#How To Use TeamViewer
Explore tagged Tumblr posts
Text
oh my god do not click links in emails that tell you to verify your data or your bank account gets locked or click links in messages telling you your safety protocol is ending, like, tomorrow, you will get SCAMMED SO BAD AND YOU WILL LOSE A LOT OF FUCKING MONEY never ever let anyone pressure you into giving away login information especially to your online banking by creating a sense of urgency oh my GOD
some things to look out for
1. spelling mistakes. do you know how many rounds of marketing and sales experts these things go through? if theres a spelling mistake dont click it
2. not using your name. if an email adresses you with "dear customer" or, even worse, a generic "ladies and gentlemen", it is most likely not actually targeted to you
3. verifying or login links. even IF your bank was stupid enough to send these to customers, dont EVER click those. look at me. they can legally argue that youve given your data away and thus they dont have to pay you anything back DONT CLICK THAT FUCKING LINK
4. creating a sense of urgency. do this or we lock your account next week. do this or your ebanking stops working tomorrow. give us all your money in cash or your beloved granddaughter will get HANGED FOR MURDERING BABIES. no serious organisation would ever do something like that over email or sms. ever. hands off.
5. ALWAYS CHECK WHO SENT YOU THE EMAIL. the display name and the email adress can vary a LOT. anyone can check the display name. look at the email adress. does it look weird? call the fucking place it says its from. you will likely hear a very weary sigh.
6. if its in a phonecall, scammers love preventing you from hanging up or talking to other people to have a little bit of a think about whats happening. there should always be a possibility to go hey i wanna think about this ill call back the official number thanks.
7. do not, i repeat, do NOT a) call a phone number flashing on your screen promising to rid your computer of viruses after clicking a dodgy link and b) let them install shit on your computer like. uh. idk. teamviewer.
7.i. TEAM VIEWER LETS PEOPLE USE YOUR COMPUTER HOWEVER THEY WANT AS LONG AS THEYRE CONNECTED. IF YOU DONT KNOW FOR FUCKING SURE YOURE TALKING TO ACTUAL TECH SUPPORT DONT GIVE ANYONE ACCESS TO YOUR COMPUTER.
fun little addendum: did you know a link can just automatically download shit? like. a virus? an app you can't uninstall unless you reset your entire device? dont click links unless youre extremely sure you know where they lead. hover your mouse over it and check the url.
thanks.
#'oh i was so stressed in the moment' thats what theyre counting on PLEASE dont do this you will lose so much money#sometimes money you dont even have#do you know how much overdraft your bank account comes with?#sometimes the answer is 15k fucking euros
17K notes
·
View notes
Text
definitely one of the most difficult moments of my professional career was when i was doing tech support for [REDACTED]'s automated biomed research lab and like. hang on lemme greentext this
>tell them i can fix this issue in half an hour with a remote support session (aka Teamviewer)
>"you want to... control our computers???? over the internet????? like some kind of HACKER???????"
>their IT submits my request to upper management and after two weeks they reluctantly allow me to get remote access to their systems
>by logging into a virtual machine using a 20-digit password and then using a specific program inside of that virtual machine
>while sharing my screen with someone from their IT team the entire time
>finally get remote access to the PC with the issue
>go to open log files to start troubleshooting
>ERROR: User does not have read permissions.
>what the fuck
>ask their IT guy why it's saying that
>"...because we don't want you looking at our stuff, duh?"
>take deep breath before calmly explaining that i need to open files in order to fix their problem
>IT guy submits my request to upper management
>after another week i go through the whole process again but can actually open the log file this time
>cool, it's exactly the issue i thought it was and i know exactly how to solve it
>open the relevant settings file, change a single number, hit Save
>ERROR: User does not have write permissions.
>what the FUCK
>ask IT guy how i'm supposed to fix their system if i can't change literally anything on it
>takes 20 minutes of arguing to get him to admit that maybe i need write access
>he submits the request to upper management
>a week goes by
>upper management denies it
>says i can just verbally tell the IT guy on the call what to type and he'll do it for me
>deep breaths. deep breaths.
>start third remote session
>go to open the relevant .log file in notepad, which isn't the default program it opens with for some reason
>they fucking disabled right clicking
>[REDACTED] has a $118 billion market cap btw
>manage to walk the IT guy through using the command line (which he had never seen before and was scared of) to edit the relevant file
>three weeks go by
>new support ticket in my inbox
>"why didn't your fix fix this completely unrelated issue?"
>they still won't give me write access
>VP of [REDACTED] yells at me in our weekly meeting for taking so long to fix a third unrelated issue they never submitted a ticket for and is also not actually an "issue" but an intended feature of our software that they don't like
>i went to college for this
#second worst part of that job was getting emails from a customer like#“hey can you bump our ticket to the top of the queue? it's really impacting our ability to do research. no pressure though! :)”#and then i'd check who it's from and it's fucking St. Jude's Children's Hospital#“no pressure but you are directly killing kids with cancer”
251 notes
·
View notes
Text
You guys need to calm down a bit and understand that George in his "sidelined era" (as some of you might think) is still so busy.
He got to 25 PR schedules by Imola last year but he got to 25 PR schedules this year only by Bahrain.
Give that man a break. If anything, rejoice that the PR schedules are even-ed out! I don't like to see George hopping to two schedules in a day and getting mobbed by fans then continued on to another two schedules the next day and blah blah. It's not being busy and "favored by Mercedes". It's him being overworked. I know he's paid millions but a human body cannot be traded with dollar bills. If it gets to a point of fatigue, it gets to a point of fatigue.
He talked about wanting to explore Kyoto/Osaka/Tokyo last year but can't due to schedules. And in Canada, he flew back and forth to NYC as well. After his heat stroke in Singapore, he directly flew to Malaysia the day after. It's not healthy.
If anything, be grateful Kimi or Valtteri is taking up the portions and helping a little. I'm not only talking about physical health but also his mental health. Even if others take 10 schedules off him, he'd still have another 20 with a whole bunch of sponsors like IWC, Adidas, Petronas, UBS, HPE, Ritz Carlton, Akkodis, Einhell, Teamviewer, and many others preferring him to be their main guy.
