#HIPAA Implementation in Bangalore
Explore tagged Tumblr posts
Text
HIPAA Certification: A Comprehensive Guide

The Health Insurance Portability and Accountability Act (HIPAA) plays a crucial role in protecting patient data privacy and security, primarily within the U.S. healthcare system. As the global demand for secure healthcare services grows, organizations outside the U.S., including those in Bangalore, India, have increasingly recognized the value of HIPAA compliance. This certification is particularly relevant for healthcare providers, insurers, IT service providers, and companies handling sensitive health information. By aligning with OHSAS 18001 Certification in Bangalore standards, organizations can demonstrate their commitment to patient data protection and strengthen their reputation in the healthcare industry.
HIPAA Implementation in Bangalore
Implementing HIPAA standards in Bangalore involves a meticulous process of understanding and adopting the rules and regulations outlined by the act. While HIPAA is not directly mandated in India, companies that serve U.S. clients or handle U.S.-based healthcare data must comply with HIPAA’s Privacy Rule, Security Rule, and Breach Notification Rule to avoid penalties and secure client trust.
Assessing Data Security Needs: The first step in HIPAA implementation is to conduct a comprehensive risk assessment to identify and analyze potential risks to the confidentiality, integrity, and availability of health data. This involves assessing the current security posture, network vulnerabilities, and compliance gaps that could compromise data privacy.
Establishing Privacy and Security Controls: After the risk assessment, organizations must create a set of privacy and security controls that align with HIPAA requirements. These controls should address physical, technical, and administrative safeguards, including access controls, encryption, and regular system monitoring. For companies in Bangalore, integrating advanced technologies like multi-factor authentication and data encryption can help enhance security controls and prevent unauthorized access.
Staff Training and Awareness: Employee training is essential to HIPAA compliance. Staff handling patient data must be thoroughly trained on data privacy best practices, including secure data handling, password management, and breach reporting protocols. HIPAA Implementation in South Africa often offers tailored training programs that can help companies educate their employees and promote a culture of privacy and data security.
Documentation and Compliance Policies: Proper documentation of privacy policies, risk assessments, and incident response plans is a crucial component of HIPAA compliance. These documents serve as evidence of the organization’s commitment to protecting health data and provide a clear framework for maintaining ongoing compliance.
HIPAA Services in Bangalore
With the rise in healthcare data digitization and remote services, Bangalore has become a hub for HIPAA compliance services. Many HIPAA certification providers, consultants, and audit firms offer comprehensive support to help organizations meet HIPAA standards. Key HIPAA services available in Bangalore include:
Compliance Consulting and Gap Analysis: Consulting services for HIPAA compliance are designed to help organizations understand where they currently stand in terms of data privacy and security. Consulting firms conduct gap analyses to identify areas that require improvement and provide recommendations for aligning with HIPAA regulations.
HIPAA Certification Programs: While HIPAA itself does not mandate certification, third-party certification programs allow organizations to demonstrate their commitment to HIPAA compliance. These certifications cover critical aspects of HIPAA’s privacy and security standards and validate an organization’s adherence to these protocols. HIPAA certification programs available in Bangalore are often customized for local businesses to ensure they meet U.S. healthcare data security requirements.
Risk Assessment and Vulnerability Management: Risk assessments are a cornerstone of HIPAA compliance, and numerous firms in Bangalore offer specialized risk assessment services for healthcare data security. These services include identifying potential vulnerabilities, testing system defenses, and implementing security measures to prevent unauthorized access.
Data Encryption and Cybersecurity Solutions: For organizations handling electronic protected health information (ePHI), data encryption and cybersecurity solutions are essential. HIPAA Services in Bahrain compliance providers offer advanced encryption, intrusion detection, and access management solutions to help companies secure sensitive data effectively. These services are instrumental in ensuring that healthcare data remains safe from cyber threats and unauthorized access.
HIPAA Audit in Bangalore
HIPAA audits are conducted to verify an organization’s compliance with HIPAA regulations. Though HIPAA audits are typically performed by the U.S. Department of Health and Human Services (HHS) in the U.S., organizations in Bangalore dealing with U.S.-based clients often conduct internal or third-party audits to ensure compliance. HIPAA audits in Bangalore generally include the following components:
Preparation for the Audit: Before an audit, organizations should review all documentation, including privacy policies, incident response plans, and risk assessments. HIPAA compliance consultants in Bangalore can assist with pre-audit preparations by helping companies address compliance gaps and organize relevant documentation.
Internal Audits: Internal audits are conducted periodically to ensure ongoing compliance with HIPAA standards. Organizations in Bangalore can engage HIPAA consultants to perform these audits and validate their adherence to privacy and security controls. Internal audits also allow organizations to identify potential issues early and implement corrective actions.
Third-Party Audits and Certification: Third-party audits provide an additional layer of assurance by offering an independent review of the organization’s compliance status. Many Bangalore-based organizations opt for third-party HIPAA audits to gain insights into their compliance practices and confirm that their data security measures align with U.S. healthcare standards.
Post-Audit Remediation: After an audit, organizations may receive a report highlighting areas of non-compliance or recommended improvements. Implementing these recommendations promptly is crucial to maintaining compliance and safeguarding sensitive health data. Many HIPAA audit firms in Bangalore provide post-audit support, helping organizations address identified issues and continuously improve their data privacy and security measures.
Conclusion
Achieving HIPAA Registration in Uganda is a valuable step for healthcare organizations, IT companies, and service providers handling U.S. healthcare data. By adopting HIPAA’s stringent data protection standards, these organizations can enhance their data privacy practices, improve their reputation, and ensure a higher level of trust from their U.S. clients. With a variety of HIPAA compliance services and audit options available locally, Bangalore-based businesses can successfully implement, monitor, and maintain HIPAA compliance to meet global data protection standards in healthcare.
0 notes
Text
Understanding HIPAA Certification Ensuring Compliance and Protecting Patient Information
In the age of digital health records and rising cybersecurity risks, safeguarding the privacy and security of patient information is more important than ever. This is where HIPAA (Health Insurance Portability and Accountability Act) comes into play. HIPAA Certification in Afghanistan indicates that an organization follows the tough requirements established to protect patient health information (PHI). This article delves into what HIPAA certification involves, its significance, and the methods necessary to obtain it.
What is HIPAA Certification?
HIPAA compliance certification verifies that a covered entity, such as a healthcare provider or business associate, has successfully completed a third-party HIPAA compliance programme. This confirms that the covered entity was HIPAA compliant at the time of completion. After that, HIPAA certification no longer ensures compliance.
Benefits of a HIPAA certification:
HIPAA in Australia programmes and processes you learn throughout HIPAA certification courses will help you become a more patient-centered hospital. You will learn how to take crucial precautions to preserve sensitive patient information such as health records, personal information, credit card information, and other documents and data. The more knowledgeable and trained your staff is, the better treatment your patients will receive.
Certification programmes can also help you get better organized and ready for future HIPAA audits. These programmes and specialists may handle minor concerns before they become major issues, walk you through documentation requirements, and provide hands-on advice for achieving or maintaining compliance.
Working with the right programme is essential for achieving the highest level of certification. Before scheduling your next certification class, consider the following:
The provider's industry and compliance expertise
How long have they been in business?
Reviews from previous organizations that went through the programme
The types of training courses they provide
How long do their courses take to complete?
Whether they provide online, in-person, or a combination of ways.
Who Wants to Be HIPAA Compliant?
Compliance with HIPAA Privacy and Security Rules is required of all "Covered Entities" and their "Business Associates."
