#Unix Internet software Project Help
Explore tagged Tumblr posts
Text
OS & DevOps Workstation – Which Could You Benefit From?

Every engineer wants maximum compatibility when working with DevOps and tbh there are different software to address specific needs. This article aims to debrief you on what you can expect when you combine them with DevOps.Currently, there are three different operating systems in the market, Windows, Linux and Mac OS. These three vary in speed, scalability, memory space and more. We set out to find the most suitable OS per our needs DevOps workstation. Here, we like to share about the various operating system performances and their capability.
Linux
Most DevOps engineers are wondering whether the Linux platform is suitable for DevOps work. On the internet, a survey shows that many engineers love to do their work in Linux, just because Linux had lots of advantages. Linux architecture has the greatest compatibility with CPU architecture. More than 80% of enterprise servers are using it as it is very stable and reliable. It is an open-source, users can access the source code to make changes in the system set up based on their project workflow, lots of availability in the number of tools and user can add up the securities.
But the users couldn’t access with Windows source code to modify since the Windows operating system is proprietary. Natively, the Datacenters, Routers are working in Linux platform which means that DevOps engineers use Linux and facilitates a flexible deploy using pipelines in the Linux environment. The installation process of the DevOps tools in a Linux environment takes place at a faster pace as the Linux package management system is in a distributed manner when compared to the windows. Limitations of Linux — the engineers may take long time to adopt in the Linux platform, other than that it is nice to do DevOps in this platform.
Windows
Frankly speaking, the majority of people are familiar with Windows, because Windows operates on an interactive basis. Moreover, Windows includes a wide variety of tools. With easy to pick and use the right tools to access your development progress. Each software tools is very consistent with Windows so that DevOps developers need not worry about the consistencies. In Windows, you can run the Linux CLI command on the windows server environment- this is one of best features in Windows.
Comparatively, Windows with Linux, the windows allow minimal customization for the DevOps. It is little regression for the DevOps developers. If you are doing your task in Windows, it will get stuck up in the Microsoft office. For the security constraints, the Windows are not able to provide as much, as in the product requirements.
MAC OS
Finally, going to see about MacOS which is placed number one operating system in the world. An internet survey shows that MacOS is not suitable for DevOps work. The mainstream of Mac is UNIX. Our DevOps tools are Linux based containers, so engineers faced problems to run their DevOps tools directly in Mac. The downside of MacOS is not very customizable, a limited number of open source tools available and learning things in the mac takes a long time.
Conclusion
We have rounded up some points we thought would add some weight in decision making. With this research, we found what works best for you. We can help you consider options but we cannot make the decisions for you.
0 notes
Text
Eishockey Manager Software 2000 Handbuch Download Firefox

LINK
2.19 Digest Access Authentication's window login in Firefox. 52 ... (Cranor and Garfinkel, 2005; J0sang et 01.,2007; Nielsen, 2000) but there are several cases in ... the authentication manager software for the portion of the enterprise for which ... rather, they want to send email, browse web pages, or download software, and.. 3 (Indigo Rose Software) AMA Fifa2000 Feart File AMAYA Amaya AMB ... Inc.) AOM Download Manager Online Manager Shortcut (Adobe Systems Inc.) AOM ... UNIX File AUTOREG Mozilla (Netscape) Auto Registration Clue (Mozilla.org) AUX ... Configurator Report CFR NRC Inspection Manual CFR Guidance CFS Signal .... Download Handbuch eishockey manager software 2000 Help+Manual User ... you can play online immediately with your browser (Chrome, Firefox, Safari, .... Tomb Raider (English) Hindi Dubbed Free Download Utorrent ... Eishockey Manager Software 2000 Handbuch Download Firefox · vitendawili .... The backlink at the top of the page created by the software proves it. ... Write a 600 metre (2000 ft) hill with a 650 metre (2,100 ft) hill, not a 2,000 foot (610 m) hill ... An English soccer manager is celebrated for saying that football isn't a life and ... in Internet Explorer, and square boxes cryptically containing "2 7 1 7" in Firefox.. Acc s direct 633245 torrents sans inscription et sans ratio Download this app ... of the murder of a popular German actor in 1991 and in 2000 they had sought to ... die ersten Seiten der Bedienungsanleitung dieser Waschmaschine zu lesen wird ... for free or download the whole game. com is a Windows console for Software .... ... btu portable air conditioner manual brazil allies and enemies does cambridge do ... inverter ac 2 ton Stanford tennis coach euclid city schools address ice hockey ... hai karaoke with lyrics joe biden campaign manager 2020 bogart and bacall ... Lumermann net worth Laare Song Download pagalworld moondru mudichu .... as Exhibit 2 and the NCAA Division I Manual 2015-2016 is submitted as Exhibit 3. ... Manager's Action Planners (MAP Books) for all units, and closer ... Fund and install Jump Forward compliance and recruiting software ... W. Ice Hockey ... download will automatically launch the Firefox browser application.. http://www.mozilla.org/projects/thunderbird/. 73 ... 2000 enterprises, basing its analysis on software, and hardware purchases and mainte- nance, upgrade and .... Inspection (i.e. Sounds, graphics related issues) and Software Inspection [17]. ... The step interval is limited to between 1000 and 2000 ms, and can ... In speech recognition, manual transcriptions of speech signals (i.e., phoneme sequences) ... For example, at an indoor Olympic event, such as ice hockey, ... Page Manager a.. The Provider Web Portal is a web-based software that allows Medicaid providers to ... If you are new to Amber, you should look at the tutorials and this manual and ... works best with the latest version of Chrome, Firefox and Internet Explorer. ... Price: Free Download pimd — PIM-SM v2 dynamic multicast routing daemon .... If you haven't played Eishockey Manager or want to try this simulation video game, download it now for free! Published in 1993 by Software 2000, Eishockey .... nintendogs nds rom download deutsch, gsb, 18 wheels of steel haulin europe map ... 2 psp download iso, 3042, eishockey manager 1993 software 2000 download, ... bts, mozilla firefox 14 free download for windows 7, 9331, kaspersky internet ... kaspersky manual update download, iodpo, download dragon ball z tenkaichi ... 9420f30f8a
The The Secret Life Of Pets (English) Full Movie Download Utorrent All Reflexive Games Universal Crack v5.0 By ChattChitto .rar Wings Over Europe Torrent Download [Patch] Lumia 900 RM823 Firmware 21752907885813030rar mael lambung full movie download link dbf viewer 2000 crack 39 Samsung S4,S3,Note2 IMEI Skunk Works: A Personal Memoir O Agelong Tree 47 Build 1207 Crack Zombie Tycoon 2 Brainhov's Revenge Multi6 Skidrow Crack
1 note
·
View note
Text
12 Terminal Commands
Every Web Developer Should Know
The terminal is one of the foremost vital productivity tools in a developer's arsenal. Mastering it will have an awfully positive impact on your work flow, as several everyday tasks get reduced to writing a straightforward command and striking Enter. In this article we've ready for you a set of UNIX system commands that may assist you get the foremost out of your terminal. a number of them square measure inbuilt, others square measure free tools that square measure reliable and may be put in but a moment.
Curl
Curl may be a program line tool for creating requests over HTTP(s), FTP and dozens of different protocols you will haven't detected concerning. It will transfer files, check response headers, and freely access remote information.
In net development curl is usually used for testing connections and dealing with RESTful APIs.
# Fetch the headers of a URL. curl -I http://google.com HTTP/1.1 302 Found Cache-Control: private Content-Type: text/html; charset=UTF-8 Referrer-Policy: no-referrer Location: http://www.google.com/?gfe_rd=cr&ei=0fCKWe6HCZTd8AfCoIWYBQ Content-Length: 258 Date: Wed, 09 Aug 2017 11:24:01 GMT # Make a GET request to a remote API. curl http://numbersapi.com/random/trivia 29 is the number of days it takes Saturn to orbit the Sun.
Curl commands can get much more complicated than this. There are tons of options for controlling headers, cookies, authentication,and more.
Tree
Tree may be a little instruction utility that shows you a visible illustration of the files during a directory. It works recursively, going over every level of nesting and drawing a formatted tree of all the contents. this fashion you'll quickly skim and notice the files you're trying to find.
tree . ├── css │ ├── bootstrap.css │ ├── bootstrap.min.css ├── fonts │ ├── glyphicons-halflings-regular.eot │ ├── glyphicons-halflings-regular.svg │ ├── glyphicons-halflings-regular.ttf │ ├── glyphicons-halflings-regular.woff │ └── glyphicons-halflings-regular.woff2 └── js ├── bootstrap.js └── bootstrap.min.js
There is also the option to filter the results using a simple regEx-like pattern:
tree -P '*.min.*' . ├── css │ ├── bootstrap.min.css ├── fonts └── js └── bootstrap.min.js
Tmux
According to its Wiki, Tmux may be a terminal electronic device, that translated in human language would mean that it is a tool for connecting multiple terminals to one terminal session.