The reason why you might not see him busy is because some of these schedules are private schedules or schedules uploaded to different platforms like LinkedIn or Douyin or Weibo. Sometimes I only knew George was visiting UBS HQ or HPE HQ for a company visit through these platforms or people updating. Many of these are off-the-record events. His on-the-record events are already a lot. Can you imagine how much off-the-records there are? Combined with his own driver duties and GPDA duties?
I understand the defensiveness but please reconsider these points. UBS hypes him so hard. So does INEOS and Akkodis. Why don't you see it? Because it's on another platform and it's off the record for us in the mainstream social media platform.
And lastly? Let's calm down and not get the narratives and rumours into our head. Focus on the reality. If you don't see it, why would you think it's real? Even if it's your speculation, you need to realize it's still a speculation. Calm down.
10 notes
·
View notes
Text
Linux/Fedora and Sims 2....
SO, as I had mentioned before, I had planned to put linux on an old potato laptop I had laying around that doesn't get used. My bestfriend came over about a week or so ago and helped me with putting Ubuntu, Lutris and wine on the laptop. I was super stoked to get started playing the Sims 2 without pink or crashing.. I folllowed Osab's installation guide for linux off of github and when I finished, I launched the game and....nothing. I tried a few different things with no luck so I cried to my bestfriend about it and he got me to get teamviewer and did some stuff in the terminal and read the logs for the game to see what was going on. Turns out there was a missing dll file and then that lead to finding out that there was a conflict with Wine and Lutris.. he had to go so he kinda told me what to do, i asked in some of the sims discord servers if anyone had experience with playing sims on linux, someone responded and helped me a bit.. she was super nice and said if i had any questions, to ask her which I completely appreciate. I got to thinking, maybe I should just bite the bullet and install fedora 41 onto an ssd I have in my computer that I don't generally use that much except for storing some editing stuff that I was doing for a youtuber friend.. I cleared it out, followed a video tutorial on how to do it. When I tried to boot Fedora onto my ssd to test it out(not install it) an error came up and it wouldn't load.. I didn't want to fuck with it incase I did something to screw with my Windows stuff so I left it. I told my bestfriend about it the next day and he said to do something about the usb and I told him I was done messing around with it because it was giving me anxiety and I literally just want to play my game. SO, this morning I called a PC place and asked if they were able to do Linux installs as a partition and they said they could but they don't install programs or anything like that, which is fine with me cause I know how to install the other two programs that I need... he said that he will do it and will teach me how to unplug my main ssd that has windows on it so no corruption ensues, I'm sure it may be a little overkill but if it protects all my stuff on my windows drive, I'll do it, lol. I take it on Friday morning and hopefully will get it back by the afternoon. it's going to cost me like 85$ or so to do it but I rather a professional handle it and not have to worry about screwing it up. SO hopefully I'll have Sims 2 running on my pc by next week and I couldn't be more excited. Here's to hoping I can finally play, I'm getting desperate LOL.
4 notes
·
View notes
Text
How to Upgrade to Windows 10 Pro with Genuine License Key

In the world of operating systems, Windows 10 Pro remains a top choice for professionals, businesses, and power users. While Windows 11 is on the rise, Windows 10 Pro continues to offer unmatched stability, extensive compatibility, and enterprise-level security features. If you’re still using Windows 10 Home or an older version, upgrading to Pro is a smart move—but it requires a legitimate Windows 10 Pro key upgrade to unlock all advanced capabilities.
This article will walk you through the benefits of upgrading to Windows 10 Pro, how to use a genuine license key, and where to get one safely and affordably.
Why Upgrade to Windows 10 Pro?
Windows 10 Pro isn’t just a shinier version of Home; it includes a host of extra features designed for security, productivity, and control. Key advantages include:
BitLocker Encryption: Keep sensitive data safe from unauthorized access by using BitLocker, which encrypts the entire hard drive. This is particularly useful for businesses and professionals handling confidential information.
Remote Desktop Access: Windows 10 Pro allows users to connect to their PC from anywhere, which is invaluable for remote work or IT professionals who need to troubleshoot or manage devices remotely.
Hyper-V Virtualization: Run virtual machines natively without third-party software. This is essential for developers, IT admins, and those working with multiple operating systems for testing or development purposes.
Group Policy Editor: Control settings across multiple systems, including password policies, user rights, and security measures. This feature is critical for businesses managing many systems.
Assigned Access: Lock users into specific apps, ensuring that those who are not authorized to access the full system only use the necessary tools, increasing security in controlled environments.
Windows Update for Business: Control when updates are installed, which allows businesses to test updates before deploying them across all devices, avoiding disruptions.
These features make Windows 10 Pro ideal for developers, system admins, and anyone managing a secure or business-oriented environment. For personal users who prioritize security, privacy, and control over system updates, Windows 10 Pro is an excellent choice.
Who Should Upgrade?
You should consider a Windows 10 Pro key upgrade if you:
Use your computer for business or freelance work: Professionals, freelancers, and small business owners can benefit from the added security, customization, and enterprise tools.
Need better control over system policies and user accounts: If you need to enforce company-wide security settings, control app access, or limit user permissions, Windows 10 Pro is designed for this.
Want to set up encrypted storage and VPN connections: BitLocker and other built-in tools help you ensure secure file storage and seamless VPN connections for remote access.
Use enterprise apps and tools: Some advanced business tools and apps only work with Windows 10 Pro, so if your work depends on these, upgrading is essential.
Need remote desktop access without third-party apps: With Windows 10 Pro, you don’t need additional software like TeamViewer or Chrome Remote Desktop for connecting to your system remotely.
Home users who value security and flexibility will also benefit from upgrading. Windows 10 Pro offers a range of features that make it perfect for those who need to take control of their system's functionality.
How to Upgrade Using a Genuine Product Key
Upgrading to Windows 10 Pro is easy if you have a genuine product key. Follow these simple steps to activate your upgrade:
Open Settings > Update & Security > Activation.