Covered Entities are healthcare organizations or professionals who create, keep, or transfer protected health information (PHI), including doctors, nurses, hospitals, pharmacies, health plans, and healthcare clearinghouses.
Business Associates are service providers or professionals who perform healthcare duties or activities on behalf of covered entities and require PHI access to complete their tasks. Business associate categories include:
Services offered include legal,
actuarial, accounting,
consulting.
Data aggregation,
management/administration,
and financial considerations.
How much does HIPAA certification cost?
According to the US Department of Health and Human Services (HHS), after adopting the HIPAA Final Rule in 2013, the expenditures per organization for obtaining HIPAA Cost in china are as follows:
$80 to update the Notice of Privacy Practices.
$763 for upgrading the breach notification standards.
$84 for revising the business associate agreements.
$113 to ensure compliance with the Security Rule.
As a result, the estimated total HIPAA cost for each organization was $1,040. However, it is crucial to highlight that this estimate may only be partially accurate, particularly given the Security Rule's intricacies.
The Top HIPAA Certification Expert for Your Company
Discover top-tier HIPAA Certification Consultants in Bangalore through B2B CERT, a globally acknowledged service provider. If you need expert advice on HIPAA certification or help implementing it in your organization, our skilled team is ready to provide top-tier services. Recognising the challenges that businesses encounter, B2B CERT provides important certification audits to help overcome roadblocks and improve overall business efficiency. B2BCERT ensures instant recognition and easy contact with influential decision-makers. B2BCERT is your go-to solution for HIPAA credential enrollment.

#HIPAA Certification in Bangalore#HIPAA Implementation in Vietnam#HIPAA Certification Consultants in france
0 notes
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
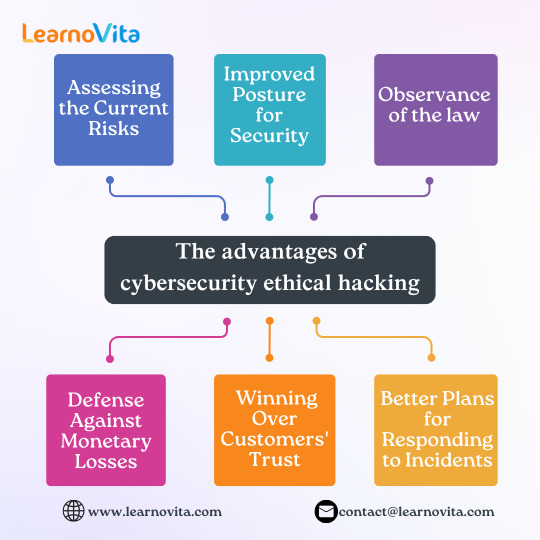
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
Web Development for Law Firms: What Sets a Niche Web Development Company Apart
In a competitive and reputation-driven industry like legal services, having a polished and strategic website isn’t just about aesthetics—it’s about trust, credibility, and client conversion. For law firms, generic websites built with one-size-fits-all templates simply don’t deliver results. What’s needed is a digital presence tailored to the unique needs of the legal profession—something only a specialized Web Development Company can offer.
A niche web development company that focuses on law firms understands the intricacies of legal marketing, compliance, client behavior, and service positioning. They don't just build websites—they craft digital strategies that support legal credibility and client acquisition.
Why Law Firms Need Specialized Web Development
Legal websites serve multiple purposes: informing, educating, collecting leads, and often supporting complex multi-location practices. Unlike standard business sites, law firm websites must also reflect professionalism, ethical standards, and confidentiality—all while ensuring they’re SEO-optimized, mobile-friendly, and compliant with bar association guidelines.
That’s a tall order—and one that generic web development agencies may not fully grasp.
1. Tailored Content Architecture for Legal Services
Law firms often provide a wide range of services—family law, criminal defense, corporate litigation, estate planning, and more. A niche web development company builds custom information architecture that organizes these services logically for both users and search engines.
They also ensure content is structured with trust signals, including attorney bios, case results, awards, client testimonials, and press mentions—all presented in a professional and compliant way.
Why it matters: Clear content structure improves navigation, user trust, and SEO rankings.
2. Conversion-Centric Design with Legal UX in Mind
Law firm websites are not e-commerce stores—they’re about generating inquiries, consultations, and case evaluations. Niche developers know how to design landing pages and forms that maximize leads without overwhelming users.
They use strategic CTA placements, intuitive contact forms, click-to-call buttons, and live chat integrations to guide visitors toward action while remaining subtle and respectful of the legal context.
Why it matters: Law firm clients often come with urgency—CRO-focused design ensures they take action quickly.
3. Local SEO and Practice Area Optimization
Most law firms serve clients in specific geographic areas. A specialized web development company optimizes for local SEO, using location-specific schema, Google Business Profile integration, localized keywords, and geo-targeted landing pages.
They also structure practice area pages to rank for long-tail keywords like “divorce lawyer in Bangalore” or “best real estate attorney in Mumbai.”
Why it matters: Ranking locally brings in high-intent leads already looking for legal representation in your area.
4. Compliance with Legal Advertising Standards
Legal websites must comply with ethical advertising rules set by local or national bar associations. These include restrictions on promises, testimonials, disclaimers, and attorney credentials.
Specialized developers are familiar with these nuances and build compliant designs and content structures that pass regulatory scrutiny while remaining effective for marketing.
Why it matters: Non-compliant websites can lead to legal challenges or reputational damage.
5. Secure Contact and Document Handling
Law firm websites often include contact forms, consultation scheduling, or client portals. These features must be secure, encrypted, and compliant with data privacy laws.
Experienced developers implement SSL encryption, secure hosting, spam protection, and GDPR or HIPAA-compliant forms, depending on your region and practice type.
Why it matters: Secure communication builds trust and protects client confidentiality—a non-negotiable for legal firms.
6. Scalable and CMS-Driven Backend
Law firms grow. Whether you’re adding new practice areas, opening branch offices, or publishing legal blogs and resources, your website should grow with you. Niche web development companies build on CMS platforms like WordPress or headless solutions that allow easy scaling and non-technical updates.
They also implement blog frameworks, knowledge hubs, and attorney directories that support SEO and thought leadership.
Why it matters: Scalability ensures your site adapts as your firm evolves—without needing a full rebuild.
7. Performance, Accessibility, and Mobile Readiness
Legal clients come from all demographics and devices. That’s why niche developers prioritize fast load times, WCAG-compliant accessibility, and responsive mobile design—so that every client, regardless of age or ability, can access and navigate your site with ease.
Why it matters: Inclusive, fast-loading websites rank better and serve a broader client base.
Final Thoughts
When it comes to web development for law firms, the stakes are high. You need more than a pretty homepage—you need a strategic digital platform that supports credibility, compliance, and conversions. This is where a specialized Web Development Company can make a transformative difference.
From intuitive UX and lead-focused design to local SEO and legal compliance, niche web development companies deliver solutions tailored to the legal profession. If your law firm is ready to grow its online presence and attract more qualified clients, the right digital partner can help turn your website into your most powerful legal marketing asset.
0 notes
Text
How Ethical Hacking Can Prevent Cyber Attacks on Businesses

Introduction
With the rapid advancement of technology, businesses worldwide are increasingly vulnerable to cyber threats. From data breaches to ransomware attacks, cybercriminals are constantly evolving their methods to exploit weaknesses in business networks. This is where ethical hacking comes into play. Ethical hacking is the practice of identifying and fixing security vulnerabilities before malicious hackers can exploit them. In this article, we will explore how ethical hacking helps prevent cyber attacks on businesses and why it is crucial in today’s digital landscape.