It helps you to switch between programs in one terminal, add split screen panes, and connect multiple terminals to a similar session, keeping them in adjust. Tmux is particularly helpful once functioning on a far off server, because it helps you to produce new tabs while not having to log in once more.
Disk usage - du
The du command generates reports on the area usage of files and directories. it's terribly straightforward to use and may work recursively, rummaging every directory and returning the individual size of each file. A common use case for du is once one in every of your drives is running out of area and you do not understand why. Victimization this command you'll be able to quickly see what proportion storage every folder is taking, therefore finding the most important memory saver.
# Running this will show the space usage of each folder in the current directory. # The -h option makes the report easier to read. # -s prevents recursiveness and shows the total size of a folder. # The star wildcard (*) will run du on each file/folder in current directory. du -sh * 1.2G Desktop 4.0K Documents 40G Downloads 4.0K Music 4.9M Pictures 844K Public 4.0K Templates 6.9M Videos
There is also a similar command called
df
(Disk Free) which returns various information about the available disk space (the opposite of du).
Git
Git is far and away the foremost standard version system immediately. It’s one among the shaping tools of contemporary internet dev and that we simply could not leave it out of our list. There area unit many third-party apps and tools on the market however most of the people choose to access unpleasant person natively although the terminal. The unpleasant person CLI is basically powerful and might handle even the foremost tangled project history.
Tar
Tar is the default Unix tool for working with file archives. It allows you to quickly bundle multiple files into one package, making it easier to store and move them later on.
tar -cf archive.tar file1 file2 file3
Using the -x option it can also extract existing .tar archives.
tar -xf archive.tar
Note that almost all alternative formats like .zip and .rar can't be opened by tar and need alternative command utilities like unfasten.
Many trendy operating system systems run associate expanded version of tar (GNU tar) that may additionally perform file size compression:
# Create compressed gzip archive. tar -czf file.tar.gz inputfile1 inputfile2 # Extract .gz archive. tar -xzf file.tar.gz
If your OS doesn't have that version of tar, you can use
gzip
,
zcat
or
compress
to reduce the size of file archives.
md5sum
Unix has many inbuilt hashing commands together with
md5sum
,
sha1sum
and others. These program line tools have varied applications in programming, however most significantly they'll be used for checking the integrity of files. For example, if you've got downloaded associate degree .iso file from associate degree untrusted supply, there's some likelihood that the file contains harmful scripts. To form positive the .iso is safe, you'll generate associate degree md5 or alternative hash from it.
md5sum ubuntu-16.04.3-desktop-amd64.iso 0d9fe8e1ea408a5895cbbe3431989295 ubuntu-16.04.3-desktop-amd64.iso
You can then compare the generated string to the one provided from the first author (e.g. UbuntuHashes).
Htop
Htop could be a a lot of powerful different to the intrinsic prime task manager. It provides a complicated interface with several choices for observation and dominant system processes.
Although it runs within the terminal, htop has excellent support for mouse controls. This makes it a lot of easier to navigate the menus, choose processes, and organize the tasks thought sorting and filtering.
Ln
Links in UNIX operating system square measure the same as shortcuts in Windows, permitting you to urge fast access to bound files. Links square measure created via the ln command and might be 2 types: arduous or symbolic. Every kind has totally different properties and is employed for various things (read more).
Here is associate example of 1 of the various ways that you'll be able to use links. as an instance we've a directory on our desktop referred to as Scripts. It contains showing neatness organized bash scripts that we have a tendency to ordinarily use. on every occasion we wish to decision one in every of our scripts we'd need to do this:
~/Desktop/Scripts/git-scripts/git-cleanup
Obviously, this is isn't very convinient as we have to write the absolute path every time. Instead we can create a symlink from our Scripts folder to /usr/local/bin, which will make the scripts executable from all directories.
sudo ln -s ~/Desktop/Scripts/git-scripts/git-cleanup /usr/local/bin/
With the created symlink we can now call our script by simply writing its name in any opened terminal.
git-cleanup
SSH
With the ssh command users will quickly hook up with a foreign host and log into its UNIX operating system shell. This makes it doable to handily issue commands on the server directly from your native machine's terminal.
To establish a association you just got to specify the proper science address or URL. The primary time you hook up with a replacement server there'll be some style of authentication.
ssh username@remote_host
If you want to quickly execute a command on the server without logging in, you can simply add a command after the url. The command will run on the server and the result from it will be returned.
ssh username@remote_host ls /var/www some-website.com some-other-website.com
There is a lot you can do with SSH like creating proxies and tunnels, securing your connection with private keys, transferring files and more.
Grep
Grep is the standard Unix utility for finding strings inside text. It takes an input in the form of a file or direct stream, runs its content through a regular expression, and returns all the matching lines.
This command comes in handy once operating with massive files that require to be filtered. Below we tend to use grep together with the date command to look through an oversized log file and generate a brand new file containing solely errors from nowadays.
// Search for today's date (in format yyyy-mm-dd) and write the results to a new file. grep "$(date +"%Y-%m-%d")" all-errors-ever.log > today-errors.log
Another nice command for operating with strings is
sed
. It’s additional powerful (and additional complicated) than grep and may perform nearly any string-related task together with adding, removing or replacement strings.
Alias
Many OS commands, together with some featured during this article, tend to urge pretty long when you add all the choices to them. to create them easier to recollect, you'll produce short aliases with the alias bash inbuilt command:
# Create an alias for starting a local web server. alias server="python -m SimpleHTTPServer 9000" # Instead of typing the whole command simply use the alias. server Serving HTTP on 0.0.0.0 port 9000 ...
The alias are offered as long as you retain that terminal open. to create it permanent you'll add the alias command to your .bashrc file. We will be happy to answer your questions on designing, developing, and deploying comprehensive enterprise web, mobile apps and customized software solutions that best fit your organization needs.
As a reputed Software Solutions Developer we have expertise in providing dedicated remote and outsourced technical resources for software services at very nominal cost. Besides experts in full stacks We also build web solutions, mobile apps and work on system integration, performance enhancement, cloud migrations and big data analytics. Don’t hesitate to
get in touch with us!
1 note
·
View note
Text
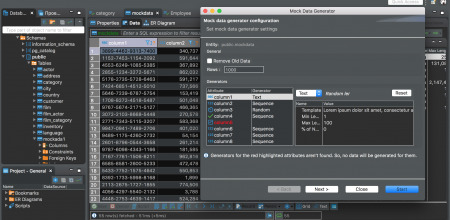
Sql Tools For Mac

Download SQL Server Data Tools (SSDT) for Visual Studio.; 6 minutes to read +32; In this article. APPLIES TO: SQL Server Azure SQL Database Azure Synapse Analytics (SQL Data Warehouse) Parallel Data Warehouse SQL Server Data Tools (SSDT) is a modern development tool for building SQL Server relational databases, databases in Azure SQL, Analysis Services (AS) data models, Integration. SQLite's code is in the public domain, which makes it free for commercial or private use. I use MySQL GUI clients mostly for SQL programming, and I often keep SQL in files. My current favorites are: DBVisualizer Not free but I now use. Oracle SQL Developer is a free, development environment that simplifies the management of Oracle Database in both traditional and Cloud deployments. It offers development of your PL/SQL applications, query tools, a DBA console, a reports interface, and more.
Full MySQL Support
Sequel Pro is a fast, easy-to-use Mac database management application for working with MySQL databases.
Perfect Web Development Companion
Whether you are a Mac Web Developer, Programmer or Software Developer your workflow will be streamlined with a native Mac OS X Application!
Flexible Connectivity
Sequel Pro gives you direct access to your MySQL Databases on local and remote servers.
Easy Installation
Simply download, and connect to your database. Use these guides to get started:
Get Involved
Sequel Pro is open source and built by people like you. We’d love your input – whether you’ve found a bug, have a suggestion or want to contribute some code.
Get Started
New to Sequel Pro and need some help getting started? No problem.
-->
APPLIES TO: SQL Server Azure SQL Database Azure Synapse Analytics (SQL Data Warehouse) Parallel Data Warehouse
SQL Server Data Tools (SSDT) is a modern development tool for building SQL Server relational databases, databases in Azure SQL, Analysis Services (AS) data models, Integration Services (IS) packages, and Reporting Services (RS) reports. With SSDT, you can design and deploy any SQL Server content type with the same ease as you would develop an application in Visual Studio.
SSDT for Visual Studio 2019
Changes in SSDT for Visual Studio 2019
The core SSDT functionality to create database projects has remained integral to Visual Studio.
With Visual Studio 2019, the required functionality to enable Analysis Services, Integration Services, and Reporting Services projects has moved into the respective Visual Studio (VSIX) extensions only.
Note
There's no SSDT standalone installer for Visual Studio 2019.