Click on Change product key.
Enter your Windows 10 Pro key upgrade.
Let Windows verify and activate the license.
Restart your PC to complete the process.
Once done, your system will automatically convert to Windows 10 Pro with all features unlocked, including BitLocker encryption, Hyper-V virtualization, and remote desktop access. You’ll enjoy enhanced control, security, and productivity tools without any interruptions.
Where to Buy a Genuine Windows 10 Pro Key
For authenticity, affordability, and instant delivery, your best option is SpotKeys.com. It’s a trusted platform known for providing 100% genuine license keys for Microsoft and other software.
Why SpotKeys?
Instant digital delivery: As soon as you purchase a Windows 10 Pro key upgrade, you’ll receive it instantly via email, allowing you to activate your system without any delays.
Secure payment options: SpotKeys offers multiple secure payment methods, including credit cards and PayPal, ensuring your transactions are safe and easy.
Verified customer satisfaction: SpotKeys has earned the trust of thousands of satisfied customers worldwide. You can count on them for top-quality service.
24/7 technical support: SpotKeys provides 24/7 support in case you face any issues with activation or need help with your purchase.
Significantly cheaper than retail pricing: SpotKeys offers Windows 10 Pro keys at affordable prices, which are significantly lower than retail, allowing you to save money while upgrading your system.
You can get a genuine Windows 10 Pro key upgrade in minutes and activate your system without hassle, ensuring that your system is secure and running optimally.
Benefits of a Licensed Windows 10 Pro System
A properly activated version of Windows 10 Pro allows you to:
Receive all critical security updates: Stay protected from vulnerabilities and cyberattacks with regular security patches and updates.
Access enterprise tools and cloud support: Windows 10 Pro is fully compatible with a range of enterprise tools, offering cloud synchronization and business-grade security.
Avoid system crashes caused by unlicensed keys: Running a system on unlicensed software can lead to crashes, system instability, and loss of productivity. A genuine Windows 10 Pro key guarantees system reliability.
Customize system-wide settings with ease: Control system settings and customize them for your business needs, such as configuring user access or enforcing security policies.
Improve productivity through remote management and automation: Windows 10 Pro offers tools for automating repetitive tasks and managing systems remotely, which boosts efficiency in business operations.
Unlicensed versions often lack access to these vital features and may lead to system instability or data loss, so it’s crucial to upgrade with a genuine license.
Other Must-Have Software from SpotKeys
To maximize your computing power, check out these other tools available at SpotKeys.com:
ABBYY FineReader Lifetime License: This OCR and PDF solution is ideal for converting, editing, and managing documents. Pair it with Windows 10 Pro for a complete digital productivity suite.
Exchange 2019 license key: For businesses using Windows 10 Pro as their system environment, Exchange 2019 offers secure email solutions and business communication tools.
SharePoint key: Improve collaboration, document management, and workflow automation within your organization by pairing Windows 10 Pro with SharePoint.
TeamViewer trial reset tool: If you're using remote desktop solutions, TeamViewer combined with Windows 10 Pro makes it easy to access your PC from anywhere.
Office 365 keys: Integrate Office 365 with your Windows 10 Pro system for seamless document creation, email management, and collaboration.
Visual Studio Enterprise 2022 product key: For developers using Windows 10 Pro, Visual Studio offers a robust platform for building custom applications.
Microsoft Office 2019: Combine Office 2019 with Windows 10 Pro for the ultimate productivity suite for personal or business use.
Corelcad 2019: For professionals needing CAD software, CorelCAD works smoothly with Windows 10 Pro to deliver powerful design tools.
Every purchase from SpotKeys comes with guaranteed authenticity and full support, ensuring a seamless experience across all your software tools.
Final Thoughts
A Windows 10 Pro key upgrade is an investment in performance, security, and control. Don’t rely on questionable cracks or key generators—those put your data and system at risk. With SpotKeys.com, you can upgrade with confidence, knowing your key is 100% genuine and your activation process will be seamless.
Whether you're a business professional, a developer, or simply someone who needs more advanced control and features, Windows 10 Pro is the best choice. The enhanced security, functionality, and productivity tools make it the ideal operating system for demanding users. Upgrade today and ensure your system is fully optimized for the tasks ahead.
Visit SpotKeys.com to get your Windows 10 Pro key upgrade today and unlock the full potential of your Windows operating system.
0 notes
Text
Things that have genuinely sent me into a near nervous breakdown today: installing plugins and calling tech support for my NEW brother printer that we were told is super easy to use💜
(it's the most painful experience I had to endure in my life, this shit is forcefully making me learn coding bc of how difficult it is to set up to scan a single document, I've been sitting at this desk for two hours and a half and it still doesn't work, I had to install TeamViewer to get help from a local technician and I'm about to start crying. I want old printers that you just plug in and use back 💜)
#sorry fir the rant but this shit is genuinely making me go insane#never have i ever experienced so much fucking triuble OVER A PRINTER. A FUCKING PRINTER.#abd the Brother website somehow diesnt even have the model listed 💜#did i get scammed by a tech shop 💜
0 notes
Text
How To Start An IT Business At Home

In today’s digital age, businesses and individuals rely on technology for their daily operations. However, technical issues can arise at any time, disrupting workflows and productivity. This is where remote IT support comes in—a service that allows IT professionals to diagnose, troubleshoot, and resolve technical problems without being physically present. Remote IT support offers a cost-effective and efficient way to handle tech-related challenges, providing businesses and individuals with expert assistance in real-time.
Understanding Remote IT Support
Remote IT support is a service that enables IT professionals to access a client’s computer, network, or software remotely to diagnose and fix issues. This is accomplished through specialized software that allows secure remote access, ensuring that IT technicians can manage and resolve problems as if they were physically present. Remote IT support can be used for a wide range of tasks, including software troubleshooting, virus removal, system updates, network monitoring, and even hardware diagnostics.
