#ICT Performance_Task
Explore tagged Tumblr posts
Text
What is Empowerment Technologies?
This blog, Empowerment Technologies, is an insight into what I have learned on our lessons about Empowerment Technologies: ICT for Professional Tracks, for 11th grade, under the teaching of Miss Shaira Denise Dela Cruz. The goal of this blog is to promote ICT and give you some insight into ICT

The first lesson that was discussed was, what is ICT? ICT is the abbreviation for Information and Communication Technologies. It refers to technologies that provide access to information through telecommunications such as mobile phones, wireless networks, telephones, and other communication mediums. The current state of ICT is WWW or World Wide Web.
The World Wide Web(WWW), commonly known as the Web, is an information system where documents and other web resources are identified by Uniform Resource Locators, which may be interlinked by hypertext, and are accessible over the Internet. It has three versions which are Web 1.0, Web 2.0, and Web 3.0. Web 1.0 is the first version and most web pages were static or “read-only web.”
The second and most used is Web 2.0, which allows users to interact and contribute with the page instead of just reading a page, the users are able to create a user account. Web 2.0 offers us five features: Folksonomy, Rich User Experience, Long Tail, User Participation, and software as a service.
The last is Web 3.0. Its aim is to have machines understand the user’s preference to be able to deliver web content specifically targeting the user. Web 3.0 hasn’t released yet as it still has some problems. Those problems are compatibility, security, vastness, vagueness, and logic.

Moving on to the next lesson which is all about ‘Online Saftey, security, ethics, and etiquette.’
The Internet consists of tens of thousands of interconnected networks run by service providers, individual companies, universities, and governments. It is defined as an information highway, which means anyone can access any information through the internet. That is why the internet is one of the most dangerous places, the reason why it is important how to keep yourself and your personal information safe. Some of the information that is in rick when spoiled on the internet are names of your immediate family, address, phone or home number, birthday, email address, your full name, and your previous and current school. It is important to keep this information top secret as cyber-creeps can use these to find you.
To keep yourself safe:
Be mindful of what you share online.
Do not just accept terms and conditions, read it.
Keep your passwords to yourself, and make sure your password is long, strong, and unique.
Do not talk or meet up with someone you don’t know.
Never post anything about a future vacation. This can signal some robbers about which date they can come and rob your house. It is better to post about your vacation when you got home already.
Add friends you know in real life, don’t accept someone you barely know or met.
Avoid visiting or downloading anything from an untrusted website, make sure to check the icon beside the search box. *picture* According to DigiCert Blog, “How to Know if a Website is Secure?”, Look at the URL of the website. If it begins with “https” instead of “http” it means the site is secured using an SSL certificate (the s stands for secure). SSL certificates secure all of your data as it is passed from your browser to the website’s server.
Make your home wifi private by adding a password.
Make sure to install and update antivirus software on your computer.
Do not reply or check links from suspicious emails as it can lead you to an untrusted site and can hack your laptop or social media.

To give you more information, here are some of the internet threats that we need to be aware of and try to avoid:
The Malware, stands for malicious software. It includes virus, worm, trojan, spyware, adware, and ransomware. The virus is the most common malware. It is a malicious program designed to replicate itself and transfer from one computer to another (internet, local networks, FDs, CDs,etc.). Worms is a standalone piece of malicious software that reproduces itself and spreads from computer to computer. The trojan is a malicious program that disguises as a useful program but once downloaded or installed, leaves your PC unprotected and allows hackers to get your information. Spyware is defined by Webroot Cybersecurity as "malware used for the purpose of secretly gathering data on an unsuspecting user." It is a program that runs in the background and spies your behavior as you are on your computer. Adware is malware that forces your browser to redirect to web advertisements, which often themselves seek to download further, even more, malicious software. Lastly, Ransomware, also known as scareware. This is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.
The Spam, this is any kind of unwanted, unsolicited digital communication, often an email, that gets sent out in bulk.
The Phishing, is a cybercrime in which a target/s are contacted by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.