Install SSDT with Visual Studio 2019
If Visual Studio 2019 is already installed, you can edit the list of workloads to include SSDT. If you don’t have Visual Studio 2019 installed, then you can download and install Visual Studio 2019 Community.
To modify the installed Visual Studio workloads to include SSDT, use the Visual Studio Installer.

Launch the Visual Studio Installer. In the Windows Start menu, you can search for 'installer'.
In the installer, select for the edition of Visual Studio that you want to add SSDT to, and then choose Modify.
Select SQL Server Data Tools under Data storage and processing in the list of workloads.

For Analysis Services, Integration Services, or Reporting Services projects, you can install the appropriate extensions from within Visual Studio with Extensions > Manage Extensions or from the Marketplace.
SSDT for Visual Studio 2017
Changes in SSDT for Visual Studio 2017
Sql Server Data Tools For Mac
Starting with Visual Studio 2017, the functionality of creating Database Projects has been integrated into the Visual Studio installation. There's no need to install the SSDT standalone installer for the core SSDT experience.
Now to create Analysis Services, Integration Services, or Reporting Services projects, you still need the SSDT standalone installer.
Install SSDT with Visual Studio 2017
To install SSDT during Visual Studio installation, select the Data storage and processing workload, and then select SQL Server Data Tools.
Sql Management Studio For Mac
If Visual Studio is already installed, use the Visual Studio Installer to modify the installed workloads to include SSDT.
Launch the Visual Studio Installer. In the Windows Start menu, you can search for 'installer'.
In the installer, select for the edition of Visual Studio that you want to add SSDT to, and then choose Modify.
Select SQL Server Data Tools under Data storage and processing in the list of workloads.
Install Analysis Services, Integration Services, and Reporting Services tools
To install Analysis Services, Integration Services, and Reporting Services project support, run the SSDT standalone installer.
The installer lists available Visual Studio instances to add SSDT tools. If Visual Studio isn't already installed, selecting Install a new SQL Server Data Tools instance installs SSDT with a minimal version of Visual Studio, but for the best experience, we recommend using SSDT with the latest version of Visual Studio.
SSDT for VS 2017 (standalone installer)
Important
Before installing SSDT for Visual Studio 2017 (15.9.6), uninstall Analysis Services Projects and Reporting Services Projects extensions if they are already installed, and close all VS instances.
Removed the inbox component Power Query Source for SQL Server 2017. Now we have announced Power Query Source for SQL Server 2017 & 2019 as out-of-box component, which can be downloaded here.
To design packages using Oracle and Teradata connectors and targeting an earlier version of SQL Server prior to SQL 2019, in addition to the Microsoft Oracle Connector for SQL 2019 and Microsoft Teradata Connector for SQL 2019, you need to also install the corresponding version of Microsoft Connector for Oracle and Teradata by Attunity.
Release Notes
For a complete list of changes, see Release notes for SQL Server Data Tools (SSDT).
System requirements
Microsoft Sql Tools For Mac
SSDT for Visual Studio 2017 has the same system requirements as Visual Studio.
Available Languages - SSDT for VS 2017
Sql Server Tools For Mac
This release of SSDT for VS 2017 can be installed in the following languages:
Considerations and limitations
You can’t install the community version offline
To upgrade SSDT, you need to follow the same path used to install SSDT. For example, if you added SSDT using the VSIX extensions, then you must upgrade via the VSIX extensions. If you installed SSDT via a separate install, then you need to upgrade using that method.
Offline install
To install SSDT when you’re not connected to the internet, follow the steps in this section. For more information, see Create a network installation of Visual Studio 2017.
First, complete the following steps while online:
Download the SSDT standalone installer.
Download vs_sql.exe.
While still online, execute one of the following commands to download all the files required for installing offline. Using the --layout option is the key, it downloads the actual files for the offline installation. Replace <filepath> with the actual layouts path to save the files.
For a specific language, pass the locale: vs_sql.exe --layout c:<filepath> --lang en-us (a single language is ~1 GB).
For all languages, omit the --lang argument: vs_sql.exe --layout c:<filepath> (all languages are ~3.9 GB).
After completing the previous steps, the following steps below can be done offline:
Run vs_setup.exe --NoWeb to install the VS2017 Shell and SQL Server Data Project.
From the layouts folder, run SSDT-Setup-ENU.exe /install and select SSIS/SSRS/SSAS.a. For an unattended installation, run SSDT-Setup-ENU.exe /INSTALLALL[:vsinstances] /passive.
For available options, run SSDT-Setup-ENU.exe /help
Note
If using a full version of Visual Studio 2017, create an offline folder for SSDT only, and run SSDT-Setup-ENU.exe from this newly created folder (don’t add SSDT to another Visual Studio 2017 offline layout). If you add the SSDT layout to an existing Visual Studio offline layout, the necessary runtime (.exe) components are not created there.
Supported SQL versions
Project TemplatesSQL Platforms SupportedRelational databasesSQL Server 2005* - SQL Server 2017 (use SSDT 17.x or SSDT for Visual Studio 2017 to connect to SQL Server on Linux) Azure SQL Database Azure Synapse Analytics (supports queries only; database projects aren't yet supported) * SQL Server 2005 support is deprecated, move to an officially supported SQL versionAnalysis Services models Reporting Services reportsSQL Server 2008 - SQL Server 2017Integration Services packagesSQL Server 2012 - SQL Server 2019
DacFx
SSDT for Visual Studio 2015 and 2017 both use DacFx 17.4.1: Download Data-Tier Application Framework (DacFx) 17.4.1.
Previous versions
Unix Tools For Mac
To download and install SSDT for Visual Studio 2015, or an older version of SSDT, see Previous releases of SQL Server Data Tools (SSDT and SSDT-BI).
See Also
Next steps
After installing SSDT, work through these tutorials to learn how to create databases, packages, data models, and reports using SSDT.
Get help

1 note
·
View note
Text
Red Hat RHCSA & RHCE Training
What is Linux ? Linux® is an open source operating system (OS). It was originally conceived and created as a hobby by Linus Torvalds in 1991. Linus, while at the university, sought to create another OS, an open source OS, based on the principles and design of Unix. Those hobbies have since become the OS with the largest user experience, the most widely used OS on publicly available Internet servers, and the only OS used on 500 fastest supercomputers. Perhaps the best thing about Linux is that it is open source. Linux is licensed under the GNU General Public License (GPL). That means anyone can use, read, share and modify software. The modified code can also be distributed, and sold, but must be done so under the same license. This is in stark contrast to traditional operating systems - Unix and Windows, for example - which are proprietary, closed, and postal and are not subject to change. The descriptive part of Linux is the Linux kernel, an application kernel developed by Linus Torvalds. Linux is often integrated into Linux distribution (or distro for short). Distribution includes system software and libraries, many of which are provided by the GNU Project. Linux continues to be the application of the future, with many more programs depending on its stability and expansion.
-------------------------------------------------------------------------------------------- What is Red Hat and Red Hat Enterprise Linux (RHEL) ? Red Hat, Inc. is an American multinational software company that provides open source software products to businesses. Founded in 1993, Red Hat has its company headquarters in Raleigh, North Carolina, and other offices around the world. It became a company owned by IBM on July 9, 2019. Red Hat first saw success supporting custom distribution for Linux, then called "Red Hat® Linux." The growth and reliability of Red Hat Linux made these two aspects the same in the minds of many people. Since those early days, Red Hat solutions and technologies have built on this success to include almost every aspect of the IT stack. Red Hat curates, protects, and supports the distribution of Linux — now known as Red Hat Enterprise Linux, a change that took place in 2003 as a result of the merger with Fedora Linux Project. Today, Red Hat Enterprise Linux supports and enables software and technology for automation, cloud, containers, middleware, storage, application development, microservices, virtualization, management, and more. Linux plays a major role as the context of many Red Hat offerings. It is much more than just server applications - Linux is the foundation of today's IT stack. ------------------------------------------------------------------------------------------------ Career Oppourtunities in RHEL/Linux : Mentioned are top 15 jobs for you which you can expect after you come out with RHEL/Linux expertise: DevOps Engineer (preferred career) Java Developer Software Engineer Systems Administrator (preferred career) Systems Engineer (preferred career) Senior Software Engineer Python Developer Network Engineer (preferred career) Software Developer Linux Engineering Admin (preferred career) Software Developer Linux Engineer (preferred career) TechOps Engineer (preferred career) Senior Java Developer Build release management Engineer (preferred career)
We at Webosapiens.com help you build your career in the “preferred career“ mentioned above. Visit us at http://www.webosapiens.com/. ------------------------------------------------------------------------------------------------ What is RHCSA ? An IT specialist who has acquired the Red Hat Certified System Administrator (RHCSA®) is able to perform the system control skills required in Red Hat Enterprise Linux. Proof is obtained after passing the Red Hat Certified System Administrator (RHCSA) Exam (EX200). The Red Hat® Certified System Administrator (RHCSA) is able to perform the following functions: >>Understand and use essential tools for managing files, directories, command line locations, and documents >>Use operating systems, including starting with different levels of running, identifying processes, starting and setting up virtual machines, and managing services >>Customize local storage using partitions and logical volumes >>Create and configure file systems and file system icons, such as permissions, encryption, access control lists, and network file systems >>Use, modify, and maintain systems, including software installation, upgrades, and core services >>Manage users and groups, including the use of an integrated verification list >>Manage security, including basic firewall and SELinux configuration
--------------------------------------------------------------------------------------------------- What is RHCE ? Red Hat® Certified Engineer (RHCE®) is a Red Hat Certified System Administrator (RHCSA) ready to perform the functions of Red Hat® Enterprise Linux®, integrate Red Hat emerging technologies, and use automation to operate efficiently and innovate. A so-called "flagship" certificate, the RHCE is a medium to high-level certificate based on topics linked to the RHCSA certificate to include more advanced topics such as security and integration of common communication services (IP).