How Remote IT Support Works
The process of remote IT support typically involves the following steps:
Initiating the Support Request – The user experiencing a technical issue contacts the IT support team via phone, email, or a support portal. The IT professional gathers initial details about the problem to determine if it can be resolved remotely.
Establishing a Secure Connection – If remote troubleshooting is possible, the IT technician provides the user with a secure link or software to establish a remote connection. The most commonly used remote access tools include TeamViewer, AnyDesk, LogMeIn, and Microsoft Remote Desktop.
Diagnosing the Issue – Once connected, the IT professional takes control of the user’s system with permission. They analyze logs, system settings, and error messages to identify the root cause of the problem.
Troubleshooting and Resolving the Problem – Based on the diagnosis, the technician applies the necessary fixes. This may include updating drivers, configuring settings, running antivirus scans, or reinstalling software.
User Verification and Disconnection – After resolving the issue, the technician asks the user to verify that everything is functioning correctly. Once confirmed, the remote session is securely terminated.
Documentation and Follow-up – Many IT support teams document the issue and resolution process for future reference. In some cases, follow-ups are conducted to ensure the problem does not recur.
Benefits of Remote IT Support
Remote IT support offers several advantages for businesses and individuals, making it a preferred choice for handling technical issues:
Cost-Effective – Businesses can save money on travel expenses and on-site support fees.
Faster Response Time – IT issues can be addressed immediately without waiting for a technician to arrive.
24/7 Availability – Many remote IT support services offer round-the-clock assistance, ensuring minimal downtime.
Access to Expert Support – Businesses can leverage the expertise of IT professionals without hiring a full-time team.
Improved Security – Secure remote access tools ensure that data remains protected while resolving IT issues.
Common Use Cases for Remote IT Support
Remote IT support is widely used in various scenarios, including:
Business IT Support – Companies rely on remote IT support for network troubleshooting, software installations, and system maintenance.
Personal Computer Troubleshooting – Individuals experiencing issues with their home computers can get assistance remotely.
Cybersecurity Monitoring – IT teams use remote access to monitor and respond to security threats in real-time.
Cloud-Based IT Services – Many cloud applications provide remote support options for seamless integration and troubleshooting.
Conclusion
Remote IT support has revolutionized the way technical issues are resolved. It provides a convenient, efficient, and secure method for IT professionals to assist users without the need for physical presence. Whether for businesses or individuals, remote IT support ensures minimal downtime, enhances productivity, and helps maintain a smooth digital experience. As technology continues to evolve, remote IT support will remain an essential service for managing and maintaining IT infrastructure effectively.
0 notes
Text
How To Install Team Viewer Into Ubuntu 16.04 Gnome Desktop
Teamviewer is remote system as your pc control. You can use various purposes like windows, linux, Mac, Chrome OS, Raspberry Pi, Android and iOS etc. So now I want to share how to install team viewer on your Ubuntu 16.04 gnome desktop. ★ How To Install Zabbix 5.0 On Centos 7 ★ How To Fix Jitsi Meet Video Conference Using Mobile Browser Step #01: Must be your server update and…
1 note
·
View note
Text
How to Set Up an Effective IT Help Desk for Small Businesses
An IT help desk is an essential component of any small business aiming to maintain smooth operations and resolve technical issues promptly. A well-structured help desk not only addresses employee concerns efficiently but also contributes to enhanced productivity and customer satisfaction. Here’s a step-by-step guide to setting up an effective IT help desk for small businesses.
1. Define the Scope and Objectives
Before diving into the technical setup, it’s crucial to outline the purpose and goals of your IT help desk. Ask yourself:
What types of issues will the help desk handle? (e.g., software troubleshooting, hardware maintenance, network issues)
Who will use the help desk? (employees, customers, or both)
What level of support is required? (basic troubleshooting or advanced technical solutions)
By defining the scope, you can ensure that the help desk aligns with your business’s specific needs and resources.
2. Choose the Right Help Desk Software
Selecting the right software is critical to the efficiency of your IT help desk. Look for solutions that offer:
Ticket Management: Allows tracking and resolving of user issues systematically.
Knowledge Base Integration: Provides users with self-help options to resolve common issues.
Multi-Channel Support: Enables communication through email, phone, chat, or a web portal.
Scalability: Can grow with your business needs.
Popular options for small businesses include Zoho Desk, Freshdesk, and Zendesk. Compare features and pricing to find the best fit for your business.
3. Assemble a Skilled Team
Your IT help desk team should possess both technical expertise and strong interpersonal skills. Depending on your business size and budget, you can choose between:
In-House Staff: Ideal for businesses with frequent and complex IT needs.
Outsourced Support: Cost-effective for smaller businesses with limited IT requirements.
Ensure your team is trained to handle technical issues, communicate effectively, and prioritize tasks based on urgency.
4. Establish Clear Processes and Workflows
Efficient processes and workflows are the backbone of an effective IT help desk. Define:
Ticket Prioritization: Set criteria for categorizing issues by urgency and impact.
Escalation Procedures: Specify how unresolved issues are escalated to higher-level support.
Response and Resolution Timeframes: Establish Service Level Agreements (SLAs) to manage user expectations.
Documentation Standards: Encourage detailed recording of issues and solutions for future reference.
5. Create a Knowledge Base
A comprehensive knowledge base empowers users to solve common problems independently, reducing the workload on your help desk team. Include:
Step-by-step guides for frequently encountered issues.
Troubleshooting checklists.
FAQs and video tutorials.
Tools like Confluence or Notion can help you organize and manage your knowledge base effectively.
6. Enable Multi-Channel Support
Small businesses benefit from offering multiple ways for users to contact the help desk, such as:
Email: For non-urgent or detailed issues.
Phone: For immediate assistance.
Live Chat: For real-time troubleshooting.
Web Portal: For tracking ticket statuses and accessing self-help resources.
Ensuring seamless communication across these channels can improve user satisfaction and help resolve issues faster.
7. Implement Remote Support Tools
Remote support tools are indispensable for resolving issues without being physically present. Popular tools include:
TeamViewer: For remote desktop access.
