cyber security institute in delhi#Web Development Course in Delhi#Advanced computer institute Delhi#Multimedia and Animation Classes in Delhi#IT training institute in delhi#Computer Courses and Classes in Delhi#Best e-accounting institute in Delhi#computer course with placement#Best computer education institute in Delhi
0 notes
Text
Learn ethical hacking online with Hacker computer school: the definitive guide

Cybersecurity is an essential in this digital world. Cyberattacks, data breaches, and hacking incidents have increased manifold, and along with these rising incidents, there has been a significant rise in the demand for ethical hackers. If you are a one who loves entering into such an exciting field, learning ethical hacking is an outstanding place to start from. Hacker Computer School stands tall, providing live classes, as well as recorded classes that you can access from anywhere in the world.
Why Learn Ethical Hacking? Before diving into the specifics of the Hacker Computer School, let’s quickly explore why ethical hacking is a valuable skill in today’s world.
Cybersecurity Jobs are in Demand: Just as technology evolves, so do the methods of cybercriminals. Ethical hackers, also known as white-hat hackers, identify vulnerabilities before malicious actors exploit them. Therefore, this is a very sought-after skill.
Lucrative Career Opportunities: Ethical hackers receive a very good salary in financial, healthcare, government, and technology sectors. An ethical hacker with the right set of skills and proper certification can command some very excellent remunerations and enjoy job stability.
Hands-on Training: Ethical hacking is much more than just a theoretical science; it’s much more about practical skills and experiences. Training in ethical hacking means experiencing real-world scenarios and practicing the art of spotting vulnerabilities, securing networks, and protecting sensitive data. Why Hacker Computer School for Ethical Hacking? Hacker Computer School is one of the best online websites to learn ethical hacking. Here’s why: 1. Live Classes with Expert Instructors Hacker Computer School allows you to enjoy live classes in which you can interact with your instructors in real time. Such instructors are not only teachers; they are experienced cybersecurity professionals who have worked on hacking projects. The live classes allow you to ask questions, clear doubts, and participate in discussions that improve your understanding of the course. There are many benefits offered through live classes.
Interaktive learning: Interaktion with lecturers und fellow students in real time Personalized attention: Address the questions and troubleshoot issues live
Dynamic learning: On the latest trends in the field of cybersecurity and ethical hacking
2. Pre-recorded classes for adaptive learning Hacker Computer School also provides you with recorded classes so you can learn at your own time. If you could not attend a class session or you want to hear it again, you can watch the recorded sessions. In this case, this style is very ideal for persons with other commitments or personal preferences that make them study at one’s own pace.
The advantages of the recorded classes are:
One can learn at any convenient time and place. Replay and review: Replay the lessons as many times you need to ensure that the most important concepts are in your head. Self-directed learning: Your learning experience is based on your schedule.
3. Hands-On Practical Experience Ethical hacking is more practical and not just a theory. Hacker Computer School has labs, virtual environments, and real-life scenarios that will put your skills to the test. Penetration testing, vulnerability scanning, ethical hacking tools, and network security protocols will be learned in this curriculum.
4. Broad Curriculum Hacker Computer School has an all-rounded curriculum which is inclusive of all aspects necessary for ethical hacking. Whether just starting, or you find yourself in the need to heighten already existing skills. The programs at the computer school are streamlined to ensure not only that you get where you are, but also take them through various advanced levels.
Some key topics you can expect in your studies consist of;
Introduction to Ethical Hacking: understanding the basics, legal implications, and ethical considerations.
Networking fundamentals: Learn about IP addresses, TCP/IP protocols, DNS, firewalls, and much more.
Footprinting and reconnaissance: Techniques for collecting information on a target.
Penetration testing: Testing network security by simulating cyberattacks
Web application security: learn how vulnerabilities in web applications occur and how to strengthen it
Cryptography: Learn about encryption and decryption techniques that can protect information.
Security tools: Master industry-standard tools like Metasploit, Nmap, Wireshark, and Burp Suite.
5. Learn from Anywhere The best aspect of Hacker Computer School is that you can learn anywhere in the world. You don’t need to be at any specific location; you may be sitting at home, inside a coffee shop, or on a vacation, yet you’ll just need a connection to the internet. This means you can then access live classes, recordings of lessons, and hand-on labs. It really is suitable for students and professionals, or anyone desiring a career change towards cybersecurity. Course format and Certification The courses at Hacker Computer School are designed to take you from beginner to advanced level. Upon completion of the course, you will be rewarded with certification, which is quite helpful in your resume and proof of your expertise in ethical hacking.