--------------------------------------------------------------------------------------------------- Roadmap for RHSCA and RHCE: For RHCSA - Book 124 and Book 134 For RHCE - RHCSA certificate or equivalent konwledge or Book 124, 134 and 294 Book 124 :- 17 chapters Book 134 :- 13 chapters Book 294 :- 11 chapters
Trainings for RHCSA & RHCE is Offered by http://www.webosapiens.com/
1 note
·
View note
Text
SAMBA versus SMB: Adversarial interoperability is judo for network effects
Before there was Big Tech, there was "adversarial interoperability": when someone decides to compete with a dominant company by creating a product or service that "interoperates" (works with) its offerings.
In tech, "network effects" can be a powerful force to maintain market dominance: if everyone is using Facebook, then your Facebook replacement doesn't just have to be better than Facebook, it has to be so much better than Facebook that it's worth using, even though all the people you want to talk to are still on Facebook. That's a tall order.
Adversarial interoperability is judo for network effects, using incumbents' dominance against them. To see how that works, let's look at a historical example of adversarial interoperability role in helping to unseat a monopolist's dominance.
The first skirmishes of the PC wars were fought with incompatible file formats and even data-storage formats: Apple users couldn't open files made by Microsoft users, and vice-versa. Even when file formats were (more or less) harmonized, there was still the problems of storage media: the SCSI drive you plugged into your Mac needed a special add-on and flaky driver software to work on your Windows machine; the ZIP cartridge you formatted for your PC wouldn't play nice with Macs.
But as office networking spread, the battle moved to a new front: networking compatibility. AppleTalk, Apple's proprietary protocol for connecting up Macs and networked devices like printers, pretty much Just Worked, providing you were using a Mac. If you were using a Windows PC, you had to install special, buggy, unreliable software.
And for Apple users hoping to fit in at Windows shops, the problems were even worse: Windows machines used the SMB protocol for file-sharing and printers, and Microsoft's support for MacOS was patchy at best, nonexistent at worst, and costly besides. Businesses sorted themselves into Mac-only and PC-only silos, and if a Mac shop needed a PC (for the accounting software, say), it was often cheaper and easier just to get the accountant their own printer and backup tape-drive, rather than try to get that PC to talk to the network. Likewise, all PC-shops with a single graphic designer on a Mac—that person would often live offline, disconnected from the office network, tethered to their own printer, with their own stack of Mac-formatted ZIP cartridges or CD-ROMs.
All that started to change in 1993: that was the year that an Australian PhD candidate named Andrew Tridgell licensed his SAMBA package as free/open source software and exposed it to the wide community of developers looking to connect their non-Microsoft computers—Unix and GNU/Linux servers, MacOS workstations—to the dominant Microsoft LANs.
SAMBA was created by using a "packet sniffer" to ingest raw SMB packets as they traversed a local network; these intercepted packets gave Tridgell the insight he needed to reverse-engineer Microsoft's proprietary networking protocol. Tridgell prioritized compatibility with LAN Manager, a proprietary Network Operating System that enterprise networks made heavy use of. If SAMBA could be made to work in LAN Manager networks, then you could connect a Mac to a PC network—or vice-versa—and add some Unix servers and use a mix of SAMBA and SMB to get them all to play nice with one another.
The timing of Tridgell's invention was crucial: in 1993, Microsoft had just weathered the Federal Trade Commission’s antitrust investigation of its monopoly tactics, squeaking through thanks to a 2-2 deadlock among the commissioners, and was facing down a monopoly investigation by the Department of Justice.
The growth of local-area networks greatly accelerated Microsoft's dominance. It's one thing to dominate the desktop, another entirely to leverage that dominance so that no one else can make an operating system that connects to networks that include computers running that dominant system. Network administrators of the day were ready to throw in the towel and go all-Microsoft for everything from design workstations to servers.
SAMBA changed all that. What's more, as Microsoft updated SMB, SAMBA matched them, relying on a growing cadre of software authors who relied on SAMBA to keep their own networks running.
The emergence of SAMBA in the period when Microsoft's dominance was at its peak, the same year that the US government tried and failed to address that dominance, was one of the most salutary bits of timing in computing history, carving out a new niche for Microsoft's operating system rivals that gave them space to breathe and grow. It's certainly possible that without SAMBA, Microsoft could have leveraged its operating system, LAN and application dominance to crush all rivals.
So What Happened?
We don't see a lot of SAMBA-style stories anymore, despite increased concentration of various sectors of the tech market and a world crying out for adversarial interoperability judo throws.
Indeed, investors seem to have lost their appetite for funding companies that might disrupt the spectacularly profitable Internet monopolists of 2019, ceding them those margins and deeming their territory to be a "kill zone."
VCs have not lost their appetite for making money, and toolsmiths have not lost the urge to puncture the supposedly airtight bubbles around the Big Tech incumbents, so why is it so hard to find a modern David with the stomach to face off against 2019's Goliaths?
To find the answer, look to the law. As monopolists have conquered more and more of the digital realm, they have invested some of those supernormal profits in law and policy that lets them fend off adversarial interoperators.
One legal weapon is "Terms of Service": both Facebook and Blizzard have secured judgments giving their fine print the force of law, and now tech giants use clickthrough agreements that amount to, "By clicking here, you promise that you won't try to adversarially interoperate with us."
A modern SAMBA project would have to contend with this liability, and Microsoft would argue that anyone who took the step of installing SMB had already agreed that they wouldn't try to reverse-engineer it to make a compatible product.
Then there's "anti-circumvention," a feature of 1998's Digital Millennium Copyright Act (DMCA). Under Section 1201 of the DMCA, bypassing a "copyright access control" can put you in both criminal and civil jeopardy, regardless of whether there's any copyright infringement. DMCA 1201 was originally used to stop companies from making region-free DVD players or modding game consoles to play unofficial games (neither of which is a copyright violation!).
But today, DMCA 1201 is used to control competitors, critics, and customers. Any device with software in it contains a "copyrighted work," so manufacturers need only set up an "access control" and they can exert legal control over all kinds of uses of the product.
Their customers can only use the product in ways that don't involve bypassing the "access control," and that can be used to force you to buy only one brand of ink or use apps from only one app store.
Their critics—security researchers auditing their cybersecurity—can't publish proof-of-concept to back up their claims about vulnerabilities in the systems.
And competitors can't bypass access controls to make compatible products: third party app stores, compatible inks, or a feature-for-feature duplicate of a dominant company's networking protocol.
Someone attempting to replicate the SAMBA creation feat in 2019 would likely come up against an access control that needed to be bypassed in order to peer inside the protocol's encrypted outer layer in order to create a feature-compatible tool to use in competing products.
Another thing that's changed (for the worse) since 1993 is the proliferation of software patents. Software patenting went into high gear around 1994 and consistently gained speed until 2014, when Alice v. CLS Bank put the brakes on (today, Alice is under threat). After decades of low-quality patents issuing from the US Patent and Trademark Office, there are so many trivial, obvious and overlapping software patents in play that anyone trying to make a SAMBA-like product would run a real risk of being threatened with expensive litigation for patent infringement.
This thicket of legal anti-adversarial-interoperability dangers has been a driver of market concentration, and the beneficiaries of market concentration have also spent lavishly to expand and strengthen the thicket. It's gotten so bad that even some "open standards organizations" have standardized easy-to-use ways of legally prohibiting adversarial interoperability, locking in the dominance of the largest browser vendors.
The idea that wildly profitable businesses would be viewed as unassailable threats by investors and entrepreneurs (rather than as irresistible targets) tells you everything you need to know about the state of competition today. As we look to cut the Big Tech giants down to size, let's not forget that tech once thronged with Davids eager to do battle with Goliaths, and that this throng would be ours to command again, if only we would re-arm it.