AnyDesk: For quick and secure connections.
LogMeIn: For comprehensive remote support capabilities.
These tools save time and resources, especially for businesses with employees working remotely or in multiple locations.
8. Monitor and Analyze Performance
Regular monitoring helps you evaluate the effectiveness of your IT help desk. Key performance indicators (KPIs) to track include:
First Response Time: How quickly the team responds to a ticket.
Resolution Time: The average time taken to resolve issues.
Ticket Volume: The number of tickets handled over a given period.
Customer Satisfaction (CSAT): User feedback on the help desk’s performance.
Use analytics tools integrated into your help desk software to generate reports and identify areas for improvement.
9. Focus on User Training and Feedback
Educating users about common technical issues and the help desk’s processes can reduce unnecessary tickets. Conduct:
Onboarding Sessions: Introduce new employees to the IT help desk.
Workshops and Webinars: Teach users how to troubleshoot basic issues.
Additionally, collect feedback through surveys and user interviews to refine your help desk operations.
10. Ensure Scalability and Future Readiness
As your business grows, your IT help desk should evolve to meet increasing demands. Plan for scalability by:
Investing in flexible software and tools.
Expanding your team as ticket volumes rise.
Regularly updating your knowledge base and workflows.
Staying proactive ensures your IT help desk remains effective and adaptable.
Conclusion
Setting up an effective IT help desk for a small business requires careful planning, the right tools, and a skilled team. By defining objectives, implementing robust processes, and focusing on user experience, you can create a help desk that not only resolves issues efficiently but also supports your business’s growth.
To learn more about IT solutions tailored for small businesses, visit our IT help desk resources hub for expert insights and tools.
0 notes
Text
Fixing freezing or black screen when remote controlled PC monitor is turned off
🚨 Facing freezing or black screen issues while using remote control? 🖥️💻
This article dives into why turning off the monitor on a remote PC causes these problems and offers solutions! ✨
Learn about EDID, HPD, and DDC, and how to use an EDID emulator to fix these issues! 🔧
👉 Read the full article:
0 notes
Text
Your Key to Flawless, Secure, and Efficient Business Communication
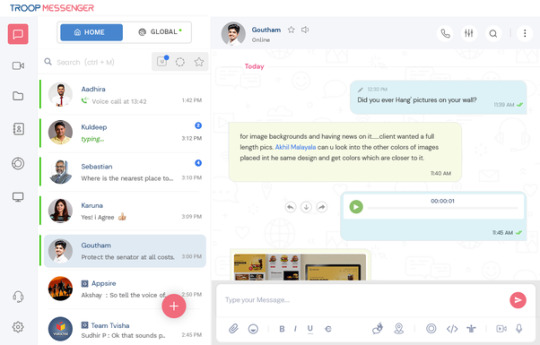
The safest and most effective way to do business is via Troop Messenger business chat. Check out Troop Messenger, the best business instant messaging solution accessible, with features like data protection, restricted and secured admittance protocol, ease of use, and intellectual property ownership. We specifically designed this business chat software with you in mind. Take pleasure in using Troop Messenger, a powerful communication tool.
What is Troop Messenger?
Troop Messenger is a centralised, secure digital platform that helps with team or interdepartmental communication. It is a solution designed to offer secure communications for Intelligence Agency Communication Solutions via message, phone, conference, and share screen, among many other time-saving productivity collaboration features.
On-premise Chat Server
Store your private and confidential call and conversation data inside your data centers using the highly secure and readily deployable on premise service paradigm! We developed this self-hosted collaboration solution with chat server that is compatible with the intranet to facilitate seamless workplace communication.
Sick of TeamViewer? Try Free TeamViewer Alternative
Troop Messenger is the best Team Viewer alternative that allows users to connect with remote teams with lightning speed.
While presenting the screen contents to remote users, one can highlight the required section with the help of screen annotation.
Why Choose On-Premise/Troop-GRIT?
Troop-GRIT is an On premise Chat Server edition of the Troop Messenger team collaboration application. That being said, you can deploy the self-managed Troop-GRIT on your local or on-premise servers to avoid third-party access to the application, such as from the public internet or any other means.
Free Live Chat Apps in India
Do you know that during the pandemic, some free live chat apps in India rescued the majority of businesses akin to online chat apps emphasizing the value of team communication while working remotely, amid the pandemic? These applications and website chat apps became an essential tool for keeping in touch with customers, clients, vendors, and others.
AnyDesk Alternatives
Market-available AnyDesk alternatives are capable of confusing users with their comparable capabilities. To avoid the contemplation process, read this blog and make an informed decision.
Troop Messenger, is one of the best team collaboration tools, offering real-time messaging, remote access, screen-sharing, and other features.
Free Screen Sharing Apps and Software
Screen sharing is one of the best dynamic collaboration features of Troop Messenger that allows members to share their screens during a chat conversation. Recipients can see real-time changes on the presenter's screen.
Troop Messenger's screen share function is powerful for enhancing team collaboration and conversation. With its smooth setup, interactive equipment, and strong security features, the Screen Sharing App on Troop Messenger permits green and productive virtual meetings. Whether you're conducting a presentation, troubleshooting trouble, or brainstorming together with your team, Troop Messenger makes display sharing simple and effective.
Empowering Collaboration Across Industries
Troop Messenger caters to diverse industries, offering tailored solutions to meet specific collaboration needs. Here's how it benefits various sectors:
1. Defence: We understand the unique challenges you face to protect your critical data. Therefore we have leveraged a thought-out military messaging solution that comes with the best possible benefits. Bind and protect your communication untouched by any intruders with the defense collaboration software, Troop Messenger. Feel secure with this messaging app for defense, with the following privileges.
2. Government: A resourceful cum end-to-end encrypted messaging app for Government sectors, designed to sort all your complicated work in one place shrinking the latency issues. HD Audio/ Video calls & messaging in one on one or groups, video conferences, secure file sharing, and among others are some of the features of this secure chat application.