Lastly, before we move to the next lesson it is important to know ‘The Core Rules of Netiquette’ are excerpted from the book Netiquette by Virginia Shea.
First, Remember the Human.When communicating online, practice the Golden rule: Do unto others as you would have others do unto you. Remember that your written works or messages are read by real people, therefore you should ask yourself, "Would I be okay with this if someone else had written it?" before sending it.
Second, Adhere to the same standards of behavior online that you follow in real life. It is a must that your best to act within the laws and ethical manners of society whenever you inhabit "cyberspace." Standards of behavior may be different in some areas of cyberspace, but they are not lower than in real life. Be ethical. Don't believe anyone who says, "The only ethics out there are what you can get away with."
Third, Know where you are in cyberspace. What's perfectly acceptable in one area may be dreadfully rude in another. And because Netiquette is different in different places, it's important to know where you are. Thus the next corollary: Lurk before you leap.
Fourth, Respect other people’s time and bandwidth. Online communication takes time: time to read and time in which to respond. Most people today lead busy lives, just like you do, and don't have time to read or respond to frivolous emails or discussion posts. It's your responsibility to ensure that the time they spend reading your posting isn't wasted.
Fifth, Make yourself look good online. One of the best things about the virtual world is the lack of judgment associated with your physical appearance, the sound of your voice, or the clothes you wear. However, you will be judged by the quality of your writing so keep in mind the following tips: (1)Always check for spelling and grammar errors, (2) Know what you're talking about and state it clearly
Sixth, Share expert knowledge. The reason for asking questions online works is that a lot of knowledgeable people are reading the questions. And if even a few of them offer intelligent answers, the sum total of world knowledge increases. The Internet itself was founded and grew because scientists wanted to share information. Gradually, the rest of us got in on the act. So do your part. Despite the long lists of no-no's in this book, you do have something to offer. Don't be afraid to share what you know.
Seventh, Help keep flame wars under control. "Flaming" is what people do when they express a strongly held opinion without holding back any emotion.g. While "flaming" is not necessarily forbidden in virtual communication, "flame wars," when two or three people exchange angry posts between one another, must be controlled or the camaraderie of the group could be compromised. Don't feed the flames; extinguish them by guiding the discussion back to a more productive direction.
Eighth, Respect other people’s privacy. Depending on what you are reading in the virtual world, be it an online class discussion forum, Facebook page, or an email, you may be exposed to some private or personal information that needs to be handled with care. Thus, Just as you expect others to respect your privacy, so should you respect the privacy of others. Be sure to err on the side of caution when deciding to discuss or not to discuss virtual communication.
Ninth, Don’t abuse your power. Some people in cyberspace have more power than others. There are wizards in MUDs (multi-user dungeons), experts in every office, and system administrators in every system. Knowing more than others, or having more power than they do, does not give you the right to take advantage of them. For example, sysadmins should never read private emails.
Tenth, Be forgiving of other people’s mistakes. Everyone was a network newbie once. So when someone makes a mistake, whether it's a spelling error or a spelling flame, a stupid question or an unnecessarily long answer, be kind about it. If you do decide to inform someone of a mistake, point it out politely, and preferably by private email rather than in public. Give people the benefit of the doubt; assume they just don't know any better.

The last lesson that was taught to us is ‘Advanced Word Processing Skill’. This lesson focuses on the software word processor the ‘Microsoft Word.’
A Word Processor is an electronic device or computer software application that performs the task of composing, editing, formatting, and printing of documents.
Microsoft Word is a word processor developed by Microsoft and the first released on October 25, 1983. Microsoft Word has features and functions which are not mostly known by others. These are the Auto-Correct, Grammar Checker, Read Aloud, Template, Thesaurus, Mail Merge, and Text Wrap.
Advance Features of Microsoft Word are discussed. Beginning with the kinds of Materials we can have in Microsoft Word.