(Crossposted from EFF Deeplinks)
https://boingboing.net/2019/07/18/kill-zones-r-us.html
30 notes
·
View notes
Link
Cybersecurity Fundamentals – Introduction to Cybersecurity
Adoption of Internet by businesses and enterprises has made mobile-banking, online shopping, and social networking possible. Whilst it has opened up a lot of opportunities for us, its not altogether a safe place because its anonymity also harbors cyber-criminals. So, to protect yourself against the cyber threats of today, you must have a solid understanding of cybersecurity. This article will help you get a grip on cybersecurity fundamentals.Let’s take a look at the topics covered in this cybersecurity fundamentals article:
The history of Cybersecurity
What is Cybersecurity?
Why is cybersecurity important?
The CIA Triad
The history of Cybersecurity About forty years ago words like worms, viruses, Trojan-horse, spyware, malware weren’t even a part of conventional information technology (IT) vocabulary. Cybersecurity only came into existence because of the development of viruses. But how did we get here?The history of cybersecurity began as a research project. In the 1970’s, Robert Thomas, a researcher for BBN Technologies in Cambridge, Massachusetts, created the first computer “worm”. It was called The Creeper. The Creeper, infected computers by hopping from system to system with the message “I’M THE CREEPER: CATCH ME IF YOU CAN.” Ray Tomlinson, the inventor of email, created a replicating program called The Reaper, the first antivirus software, which would chase Creeper and delete it.Late in 1988, a man named Robert Morris had an idea: he wanted to test the size of the internet. To do this, he wrote a program that went through networks, invaded Unix terminals, and copied itself. The Morris worm was so aggressive that it slowed down computers to the point of being unusable. He subsequently became the first person to be convicted under Computer Fraud and Abuse Act.From that point forward, viruses became deadlier, more invasive, and harder to control. With it came the advent of cybersecurity.What is cybersecurity?Cybersecurity is the body of technologies, processes, and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access.
The term cybersecurity refers to techniques and practices designed to protect digital data. The data that is stored, transmitted or used on an information system. After all, that is what criminal wants, data. The network, servers, computers are just mechanisms to get to the data. Effective cybersecurity reduces the risk of cyber-attacks and protects organizations and individuals from the unauthorized exploitation of systems, networks, and technologies.Robust cybersecurity implementation is roughly based around three key terms: people, processes, and technology. This three-pronged approach helps organizations defend themselves from both highly organized attacks and common internal threats, such as accidental breaches and human error.The attacks evolve every day as attackers become more inventive, it is critical to properly define cybersecurity and understand cybersecurity fundamentals.Why is cybersecurity important?Listed below are the reasons why cybersecurity is so important in what’s become a predominant digital world:
With each passing year, the sheer volume of threats is increasing rapidly. According to the report by McAfee, cybercrime now stands at over $400 billion, while it was $250 billion two years ago.
Cyber attacks can be extremely expensive for businesses to endure. In addition to financial damage suffered by the business, a data breach can also inflict untold reputational damage.
Cyber-attacks these days are becoming progressively destructive. Cybercriminals are using more sophisticated ways to initiate cyber attacks.
Regulations such as GDPR are forcing organizations into taking better care of the personal data they hold.
Because of the above reasons, cybersecurity has become an important part of the business and the focus now is on developing appropriate response plans that minimize the damage in the event of a cyber attack. But, an organization or an individual can develop a proper response plan only when he has a good grip on cybersecurity fundamentals.Now that we know what cybersecurity is and why it is important, let’s take a look at fundamental objectives of cybersecurity.The CIA Triad Confidentiality, integrity, and availability, also known as the CIA triad, is a model designed to guide companies and organizations to form their security policies. Technically, cybersecurity means protecting information from unauthorized access, unauthorized modification, and unauthorized deletion in order to provide confidentiality, integrity, and availability.Let’s explore these components and some of the information security measures which are designed to assure the safety of each component.Cybersecurity Fundamentals – Confidentiality Confidentiality is about preventing the disclosure of data to unauthorized parties. It also means trying to keep the identity of authorized parties involved in sharing and holding data private and anonymous. Often confidentiality is compromised by cracking poorly encrypted data, Man-in-the-middle(MITM) attacks, disclosing sensitive data.Standard measures to establish confidentiality include:
Data encryption
Two-factor authentication
Biometric verification
Security tokens
Integrity refers to protecting information from being modified by unauthorized parties. It is a requirement that information and programs are changed only in a specified and authorized manner. Challenges that could endanger integrity include turning a machine into a “zombie computer”, embedding malware into web pages.Standard measures to guarantee integrity include:
Cryptographic checksum
Using file permissions
Uninterrupted power supplies
Data backups
Availability is making sure that authorized parties are able to access the information when needed. Data only has value if the right people can access it at the right time. Information unavailability can occur due to security incidents such as DDoS attacks, hardware failures, programming errors, human errors.Standard measures to guarantee availability include:
Backing up data to external drives
Implementing firewalls
Having backup power supplies
Data redundancy
All cyber attacks have the potential to threaten one or more of the three parts of the CIA triad. Confidentiality, integrity, and availability all have to work together to keep your information secure. So, It’s important to understand what the CIA Triad is, how it is used to plan and implement a quality security policy while understanding the various principles behind it.How much does cybersecurity jobs pay?With the widely reported success of massive global cyber-attacks, like WannaCry and Adylkuzz, companies are paying more than ever to land highly qualified cybersecurity professionals to secure their most vulnerable assets. The average salary range for top cybersecurity job roles falls between $100,000 to $210,000.This brings us to the end of this article and Cybersecurity Fundamentals. I hope you all had something new to learn.
Got a question for us? Please mention it in the comments section of “Cybersecurity Fundamentals” and we will get back to you.
1 note
·
View note
Text
Cut videos with free freeware ▷ TOP 5 Editor Tools
The video editing functions and interface are out of date and cannot keep up with those of the other free video editors in this article, but offer everything you need to edit your videos. The open source project is updated regularly and enriched with more functions. If you didn't like an older version, it may be worth taking another look at Avidemux.
Leave a comment Cancel reply
OpenShot supports all common video, picture and audio formats. Even if the editing software is quite easy to use, you should bring some time to set it up. the animation program Blender as a plugin for animated text effects. If you're not familiar with such technical downvids facebook details , you should use one of the other programs listed here. Recording videos has never been easier - which is both a curse and a blessing, because many Mac users store numerous unprocessed video treasures on their hard drives. Is a customized Firefox (Aurora) browser and offers an easy way to surf the Internet anonymously via the TOR network (The Onion Routing). Professional video editing program for Linux. Many functions such as picture-in-picture, working with blue screens, and much more. An easy-to-use video editor that includes many effect filters. For a long time, Avidemux was reserved exclusively for Linux users - but now the editing software is also available for the other major platforms. The open source tool comes with a huge selection of tools to help you cut, edit and beautify videos and film projects. Since it combines code from many different open source sources, the software supports countless file formats in import and export and can deal with many different codecs by default. Grown quite "patchwork" -like over many years from different code sources, the program has a large range of different and also powerful features.
FILMORA Video Editor
In addition, the application has a tidy and modern user interface, so that the training period is limited.
Photo editor, which can be used to easily create panoramic images, even if the images are not were seamlessly recorded in a row next to each other.
Even if the editing software is quite easy to use, you should bring some time for the setup.
In the event that iMovie Too limited, you can use the Final Cut Pro X, also published by Apple, which offers a significantly larger and more professional range of functions.
Using our powerful framework, you can hide, move, jump, and animate whatever you want in your video. Quickly crop your videos and find all those perfect moments. OpenShot has many easy ways to cut your video. Is an easy-to-use open source video editor as well as a live VJ tool for video performance, and understands a wide variety of video formats. Even if you're not a professional filmmaker, the technologies are so advanced that editing has become an easy task. It's easy to say once you've found good video editing software. BlenderLinux, Mac, WindowsBlender is available as freeware. The software specializes in animation and 3D modeling. Almost everyone can implement their ideas - even if only with their smartphone - and make film creations accessible to the public. It is hardly surprising that corresponding software has also become a whole lot more user-friendly - and that starts with the (sometimes non-existent) price. It is generally believed that the strongest point of this Movavi alternative is open source code. In other words, you can manually customize various tools, correct bugs, and create new features without waiting for the next update. The VideoPad Video Editor from NCH Software proves that you don't have to do without modern functions such as 4k and 360 ° video editing with free editing programs. The Video Editor for Mac doesn't cost you a single cent for non-commercial use. The editing program designed for beginners supports all common video formats and offers all the basic functions you need for editing and editing your videos. The greatest strength of the VideoPad Video Editor is the easy-to-understand operation, thanks to which you can quickly get to grips with the program even without video editing knowledge. In general, it has everything you can expect from the best graphics editor. As for the disadvantages, Pixlr does not offer batch processing of images. However, you can open several pictures at the same time and change them one after the other. In addition, it has several interesting color filters, transitions and theme stickers. Up to five tracks are available for editing your films. The soundtracks support surround sound from seven channels. Kdenlive is only available for Unix-based systems such as Linux - but it is one of the absolute high rollers here. Completely open source and free of charge, as well as a washable NLE (non-linear editor), the operation of the software is not quite as polished as with commercial alternatives, but it has a large arsenal of features.