Understanding Ethical Hacking
Ethical hacking, also known as penetration testing or white-hat hacking, involves simulating cyber attacks to evaluate the security of a business’s IT infrastructure. Ethical hackers use their skills to detect vulnerabilities in software, networks, and systems, allowing organizations to strengthen their cybersecurity measures proactively.
Many professionals undergo specialized training to become certified ethical hackers. If you are looking to build a career in this field, you may consider Ethical Hacking Training in Bangalore, which provides hands-on experience and industry-recognized certifications.
How Ethical Hacking Prevents Cyber Attacks on Businesses
1. Identifying Security Vulnerabilities
One of the primary benefits of ethical hacking is its ability to uncover security weaknesses in a business’s IT infrastructure. Ethical hackers conduct penetration testing to analyze:
Weak passwords and authentication flaws
Unsecured network configurations
Software vulnerabilities
Inadequate encryption practices
By identifying these vulnerabilities before cybercriminals do, businesses can take necessary precautions to fix them and prevent potential attacks.
2. Preventing Data Breaches
Data breaches can cause severe financial and reputational damage to businesses. Ethical hackers help organizations:
Assess the security of databases and cloud storage
Strengthen access control mechanisms
Encrypt sensitive information effectively
Detect any unauthorized access attempts
With these preventive measures, businesses can ensure the safety of customer and business-critical data, reducing the risk of data theft.
3. Strengthening Network Security
Network security is crucial for businesses as cybercriminals often exploit network vulnerabilities to gain unauthorized access. Ethical hacking helps in:
Identifying weak firewall configurations
Conducting wireless network security assessments
Securing IoT (Internet of Things) devices
Monitoring for suspicious network activity
By implementing the necessary security patches and configurations, businesses can create a robust defense against cyber attacks.
4. Protecting Against Ransomware and Malware
Ransomware and malware attacks can cripple a business by encrypting sensitive data and demanding ransom payments. Ethical hackers conduct malware analysis and help businesses:
Implement strong endpoint security measures
Train employees to recognize phishing attempts
Regularly update and patch software vulnerabilities
Use behavior-based detection systems to identify threats early
Through proactive security assessments, businesses can reduce their exposure to ransomware attacks.
5. Enhancing Employee Awareness
A significant percentage of cyber attacks occur due to human error. Ethical hackers assist businesses in improving employee cybersecurity awareness by conducting:
Phishing attack simulations
Social engineering testing
Security training workshops
With better awareness and training, employees become the first line of defense against cyber threats.
6. Ensuring Compliance with Security Regulations
Many industries have strict cybersecurity regulations that businesses must comply with, such as GDPR, HIPAA, and PCI-DSS. Ethical hackers help businesses:
Conduct security audits
Identify compliance gaps
Implement necessary security measures to meet regulatory standards
By staying compliant, businesses avoid hefty fines and legal complications while ensuring customer data protection.
The Future of Ethical Hacking in Business Security
As cyber threats continue to evolve, ethical hacking will play a critical role in business security. Companies investing in ethical hacking strategies will be better prepared to prevent cyber attacks and mitigate security risks.
If you are interested in learning more about ethical hacking and building a career in this field, consider enrolling in Ethical Hacking Training in Bangalore, where you can gain practical skills and industry expertise.
Conclusion
Ethical hacking is an essential tool in the fight against cybercrime. By identifying vulnerabilities, preventing data breaches, strengthening network security, and enhancing employee awareness, ethical hackers help businesses stay secure in an increasingly digital world. Organizations must invest in ethical hacking strategies to safeguard their sensitive information and maintain customer trust.
If you want to pursue a career in ethical hacking, now is the time to explore training opportunities that will equip you with the skills to protect businesses from cyber threats.
0 notes
Text
Navigating HIPAA Certification in Bangalore: A Complete Guide
With its robust healthcare and IT infrastructure, Bangalore is a key player in the global healthcare services industry. Many organizations in the city handle sensitive patient data for hospitals, insurance companies, and telemedicine providers worldwide. Consequently, compliance with data protection laws like the Health Insurance Portability and Accountability Act (HIPAA) is becoming increasingly critical.
This blog provides insights into HIPAA certification, its importance, and how businesses in Bangalore can achieve it efficiently.
What is HIPAA?
HIPAA is a United States federal law enacted in 1996 to safeguard protected health information (PHI). It outlines the standards and practices healthcare organizations and their business associates must follow to ensure the confidentiality, integrity, and availability of patient data.
HIPAA certification in Bangalore primarily applies to entities operating in the U.S., its requirements are relevant globally for organizations that work with U.S.-based healthcare clients or manage data involving U.S. citizens.
For businesses in Bangalore that provide healthcare IT services, medical billing, or data processing for U.S. clients, demonstrating HIPAA compliance is essential for maintaining trust and securing business opportunities.
Why is HIPAA Compliance Important?
Organizations handling healthcare data face several challenges, including cyber threats, privacy breaches, and stringent client requirements. Non-compliance with HIPAA can lead to severe penalties and loss of business opportunities.
Regulatory Penalties: HIPAA violations can result in fines ranging from $100 to $50,000 per violation, with an annual maximum of $1.5 million.
Reputation Risk: A breach of PHI can tarnish an organization’s credibility, resulting in client attrition and a loss of new business.
Business Continuity: Many U.S.-based healthcare organizations mandate HIPAA compliance for their vendors as a contractual requirement.
By becoming HIPAA-compliant, businesses in Bangalore can establish themselves as trustworthy partners for U.S. healthcare providers.
What is HIPAA Certification?
Unlike some regulatory standards, HIPAA registration in Bangalore does not have a formal certification process overseen by a governing body. However, organizations can achieve HIPAA certification through third-party audits, which verify compliance with the regulation’s requirements.
This involves implementing safeguards outlined in HIPAA’s Privacy, Security, and Breach Notification Rules. Third-party certification can serve as proof of compliance for clients and stakeholders.
Key Steps to Achieving HIPAA Certification
Understand HIPAA Requirements: HIPAA is divided into several rules, including:
Privacy Rule: Governs the use and disclosure of PHI.
Security Rule: Focuses on safeguarding electronic PHI (ePHI).
Breach Notification Rule: Requires organizations to notify affected parties in case of a data breach.
Conduct a Risk Assessment: Identify potential vulnerabilities in your systems, processes, and policies related to PHI.
Implement Safeguards:
Administrative Safeguards: Policies and procedures to manage PHI securely.
Physical Safeguards: Controls to prevent unauthorized physical access to data.
Technical Safeguards: Measures like encryption, access controls, and audit logs.
Develop Policies and Procedures: Draft detailed documentation on how your organization will comply with HIPAA requirements.
Employee Training: Ensure your staff understands their roles in maintaining HIPAA compliance.
Engage a Certification Partner: Partner with a trusted consultancy like B2Bcert to assess your compliance and help you achieve certification.
Benefits of HIPAA Certification
Client Trust: Certification demonstrates your commitment to protecting patient data, enhancing credibility with U.S. healthcare clients.
Competitive Advantage: HIPAA compliance sets you apart from competitors in Bangalore, helping you secure more international business.
Data Security: Strengthened data protection measures reduce the risk of breaches and associated penalties.
Operational Efficiency: The certification process often leads to streamlined processes and improved data management practices.
HIPAA Certification Challenges in Bangalore
While HIPAA compliance offers significant advantages, organizations in Bangalore may face challenges such as:
Understanding U.S. Regulations: Navigating the nuances of a foreign law can be complex.