3. Politics: Share party news, official announcements, latest activity updates of the party, all across one platform through customized political campaign software! Keep your party associates connected all the time through this Android and iOS voter management apps!
Provides secure collaboration for the political parties with:
Messaging, calling, audio-video conferencing, live-telecasting, voter participation on social media, and more! For Political Party Leaders, it's all in one safe political collaboration tool. Bring people, cadre, and party activists to this instant messaging app for political parties for optimal and well-organized party discussions. Spread your political campaign with the features and facilities.
4. Ministry of Defence: Troop Messenger facilitates transparent MOD communication services to convey the policy framework of MOD to the armed forces to carry out their responsibilities. You can bring all entities onto this DOD mobile application to deliver the information securely.
5. Army: Initiate Chat, Calls, remote screen access, conferencing, and more within this army chat app! Secure your sensitive army information with the world’s best security protocols and practices that combines the Double Ratchet algorithm, Pre-keys, and a triple Elliptic-curve Diffie–Hellman (3-DH) handshake, Curve25519, AES-256, HMAC-SHA256 as primitives.
6. Navy: High-trust and uniquely determined collaboration features for the seaborne branch! Integrate our end-to-end encrypted navy messaging system, the Troop Messenger, into your communication ecosystem; to securely chat, call, collaborate and meet.
7. Air Force: Reach the skies with secured Command-Control Instructions from the Base! We have incorporated highly secured collaborative tools for Airforce, such as chat, calling, audio-video conferencing, screen sharing, and others. Use it while conversating daily interactions, during natural disasters and internal disturbances, and for your other critical missions.
8. Defence Manufacturing: Our advanced Defence Manufacturing messaging system, Troop Messenger, help you exchange secure and classified conversations while you develop a comprehensive production infrastructure to produce weapons, systems, platforms, and military equipment required for defence across your Defence manufacturing industries.
9. Courts And Justice:Troop Messenger is an instant messaging and video conferencing tool designed for Indian courts. A unified communication system is necessary for a single, integrated, and independent judiciary to enable smooth cooperation among its judges, attorneys, court employees, etc. With this court administration software, you may transmit court orders over encrypted lines, upload case files to a secure file repository, broadcast court sessions live, and much more.
Virtual Communication Support for Virtual Courts
Courts need secure video solutions for virtual courts, such as Troop Messenger. Start conversating with the wide range of features and facilities available within this secure communication for court and justice department that helps have seamless virtual court proceedings.
10. Law Enforcement Agencies: Hinge on this law enforcement app to bring the hierarchies of your police system onto the unified communication platform to pass on the orders of law enforcement to the police on duty to maintain public safety and social order and prevent crime across your jurisdiction.
Secure Messaging Web and Mobile App for Police
A compliant messaging system for Police, Troop Messenger, is the best platform designed to solve the complexity of the communication process. With the help of advanced, safe, and secure features and intense collaboration facilities, it shall not allow classified data to fall into the hands of unauthorized persons.
11. Intelligence Agencies: Use this modern, agile, and sophisticated instant messenger for intelligence in your country’s internal and external intelligence agencies to encrypt and safeguard the flow of critical conversations while protecting your nation against domestic and foreign threats.
100+ features which can transform & enhance workplace productivity.
12. IT and Software Development: In the fast-paced world of IT and software development, effective collaboration is paramount for project success. Troop Messenger facilitates real-time communication among developers, testers, and project managers, enabling agile development practices and accelerating time-to-market.
13. Healthcare: In the healthcare sector, timely communication can be a matter of life and death. Troop Messenger provides secure messaging channels compliant with HIPAA regulations, enabling healthcare professionals to exchange sensitive patient information securely while collaborating on patient care.
14. Education: In the realm of education, seamless communication between educators, administrators, and students is essential for academic success. Troop Messenger serves as a virtual classroom, enabling educators to conduct lectures, share resources, and engage with students in real time, regardless of physical distance.
15. Finance and Banking: Security and compliance are paramount in the finance and banking industry. Troop Messenger offers end-to-end encryption and compliance features, ensuring secure communication among financial professionals while facilitating collaboration on transactions, compliance tasks, and risk management.
Features that Propel Team Collaboration
Troop Messenger offers a plethora of features geared towards facilitating smooth communication and collaboration among team members. Here's a closer look at some of its standout features:
Instant Messaging: With Troop Messenger, exchanging messages in real-time has never been easier. Whether you're seeking quick updates or engaging in brainstorming sessions, the app enables instant communication, fostering agility and responsiveness within teams.
File Sharing: Gone are the days of cumbersome email exchanges. Troop Messenger allows users to effortlessly share files of various formats, including documents, images, videos, and more. This feature ensures that crucial information is readily accessible to team members, promoting efficiency and productivity.
Group Chats: Collaboration often involves multiple stakeholders. Troop Messenger simplifies group communication by offering robust group chat functionality. Users can create dedicated chat groups for projects, departments, or specific topics, enabling seamless collaboration and knowledge sharing.
Voice and Video Calls: Sometimes, a face-to-face conversation is necessary to convey complex ideas or resolve issues effectively. Troop Messenger supports voice and video calls, allowing team members to connect instantly and engage in productive discussions irrespective of their physical location.
Integration Capabilities: Troop Messenger seamlessly integrates with a variety of third-party applications commonly used in the workplace, such as Google Drive, Dropbox, Trello, and more. This integration enhances workflow efficiency by centralizing communication and eliminating the need to switch between multiple platforms.
Remote Screen Share: Reach out to your remotest office teams with Troop Messenger’s productive and ultra-new screen share feature.
End-to-End Encryption: Your work conversations are under your complete control! Chats, calls, and conferences are end-to-end encrypted in this office chat app.
Conclusion
It becomes clear that Troop Messenger is a flexible and essential tool for encouraging teamwork and communication in a variety of industries. Troop Messenger is an office chat app that helps businesses meet their goals faster by streamlining processes, increasing productivity, and providing industry-specific solutions. Its extensive feature set and user-friendly design make it the ideal choice for any kind of organisation. Troop Messenger is the best team collaboration app for business talks and is suitable for nonprofit organisations, large corporations, and startups alike. It makes teamwork simple and boosts productivity in the digital sphere.