Certification benefits you in the following aspects:
Gain credibility in the cybersecurity industry.
Your chances of getting a job are improved, and your potential for salary increases. Show off your skills to potential employers. Why Online Learning is the Future of Ethical Hacking
While there is much to be said for the traditional classroom, online learning offers flexibility, accessibility, and an awful lot of resources that can meet the needs of the students interested in ethical hacking. On such online platforms as Hacker Computer School, students can:
Learn at their own pace: Online courses enable one to learn at their pace, hence it becomes easier to balance other commitments. Global access to experts: You get to learn from the best teachers and security experts in the world. Connect with others: There usually are forums and discussion boards on the online platform where you can connect with other learners, share your ideas, and seek assistance.
Ethical hacking is among the most valuable skills in the ever-growing field of cybersecurity. Hacker Computer School’s live and recorded classes will bring you flexibility and expert guidance that will help you master ethical hacking and drive a successful career in cybersecurity.
Hacker Computer School offers practical, hands-on experience and full curriculum at the feet of top-flight instructors. That makes it extremely easy to learn ethical hacking from anywhere in the globe. Whether you are a professional or just an amateur, there always is something to learn there in ethical hacking.
Getting started today can be achieved by taking that first stride towards becoming an ethical hacker with Hacker Computer School.
Official website - Online Cyber Secyrity Training Live - CEEH | KLSFP | MCSD | Black Hat | Python 101
Official website - Home | Cyber Security Course
#online ethical hacking course#online ethical hacking training#online cehv13 training#online hacking course#online cybersecurity course
0 notes
Text
Why 2025 Is The Perfect Time To Start Your Ethical Hacking Journey

The technological environment is growing at an alarming rate, and, as businesses move further into the digital age, they must rely on technology to store so much data. This growth brings with it the ever so looming risk of cyber attacks and this is why ethical hacking is so valued. For anyone considering cyber security as a profession, it cannot be any better time than 2025 to begin your ethical hacking.
#cyber security ethical hacking certification#ethical hacking course with certificate#certified ethical hacker certification training#certified ethical hacker#certified ethical hacker certification#ethical hacking course#certified ethical hacker course#best ethical hacking course
0 notes
Text
In this episode, we dive into the importance of ethical hacking training in Dubai and explore how Cyber Security and Ethical Hacking Certification Courses in Dubai can empower professionals to protect businesses from cyber threats. Tune in to learn why ethical hacking is essential in today’s tech landscape and how certification can open doors to a thriving career in cybersecurity.
#ethical hacking training in Dubai#Cyber Security and Ethical Hacking Certification Courses in Dubai
0 notes
Text
0 notes
Text
IT Education Center is a dedicated and reputable supplier of solutions and training in the areas of networking, ethical hacking, and IT security. Delivering top-notch products and solutions to our clients is how we aim for excellence in everything we do. Our clients and students benefit greatly from our emphasis on practical, hands-on training, which helps them grow quickly and flourish in their chosen field(s). We specialize in addressing Black Hat level topics such as exploit development, reverse engineering, penetration testing, etc. and our primary activity is offering elite training in information security and networking, ethical hacking, and other related areas.
0 notes
Text
Brillica Services offers a comprehensive Cyber Security Course in Dehradun, India, designed to equip you with the skills needed to secure digital systems and networks. Our course covers key topics such as ethical hacking, cybersecurity fundamentals, network security, and more. With hands-on training and industry-recognized certifications, you'll gain practical experience in identifying and mitigating potential threats. Join us to become a cybersecurity expert and protect organizations from evolving cyber threats!
0 notes
Text
Take a glimpse into our vibrant learning environment as our skilled teachers lead hands-on sessions in Multimedia, Diploma in Multimedia and Animation, Software, and Accounts-related courses. From mastering graphic design to honing accounting software skills, our computer lab is where students unlock their potential with real-world applications
#advanced excel courses in dubai#diploma in accounting and finance courses in dubai#english language training in dubai#adobe photoshop courses in dubai#ethical hacking training in dubai#diploma in finance management courses in dubai#ielts courses in dubai#oet courses in dubai#digital marketing diploma courses in dubai#tally course in dubai
0 notes