Cost of Implementation: Upgrading systems and processes may require investment.
Ongoing Maintenance: HIPAA compliance is not a one-time achievement; continuous monitoring and updates are necessary.
How B2Bcert Simplifies HIPAA Certification
For businesses in Bangalore seeking HIPAA certification, partnering with a trusted consultancy can make all the difference. B2Bcert offers end-to-end support, helping organizations achieve and maintain compliance effortlessly.
Expert Guidance: B2Bcert has a team of experienced consultants who simplify HIPAA requirements and align them with your business processes.
Customized Solutions: Every organization is unique. B2Bcert tailors its approach to your specific operations, ensuring an efficient path to compliance.
Comprehensive Support: From risk assessments to audits and employee training, B2Bcert provides holistic assistance throughout the certification journey.
Proven Success: Many organizations in Bangalore have achieved HIPAA certification with B2Bcert’s reliable services.
Conclusion
HIPAA consultant in Bangalore - For businesses in Bangalore involved in healthcare services or handling sensitive patient data, HIPAA compliance is no longer optional. It is a strategic necessity to build trust, secure international partnerships, and protect sensitive information.
By working with a professional consultancy like B2Bcert, you can navigate the complexities of HIPAA compliance confidently and efficiently. Take the first step toward safeguarding patient data and enhancing your global reputation with B2Bcert today!
0 notes
Text
HIPAA Certification in Bangalore: Safeguarding Patient Data in the Digital Age

In today’s rapidly evolving healthcare landscape, patient data protection has become paramount. With an increasing reliance on digital platforms for managing healthcare information, safeguarding sensitive medical data is critical. HIPAA (Health Insurance Portability and Accountability Act) Certification ensures that healthcare providers and associated businesses adhere to the highest standards of data privacy and security. For healthcare organizations in Bangalore, achieving HIPAA Certification in Bangalore not only demonstrates compliance with global standards but also reinforces trust with patients by ensuring that their personal information is securely handled.
Navigating HIPAA Certification in Bangalore: A Guide to Healthcare Compliance
Navigating HIPAA Certification in Bangalore requires healthcare organizations to implement a robust compliance framework that adheres to the stringent requirements set by HIPAA regulations. This includes ensuring that all electronic health records (EHRs), personal health information (PHI), and other sensitive patient data are securely stored, managed, and shared. The process involves conducting thorough risk assessments, implementing data encryption technologies, and creating policies that limit access to authorized personnel only. In addition, regular audits and staff training are essential components of maintaining HIPAA compliance. For Bangalore’s healthcare sector, this structured approach to patient data protection is crucial for aligning with international healthcare standards.
The Importance of HIPAA Certification for Healthcare Providers in Bangalore
HIPAA Certification is a vital credential for healthcare providers in Bangalore who aim to protect patient information while maintaining compliance with global data protection standards. The certification is essential for hospitals, clinics, medical billing companies, and other entities that handle healthcare data. Achieving HIPAA Certification helps prevent potential data breaches, fines, and legal issues that could arise from mishandling patient data. Additionally, as the digital transformation of healthcare continues, patients are becoming increasingly aware of their rights to privacy, making HIPAA Certification a key differentiator for healthcare providers that prioritize data security.
Achieving HIPAA Certification in Bangalore: Enhancing Data Security Standards
The journey to HIPAA Certification in Bangalore involves several crucial steps designed to enhance data security across healthcare organizations. This begins with identifying the types of patient information that need protection, followed by conducting a detailed analysis of potential vulnerabilities in the organization’s systems. By implementing technical safeguards such as firewalls, encryption protocols, and secure access controls, healthcare providers can significantly reduce the risk of data breaches. In addition to technical measures, HIPAA Certification also emphasizes administrative safeguards, including employee training, regular audits, and the development of contingency plans in case of data incidents. By following these best practices, healthcare organizations in Bangalore can ensure they meet HIPAA’s stringent data security standards.
HIPAA Compliance in Bangalore: Strengthening Healthcare Data Protection
As the healthcare sector in Bangalore continues to embrace digital innovation, maintaining HIPAA compliance is critical to safeguarding patient data. HIPAA Compliance is not a one-time certification but an ongoing commitment to data protection. Regular risk assessments, continuous monitoring of security protocols, and updated staff training programs are all essential components of ensuring that healthcare data remains secure over time. By achieving and maintaining HIPAA compliance, healthcare providers in Bangalore can demonstrate their dedication to data privacy, enhance their reputation, and foster greater trust with patients, ultimately strengthening the overall quality of healthcare services in the region.
In conclusion, HIPAA Certification in Bangalore is a crucial step for healthcare providers aiming to align with global standards, protect patient data, and build trust in an increasingly digital world. By prioritizing HIPAA compliance, healthcare organizations can ensure they are well-equipped to manage the challenges of data security in the digital age.
0 notes
Text
Cyber security essential
Course Overview
The Cyber Security Essentials course in Bangalore is designed to provide a foundational understanding of the principles and practices essential for protecting digital assets and ensuring information security. Ideal for beginners and professionals, this course will help you build the essential skills needed to navigate the cyber security landscape.
Course Objectives
Understand Basic Concepts: Gain a solid grounding in fundamental cyber security concepts.
Identify Threats and Vulnerabilities: Learn to recognize common security threats and vulnerabilities.
Implement Basic Security Measures: Acquire skills to apply essential security controls and practices.
Respond to Security Incidents: Develop a basic understanding of incident response and management.
Module 1: Introduction to Cyber Security
What is Cyber Security?
Importance of Cyber Security
Key Concepts and Terminology
Types of Cyber Threats
Module 2: Understanding Threats and Vulnerabilities
Common Cyber Threats: Viruses, Malware, Phishing, Ransomware
Identifying Vulnerabilities: Software, Hardware, Human Factors
Real-World Examples and Case Studies
Module 3: Cyber Security Principles
Confidentiality, Integrity, and Availability (CIA Triad)
Risk Management
Access Control Mechanisms
Security Policies and Procedures
Module 4: Network Security Basics
Introduction to Networking
Common Network Attacks: DoS, Man-in-the-Middle, Spoofing
Basic Network Security Measures: Firewalls, VPNs, Intrusion Detection Systems
Module 5: Protecting Your Systems
Endpoint Security: Anti-virus, Anti-malware, Patching
Password Management
Safe Browsing Practices
Data Encryption and Backup
Module 6: Incident Response and Management
Understanding Incident Response
Developing an Incident Response Plan
Basic Steps in Incident Handling
Post-Incident Review and Improvement
Module 7: Regulatory and Ethical Considerations
Legal and Regulatory Frameworks: GDPR, CCPA, HIPAA
Ethical Hacking and Penetration Testing
Privacy Concerns and Best Practices
Course Delivery
Format: Classroom instruction, hands-on labs, and case studies.
Duration: [Specify Duration, e.g., 4 weeks]
Prerequisites: None; suitable for beginners.
Assessment and Certification
Quizzes and Practical Labs
Final Exam
Certification of Completion
Instructor
[Instructor Name]: [Brief Bio and Qualifications]
Enrollment
How to Register: [Registration Details]
Course Fee: [Fee Details]
Contact Information: [Contact Details]
Additional Resources
Recommended Reading
Online Resources and Tools
Support and Community Access
Join us in Bangalore to enhance your knowledge and skills in cyber security. Our Cyber Security Essentials course will equip you with the fundamental tools and strategies to protect against cyber threats in today’s digital world.