0 notes
Text
Strengthening Cybersecurity: A Collective Responsibility
Cybersecurity is a critical component of business operations and the responsibility of the business and the individual. A recent breach involving TeamViewer’s employee credentials underscores this. This incident serves as a reminder that it’s not solely the domain of the IT department; rather, it requires a concerted effort from every individual within the organization. Each employee plays a crucial role in maintaining security and must be aware of their actions and the potential impact. The Role of Businesses in Cybersecurity It goes without question that today businesses must foster a culture of cybersecurity awareness. This means implementing robust security protocols, continuously monitoring for threats, and educating employees about best practices. However, awareness alone isn’t enough. Companies must also invest in ongoing training and provide the necessary tools to help employees recognize and respond to potential threats. Empowering Employees with Training At Breach Secure Now, we understand the importance of employee engagement in cybersecurity. Our award-winning training programs are designed to keep up with current threats and ensure that employees are equipped with the knowledge and skills needed to protect sensitive information. These programs are not only informative but also engaging, making learning about cybersecurity an interactive and rewarding experience. Tools and Solutions for MSPs For Managed Service Providers (MSPs), Breach Secure Now offers tools to help clients build strong and all-encompassing cybersecurity programs. We create awareness and promote proactive security measures. Here’s how: Employee Security Training: Our comprehensive training modules cover many topics, from phishing awareness to secure password practices. These modules are regularly updated to address emerging threats, ensuring employees stay informed about the latest cybersecurity trends. Security Assessments: We provide thorough security assessments to identify vulnerabilities within an organization. These assessments offer valuable insights that MSPs can use to strengthen their clients’ security posture. Phishing Simulations: To test and improve employees’ response to phishing attempts, we offer realistic phishing simulations. These exercises help employees recognize phishing emails and understand the appropriate actions to take. Compliance Management: Our compliance management tools assist businesses in meeting regulatory requirements and maintaining industry standards. This is crucial for avoiding fines and protecting the organization’s reputation. Productivity Suite: Knowing how to utilize the tools available provides businesses with a more efficient and productive team. Let this breach at TeamViewer be a reminder that cybersecurity is a shared responsibility, requiring the involvement of the organization and its employees. MSPs can empower their clients to build a strong cybersecurity foundation and stay ahead of evolving threats by utilizing the tools and resources like those that we provide for our partners at BSN. For more information on how these can help your business, contact us today! The post Strengthening Cybersecurity: A Collective Responsibility appeared first on Breach Secure Now!. The post Strengthening Cybersecurity: A Collective Responsibility appeared first on IPM Computers LLC. from https://www.ipmcomputers.com/
0 notes
Text
How to share screen with teamviewer
TeamViewer is a popular remote desktop software application that allows you to share your screen, control another computer remotely, and provide or receive technical support. It’s widely used in various settings, from corporate environments to personal use. This comprehensive tutorial will guide you through the process of setting up and using TeamViewer to share your screen effectively. Table of…
View On WordPress
0 notes
Text
Remote IT Support Jobs
The landscape of work has dramatically shifted in recent years, with remote jobs becoming increasingly popular across various industries. Among these, remote IT support jobs stand out as a significant opportunity for tech-savvy professionals. If you’re considering a career in IT support but wish to work from the comfort of your home, this guide will provide you with all the information you need to get started.

Why Remote IT Support?
Remote IT support roles offer numerous advantages:
Flexibility: Work from anywhere, whether it's your home, a coffee shop, or a co-working space.
Work-Life Balance: Save time on commuting and have more time for personal activities.
Global Opportunities: Access job openings from companies around the world, not just in your local area.
Cost Savings: Cut down on daily expenses such as commuting costs and work attire.
Key Responsibilities of Remote IT Support Jobs
As a remote IT support specialist, your tasks may include:
Troubleshooting: Solving technical issues for clients or employees via phone, email, or chat.
Maintenance: Performing regular maintenance tasks to ensure systems are running smoothly.
Installation: Assisting with the installation of software and hardware.
Customer Service: Providing excellent customer service to ensure user satisfaction.

Essential Skills and Qualifications
To succeed in remote IT support, you’ll need:
Technical Proficiency: Strong knowledge of computer systems, networks, and software.
Problem-Solving Skills: Ability to diagnose and resolve issues efficiently.
Communication Skills: Clear and effective communication, both written and verbal.
Time Management: Ability to manage your time and prioritize tasks effectively.
Finding Remote IT Support Jobs
The demand for remote IT support professionals is high. To find these jobs, consider:
Job Boards: Websites like Indeed, Glassdoor, and LinkedIn often list remote IT support positions.
Company Websites: Many companies advertise job openings on their own career pages.
Freelancing Platforms: Websites like Upwork and Freelancer can offer remote IT support gigs.
Networking: Connect with other IT professionals through social media and industry events.
Tools and Technology for Remote IT Support
Working remotely in IT support requires the right set of tools and technologies:
Remote Desktop Software: Tools like TeamViewer or AnyDesk to access client systems remotely.
Communication Platforms: Slack, Microsoft Teams, or Zoom for staying connected with colleagues and clients.
Project Management Software: Asana, Trello, or Jira to keep track of tasks and projects.
Knowledge Base: A comprehensive knowledge base or FAQ to quickly address common issues.
Tips for Success in Remote IT Support
Set Up a Dedicated Workspace: Create a comfortable and efficient workspace at home. Ensure you have a reliable internet connection, ergonomic furniture, and minimal distractions.
Stay Updated: Keep up with the latest technology trends and updates in the IT field. Continuous learning is crucial in tech.
Develop Soft Skills: Improve your communication and customer service skills. Being able to explain technical issues in simple terms is invaluable.
Manage Your Time: Use tools and techniques to manage your workload and deadlines effectively. Techniques like the Pomodoro Technique can help improve productivity.