The first is Pictures. Generally, these are electronic or digital pictures or photographs you have saved on any local storage device. There are three file formats that pictures have which are JPEG or Joint Photographic Expert Group, this can support 16.7 million colors so that it is suitable for use when working with full-color photographic images, GIF or Graphics Interchange Format, this is used for computer-generated images that support animation, can only support up to 256 colors., lastly, PNG or Portable Network Graphics, this is similar to GIF except it has smaller file size but does not support animation, it can display up to 16 million colors and allows the control of the transparency level or opacity of images.
The second material is Clip Art. This is generally a GIF type; line art drawings or images used as a generic representation for ideas and objects that you might want to integrate into your document.
The third is Shapes. These are printable objects or materials that you can integrate in your document to enhance its appearance or to allow you to have some tools to use for composing and representing ideas or messages. The fourth is Smart Art. Generally, these are predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature.
The fifth is Chart. Another type of material that you can integrate into your Word document that allows you to represent data characteristics and trends.
The sixth is Screenshot. Sometimes, creating reports or manuals for training or procedure will require the integration of a more realistic image of what you are discussing on your report or manual.
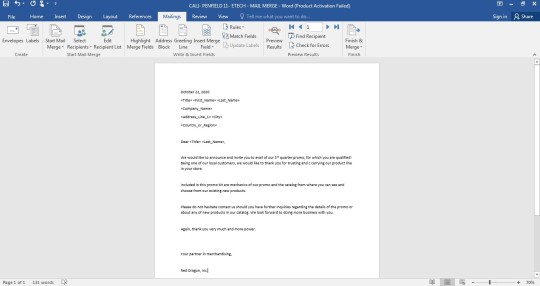
Moving on to the most focused part of the lesson which is the Mail Merge. Mail Merge is a useful tool that allows you to produce multiple letters, labels, envelopes, name tags, and more using information stored in a list, database, or spreadsheet. When these two documents are combined (merged), each document includes the individual names and addresses you need to send it to. The two components of Mail Merge are the Form Document, this contains the main body of the message we want to convey or send., and the List or Data File, This is where the individual information or data that needs to be plugged in (merged) to our form document is placed and maintained.
It was demonstrated to us, how to use and make mail merge, and here’s mine:

Before ending this blog, I would like to show you some of my modules for the subject Empowerment Technologies(ETech): ICT for Professional Track.
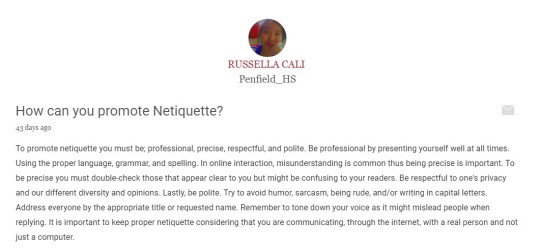
First, the open forum about the “How can you promote Netiquette?”
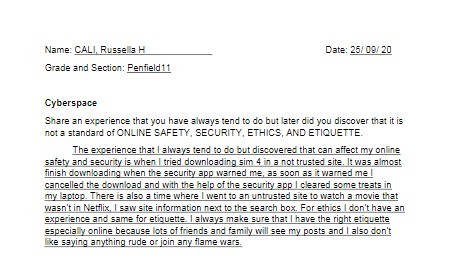
Second, an assignment about “Cyberspace: Share an experience that you have always tend to do but later did you discover that it is not a standard of ONLINE SAFETY, SECURITY, ETHICS, AND ETIQUETTE. “
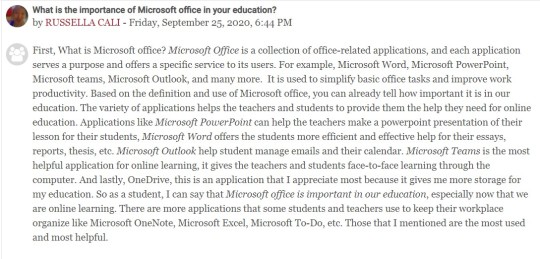
Third, another open forum about “What is the importance of Microsoft office in your education?”
Lastly is another assignment, making an Infographic: Promoting your specific track/strand. My infographic is a promotion of my strand, STEM or Science, Technology, Engineering, and Mathematics.