0 notes
Text
Navigating the Cloud: Specialized Cloud Computing Courses in Bangalore

Bangalore, known as the Silicon Valley of India, is at the forefront of technological innovation and is home to a thriving ecosystem of tech companies, startups, and educational institutions. With the increasing adoption of cloud computing technologies across industries, there is a growing demand for skilled professionals who can design, deploy, and manage cloud-based solutions effectively. To meet this demand, several specialized cloud computing courses are available in Bangalore, offering in-depth training in emerging technologies, industry best practices, and practical skills development. In this article, we'll explore the specialized cloud computing courses available in Bangalore and how they equip students with the expertise needed to succeed in this dynamic field.
Advanced Cloud Architectures and Solutions: Advanced cloud computing courses in Bangalore focus on designing and implementing complex cloud architectures and solutions tailored to specific business needs. These courses delve into advanced topics such as multi-cloud and hybrid cloud deployments, microservices architecture, containerization (e.g., Docker, Kubernetes), serverless computing, and advanced networking and security concepts. Students learn how to leverage cutting-edge cloud technologies and best practices to architect scalable, resilient, and secure cloud-based solutions that meet the demands of modern enterprises.
DevOps and Continuous Integration/Continuous Deployment (CI/CD): DevOps has become integral to the software development lifecycle, facilitating collaboration between development and operations teams and enabling rapid and reliable software delivery. Specialized cloud computing courses in Bangalore focus on DevOps principles, practices, and tools, including version control systems (e.g., Git), automated testing, continuous integration/continuous deployment (CI/CD) pipelines, infrastructure as code (IaC), and configuration management tools (e.g., Ansible, Terraform). Students gain hands-on experience building, deploying, and managing cloud-native applications using DevOps methodologies and tools, preparing them for roles such as DevOps engineer, site reliability engineer (SRE), or cloud automation specialist.
Cloud Security and Compliance: With the increasing adoption of cloud computing, ensuring the security and compliance of cloud-based systems has become a top priority for organizations. Specialized cloud computing courses in Bangalore focus on cloud security fundamentals, threat detection and response, data encryption, identity and access management (IAM), compliance frameworks (e.g., GDPR, HIPAA), and cloud security best practices. Students learn how to design and implement robust security controls and measures to protect cloud-based assets and sensitive data, mitigate risks, and ensure compliance with industry regulations and standards.
Big Data Analytics and Machine Learning on the Cloud: Big data analytics and machine learning (ML) are transforming industries by enabling organizations to derive actionable insights, automate decision-making processes, and drive innovation. Specialized cloud computing courses in Bangalore cover topics such as big data processing frameworks (e.g., Apache Hadoop, Spark), distributed data storage and processing (e.g., Amazon S3, Google BigQuery), data visualization tools (e.g., Tableau, Power BI), and machine learning algorithms and techniques. Students learn how to leverage cloud-based platforms and services to build scalable, high-performance data analytics and ML solutions that unlock the value of big data and drive business growth.
Cloud-native Application Development: Cloud-native application development courses in Bangalore focus on building and deploying cloud-native applications that leverage cloud-native principles, architectures, and services. Students learn how to design, develop, deploy, and manage cloud-native applications using modern development frameworks (e.g., Spring Boot, Node.js), container orchestration platforms (e.g., Kubernetes), serverless computing services (e.g., AWS Lambda, Azure Functions), and cloud-native databases (e.g., Amazon DynamoDB, Google Cloud Firestore). These courses emphasize principles such as scalability, resilience, elasticity, and observability, preparing students for roles as cloud-native developers, architects, or engineers.
In conclusion, specialized cloud computing courses in Bangalore cater to the diverse needs and interests of students seeking to advance their careers in cloud computing and related fields. Whether you're interested in architecting complex cloud solutions, implementing DevOps practices, ensuring cloud security and compliance, leveraging big data analytics and ML, or building cloud-native applications, there are specialized courses available in Bangalore to help you acquire the skills and knowledge needed to succeed in this rapidly evolving industry. By enrolling in these courses, students can gain a competitive edge in the job market and contribute to the innovation and growth of the cloud computing ecosystem in Bangalore and beyond.
0 notes
Text
HIPAA Certification in Bangalore: Ensuring Data Privacy and Security in Healthcare

HIPAA Certification in Bangalore - As healthcare services in Bangalore continue to grow, so do the challenges associated with safeguarding sensitive patient data. The Health Insurance Portability and Accountability Act (HIPAA) is a critical U.S. regulation designed to protect the privacy and security of healthcare information. While HIPAA is mandatory in the United States, healthcare providers, medical facilities, and organizations in Bangalore are increasingly seeking HIPAA compliance to enhance their data security standards and to build trust with global partners, particularly those based in the U.S. In this blog, we will explore HIPAA implementation, services, and auditing in Bangalore.
HIPAA Implementation in Bangalore
HIPAA implementation in Bangalore requires a comprehensive approach to ensure that healthcare providers and associated businesses meet the rigorous requirements for protecting patient information. HIPAA focuses on both the privacy and security of healthcare data, requiring organizations to adopt a range of technical, administrative, and physical safeguards.
Key Steps in HIPAA Implementation:
Risk Assessment: The first step in HIPAA compliance is to conduct a risk assessment to identify potential vulnerabilities within an organization's IT systems and processes. Healthcare providers in Bangalore must evaluate their electronic health records (EHRs), data storage systems, and communication channels to identify gaps that could expose patient data to unauthorized access or breaches.
Security Measures: Based on the results of the risk assessment, organizations need to implement the necessary security measures. These include:
Encryption: Ensuring that sensitive healthcare data is encrypted during transmission and storage.
Access Controls: Implementing strict access controls to limit who can access patient information. This includes creating secure login procedures and two-factor authentication.
Backup and Disaster Recovery Plans: Organizations must have robust backup systems in place, ensuring data can be recovered in case of an emergency or system failure.
Training and Awareness: One of the key aspects of HIPAA compliance is ensuring that all employees are aware of their responsibilities. This includes conducting regular training programs that cover HIPAA regulations, security protocols, and data privacy best practices. In Bangalore, healthcare organizations need to ensure both technical and non-technical staff are trained to handle sensitive patient information appropriately.
Documentation and Policies: HIPAA requires organizations to have a formal set of policies and procedures in place that outline how they protect patient data. These policies must be documented and regularly reviewed to ensure compliance with HIPAA standards.
HIPAA Implementation in Bangalore involves not only upgrading technical infrastructure but also fostering a culture of data privacy and security throughout the organization.
HIPAA Services in Bangalore
As demand for HIPAA compliance grows in Bangalore, several companies offer specialized HIPAA compliance services to healthcare providers, medical facilities, and other businesses handling health data. These services are designed to help organizations navigate the complex requirements of HIPAA and implement best practices for safeguarding patient information.
Types of HIPAA Services Available in Bangalore:
HIPAA Compliance Consulting: Consultants work with organizations to understand their current security and privacy measures, assess gaps, and develop a roadmap for achieving HIPAA compliance. These experts provide customized solutions based on the specific needs of each organization, ensuring that they meet all required standards.
HIPAA Training: HIPAA service providers in Bangalore offer specialized training programs for staff. These programs educate employees about HIPAA regulations, their responsibilities in maintaining compliance, and how to handle sensitive healthcare data securely. Training is often customized to suit the roles of technical staff, management, and frontline employees.
Security and Risk Assessments: Regular risk assessments are essential for ensuring continued HIPAA compliance. Service providers conduct vulnerability assessments, penetration testing, and security audits to identify potential risks and recommend solutions to address them.