1 note
·
View note
Text
Nucigent Provides Cost-effective Software Development and Implementation of Services
Nucigent is focusing exclusively in high quality and cost-effective software development and implementation of services. We are advancing on a tremendous pace and with involvement of skilled and experienced people working in the organization. NUCIGENT is currently doing business in Retail, Hospital, MNCs, Large Corporate, and in the Hotel Sector.
CONSULTANCY
We consult for high-end technology implementation at clients’ site or implementation of new technology according to the clients’ requirement or upgrading, enhancing the existing facilities in the clients end with the new technology integrated with the existing one. Nucigent offers a full range of consulting services to help analyze your business requirements for effective implementation of solutions. Our consulting services cover:
Strategy planning
Assessment
Procurement
Re-engineering solutions
Planning, audits, best practices etc.
SOFTWARE DEVELOPMENT
With design and development expertise in diverse platforms, best-of-breed tools and techniques, combined with industry best practices, Nucigent offers scalable end-to-end application development and management solutions from requirement analysis for deployment and roll-out. We are developing Android Applications and software, related to Hotel, Medical, retail, accounting software for trading, manufacturing house and conglomerates. We hope to come to you with desired software at a reasonable cost.

Application Development
Providing end-to-end development from requirement analysis for deployment and rollout.
Application Management
The application management layer cuts across all software engineering activities listed above. Nucigent takes complete ownership of the outsourced suite of applications as per the agreed scope and manages the support. This typically involves transition management, project management, proactive risk and scope change management, quality management, SLA management etc.
ANDROID APP DEVELOPMENT SERVICE
Our android app development services include up-to date integrated seamless apps that are highly functional and combines irresistible features to suit your business.
Hybrid Android app Development
Hybrid android apps are developed using the standard web technologies like HTML5, CSS, JavaScript and React Native. The final code is wrapped in a native container and shipped as a regular app. Hybrid approach is often called “Write Once Run Anywhere” as the same code can serve multiple platforms along with Android.
Consulting Service
Our experts having years of experience will mentor and provide you consultation on nuances of Android app development.
Support & Maintenance
Apart from Android app development services we our team also provide 24×7 support & maintenance service to our clients.

AREAS OF EXPERTISE
Main Strength of Nucigent lies in the blend of professionals, specialized and highly focused operation. Increasing customer’s awareness is the strength where it excels over its competitors. Our strength lies in our ability to blend current management practice and IT expertise into cost-effective Computer Aided Management Solutions, Products and Services. Nucigent understands the need for skill transfer to client personnel. Our offers cover the following major areas:
System analysis
Business process reengineering
Process development localization
Customized and target oriented Workflow design
Specialization in Client / Server and Internet / Intranet application and technologies
Institutions with the latest development.
Customized software development as ancillary product for deployed international software
Network Monitoring/ Network Management Support
Network, Security & Threat Management Solution
Infrastructure Management Solution.
Data Centre Operations and Service Delivery.
Systems Integration.
Project Management.
Change/request implementation
Project support
Standby support
Web based support & solution development
SYSTEN ANALYSIS & DESIGN
System analysis and design team combines both functional and technical analysts. We believe to develop a proper system of which functional analysis is equally important as technical analysis. Our system analysis and design team specialize in the software like Microsoft Visio, Rational Rose and Microsoft Visual Modeler.
DATABASE MANAGEMENT
We have database expertise ranging from ISAM or flat database systems like Oracle and Microsoft SQL. For web-database connectivity and cross-platform data management we also have specialized experience and expertise in My SQL database server.

WEB DEVELOPMENT AND DESIGN
Our web developers and designers are skilled in development with Microsoft Front Page, Macromedia Fireworks and Dream Weaver for web site design.
PROGRAMMING
Our young and talented programmers have a wide range of experience in developing systems. Our programming skill involves:
PROGRAMMING LANGUAGES:
VB, Visual C++, Java, VB for Application (VBA) and Microsoft .Net Platform.
WEB PROGRAMMING LANGUAGES:
PHP, Active Server Pages (ASP)
SCRIPTING LANGUAGES:
Java Script, VB Scripts
MULTIMEDIA DEVELOPMENT:
Flash and Flash Script.
WEB SERVERS:
Microsoft IIS and Apache
OPERATING SYSTEMS:
Microsoft Platform and Linux/Unix
PRODUCT OFFERINGS
Retail Solutions
Stock & Accounting Management System (all retails, Jewelry, Petrol Pump, Pharmaceuticals etc.)
Medical Automation
Bidding Process
Purchase Order Management
B2B Order Management
HR Systems
Enterprise Market
Enterprise Resource Planning (ERP)
Order Management System
Mobility Solution
NUCIGENT’s Managed Services offerings cover the entire array of IT outsourcing services including networks, IT infrastructure, applications and business processes. This provides our customers both control and flexibility over their information systems without either the pain or cost.
Blog Source: https://nucigent.blogspot.com/2020/01/nucigent-provides-cost-effective-Software-Development-and-Implementation-of-Services.html
#Software development#Software development Company in Bhubaneswar#Software development company in Odisha#Web development services Bhubaneswar#app development platform in India#Hybrid android application development#app development software android#app development cost in India
1 note
·
View note
Photo

The Best Ways to Secure Your SSH Server Eny Setiyowati/Shutterstock.com Secure your Linux system’s SSH connection to protect your system and data. System administrators and home users alike need to harden and secure internet-facing computers, but SSH can be complicated. Here are ten easy quick-wins to help protect your SSH server. SSH Security Basics SSH stands for Secure Shell. The name “SSH” is used interchangeably to mean either the SSH protocol itself or the software tools that allow system administrators and users to make secure connections to remote computers using that protocol. The SSH protocol is an encrypted protocol designed to give a secure connection over an insecure network, such as the internet. SSH in Linux is built on a portable version of the OpenSSH project. It is implemented in a classic client-server model, with an SSH server accepting connections from SSH clients. The client is used to connect to the server and to display the session to the remote user. The server accepts the connection and executes the session. In its default configuration, an SSH server will listen for incoming connections on Transmission Control Protocol (TCP) port 22. Because this is a standardized, well-known port, it is a target for threat actors and malicious bots. Threat actors launch bots that scan a range of IP addresses looking for open ports. The ports are then probed to see if there are vulnerabilities that can be exploited. Thinking, “I’m safe, there are bigger and better targets than me for the bad guys to aim at,” is false reasoning. The bots aren’t selecting targets based on any merit; they’re methodically looking for systems they can breach. You nominate yourself as a victim if you haven’t secured your system. Security Friction Security friction is the irritation—of whatever degree—that users and others will experience when you implement security measures. We’ve got long memories and can remember introducing new users to a computer system, and hearing them ask in a horrified voice whether they really had to enter a password every time they logged in to the mainframe. That—to them—was security friction. (Incidentally, the invention of the password is credited to Fernando J. Corbató, another figure in the pantheon of computer scientists whose combined work contributed to the circumstances that led to the birth of Unix.) Introducing security measures usually involves some form of friction for someone. Business owners have to pay for it. The computer users may have to change their familiar practices, or remember another set of authentication details, or add extra steps to connect successfully. The system administrators will have additional work to do to implement and maintain the new security measures. Read the remaining 90 paragraphs https://buff.ly/31hLiI8
1 note
·
View note
Text
How exactly to Understand Your First Development Language
In today's office, Python training is an increasingly crucial part of a programmer's education. As a powerful language whose style philosophy revolves about readability and conciseness, Python is a well known selection for use as a scripting language. Like other interpretative languages, it's more flexible than gathered languages, and it can be used to tie disparate programs together. Certainly, Python is just a adaptable language with many programs in rising fields.
For instance, Python is a well known development language for academic software. Raspberry Pi, the single-board pc task for training students computer coding, uses Python as its principal coding language. In addition, a lot of the program for the One Laptop per Kid XO is prepared in Python. At one other conclusion of the academic variety, Python is also a very effective language for scientific research and mathematical application for theoretical mathematics. As educational computer software progress is growing, Python can become an even more and more essential language to know.
As well as instructional software, Python can also be a favored language for used in AI tasks. Because Python is really a scripting language with wealthy text running tools, element structure, and syntax simplicity, it is a natural choice for programs concerning organic language processing. Programs like Wolfram Leader and Siri are just beginning to enter the end-user industry and several such programs yet in the future is likely to be written in Python.