Document Everything: Keep detailed records of the issues you handle and the solutions you provide. This can help in building a knowledge base and improving your efficiency.
Challenges of Remote IT Support and How to Overcome Them
Remote work is not without its challenges. Some common issues and solutions include:
Isolation: Remote work can be isolating. Combat this by scheduling regular check-ins with your team and participating in virtual social activities.
Communication Barriers: Ensure clear and concise communication by using various tools and confirming receipt of important messages.
Time Zone Differences: If working with a global team, be mindful of time zones and try to schedule meetings at times that are convenient for everyone.

Career Growth and Opportunities
Remote IT support can be a stepping stone to other career opportunities within the tech industry. Possible career paths include:
IT Support Manager: Overseeing a team of IT support specialists.
Systems Administrator: Managing and maintaining an organization’s IT infrastructure.
Network Engineer: Designing and implementing network solutions.
Cybersecurity Specialist: Protecting systems and data from cyber threats.
Ready to Start Your Remote IT Support Career?
Remote IT support jobs offer a rewarding career path with the flexibility to work from anywhere. Whether you're just starting out in IT or looking to transition from an office-based role, remote work can provide the balance and opportunities you seek.
For more information on remote IT support jobs and to explore current job openings, visit earnworkingfromhome.com. Start your journey to a fulfilling remote IT support career today!
0 notes
Text
What is Remote Desktop Connection Manager (RDCMan)?
Remote Desktop Connection Manager (RDCMan) is a free Microsoft tool that allows IT professionals and system administrators to manage and organize multiple remote desktop connections from a single, intuitive interface.
RDCMan is a comprehensive application that simplifies the process of remotely accessing and managing various computers, servers, and other devices within an organization. Unlike the standard Remote Desktop Connection (RDC) tool, which can only handle a single remote connection at a time, RDCMan enables users to consolidate all their remote connections into a single window.
With RDCMan, users can:
Manage and maintain servers, workstations, and other devices remotely
Access and troubleshoot systems from a central location
Manage and deploy software updates
Monitor system performance and resource usage
Provide technical support to users
The key features that set RDCMan apart from other remote connection management tools include the ability to:
Organize connections into groups and sessions for better management
Save connection details, including user IDs and passwords, for quick access
Quickly switch between multiple remote connections without having to re-enter credentials
Customize settings and preferences to suit individual needs

How to Use RDCMan
To use RDCMan, users first need to download the latest version from the Microsoft website. Unlike previous versions, the current version (v2.92) does not require installation, as it is a standalone application. Once the download is complete, users can extract the files and start using the tool. RDCMan provides several keyboard shortcuts to help users navigate and manage their remote connections more efficiently. Some of the common shortcuts include:
F2: Rename the selected connection
F5: Refresh the current view
Ctrl + N: Create a new connection
Ctrl + W: Close the current connection
Ctrl + Shift + N: Create a new group
To set up a new remote connection, users can click the “New” button and enter the necessary details, such as the computer name, user ID, and password. They can also organize their connections into groups and sessions for better management.
RDCMan Vulnerability and Security Considerations
In 2020, a security researcher discovered a vulnerability in RDCMan that could allow an attacker to execute malicious code on the target system. This vulnerability was quickly addressed by Microsoft, who released a patch in RDCMan version 2.7 that included a validation mechanism for opening rdg files.
It’s important to note that, like any software, RDCMan should be regularly updated to ensure that users receive the latest security patches and fixes. Failure to do so could leave the system vulnerable to potential attacks. 3Additionally, users should be cautious when opening .rdg files from untrusted sources, as they could potentially contain malicious code. It’s recommended to only open .rdg files from trusted sources and to always verify the integrity of the file before opening it.
Alternatives to RDCMan
While RDCMan is a popular and widely-used tool for managing remote desktop connections, there are several alternative solutions available in the market. Some of the popular alternatives include:
mRemoteNG: A free and open-source remote connection manager that supports a wide range of protocols, including RDP, VNC, SSH, and Telnet.
Devolutions Remote Desktop Manager: A comprehensive remote connection management solution that offers features such as password management, role-based access control, and two-factor authentication.
TeamViewer: A popular remote desktop software that allows users to access and control remote computers, as well as collaborate with others in real time.
LogMeIn: A cloud-based remote access and support solution that enables users to securely connect to and control remote computers from anywhere.
When choosing a remote connection management tool, it’s important to consider factors such as the number of remote connections, the level of security required, and the specific features and integrations needed to support the organization’s IT infrastructure.
Conclusion
Remote Desktop Connection Manager (RDCMan) is a powerful and versatile tool that simplifies the process of managing and organizing multiple remote desktop connections. With its ability to consolidate connections, save user credentials, and provide customizable settings, RDCMan has become an essential tool for IT professionals and system administrators who need to efficiently manage and maintain remote systems.
While RDCMan has faced some security concerns in the past, the latest version of the tool includes robust security measures to protect against potential attacks. By regularly updating the software and exercising caution when opening .rdg files, users can ensure that RDCMan remains a secure and reliable solution for their remote connection management needs.
0 notes
Text
pondering some minor Work Things while the insomnia wins and yknow. i do love the two man team of very autistic dudes who have spent 30+ years developing and maintaining the extensive, industry-specific inventory/customer/accounting/sales management software that we use at my job. their names are the equivalent of like. matt and richard. one of them is british. every time i call them for something and they need to get on teamviewer to help me they immediately start poking around in my computer settings and sending me amazon links to pieces of hardware bc it drives them absolutely bugfuck crazy how slow our ancient desktops are. i love them. but i DO wonder about some of the limitations theyve put on the accounting side of the software sometimes.... like.... boys. fellas. why in this day and age is there a character limit of thirty on the payee field of checks...... today i was trying to write a check to like. literally one of the most prominent and trusted labs and educators in the industry and i couldnt fit the full name on the check. insanity
#sage talks#theyre so funny and im so grateful to them but you can Tell neither of them gives two shits about accounting skdndks
1 note
·
View note