HIPAA Policy Development: Service providers assist organizations in creating detailed policies and procedures that align with HIPAA requirements. This includes policies on data storage, transmission, breach notification, and patient access to information.
Data Encryption and Security Solutions: Many HIPAA service providers in Bangalore offer technology solutions to enhance the security of healthcare data. This includes encryption tools, secure communication platforms, and access control systems.
By leveraging HIPAA services in Bangalore, organizations can ensure that they meet all necessary requirements for data privacy and security, reducing the risk of breaches and penalties.
HIPAA Audit in Bangalore
HIPAA audits are a critical aspect of ensuring that healthcare organizations remain compliant with the regulations. These audits evaluate whether an organization has effectively implemented the necessary safeguards to protect patient data and can help identify areas for improvement.
Steps Involved in a HIPAA Audit:
Pre-Audit Preparation: Organizations must ensure that they have all necessary documentation in place, including security policies, training records, risk assessment reports, and evidence of data protection measures. Proper documentation is key to passing a HIPAA audit.
On-Site Audit or Remote Review: HIPAA audits can be conducted either on-site or remotely. During the audit, the auditor will evaluate the organization’s compliance with HIPAA’s administrative, technical, and physical safeguard requirements. This includes reviewing how access controls are implemented, whether data encryption protocols are followed, and how well the organization responds to potential security incidents.
Evaluation of Risk Management Practices: One of the main focuses of a HIPAA audit is assessing how well the organization manages risks to patient data. The auditor will examine whether the organization regularly conducts risk assessments, how it mitigates identified risks, and whether security controls are regularly updated.
Audit Report: After the audit, the organization will receive a report outlining its compliance status. If any deficiencies are identified, the report will include recommendations for corrective action. Organizations that pass the audit can demonstrate their commitment to HIPAA compliance, which enhances trust with patients and partners.
Corrective Action Plan (if required): If the audit identifies any areas of non-compliance, organizations will need to implement a corrective action plan (CAP) to address these issues. The CAP will include timelines and specific actions required to bring the organization into full compliance.
Conclusion
HIPAA Registration in Bangalore is essential for healthcare providers, medical institutions, and businesses that handle sensitive patient information. By implementing strong security measures, leveraging specialized HIPAA services, and conducting regular audits, organizations can ensure they remain compliant with HIPAA regulations. This not only protects patient data but also builds trust with patients, partners, and regulators. HIPAA compliance is not just a regulatory necessity—it is a critical component of building a secure and ethical healthcare environment in Bangalore.
0 notes
Text
HIPAA certification ensures the protection of sensitive health information
Introduction:
In the ever-changing landscape of healthcare, protecting patient information is critical. The Health Insurance Portability and Accountability Act (HIPAA) was passed in 1996 to meet this critical need, establishing a standard for protecting sensitive patient data. While HIPAA Certification in Afghanistan does not offer certification, the term "HIPAA Certification" refers to a variety of training programmes and services aimed to assure compliance with HIPAA standards. This article discusses the significance of HIPAA certification, the components of HIPAA, and how organizations can attain and maintain compliance.
Understanding HIPAA
HIPAA is a set of regulations designed to protect patient privacy while facilitating the flow of health information required to provide high-quality healthcare. HIPAA's primary components include the Privacy Rule, Security Rule, and Breach Notification Rule.
The Role of HIPAA Certification:
HIPAA Consultants in Bangalore does not necessitate certification, obtaining it through recognised programmes displays a commitment to compliance and helps ensure that staff understand the rules. These programmes often address the following topics:
HIPAA Regulations: A thorough understanding of the Privacy, Security, and Breach Notification Rules.
Risk Management: Methods for identifying and minimizing risks to PHI.
Security measures include the implementation of administrative, physical, and technology precautions.
Incident Response: Procedures for handling breaches of PHI.
Benefits of HIPAA Certification:
enhances security: HIPAA Implementation in Australia enhances security by protecting sensitive health information from breaches and unauthorized access.
Regulatory Compliance: Ensures that the organization adheres to all regulatory obligations, lowering the risk of fines and legal action.
Patient confidence: Shows a commitment to preserving patient information, which builds confidence and credibility with patients and partners.
Operational Efficiency: Improves procedures by following best practices for data security and risk management.
Professional Development: Provides individuals with valuable knowledge and skills, hence promoting their professional growth.
Choosing A HIPAA Certification Programme:
When choosing a HIPAA certification programme, consider the following factors:
Curriculum: Look for a thorough understanding of all HIPAA laws and requirements.
Flexibility: Select a programme that provides flexible learning opportunities, such as online classes.
Reputation: Look into the program's reputation and reviews from prior participants.
Support: Look for programmes that provide ongoing assistance and resources for keeping compliance.
Understanding the cost of HIPAA certification:
HIPAA Cost in China varies greatly based on a number of criteria, including the size of the organization, the complexity of its operations, and the individual certification programme chosen. Individual employee training programmes typically cost $200 to $1,000 per person, whereas comprehensive organizational certification services, such as risk assessments, policy development, and ongoing compliance support, can cost several thousand to tens of thousands of dollars. Additionally, costs may include the resources required to adopt relevant security procedures and technology to assure compliance. Investing in HIPAA certification, on the other hand, is frequently justified by the possibility to avoid significant fines for noncompliance, as well as the increased trust and efficiency that certified organizations can obtain.
Guide to Achieving HIPAA Certification :
HIPAA registration in Bangalore ensures that items are consistently made and controlled in compliance with quality standards. It is crucial in businesses such as pharmaceuticals, food, and cosmetics to maintain product safety and effectiveness. B2B CERT is most likely a certification organization or procedure developed for business-to-business transactions that certify HIPAA compliance throughout supply chains. This certification fosters trust and credibility among partners by demonstrating a commitment to quality and compliance.

#HIPAA Certification in Bangalore#HIPAA Certification Consultants in Bangalore#HIPAA Registration in Afghanistan
0 notes
Text
Building Trust in Healthcare Hosting: A Comprehensive Look at HIPAA Certifications
A blog regarding HIPAA certification HIPAA Certification in Bangalore sets forth standards for protecting sensitive patient information, and covered entities (healthcare providers, health plans, etc.) are required to comply with these standards. Regarding web hosting in the context of healthcare and HIPAA compliance, the focus is on ensuring that the hosting provider implements the necessary…
View On WordPress
0 notes
Text
Ethical Hacking in Healthcare: Protecting Sensitive Patient Data
The healthcare industry is increasingly relying on technology to store and manage patient data. While this digitalization brings numerous benefits, it also exposes sensitive information to potential cyber threats.

For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Training Institute in Bangalore becomes a strategic imperative. We will explore the importance of ethical hacking in healthcare and discuss key measures to protect sensitive patient data.
Importance of Ethical Hacking in Healthcare:
Identifying Vulnerabilities: Ethical hacking helps healthcare organizations identify vulnerabilities in their systems, networks, and applications. By simulating real-world cyber attacks, ethical hackers can uncover weaknesses that malicious actors could exploit to gain unauthorized access to patient data. This enables organizations to patch vulnerabilities and enhance their security posture.
Protecting Patient Privacy: Patient data, including personal information, medical records, and billing details, is highly valuable to cybercriminals. Ethical hacking assists in identifying security gaps that could compromise patient privacy. By addressing these vulnerabilities, healthcare organizations can ensure that patient data remains confidential and protected.
Compliance with Regulations: Healthcare organizations are subject to various data protection regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Ethical hacking helps organizations assess their compliance with these regulations, identify gaps, and implement necessary safeguards to avoid penalties and reputational damage.