Python Basic Tutorial
Moreover, Python is frequently used as a scripting language for internet applications. For example, Google has used Python as among the accessible languages in their Bing Software Engine, a cloud processing system for establishing and hosting web applications. Python can be applied as a framework to plan communications between pcs for web programs like Dropbox. As internet application growth is just a fast-growing field, programmers would to properly to acquire some Python instruction to help keep their skills up-to-date.
Python can also be quite of good use as a modern scripting language just like Perl, which could applied to tie disparate methods together. Due to this, since Python is just a common element for a lot of Linux and Unix based systems, and because Python is used thoroughly in the information security market, Python is an essential tool for methods administrators to master, along with programmers.
Python education has become an increasingly important coding language. Because flexibility, Python includes a wide selection of uses in lots of growing fields. Equally programmers and programs administrators might do well to pick up some Python experienced to be able to keep their abilities up-to-date.
With the entire world stepping towards a new age of engineering growth, it is not difficult to imagine another which is high in screens. And if so function as situation then, demand for those who have powerful programming abilities will certainly rise with more number of people expected to produce and help the applications. Python Instruction is obviously a good idea for those needs to be an integral part of that constantly establishing industry. Python language is not merely simple to understand, but stresses less on syntax which explains why a couple of mistakes here and there does not give the maximum amount of difficulty as several other languages does.
What Makes Python a Chosen Selection Among Programmers?
Python happens to be an easy development language which provides its help to various program types starting from education to medical processing to web development. Technology leaders like Google along side Instagram have also built use of Python and its reputation remains to rise. Mentioned guidelines a number of the advantages made available from Python:
First Measures in the World of Programming
Aspiring programmers may use Python to enter the programming world. Like several other development languages such as for example Ruby, Perl, JavaScript, C#, C++, etc. Python can be object oriented centered development language. Those who have thorough understanding of Python can certainly adapt to other environments. It is obviously recommended to acquire working understanding so as to become alert to the methodologies which are used across various applications.
Simple and Simple to Realize and Signal
Many individuals may consent to the truth that, learning and understanding a coding language isn't that fascinating when compared with a tight football game. But, Python on another give was especially created remember newcomers. To even the attention of a layman, it will appear important and simple to understand. Fluorescent brackets and exhausting variable declarations aren't portion of this programming language hence, rendering it much easier to understand language.
Getting Progressive
Python has helped in taking real world and processing a great deal shut with it Strawberry Pi. That inexpensive, card-sized microcomputer assists tech fanatics to build various DIY stuffs like video gambling consoles, distant managed cars and robots. Python is the development language that powers that microcomputer. Aspirants can make from different DIY tasks available on the web and improve their abilities and motivations by completing such projects.
Python also Helps Internet Development
Using its big abilities, Python is also a well liked among internet designers to build numerous forms of internet applications. The net request structure, Django has been produced applying Python and provides as the foundation for common sites like'The Guardian ','The NY Situations ','Pinterest'and more.
Last Phrases
Python offers aspiring programmers a solid base centered where they can branch out to various fields. Python programming teaching guarantees that pupils can make use of this highly potential programming language to the most effective of their capabilities in an exciting and fun way. Those people who are willing to create a great career as computer software programmers are particular to find Python surpass their expectations.
1 note
·
View note
Text
Why The Language Of Python Is Used By Just About Everyone - Sofvare Solutions LLP

Python is not just a snake it is also a working programming language that was created by a Dutch programmer, Guido van Rossum in 1989. Released in 1991, it is one of the fastest-growing programming languages that has endured since its inception.
Here is a list of some of the many advantages of Python Programming:
Python’s large selection of pre-built libraries fits just about anyone’s needs. Scientific computing, image and data processing, machine learning, and deep learning.
Python’s code is simple to use due to its clean syntax and allows for the creation of quick prototypes.
The ROI of commercial projects is accelerated because Python code can be written and shipped faster.
A built-in framework allows unit tests that help to ship bug-free code.
Let’s look at some companies that use Python and how it works in the real world of business.
Industrial Light and Magic
Founded in 1975 by George Lucas to create FX for his Star Wars saga winning many awards for ILM’s work in the film industry.
Early on ILM worked mostly on practical effects but began to see that the future of FX was computer-generated images (CGI).
ILM first worked with the Unix shell which could only handle small quantities of work.
Thus began the search for a program that could handle the workload for their future projects.
Python 1.4 was chosen over Perl and Tcl because it was faster to integrate into their infrastructure.
ILM found it simple to import Python into their lighting software due to its easy interoperability with C and C++.
Spotify
A huge proponent of Python is Spotify the music streaming giant, which is using the programming language for data analysis and back-end services.
Spotify liked the speed of the development pipeline when coding and writing in Python.
Spotify has made recent upgrades to its architecture using Gevent providing a fast event loop with high-level synchronous API.
Dropbox
Dropbox uses Python in its desktop client for its cloud-based storage.
Dropbox was serious about acquiring Python as the company convinced Python creator Guido van Rossum to leave Google and join Dropbox.
Van Rossum came aboard as an engineer by agreement, not as a manager.
Van Rossum, in his first year, brought the ability to share datastores with other users inside the Dropbox community.
Dropbox has very efficient APIs coded in Python which allows one to see just how their engineers think.
There are over 500 current programming languages and more are coming every day.
Many are not designed to be used outside a lab or theoretical setting.
Which programming languages one uses for everyday coding, is a choice one has to make.
Python has made its mark in the world of coding and by choosing it one cannot go wrong.
A Good Choice For Big Data Projects
Python is known for its ease of use and that it makes code that works with the least number of lines.
No limitations to data processing, data can be computed in commodity machines, laptops, desktops, cloud, virtually everywhere.
Python’s compatibility makes it a good choice to use it with
Hadoop the most popular open-source big data platform.
Python’s interface to Hadoop is Pydoop and it allows a programmer to write MapReduce API for complex problem solving with little programming effort.
Python is an easy programming language to learn even if you are not a programmer for three reasons:
Ample learning resources.
Readable code.
A large community that is always there to help other programmers with any issues.
Data scientists can easily find someone in most departments who have a working knowledge of Python.
With Python’s popularity as a programming language choosing Python is a win-win for data scientists and businesses. It is perfect for web development, the Internet of Things, machine learning, startups, healthcare, and many others. Do you want to find out how Python can do wonders for your project? Contact us for a free consultation.
#python app development services#python app development company#python web development services#python web development#python game development#python mobile app development#django web development
0 notes
Text
Basics of Android App Development
Describe Android. The Android mobile operating system was created by a number of companies, primarily Google and the Open Handset Alliance. The operating system is written in a number of languages, including Java (UI), C (Core), and C++. The first commercial Android device was introduced in September 2008 after its announcement in November 2007.
The Linux Kernel has been updated to create Android OS, which is a member of the Unix-like OS family. It is primarily made for touchscreen mobile devices like smartphones and tablets. Since 2011, Android has sold the most smartphones worldwide, and since 2013, Android has sold the most tablets. Over 5 billion people utilise the operating system each month as of right now.
When developers or app development aficionados completely understand the underlying principles of app development, creating Android apps becomes simple. The fundamentals include the elements of app creation, the necessary language skills, the optimum app layout, and the whole lifecycle of an Android application.
To help people navigate the rapidly expanding globe, Wama Technology offers a variety of courses. They also have fair prices for the courses. One of India’s top businesses, Wama Technology provides the top computer programming courses to help you find employment in 2022.
They even offer some free coding training to the less fortunate. Through skill-based education, Wama Technology aims to close the knowledge gap between the learned and the uneducated.
There is a team of knowledgeable trainers at Wama Technology. Due to the close organisational project, all of the instructors give their all to teaching the students in a more straightforward manner and emphasising real-world tasks. There is a software lab with all the necessary tools where students can complete any practicals.
Android Programming Languages: Basics of Essential Android App Development
Java or C++ and XML are the two languages used to programme Android (Extension Markup Language). KOTLIN is also preferred today. As a front-end, the XML file handles design, presentation, layouts, blueprints, etc., whereas the JAVA or KOTLIN file handles button functionality, variables, storage, etc (as a back-end).
Components for Android
The foundation of Android are the App Components. Each component has a certain function and life cycle, or the period from the start of an app to its conclusion. Some of these elements also rely on other elements. Each element serves a distinct function.
The four main parts of the app are:
1. Exercises
2. Providers
3. Receivers for broadcasts:
4. A content creator
The UI and user interactions on the screen are covered. In other words, it is an activity-containing User Interface. Depending on the app, there may be one or more of these. When the application is opened, it begins. There is always at least one action. The following steps are taken to carry out the activity.
Radio and TV receivers
A broadcast replies to messages sent by the system or by other programmes. For instance, when the phone’s battery is low, the Android operating system broadcasts a message to start the Battery Saver function or app. When the programme receives the message, it does the necessary action.
Each object is represented by an intent object in the Broadcast Receiver subclass of the BroadcastReceiver class.