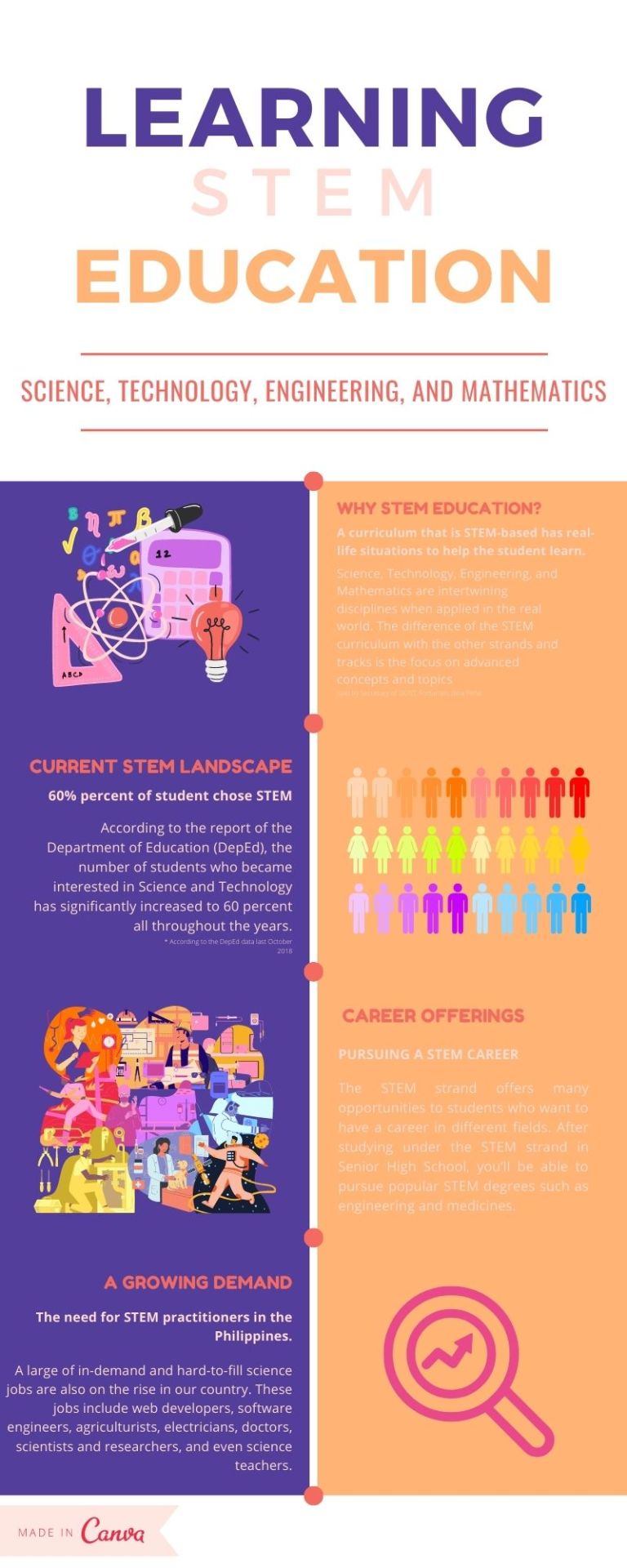
Hope you learn a lot from this blog as I learn a lot from my subject teacher for Empowerment Technologies(ETech): ICT for Professional Track.
Let this day be filled with success in all the ventures you make today. Have a great day!
Photo Credits:
1
https://curatti.com/wp-content/uploads/2019/11/WWW-Image-1.jpg
2
https://go4customer.com/articleimages/1581925569Safety_Internet_Day.png
3
https://futureofsourcing.com/sites/default/files/articles/internet_attacks.jpg
4
https://i.pinimg.com/originals/fc/37/e1/fc37e162244d19115d88ab58e07ccc2b.png
5
https://cdn.guidingtech.com/imager/assets/2019/05/226896/Image-Best-Microsoft-Word-Online-Tips-and-Tricks 2_4d470f76dc99e18ad75087b1b8410ea9.png?1558678050
2 notes
·
View notes