Proactive Risk Management: Ethical hacking provides healthcare organizations with valuable insights into potential risks and vulnerabilities. By proactively identifying and addressing these issues, organizations can minimize the likelihood of data breaches and other security incidents. This approach helps in building a proactive risk management culture within the healthcare sector.
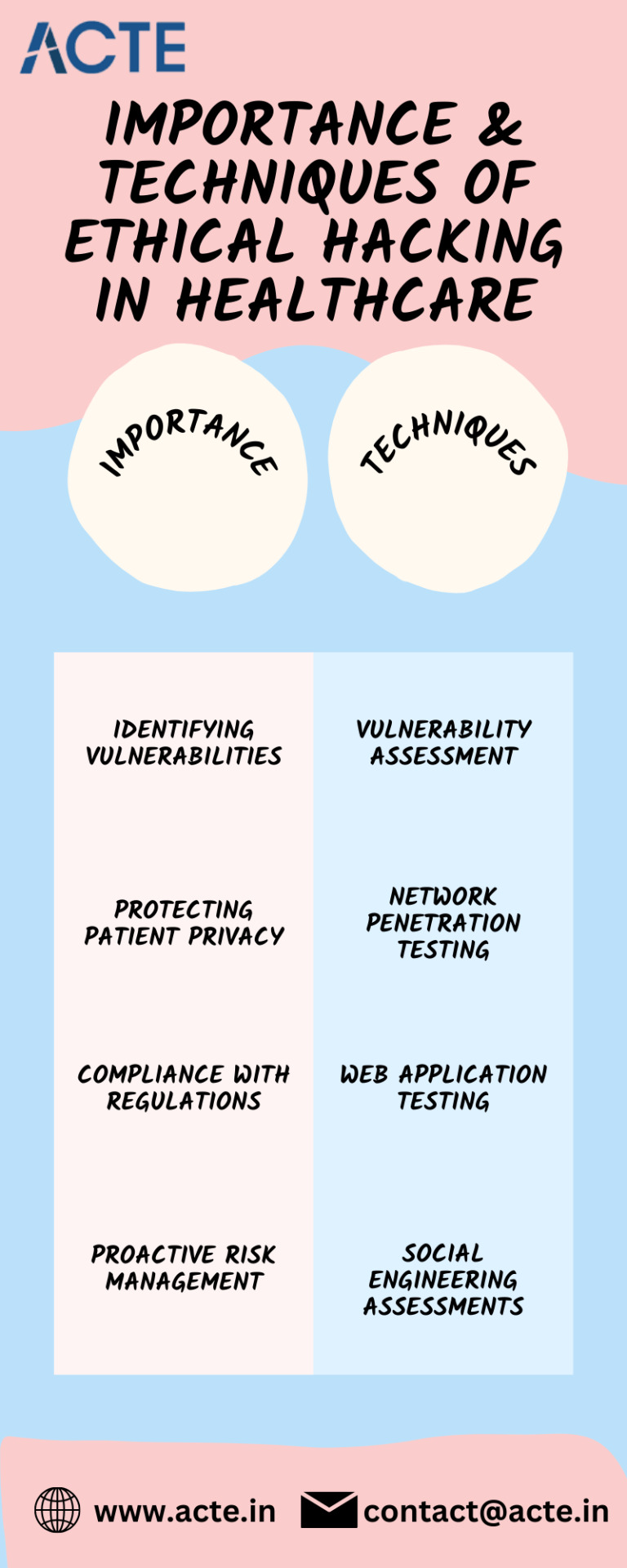
Ethical Hacking Techniques in Healthcare:
Vulnerability Assessment: Ethical hackers conduct vulnerability assessments to identify weaknesses in healthcare systems, networks, and applications. This involves using specialized tools to scan for known vulnerabilities and misconfigurations.
Network Penetration Testing: Network penetration testing involves simulating an attack on healthcare networks to identify potential entry points and vulnerabilities. Ethical hackers attempt to exploit weaknesses to gain unauthorized access and provide recommendations for strengthening network security.
Web Application Testing: Healthcare organizations often rely on web applications to store and process patient data. Ethical hackers perform web application testing to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references. This helps in securing web-based interfaces and preventing data breaches.
Social Engineering Assessments: Social engineering involves exploiting human vulnerabilities to gain unauthorized access to systems or sensitive information. Ethical hackers conduct social engineering assessments to test employees’ security awareness and identify potential weaknesses in organizational processes.
Ethical hacking plays a crucial role in protecting sensitive patient data in the healthcare industry. By proactively identifying vulnerabilities, healthcare organizations can strengthen their security measures, comply with data protection regulations, and safeguard patient privacy.
Ethical hacking techniques, such as vulnerability assessments, network penetration testing, web application testing, and social engineering assessments, provide valuable insights into potential risks and enable organizations to take proactive measures to mitigate them.
Embracing ethical hacking as a part of a comprehensive cybersecurity strategy is essential for healthcare organizations to maintain trust, protect patient data, and ensure the confidentiality and integrity of healthcare systems.
If you’re keen on ethical hacking, consider enrolling in an Ethical Hacking course in Bangalore. They often provide certifications, mentorship, and job placement opportunities to support your learning journey.
0 notes
Text
Getting To Intelligent Data Management
Intelligent data management is crucial in today's data-driven world, as it enables organizations to harness the full potential of their data for informed decision-making and competitive advantage. To get started with intelligent data management, follow these steps:
Define Your Data Strategy:
Begin by understanding your organization's goals and objectives related to data.
Determine what data is critical for your business and what insights you want to gain from it.
Data Collection and Integration:
Collect data from various sources, including internal databases, external APIs, IoT devices, and more.
Ensure data quality and consistency by cleaning and normalizing the data.
Integrate data from different sources to create a unified view.
Data Storage:
Choose appropriate storage solutions such as relational databases, NoSQL databases, data lakes, or a combination based on your data needs.
Consider cloud-based storage options for scalability and flexibility.
Data Security and Compliance:
Implement robust security measures to protect sensitive data.
Comply with data privacy regulations (e.g., GDPR, HIPAA) by establishing data governance policies and procedures.
Data Cataloging and Metadata Management:
Create a data catalog that documents data assets, their lineage, and usage.
Manage metadata to improve data discoverability and understanding.
Data Transformation and ETL (Extract, Transform, Load):
Use ETL processes to transform raw data into a usable format.
Apply data cleansing, enrichment, and aggregation as needed.
Data Analytics and Machine Learning:
Leverage data analytics tools and platforms for insights and reporting.
Incorporate machine learning and AI techniques for predictive analytics and automation.
Data Governance:
Establish data governance policies and roles to ensure data quality, security, and compliance.
Implement data stewardship to manage and maintain data assets.
Data Lifecycle Management:
Define data retention policies to manage data throughout its lifecycle.
Implement data archiving and deletion processes as required.
Data Visualization and Reporting:
Use data visualization tools to create dashboards and reports for data-driven decision-making.
Share insights with stakeholders across the organization.
Continuous Monitoring and Optimization:
Monitor data processes and performance to identify bottlenecks or issues.
Continuously optimize your data management systems for efficiency and cost-effectiveness.
Adoption of AI and Automation:
Incorporate artificial intelligence and automation to streamline data management tasks, such as anomaly detection, predictive maintenance, and data classification.
Training and Skill Development:
Invest in training your team to keep up with the latest data management technologies and practices.
Feedback and Iteration:
Gather feedback from users and stakeholders to improve data management processes continually.
Scalability and Future-Proofing:
Plan for scalability to accommodate growing data volumes and evolving technology.