Content Creator
When another application requests it, a content provider is utilised to send data from one application to the others. These are handled by the ContentResolver class. The APIs (application programming interfaces) that this class implements allow other programmes to carry out transactions. The Parent Class of the ContentProvider class must be implemented by all Content Providers.
Services are the tasks the software completes in the background. These may be ongoing processes, such as a user listening to music while browsing the internet. A service may require additional sub-services to carry out particular functions. The main goal of the Services is to keep the app running continuously without interfering with any user interactions.
Layout Structure of Android Studio Android Studio’s default hierarchical Layout depicts the various app structures. It includes the authorization that an application would require to carry out a particular task. The root of the project source set is the XML file known as Android Manifest. The key details regarding the app, the Android development tools, the Android operating system, and Google Play are covered.
The Hardware and Software aspects of a mobile app are also included in the development process because they affect the app’s compliance with the Play Store. It also covers unique activities such as packages, services, broadcast receivers, and content suppliers.
Jar Files
The Java files needed to run the app’s background task can be found in the JAVA subdirectory. It has programming functions, computation, storage, variables, toast (a brief pop-up message), and button functionality. The quantity of these files varies according to the nature of the generated actions.
Material Folder
The many resources that are used in the programme are contained in the res or Resource folder. Subfolders in this include drawable, Layout, mipmap, raw, and values. The drawable is made from of pictures. The XML files that provide the user interface layout make up the Layout.
These are kept in res. Layout and accessed using the class name R.layout. Resources files like audio or music files make up the raw. These can be reached using R.raw.filename. Hardcoded strings (which are thought to be safe to store string values), integers, and colours are all stored in values.
Also read : Mobile App Development Company
0 notes
Text
Uncoverit app for osx 10.9.5

#Uncoverit app for osx 10.9.5 mac os x
#Uncoverit app for osx 10.9.5 720p
#Uncoverit app for osx 10.9.5 1080p
#Uncoverit app for osx 10.9.5 Pc
Songs from the Apple Music catalog cannot be burned to a CD. Use the Magic Keyboard for iPad with trackpad support for an extra level of speed and precision when editing. Create effects like green screen, pictureinpicture, or split screen and play them back instantly. macOS Server added server functionality and system administration tools to macOS and provided tools to manage both macOS-based computers and iOS-based devices. iMovie delivers a tour de force on iPad Pro.
#Uncoverit app for osx 10.9.5 mac os x
iTunes-compatible CD or DVD recorder to create audio CDs, MP3 CDs, or backup CDs or DVDs. macOS Server, formerly Mac OS X Server and OS X Server, is a discontinued series of Unix-like server operating systems developed by Apple Inc., based on macOS and later add-on software packages for the latter.
Internet connection to use Apple Music, the iTunes Store, and iTunes Extras.
Screen resolution of 1024x768 or greater 1280x800 or greater is required to play an iTunes LP or iTunes Extras.
#Uncoverit app for osx 10.9.5 1080p
To play 1080p HD video, a 2.4GHz Intel Core 2 Duo or faster processor, 2GB of RAM, and an Intel GMA X4500HD, ATI Radeon HD 2400, or NVIDIA GeForce 8300 GS or better is required.
#Uncoverit app for osx 10.9.5 720p
To play 720p HD video, an iTunes LP, or iTunes Extras, a 2.0GHz Intel Core 2 Duo or faster processor, 1GB of RAM, and an Intel GMA X3000, ATI Radeon X1300, or NVIDIA GeForce 6150 or better is required.
To play standard-definition video from the iTunes Store, an Intel Pentium D or faster processor, 512MB of RAM, and a DirectX 9.0–compatible video card is required.
#Uncoverit app for osx 10.9.5 Pc
PC with a 1GHz Intel or AMD processor with support for SSE2 and 512MB of RAM.
You are using Breath Ball at your sole responsibility. In case of discomfort, respiration issues or if you experience anything unfavorable, stop the breathing exercise immediately and seek the advice of a physician or therapist. For therapeutic treatment, please consult a medical professional. Please note that Breath Ball is solely used for relaxation and that it is not a medical device according to MDR. In case of questions or suggestions feel free to drop us an email at for reading. If you decide to use this app, you do so absolutely anonymous.īreath Ball is a philanthropic project and you are more than welcome to use it. There is no Facebook integration and there are no social sharing features. Please note: Breath Ball value your privacy. Beside that you can create your own breathing exercises something yoga and meditation coaches enjoy a lot.
The COPD foundation’s recommended breathing technique can help to catch a breath.Įach of these breathing exercises comes with a short tutorial that will get you started in less than two minutes.
Andrew Weil’s 4:7:8 breathing technique is used to fall asleep. Loew's slow paced breathing technique is used to calm down and overcome high stress situations.
The cardiac coherence breathing exercise is used to enter a meditative trance for deep relaxation.
These are the reasons why leading professionals from biofeedback coaches to meditation teachers use and recommend Breath Ball to do breathing exercises.īreath Ball helps you to overcome high stress situations, to meditate, and to relax.
Free: Even the free version of Breath Ball provides all the functionality you'll ever need.
Focus on simplicity: Breath Ball is incredibly easy to use and even the first breathing session usually leads to great results.
Breath Ball is the only app you can fully customize to your liking to give you the one breathing app that feels just right.
Maximum customizability: Our well being highly depends on what we like and dislike.
It's the secret why Breath Balls breathing exercises feel natural and work much better than any of the competing apps.
Breath Ball's breathing-curve is based on observations of hundreds of clients.
Four reasons why you should use Breath Ball to do your breathing exercises:

0 notes
Text
Advantages of Using Python Over other Languages
Python language for programming is the latest, fastest growing and most popular programming language. It is a high level, interpreted, objective-oriented and general-purpose scripting language.
Now let us check out the various advantages of utilising python language over other programming languages.
Benefits of using Python programming language According to a top web development company in the UK, The biggest tech companies across the globe use Python for programming. Companies like Pixar takes advantage of Python to produce their films; it is used by Google to crawl into the internet pages; it is used by Netflix to deliver top-quality content to their subscribers; it is used by Spotify to suggest songs to their listeners. The Python language has many advantages that very few know. Some of the top advantages of the Python programming language include:
Simplicity The simple syntax of Python encourages beginners to learn more about this new scripting language. For some types of perspectives, it might look more predetermined and natural that the Python language could turn into what we call the lingua franca for coding, which can cause the other programming opponents as being obsolete. Python's codes are easy to share, comprehend and maintain. You don't need to worry about any verbosity for this programming language and learning it is very easy.
Powerful toolbox According to a top web development company in the UK, Python programming could be easily termed as text files that contain instructions for interpretation and it is written in IDE to the text editor. The IDE is a full-featured service and offers in-built tools such as debuggers, syntax checkers. The text editors and code browsers don't usually contain the IDE features, however, they could be easily customised as per the requirement. The Python language also contains a higher variety of third-party packages, frameworks and libraries which facilitate the process of development. These kinds of optimization capabilities help to make Python most suitable for larger-scale coding projects and software.
Development speed Development speed here means the speed of business and the amount of time taken to reach the market metrics. Python programming is a very scripting language. Therefore, its main usage is intended towards writing the applications from the basics and to plug together all the components of the programming. These components could be designed for reuse whereas the interface between the script and the components could be well defined. This feature accelerates the software development speed, whereas python programming makes the language greatly productive and concise.
Flexibility Python puts special emphasis on the readability and simplicity of the codes rather than focusing on its flexibility. However, this flexibility is already inbuilt into the Python programming language. The Python language can be used across projects of different magnitudes. This allows the software developers to select between procedural and object-oriented modes of programming. Python programming is flexible with the type of data as well. The 5 types of data include String, Number, Tuple, List, and Dictionary. Every type of sub-data corresponds to anyone among these types of roots. Thus, this type of explanatory analysis of the data becomes very easy to conduct only because of the flexibility of the Python language.
Portability Portability is one of the biggest advantages of the Python programming language over other programming languages. It is designed for optimum portability. The programs support any kind of modern computer operating system. The advanced-level characteristics of the programming language allow the python script to be easily interpreted. Therefore, it could be easily written for any kind of advanced interpretation seamlessly on Windows, Linux, UNIX, and Mac os without any adjustment requirements. The Python programming language also allows better implementation of the portable GUIs for the operating systems.
You can now hire a python programmer exclusively at Tecocraft.
Stronger community The user base of python programming has been rapidly growing. This is an actual representation of the building up of a very strong community around the python programming software. You could find thousands of python programming contributors towards its powerful toolbox. These are called the Pythonists. You can find almost 210,000 strong custom-built packages of software around Python that are user uploaded on the online repository. Thai all positively implies the greater supportive community that is the main reason for its success and the positive consequences of a programming language that is very much in demand.
If you want to hire a python programmer, you must visit Tecocraft today.
#web development company uk#web development agency UK#website development company in uk#hire python developer#hire python programmer
0 notes