Stay informed about emerging data management trends and technologies.
Intelligent data management is an ongoing process that requires a combination of technology, processes, and people. By following these steps and staying adaptable to changes in the data landscape, organizations can unlock the full potential of their data for better decision-making and competitiveness.
B2b events and conferences
Business events in Bangalore
B2b events
Tech summit
Business events in India
corporate events in India
Business Events
HR World Summit
0 notes
Text
Understanding the Cost and ROI of Security Automation Systems

The security of your business is essential to its success, and investing in security automation systems can help protect your assets, employees, and customers. However, understanding the cost and ROI of security automation systems is crucial before making any investment. In this blog, we'll discuss the factors that contribute to the cost of security automation systems and the return on investment (ROI) that can be expected from them.
Cost Factors for Security Automation Systems
Several factors contribute to the cost of implementing security automation systems. Here are some of the most significant ones:
-Type of Security Automation System: The type of security automation system you choose will greatly affect the cost. Access control systems, CCTV systems, and alarm systems all have varying costs, and some systems may require additional hardware and installation expenses.
-Number of Security Devices: The number of devices needed to secure your business is another cost factor. The more devices required, the higher the cost will be. For instance, a small business with a single entry door may only require one access control device, whereas a large enterprise with multiple entrances and exits will require several access control devices.
-Level of Integration: Security automation systems can integrate with other systems, such as lighting, HVAC, and fire hydrant installer in Bangalore, among others. The level of integration required will affect the cost.
-Installation and Maintenance: Installation and maintenance costs should also be factored into the total cost of the system. If you require additional hardware or software, this will incur additional expenses. Also, ongoing maintenance and support fees will add to the total cost.
?
ROI of Security Automation Systems
Security automation systems can help reduce the risk of theft, vandalism, and other criminal activities in your business. Here are some ways security automation systems can provide a return on investment:
Reduced theft and vandalism:
Security automation systems can help prevent theft and vandalism by deterring criminals and alerting authorities when an incident occurs. This can lead to lower costs associated with replacing stolen or damaged equipment as well as reduced insurance premiums.
Increased Productivity:
Implementing a security automation system can also increase productivity in the workplace. Employees will feel safer and more secure, which can lead to higher morale and improved job satisfaction. This, in turn, can lead to increased productivity and reduced absenteeism.
Improved Compliance:
Businesses can use security automation systems to comply with regulatory standards set by organizations like OSHA and HIPAA. By implementing security automation systems, businesses can reduce the risk of security breaches and avoid costly penalties associated with non-compliance.
Are you looking for the best public address system supplier in Bangalore?
Cost Savings:
Over time, security automation systems can lead to significant cost savings. By reducing the risk of theft and vandalism, businesses can avoid the costs associated with replacing stolen or damaged equipment. Additionally, the increased productivity and improved compliance that come with a security automation system can lead to higher profits and cost savings.
Trident Automation Systems Pvt. Ltd. has been serving this industry for so long, and now they are providing the best security solutions like fire hydrant services in Bangalore and CCTV services in HSR layout for a better ROI experience.
0 notes
Text
A Complete Guide to VAPT Certification Understanding
In the current digital era, cybersecurity is crucial for every company. Being certified in Vulnerability Assessment and Penetration Testing (VAPT) is essential to protecting your company. This certification guarantees the security of your systems from possible attacks. We will discuss what VAPT certification is, how it helps businesses, what kinds of organizations should consider it, how much it costs, what its main purpose is, how the audit and gap analysis process works, and how to locate a trustworthy VAPT consultant in this blog article.
VAPT Certification in Bangalore: What Is It?
The methodical process of finding, assessing, and addressing security flaws in an organization's IT infrastructure is known as VAPT certification. It integrates two crucial procedures:
Vulnerability Assessment (VA): VAPT Certification in Bangalore helps in the process of examining the system to find any weaknesses that an attacker may exploit.
Penetration testing (PT): This approach goes one step further by mimicking cyberattacks to evaluate the efficacy of security protocols and pinpoint vulnerabilities that require resolution.
A company that has achieved VAPT certification has demonstrated that it has taken proactive measures to protect its systems against cyberattacks.
VAPT Certification's Advantages for Businesses
Enhanced Security Posture: By assisting in the early detection and remediation of security weaknesses, VAPT certification helps to fortify the overall security of your company.
Regulatory Compliance: Adherence to certain security requirements is mandated by several sectors. VAPT Registration in Bangalore guarantees adherence to laws including PCI-DSS, HIPAA, and GDPR.
Customer Trust: By proving your dedication to cybersecurity with a VAPT certification, you may win over customers' trust and build stronger business ties.
Risk management: Organizations may prevent possible financial losses and harm to their reputation by proactively identifying and minimizing risks.
Operational Efficiency: To guarantee that the IT infrastructure runs smoothly and safely, routine VAPT inspections can enhance the effectiveness of security measures.
Which Type of Company Can Use VAPT Implementation?
VAPT certification is beneficial for any firm, but it is especially important for:
Financial Institutions: VAPT Services in Bangalore suitable for companies which are handling sensitive financial data, banks, insurance providers, and investment organizations are frequently the targets of cyberattacks.
Healthcare Providers: Because they handle private patient data, hospitals and clinics are targets for hackers.
E-commerce Platforms: Due to the large volumes of client data and financial transactions they handle, online merchants need to implement strong security measures.
IT and Software Companies: Companies that create and oversee software programs must make sure their offerings are safe from security flaws.
Government Agencies: Entities in the public sector are responsible for protecting vital data from potential attacks.
How Much Does It Cost to Get VAPT Certification?
Examine the extent and intricacy of the IT infrastructure under evaluation.
Testing Frequency: Frequent evaluations may raise the VAPT Cost in Bangalore
Consultant Fees: Hiring reliable and skilled VAPT experts might have an impact on costs.
Tools and Technologies: The price of the cutting-edge testing instruments and technologies that were employed in the evaluation.
What is VAPT Certification's Principal Function?
Assuring that an organization's IT systems are safe from possible cyber attacks is the main function of VAPT certification. This includes:
The process of identifying vulnerabilities involves locating holes in the system that an attacker may exploit.
Risk mitigation involves putting policies in place to deal with and resolve vulnerabilities that are found.
Validating Security Posture: Consistent testing to make sure security precautions hold up throughout time.
Improving Compliance: Fulfilling legal and security criteria unique to a certain sector.
Process of VAPT Certification Audit and Gap Analysis
The following steps are usually included in the VAPT certification process:
First Assessment: Analyzing the security posture as it stands now and pointing out any weaknesses.
Gap analysis is the process of identifying areas that require improvement by comparing the existing status to industry standards.
Penetration testing is the process of modeling assaults to evaluate how well security controls work.
Remediation: Taking care of vulnerabilities found and putting in place the required security measures.
Certification: The company receives VAPT in Bangalore when all vulnerabilities have been fixed.
Continuous Monitoring: Frequent evaluations to guarantee ongoing security and compliance.
How to Get a VAPT Consultant ?
A group of skilled experts at b2bcert Consultant specializes in VAPT services. Their knowledge guarantees an exhaustive and efficient evaluation of your IT infrastructure.Make sure the conditions of the contract and the cost match your demands and your budget by comparing them. Avoid paying excessively little or a lot of money, and find out exactly what the costs include.Selecting a VAPT Consultants in Bangalore such as b2bcert Consultant will enable you to efficiently handle the VAPT certification procedure, protecting your company from online attacks and strengthening your security posture all around.
0 notes